Proposal of a Service Model for Blockchain-Based Security Tokens
Abstract
1. Introduction
2. Related Studies
2.1. Problem with Investment in Assets
2.2. Other Approaches for Asset Tokenization including Security Tokens
3. A Service Model for Blockchain-Based Security Tokens
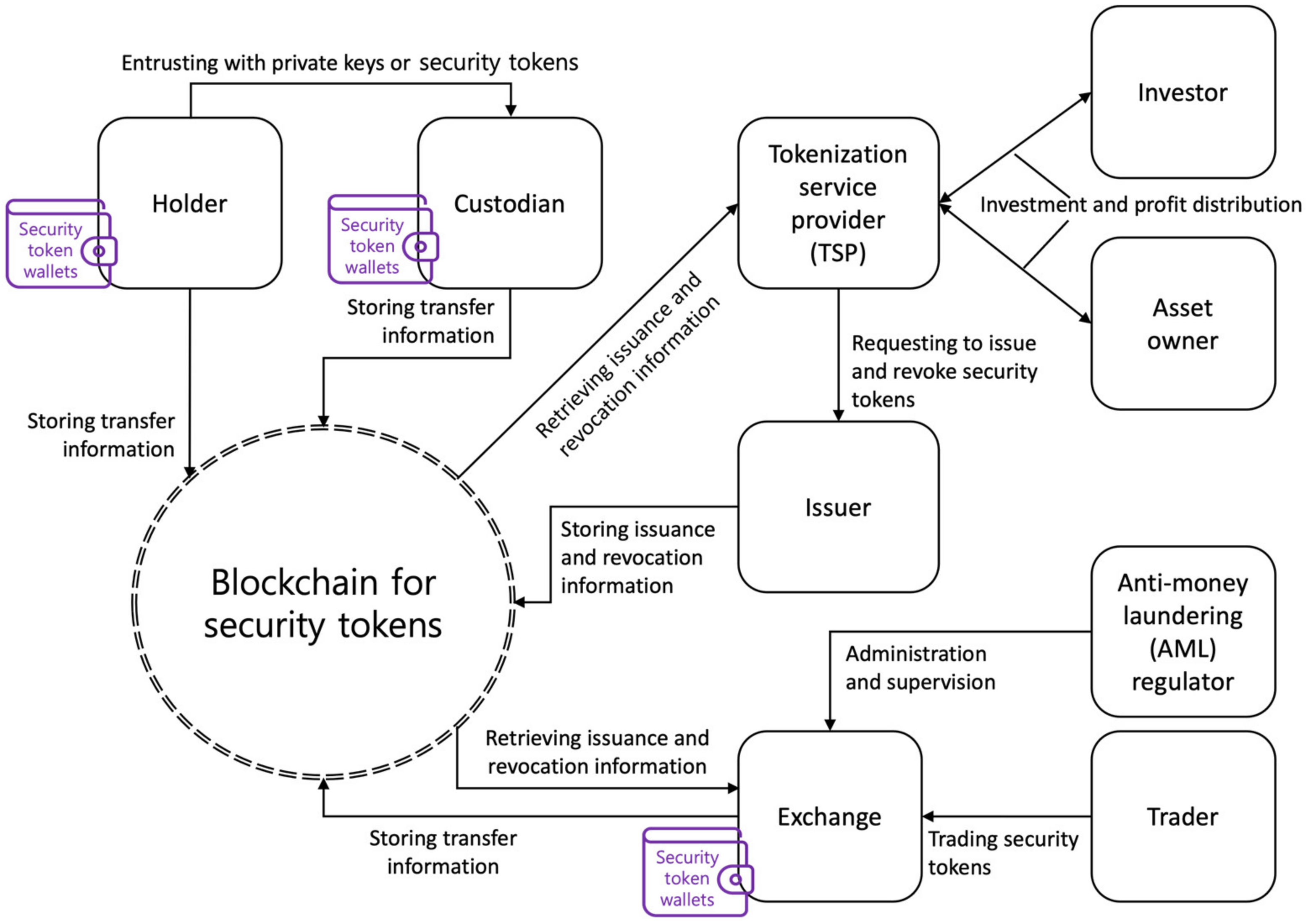
3.1. Service Model
- The holder with security token wallets is the owner of security tokens issued by issuers, bought from exchanges, or transferred from other entities. Holders transfer security tokens on the blockchain and entrust their private keys or security tokens to custodians.
- The custodian with security token wallets stores and maintains the holder’s private keys, which are used to transfer the holder’s security tokens. If the holder is a legal person, a child, an elderly person, or a digitally disabled person, the custodian transfers the holder’s security tokens on the blockchain on behalf of the holder. The custodian stores and maintains the security tokens received from the holders.
- The tokenization service provider (TSP) registers tangible assets (e.g., real estate, art, agricultural products, fishery products, livestock products, etc.) or intangible assets (e.g., music, movies, copyrights, intellectual property rights, etc.) and provides tokenized assets for investment. The TSP requests the issuer to issue and revoke security tokens and retrieves the issuance and revocation information of the security tokens from the blockchain.
- The asset owner registers his/her tangible and intangible assets with the TSP and receives payment from the TSP for investments in the registered assets. The asset owner provides the price for the registered asset to the TSP.
- The investor pays the TSP for investments in tokenized assets and receives the profit from the asset management of the TSP.
- The issuer issues and revokes security tokens in accordance with the request of the TSP. The issuers store issuance and revocation information for the security tokens on the blockchain.
- The anti-money laundering (AML) regulator administers and supervises exchanges to prevent money laundering involving security tokens.
- The blockchain stores and maintains information on the issuance, transfer, and revocation of security tokens. Since the proposed service model does not require the mining of security tokens, the type of blockchain can either be private or permissioned. The consensus algorithm can be either Proof of Stake (PoS) or Delegated Proof of Stake (DPoS). TSPs, issuers, exchanges, and AML regulators can participate as nodes on the blockchain.
3.2. Service Scenarios and Data Flows
- The asset owner registers his/her assets with the tokenization service provider (TSP). The asset owner provides the TSP with minimally required data, such as the identity information of the asset owner, the identifier of the asset, and the price of the asset (AP). The TSP tokenizes the registered asset at the price of a security token (SP). If the AP is $100,000 and the SP is $100, the asset will be tokenized into 1000 security tokens.
- The investor invests in the tokenized assets on the TSP. The investor provides the TSP with minimally required data, such as the identity of an investor, the identifier of an asset, and the amount of the security token. If the AP is $100,000 and the asset is tokenized into 1000 security tokens, the investor can even invest in the tokenized asset by purchasing one security token worth $100.
- The TSP requests the issuer to issue security tokens. The TSP provides the issuer with minimally required data, such as the identifier of an asset, the price of a security token, the issue date of security tokens, the expiry date of security tokens, and the amount of security tokens to be issued.
- The issuer stores the transaction to issue security tokens on the blockchain. The transaction contains minimally required data, such as the identifier of a security token, the identifier of an asset, the price of a security token, the name of an issuer, the issue date of security tokens, the expiry date of security tokens, and the amount of security tokens to be issued.
- The issuer issues and distributes the security tokens to investors in proportion to the investment.
- The TSP verifies, through the blockchain, whether the amount of issued security tokens and the amount of security tokens requested for issuance are the same. The TSP retrieves the ledgers on the blockchain containing the issuance information for the security tokens.
- The TSP pays the investment to the asset owner, and the investor owns the asset in proportion to the investment.
- If profits are made from the TSP’s asset management, the TSP distributes the profits to the investor in proportion to the amount of security tokens held.
- Once asset management is fulfilled, the TSP requests the issuer to revoke security tokens. The TSP provides the issuer with minimally required data, such as the identifier of a security token, the identifier of an asset, the price of a security token, the name of an issuer, the issue date of security tokens, the expiry date of security tokens, and the amount of security tokens to be revoked.
- The issuer stores the transaction to revoke security tokens on the blockchain. The transaction contains minimally required data, such as the identifier of a security token, the identifier of an asset, the price of a security token, the name of an issuer, the issue date of security tokens, the expiry date of security tokens, and the amount of security tokens to be revoked.
- The TSP verifies, through the blockchain, whether the amount of revoked security tokens and the amount of security tokens requested for revocation are the same. The TSP retrieves the ledgers on the blockchain containing the revocation information for the security tokens.
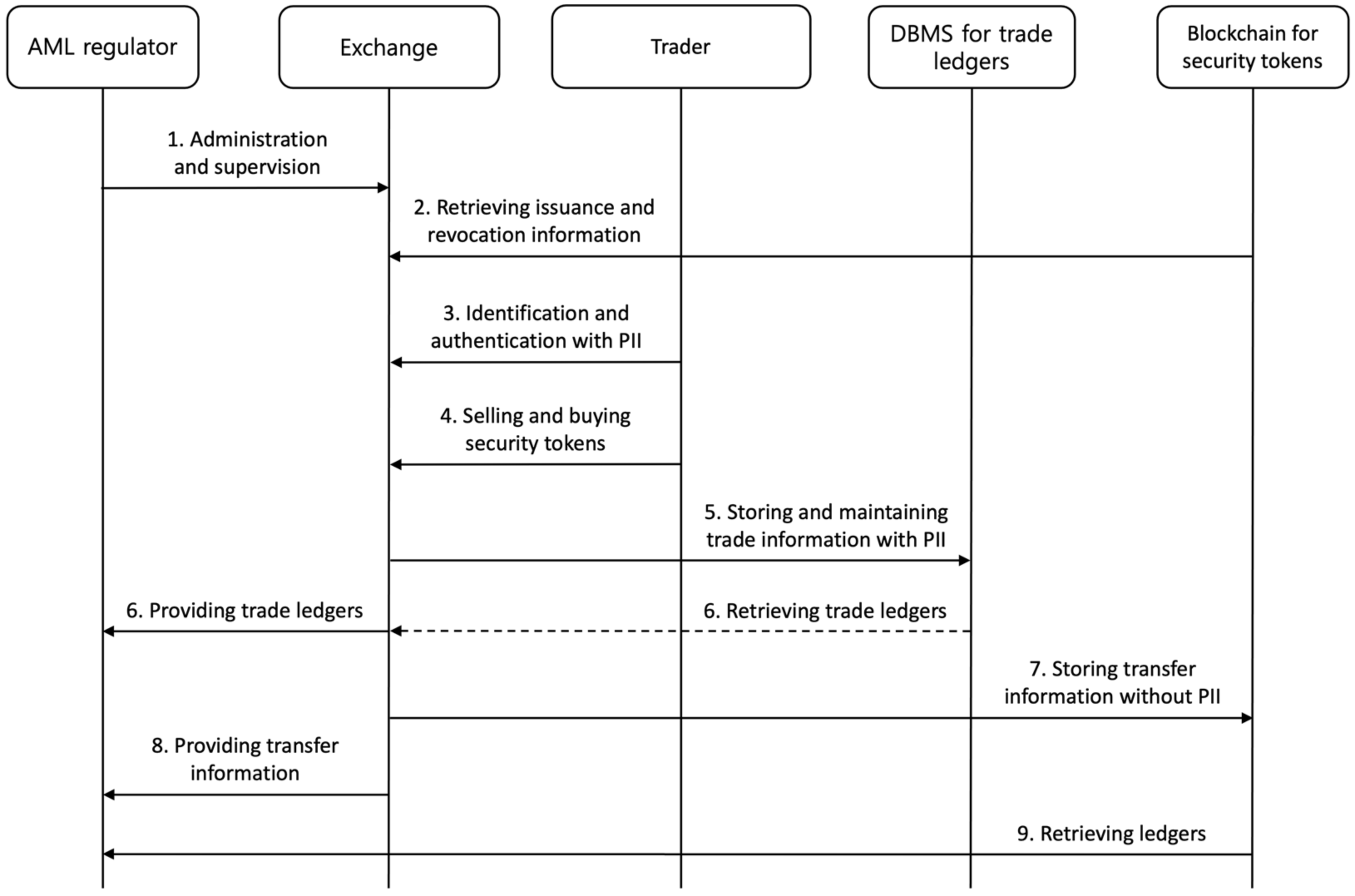
- The AML regulator administers and supervises the exchange to prevent money laundering involving security tokens. The regulator enforces the exchange with the policy for anti-money laundering (AML), and the exchange complies with the policy.
- The exchange retrieves the issuance and revocation information for security tokens on the blockchain. Issued security tokens can be listed on the exchange, and revoked security tokens must be delisted from the exchange.
- The trader is identified and authenticated by the exchange. The trader provides the exchange with his/her identity information, and the exchange provides the trader with the wallet addresses for transferring security tokens.
- The trader buys and sells security tokens on the exchange. The exchange provides the trader with trading between security tokens and fiat currencies, including CBDCs, between security tokens and cryptocurrencies (e.g., Bitcoin, Ether, etc.), and between security tokens.
- The exchange stores and maintains the ledgers containing trade information for security tokens using a database management system (DBMS). The exchange provides the DBMS with minimally required data, such as the date of trade, the identifier of a security token, the identifier of a seller, the identifier of a buyer, and the amount of traded security tokens.
- The exchange provides the AML regulator with trade ledgers retrieved from the DBMS in accordance with AML policy. The trade ledger includes minimally required data, such as the date of trade, the identifier of a security token, the identifier of a seller, the identifier of a buyer, and the amount of traded security tokens.
- The exchange stores transfer information for security tokens on the blockchain. The transfer information includes minimally required data, such as the date of transfer, the identifier of a security token, an originator’s wallet address, a beneficiary’s wallet address, and the amount of transferred security tokens.
- The exchange provides transfer information for the security tokens. The transfer information includes minimally required data, such as the date of transfer, the identifier of a security token, the identifier of an originator, an originator’s wallet address, the identifier of a beneficiary, a beneficiary’s wallet address, and the amount of transferred security tokens.
- The AML regulator retrieves the transfer ledgers for security tokens from the blockchain. The transfer ledger includes minimally required data, such as the date of transfer, the identifier of a security token, an originator’s wallet address, a beneficiary’s wallet address, and the amount of transferred security tokens. The AML regulator verifies whether the transfer information provided by the exchange and the transfer information retrieved from the blockchain are the same.
4. Security Threats and Requirements
4.1. Security Threats
- (ST-1) Deception involving the amount of issued security tokens: An issuer can falsify the amount of issued security tokens. The issuer can issue security tokens for more or less than the investment. This threat can cause money laundering involving security tokens and the embezzlement of investments.
- (ST-2) Deception involving the amount of revoked security tokens: An issuer can falsify the amount of revoked security tokens. The issuer can revoke security tokens for less than the amount of issued security tokens. This threat can cause money laundering involving security tokens.
- (ST-3) Unauthorized transfer of security tokens: A custodian can transfer security tokens without the holder’s permission. This threat can cause money laundering and embezzlement involving security tokens.
- (ST-4) Leakage of PII from a TSP: The massive PII of investors and asset owners can be leaked from a TSP that has stored and maintained the identity information of investors and asset owners. This threat can cause privacy issues related to investors and asset owners.
- (ST-5) Leakage of PII from an exchange: The massive PII of traders can be leaked from an exchange that has stored and maintained the identity information of traders and the trade ledger. This threat can cause privacy issues related to traders.
- (ST-6) Malicious behavior: An asset owner can falsify the price of his/her asset to be registered in a TSP. An asset owner can register other people’s assets in a TSP through identity theft. An employee or employer of a TSP can embezzle investments. This threat can cause financial issues related to the TSP.
4.2. Security Requirements
- (SR-1) Separation between an issuer and a TSP: The issuer of security tokens and the TSP should be two physically separate entities. The TSP should verify whether the amount of issued security tokens and the amount of security tokens requested to be issued are the same, as well as whether the amount of revoked security tokens and the amount of security tokens requested to be revoked are the same. This requirement can mitigate the ST-1 and ST-2 identified in Section 4.1.
- (SR-2) Separation between an issuer and an exchange: The issuer of security tokens and the exchange should be two physically separate entities. The exchange should verify whether the amount of issued security tokens and the amount of revoked security tokens are the same. This requirement can mitigate the ST-2 identified in Section 4.1.
- (SR-3) Wallet separation and audit logs: A custodian should create and maintain a security token wallet for each holder and allow each holder to transfer security tokens only through that wallet. The custodian should store and maintain the audit logs for the transfer of security tokens and inform the holders of the transfer history of security tokens in real time. The transfer information of security tokens should include the custodian’s digital signature for nonrepudiation. This requirement can mitigate the ST-3 identified in Section 4.1.
- (SR-4) Data encryption: A TSP should use secure encryption algorithms (e.g., AES-128 [18], SHA-256 [19], etc.) to encrypt the PII related to the identity information of investors and asset owners when storing the PII. An exchange should use secure encryption algorithms (e.g., AES-128, SHA-256, etc.) and secure cryptographic protocols (e.g., TLS [20,21]) to encrypt the PII related to the identity information and trade ledgers of traders when storing and transmitting the PII. This requirement can mitigate the ST-4 and ST-5 identified in Section 4.1.
- (SR-5) Decentralized identification: An investor and an asset owner should present their identity certificates to a TSP using decentralized identity (DID) [22,23]. A trader should present his/her identity certificate to an exchange using DID. DID allows a TSP and an exchange not to store and maintain the PII related to identity information of investors, asset owners, and traders. This requirement can mitigate the ST-4 and ST-5 identified in Section 4.1;
- (SR-6) Investment protection: A TSP should assess the assets to be registered by asset owners. The TSP should verify, through an assessment, whether the asset price provided by an asset owner is reasonable. The TSP can conduct the assessment via a trustworthy third party. A TSP should entrust financial companies (e.g., banks, securities companies, etc.) with investments. This requirement can mitigate the ST-6 identified in Section 4.1.
5. Discussion and Conclusions
- Separation between issuance and trade of security tokens: To prevent money laundering and market monopoly, it is necessary to strictly separate the issuer and exchange of security tokens. The issuer cannot provide a trading service for security tokens, and the exchange cannot issue security tokens. The issuers and exchanges, as stakeholders, can mutually monitor the amount of security tokens issued and transferred through the blockchain.
- Prohibition of excessive administration of security tokens: Since the amount of issued and revoked security tokens can be monitored through the blockchain (i.e., a decentralized distributed ledger system), if the regulator operates the nodes of the blockchain, it is unnecessary for the regulator to administer the amount of issued and revoked security tokens. The history of the issuance, distribution, usage, storage, and revocation of security tokens can be stored and maintained on the blockchain. Holders can entrust their security tokens to custodians. Financial companies (e.g., banks, etc.) can be custodians of security tokens.
- Prevention of monopoly in security token trading and expansion of the trading market: Rather than trading security tokens only on specific exchanges, through interoperability (e.g., sharing order books, etc.) between exchanges that list and do not list security tokens, trading between security tokens and fiat currencies, including CBDCs, between security tokens and cryptocurrencies (e.g., Bitcoin, Ether, etc.), and between security tokens must be allowed. The trade of security tokens must be allowed on cryptocurrency exchanges complying with AML regulations.
- There is no need for the restriction of assets to be tokenized. The increase in sales of TSPs, which tokenize tangible and intangible assets, is the most important element in the virtuous cycle structure that leads to the increased sales of issuers and exchanges due to the increased issuance and trading volume of security tokens. In addition to investing in already created assets (e.g., buildings, art, music, movies, etc.), there is no need to restrict the assets to be tokenized to make a profit by investing in creating assets. For example, this can include building construction and renovation, the production of agricultural, fishery, and livestock products, including processed products, and the creation of intellectual property (e.g., webtoons, music, movies, etc.).
- Feature of security token wallet: Private keys for security tokens must be securely stored and maintained where the Internet is not connected.
- Feature of security token revocation: Once asset management is fulfilled, the security tokens must be permanently revoked. The revoked security tokens must not be transferred.
- Feature of privacy preservation: The PII of users must be securely stored and maintained where the Internet is not connected, and must be securely transmitted even over the Internet.
- Feature of investment management: The entire amount of the investment must be separated into TSP’s funds and entrusted to financial companies, such as banks, securities companies, etc. The investment system must be assessed for compliance with requirements under AML laws.
- Feature of AML: AML systems involving security tokens must be assessed for compliance with requirements under AML laws.
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- tZERO. Democratizing Markets Through Innovation. Available online: https://www.tzero.com (accessed on 29 December 2023).
- Securitize. Accessed the Most Exclusive Asset Class in the World—Private Markets. Available online: https://securitize.io (accessed on 29 December 2023).
- INX. Trade & Invest in Digital Assets. Available online: https://www.inx.co (accessed on 29 December 2023).
- Security Token Market (STM). Security Tokens. Available online: https://stomarket.com (accessed on 29 December 2023).
- JSTA. A Non-Profit Organization That Consolidates the Knowledge of Security Tokens and Promotes the Sound Development of the Security Token Ecosystem. Available online: https://securitytoken.or.jp/en/ (accessed on 29 December 2023).
- CoinDesk. Tokenized RWAs Could Grow to a $10T Market by 2030 as Crypto Converges to TradFi: Report. Available online: https://www.coindesk.com/markets/2023/10/17/tokenized-rwas-could-grow-to-a-10t-market-by-2030-as-crypto-converges-to-tradfi-report/ (accessed on 29 December 2023).
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 30 December 2023).
- Ethereum. Ethereum White Paper. Available online: https://ethereum.org/en/whitepaper/ (accessed on 30 December 2023).
- GitHub. ERC 1400: Security Token Standard. Available online: https://github.com/ethereum/EIPs/issues/1411 (accessed on 27 December 2023).
- Dossa, A.; Moore, G.; Lancaster, J.; Buchanan, M.; Ruiz, P. Polymesh Whitepaper v1.2. Available online: https://assets.polymesh.network/Whitepaper.pdf (accessed on 28 December 2023).
- Arner, D.; Auer, R.; Frost, J. Stablecoins: Risks, Potential and Regulation. Available online: https://www.bis.org/publ/work905.pdf (accessed on 28 December 2023).
- Lebrun, J.; Falempin, L.; Thizy, K.; Malghem, T.; Aznal, X.; Bousselin, T.; Croiseaux, F. Whitepaper, ERC3643, The T-REX Protocol (Token for Regulated EXchanges), The Token Standard for Real-World Asset Tokenization. Available online: https://www.erc3643.org (accessed on 27 December 2023).
- Kreppmeier, J.; Laschinger, R.; Steininger, B.; Dorfleitner, G. Real Estate Security Token Offerings and the Secondary Market: Driven by Crypto Hype or Fundamentals? J. Bank. Financ. 2023, 154, 106940. [Google Scholar] [CrossRef]
- Lambert, T.; Liebau, D.; Roosenboom, P. Security token offerings. Small Bus. Econ. 2022, 59, 299–325. [Google Scholar] [CrossRef]
- Laurent, P.; Chollet, T.; Burke, M.; Seers, T. The Tokenization of Assets is Disrupting the Financial Industry. Are You Ready? Inside Magazine Issue 19 2019. Available online: https://www.wyoleg.gov/InterimCommittee/2019/S3-20190506TokenizationArticle.pdf (accessed on 28 December 2023).
- Li, X.; Wu, X.; Pei, X.; Yao, Z. Tokenization: Open Asset Protocol on Blockchain. In Proceedings of the 2019 IEEE 2nd International Conference on Information and Computer Technologies (ICICT), Kahului, HI, USA, 14–17 March 2019. [Google Scholar] [CrossRef]
- Benedetti, H.; Rodríguez-Garnica, G. Tokenized Assets and Securities. In The Emerald Handbook on Cryptoassets: Investment Opportunities and Challenges; Emerald Publishing Limited: Bingley, UK, 2023. [Google Scholar] [CrossRef]
- Dworkin, M. Advanced Encryption Standard (AES). Available online: https://www.nist.gov/publications/advanced-encryption-standard-aes-0 (accessed on 30 December 2023).
- Internet Engineering Task Force (IETF). US Secure Hash Algorithms (SHA and SHA-based HMAC and HKDF). Available online: https://datatracker.ietf.org/doc/html/rfc6234 (accessed on 30 December 2023).
- OpenSSL Software Foundation. Vulnerabilities. Available online: https://www.openssl.org/news/vulnerabilities.html (accessed on 30 December 2023).
- Internet Engineering Task Force (IETF). The Transport Layer Security (TLS) Protocol Version 1.3. Available online: https://datatracker.ietf.org/doc/html/rfc8446 (accessed on 30 December 2023).
- Sporny, M.; Longley, D.; Sabadello, M.; Reed, D.; Steele, O.; Allen, C. Decentralized Identifiers (DIDs) v1.0 Core Architecture, Data Model, and Representations. Available online: https://www.w3.org/TR/did-core/ (accessed on 31 December 2023).
- Sporny, M.; Longley, D.; Chadwick, D.; Steele, O. Verifiable Credentials Data Model v2.0. Available online: https://www.w3.org/TR/vc-data-model-2.0/ (accessed on 31 December 2023).




Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Park, K.; Youm, H.-Y. Proposal of a Service Model for Blockchain-Based Security Tokens. Big Data Cogn. Comput. 2024, 8, 30. https://doi.org/10.3390/bdcc8030030
Park K, Youm H-Y. Proposal of a Service Model for Blockchain-Based Security Tokens. Big Data and Cognitive Computing. 2024; 8(3):30. https://doi.org/10.3390/bdcc8030030
Chicago/Turabian StylePark, Keundug, and Heung-Youl Youm. 2024. "Proposal of a Service Model for Blockchain-Based Security Tokens" Big Data and Cognitive Computing 8, no. 3: 30. https://doi.org/10.3390/bdcc8030030
APA StylePark, K., & Youm, H.-Y. (2024). Proposal of a Service Model for Blockchain-Based Security Tokens. Big Data and Cognitive Computing, 8(3), 30. https://doi.org/10.3390/bdcc8030030








