A Survey on UxV Swarms and the Role of Artificial Intelligence as a Technological Enabler
Abstract
1. Introduction
1.1. Our Contribution
- Present a thorough overview of the existing literature, i.e., reviews, surveys, etc., in the domain of swarm technologies and identify research gaps.
- Enhance understanding on how AI can be integrated in different swarm operations, e.g., path planning, formation control, etc.
- Investigate how AI can improve the swarm’s networking, e.g., adaptive communication protocols, channel selection, etc.
- Enhance the security posture of the swarm with anomaly detection, self-recovery, and self-adaptability to external and internal factors.
- Analyze trends in vehicle selection to highlight dominant platforms and neglected domains.
- Discuss our findings and elaborate on future areas of research.
1.2. Methodology
- MDPI;
- IEEE Xplore Digital Library;
- SpringerLink;
- ScienceDirect;
- Scopus;
- Google Scholar.
- Focused on UxV swarms (UAV, UGV, USV, UUV, or mixed swarms);
- Applied AI-, ML-, or data-driven methods to swarm intelligence, communication, or security;
- Were published in English and peer-reviewed (journal or conference).
- Non-peer-reviewed works such as patents, theses, and white papers;
- Duplicate records across databases.
2. Previous Review and Survey Works
- AI in Swarm Intelligence: Applications of AI to swarm coordination, path planning, resource allocation, target tracking, formation control, and other collective swarm behaviors.
- AI-Based Adaptive Communications: Use of AI to enable dynamic and adaptive communication systems, including adaptive routing protocols, frequency allocation, channel selection, topology control, and quality-of-service (QoS) optimization.
- AI-Driven Security Mechanisms: Techniques leveraging AI to enhance the security and resilience of the swarm and individual agents, including anomaly detection, intrusion detection, self-healing, fault tolerance, and automated incident response.
- ✓: Indicates that the survey offers a comprehensive analysis of the subject, supported by examples and in-depth discussion.
- ✗: Indicates that the survey does not address the subject at all.
- Partially: Indicates that the survey mentions the subject briefly or superficially, without detailed discussion or illustrative examples.
2.1. AI in Swarm Intelligence
2.2. AI-Based Adaptive Communications
2.3. AI-Driven Security Mechanisms
2.4. Comparative Analysis
3. AI in Swarm Intelligence
- Path Planning and Navigation: These involve how both individual UxVs and the whole swarm plan their routes within the operating environment.
- Obstacle and Collision Avoidance: This concerns how UxVs and the swarm avoid environmental obstacles and internal collisions.
- Formation Control: This describes how UxVs form and maintain formations, as well as how they adapt these formations dynamically.
- Target Search: This includes detecting targets, pursuing them efficiently, and ultimately reaching them.
- Mission Planning: This addresses how the swarm can operate more effectively given specific goals and environmental conditions.
- Task Optimization: This focuses on how the swarm efficiently performs assigned tasks and allocates them to individual UxVs.
- Resource Optimization: This primarily relates to energy efficiency and how the swarm can complete tasks without depleting its resources.
- Approaches Relying on Reinforcement Learning: This chapter mostly includes academic papers which rely on RL and algorithms from the RL family to perform the swarm operations.
- Supervised, Federated, and Probabilistic Models: In this section, we deal with pieces of work which rely on supervised NNs, FL, or probabilistic approaches.
- Hybrid, Bio-Inspired, and Other Methods: Finally, this category includes research that relies on bio-inspired algorithms, e.g., ACO, PPO, etc., and approaches that do not belong in any of the previous categories.
3.1. Approaches Relying on Reinforcement Learning
3.2. Supervised, Federated, and Probabilistic Models
3.3. Hybrid, Bio-Inspired, and Other Methods
3.4. Conclusion
4. AI-Based Adaptive Communications
- Network Architecture and Topologies: These address how nodes (UAVs, relays, base stations) are physically or logically arranged, and how coverage and connectivity are maintained—particularly in dynamic, multi-node environments.
- Channel and Propagation Modeling: This involves how signals behave during transmission, as well as methods to model, predict, measure, or enhance signal behavior.
- Signal Quality: This refers to signal processing techniques that improve signal fidelity, energy efficiency, or robustness.
- Routing and Protocols: These describe how data paths are selected and how nodes communicate using predefined or adaptive rules.
- Network Management and Optimization: These encompass system-level strategies for dynamically allocating resources, maintaining service quality, and optimizing overall network performance.
- Approaches Relying on Reinforcement Learning: This chapter mostly includes academic papers which rely on RL and algorithms from the RL family to perform the swarm operations.
- Supervised, Federated, and Probabilistic Learning Models: In this section, we deal with pieces of work which rely on supervised NNs, FL, or probabilistic approaches.
- Hybrid, Bio-Inspired, and Other Methods: Finally, this category includes research that relies on bio-inspired algorithms, e.g., ACO, PPO, etc., and approaches that do not belong in any of the previous categories.
4.1. Approaches Relying on Reinforcement Learning
4.2. Supervised, Federated, and Probabilistic Models
4.3. Hybrid, Bio-Inspired, and Other Methods
4.4. Conclusions
5. AI-Driven Security Mechanisms
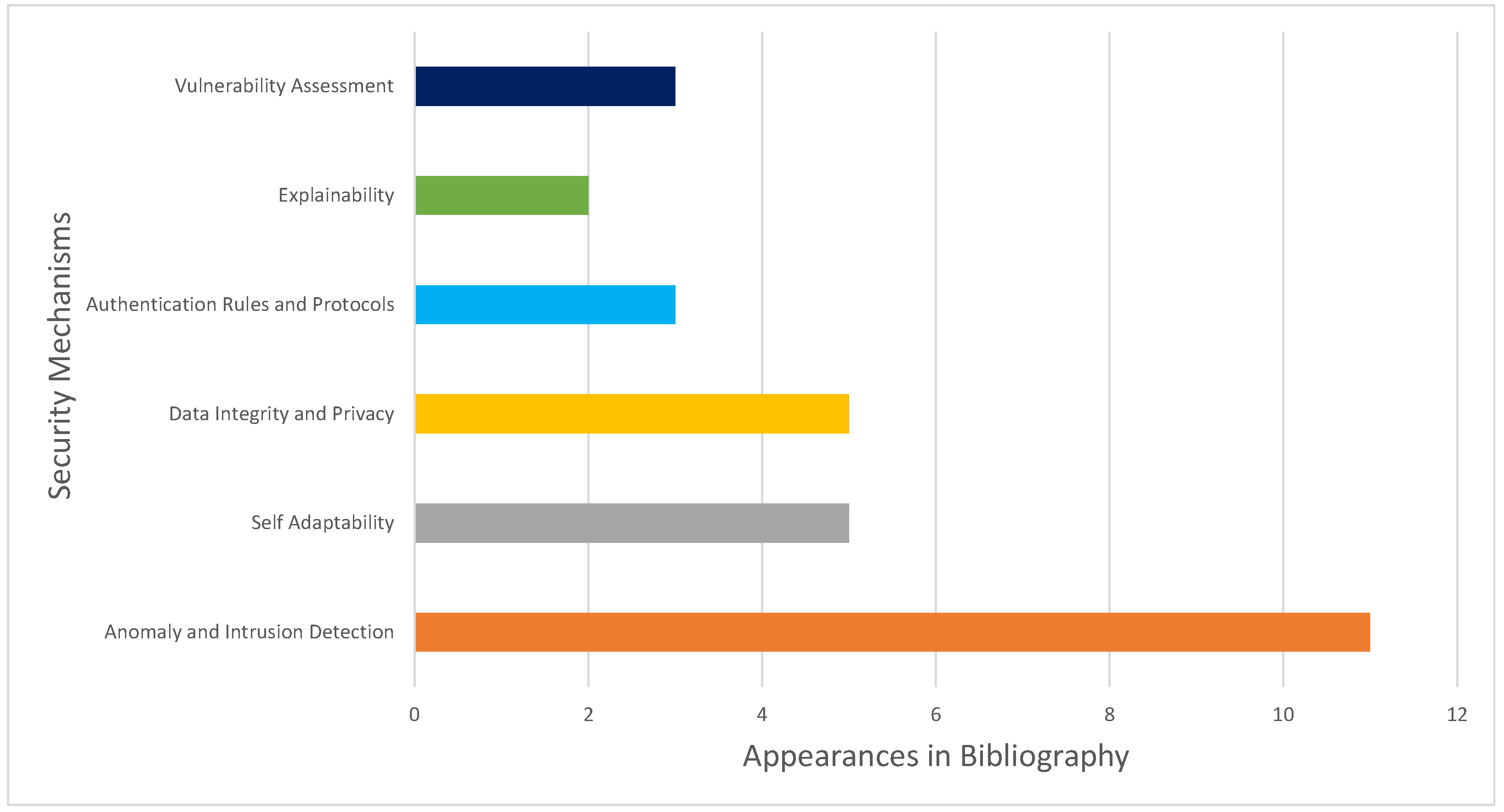
- Anomaly and Intrusion Detection: Refer to the ability to identify abnormal behavior.
- Data Integrity and Privacy: These involve techniques to ensure that data are kept, transmitted, and processed in a secure manner.
- Self Adaptability: This refers to the swarm’s ability to effectively respond to threats, faulty behavior, and generally dynamic internal and external changes.
- Authentication Rules and Protocols: These include rules and protocols that ensure that individual vehicles of the swarm are always authenticated.
- Explainability: AI, especially in security, should include methods to log decisions and provide an explanation.
- Supervised, Federated, and Probabilistic Learning Models: In this section, we deal with pieces of work which rely more on supervised NNs, FL, or probabilistic approaches.
- Unsupervised, Hybrid, and Other Approaches: Finally, this category includes the rest of the literature we found on the security aspects of the swarm.
5.1. Supervised, Federated, and Probabilistic Models
5.2. Unsupervised, Hybrid, and Other Methods
5.3. Conclusions
6. Discussion
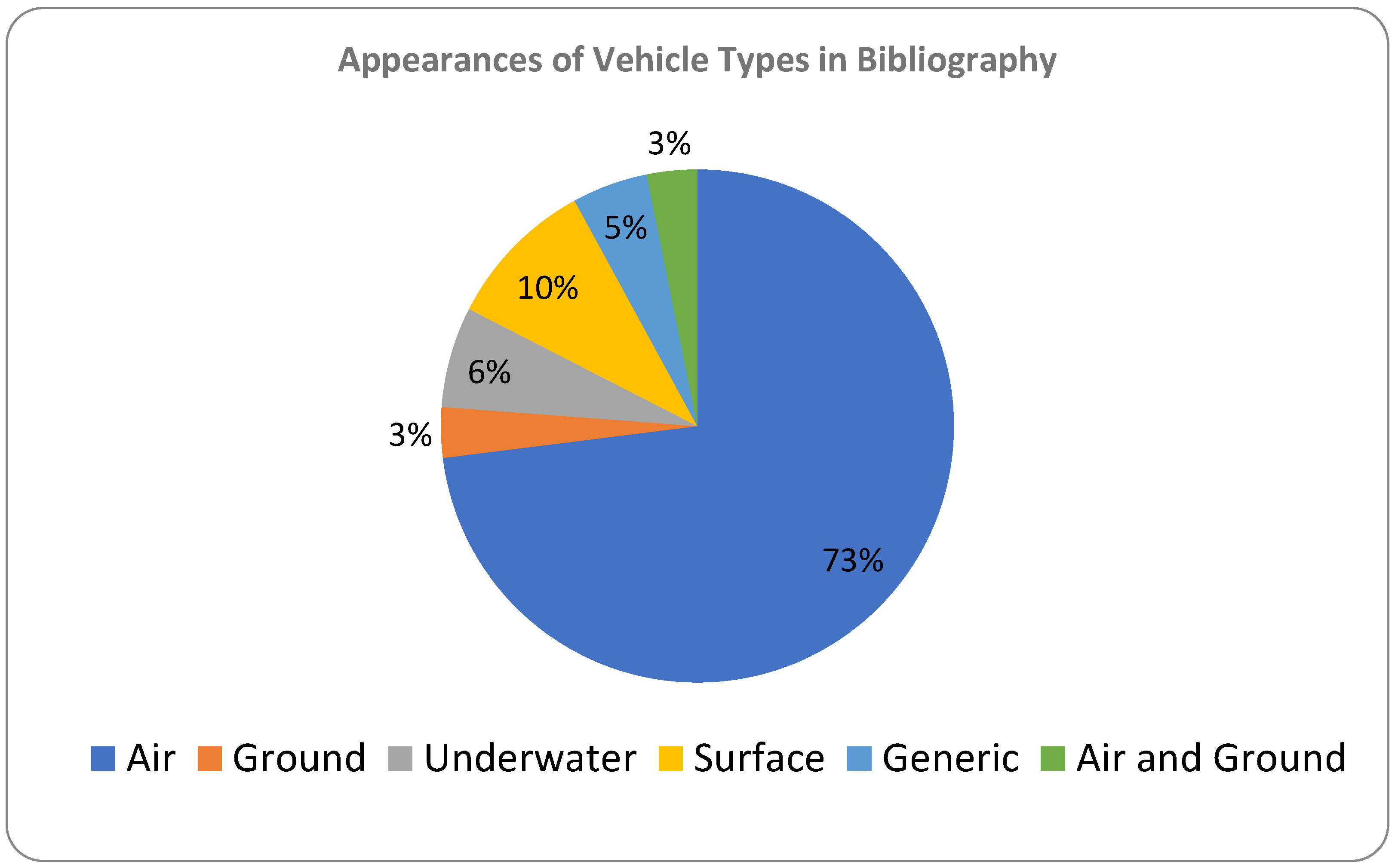
- Type of vehicle;
- Swarm aspects;
- Type of AI.
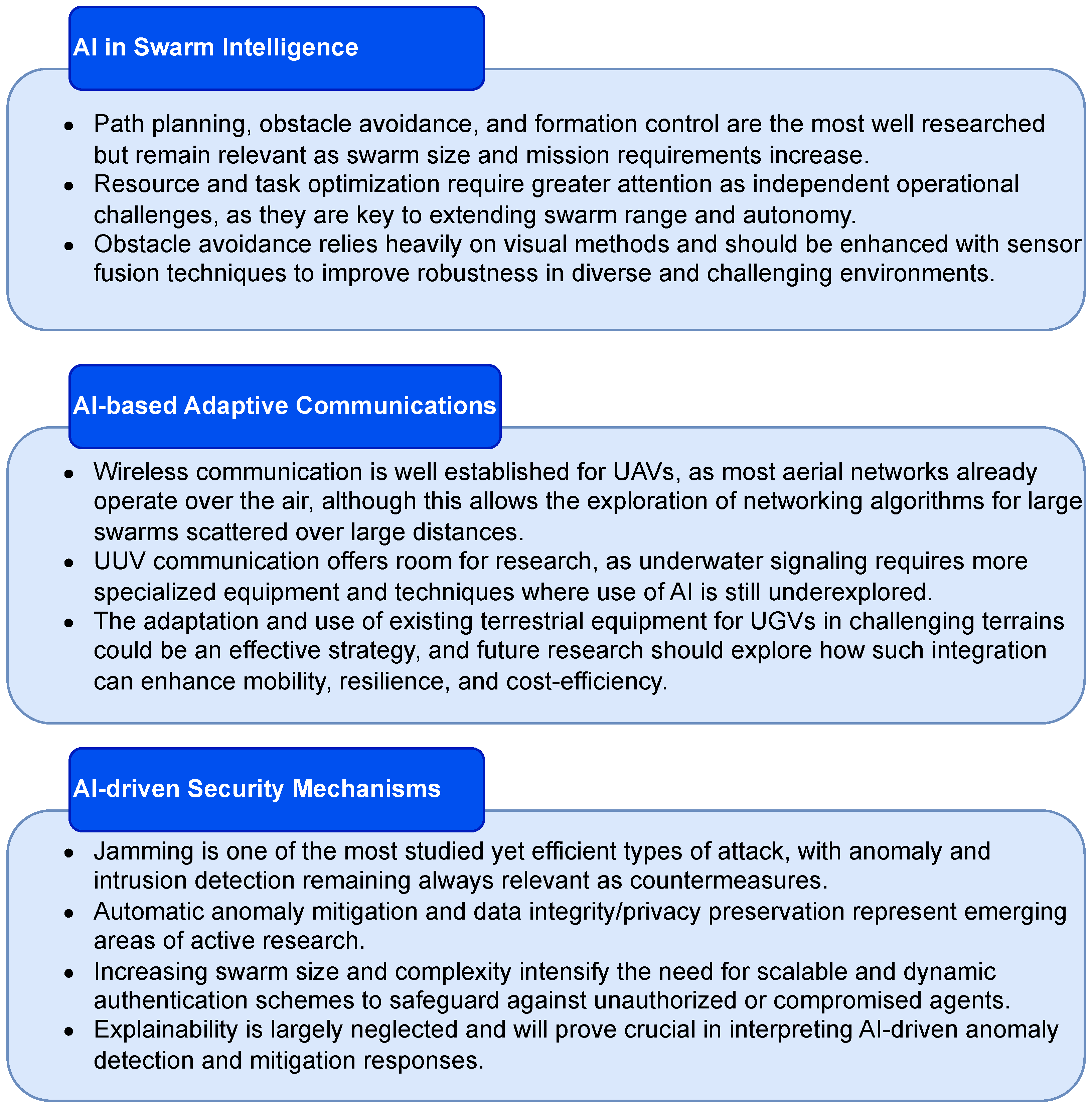
- Expansion beyond UAVs to ground and underwater swarms or combinations of different vehicles in the same swarm.
- Facing task and resource optimization as standalone swarm functions.
- Development of communication techniques and coverage expansion to environments with limited coverage by terrestrial means.
- Adoption of proactive and AI-driven security strategies with a focus on explainability.
- Integration of LLMs into swarm decision-making.
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| ACO | Ant Colony Optimization |
| ADS-B | Automatic Dependent Surveillance–Broadcast |
| AI | Artificial Intelligence |
| CNNs | Convolutional Neural Networks |
| COTS | Commercial-Off-The-Shelf |
| DDPG | Deep Deterministic Policy Gradient |
| DDQL | Double Deep Q-Learning |
| DL | Deep Learning |
| DOAJ | Directory of Open Access Journals |
| DQN | Deep Q-Networks |
| DRL | Deep Reinforcement Learning |
| FANETs | Flying Ad Hoc Networks |
| FL | Federated Learning |
| GAI | Generative Artificial Intelligence |
| GAN | Generative Adversarial Network |
| IoD | Internet of Drones |
| IoT | Internet of Things |
| KNN | K-Nearest Neighbors |
| LLMs | Large Language Models |
| MARL | Multi-Agent RL |
| MDPI | Multidisciplinary Digital Publishing Institute |
| ML | Machine Learning |
| MIMO | Multiple-Input and Multiple-Output |
| NNs | Neural Networks |
| NOMA | Non-Orthogonal Multiple Access |
| NTN | Non-Terrestrial Network |
| PDR | Packet Delivery Ratio |
| PPO | Proximal Policy Optimization |
| PRISMA | Preferred Reporting Items for Systematic Reviews and Meta-Analyses |
| PSO | Particle Swarm Optimization |
| QoS | Quality of Service |
| RL | Reinforcement Learning |
| RNNs | Recurrent Neural Networks |
| SDN | Software-Defined Networking |
| SHAP | SHapley Additive exPlanations |
| SI | Swarm Intelligence |
| SINR | Signal-to-Interference-Plus-Noise Ratio |
| SotA | State of the Art |
| UAVs | Uncrewed Aerial Vehicles |
| UGVs | Uncrewed Ground Vehicles |
| USVs | Uncrewed Surface Vehicles |
| UUVs | Uncrewed Underwater Vehicles |
| UxV | Uncrewed Vehicle |
| VLC | Visible Light Communication |
References
- Zaytsev, V. Unmanned Aerial Vehicles in Ukraine: Modernity, Challenges, and Development Prospects. In Intelligent Transport Systems: Ecology, Safety, Quality, Comfort; Slavinska, O., Danchuk, V., Kunytska, O., Hulchak, O., Eds.; Lecture Notes in Networks and Systems; Springer Nature Switzerland: Cham, Switzerland, 2025; Volume 1335, pp. 296–307. [Google Scholar] [CrossRef]
- Alzahrani, B.; Oubbati, O.S.; Barnawi, A.; Atiquzzaman, M.; Alghazzawi, D. UAV assistance paradigm: State-of-the-art in applications and challenges. J. Netw. Comput. Appl. 2020, 166, 102706. [Google Scholar] [CrossRef]
- Kumar, A.; Ahuja, N.J.; Thapliyal, M.; Dutt, S.; Kumar, T.; De Jesus Pacheco, D.A.; Konstantinou, C.; Raymond Choo, K.K. Blockchain for unmanned underwater drones: Research issues, challenges, trends and future directions. J. Netw. Comput. Appl. 2023, 215, 103649. [Google Scholar] [CrossRef]
- Chaurasia, R.; Mohindru, V. Unmanned Aerial Vehicle (UAV): A Comprehensive Survey. In Unmanned Aerial Vehicles for Internet of Things (IoT), 1st ed.; Mohindru, V., Singh, Y., Bhatt, R., Gupta, A.K., Eds.; Wiley: Hoboken, NJ, USA, 2021; pp. 1–27. [Google Scholar] [CrossRef]
- Tsouros, D.C.; Bibi, S.; Sarigiannidis, P.G. A Review on UAV-Based Applications for Precision Agriculture. Information 2019, 10, 349. [Google Scholar] [CrossRef]
- Mohsan, S.A.H.; Khan, M.A.; Noor, F.; Ullah, I.; Alsharif, M.H. Towards the Unmanned Aerial Vehicles (UAVs): A Comprehensive Review. Drones 2022, 6, 147. [Google Scholar] [CrossRef]
- Munasinghe, I.; Perera, A.; Deo, R.C. A Comprehensive Review of UAV-UGV Collaboration: Advancements and Challenges. J. Sens. Actuator Netw. 2024, 13, 81. [Google Scholar] [CrossRef]
- Mueller, M.; Smith, N.; Ghanem, B. A Benchmark and Simulator for UAV Tracking. In Computer Vision–ECCV 2016, Amsterdam, The Netherlands, 11–14 October 2016; Leibe, B., Matas, J., Sebe, N., Welling, M., Eds.; Springer International Publishing: Cham, Switzerland, 2016; Volume 9905, pp. 445–461. [Google Scholar] [CrossRef]
- Tijjani, A.S.; Chemori, A.; Creuze, V. A survey on tracking control of unmanned underwater vehicles: Experiments-based approach. Annu. Rev. Control 2022, 54, 125–147. [Google Scholar] [CrossRef]
- Wibisono, A.; Piran, M.J.; Song, H.K.; Lee, B.M. A Survey on Unmanned Underwater Vehicles: Challenges, Enabling Technologies, and Future Research Directions. Sensors 2023, 23, 7321. [Google Scholar] [CrossRef]
- Li, J.; Zhang, G.; Jiang, C.; Zhang, W. A survey of maritime unmanned search system: Theory, applications and future directions. Ocean Eng. 2023, 285, 115359. [Google Scholar] [CrossRef]
- Bae, I.; Hong, J. Survey on the Developments of Unmanned Marine Vehicles: Intelligence and Cooperation. Sensors 2023, 23, 4643. [Google Scholar] [CrossRef]
- Farella, A.; Paciolla, F.; Quartarella, T.; Pascuzzi, S. Agricultural Unmanned Ground Vehicle (UGV): A Brief Overview. In Farm Machinery and Processes Management in Sustainable Agriculture; Lorencowicz, E., Huyghebaert, B., Uziak, J., Eds.; Springer Nature Switzerland: Cham, Switzerland, 2024; Volume 609, pp. 137–146. [Google Scholar] [CrossRef]
- Ni, J.; Hu, J.; Xiang, C. A review for design and dynamics control of unmanned ground vehicle. Proc. Inst. Mech. Eng. Part D J. Automob. Eng. 2021, 235, 1084–1100. [Google Scholar] [CrossRef]
- Ersü, C.; Petlenkov, E.; Janson, K. A Systematic Review of Cutting-Edge Radar Technologies: Applications for Unmanned Ground Vehicles (UGVs). Sensors 2024, 24, 7807. [Google Scholar] [CrossRef] [PubMed]
- Baras, N.; Dasygenis, M. UGV Coverage Path Planning: An Energy-Efficient Approach through Turn Reduction. Electronics 2023, 12, 2959. [Google Scholar] [CrossRef]
- Miki, T.; Khrapchenkov, P.; Hori, K. UAV/UGV Autonomous Cooperation: UAV assists UGV to climb a cliff by attaching a tether. In Proceedings of the 2019 International Conference on Robotics and Automation (ICRA), Montreal, QC, Canada, 20–24 May 2019; pp. 8041–8047. [Google Scholar] [CrossRef]
- Gabrlik, P.; Lazna, T.; Jilek, T.; Sladek, P.; Zalud, L. An automated heterogeneous robotic system for radiation surveys: Design and field testing. J. Field Robot. 2021, 38, 657–683. [Google Scholar] [CrossRef]
- Asadi, K.; Kalkunte Suresh, A.; Ender, A.; Gotad, S.; Maniyar, S.; Anand, S.; Noghabaei, M.; Han, K.; Lobaton, E.; Wu, T. An integrated UGV-UAV system for construction site data collection. Autom. Constr. 2020, 112, 103068. [Google Scholar] [CrossRef]
- Stöcker, C.; Bennett, R.; Nex, F.; Gerke, M.; Zevenbergen, J. Review of the Current State of UAV Regulations. Remote Sens. 2017, 9, 459. [Google Scholar] [CrossRef]
- Henderson, I.L. Aviation safety regulations for unmanned aircraft operations: Perspectives from users. Transp. Policy 2022, 125, 192–206. [Google Scholar] [CrossRef]
- Zwickle, A.; Farber, H.B.; Hamm, J.A. Comparing public concern and support for drone regulation to the current legal framework. Behav. Sci. Law 2019, 37, 109–124. [Google Scholar] [CrossRef] [PubMed]
- Glossner, J.; Murphy, S.; Iancu, D. An Overview of the Drone Open-Source Ecosystem. arXiv 2021. [Google Scholar] [CrossRef]
- Sai, S.; Garg, A.; Jhawar, K.; Chamola, V.; Sikdar, B. A Comprehensive Survey on Artificial Intelligence for Unmanned Aerial Vehicles. IEEE Open J. Veh. Technol. 2023, 4, 713–738. [Google Scholar] [CrossRef]
- Arafat, M.Y.; Alam, M.M.; Moh, S. Vision-Based Navigation Techniques for Unmanned Aerial Vehicles: Review and Challenges. Drones 2023, 7, 89. [Google Scholar] [CrossRef]
- Chen, X.; Tang, J.; Lao, S. Review of Unmanned Aerial Vehicle Swarm Communication Architectures and Routing Protocols. Appl. Sci. 2020, 10, 3661. [Google Scholar] [CrossRef]
- Chen, W.; Liu, J.; Guo, H.; Kato, N. Toward Robust and Intelligent Drone Swarm: Challenges and Future Directions. IEEE Netw. 2020, 34, 278–283. [Google Scholar] [CrossRef]
- Sarkar, N.I.; Gul, S. Artificial Intelligence-Based Autonomous UAV Networks: A Survey. Drones 2023, 7, 322. [Google Scholar] [CrossRef]
- Puente-Castro, A.; Rivero, D.; Pazos, A.; Fernandez-Blanco, E. A review of artificial intelligence applied to path planning in UAV swarms. Neural Comput. Appl. 2022, 34, 153–170. [Google Scholar] [CrossRef]
- Abdelkader, M.; Güler, S.; Jaleel, H.; Shamma, J.S. Aerial Swarms: Recent Applications and Challenges. Curr. Robot. Rep. 2021, 2, 309–320. [Google Scholar] [CrossRef]
- Tahir, A.; Böling, J.; Haghbayan, M.H.; Toivonen, H.T.; Plosila, J. Swarms of Unmanned Aerial Vehicles—A Survey. J. Ind. Inf. Integr. 2019, 16, 100106. [Google Scholar] [CrossRef]
- Li, Z.; Min, G.; Ren, P.; Luo, C.; Zhao, L.; Luo, C. Ubiquitous and Robust UxV Networks: Overviews, Solutions, Challenges, and Opportunities. IEEE Netw. 2024, 38, 26–34. [Google Scholar] [CrossRef]
- Schranz, M.; Umlauft, M.; Sende, M.; Elmenreich, W. Swarm Robotic Behaviors and Current Applications. Front. Robot. AI 2020, 7, 36. [Google Scholar] [CrossRef] [PubMed]
- Alqudsi, Y.; Makaraci, M. UAV swarms: Research, challenges, and future directions. J. Eng. Appl. Sci. 2025, 72, 12. [Google Scholar] [CrossRef]
- Zaitseva, E.; Levashenko, V.; Mukhamediev, R.; Brinzei, N.; Kovalenko, A.; Symagulov, A. Review of Reliability Assessment Methods of Drone Swarm (Fleet) and a New Importance Evaluation Based Method of Drone Swarm Structure Analysis. Mathematics 2023, 11, 2551. [Google Scholar] [CrossRef]
- Asaamoning, G.; Mendes, P.; Rosário, D.; Cerqueira, E. Drone Swarms as Networked Control Systems by Integration of Networking and Computing. Sensors 2021, 21, 2642. [Google Scholar] [CrossRef] [PubMed]
- Chung, S.J.; Paranjape, A.A.; Dames, P.; Shen, S.; Kumar, V. A Survey on Aerial Swarm Robotics. IEEE Trans. Robot. 2018, 34, 837–855. [Google Scholar] [CrossRef]
- Connor, J.; Champion, B.; Joordens, M.A. Current Algorithms, Communication Methods and Designs for Underwater Swarm Robotics: A Review. IEEE Sens. J. 2021, 21, 153–169. [Google Scholar] [CrossRef]
- Wu, G.; Xu, T.; Sun, Y.; Zhang, J. Review of multiple unmanned surface vessels collaborative search and hunting based on swarm intelligence. Int. J. Adv. Robot. Syst. 2022, 19, 17298806221091885. [Google Scholar] [CrossRef]
- Vedachalam, N.; Ramesh, R.; Jyothi, V.B.N.; Doss Prakash, V.; Ramadass, G.A. Autonomous underwater vehicles–challenging developments and technological maturity towards strategic swarm robotics systems. Mar. Georesources Geotechnol. 2019, 37, 525–538. [Google Scholar] [CrossRef]
- Liu, G.; Chen, L.; Liu, K.; Luo, Y. A swarm of unmanned vehicles in the shallow ocean: A survey. Neurocomputing 2023, 531, 74–86. [Google Scholar] [CrossRef]
- Boccadoro, P.; Striccoli, D.; Grieco, L.A. An extensive survey on the Internet of Drones. Ad Hoc Netw. 2021, 122, 102600. [Google Scholar] [CrossRef]
- Michailidis, E.T.; Maliatsos, K.; Skoutas, D.N.; Vouyioukas, D.; Skianis, C. Secure UAV-Aided Mobile Edge Computing for IoT: A Review. IEEE Access 2022, 10, 86353–86383. [Google Scholar] [CrossRef]
- Zhou, Y.; Rao, B.; Wang, W. UAV Swarm Intelligence: Recent Advances and Future Trends. IEEE Access 2020, 8, 183856–183878. [Google Scholar] [CrossRef]
- Javed, S.; Hassan, A.; Ahmad, R.; Ahmed, W.; Ahmed, R.; Saadat, A.; Guizani, M. State-of-the-Art and Future Research Challenges in UAV Swarms. IEEE Internet Things J. 2024, 11, 19023–19045. [Google Scholar] [CrossRef]
- Liu, G.; Van Huynh, N.; Du, H.; Hoang, D.T.; Niyato, D.; Zhu, K.; Kang, J.; Xiong, Z.; Jamalipour, A.; Kim, D.I. Generative AI for Unmanned Vehicle Swarms: Challenges, Applications and Opportunities. arXiv 2024. [Google Scholar] [CrossRef]
- Azoulay, R.; Haddad, Y.; Reches, S. Machine Learning Methods for UAV Flocks Management—A Survey. IEEE Access 2021, 9, 139146–139175. [Google Scholar] [CrossRef]
- Pandey, D.; Kushwaha, V. An exploratory study of congestion control techniques in Wireless Sensor Networks. Comput. Commun. 2020, 157, 257–283. [Google Scholar] [CrossRef]
- Ding, Y.; Yang, Z.; Pham, Q.V.; Hu, Y.; Zhang, Z.; Shikh-Bahaei, M. Distributed Machine Learning for UAV Swarms: Computing, Sensing, and Semantics. IEEE Internet Things J. 2024, 11, 7447–7473. [Google Scholar] [CrossRef]
- Cai, W.; Liu, Z.; Zhang, M.; Wang, C. Cooperative Artificial Intelligence for underwater robotic swarm. Robot. Auton. Syst. 2023, 164, 104410. [Google Scholar] [CrossRef]
- Xiao, J.; Pisutsin, P.; Feroskhan, M. Collaborative Target Search With a Visual Drone Swarm: An Adaptive Curriculum Embedded Multistage Reinforcement Learning Approach. IEEE Trans. Neural Netw. Learn. Syst. 2025, 36, 313–327. [Google Scholar] [CrossRef] [PubMed]
- Perrusquía, A.; Guo, W. Uncovering Reward Goals in Distributed Drone Swarms Using Physics-Informed Multiagent Inverse Reinforcement Learning. IEEE Trans. Cybern. 2025, 55, 14–23. [Google Scholar] [CrossRef]
- Nguyen, H.T.; Nguyen, T.D.; Garratt, M.; Kasmarik, K.; Anavatti, S.; Barlow, M.; Abbass, H.A. A Deep Hierarchical Reinforcement Learner for Aerial Shepherding of Ground Swarms. In Neural Information Processing; Gedeon, T., Wong, K.W., Lee, M., Eds.; Springer International Publishing: Cham, Switzerland, 2019; Volume 11953, pp. 658–669. [Google Scholar] [CrossRef]
- Zhang, J.; Yu, Z.; Mao, S.; Periaswamy, S.C.G.; Patton, J.; Xia, X. IADRL: Imitation Augmented Deep Reinforcement Learning Enabled UGV-UAV Coalition for Tasking in Complex Environments. IEEE Access 2020, 8, 102335–102347. [Google Scholar] [CrossRef]
- Venturini, F.; Mason, F.; Pase, F.; Chiariotti, F.; Testolin, A.; Zanella, A.; Zorzi, M. Distributed Reinforcement Learning for Flexible and Efficient UAV Swarm Control. IEEE Trans. Cogn. Commun. Netw. 2021, 7, 955–969. [Google Scholar] [CrossRef]
- Qamar, S.; Khan, S.H.; Arshad, M.A.; Qamar, M.; Gwak, J.; Khan, A. Autonomous Drone Swarm Navigation and Multitarget Tracking With Island Policy-Based Optimization Framework. IEEE Access 2022, 10, 91073–91091. [Google Scholar] [CrossRef]
- Gan, W.; Qu, X.; Song, D.; Yao, P. Multi-USV Cooperative Chasing Strategy Based on Obstacles Assistance and Deep Reinforcement Learning. IEEE Trans. Autom. Sci. Eng. 2024, 21, 5895–5910. [Google Scholar] [CrossRef]
- Cao, Y.; Fang, X. Optimized-Weighted-Speedy Q-Learning Algorithm for Multi-UGV in Static Environment Path Planning under Anti-Collision Cooperation Mechanism. Mathematics 2023, 11, 2476. [Google Scholar] [CrossRef]
- Wang, S.; Lin, C.; Han, G.; Zhu, S.; Li, Z.; Wang, Z.; Ma, Y. Multi-AUV Cooperative Underwater Multi-Target Tracking Based on Dynamic-Switching-Enabled Multi-Agent Reinforcement Learning. IEEE Trans. Mob. Comput. 2025, 24, 4296–4311. [Google Scholar] [CrossRef]
- Yuwen, C.; Wen, G.; Zhou, J.; Luan, M.; Huang, T. Distributed Nash Equilibrium Seeking in Coalition Games for Uncertain Euler-Lagrange Systems With Application to USV Swarm Confrontation. arXiv 2025. [Google Scholar] [CrossRef]
- Qin, D.; Dong, H.; Sun, S.; Wen, Z.; Li, J.; Li, T. Model-Driven Cooperative Path Planning for Dynamic Target Searching of Unmanned Unterwater Vehicle Formation. J. Mar. Sci. Eng. 2024, 12, 2094. [Google Scholar] [CrossRef]
- Praczyk, T. Neural control system for a swarm of autonomous underwater vehicles. Knowl.-Based Syst. 2023, 276, 110783. [Google Scholar] [CrossRef]
- Raj, A.; Ahuja, K.; Busnel, Y. AI Algorithm for Predicting and Optimizing Trajectory of UAV Swarm. arXiv 2024. [Google Scholar] [CrossRef]
- Cabuk, U.C.; Tosun, M.; Dagdeviren, O.; Ozturk, Y. Modeling Energy Consumption of Small Drones for Swarm Missions. IEEE Trans. Intell. Transp. Syst. 2024, 25, 10176–10189. [Google Scholar] [CrossRef]
- Kusyk, J.; Uyar, M.U.; Ma, K.; Wu, J.J.; Ruan, W.; Guha, D.K.; Bertoli, G.; Boksiner, J. AI Based Flight Control for Autonomous UAV Swarms. In Proceedings of the 2018 International Conference on Computational Science and Computational Intelligence (CSCI), Las Vegas, NV, USA, 12–14 December 2018; pp. 1155–1160. [Google Scholar] [CrossRef]
- Zeng, T.; Semiari, O.; Mozaffari, M.; Chen, M.; Saad, W.; Bennis, M. Federated Learning in the Sky: Joint Power Allocation and Scheduling with UAV Swarms. In Proceedings of the ICC 2020-2020 IEEE International Conference on Communications (ICC), Dublin, Ireland, 7–11 June 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Trihinas, D.; Agathocleous, M.; Avogian, K.; Katakis, I. FlockAI: A Testing Suite for ML-Driven Drone Applications. Future Internet 2021, 13, 317. [Google Scholar] [CrossRef]
- Saeed, R.A.; Omri, M.; Abdel-Khalek, S.; Ali, E.S.; Alotaibi, M.F. Optimal path planning for drones based on swarm intelligence algorithm. Neural Comput. Appl. 2022, 34, 10133–10155. [Google Scholar] [CrossRef]
- Gal, O. Adaptive USVs Swarm Optimization for Target Tracking in Dynamic Environments. arXiv 2024. [Google Scholar] [CrossRef]
- Sundelius, N.; Funk, P.; Sohlberg, R. Simulation Environment Evaluating AI Algorithms for Search Missions Using Drone Swarms. In International Congress and Workshop on Industrial AI and eMaintenance 2023; Kumar, U., Karim, R., Galar, D., Kour, R., Eds.; Springer Nature Switzerland: Cham, Switzerland, 2024; pp. 191–204. [Google Scholar] [CrossRef]
- Zeng, Q.; Nait-Abdesselam, F. Multi-Agent Reinforcement Learning-Based Extended Boid Modeling for Drone Swarms. In Proceedings of the ICC 2024-IEEE International Conference on Communications, Denver, CO, USA, 9–13 June 2024; pp. 1551–1556. [Google Scholar] [CrossRef]
- Awasthi, S.; Balusamy, B.; Porkodi, V. Artificial Intelligence Supervised Swarm UAVs for Reconnaissance. In Data Science and Analytics; Batra, U., Roy, N.R., Panda, B., Eds.; Springer Singapore: Singapore, 2020; Volume 1229, pp. 375–388. [Google Scholar] [CrossRef]
- Zhu, T.; Xiao, Y.; Zhang, H. Maritime patrol tasks assignment optimization of multiple USVs under endurance constraint. Ocean Eng. 2023, 285, 115445. [Google Scholar] [CrossRef]
- Liu, J.; Anavatti, S.; Garratt, M.; Abbass, H.A. A hierarchical mission planning system for multi-uncrewed ground vehicles using fast cost evaluation and ant colony optimisation. Inf. Sci. 2024, 679, 121029. [Google Scholar] [CrossRef]
- Hussein, A.; Nguyen, H.; Abbass, H.A. Machine teaching in Swarm Metaverse under different levels of autonomy. Philos. Trans. R. Soc. A Math. Phys. Eng. Sci. 2025, 383, 20240149. [Google Scholar] [CrossRef]
- Saffre, F.; Hildmann, H.; Karvonen, H.; Lind, T. Self-Swarming for Multi-Robot Systems Deployed for Situational Awareness. In New Developments and Environmental Applications of Drones; Lipping, T., Linna, P., Narra, N., Eds.; Springer International Publishing: Cham, Switzerland, 2022; pp. 51–72. [Google Scholar] [CrossRef]
- Kurunathan, H.; Huang, H.; Li, K.; Ni, W.; Hossain, E. Machine Learning-Aided Operations and Communications of Unmanned Aerial Vehicles: A Contemporary Survey. IEEE Commun. Surv. Tutor. 2024, 26, 496–533. [Google Scholar] [CrossRef]
- Divakar, D.; Kanmani; Supriya, A.V. Drone Swarm Coordination Using Machine Learning in IoT Networks. In Machine Learning for Drone-Enabled IoT Networks; Hassan, J., Khalifa, S., Misra, P., Eds.; Springer Nature Switzerland: Cham, Switzerland, 2025; pp. 39–64. [Google Scholar] [CrossRef]
- Khan, M.A.; Kumar, N.; Mohsan, S.A.H.; Khan, W.U.; Nasralla, M.M.; Alsharif, M.H.; Żywiołek, J.; Ullah, I. Swarm of UAVs for Network Management in 6G: A Technical Review. IEEE Trans. Netw. Serv. Manag. 2023, 20, 741–761. [Google Scholar] [CrossRef]
- Koushik, A.; Hu, F.; Kumar, S. Deep Q-Learning-Based Node Positioning for Throughput-Optimal Communications in Dynamic UAV Swarm Network. IEEE Trans. Cogn. Commun. Netw. 2019, 5, 554–566. [Google Scholar] [CrossRef]
- Wei, J.; Zhao, Y.; Yang, K. Integrated Communication and Control for Intelligent Formation Management of UAV Swarms: A Deep Reinforcement Learning Approach. IEEE Wirel. Commun. Lett. 2025, 14, 1351–1355. [Google Scholar] [CrossRef]
- Wang, X.; Xu, Y.; Chen, C.; Yang, X.; Chen, J.; Ruan, L.; Xu, Y.; Chen, R. Machine Learning Empowered Spectrum Sharing in Intelligent Unmanned Swarm Communication Systems: Challenges, Requirements and Solutions. IEEE Access 2020, 8, 89839–89849. [Google Scholar] [CrossRef]
- Mao, Q.; Zhang, L.; Hu, F.; Bentley, E.S.; Kumar, S. Deep Learning (DL)-based adaptive transport layer control in UAV Swarm Networks. Comput. Netw. 2021, 201, 108511. [Google Scholar] [CrossRef]
- Xiao, Y.; Ye, Y.; Huang, S.; Hao, L.; Ma, Z.; Xiao, M.; Mumtaz, S.; Dobre, O.A. Fully Decentralized Federated Learning-Based On-Board Mission for UAV Swarm System. IEEE Commun. Lett. 2021, 25, 3296–3300. [Google Scholar] [CrossRef]
- Xu, J.; Yao, H.; Zhang, R.; Mai, T.; Huang, S.; Guo, S. Federated Learning Powered Semantic Communication for UAV Swarm Cooperation. IEEE Wirel. Commun. 2024, 31, 140–146. [Google Scholar] [CrossRef]
- Myers, R.J.; Perera, S.M.; McLewee, G.; Huang, D.; Song, H. Multi-Beam Beamforming-Based ML Algorithm to Optimize the Routing of Drone Swarms. Drones 2024, 8, 57. [Google Scholar] [CrossRef]
- Tsipi, L.; Tatsis, V.I.; Skoutas, D.N.; Vouyioukas, D.; Skianis, C. A Machine Learning UAV Deployment Approach for Emergency Cellular Networks. In Proceedings of the ICC 2023-IEEE International Conference on Communications, Rome, Italy, 28 May–1 June 2023; pp. 5683–5688. [Google Scholar] [CrossRef]
- Khalil, H.; Rahman, S.U.; Ullah, I.; Khan, I.; Alghadhban, A.J.; Al-Adhaileh, M.H.; Ali, G.; ElAffendi, M. A UAV-Swarm-Communication Model Using a Machine-Learning Approach for Search-and-Rescue Applications. Drones 2022, 6, 372. [Google Scholar] [CrossRef]
- Khalil, H.; Ali, G.; Ur Rahman, S.; Asim, M.; El Affendi, M. Outage Prediction and Improvement in 6G for UAV Swarm Relays Using Machine Learning. Prog. Electromagn. Res. B 2024, 107, 33–45. [Google Scholar] [CrossRef]
- Lim, R.Y.H.; Lim, J.M.Y.; Lan, B.L.; Ho, P.W.C.; Ho, N.S.; Ooi, T.W.M. UAV Swarm Communication Reliability Prediction using Machine Learning. In Proceedings of the 2023 IEEE 8th International Conference on Recent Advances and Innovations in Engineering (ICRAIE), Kuala Lumpur, Malaysia, 2–3 December 2023; pp. 1–6. [Google Scholar] [CrossRef]
- Chandhar, P.; Danev, D.; Larsson, E.G. Massive MIMO for Communications With Drone Swarms. IEEE Trans. Wirel. Commun. 2018, 17, 1604–1629. [Google Scholar] [CrossRef]
- Lakas, A.; Belkacem, A.N.; Al Hassani, S. An Adaptive Multi-clustered Scheme for Autonomous UAV Swarms. In Proceedings of the 2020 International Wireless Communications and Mobile Computing (IWCMC), Limassol, Cyprus, 15–19 June 2020; pp. 1567–1572. [Google Scholar] [CrossRef]
- Sousa, D.; Luís, M.; Sargento, S.; Pereira, A. An Aquatic Mobile Sensing USV Swarm with a Link Quality-Based Delay Tolerant Network. Sensors 2018, 18, 3440. [Google Scholar] [CrossRef]
- Nomikos, N.; Giannopoulos, A.; Kalafatelis, A.; Özduran, V.; Trakadas, P.; Karagiannidis, G.K. Improving Connectivity in 6G Maritime Communication Networks With UAV Swarms. IEEE Access 2024, 12, 18739–18751. [Google Scholar] [CrossRef]
- Pham, Q.V.; Huynh-The, T.; Alazab, M.; Zhao, J.; Hwang, W.J. Sum-Rate Maximization for UAV-Assisted Visible Light Communications Using NOMA: Swarm Intelligence Meets Machine Learning. IEEE Internet Things J. 2020, 7, 10375–10387. [Google Scholar] [CrossRef]
- Zhou, F.; Lagkas, T.; Aadil, F. Optimizing Edge Computing for Internet of Drones: A Hybrid Approach Using Deep Learning and Swarm-Based Routing. Macaw Int. J. Adv. Res. Comput. Sci. Eng. 2025, 10, 64–73. [Google Scholar] [CrossRef]
- Mahmood, M.; Ghadaksaz, M.; Koc, A.; Le-Ngoc, T. Deep Learning Meets Swarm Intelligence for UAV-Assisted IoT Coverage in Massive MIMO. IEEE Internet Things J. 2024, 11, 7679–7696. [Google Scholar] [CrossRef]
- Liu, Z.; Ghulam, M.u.d.; Zheng, J.; Wang, S.; Muhammad, A. A novel deep learning based security assessment framework for enhanced security in swarm network environment. Int. J. Crit. Infrastruct. Prot. 2022, 38, 100540. [Google Scholar] [CrossRef]
- Da Silva, L.M.; Ferrão, I.G.; Dezan, C.; Espes, D.; Branco, K.R.L.J.C. Anomaly-Based Intrusion Detection System for In-Flight and Network Security in UAV Swarm. In Proceedings of the 2023 International Conference on Unmanned Aircraft Systems (ICUAS), Warsaw, Poland, 6–9 June 2023; pp. 812–819. [Google Scholar] [CrossRef]
- Challita, U.; Ferdowsi, A.; Chen, M.; Saad, W. Machine Learning for Wireless Connectivity and Security of Cellular-Connected UAVs. IEEE Wirel. Commun. 2019, 26, 28–35. [Google Scholar] [CrossRef]
- Halli Sudhakara, S.; Haghnegahdar, L. Security Enhancement in AAV Swarms: A Case Study Using Federated Learning and SHAP Analysis. IEEE Open J. Intell. Transp. Syst. 2025, 6, 335–345. [Google Scholar] [CrossRef]
- Chouhan, N.; Jakka, G.; Navale, G.S.; Verma, G.; Patil, P.S.; Dhotay, M.A. A Novel Machine Learning Unmanned Swarm Intelligence Based Data Security in Defence System. In Proceedings of the 2023 International Conference on Advances in Computing, Communication and Applied Informatics (ACCAI), Chennai, India, 25–26 May 2023; pp. 1–8. [Google Scholar] [CrossRef]
- Ahn, H.; Choi, H.L.; Kang, M.; Moon, S. Learning-Based Anomaly Detection and Monitoring for Swarm Drone Flights. Appl. Sci. 2019, 9, 5477. [Google Scholar] [CrossRef]
- Nebe, E.; Sanni, M.L.; Adetona, R.A.; Akinyemi, B.O.; Bello, S.A.; Aderounmu, G.A. Chaos Detection and Mitigation in Swarm of Drones Using Machine Learning Techniques and Chaotic Attractors. Int. J. Adv. Comput. Sci. Appl. 2022, 13, 449–460. [Google Scholar] [CrossRef]
- Gackowska-Kątek, M.; Cofta, P. Explainable machine learning model of disorganisation in swarms of drones. Sci. Rep. 2024, 14, 22519. [Google Scholar] [CrossRef]
- Wedaj Kibret, S. Property-based attestation in device swarms: A machine learning approach. In Machine Learning for Cyber Security; Malik, P., Nautiyal, L., Ram, M., Eds.; De Gruyter: Berlin, Germany, 2022; pp. 71–90. [Google Scholar] [CrossRef]
- Karmakar, R.; Kaddoum, G.; Akhrif, O. A Blockchain-Based Distributed and Intelligent Clustering-Enabled Authentication Protocol for UAV Swarms. IEEE Trans. Mob. Comput. 2024, 23, 6178–6195. [Google Scholar] [CrossRef]
- Semenov, S.; Krupska-Klimczak, M.; Mazurek, P.; Zhang, M.; Chernikh, O. Improving Unmanned Aerial Vehicle Security as a Factor in Sustainable Development of Smart City Infrastructure: Automatic Dependent Surveillance–Broadcast (ADS-B) Data Protection. Sustainability 2025, 17, 1553. [Google Scholar] [CrossRef]
- Guerber, C.; Royer, M.; Larrieu, N. Machine Learning and Software Defined Network to secure communications in a swarm of drones. J. Inf. Secur. Appl. 2021, 61, 102940. [Google Scholar] [CrossRef]
- Tayyab, M.; Mumtaz, M.; Muzammal, S.M.; Jhanjhi, N.Z.; tuz Zahra, F. Swarm Security: Tackling Threats in the Age of Drone Swarms. In Advances in Information Security, Privacy, and Ethics; Shah, I.A., Jhanjhi, N.Z., Eds.; IGI Global: Hershey, PA, USA, 2024; pp. 324–342. [Google Scholar] [CrossRef]
- Phadke, A.; Medrano, F.A. Towards Resilient UAV Swarms—A Breakdown of Resiliency Requirements in UAV Swarms. Drones 2022, 6, 340. [Google Scholar] [CrossRef]
- Naous, T.; Itani, M.; Awad, M.; Sharafeddine, S. Reinforcement Learning in the Sky: A Survey on Enabling Intelligence in NTN-Based Communications. IEEE Access 2023, 11, 19941–19968. [Google Scholar] [CrossRef]
- Huang, X.; Marques-Silva, J. On the failings of Shapley values for explainability. Int. J. Approx. Reason. 2024, 171, 109112. [Google Scholar] [CrossRef]
- Khan, H.A.; Khan, H.; Ghafoor, S.; Khan, M.A. A Survey on Security of Automatic Dependent Surveillance -Broadcast (ADS-B) Protocol: Challenges, Potential Solutions and Future Directions. IEEE Commun. Surv. Tutor. 2024; early access. [Google Scholar] [CrossRef]
- Manzanilla, A.; Reyes, S.; Garcia, M.; Mercado, D.; Lozano, R. Autonomous Navigation for Unmanned Underwater Vehicles: Real-Time Experiments Using Computer Vision. IEEE Robot. Autom. Lett. 2019, 4, 1351–1356. [Google Scholar] [CrossRef]
- Wu, X.; Chen, H.; Chen, C.; Zhong, M.; Xie, S.; Guo, Y.; Fujita, H. The autonomous navigation and obstacle avoidance for USVs with ANOA deep reinforcement learning method. Knowl.-Based Syst. 2020, 196, 105201. [Google Scholar] [CrossRef]
- Iqbal, A.; Tham, M.L.; Wong, Y.J.; Al-Habashna, A.; Wainer, G.; Zhu, Y.X.; Dagiuklas, T. Empowering Non-Terrestrial Networks With Artificial Intelligence: A Survey. IEEE Access 2023, 11, 100986–101006. [Google Scholar] [CrossRef]
- Ali, M.F.; Jayakody, D.N.K.; Chursin, Y.A.; Affes, S.; Dmitry, S. Recent Advances and Future Directions on Underwater Wireless Communications. Arch. Comput. Methods Eng. 2020, 27, 1379–1412. [Google Scholar] [CrossRef]
- Dulac-Arnold, G.; Mankowitz, D.; Hester, T. Challenges of Real-World Reinforcement Learning. arXiv 2019. [Google Scholar] [CrossRef]
- Salvato, E.; Fenu, G.; Medvet, E.; Pellegrino, F.A. Crossing the Reality Gap: A Survey on Sim-to-Real Transferability of Robot Controllers in Reinforcement Learning. IEEE Access 2021, 9, 153171–153187. [Google Scholar] [CrossRef]
- Tobin, J.; Fong, R.; Ray, A.; Schneider, J.; Zaremba, W.; Abbeel, P. Domain Randomization for Transferring Deep Neural Networks from Simulation to the Real World. arXiv 2017. [Google Scholar] [CrossRef]
- Alrefaei, F. Machine Learning for Intrusion Detection into Unmanned Aerial System 6G Networks. Ph.D. Thesis, Embry-Riddle Aeronautical University, Daytona Beach, FL, USA, 2024. [Google Scholar]
- Kheddar, H. Transformers and Large Language Models for Efficient Intrusion Detection Systems: A Comprehensive Survey. arXiv 2025. [Google Scholar] [CrossRef]
- Ali, T. Next-Generation Intrusion Detection Systems with LLMs: Real-Time Anomaly Detection, Explainable AI, and Adaptive Data Generation. Master’s Thesis, University of Oulu, Oulu, Finland, 2024. [Google Scholar]
- Hassanin, M.; Moustafa, N. A Comprehensive Overview of Large Language Models (LLMs) for Cyber Defences: Opportunities and Directions. arXiv 2024. [Google Scholar] [CrossRef]
- Otal, H.T.; Canbaz, M.A. LLM-Assisted Crisis Management: Building Advanced LLM Platforms for Effective Emergency Response and Public Collaboration. arXiv 2024. [Google Scholar] [CrossRef]
- Xia, Y.; Zhang, J.; Jazdi, N.; Weyrich, M. Incorporating Large Language Models into Production Systems for Enhanced Task Automation and Flexibility. arXiv 2024. [Google Scholar] [CrossRef]
- Hays, S.; White, J. Employing LLMs for Incident Response Planning and Review. arXiv 2024. [Google Scholar] [CrossRef]
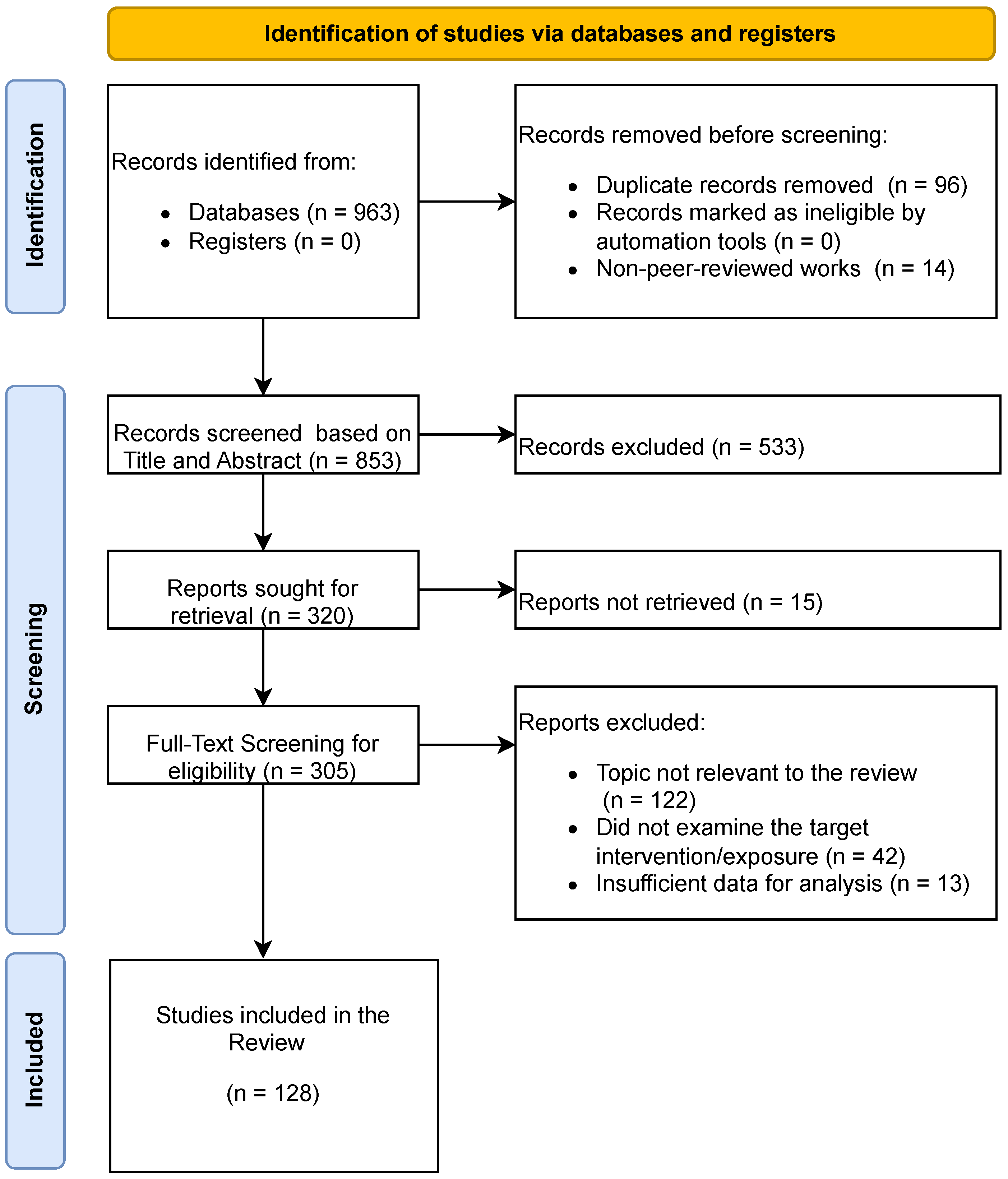
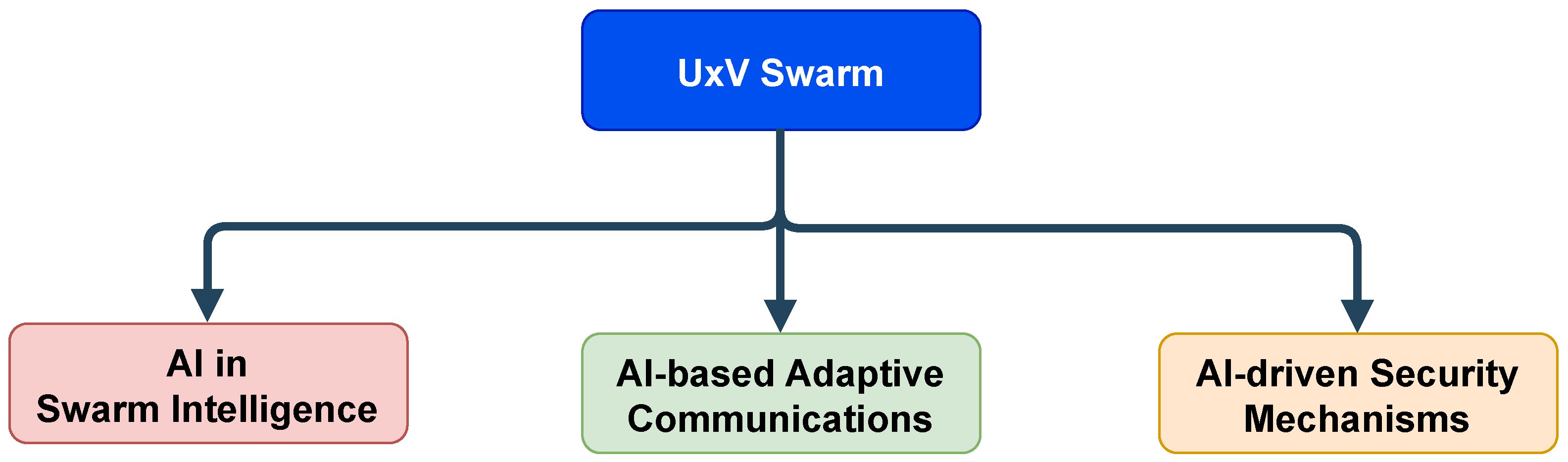


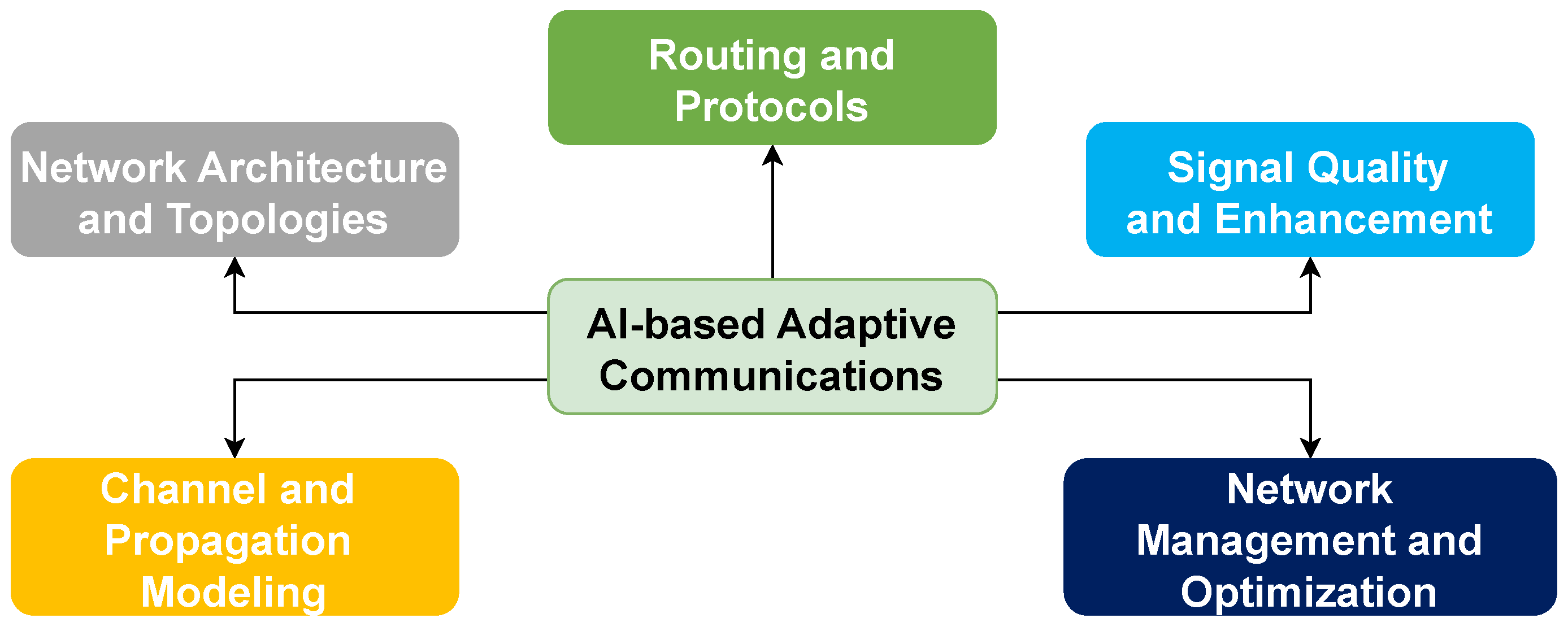

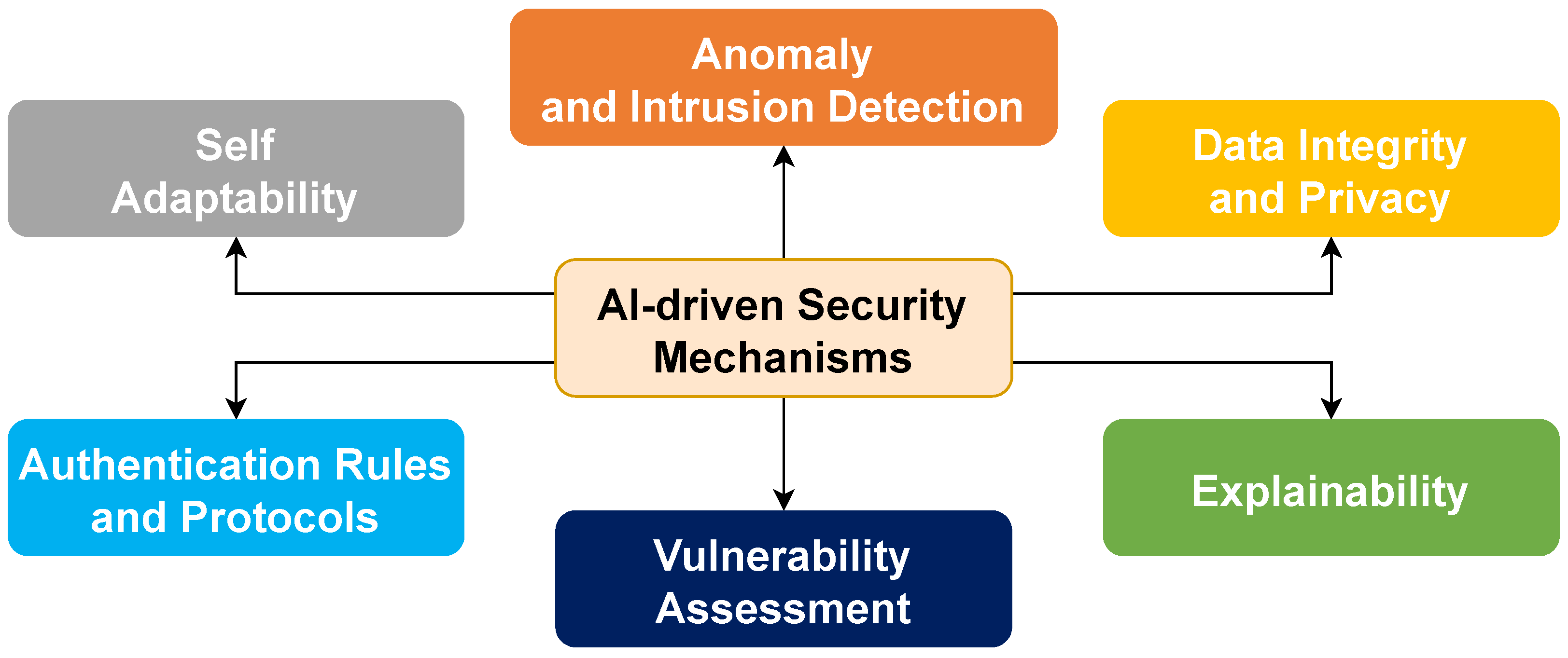
| Reference | Year | Short Description | AI in Swarm Intelligence | AI-Based Adaptive Communications | AI-Driven Security Mechanisms |
|---|---|---|---|---|---|
| Chen, Xi et al. [26] | 2020 | Centered on communication architectures and routing protocols, with only indirect references to optimization. | ✗ | ✓ | ✗ |
| Chen, Wu et al. [27] | 2020 | Proposes robustness techniques for drone swarms using rule-based models with limited AI coverage. | Partially | ✗ | ✗ |
| Sarkar et al. [28] | 2023 | Examines AI methods for network control and UAV coordination, with swarming treated as one of several enabling technologies. | ✓ | ✓ | Partially |
| Puente-Castro et al. [29] | 2022 | Focused survey on AI-driven path planning for UAV swarms using RL, SI, and GNN, without discussing swarm security aspects. | ✓ | ✗ | ✗ |
| Abdelkader et al. [30] | 2021 | Discusses UAV swarms through the lens of localization and planning, minimizing AI and communication complexity. | Partially | Partially | ✗ |
| Tahir et al. [31] | 2019 | Engineering-oriented survey of UAV swarms focusing on control systems, decentralized coordination, and layered communications. | ✗ | ✗ | ✗ |
| Li et al. [32] | 2024 | Integrates AI for adaptive control in heterogeneous UxV networks, centered around SDN architecture rather than swarm systems. | Partially | ✓ | ✗ |
| Schranz et al. [33] | 2020 | Provides a taxonomy of swarm behaviors with examples, avoiding technical AI or communication system analysis. | ✗ | Partially | ✗ |
| Alqudsi et al. [34] | 2025 | Holistic review integrating AI, ML, communication networks, and ethics in design of scalable, intelligent UAV swarms. | ✓ | Partially | ✗ |
| Zaitseva et al. [35] | 2023 | Examines reliability modeling and structural analysis of drone swarms, treating swarms as topological systems, not AI-driven. | ✗ | ✗ | ✗ |
| Asaamoning et al. [36] | 2021 | Reviews drone swarms as distributed control systems, highlighting self-organizing algorithms, system security, and resource management. | ✓ | Partially | ✗ |
| Chung et al. [37] | 2018 | Comprehensive review of UAV swarms, covering flight dynamics, control algorithms, and 3D autonomy. | Partially | ✗ | ✗ |
| Connor et al. [38] | 2021 | Reviews underwater swarm platforms, sensor types, and role-based designs with minimal focus on AI or SI. | Partially | ✗ | ✗ |
| Reference | Year | Short Description | AI in Swarm Intelligence | AI-Based Adaptive Communications | AI-Driven Security Mechanisms |
|---|---|---|---|---|---|
| Wu et al. [39] | 2022 | Research on collaborative search and hunting using multiple USVs. AI central in functions such as path planning, task allocation, and collaborative search. | ✓ | ✗ | ✗ |
| Vedachalam et al. [40] | 2019 | Discusses AUV design and reliability for strategic use, emphasizing battery modeling and navigation accuracy. | Partially | ✗ | ✗ |
| Liu et al. [41] | 2023 | Focuses on coordination challenges of underwater swarms, highlighting environmental constraints and communication limitations. | ✗ | Partially | ✗ |
| Boccardo et al. [42] | 2021 | Summarizes real-world use cases and scenarios and cites works that implemented/tested UAV systems in practice. | Partially | Partially | Partially |
| Michailidis et al. [43] | 2022 | Examines the possibility of a UAV-aided IoT network. Focuses on networking and secure communications. | Partially | ✓ | ✓ |
| Zhou et al. [44] | 2020 | Examines SI by focusing on decision-making, path planning, control, communication, and applications. | ✓ | Partially | ✗ |
| Javed et al. [45] | 2024 | Covers aspects of UAV swarms such as formation control, path planning, autonomy, coordination, security, and communications. | ✓ | ✓ | ✓ |
| Liu et al. [46] | 2024 | Aims to provide a comprehensive survey on applications, challenges, and opportunities of GAI in unmanned vehicle swarms. | ✓ | ✓ | ✓ |
| Azoulay et al. [47] | 2021 | Offers a rich and methodical review of ML techniques for UAV flock formation, task allocation, and coordination | ✓ | Partially | ✗ |
| Reference | Vehicle | Path Planning and Navigation | Obstacle and Collision Avoidance | Formation Control | Target Search | Mission Planning | Task Optimization | Resource Optimization |
|---|---|---|---|---|---|---|---|---|
| Xiao et al. [51] | UAV | ✓ | ✓ | ✓ | ||||
| Perrusquia et al. [52] | UAV | ✓ | ✓ | ✓ | ||||
| Nguyen et al. [53] | UAV, UGV | ✓ | ✓ | ✓ | ||||
| Zhang et al. [54] | UAV, UGV | ✓ | ✓ | ✓ | ✓ | |||
| Venturini et al. [55] | UAV | ✓ | ✓ | ✓ | ✓ | ✓ | ||
| Qamar et al. [56] | UAV | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | |
| Gan et al. [57] | USV | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| Cao et al. [58] | UGV | ✓ | ✓ | ✓ | ||||
| Wang et al. [59] | UUV | ✓ | ✓ | ✓ | ✓ |
| Reference | Vehicle | Path Planning and Navigation | Obstacle and Collision Avoidance | Formation Control | Target Search | Mission Planning | Task Optimization | Resource Optimization |
|---|---|---|---|---|---|---|---|---|
| Yuwen et al. [60] | USV | ✓ | ✓ | ✓ | ||||
| Qin et al. [61] | UUV | ✓ | ✓ | ✓ | ||||
| Praczyk et al. [62] | UUV | ✓ | ✓ | ✓ | ||||
| Raj et al. [63] | UAV | ✓ | ✓ | |||||
| Cabuk et al. [64] | UAV | ✓ | ✓ | |||||
| Kusyk et al. [65] | UAV | ✓ | ✓ | ✓ | ✓ | |||
| Zeng et al. [66] | UAV | ✓ | ✓ | |||||
| Trihinas et al. [67] | UAV | ✓ | ✓ | ✓ |
| Reference | Vehicle | Path Planning and Navigation | Obstacle and Collision Avoidance | Formation Control | Target Search | Mission Planning | Task Optimization | Resource Optimization |
|---|---|---|---|---|---|---|---|---|
| Saeed et al. [68] | UAV | ✓ | ✓ | ✓ | ||||
| Gal [69] | USV | ✓ | ✓ | ✓ | ✓ | ✓ | ||
| Sundelius et al. [70] | UAV | ✓ | ✓ | ✓ | ✓ | |||
| Zeng and Nait-Abdesselam [71] | UAV | ✓ | ✓ | ✓ | ✓ | |||
| Awasthi et al. [72] | UAV | ✓ | ✓ | ✓ | ✓ | |||
| Zhu et al. [73] | USV | ✓ | ✓ | |||||
| Liu, Jing et al. [74] | UGV | ✓ | ✓ | ✓ | ||||
| Hussein et al. [75] | Generic | ✓ | ✓ | ✓ | ||||
| Saffre et al. [76] | UAV | ✓ | ✓ |
| Reference | Vehicle | Network Architecture and Topologies | Channel and Propagation Modeling | Signal Quality and Enhancement | Routing and Protocols | Network Management and Optimization |
|---|---|---|---|---|---|---|
| Kurunathan et al. [77] | UAV | ✓ | ✓ | ✓ | ✓ | |
| Divakar et al. [78] | UAV | ✓ | ✓ | ✓ | ||
| Khan et al. [79] | UAV | ✓ | ✓ | ✓ | ✓ | |
| Koushik et al. [80] | UAV | ✓ | ✓ | ✓ | ||
| Wei et al. [81] | UAV | ✓ | ✓ | ✓ | ✓ | |
| Wang et al. [82] | UAV | ✓ | ✓ |
| Reference | Vehicle | Network Architecture and Topologies | Channel and Propagation Modeling | Signal Quality and Enhancement | Routing and Protocols | Network Management and Optimization |
|---|---|---|---|---|---|---|
| Kurunathan et al. [77] | UAV | ✓ | ✓ | ✓ | ✓ | |
| Mao et al. [83] | UAV | ✓ | ✓ | ✓ | ||
| Xiao et al. [84] | UAV | ✓ | ✓ | |||
| Xu et al. [85] | UAV | ✓ | ✓ | |||
| Myers et al. [86] | UAV | ✓ | ✓ | ✓ | ✓ | |
| Tsipi et al. [87] | UAV | ✓ | ✓ | ✓ | ||
| Khalil et al. [88] | UAV | ✓ | ✓ | ✓ | ||
| Khalil et al. [89] | UAV | ✓ | ✓ | ✓ | ||
| Lim et al. [90] | UAV | ✓ | ✓ | ✓ |
| Reference | Vehicle | Network Architecture and Topologies | Channel and Propagation Modeling | Signal Quality and Enhancement | Routing and Protocols | Network Management and Optimization |
|---|---|---|---|---|---|---|
| Chandhar et al. [91] | UAV | ✓ | ✓ | |||
| Lakas et al. [92] | UAV | ✓ | ✓ | |||
| Sousa et al. [93] | USV | ✓ | ✓ | |||
| Nomikos et al. [94] | UAV | ✓ | ✓ | ✓ | ||
| Pham et al. [95] | UAV | ✓ | ✓ | ✓ | ✓ | |
| Zhou et al. [96] | UAV | ✓ | ✓ | ✓ | ||
| Mahmood et al. [97] | UAV | ✓ | ✓ | ✓ |
| Reference | Vehicle | Anomaly and Intrusion Detection | Self Adaptability | Data Integrity and Privacy | Authenti-cation Rules and Protocols | Explainability | Vulnerability Assessment |
|---|---|---|---|---|---|---|---|
| Liu et al. [98] | Generic | ✓ | ✓ | ||||
| Da Silva et al. [99] | UAV | ✓ | ✓ | ||||
| Challita et al. [100] | UAV | ✓ | ✓ | ✓ | |||
| Halli Sudhakara and Haghnegahdar [101] | UAV | ✓ | ✓ | ✓ | |||
| Chouhan et al. [102] | UAV | ✓ | ✓ | ✓ | |||
| Ahn et al. [103] | UAV | ✓ | |||||
| Nebe et al. [104] | UAV | ✓ | ✓ | ||||
| Gackowska-Katek and Cofta [105] | UAV | ✓ | ✓ | ✓ |
| Reference | Vehicle | Anomaly and Intrusion Detection | Self Adaptability | Data Integrity and Privacy | Authenti-cation Rules and Protocols | Explainability | Vulnerability Assessment |
|---|---|---|---|---|---|---|---|
| Wedaj Kibret [106] | Generic | ✓ | |||||
| Karmakar et al. [107] | UAV | ✓ | ✓ | ||||
| Semenov et al. [108] | UAV | ✓ | |||||
| Guerber et al. [109] | UAV | ✓ | ✓ | ||||
| Tayyab et al. [110] | UAV | ✓ | ✓ | ||||
| Phadke & Medrano [111] | UAV | ✓ | ✓ |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Dimos, A.; Skoutas, D.N.; Nomikos, N.; Skianis, C. A Survey on UxV Swarms and the Role of Artificial Intelligence as a Technological Enabler. Drones 2025, 9, 700. https://doi.org/10.3390/drones9100700
Dimos A, Skoutas DN, Nomikos N, Skianis C. A Survey on UxV Swarms and the Role of Artificial Intelligence as a Technological Enabler. Drones. 2025; 9(10):700. https://doi.org/10.3390/drones9100700
Chicago/Turabian StyleDimos, Alexandros, Dimitrios N. Skoutas, Nikolaos Nomikos, and Charalabos Skianis. 2025. "A Survey on UxV Swarms and the Role of Artificial Intelligence as a Technological Enabler" Drones 9, no. 10: 700. https://doi.org/10.3390/drones9100700
APA StyleDimos, A., Skoutas, D. N., Nomikos, N., & Skianis, C. (2025). A Survey on UxV Swarms and the Role of Artificial Intelligence as a Technological Enabler. Drones, 9(10), 700. https://doi.org/10.3390/drones9100700









