Systematic Method for Identifying Safety and Security Requirements in Autonomous Driving: Case Study of Autonomous Intersection System
Abstract
1. Introduction
2. State of the Art
2.1. Systems Engineering
2.1.1. Model Based Systems Engineering
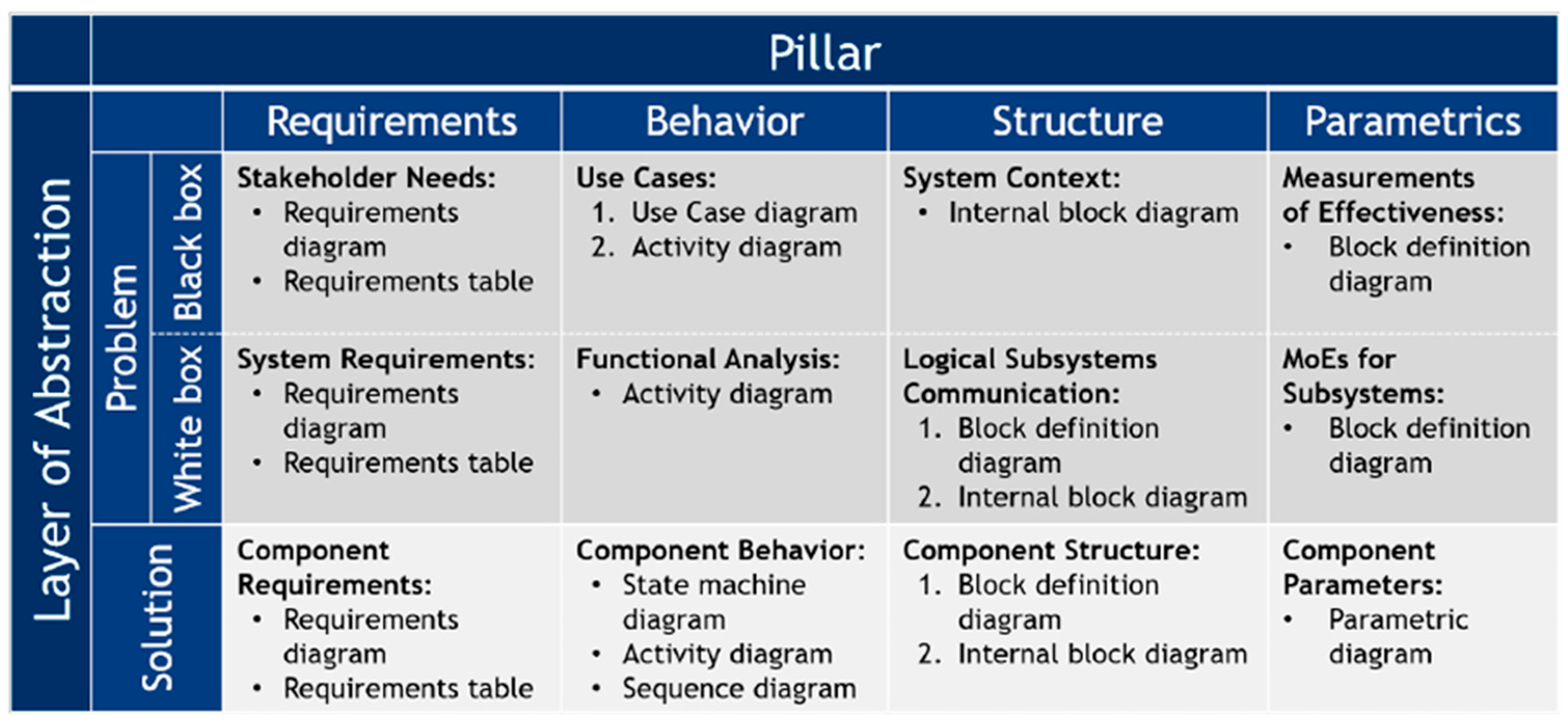
2.1.2. MBSE Grid Method
2.2. Safety and Security Engineering
2.2.1. Requirements Engineering for Safety and Security
2.2.2. Safety Engineering Methods
2.2.3. Security Engineering Methods
2.2.4. MBSE Based Approaches to Safety and Security Engineering
2.3. Research Questions
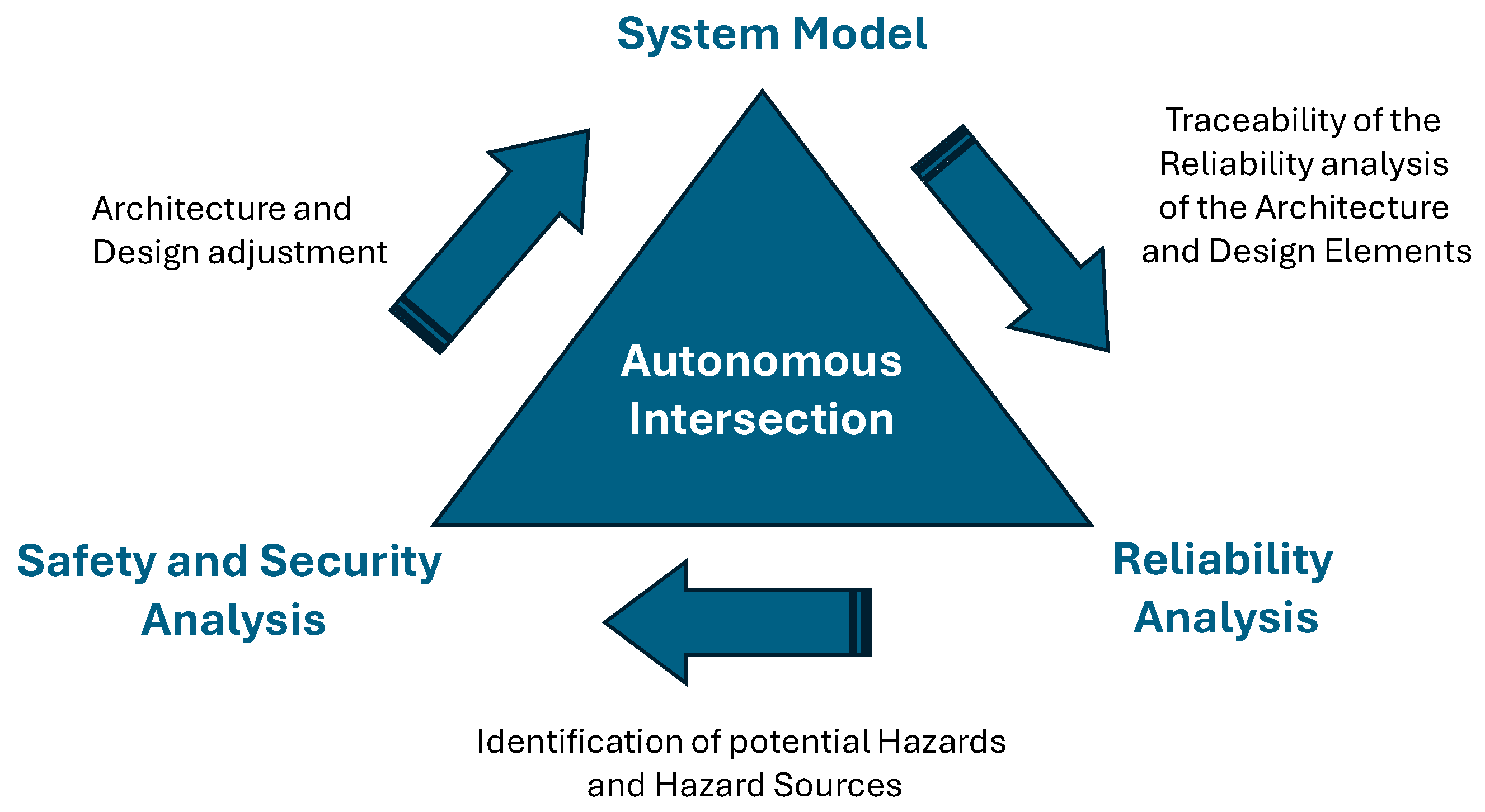
3. Development of the Intersection System Model
3.1. System Elements
3.2. Framework Development
3.3. MBSE Modeling—Black Box Problem Level
3.3.1. Stakeholder Needs
3.3.2. Use Cases
3.3.3. System Context
3.4. MBSE Modeling—White Box Problem Level
3.4.1. System Requirements
3.4.2. Functional Analysis
3.4.3. Logical Architecture
3.5. MBSE Modeling—Solution Level
3.5.1. Component Requirements
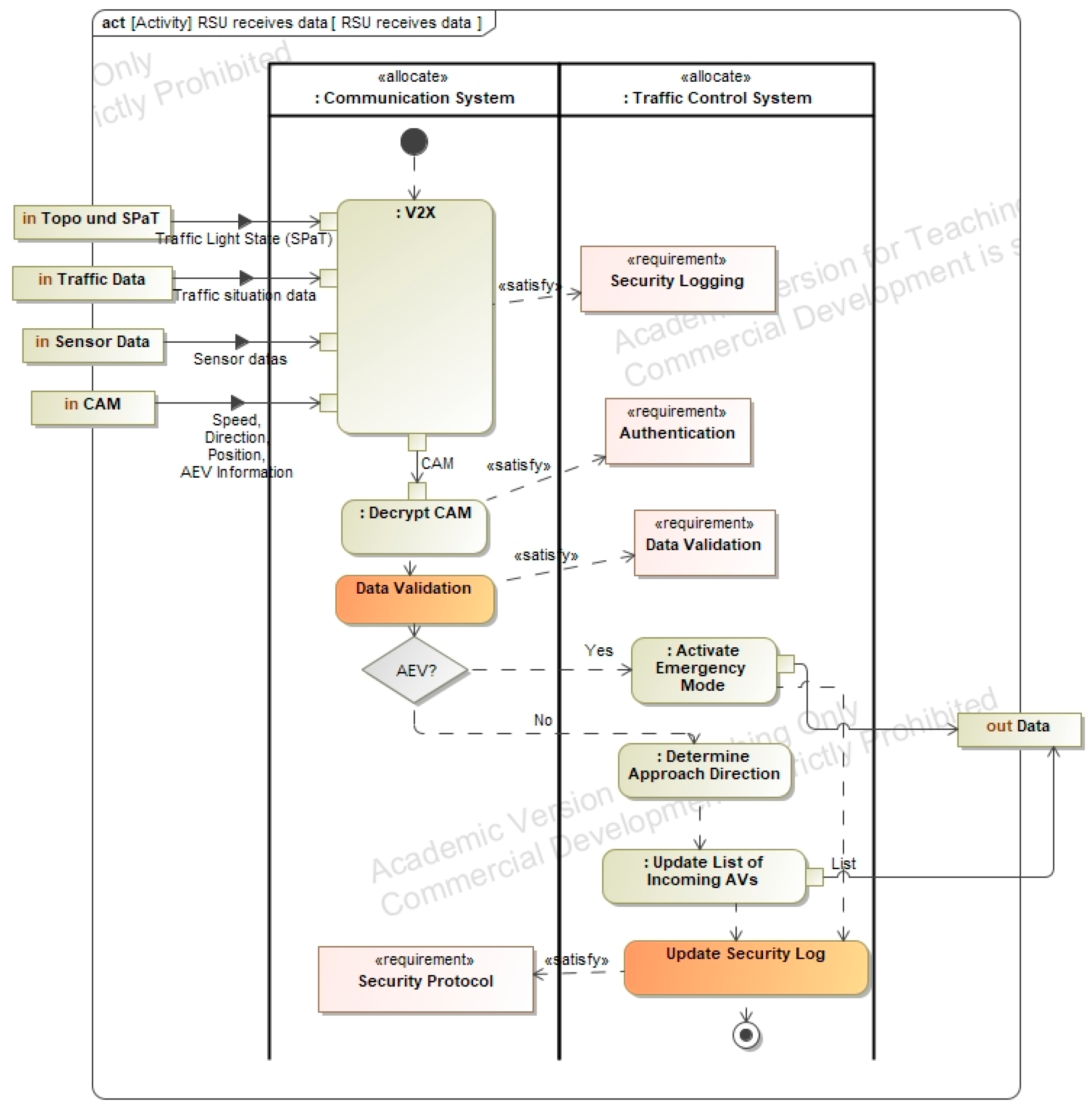
3.5.2. Component Behavior
3.5.3. Component Assembly
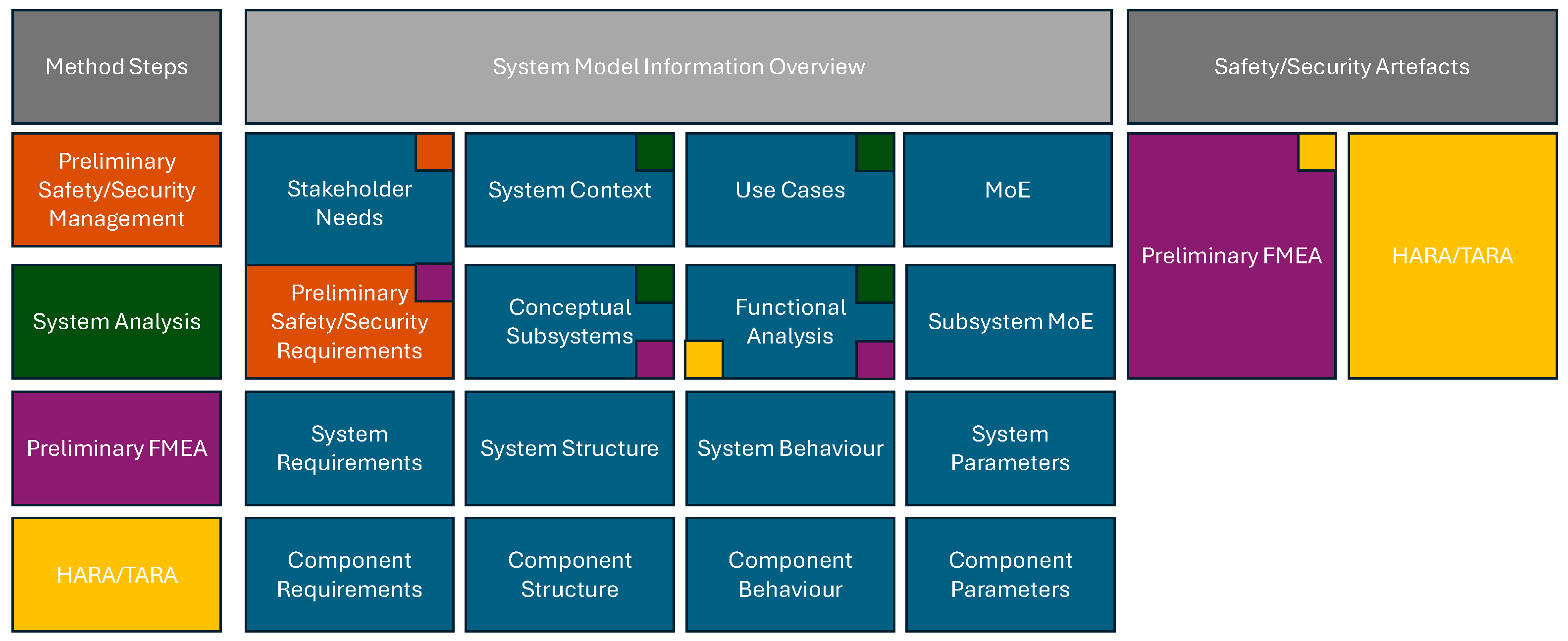
4. Method for Identifying Safety and Security Requirements
4.1. Dassault Systemes Safety and Reliability Analysis
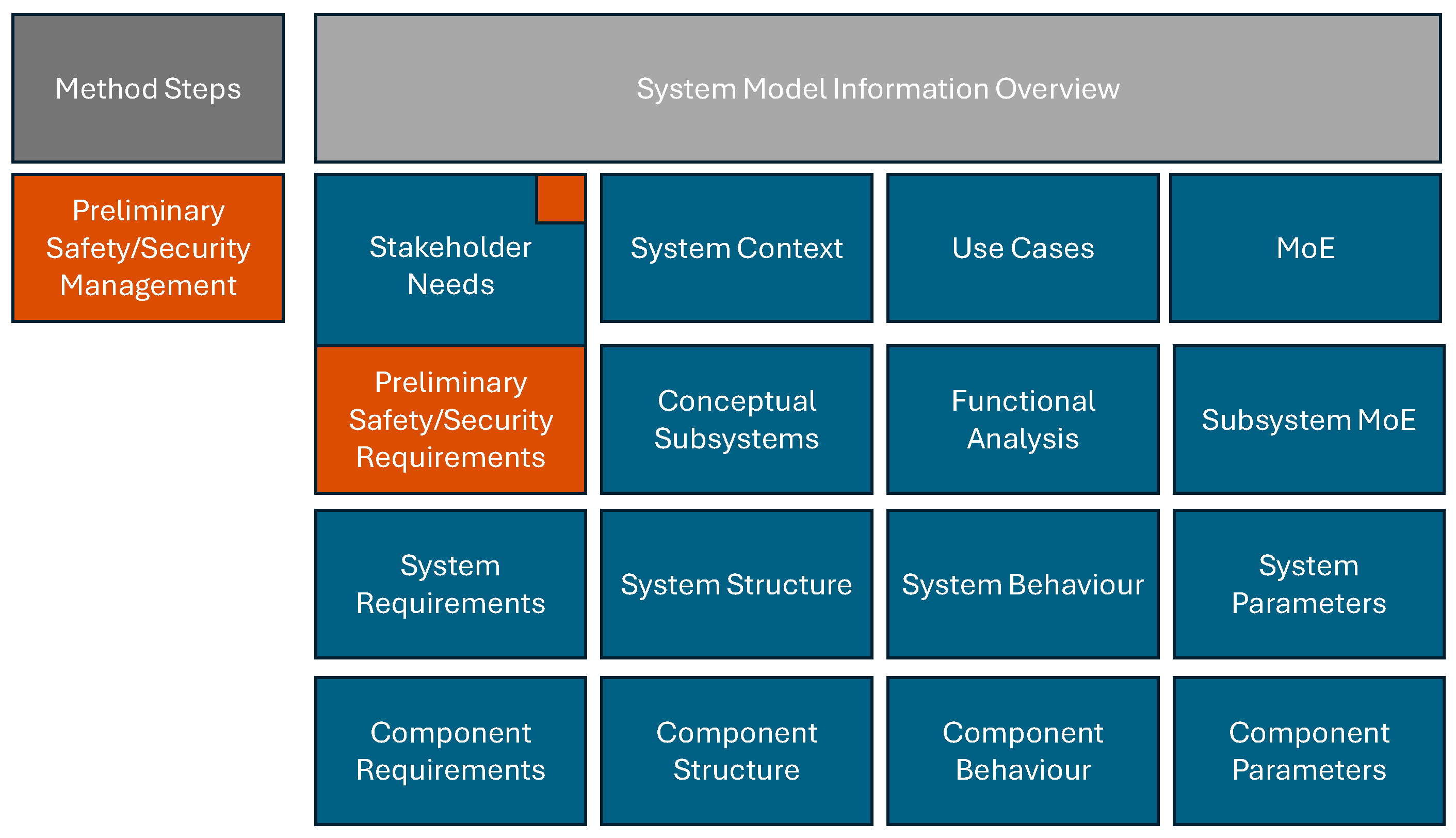
4.2. Method for the General Implementation of Safety and Security Requirements
4.2.1. Initialization of the Method
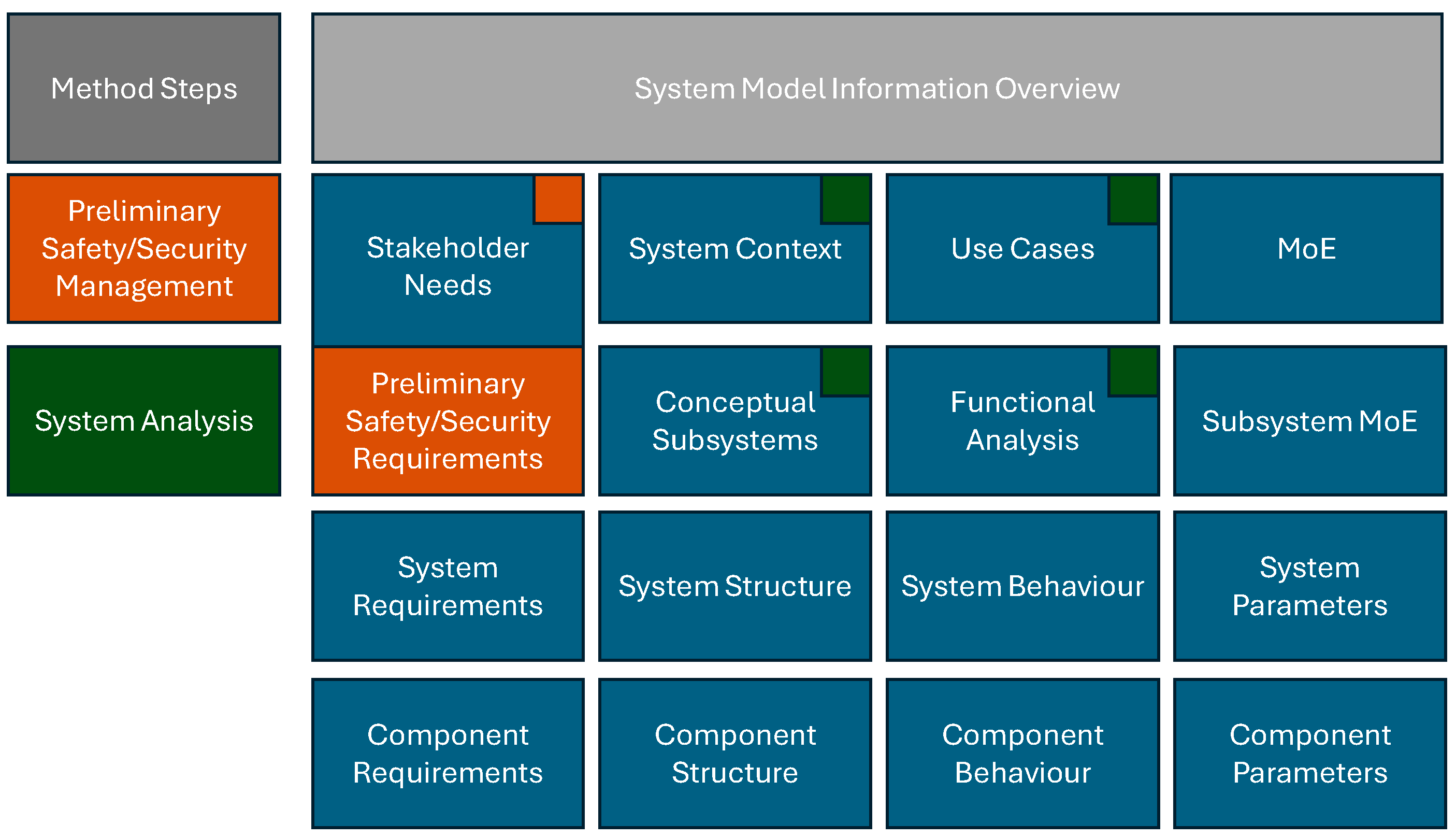
4.2.2. Preliminary Safety and Security Management
4.2.3. System Analysis
4.2.4. System FMEA
4.2.5. HARA/TARA
4.2.6. Safety/Security Concept
5. Application of the Method to the Autonomous Intersection System
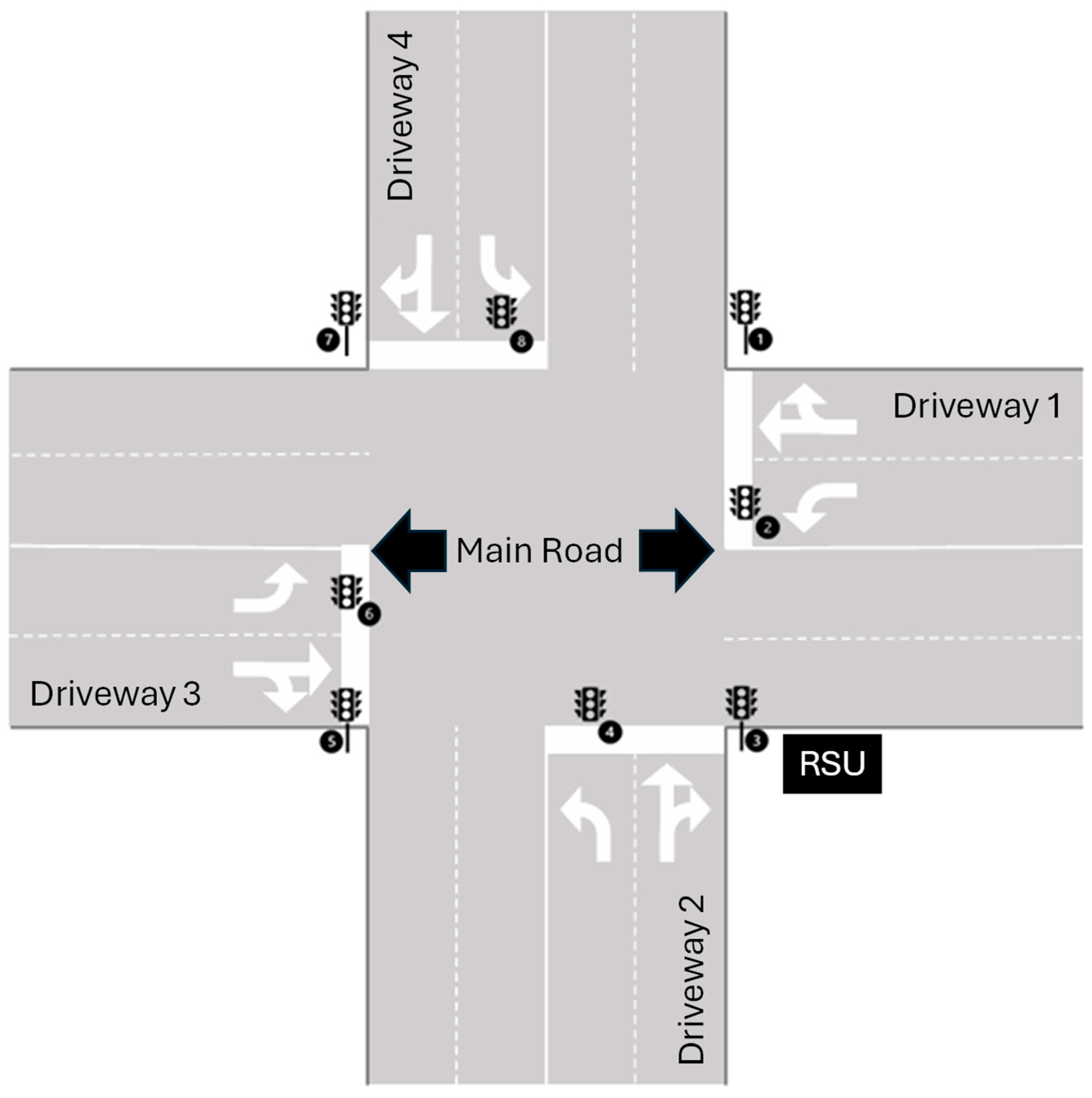
5.1. Modeling Scope and Context
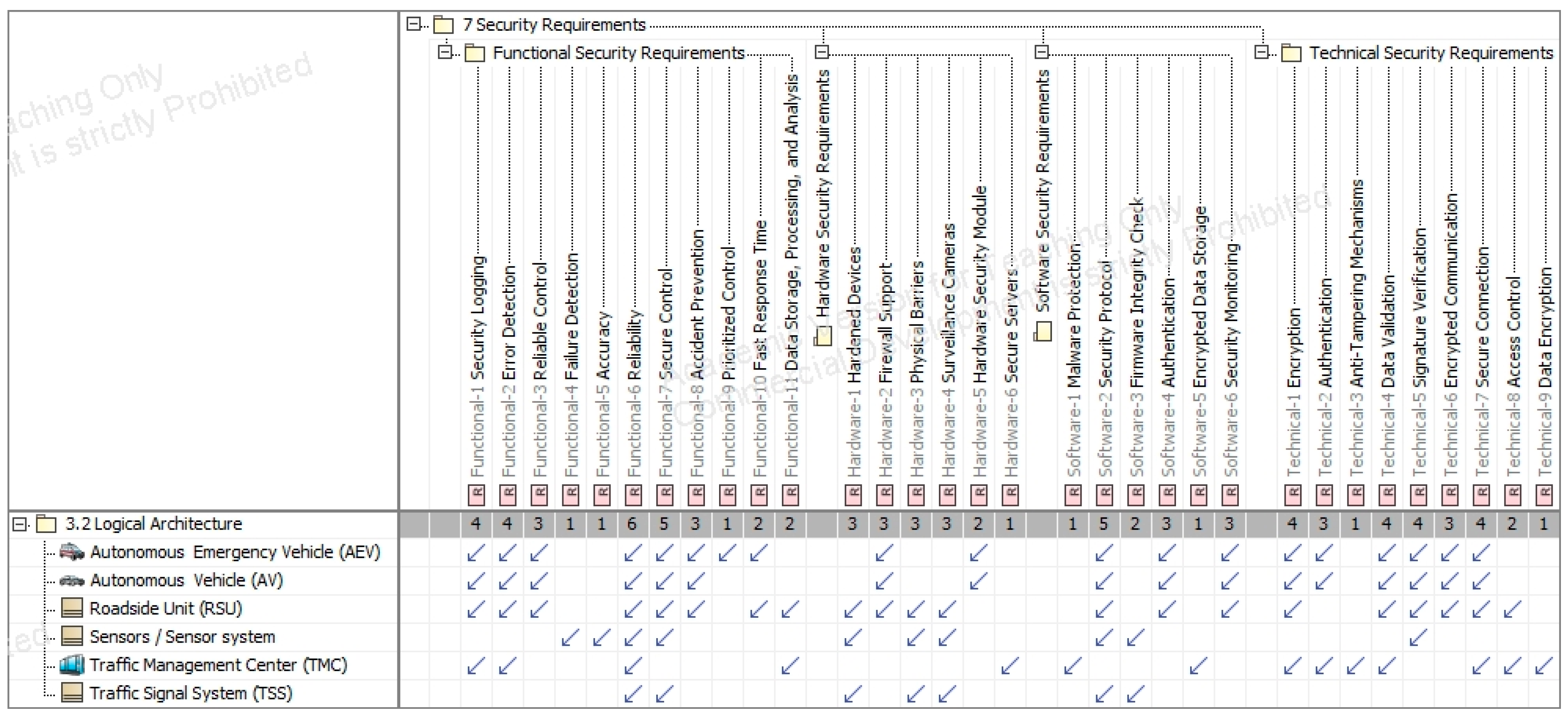
5.2. Integration of Preliminary Safety and Security Requirements
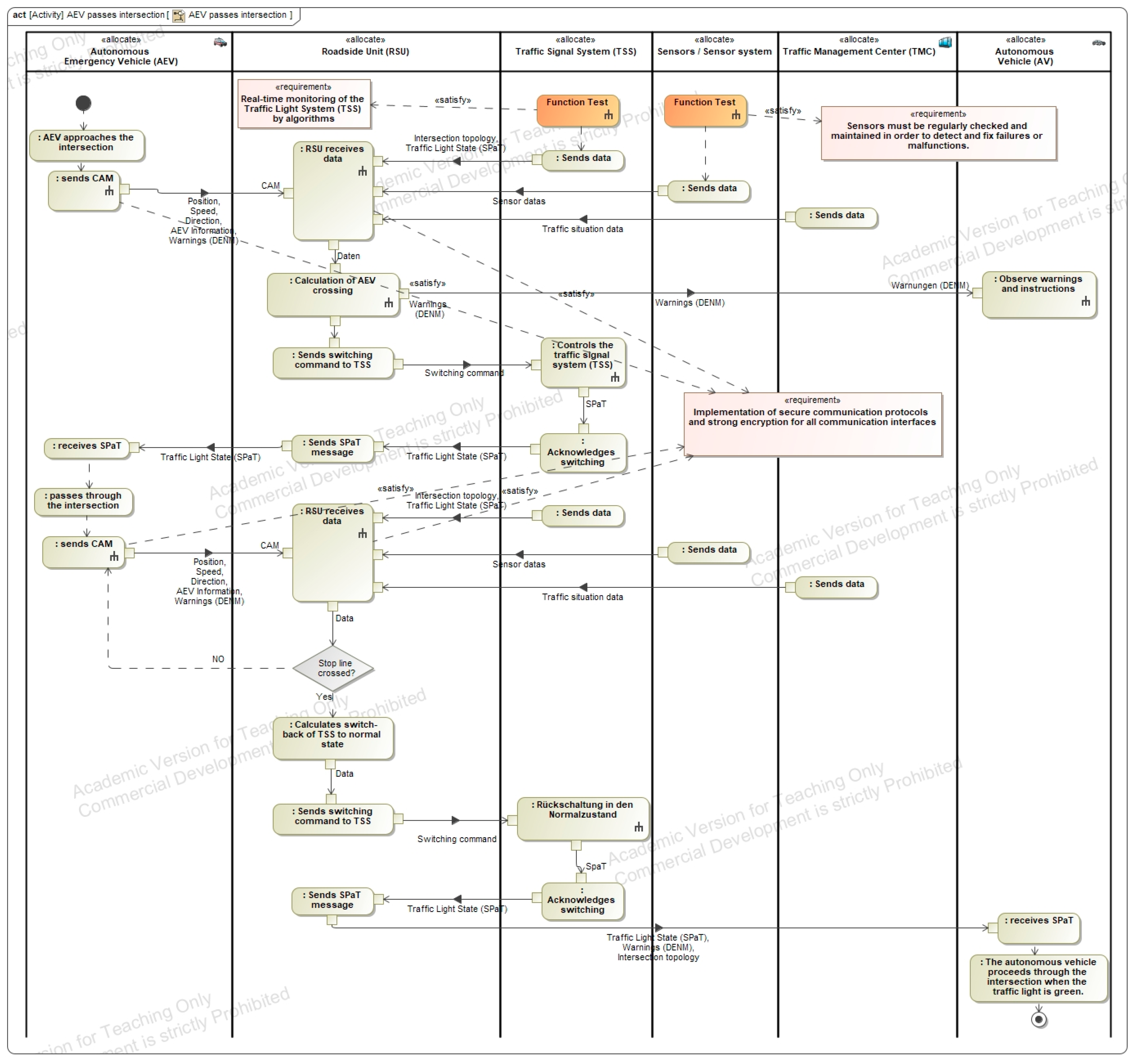
5.3. System Analysis
5.4. System FMEA
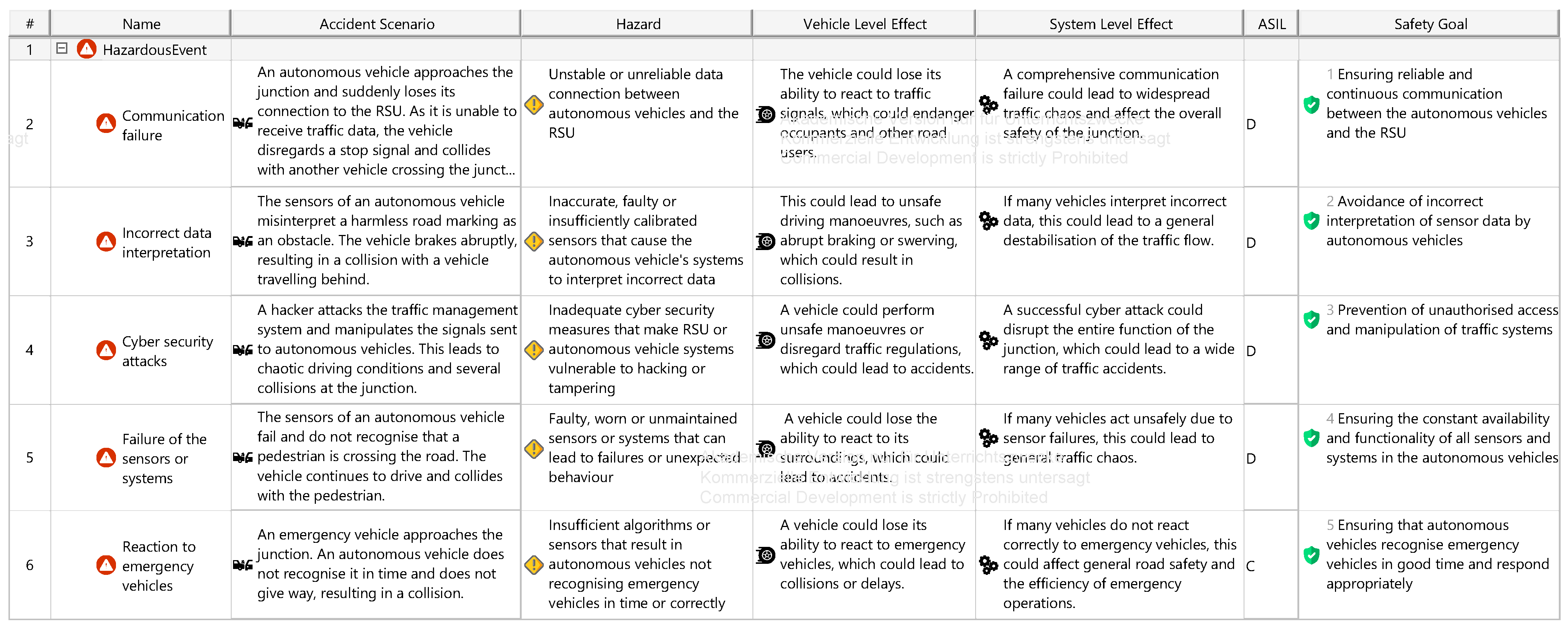
5.5. HARA/TARA
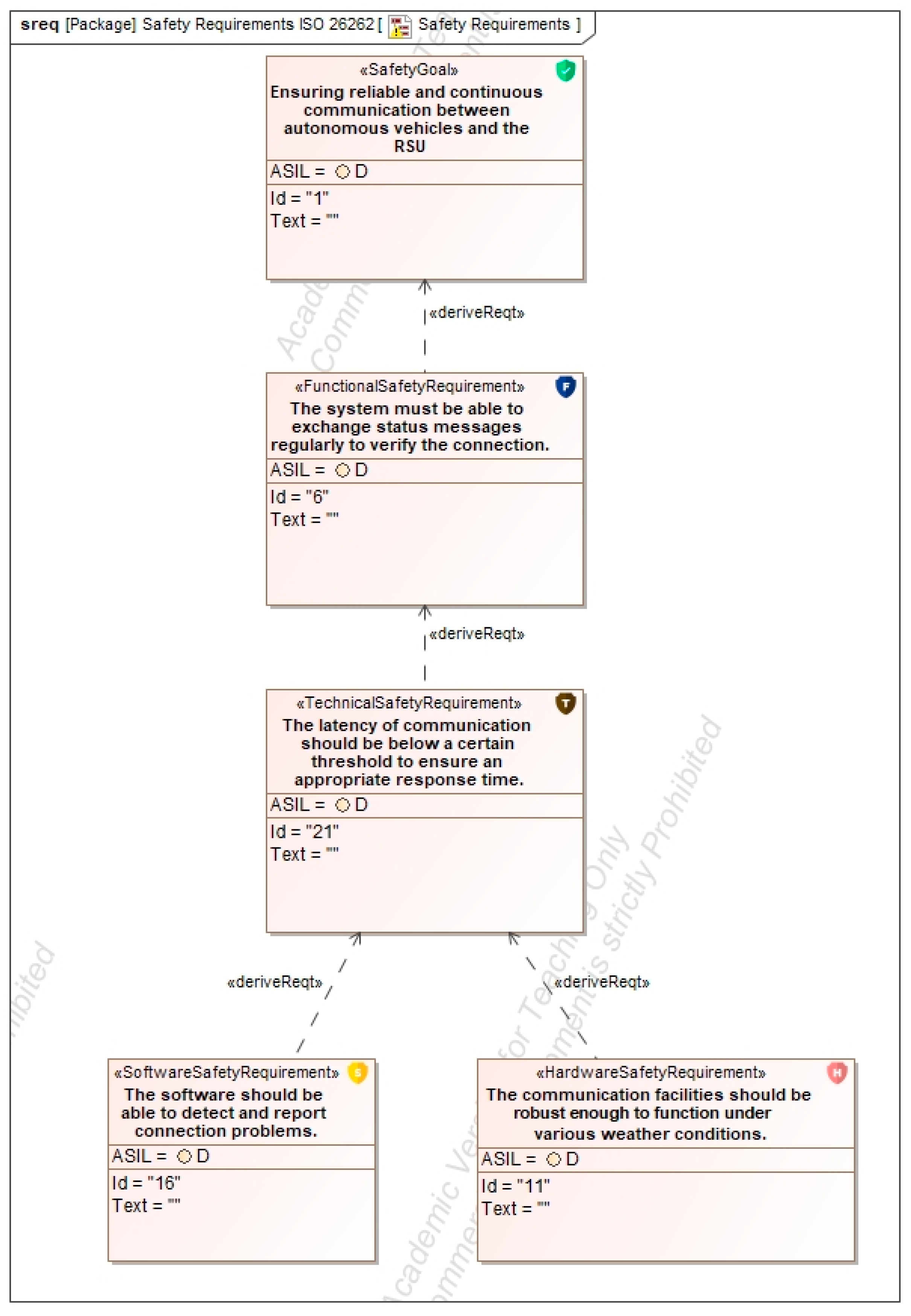
5.6. Safety/Security Concept
6. Discussion
7. Conclusions
8. Outlook
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| ASIL | Automotive Safety Integrity Level |
| AEV | Autonomous Emergency Vehicle |
| AV | Autonomous Vehicle |
| CPS | Cyber Physical System |
| DET | Detectability |
| FMEA | Failure Mode and Effects Analysis |
| FTA | Failure Tree Analysis |
| HARA | Hazard analysis and Risk Assessment |
| Hazop | Hazard and Operapility Study |
| IEC | International Electrotechnical Comission |
| INCOSE | International Council on Systems Engineering |
| ISO | International Organisation for Standardisation |
| LIDAR | Light Detection and Ranging |
| LSA(TSS) | Traffic Signal System |
| MBSE | Model Based Systems Engineering |
| MoE | Measures of Effectiveness |
| OCC | Occurrence |
| OMG | Object Management Group |
| RPN | Risk Priority Number |
| RSU | Roadside Unit |
| SE | Systems Engineering |
| SEV | Severity |
| STRIDE | Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, Elevation of Privilege |
| SysML | System Modeling Language |
| TARA | Threat Analysis and Risk Assessment |
| TMC | Traffic Management Center |
| V2X | Vehicle to X |
| VDI | Verein Deutscher Ingenieure |
Appendix A
Appendix A.1. Problem (Black Box) Diagrams
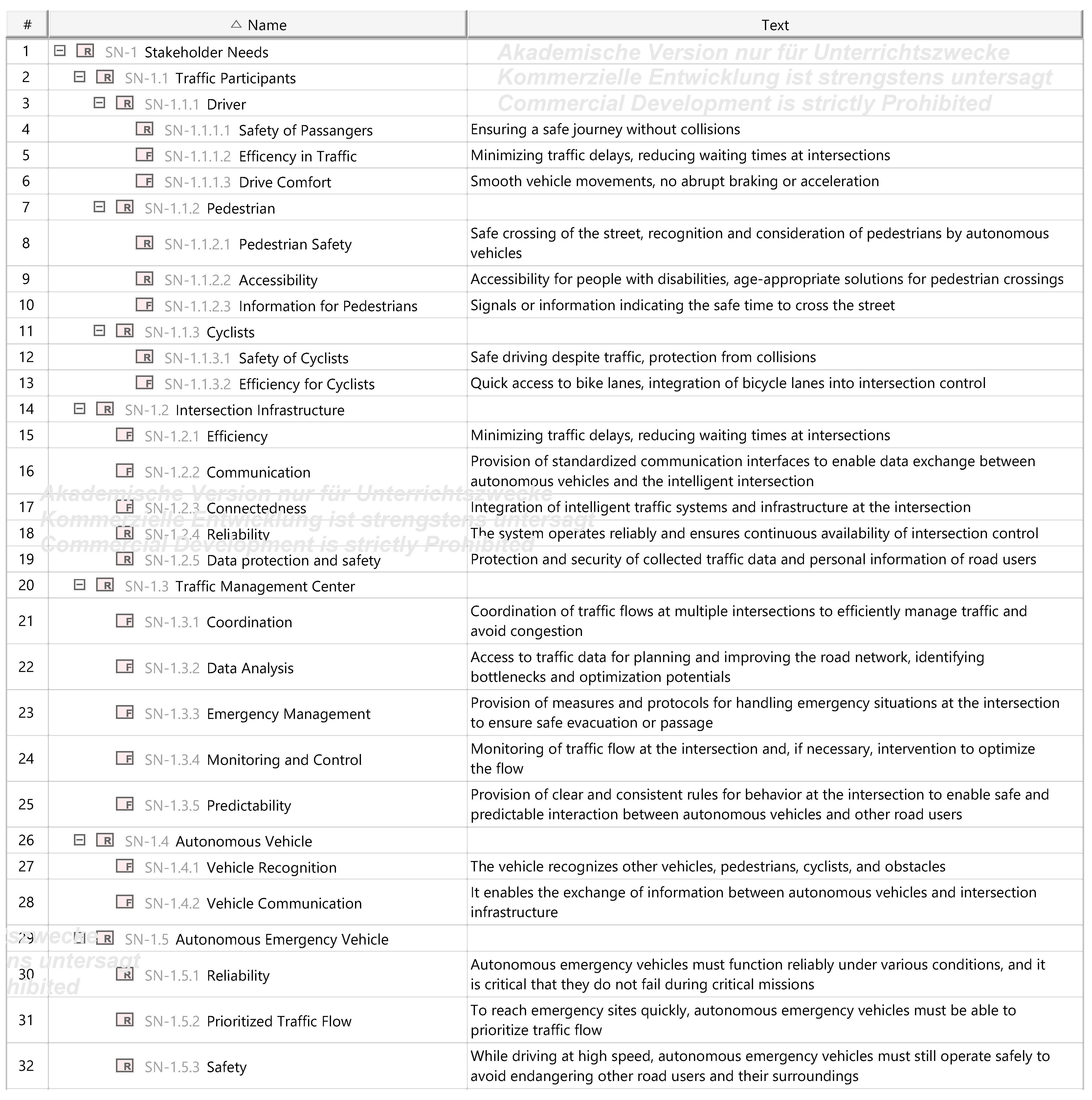
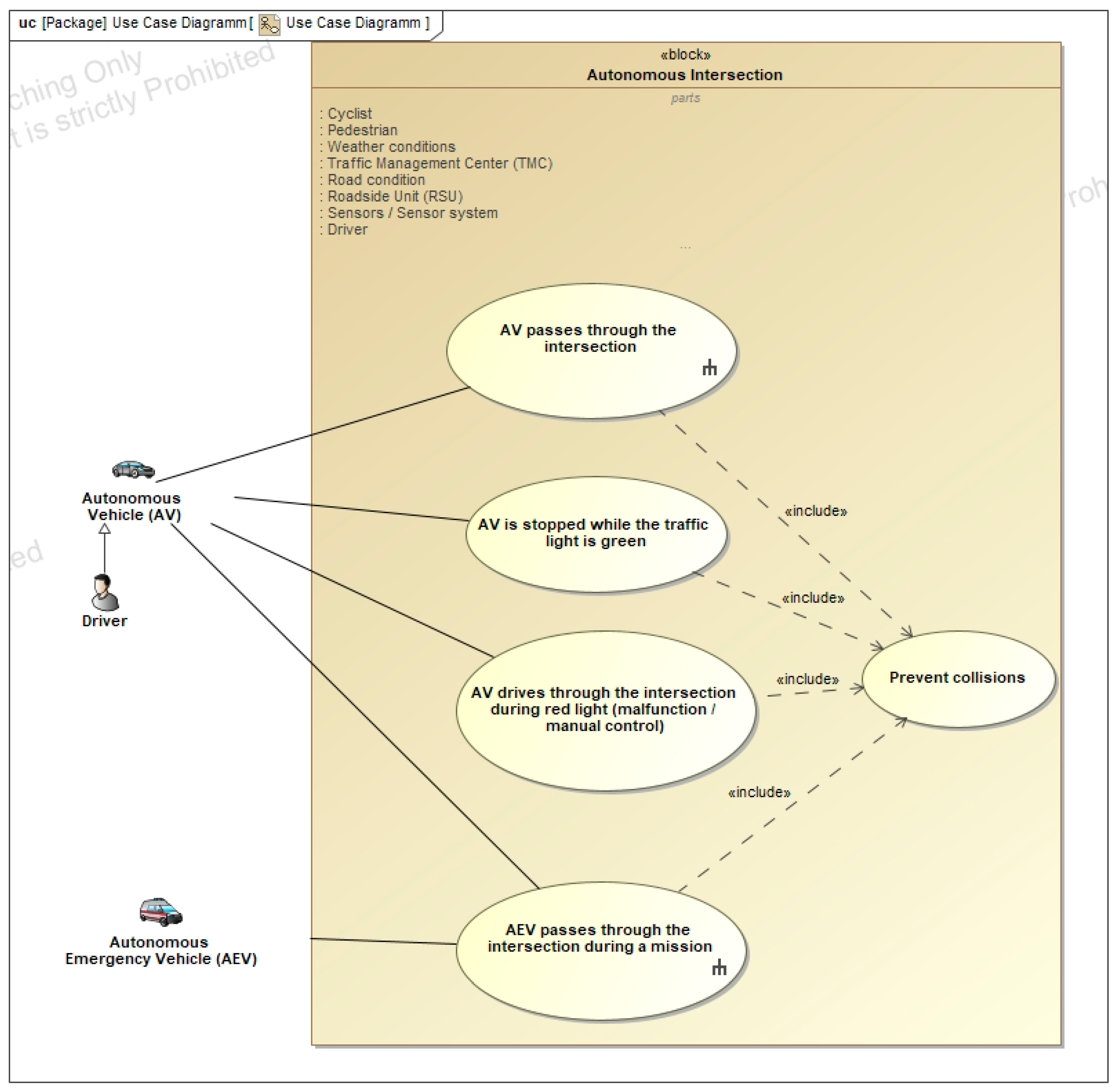


Appendix A.2. Problem (White Box) Diagrams
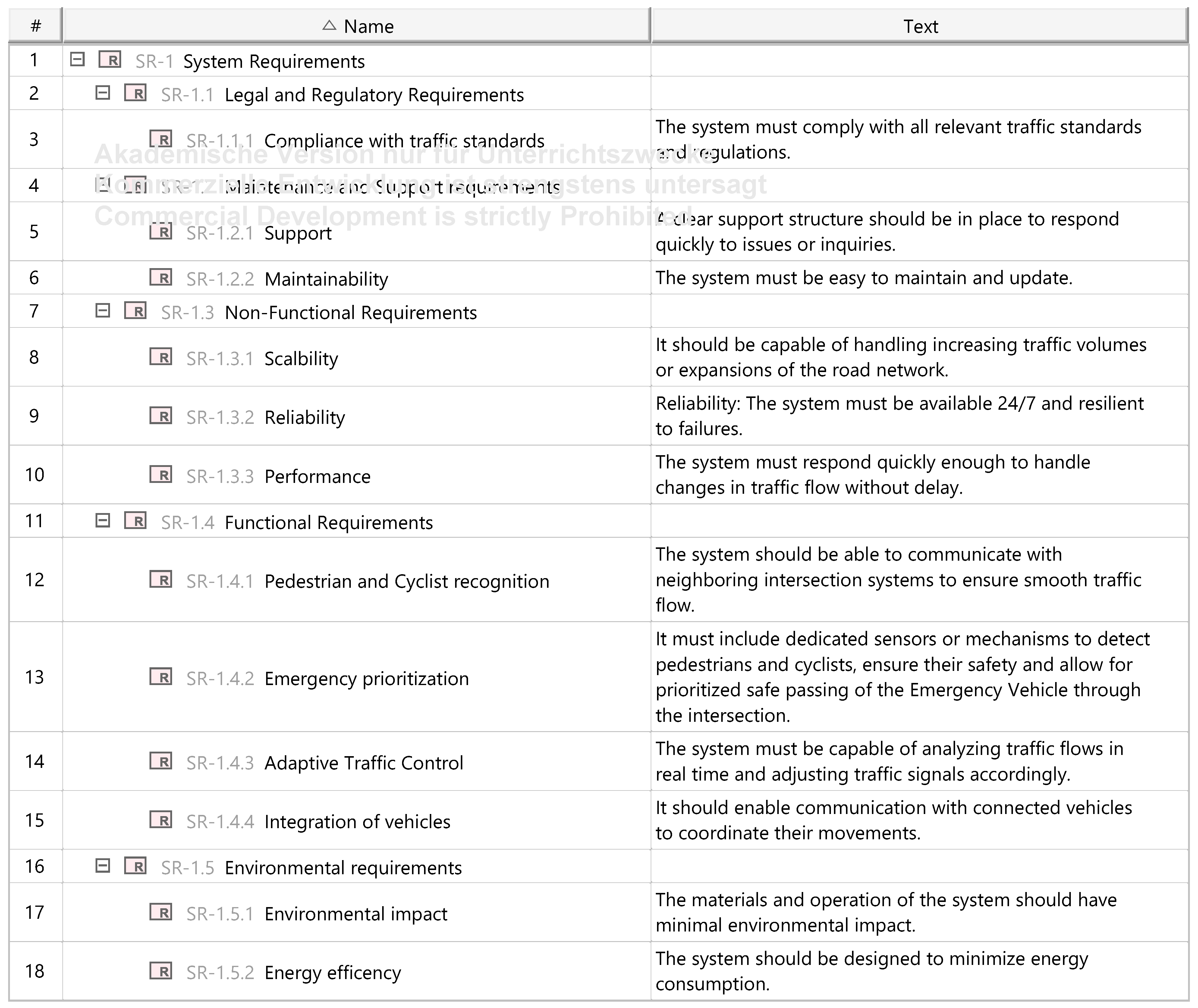
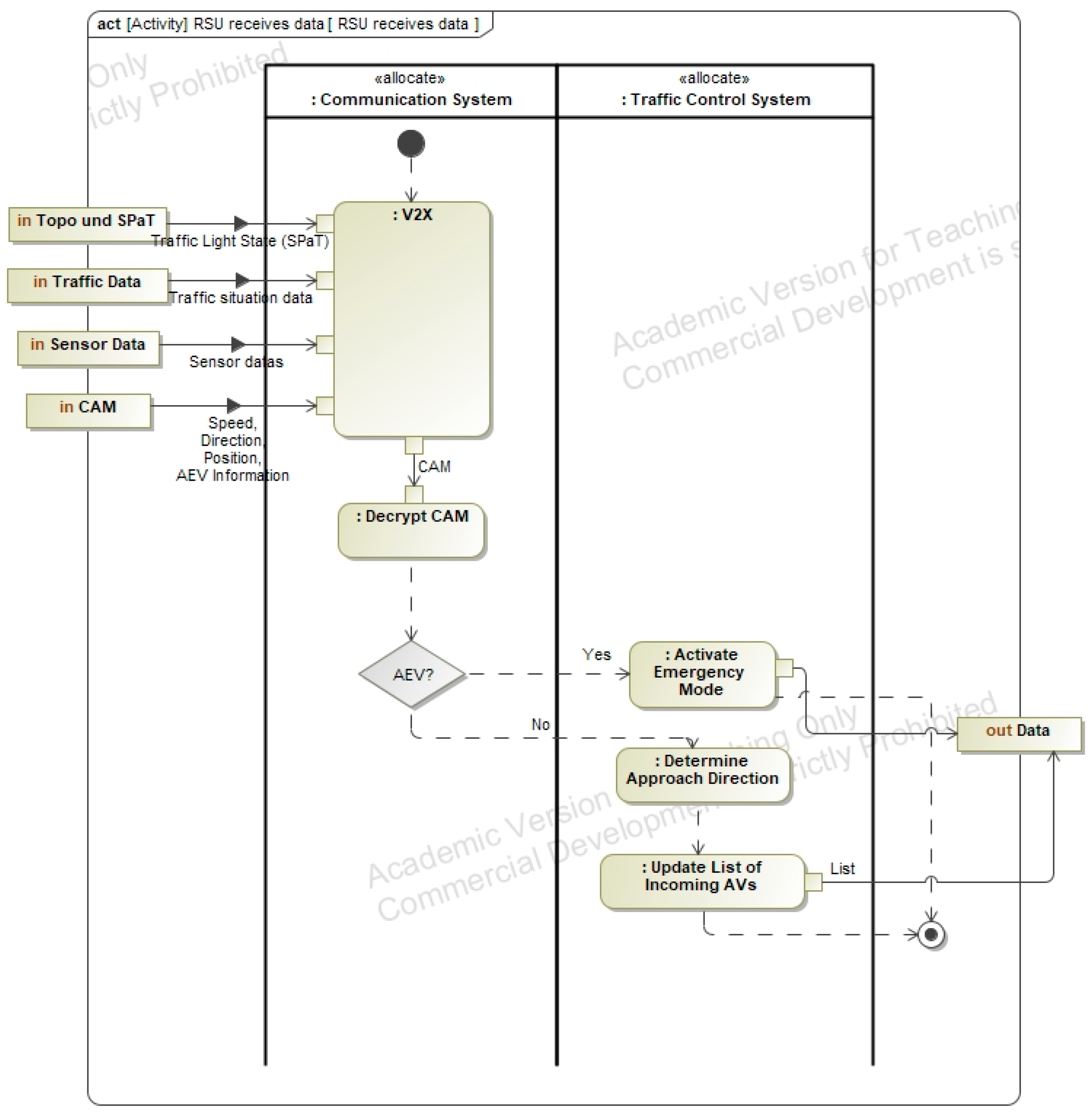
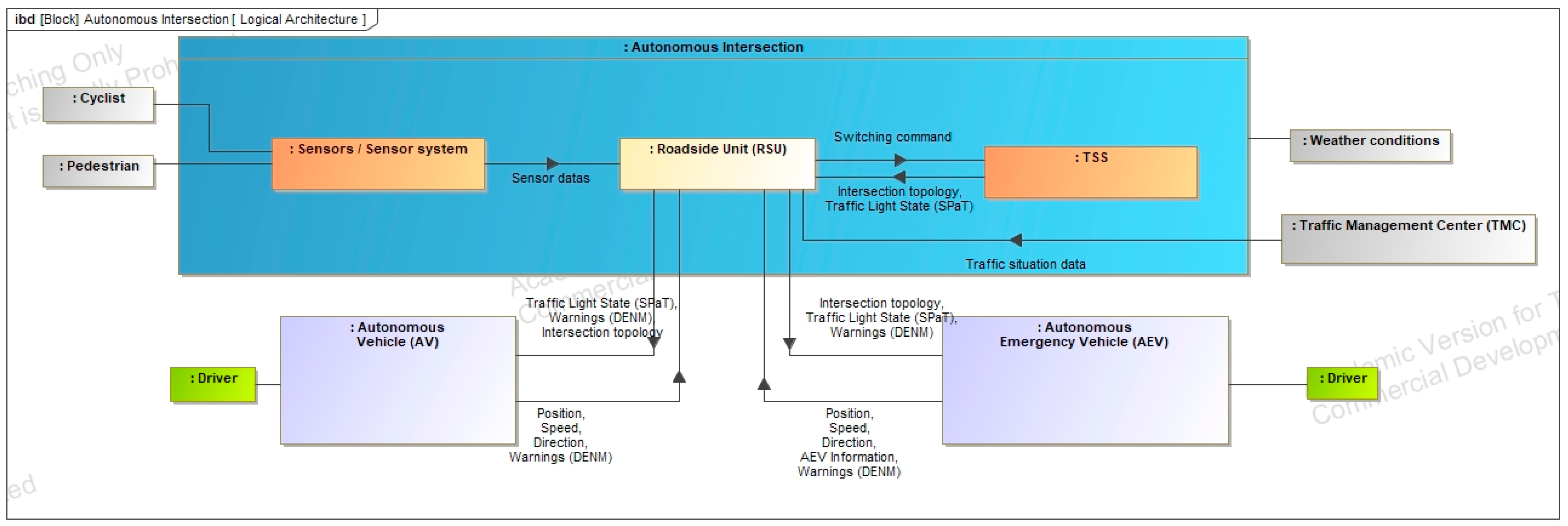
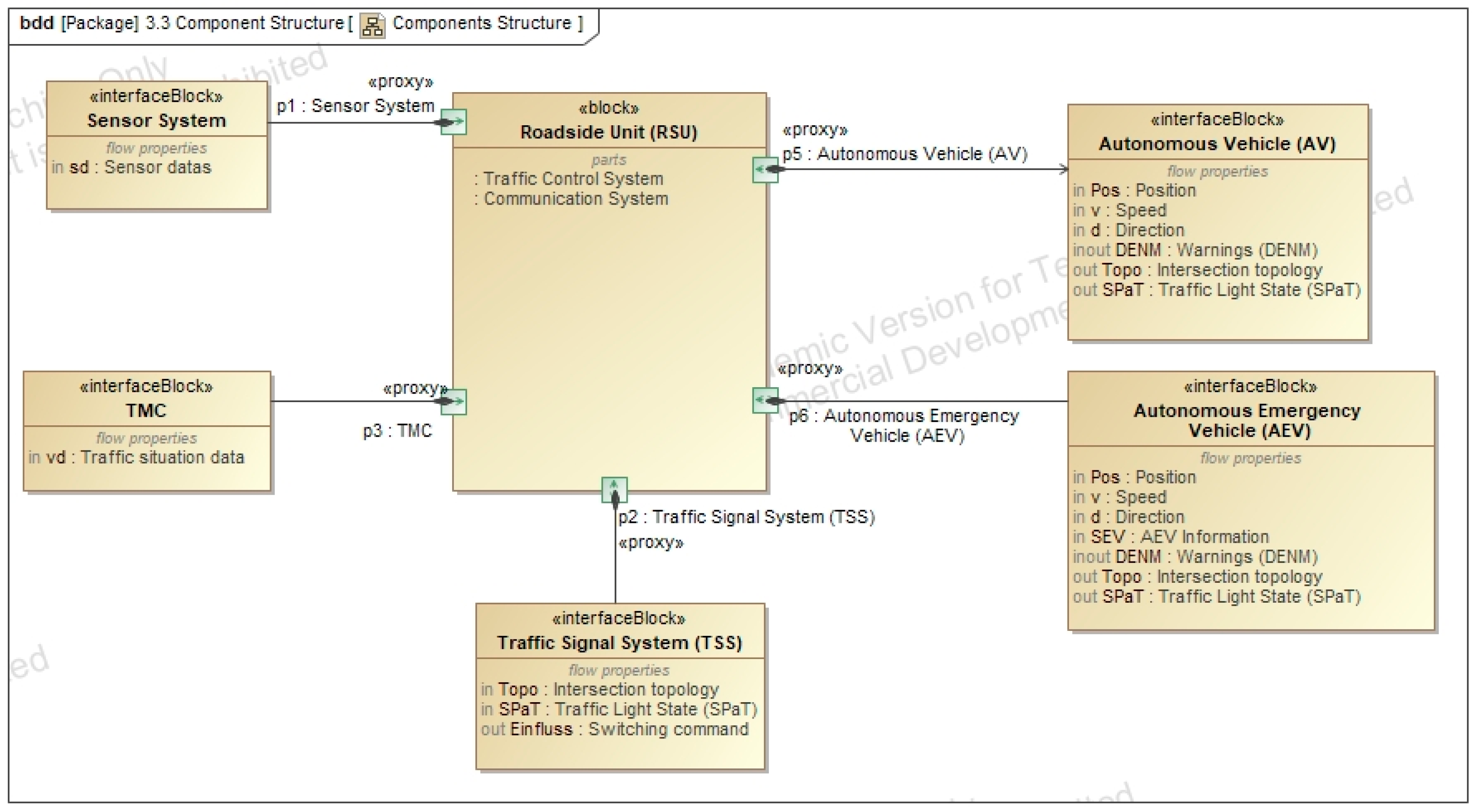
Appendix A.3. Solution Diagrams



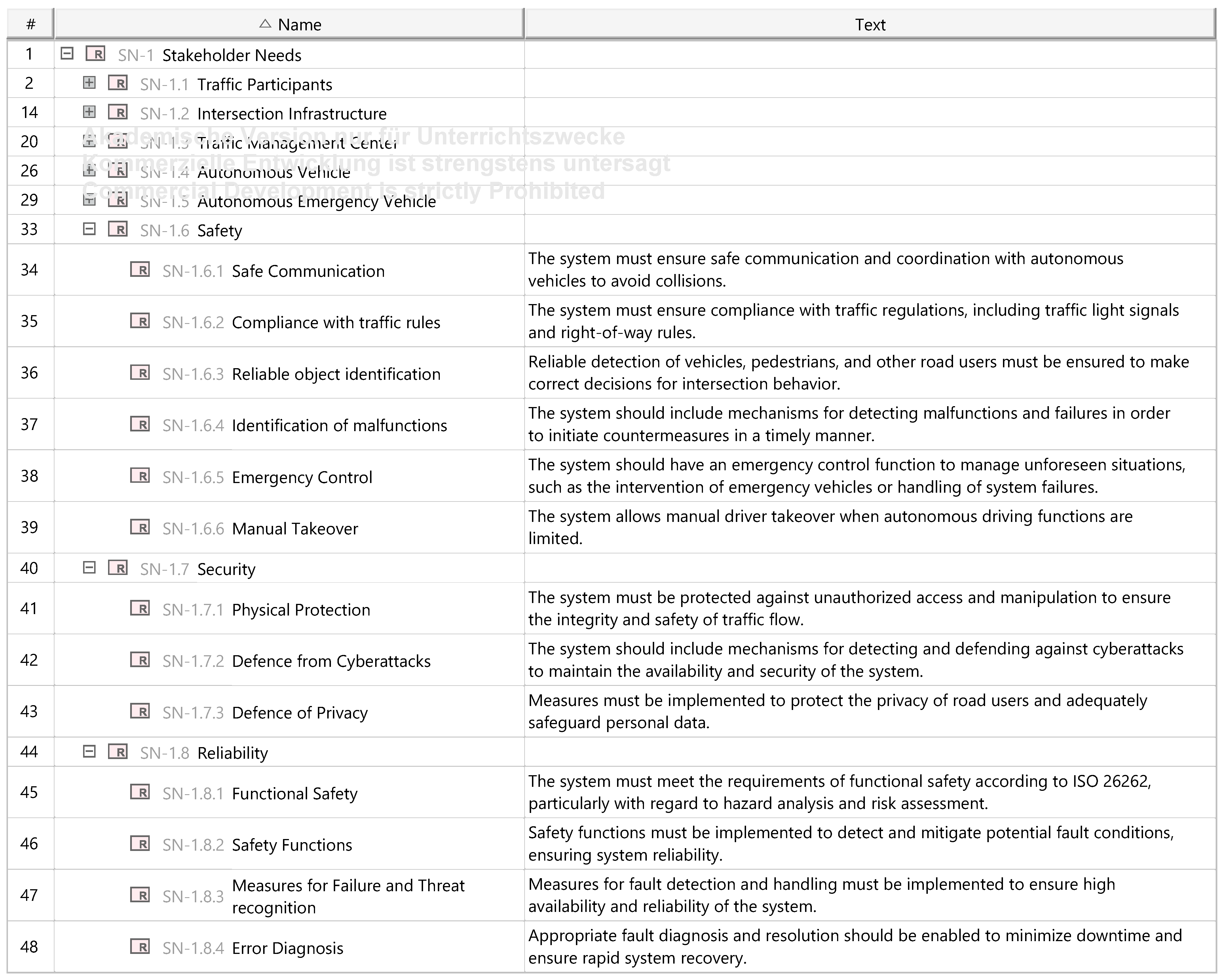
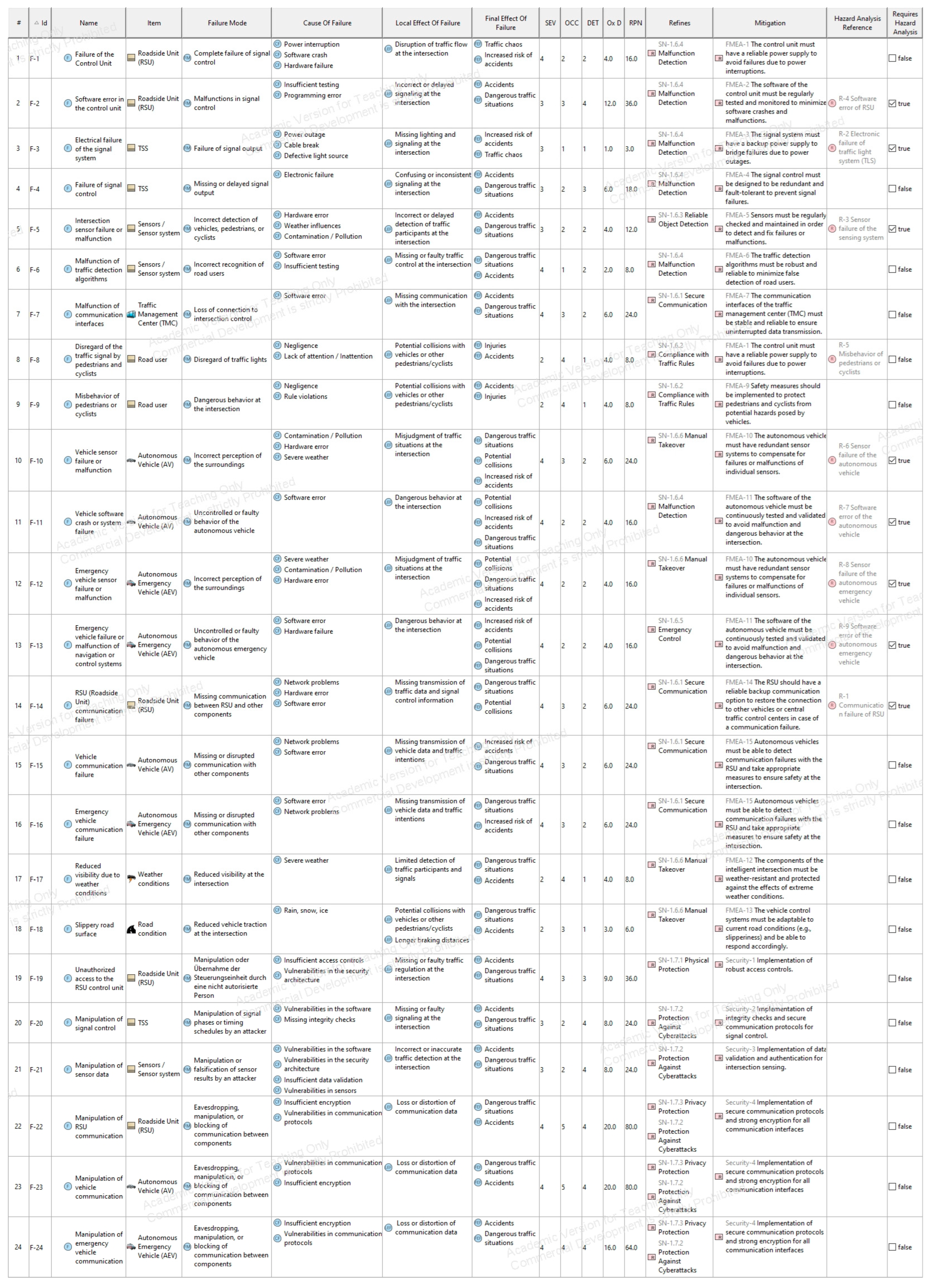
Appendix A.4. Method Implementation

| ID | Location | Assets | Threats | Attacks | Threat Level | Impact Level | Security Level | Security Goal |
|---|---|---|---|---|---|---|---|---|
| 1 | RSU | Data | Hacker attack | Malware, Hacking, Physical attack | High | High | Medium | Integrity, Confidentiality |
| 2 | TSS | Control | Sabotage | Physical attack | Medium | High | Medium | Availability |
| 3 | Sensors | Information | Manipulation | Malware, Hacking | High | Medium | Low | Integrity |
| 4 | AV | Vehicle control | Unauthorized control | Hacking | High | High | Medium | Safety, Integrity |
| 5 | AEV | Control | Unauthorized control | Hacking | High | High | Medium | Safety, Integrity |
| 6 | TMC | Traffic data | Data theft | Malware, Hacking | Medium | Medium | High | Confidentiality |
| 7 | Pedestrians/Cyclists | Safety | Accidents due to system failure | Technical failure | High | High | Low | Safety |
References
- Gausemeier, J.; Czaja, A.; Wiederkehr, O.; Dumitrescu, R.; Tschirner, C.; Steffen, D. Studie: Systems Engineering in der industriellen Praxis. In Tag des Systems Engineering; Maurer, M., Schulze, S.-O., Eds.; Carl Hanser Verlag GmbH & Co. KG: München, Germany, 2013; pp. 113–122. ISBN 978-3-446-43915-3. [Google Scholar]
- Alt, O. Modellbasierte Systementwicklung mit SysML; Carl Hanser Verlag GmbH & Co. KG: München, Germany, 2012; ISBN 978-3-446-43066-2. [Google Scholar]
- VDI/VDE 2206:2021-11; Development of Mechatronic and Cyber-Physical Systems. Verein Deutscher Ingenieure (VDI): Düsseldorf, Germany, 2021.
- Windolph, A. Das V-Modell im Projektmanagement: Definition, Typen und Phasen. Available online: https://projekte-leicht-gemacht.de/blog/projektmanagement/klassisch/v-modell/ (accessed on 8 April 2025).
- INCOSE. Systems Engineering Vision 2020; INCOSE: San Diego, CA, USA, 2007. [Google Scholar]
- Hick, H.; Bajzek, M.; Faustmann, C. Definition of a system model for model-based development. SN Appl. Sci. 2019, 1, 1074. [Google Scholar] [CrossRef]
- Two Pillars GmbH. What Is MBSE? Available online: https://www.two-pillars.de/was-ist-mbse/ (accessed on 8 April 2025).
- Huth, T.; Vietor, T. Systems Engineering in der Produktentwicklung: Verständnis, Theorie und Praxis aus ingenieurswissenschaftlicher Sicht. Gr. Interakt. Org. 2020, 51, 125–130. [Google Scholar] [CrossRef]
- Friedenthal, S.; Moore, A.; Steiner, R. A practical Guide to SysML: The Systems Modeling Language, 3rd ed.; Elsevier: Amsterdam, The Netherlands; Morgan Kaufmann: Waltham, MA, USA, 2015; ISBN 0128008008. [Google Scholar]
- Morkevicius, A.; Aleksandraviciene, A.; Mazeika, D.; Bisikirskiene, L.; Strolia, Z. MBSE Grid: A Simplified SysML-Based Approach for Modeling Complex Systems. INCOSE Int. Symp. 2017, 27, 136–150. [Google Scholar] [CrossRef]
- Yaacoub, J.-P.A.; Salman, O.; Noura, H.N.; Kaaniche, N.; Chehab, A.; Malli, M. Cyber-physical systems security: Limitations, issues and future trends. Microprocess. Microsyst. 2020, 77, 103201. [Google Scholar] [CrossRef]
- Macher, G.; Schmittner, C.; Veledar, O.; Brenner, E. ISO/SAE DIS 21434 Automotive Cybersecurity Standard—In a Nutshell. In Proceedings of the International Conference on Computer Safety, Reliability, and Security. SAFECOMP 2020 Workshops, Lisbon, Portugal, 15 September 2020; Casimiro, A., Ortmeier, F., Schoitsch, E., Bitsch, F., Ferreira, P., Eds.; Springer International Publishing: Cham, Switzerland, 2020; pp. 123–135, ISBN 978-3-030-55582-5. [Google Scholar]
- ISO 26262:2018; Road Vehicles—Functional Safety. International Standards Organization: Geneva, Switzerland, 2018.
- ISO 21434:2021; Road Vehicles—Cybersecurity Engineering. International Standards Organization: Geneva, Switzerland, 2021.
- Tacchini, M. What is Functional Safety. In Functional Safety of Machinery; Tacchini, M., Ed.; Wiley: Hoboken, NJ, USA, 2023; pp. 47–86. ISBN 9781119789048. [Google Scholar]
- Lundgren, B.; Möller, N. Defining Information Security. Sci. Eng. Ethics 2019, 25, 419–441. [Google Scholar] [CrossRef]
- Kriso, S.; Klarmann, J.; Loderhose, C.; Wiemer, F.; Gebauer, C.; Burton, S.; Ihle, M. Safety Oder Security: Sicher Unterwegs in Einer Manipulierten Umwelt. Available online: https://www.embedded-software-engineering.de/safety-oder-security-sicher-unterwegs-in-einer-manipulierten-umwelt-a-813822/ (accessed on 8 April 2025).
- Furrer, F.J. Safety and Security of Cyber-Physical Systems; Springer Fachmedien Wiesbaden: Wiesbaden, Germany, 2022; ISBN 978-3-658-37181-4. [Google Scholar]
- Nolte, B.; Stein, A.; Vietor, T. Designing a Method for Identifying Functional Safety and Cybersecurity Requirements Utilizing Model-Based Systems Engineering. Appl. Syst. Innov. 2025, 8, 45. [Google Scholar] [CrossRef]
- Ebert, C.; Brasse, M.; Metzker, E. Safety and security requirements engineering. In Proceedings of the 16th Internationales Stuttgarter Symposium, Stuttgart, Germany, 15–16 March 2016; Bargende, M., Reuss, H.-C., Wiedemann, J., Eds.; Springer Fachmedien Wiesbaden: Wiesbaden, Germany, 2016; pp. 1171–1182, ISBN 978-3-658-13254-5. [Google Scholar]
- Tietjen, T.; Decker, A. FMEA-Praxis: Einstieg in die Risikoabschätzung von Produkten, Prozessen und Systemen, 4th ed.; Carl Hanser Verlag GmbH & Co. KG: München, Germany, 2020; ISBN 9783446462113. [Google Scholar]
- Edler, F.; Soden, M.; Hankammer, R. Fehlerbaumanalyse in Theorie und Praxis; Springer: Berlin/Heidelberg, Germany, 2015; ISBN 978-3-662-48165-3. [Google Scholar]
- International Electrotechnical Commission; International Electrotechnical Commission Technical Committee 56. Hazard and Operability Studies (HAZOP Studies): Application Guide/International Electrotechnical Commission = Études de Danger et d’Exploitatbilité (Études HAZOP): Guide d’Application/Commission Electrotechnique Internationale, 2nd ed.; International Electrotechnical Commission: Geneva, Switzerland, 2016; ISBN 9782832232088. [Google Scholar]
- Okamura, H.; Dohi, T. SRATS: Software reliability assessment tool on spreadsheet (Experience report). In Proceedings of the 2013 IEEE 24th International Symposium on Software Reliability Engineering (ISSRE 2013), Pasadena, CA, USA, 4–7 November 2013; pp. 100–107. [Google Scholar]
- Microsoft. Threat Modeling. Available online: https://www.microsoft.com/en-us/securityengineering/sdl/threatmodeling (accessed on 8 April 2025).
- Verein Deutscher Ingenieure. Automotive Security 2019; Verein Deutscher Ingenieure (VDI): Düsseldorf, Germany, 2019; ISBN 9783181023587. [Google Scholar]
- Wuthishuwong, C.; Traechtler, A.; Bruns, T. Safe trajectory planning for autonomous intersection management by using vehicle to infrastructure communication. J. Wirel. Com. Netw. 2015, 2015, 33. [Google Scholar] [CrossRef]
- Wang, C.; Ma, X.; Jia, L.; Lai, Z.; Yang, Z.; Yan, H.; Zhao, J. CPS Architecture Design for Urban Roadway Intersections Based on MBSE. J. Int. Con. Veh. 2024, 7, 190–204. [Google Scholar] [CrossRef]
- Japs, S.; Anacker, H.; Dumitrescu, R. SAVE: Security & safety by model-based systems engineering on the example of automotive industry. Procedia CIRP 2021, 100, 187–192. [Google Scholar] [CrossRef]
- Mažeika, D.; Butleris, R. MBSEsec: Model-Based Systems Engineering Method for Creating Secure Systems. Appl. Sci. 2020, 10, 2574. [Google Scholar] [CrossRef]
- Mažeika, D.; Butleris, R. Integrating Security Requirements Engineering into MBSE: Profile and Guidelines. Secur. Commun. Netw. 2020, 2020, 5137625. [Google Scholar] [CrossRef]
- PiąTek, P.; Mydłowski, P.; Buczacki, A.; Moskwa, S. Concept of Using the MBSE Approach to Integrate Security Patterns in Safety-Related Projects for the Automotive Industry. IEEE Trans. Intell. Transport. Syst. 2024, 25, 15477–15492. [Google Scholar] [CrossRef]
- Lee, W.-H.; Chiu, C.-Y. Design and Implementation of a Smart Traffic Signal Control System for Smart City Applications. Sensors 2020, 20, 508. [Google Scholar] [CrossRef] [PubMed]
- Lorkowski, S.; Kannenberg, O.; Kesting, A.; Witte, N. UR:BAN—Vernetztes Verkehrssystem: Forschungsprojekt: Schlussbericht zu den Teilprojekten: VV—Vernetztes Verkehrssystem: Laufzeit: 01.01.2012-31.12.2015. Available online: https://www.tib.eu/de/suchen/id/TIBKAT%3A870099108/UR-BAN-Vernetztes-Verkehrssystem-Forschungsprojekt (accessed on 8 April 2025).
- Gath, N.; Kaths, J.; Kürschner, M.; Schendzielorz, T.; Krause, J.; Schön, T.; Noll, B.; Mosebach, H.; Petry, F.; Ungureanu, T.; et al. Leitfaden für die Einrichtung Kooperativer Systeme auf Öffentlicher Seite. Available online: https://www.mos.ed.tum.de/vt/forschung/projekte/abgeschlossene-projekte/urban-abgeschlossen-2016/urban-leitfaden/ (accessed on 8 April 2025).
- J2735_202007; V2X Communications Message Set Dictionary. SAE International: Warrendale, PA, USA, 2020.
- Morkevičius, A.; Aleksandravičienė, A. MagicGrid® Book of Knowledge; Dassault Systèmes: Waltham, MA, USA, 2021. [Google Scholar]
- Biggs, G.; Post, K.; Armonas, A.; Yakymets, N.; Juknevicius, T.; Berres, A. OMG standard for integrating safety and reliability analysis into MBSE: Concepts and applications. INCOSE Int. Symp. 2019, 29, 159–173. [Google Scholar] [CrossRef]
- International Electrotechnical Commission. Analysis Techniques for System Reliability: Procedure for Failure Mode and Effects Analysis (FMEA), 2nd ed.; Prepared by IEC Technical Committee 56, Dependability; International Electrotechnical Commission: Geneva, Switzerland, 2006; ISBN 283188425X. [Google Scholar]
- IEC 62304:2006(en); Medical Device Software—Software Life Cycle Processes. International Standards Organization: Geneva, Switzerland, 2006.
- ISO 14971:2019; Medical Devices—Application of Risk Management to Medical Devices. International Standards Organization: Geneva, Switzerland, 2019.



| Publication | Source | Intersection | MBSE | Safety | Security | Requirements Engineering | Autonomous Mobilty | Additional Analytical Methods (e.g., FMEA) | Normative Basis |
|---|---|---|---|---|---|---|---|---|---|
| Nolte et al. | [19] | - | + | + | + | + | + | - | + |
| Wuthishuwong et al. | [27] | + | - | + | - | - | + | - | - |
| Wang et al. | [28] | + | + | + | - | + | + | + | - |
| Japs et al. | [29] | - | + | + | + | + | + | - | + |
| Mažeika & Butleris (2020a) | [30] | - | + | + | + | + | - | - | - |
| Mažeika & Butleris (2020b) | [31] | - | + | - | + | + | - | - | + |
| Piątek et al. | [32] | - | + | + | + | + | - | - | + |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Published by MDPI on behalf of the International Institute of Knowledge Innovation and Invention. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kizgin, U.V.; Stein, A.; Esapathi, J.; Vietor, T. Systematic Method for Identifying Safety and Security Requirements in Autonomous Driving: Case Study of Autonomous Intersection System. Appl. Syst. Innov. 2025, 8, 168. https://doi.org/10.3390/asi8060168
Kizgin UV, Stein A, Esapathi J, Vietor T. Systematic Method for Identifying Safety and Security Requirements in Autonomous Driving: Case Study of Autonomous Intersection System. Applied System Innovation. 2025; 8(6):168. https://doi.org/10.3390/asi8060168
Chicago/Turabian StyleKizgin, Umut Volkan, Armin Stein, Johanna Esapathi, and Thomas Vietor. 2025. "Systematic Method for Identifying Safety and Security Requirements in Autonomous Driving: Case Study of Autonomous Intersection System" Applied System Innovation 8, no. 6: 168. https://doi.org/10.3390/asi8060168
APA StyleKizgin, U. V., Stein, A., Esapathi, J., & Vietor, T. (2025). Systematic Method for Identifying Safety and Security Requirements in Autonomous Driving: Case Study of Autonomous Intersection System. Applied System Innovation, 8(6), 168. https://doi.org/10.3390/asi8060168







