1. Introduction
The development of information technology has reached a new peak with the explosive growth of wireless networks. Although the Fifth Generation (5G) mobile communication networks have been gradually commercialized, 5G networks still suffer an enormous communication burden due to the need for ultra-reliable, low-latency communication, and the rising demand for ubiquitous wireless services [
1,
2]. To tackle such difficulties, industry and academia have prioritized research on Sixth Generation (6G) networks. In typical 6G network application scenarios, such as emergency communication, traffic control, monitoring, search and rescue, the unmanned aerial vehicles (UAVs) can use their flexibility to expand the communication coverage, reduce the path loss of signal transmission, improve communication quality, reduce transmission delay, and so on [
3,
4,
5,
6,
7,
8]. Thus, UAV-enabled communications will play an importance role of assistance in the future 6G networks. However, the line-of-sight channel (LC) link and broadcast characteristics of wireless communications make UAV communications in 6G networks particularly susceptible to serious security threats such as intentional jamming and eavesdropping. Therefore, studying how to solve the security issues of UAV networks has turned into a challenging and thorny problem in industry and academia.
UAVs can provide superiority conditions for legitimate nodes over malignant ground nodes using their adjustable flying trajectories. Several works have studied various UAV-enabled secure communication systems. These studies mainly fall into two categories: one against passive eavesdroppers [
9,
10,
11,
12,
13,
14,
15,
16,
17] and the other against active eavesdroppers [
18,
19,
20,
21,
22,
23]. Especially for the first category, the UAV trajectory, power control, and time allocation can be combined to improve the secrecy rates in UAV networks. However, full-duplex technology has become a viable strategy for improving future communication systems’ spectrum efficiency. Therefore, active eavesdroppers can further threaten the UAV communication systems by employing the full-duplex technology. Specifically, the active eavesdroppers not only wiretap the confidential information between legitimate ground nodes and the UAV, but also transmit jamming signals to the legitimate nodes. As a result, the research of secure UAV-enabled communication when active eavesdroppers are present is particularly important. In [
18], the authors investigated the secure UAV communication involving uplink and downlink transmission. The average secrecy rate was improved by jointly optimizing the UAV trajectory, the power allocation of the UAV, and legitimate ground nodes. The literature [
19] proposed a secure UAV communication scheme based on artificial noise beamforming, in which the full-duplex relay UAVs send jamming signals to confuse active eavesdropping nodes. The authors designed an algorithm based on reinforcement learning to find the best UAV trajectory and appropriate allocation to ensure secure transmission. The authors in [
20] investigated the wireless surveillance problem in UAV relay systems, by optimizing the interference power allocation of the legal monitor, the average effective eavesdropping rate is maximized, and the proposed active eavesdropping method significantly improved the eavesdropping rate. The literature [
21] studied the UAV-assisted secure communication system, in which the source communicates with a legitimate UAV while a full-duplex active eavesdropper interferes. In order to minimize the mixed outage probability, the authors jointly designed the power distribution ratio of the transmit signal and the UAV altitude. To decrease the power consumption of the UAV, the literature [
22] proposed a UAV secure communication system model based on an energy harvesting scheme. By analyzing the secrecy performance under the full-duplex active eavesdropping, it obtained the optimal coding rate through the derived transmission outage probability expression. The literature [
23] discussed the secrecy performance of communication systems in which the UAVs send friendly interference signals to prevent full-duplex active eavesdropping with the help of caching. The authors designed an algorithm based on alternating optimization (AO) and successive convex approximation (SCA) to minimize the sum of intercept probability and maximum outage probability for all users.
Although the above literatures optimize the UAV trajectory air-ground channel modeling design for secure UAV communication with active eavesdropping nodes, most of them adopted the Rician fading channel model or LC. Firstly, there are two practical limits to adopting the LC: (i) The critical impacts of LC and non-LC (NLC) conditions related to air-to-ground transmission in city environments are not fully captured by LC [
24]; (ii) Since the elevation between the ground node and the UAV is closely related to the flight path of the UAV, the elevation angle-distance trade-off can not be described accurately [
25]. Secondly, in urban or suburban environments where the UAV flies at high elevations and small-scale fading can dominate channel states, the Ricia fading channel model is more applicable [
26]. In contrast, the PrLC model completely ponders the probability of LC and NLC conditions. When a UAV performs its mission in city areas, sometimes random buildings may block the communications. In this instance, through the 3D UAV trajectory design, the PrLC model can represent more significant shadowing effects.
Inspired by them, we ponder a UAV downlink secure communication system based on the PrLC model, in which the UAV sends classified messages to the legitimate ground nodes under the environment with multiple active eavesdroppers. By concurrently optimizing the communication connection, the 3D UAV trajectory, and the UAV’s transmit power, this paper intends to improve the worst-case average max-min secrecy rate for avoiding against severe threats from the active eavesdroppers. However, obtaining the optimal solution is difficult because it is a non-convex problem, and its secrecy rate expression is complex. Firstly, we approximate the secrecy rate to solve such a problem efficiently without losing the secrecy performance. Secondly, we divided the original problem into four subproblems based on the block coordinate descent (BCD) technique, i.e., the communication connection, the UAV’s transmit power, horizontal trajectory, and altitude optimization. By introducing the SCA technique and slack variables, the non-convex subproblems are converted into convex ones that can be well addressed. Numerical results prove that our proposed algorithm performs better than other benchmark algorithms in improving secrecy rate performance, which highlights the importance of using 3D trajectories using a more precise PrLC model in city environments.
2. System Model
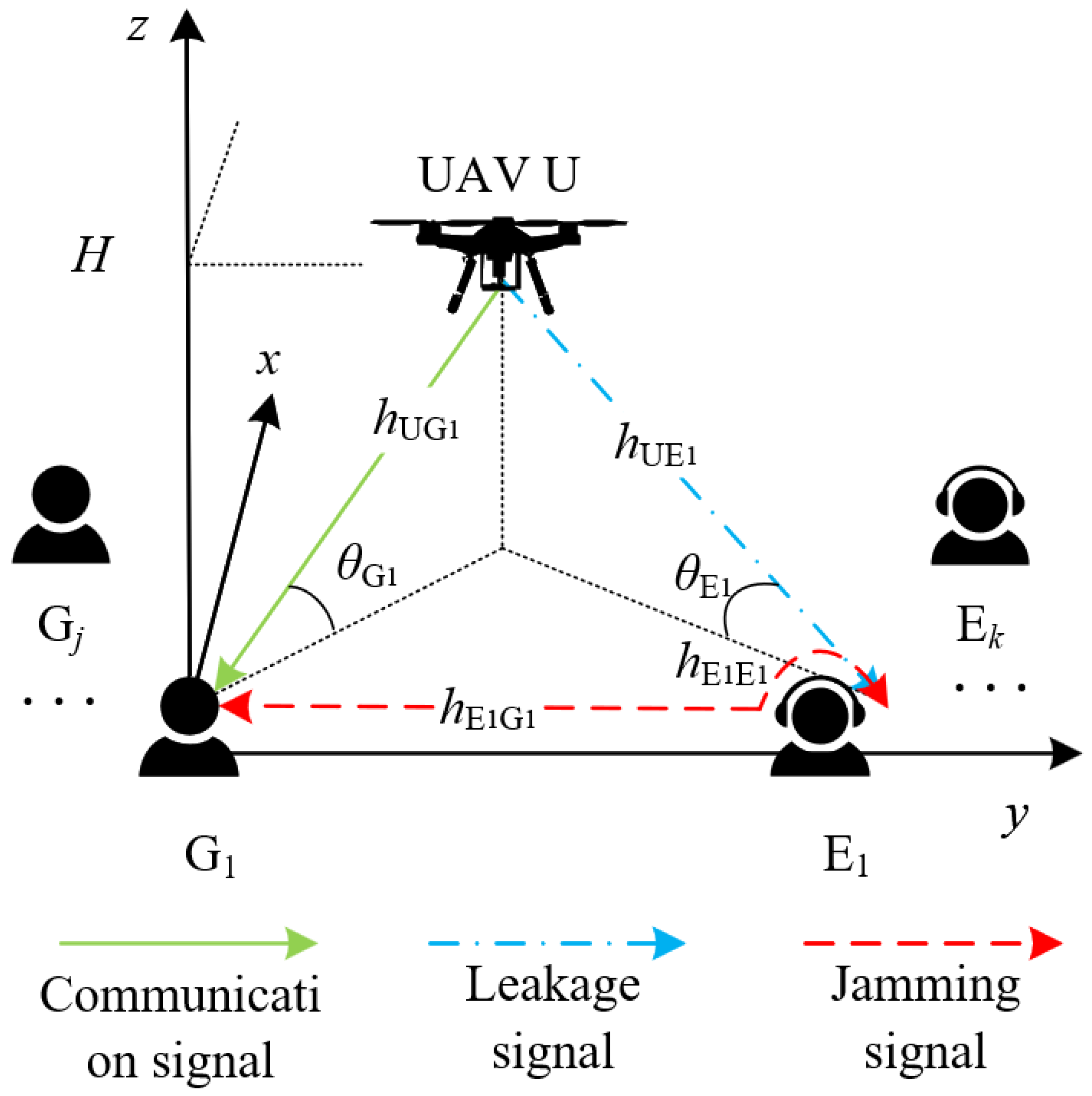
We consider a secure UAV network against active eavesdropping in this paper, as shown in
Figure 1. Specifically, a UAV sends classified messages to ground nodes denoted by
, while multiple active eavesdroppers denoted by
not only wiretap their transmission but also send jamming signals to interfere with the legitimate receivers.
In this paper, the location of each node is represented by a three-dimensional Cartesian coordinate system, in which the horizontal coordinate of
and
are represented by
and
, respectively. In practical applications, the locations of the active eavesdroppers can be accurately determined by using existing technologies, such as the global positioning system (GPS) and optoelectronic devices [
27,
28,
29], so we assume that
is known in advance.
Furthermore, we suppose that the UAV flies horizontally from its original position to its final location, which is represented by and , respectively, and are the fixed altitude. In order to solve this problem flexibly, we divide the limited flying time T of the UAV into N equal-length time slots, each of which is indicated as . Therefore, when is sufficiently small, the continuous 3D UAV trajectory is approximated by , and represent the horizontal and vertical coordinates of the UAV at time slot n, respectively.
Let binary variables
for
represent the channel condition in time slot
n, where
is the LC conditions and
is NLC condition. This paper adopts the PrLC model [
30], for which the UAV-to-
channel or the UAV-to-
channel can be described by LC or NLC condition. Thus, in the
nth time slot, the LC probability for
or
is given by
where
and
are constants specified by the actual area, and the elevation angle from the UAV to
or
is denoted as
Then, the NLC probability between the UAV and or is denoted as .
Thus, the power gain of the UAV and
or
is denoted as
where
and
,
and
are the path loss exponents,
is the signal attenuation factor. Furthermore, the length between the UAV and
or
in
nth is expressed as
.
The channel between
and
is described by the Rayleigh channel, and its power gain is expressed as
where
denotes the path loss exponent,
is the distance between
and
, and
denotes a random variable with a zero-mean and unit-variance circularly symmetric complex Gaussian (CSCG) random variable.
Because of the limitation of airborne energy, the UAV’s transmit power
should be constrained by the average power and peak power, which are described by
and
, i.e.,
Suppose that UAV U serves the ground nodes in Time Division Multiple Access (TDMA) mode. Let
denotes the scheduling constraint between the UAV and
in the
nth, and
represents that the UAV does not communicate with
; or else
. Therefore, the average achievable secrecy rate in bps/Hz of
over
N time slots can be denoted as [
31,
32]
where,
,
where
is the expectation operator about
,
represents the maximum jamming power of
, and
is the self-interference between
’s receiving antenna and its transmitting antenna. Since we assume that the distance between the eavesdroppers is great, only the self-interference of the eavesdroppers exists, without the interference from other eavesdroppers, which thus can be ignored.
We notice that
is convex with respect to (w.r.t.)
in
. Therefore, based on Jensen’s inequality, the lower bound of
is expressed as
Since this paper considers the worst-case secrecy rate performance, we assume that during the UAV’s mission, the active eavesdropping node
transmits with its maximum power while being able to eliminate its self-interference
completely. Therefore,
can be upper-bounded by
Therefore, according to [
24], using the total probability theorem, the expected achievable rate of
or
at slot
n is denoted as
where
and
denote the reachable rates conditioned on the LC and NLC conditions from the UAV to
, respectively.
Furthermore, and indicate the reachable rate of UAV to under the LC and NLC conditions.
For ease of solution, we approximate the anticipated rate in (
11) as
To demonstrate the accuracy of the approximate result
in (
12), we suppose that the UAV remains level during the flight from
to
, where
locates at
m and
’s horizontal coordinate is
m. Furthermore, the simulation parameters set as
m,
dB,
,
,
W,
W,
,
,
,
dBm and
dB. As shown in
Figure 2, we provide an illustrative result, the values of the NLC terms
and
in the
expression in (
11) are both close to zero. Therefore, the rate expression can be calculated without affecting the accuracy of the rate expression.
3. Problem Formulation
Let
,
,
and
express the communication connection, the UAV’s transmit power, horizontal trajectory and altitude, respectively, where
,
. By jointly designing
,
,
and
, we aim to maximize the average secrecy rate. Thus, the optimization problem is generally expressed as follows
where we let
,
represents the maximum achievable rate of the eavesdroppers at the
nth time slot. Among them, (15)–(18) are the movement constraints of the UAV.
and
represent the maximum horizontal and vertical flight speeds in meters per second (m/s).
and
are the minimum and maximum altitudes that the UAV can reach. Thus, in each time slot
n, the farthest horizontal and vertical distance that the UAV flies can be denoted as
and
, respectively.
Since the secrecy rate in practice will not be negative, by allocating
, the best result of (
6) can be at least zero. Thus, we can drop the operation
. However, problem (13) remains intractable for the following three main reasons: (1) The interference and wiretapping caused by the multiple active eavesdroppers; (2) The probability in (
12) is higly related to the UAV’s 3D trajectory; (3) It is challenging to settle the mixed-integer optimization problem caused by binary variable constraints (19) and (20).
Thus, this paper design an efficient iterative algorithm to settle (13) alternately in the next section.
4. Optimization Algorithm Design
With the BCD and SCA techniques, this paper design an efficient algorithm to solve problem (13). Specifically, this paper divide (13) into four sub-problems, and iteratively optimize the variables of the communication connection , the UAV’s transmit power , its horizontal trajectory , and the altitude of the UAV until it converges.
4.1. Communication Scheduling Optimization
Problem (13) can be expressed as follows by giving any appropriate
,
and
Since (21) has been transformed into a convex problem, it is settled by using the CVX toolbox [
33].
4.2. Optimization of the UAV’s Transmit Power
By giving any appropriate
,
and
, problem (13) can be denoted as follows
We set
,
to deal with the non-convex constraint (14), where
. Therefore, problem (23) can be definited as
Because of the non-convex constraint (25), (24) is still non-convex. However, it is observed that
in (25) is concave w.r.t.
, so the first-order Taylor expansion can be used for the local point
in the
fth iteration to obtain its upper bound, i.e.,
where
.
Using (26) to replace (25), problem (24) can be reconstructed as
which has been converted into a convex optimization problem that can be successfully settled by applying the interior point method [
34].
4.3. Optimization of the UAV’s Horizontal Trajectory
By giving any appropriate
,
,
, problem (13) can be denoted as follows
By using slack variables
,
,
and
, where
, problem (29) can be reconstructed as
where
and
. Furthermore,
and
are slack variables, where
.
Due to non-convex constraints (31), (32), (35)–(37), it is difficult to find the best result of problem (30).
Though the constraint (31) is non-convex,
is jointly convex w.r.t. both
and
. Therefore, in the
fth iteration, the first-order Taylor expansion for the given local points
and
, where
, can be expressed as
where
,
.
For the non-convex constraint (32), we take the logarithm to decouple the optimization variables. Then, by giving slack variables
and
, where
, we can get
Although the constraints (35)–(37), (40) and (42) are non-convex, we can observe that
in (35) is convex w.r.t.
,
in (36) is convex w.r.t.
, and the right-hand side of (37) is convex w.r.t.
,
in (40) is concave w.r.t.
, and the left-hand side of (42) is convex w.r.t.
. Therefore, the first-order Taylor formula can be expanded at local points
,
,
and
in the
fth iteration, where
, i.e.,
where
,
, .
With (39), (41), and (43)–(47), problem (30) can be transformed into the convex optimization formula as follows
By applying the interior point method, the above problems can be easily worked out. Therefore, the solution obtained from this sub-problem as a given variable in the sub-problem of vertical trajectory optimization for UAV in the next subsection.
4.4. Optimization of the UAV’s Vertical Trajectory
Problem (13) can be denoted as follows by giving any appropriate
,
and
For the optimization variable , following the procedure for solving problem (29), problem (50) can be solved similarly. The same convex constraints (33), (34), (37), (41), (43), (46), (47), and (49) can be obtained by introducing similar slack variables and approximating them using the SCA technique. Furthermore, since the right-hand sides of the non-convex conditions (36) and (38) are convex and concave w.r.t optimization variable , respectively, they can also be converted to convex constraints by using SCA techniques. Together with (17) and (18), problem (50) can be reformulated into a convex optimization problem.
In conclusion, by resolving four sub-problems (21), (27), (48) and (50) until the algorithm converges to a prespecified accuracy
, the suboptimal solution to (13) can be found. Algorithm 1 summarizes the process of obtaining the sub-optimal solution.
| Algorithm 1 Algorithm to solve problem (13) |
- 1:
Initialize variable , , , , let the number of iterations; - 2:
repeat: - 3:
Given , , , solve the problem (21), get as the optimal solution; - 4:
Given , , , solve the problem (27), get as the optimal solution; - 5:
Given , , , solve the problem (48), get as the optimal solution; - 6:
Given , , , solve the problem (50), get as the optimal solution; - 7:
number of update iterations ; - 8:
until: convergence to a given accuracy .
|
5. Numerical Results
In this part, three benchmark strategies are analyzed and compared to verify our proposed algorithm’s effectiveness under the PrLC model represented by TP-PrLC:
3D UAV trajectory design without power control based on the PrLC model (represented as TNP-PrLC);
A joint majorization strategy of UAV horizontal trajectory and power control based on the PrLC model, in which the UAV altitude is fixed as the lowest altitude (represented as HTP-PrLC);
A joint development strategy of UAV 3D trajectory and communication resources based on the LC model (represented as TP-LC).
Specifically, in the TNP-PrLC strategy, the UAV’s transmit power is fixed to be its average power rate, i.e.,
. The solutions to the communication connection and 3D UAV trajectory are obtained by solving problems (21), (48), (50) alternatively. While in the HTP-PrLC strategy, the UAV altitude is fixed to the minimum height, i.e.,
m. By solving problems (21), (27) and (48) alternately in an iterative manner, we can obtain the optimized communication connection and horizontal trajectory of the UAV.
Table 1 shows the simulation parameters.
Next, the numerical results are divided into two subsections. We analyze the different case of a single ground node and eavesdropper, as well as that with more practical multiple ground nodes and eavesdroppers.
5.1. Single Ground Node and Active Eavesdropper Instance
The convergence performance of Algorithm 1 is verified in
Figure 3, where
= 0.02 W. As the number of iterations increases, the average achievable rate will also increase. For different time
T, about ten iterations, it will be convergent. As
T increases, the average achievable rate increases significantly. This is because as
T increases, the UAV has more time to hover at the optimal position, so as to strike a balance between mitigating the malicious interference as well as eavesdropping caused by the active eavesdropper and increasing the achievable rate at the ground node.
Figure 4a presents the horizontal trajectories of the UAV with different strategies when
T = 160 s and
= 0.02 W. In the TP-LC strategy, the UAV first flies to the left of
along an approximately straight path. However, the UAV under the PrLC model flies directly to the top of
. This is because the PrLC model has an additional elevation-distance trade-off compared to the LC model. Therefore, the UAV can achieve a better balance between minimizing the message leakage rate to
and maximizing the achievable rate to
. During the return journey, to reduce the message leakage of the UAV, almost benchmarks follow a larger arc trajectory to move away from
. However, the UAV in the TP-LC strategy can only trade off the information achievable rate and information leakage rate by adjusting the distance, so it can only shorten the distance with
along an approximately straight line to the destination. In the TNP-PrLC strategy, because of the lack of power control, the UAV can only move away along a larger arc trajectory to move away from
to reduce unnecessary information leakage.
Figure 4b presents the 3D trajectories of the UAV with different strategies. The UAV in the TP-PrLC strategy first climbs to the highest altitude to rise its elevation angle to
, resulting in a higher LC probability, and flies at
towards
. Then, when almost reaching
, the UAV descends rapidly to reduce path loss while still insisting a high LC probability. However, in order to attain best channel quality, in the TP-LC strategy, the UAV needs to rely on shorter distances to
. Therefore, the UAV remains at its lowest altitude and flies towards
. During the return journey, the UAV in the TP-PrLC strategy adopts a flight trend of first ascending and then descending to adjust its elevation angle to achieve the optimal secrecy rate balance. In contrast, in the TP-LC strategy, the UAV perform its mission by climbing to the highest altitude to increase the distance from
while not getting too far from
.
Figure 5 presents the 3D trajectories of the UAV with different jamming powers in the TP-PrLC strategy when
T = 160 s. It can be seen that the UAV of all strategies follows the same 3D trajectory. This is because the malicious interference generated by
mainly affects the information reception of the legitimate node
but cannot interfere with the information transmission of the UAV. Therefore, in the UAV downlink information transmission, the change in interference power does not result in a change in the optimized UAV trajectory.
Figure 6 presents the relationship between the average secrecy rates of different strategies with different
T and
. It can be seen that the TP-PrLC strategy achieves the best average secrecy rate; however, the TP-LC strategy has the worst performance. This verifies the accuracy of PrLC model compared with LC model for the representation of the path loss and shadow fading in city areas. In contrast, since the TNP-PrLC strategy cannot further adjust the secrecy rate through power control, it cannot effectively combat the threats of the active eavesdropper, which results in worse performance. Due to the lack of additional gain obtained by altitude optimization, the secrecy rate of the HTP-PrLC strategy is lower than that of the TP-PrLC strategy. Furthermore, as
increased, the gaps between all strategies increased with
T. This shows that in complex city environments, jointly designing the 3D trajectory and the UAV’s power control can significantly reduce the adverse impact of the active eavesdropper.
5.2. Multiple Ground Nodes and Active Eavesdroppers Instance
We consider two legitimate ground nodes in this subsection,
and
, and two active eavesdroppers,
and
. Specifically,
Figure 7 reveals the 3D trajectory of the UAV with different strategies when
T = 160 s and
= 0.02 W;
Figure 8 illustrates the transmit power of various strategies with
= 0.02 W;
Figure 9 demonstrates the average secrecy rate with
= 0.02 W.
Figure 7a presents the horizontal trajectories for different strategies when
T = 160 s and
= 0.02 W. It can be noted that the UAVs of all strategies fly from
to
, and from
to
, at their maximum flying speeds to complete their missions as soon as possible. However, when the UAVs fly from
to
, their trajectories show obvious differences. Specifically, in the TP-PrLC and HTP-PrLC strategies, the UAV trajectory takes an arcing flight, making the elevation angles between the UAV and
and
much more extensive than those with
and
, thereby obtaining a higher LC probability. In contrast, the UAV trajectory in the TP-LC strategy is closer to both legitimate and illegitimate nodes, because it can only trade-off the secrecy rate by adjusting its distance to these nodes. In the TNP-PrLC strategy, because lack of power control, the UAV can only fly farther to escape the active eavesdroppers obtaining more information.
Figure 7b presents the UAV 3D trajectories with different strategies when
T = 160 s and
= 0.02 W. During the flight of the UAV from
to
, the UAVs in both of the TP-PrLC and TNP-PrLC strategies first rise then descend, since the higher LC probabilities with
and
can be obtained. However, the UAVs in both strategies transmit at lower power to avoid leaking more information to
and
. During the flight towards
, the UAVs still have higher LC probabilities with the gournd nodes, compared to the active eavesdrop nodes. Therefore, the UAVs are able to send messages at higher powers which can be verified in
Figure 8. For the flight from
to
, compared to other bechmark strategies that the UAVs fly at their lowest altitude to achieve better secrecy perofrmance, the UAV in the TP-LC strategy ascends to enlarge the distance with the active eavesdroppers, but it cannot fly too high due to the guarantee of less pathloss.
Figure 8 presents the schematic of the UAV’s transmit power change with time
T under different strategies when
= 0.02 W. It is worth noting that the UAV under the PrLC model can stay longer at the hovering position above
and
to transmit information with the highest possible transmit power, which can greatly balance the trade-off between elevation and distance. However, since in the TP-LC strategy, the UAV can only avoid the threats from the active eavesdroppers by adjusting the distance, it cannot stay at the hovering location for too long. It can transmit at a certain power to increase the secrecy rate as much as possible. Moreover, when the UAV approaches
, compared with the TP-PrLC strategy, the UAV in the HTP-PrLC, can only increase its transmit power to enhance the achievable rates at
.
Figure 9 plots the comparison of the relation between average secrecy rate and time
T of different strategies when
= 0.02 W. It can also be seen that compared with the single legitimate ground node and active eavesdropper case, applying the PrLC model for creating the UAV’s 3D trajectory and power control can provide a more significant secrecy rate improvement in the more practical multiple ground nodes and eavesdroppers case. This confirms that the PrLC model can more accurately describe the channel condition between the UAVs and multiple ground nodes in city environments.