Confidential Intelligent Traffic Light Control System: Prevention of Unauthorized Traceability
Abstract
1. Introduction
2. Related Work
2.1. Intelligent Traffic Light Control Systems
2.2. Secure Communication Protocols for Intelligent Traffic Management Systems
3. Traffic Light Control System
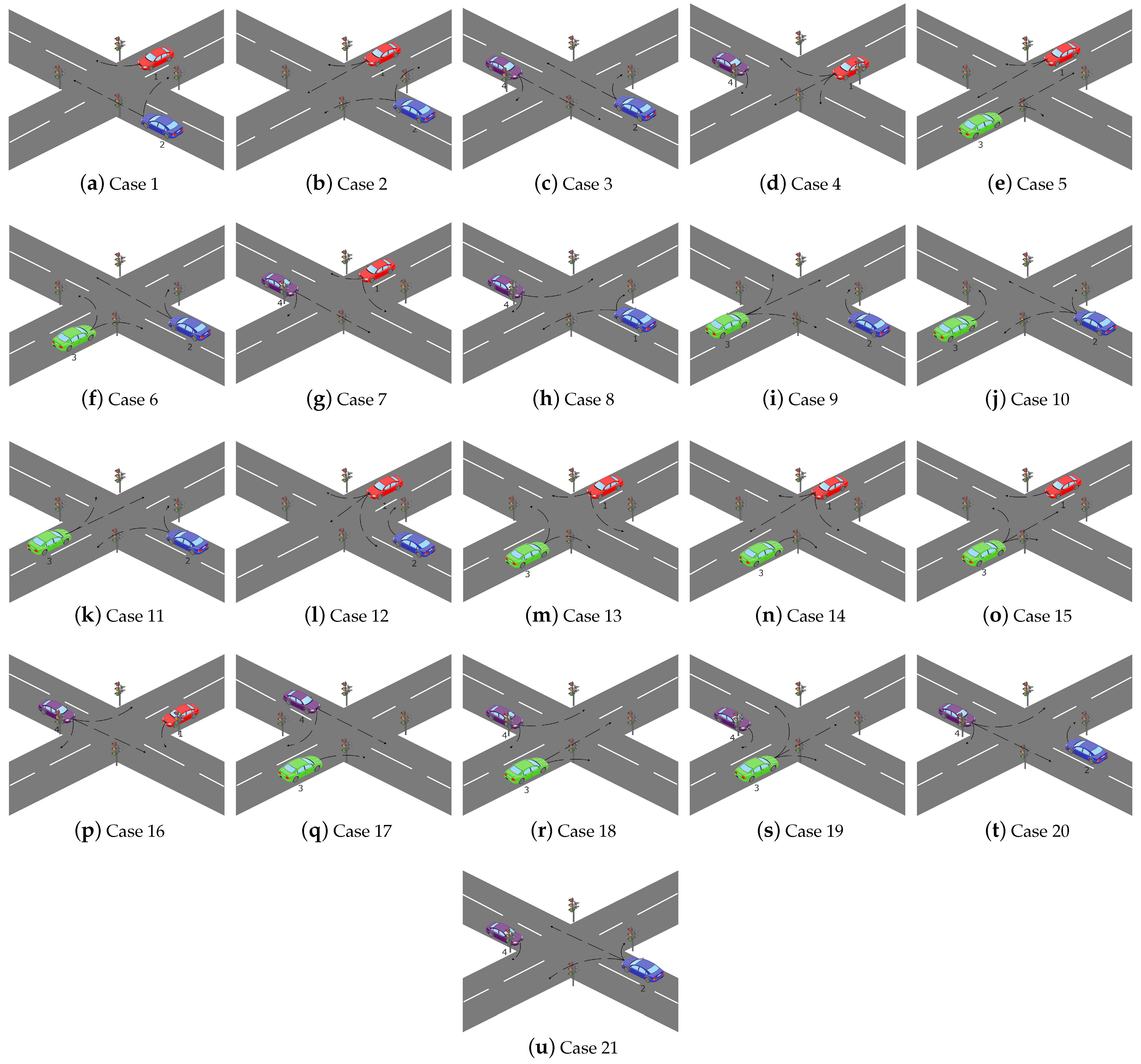
4. Possible Attacks at Intelligent Traffic Light Systems
5. Proposed Confidential Intelligent Traffic Light Control System
- : indicates the distance between the vehicle and the traffic light. This attribute needs sensors or Global Positioning System (GPS) tools to measure it accordingly.
- : indicates the direction of each vehicle concerning the traffic light. It determines whether the vehicle is moving toward or away from the traffic light: “Toward” or “Away” options. This attribute is determined based on the vehicle’s position and movements on the road.
- : denotes the specific lane in which the vehicle is situated. It could be specified as leftmost lane, middle lane, or rightmost lane. This attribute helps determine the vehicle’s lateral position concerning the traffic light.
- : The vehicle category may be identified internally based on its registration information. It can be categorized as a regular vehicle, truck, motorcycle, etc.
- : The vehicle’s speed may be determined by onboard sensors such as radars. The speed characteristic is crucial for managing traffic flow and altering the timings of traffic lights depending on the speed at which vehicles are approaching.
- “”,
- “”,
- “”,
- “”,
- “”.
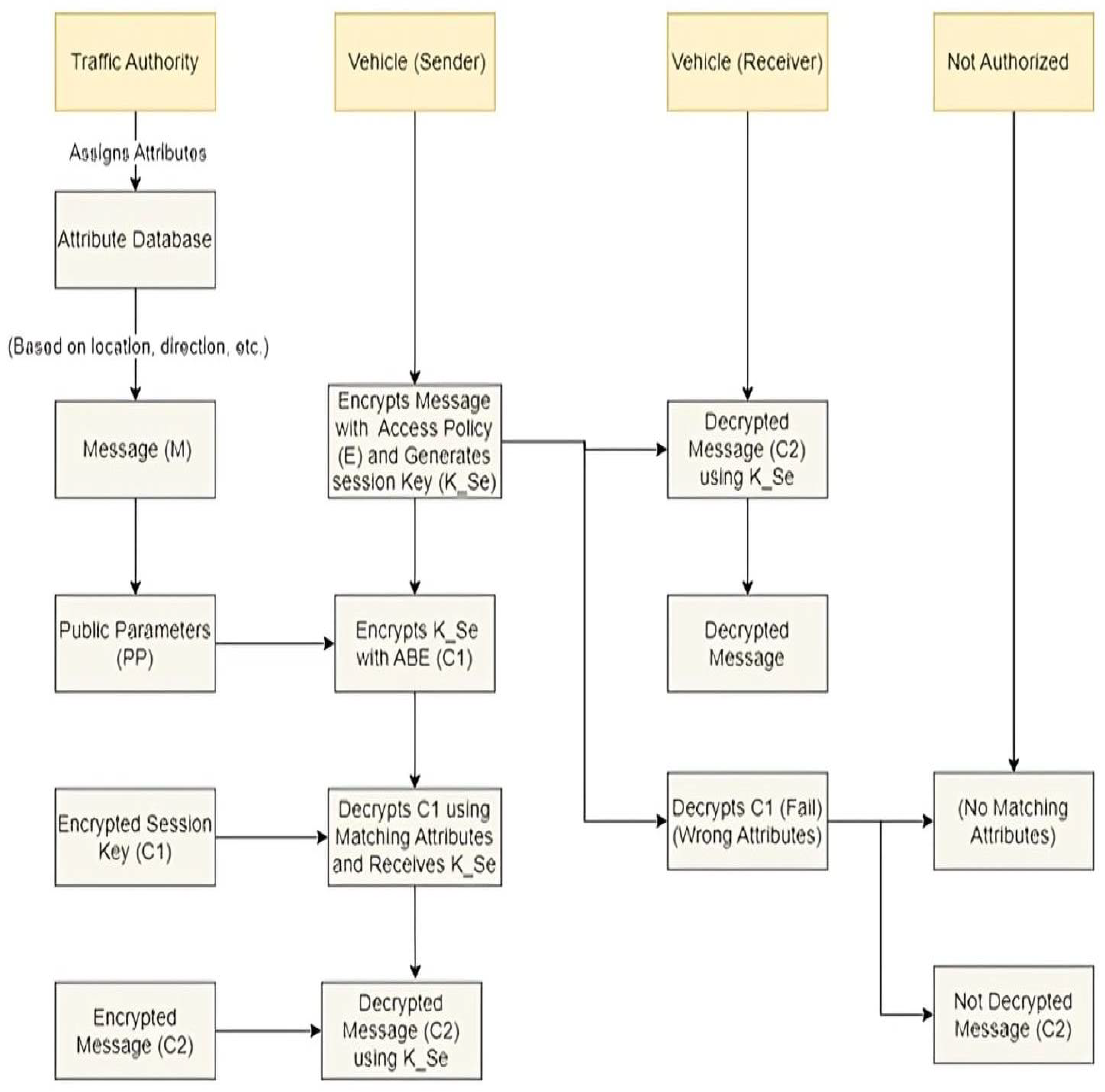
- Key Generation: The key generation procedure, often referred to as the Key Authority (KA), is performed by a reliable and authoritative entity. In a real road scenario, this can be accomplished by roadside units (RSUs) that are connected directly to the traffic authority. The Key Authority (KA) generates the master secret key (MSK) and the appropriate public parameters (PPs) required for the attribute-based encryption (ABE) scheme. The MSK is highly sensitive information that must be securely maintained and used to create private keys associated with certain properties. For the key creation process, the NIST P-256 elliptic curve [47] is a viable choice for pairing operations. This option facilitates the efficient pairing processes for implementing attribute-based encryption (ABE).
- Attribute-Based Encryption Setup: The public parameters (PPs) produced by the key authority (KA) are openly disseminated and accessible to vehicles and infrastructures (i.e., smart traffic lights) in the system. Including these public parameters (PPs) is crucial for executing the ABE method’s encryption and decryption procedures. This includes the details of the privacy policy, the selected cryptographic algorithms, system configurations, and other essential information required to ensure safe encryption and decryption.
- Private Key Generation: After the generation of the master secret key (MSK) by the KA, each vehicle proceeds to produce a private key that corresponds to its specified attributes. Each vehicle obtains a unique private key that corresponds to the characteristics granted to it during the attribute assignment process. The KA announces the MSK and the qualities to produce a unique private key for each vehicle according to their assigned attributes.
- Private Key Distribution: The KA generates private keys for each vehicle and securely distributes them to the respective vehicles. The distribution of private keys must provide secrecy and integrity to prevent unauthorized access to the keys. For the distribution of private keys, KA uses secure communication methods that guarantee the secrecy and integrity of the key transfer. The channels are created between KA and vehicles in motion, enabling the safe transfer of private keys. This strategy was selected based on its efficacy in thwarting unauthorized access to the keys. It is important to emphasize that private keys are only given to vehicles and entities with legitimate attributes issued by the traffic management system. This guarantees that only approved vehicles can use encrypted messages to transmit and exchange.
- Updating Keys: In a dynamic traffic environment, the attributes of vehicles may change over time (e.g., as vehicles move closer or farther from the traffic light). The system should have mechanisms to update or revoke private keys to accommodate attribute updates. The key authority securely manages key updates and revocations. Updating the keys regularly based on the attributes of the vehicles is the main feature that prevents unauthorized traceability and linkability.
- “”,
- “”.
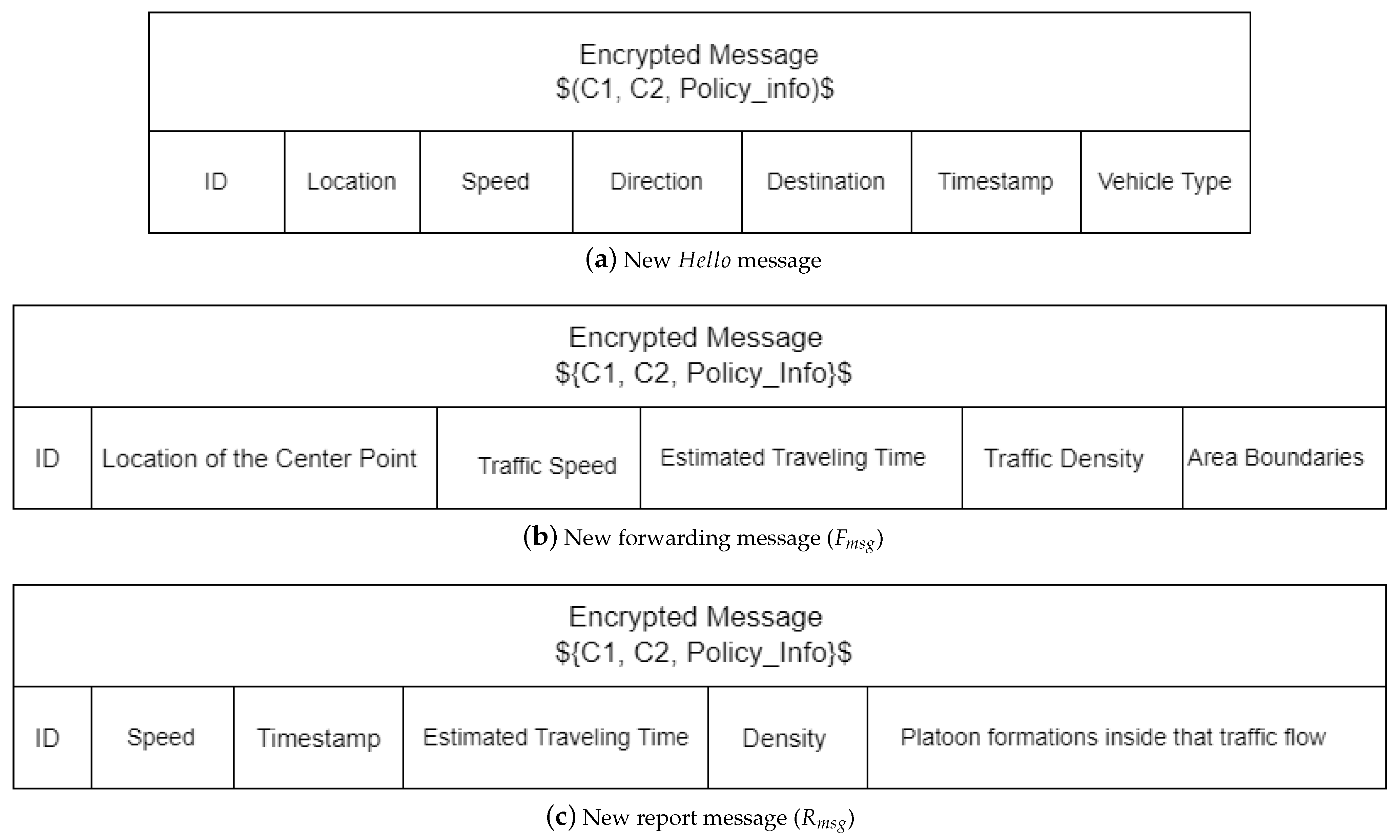
- Access Policy Encoding: Converts the access policy into a mathematical form appropriate for attribute-based encryption (ABE) operations. The access policy comprises logical expressions that are determined by the characteristics given to the receivers.
- Random Session Key Generation: Produces a random session key (). This key is used to encrypt the actual message “M”.
- Attribute-Based Encryption: Performs the attribute-based encryption on the session key () using the encoded access policy and the public parameters. This produces the ciphertext representing the encrypted session key. We denote this encrypted value by (C1), as illustrated in Equation (1):
- Symmetric Encryption: Symmetrically encrypts the actual message “M” using the session key “”, generating another ciphertext (C2), as illustrated in Equation (2):
6. Performance Evaluation and Result Discussion
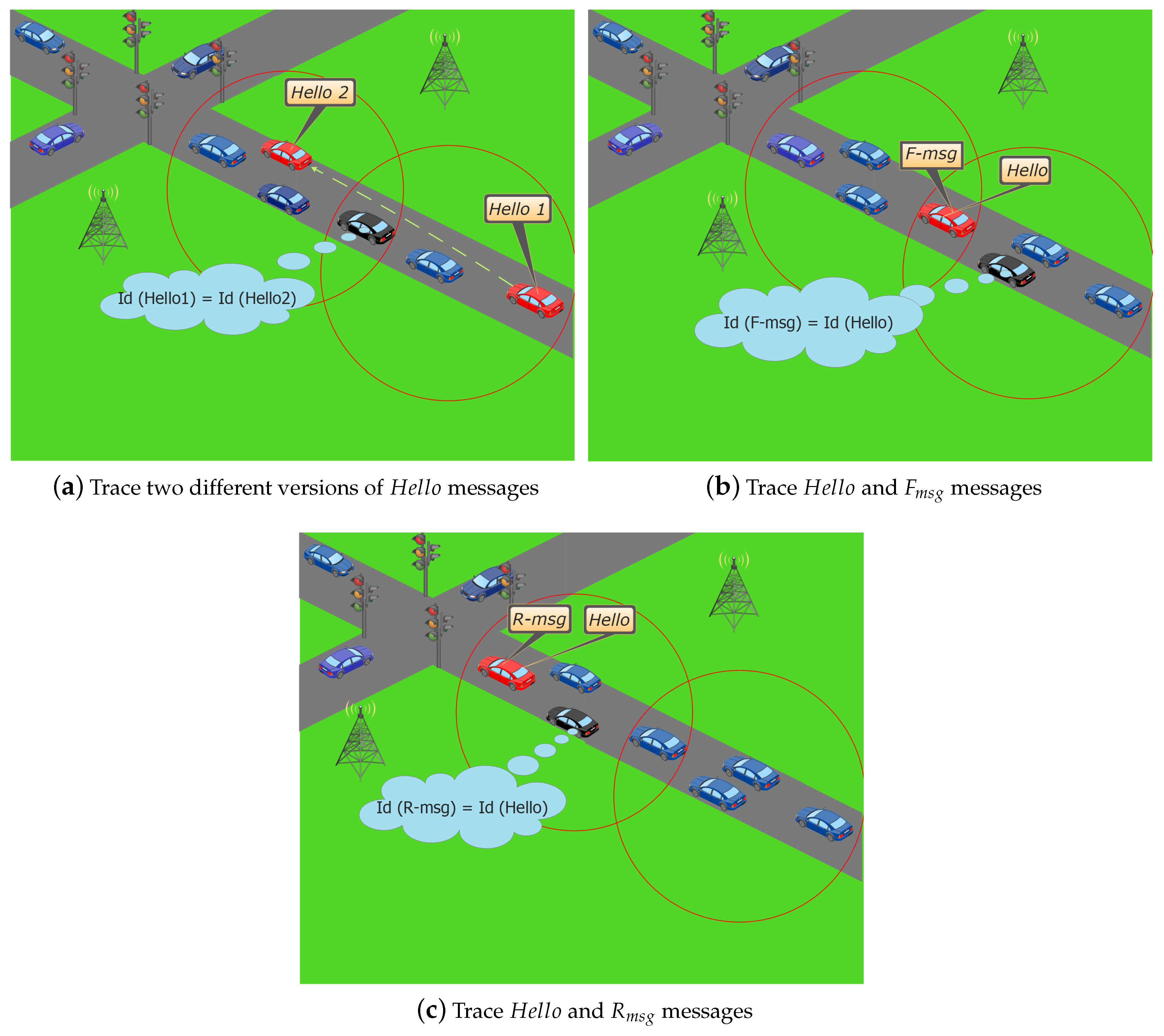
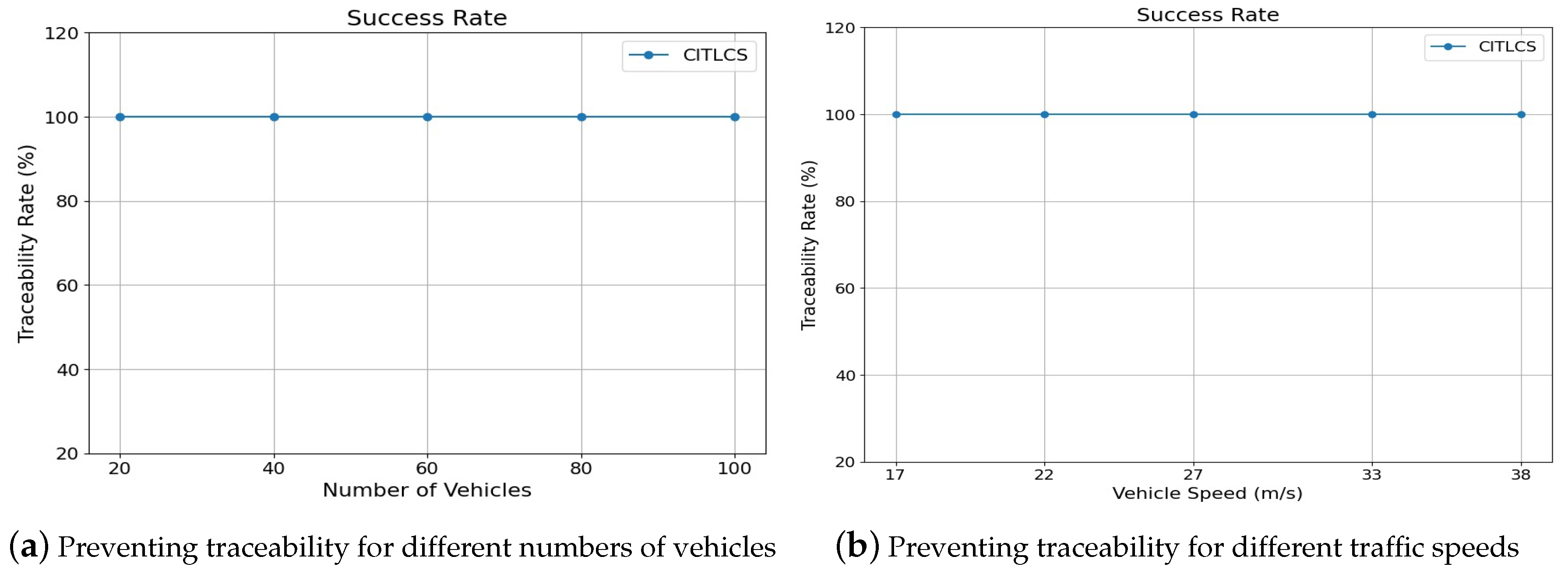
6.1. Preventing Traceability Attacks
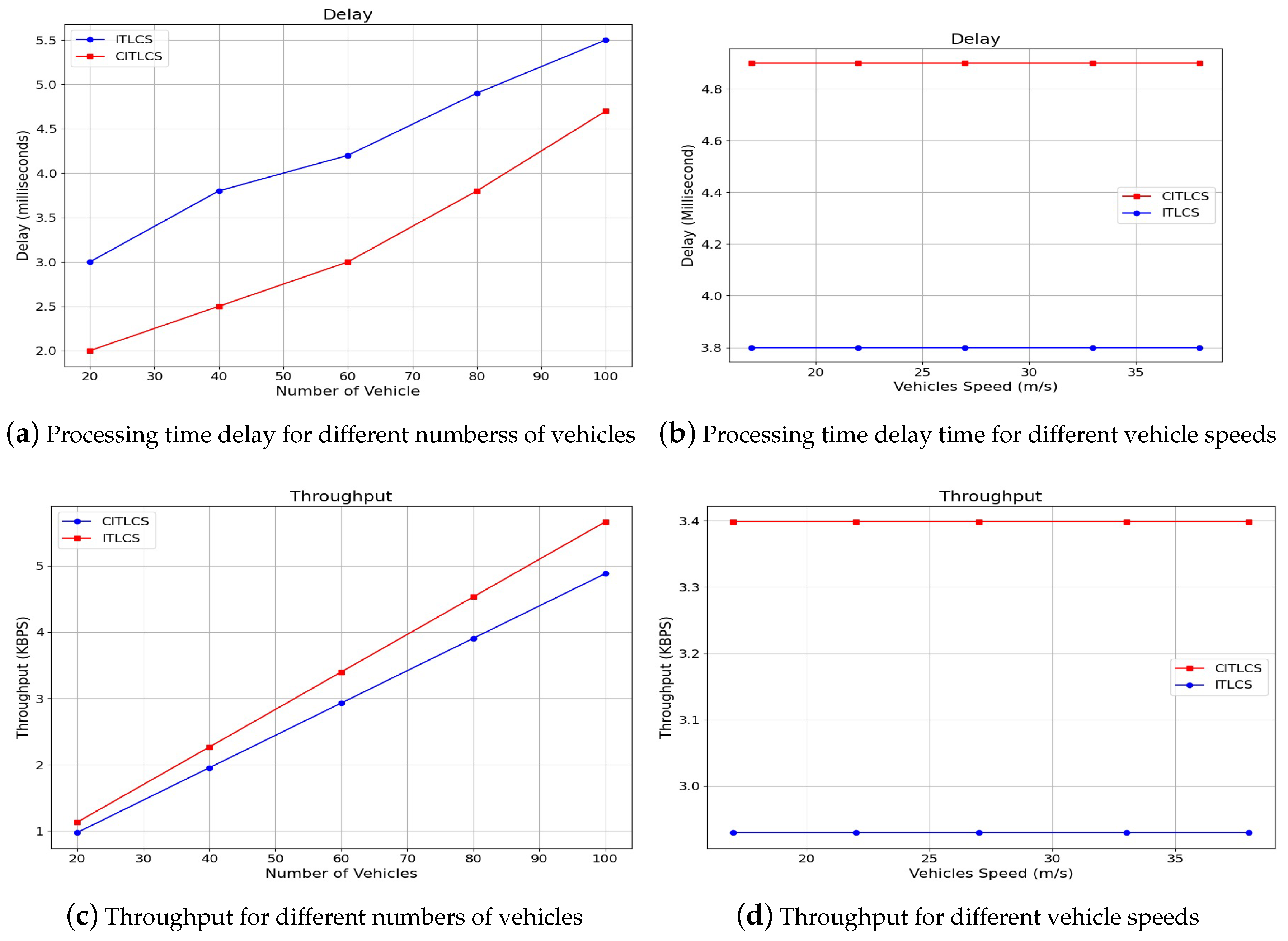
6.2. Efficiency of CITLCS
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Song, K.; Ni, T.; Song, L.; Xu, W. Emma: An accurate, efficient, and multi-modality strategy for autonomous vehicle angle prediction. Intell. Converg. Netw. 2023, 4, 41–49. [Google Scholar] [CrossRef]
- Hu, S.; Tao, Y.; Xu, G.; Deng, Y.; Chen, X.; Fang, Y.; Kwong, S. Cp-guard: Malicious agent detection and defense in collaborative bird’s eye view perception. In Proceedings of the AAAI Conference on Artificial Intelligence, Philadelphia, PA, USA, 25 February–4 March 2025; Volume 39, pp. 23203–23211. [Google Scholar]
- Qiao, J.; Zhang, D.; de Jonge, D. Priority-based traffic management protocols for autonomous vehicles on road networks. In Proceedings of the AI 2021: Advances in Artificial Intelligence: 34th Australasian Joint Conference, Sydney, NSW, Australia, 2–4 February 2022; Springer International Publishing: Cham, Switzerland, 2022; pp. 240–253. [Google Scholar]
- Gaouar, N.; Lehsaini, M.; Nebbou, T. CCITL: A cloud-based smart traffic management protocol using intelligent traffic light system in VANETs. Concurr. Comput. Pract. Exp. 2023, 35, e7686. [Google Scholar] [CrossRef]
- Li, Z.; Yu, H.; Zhang, G.; Dong, S.; Xu, C.Z. Network-wide traffic signal control optimization using a multi-agent deep reinforcement learning. Transp. Res. Part Emerg. Technol. 2021, 125, 103059. [Google Scholar] [CrossRef]
- Younes, M.B.; Boukerche, A. A performance evaluation of a context-aware path recommendation protocol for vehicular ad-hoc networks. In Proceedings of the 2013 IEEE Global Communications Conference (GLOBECOM), Atlanta, GA, USA, 9–13 December 2013; IEEE: Piscataway, NJ, USA, 2013; pp. 516–521. [Google Scholar]
- Rapelli, M.; Casetti, C.; Sgarbi, M. A Distributed V2V-Based Virtual Traffic Light System. In Proceedings of the 2020 International Conference on COMmunication Systems and NETworkS (COMSNETS), Bangalore, India, 7–11 January 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 122–128. [Google Scholar]
- Eom, M.; Kim, B.I. The traffic signal control problem for intersections: A review. Eur. Transp. Res. Rev. 2020, 12, 50. [Google Scholar] [CrossRef]
- Cao, M.; Li, V.O.; Shuai, Q. Gain with no pain: Exploring intelligent traffic signal control for emergency vehicles. IEEE Trans. Intell. Transp. Syst. 2022, 23, 17899–17909. [Google Scholar] [CrossRef]
- Pinto, A.C.; Mattioli, G.V. Intelligent Traffic Lights Control System Using Fuzzy Logic (No. 2014-36-0359); SAE Technical Paper; SAE International: Warrendale, PA, USA, 2014. [Google Scholar]
- Hossan, S.; Nower, N. Fog-based dynamic traffic light control system for improving public transport. Public Transp. 2020, 12, 431–454. [Google Scholar] [CrossRef]
- Ximenes, D.S.; Simões, T.; Silva, A.C.d.; Martino, G.P.d.; Emiliano, W.M.; Menzori, M.; Meyer, Y.A.; Júnior, V.E.M. Vehicular Traffic Flow Detection and Monitoring for Implementation of Smart Traffic Light: A Case Study for Road Intersection in Limeira, Brazil. Future Transp. 2024, 4, 1388–1401. [Google Scholar] [CrossRef]
- Younes, M.B.; Boukerche, A.; Mammeri, A. Context-aware traffic light self-scheduling algorithm for intelligent transportation systems. In Proceedings of the 2016 IEEE Wireless Communications and Networking Conference, Doha, Qatar, 3–6 April 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 1–6. [Google Scholar]
- Sachan, A.; Kumar, N. Intelligent Traffic Control System for Emergency Vehicles. In IoT and Analytics for Sensor Networks: Proceedings of ICWSNUCA 2021; Springer: Singapore, 2022; pp. 151–160. [Google Scholar]
- Younes, M.B.; Boukerche, A. Intelligent traffic light controlling algorithms using vehicular networks. IEEE Trans. Veh. Technol. 2015, 65, 5887–5899. [Google Scholar] [CrossRef]
- Khalid, T.; Khan, A.N.; Ali, M.; Adeel, A.; ur Rehman Khan, A.; Shuja, J. A fog-based security framework for intelligent traffic light control system. Multimed. Tools Appl. 2019, 78, 24595–24615. [Google Scholar] [CrossRef]
- Liu, J.; Li, J.; Zhang, L.; Dai, F.; Zhang, Y.; Meng, X.; Shen, J. Secure intelligent traffic light control using fog computing. Future Gener. Comput. Syst. 2018, 78, 817–824. [Google Scholar] [CrossRef]
- Elsagheer Mohamed, S.A.; AlShalfan, K.A. Intelligent traffic management system based on the internet of vehicles (IoV). J. Adv. Transp. 2021, 2021, 1–23. [Google Scholar] [CrossRef]
- Habib, M.A.; Ahmad, M.; Jabbar, S.; Khalid, S.; Chaudhry, J.; Saleem, K.; Khalil, M.S. Security and privacy based access control model for internet of connected vehicles. Future Gener. Comput. Syst. 2019, 97, 687–696. [Google Scholar] [CrossRef]
- Younes, M.B.; Boukerche, A. SCOOL: A secure traffic congestion control protocol for VANETs. In Proceedings of the 2015 IEEE Wireless Communications and Networking Conference (WCNC), New Orleans, LA, USA, 9–12 March 2015; pp. 1960–1965. [Google Scholar]
- Younes, M.B.; Alonso, G.R.; Boukerche, A. A distributed infrastructure-based congestion avoidance protocol for vehicular ad hoc networks. In Proceedings of the 2012 IEEE Global Communications Conference (GLOBECOM), Anaheim, CA, USA, 3–7 December 2012; IEEE: Piscataway, NJ, USA, 2012; pp. 73–78. [Google Scholar]
- Alharbi, A.; Halikias, G.; Sen, A.A.A.; Yamin, M. A framework for dynamic smart traffic light management system. Int. J. Inf. Technol. 2021, 13, 1769–1776. [Google Scholar] [CrossRef]
- Gupta, S.; Zhang, Y.; Su, R. Urban traffic light scheduling for pedestrian–vehicle mixed-flow networks using discrete sine–cosine algorithm and its variants. Appl. Soft Comput. 2022, 120, 108656. [Google Scholar] [CrossRef]
- Sun, G.; Qi, R.; Liu, Y.; Xu, F. A dynamic traffic signal scheduling system based on improved greedy algorithm. PLoS ONE 2024, 19, E0298417. [Google Scholar] [CrossRef]
- Aleko, D.R.; Djahel, S. An efficient adaptive traffic light control system for urban road traffic congestion reduction in smart cities. Information 2020, 11, 119. [Google Scholar] [CrossRef]
- Jin, Q. Automatic Control of Traffic Lights at Multiple Intersections Based on Artificial Intelligence and ABST Light. IEEE Access 2024, 12, 103004–103017. [Google Scholar] [CrossRef]
- Wided, A.; Assia, B.; Fatima, B. Traffic Management system and Traffic Light Control in Smart City to Reduce Traffic Congestion. Int. J. Autom. Amart Technol. 2023, 13, 2464. [Google Scholar] [CrossRef]
- Sihwail, R.; Ibrahim, D. A New Image Encryption Method Using an Optimized Smart Codebook. Hum. Behav. Emerg. Technol. 2025, 2025, 7807003. [Google Scholar] [CrossRef]
- Ibrahim, D.; Sihwail, R.; Arrifin, K.A.Z.; Abuthawabeh, A.; Mizher, M. A novel color visual cryptography approach based on Harris Hawks Optimization Algorithm. Symmetry 2023, 15, 1305. [Google Scholar] [CrossRef]
- Mizher, M.A.A.J.A.; Sulaiman, R.; Abdalla, A.M.A.; Mizher, M.A.A. A simple flexible cryptosystem for meshed 3D objects and images. J. King Saud-Univ.-Comput. Inf. Sci. 2021, 33, 629–646. [Google Scholar] [CrossRef]
- Mizher, M.A.; Sihwail, R.; Baker, M.B.; Mazhar, A.A.; Mizher, M.A.; Ibrahim, D. A review of cybersecurity for internet-of-things based on next generation healthcare networks. AIP Conf. Proc. 2023, 2979, 070004. [Google Scholar]
- Said, S.O.; Sihwail, R.; Shehadeh, H.; Hashim, I.; Alieyan, K. Hybrid Newton–sperm swarm optimization algorithm for nonlinear systems. Mathematics 2023, 11, 1473. [Google Scholar] [CrossRef]
- Feng, Y.; Huang, S.; Chen, Q.A.; Liu, H.X.; Mao, Z.M. Vulnerability of traffic control system under cyberattacks with falsified data. Transp. Res. Rec. 2018, 2672, 1–11. [Google Scholar] [CrossRef]
- Chen, C.; Wei, H.; Xu, N.; Zheng, G.; Yang, M.; Xiong, Y.; Xu, K.; Li, Z. Toward a thousand lights: Decentralized deep reinforcement learning for large-scale traffic signal control. In Proceedings of the AAAI Conference on Artificial Intelligence, New York, NY, USA, 7–12 February 2020; Volume 34, pp. 3414–3421. [Google Scholar]
- Kumar, N.; Rahman, S.S.; Dhakad, N. Fuzzy inference enabled deep reinforcement learning-based traffic light control for intelligent transportation system. IEEE Trans. Intell. Transp. Syst. 2020, 22, 4919–4928. [Google Scholar] [CrossRef]
- Zheng, G.; Xiong, Y.; Zang, X.; Feng, J.; Wei, H.; Zhang, H.; Li, Z. Learning phase competition for traffic signal control. In Proceedings of the 28th ACM International Conference on Information and Knowledge Management, Beijing, China, 3–7 November 2019; pp. 1963–1972. [Google Scholar]
- Liang, X.; Du, X.; Wang, G.; Han, Z. A deep reinforcement learning network for traffic light cycle control. IEEE Trans. Veh. Technol. 2019, 68, 1243–1253. [Google Scholar] [CrossRef]
- Shinde, S.M. Adaptive traffic light control system. In Proceedings of the 2017 1st International Conference on Intelligent Systems and Information Management (ICISIM), Aurangabad, India, 5–6 October 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 300–306. [Google Scholar]
- Wang, Y.; Yang, X.; Liang, H.; Liu, Y. A review of the self-adaptive traffic signal control system based on future traffic environment. J. Adv. Transp. 2018, 2018. [Google Scholar] [CrossRef]
- Yousef, K.M.; Al-Karaki, M.N.; Shatnawi, A.M. Intelligent traffic light flow control system using wireless sensors networks. J. Inf. Sci. Eng. 2010, 26, 753–768. [Google Scholar]
- Rezgui, J.; Barri, M.; Gayta, R. Smart traffic light scheduling algorithms. In Proceedings of the 2019 International Conference on Smart Applications, Communications and Networking (SmartNets), Sharm El Sheik, Egypt, 17–19 December 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–7. [Google Scholar]
- Liu, C.; Ke, L. Cloud assisted Internet of things intelligent transportation system and the traffic control system in the smart city. J. Control Decis. 2023, 10, 174–187. [Google Scholar] [CrossRef]
- Yuan, S.; Li, H.; Han, X.; Xu, G.; Jiang, W.; Ni, T.; Zhao, Q.; Fang, Y. ITPatch: An Invisible and Triggered Physical Adversarial Patch against Traffic Sign Recognition. arXiv 2024, arXiv:2409.12394. [Google Scholar]
- Yuan, S.; Xu, G.; Li, H.; Zhang, R.; Qian, X.; Jiang, W.; Cao, H.; Zhao, Q. FIGhost: Fluorescent Ink-based Stealthy and Flexible Backdoor Attacks on Physical Traffic Sign Recognition. arXiv 2025, arXiv:2505.12045. [Google Scholar]
- Alqarqaz, M.; Younes, M.B.; Qaddoura, R. An object classification approach for autonomous vehicles using machine learning techniques. World Electr. Veh. J. 2023, 14, 41. [Google Scholar] [CrossRef]
- Arshad, H.; Johansen, C.; Owe, O.; Picazo-Sanchez, P.; Schneider, G. Semantic Attribute-Based Encryption: A framework for combining ABE schemes with semantic technologies. Inf. Sci. 2022, 616, 558–576. [Google Scholar] [CrossRef]
- Aldolimi, W.S.; Hnaif, A.A.; Alia, M.A. Light fidelity to transfer secure data using advanced encryption standard algorithm. In Proceedings of the 2021 International Conference on Information Technology (ICIT), Amman, Jordan, 14–15 July 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 963–967. [Google Scholar]
- Rehmani, M.H.; Saleem, Y. Network simulator NS-2. In Encyclopedia of Information Science and Technology, 3rd ed.; IGI Global: Hershey, PA, USA, 2015; pp. 6249–6258. [Google Scholar]
- Nawej, C.; Owolawi, P.; Walingo, T. Design and simulation of vanets testbed using openstreetmap, sumo, and ns-2. In Proceedings of the 2021 IEEE 6th International Conference on Computer and Communication Systems (ICCCS), Chengdu, China, 23–26 April 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 582–587. [Google Scholar]
- Kusari, A.; Li, P.; Yang, H.; Punshi, N.; Rasulis, M.; Bogard, S.; LeBlanc, D.J. Enhancing SUMO simulator for simulation based testing and validation of autonomous vehicles. In Proceedings of the 2022 IEEE Intelligent Vehicles Symposium (IV), Aachen, Germany, 4–9 June 2023; IEEE: Piscataway, NJ, USA, 2023; pp. 829–835. [Google Scholar]

| Control Mechanism | Traffic Characteristics Gathering | Technology Used | Main Considerations | Handled Road Scenario | Considered Security Threat |
|---|---|---|---|---|---|
| ITLC [6] | Traffic speed, density, estimated traveling time, and the number of vehicles within the ready area for each traffic flow | Vehicular Ad Hoc Network (VANET) | Waiting delay time and throughput | Isolated road intersection | None |
| STL [22] | Level of Traffic Congestion | Images taken by long range digital camera | Waiting delay time and throughput | Isolated road intersection | None |
| Pedestrian–Vehicle [23] | Pedestrians’ needs and vehicle drivers’ needs | Vehicular Ad Hoc Network (VANET) | Total network-wise delay times of vehicles and pedestrians within a given finite-time window | Isolated road intersection | None |
| DTLS [13] | Traffic speed, density, estimated traveling time, and emergency vehicles existence | Vehicular Ad Hoc Network (VANET) | Traffic density and emergency vehicles | Isolated road intersection | None |
| Greedy [24] | Traffic speed, density, estimated traveling time, and emergency vehicles existence | Vehicular Ad Hoc Network (VANET), dataset for greedy algorithm | Traffic density and emergency vehicles | Isolated road intersection | None |
| ATL [6] | Traffic speed, density, estimated traveling time, and the number of vehicles within the ready area for each traffic flow. | Vehicular Ad Hoc Network (VANET) | Waiting delay time, throughput, and arrival platoons from neighboring intersections. | Open network or arterial street | None |
| ATLCS [25] | The presence of vehicles passing over the sensors | Vehicular Ad Hoc Network (VANET) and magnetometer sensors | Travel time is the number of occurrences of the “stop and go”. | Downtown-area open-network or arterial street | None |
| AI Models [26] | Number of incoming and outgoing vehicles | Reinforcement learning and Markov decision, deep Q-learning networks, multi-head attention mechanisms, and graph convolutional networks | Average waiting time, fuel consumption, and throughput. | Open road network | None |
| EDTLCM [11] | Number of incoming and outgoing vehicles there | Fog computing and wireless sensors | Average waiting time, fuel consumption, and throughput. | Closed road network | None |
| Grid Optimizer [11] | Flow through the downtown grid | Optimization algorithms | Vehicle movement on the road network. | Closed road network | None |
| Secure Mechanism | Technology Used | Security Tool | Handled Attacks |
|---|---|---|---|
| FSF-ITLCS, Khalid, T. [16] | Fog computing | Utilizes symmetric, asymmetric cryptography, hash function, and digital signature to ensure confidentiality, integrity, and credibility. | Replay attacks, denial of service, Sybil, and impersonation attacks. |
| STLMS, Liu, J. [17] | Fog computing | Computational Diffie–Hellman (CDH) puzzle. | Denial of service |
| ITMS, Els, M. [18] | Internet of Vehicles (IoV) and VANETs | Digital certificates, security and anti-tampering units and a set of anonymous certificates | Privacy and tampering attacks |
| SPBAC, Habib, M. [19] | Internet of Connected Vehicles (IoCV) | A Security and Privacy-Based Access Control (SPBAC) model for the Internet of Connected Vehicles. | Unauthorized access and data theft. |
| VTCS, Feng, Y. [33] | Use advanced data analysis methods | Implement a comprehensive security framework | A cyberattack with falsified data |
| Parameter | Value |
|---|---|
| MAC type | IEEE802.11P |
| Transmission range (m) | 200 |
| Vehicle’s speed (m/s) | 17, 22, 27, 33, 38 |
| Simulation area (m2) | 1000 m × 1000 m |
| Number of vehicles | 20, 40, 60, 80, 100 |
| Simulation time | 10,000 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Audat, A.; Younes, M.B.; Yahia, M.; Ghoul, S. Confidential Intelligent Traffic Light Control System: Prevention of Unauthorized Traceability. Big Data Cogn. Comput. 2025, 9, 169. https://doi.org/10.3390/bdcc9070169
Audat A, Younes MB, Yahia M, Ghoul S. Confidential Intelligent Traffic Light Control System: Prevention of Unauthorized Traceability. Big Data and Cognitive Computing. 2025; 9(7):169. https://doi.org/10.3390/bdcc9070169
Chicago/Turabian StyleAudat, Ahmad, Maram Bani Younes, Marah Yahia, and Said Ghoul. 2025. "Confidential Intelligent Traffic Light Control System: Prevention of Unauthorized Traceability" Big Data and Cognitive Computing 9, no. 7: 169. https://doi.org/10.3390/bdcc9070169
APA StyleAudat, A., Younes, M. B., Yahia, M., & Ghoul, S. (2025). Confidential Intelligent Traffic Light Control System: Prevention of Unauthorized Traceability. Big Data and Cognitive Computing, 9(7), 169. https://doi.org/10.3390/bdcc9070169








