Abstract
Fog technology is one of the recent improvements in cloud technology that is designed to reduce some of its drawbacks. Fog technology architecture is often widely distributed to minimize the time required for data processing and enable Internet of Things (IoT) innovations. The purpose of this paper is to evaluate the main factors that might influence the adoption of fog technology. This paper offers a combined framework that addresses fog technology adoption based on the technology adoption perspective, which has been comprehensively researched in the information systems discipline. The proposed integrated framework combines the technology acceptance model (TAM) and diffusion of innovation (DOI) theory to develop a holistic perspective on the adoption of fog technology. The factors that might affect the adoption of fog technology are analyzed from the results of an online survey in 43 different organizations across a wide range of industries. These factors are observed based on data collected from 216 participants, including professional IT staff and senior business executives. This analysis was conducted by using structural equation modeling (SEM). The research results identified nine factors with a statistically significant impact on the adoption of fog technology, and these factors included relative advantage, compatibility, awareness, cost-effectiveness, security, infrastructure, ease of use, usefulness, and location. The findings from this research offer insight to organizations looking to implement fog technology to enable IoT and tap into the digital transformation opportunities presented by this new digital economy.
1. Introduction
Information technology (IT) has been a mainstay of productivity enhancement and innovation for virtually all enterprises over the past few decades [1]. IT has also altered the way people communicate, primarily because of the evolution of smart devices [2]. As IT continues to be more widely utilized, its major impacts on both business and society have led to massive digital transformation opportunities [3]. The use of IT resources continues to grow exponentially during recent turbulent times [4], and the phenomena of digital transformation have only been exacerbated by the COVID-19 pandemic and economic disruptions across global industries. A major technology solution of recent IT innovations is cloud technology, which offers an elastic architecture to provide IT services with minimal effort [5]. An important aspect of cloud technology in relation to productivity enhancement for an enterprise is supporting organizations to optimize their use of IT resources for different business operations [6]. However, an analysis of a very large dataset shows limitations related to the use of cloud technology that may result in unexpected costs, lower availability, and longer task lengths for many business cases such as autonomous cars and smart devices [7].
Cloud technology faces several challenges, including limitations of network bandwidth, latency-sensitive applications, and increased demand for real-time applications [8,9,10,11]. While cloud technology has been successful in numerous technology innovations over the past few years, there is an opportunity to boost network connectivity [12], such as the rollout of 5G connectivity for more responsive processing at the device (edge) layer as computing and storage capacities of edge devices continue to improve. Cloud technology architecture shows limitations in terms of the delay of sensitive computing services between cloud servers and edge devices. For instance, when using cloud technology, long data processing time may be needed due to the lack of a data center; therefore, the service delivery can become inefficient [13,14]. In addition, vast amounts of data (also known as Big Data) are handled and processed by cloud technology storage. Consequently, due to the large amount of data, accessing and handling relevant information that should be analyzed is a challenge [15,16]. The trend toward data redundancy has been attributed to the large quantity of data that is ineffectively managed by cloud technology [17].
Fog technology has been presented as a new type of computing model to extend the architecture and application of cloud technology [18]. Fog technology is often widely dispersed to reduce the time required for processing data in a certain industry, which can take advantage of local processing, as it is situated at the edge of the Internet of Things (IoT) and artificial intelligence (AI) devices [18,19]. Due to these features, fog technology is also termed ‘edge computing’, although many scholars and practitioners have different interpretations of these two technologies. For simplicity and clarity, we will refer to ‘fog technology’ as a singular construct in this research that may be referred to as ‘fog computing’, ‘edge computing’, ‘fog networking’, or ‘fogging’ in other research and practice. The major rationale for this use of a consistent construct is to avoid concept proliferation and to stress that the main point of differentiation of fog technology is its decentralized architecture as compared to cloud computing. This distinction of fog computing over cloud computing is the primary driver to investigate this research that studies distinct adoption factors attributed to fog computing in contrast with many studies that look at adoption factors for cloud computing. Likewise, since the amount of data is continuously growing with the continued use of computing devices, the information produced requires comprehensive data processing at the point of data being collected (edge devices) to achieve strategic advantages in the industry [20]. Fog technology, as a modern computing architecture, has the potential to provide end users with networking based on the growing local computing resources at the device level [21].
Essentially, fog technology increases the heterogeneity of data from multiple formats as well as the heterogeneity of the utilized devices and platforms [22]. The analysis approach of transitional data must therefore be conducted on streaming data by comparing and processing various types of sources [5]. The consistency of the outcome must focus on the flow of data in fog technology. The quality of the outcome is more likely to depend on the established requirements of the industry before any technology adoption decisions are made [23]. Researchers have found that there is minimal study on the factors that might influence the adoption of fog technology [5,20,24]. This has led researchers to pose the following research question: What are the key factors that should be considered by organizations when intending to adopt fog technology? To answer this question, we propose integrating the diffusion of innovation (DOI) [25] and the technology acceptance model (TAM) [26,27], along with other important factors considered from the literature [23,28,29,30,31,32,33,34,35,36,37,38,39,40,41,42,43,44,45,46]. This convergence of two well-known theories and important factors identified in the literature is aimed at providing a clear picture to understand the critical factors that might influence decisions about investment in fog technology within different organizational contexts.
The main purpose of this research study is to make a significant contribution toward decision making for the adoption of fog technology. The major categories of factors, including innovative, operational, technical, economic, and situational considerations, that are relevant to investment strategies for fog technology adoption will be investigated. Survey data were collected from 216 IT staff and senior executives who work in 43 organizations in various industries to test the proposed framework.
This research outlines the primary adoption factors for fog technology that will be useful in understanding the trade-off between the security issues and the response time while implementing the fog technology. The overload issue of cloud technology can be reduced by fog technology, as it offloads many computing processes requiring minimal computations. Nevertheless, studies on the successful adoption of fog technology remain scarce. This study can be considered one of the first efforts to investigate the factors that may offer insight into the adoption of fog technology. As such, this study may support future studies in the subsequent adoption of other technologies (such as 5G and IoT) that depend on the fog technology architecture to look at digital transformation across industries more holistically.
This research contributes to supporting the adoption of fog technology that permits the delivery of innovative services for digital transformation across industries. In addition, this research contributes to the body of knowledge that advocates for considering fog technology as a technology architecture that complements cloud architecture for adoption by organizations rather than looking at specific edge devices or services.
The remaining parts of this research paper are organized as follows. Section 2 provides a background on fog technology and discusses the importance of fog technology for organizations. Section 3 presents the conceptual research framework. The research framework and hypotheses are presented in Section 4. The research methodology is explained in Section 5. All the research results are outlined in Section 6. The research contributions and limitations are discussed in Section 7. Section 8 concludes the paper.
2. Fog Technology
2.1. Fog Technology Background
In 2012, Cisco presented the concept of fog technology to differentiate its architecture and scope from the predominant cloud computing architecture based on the distributed and decentralized computing resources that are possible with emerging technologies such as smart sensors and 5G and build strong innovation capital with the advent of IoT and subsequently the overall digital transformation of organizations. In simpler terms, the analogy of ‘fog’ being ‘visible’ (pun intended) to the earth as compared to the remote ‘cloud’ is used to explain the differences between cloud computing where computing occurs at centralized cloud servers and fog technology where lightweight edge devices and services perform some levels of computing, storage, and processing activities at the local level closer to the device. Fog technology is designed to improve computing processes for resources that constrain IoT devices, as well as for the storage of data that are transmitted by these devices [47,48,49]. Fog technology has been defined as “an end-to-end horizontal architecture that distributes computing, storage, control, and networking functions closer to users along the cloud-to-thing continuum” [50].
Fog technology was presented to mitigate some of the issues of cloud computing such as the shortening of response times, mobility, location awareness of IoT applications, and the distributed nature of IoT devices [51,52]. Therefore, fog and edge computing are considered advancements in cloud services that bridge the gap between IoT devices and cloud servers, which can be useful in several business cases. Therefore, fog technology can extend the value of cloud services toward end users’ devices, where a fog node may conduct control, communication, and computation activities on behalf of or complementary to the cloud, and it may provide a storage facility close to end users, thus reducing the time of execution on cloud servers [10,53,54].
In general, fog architecture consists of three layers connected to public authorities as key generation centers and certificate authorities [53,55]. The first layer in this architecture is the device layer, which is the closest layer to end users, as it includes all mobile or static IoT devices such as smartphones, smart vehicles, and sensors [55]. The second layer, the mainstream fog layer, acts as the middleware layer among the device and cloud layers, yet it is located closer to the device layer. This layer contains a distributed number of fog nodes, such as cloudlets, that extend the cloud layer to provide services such as real-time data analysis, temporary storage, and data transmitting summaries of IoT devices [56]. These services reduce the processing load of IoT devices [56]. The last layer is the cloud layer, which is involved in the permanent storage of data and high-performance servers [53]. Many services are offered by this layer, such as remote and complex analysis and transportation and power distribution applications [8]. This layer also provides the fog with control policies and strategies that help to improve the quality offered by fog nodes such as latency-sensitive services [8].
Since ‘fogging’ can be viewed as a suitable technology for applications that require instant response and feedback, it may offer several benefits to latency-sensitive computer applications [51]. For instance, applications such as smart transportation, smart traffic signals, smart environments, wireless sensors and actuator networks (WSANs), brain machines, energy grids, disaster support applications, health systems, video streaming, and 5G mobile networks can gain several benefits from the utilization of fog technology [57]. Among these benefits are reducing latency, supporting cognition and mobility, enhancing agility, security, and efficiency, saving bandwidth, enabling low energy consumption, and decentralizing data analytics [23,53,58].
Despite being part of the entire cloud architecture stack, fog technology has its own unique environment due to its distributed nature, remote operations, and resource constraints [51]. This environment has created additional challenges related to the security and privacy of IoT applications. The current fog technology literature reports that the fog layer may decrease the privacy and security of IoT applications, yet some researchers conclude that fog can enhance IoT applications’ security and privacy in comparison to clouds [50,59,60,61]. From the fog technology literature, several security and privacy threats, such as forgery, tampering, and spam, have been identified, and varied research efforts have been proposed to address these threats by utilizing varied authentication and encryption techniques and procedures [62,63,64]. To summarize, fog and edge computing are designed to limit the latency between cloud data centers and end devices. Since all data centers are connected between user devices and cloud services, these networks are long, thin, and susceptible to network failures. On the other hand, fog technology supports a three-layer service model in fog technology, where the resource allocation is primarily performed by the fog node, whereas in edge computing, the resource allocation is performed by the edge node. There is a lack of a central entity controlling the fog layer; hence, it is difficult to assert whether a given device is indeed performing compute functions in the network. On the other hand, there are many open-ended issues in edge computing, where application deployment strategies, edge node security, and failure recovery are some of the adoption issues that need further research. As noted earlier, this research recognizes the technology differences between fog computing and edge computing. However, given that this research topic considers organizational adoption strategies on the decentralized nature of cloud services in sharp contrast with cloud computing, we will use “fog technology” throughout the remainder of this paper to refer to both fog and edge computing and their distinction from cloud computing.
2.2. Why Does Fog Technology Need to Be Embraced by Organizations?
The future outlook for adopting fog technology may be bleak as businesses are comfortable with cloud technology and they are satisfied with its capacity for fulfilling business applications. However, when we consider automation with machine-to-machine interactions and associated AI opportunities, fog technology offers immense potential for future adoption by organizations. At the current stage, organizations may recognize that cloud technology still has ample processing capacity, so it is doubtful that they will explore proposals to implement fog technology [65]; however, such a strategy may not be sustainable for forward-looking digital transformation initiatives. Moreover, in certain localized and remote areas, where cloud technology data centers are installed, they may fail to ensure proper service latency, energy usage, network costs, and bandwidth [66]. Therefore, the implementation of fog technology may be necessary to mitigate these challenges.
Fog technology can be viewed as a facilitator for many differential value-adding services due to its proximity and geographical coverage, accessibility, the bandwidth required, and the data processing needs created by various devices [67]. However, as mentioned, organizations from different sectors are still not taking advantage of the full benefits of the implementation of this technology. Research on this specific technology is in its infancy, so a thorough understanding of the organizational benefits of the adoption of fog technology is lacking [67]. Fog technology helps to provide relevant information to several industries, such as healthcare and manufacturing. For example, data are demanded by industries for local processing with sufficient security policies for responsive equipment alarms [68]. Fog systems serve a wide variety of industrial applications because of their capability of instantaneous responses [67]. Many previous studies have acknowledged the comprehensive nature of fog technology at the organizational level that accomplishes fair and effective resource utilization [69,70]. The decentralization of fog technology and its supporting architecture is recognized as a revolutionary mechanism that reduces the total latency [69,71]. However, the fog technology framework is likely to vary in implementation, as it relies on technical and nontechnical executions [68]. The limited bandwidth for processing and storing end-user devices is reliant on external processing. Fog technology has improved its potential to offer a better approach to data collection, storage, and hosting [72]. The resources of fog technology can be expanded on demand as the computation of end-user devices is transferred to the network [71,73].
In fog technology, vast volumes of data produced from IoT devices in distributed environments are effectively processed. The acquired data are further processed and analyzed by using fog nodes to meet the prerequisite for data integrity [19]. Therefore, it is necessary to place the fog nodes close to IoT devices to address the requirements for processing large amounts of data with minimal latency [28]. Fog technology is equipped with highly secured criteria for large-scale IoT implementations [74]. The properties of fog technology help maintain and upgrade fog security credentials and software to prevent constant disturbance to organizational processes and technical components [75]. In fog technology, security requirements are able to offer cost-effective solutions that boost performance in systems and display high failure tolerance [64,76]. Therefore, it is expected that fog technology will be further embraced by organizations as the value of the technology becomes more apparent to stakeholders.
Table 1 highlights the summary and limitations of existing literature related to investigating the adoption of fog technology within organizations.

Table 1.
Summary of the literature.
3. Background on the Research Conceptual Framework
The advent and functionality of information systems (ISs) have contributed to the acceleration of technology distribution in many countries to promote growth policies that further bridge the digital gap between organizations of various sectors [77,78]. However, Steinmueller [77] argues that it is not easy to understand the advantages of using technology transition techniques because of practical obstacles. Such obstacles may include local business constraints as well as technological adaptation to the local preferences, costs, and expertise needed to work effectively. Limited experience and knowledge in importing ISs often contribute to failed adoption and, hence, limit organizations to take advantage of technologies [29]. While innovation in information and communication technologies (ICT) put a large emphasis on socioeconomic contexts, the approach used for such innovation acceptance has major gaps [30]. The dissemination of creativity must be enabled by systemic commitment and encouragement for technologies to be implemented effectively.
While the adoption of advanced technologies helps to accelerate economic prosperity and community resilience [31], acceptance rates vary due to diverse social and cultural restrictions that are sometimes ignored during the dissemination period. The multidimensional character of the acceptance and dissemination of innovations suggests a gap in technology adoption patterns, not only because of economic and technical considerations but also sociocultural influences [32]. The dissemination and acceptance of technologies need to take into account the current cultural and social contexts for adopters, which, in turn, may affect the progress or failure of the technology adoption mechanism [79].
In many industries around the globe, companies have seen that the prevailing global economic crises have contributed to a decline in their expenditure budgets, which has driven many companies to pursue cost-saving initiatives in their market or business to stay competitive [33]. Fog technology and its scalable operating model have appeared as a viable solution for carrying out the cost-reduction steps demanded by organizations, without compromising performance and productivity [34]. Moreover, fog technology’s scalability and cost structures are more appealing to emerging organizations [28].
The acceptance and innovation diffusion of IT have been proposed by various theories. Using these theories, it becomes possible to examine the implementation of technology at the organizational and individual levels [9,80]. The theory of planned behavior (TPB) is one of the most significant theories that has been used to assess the implementation of technology at an individual level [81]. Through TPB, one can present the influence on individual performance by developing the implementation of technology based on behavioral intention, social influence, and the individual’s feelings [82]. The adoption of individual-level technology has been clarified by the Unified Theory of Acceptance and Use of Technology (UTAUT) [35,83]. The association between the attitudes and the beliefs of users, as well as the aim to implement technology, has been stated by the theory of reasoned action (TRA) [84] and the TAM [26,27,85]. At the organizational level, the technology–organization–environment (TOE) framework [86] and DOI theory [25] have been used to develop technology adoption frameworks.
Theories such as the DOI [25] and TAM [26] have been utilized in different fields, and particularly in IS disciplines for the adoption of mobile services, library and information science research, e-learning systems, and cloud services [25,87,88,89], to describe user behavioral patterns in the implementation of technologies. DOI recognizes creativity transmitted over time and through a given social structure using communication networks. Nevertheless, it does not accept behavioral factors influencing a person’s ability to adopt creativity, which is why it must be triangulated with another theory that concentrates on innovative adoption. While theories such as the TPB [81], TRA [84], and TAM are all intentional and social psychology-based theories, TAM has actually been applied to the area of IS using the TRA. The role of the TAM is to understand a person’s desire to use a technology, which is viewed as beneficial and easy to use. Davis [26] defines perceived utility as the degree to which the efficiency of an individual using specific technology will increase. Even though the use of a system will boost performance, assessment of the commitment to use a system cannot be understated. Therefore, perceived user-friendly adoption is as significant as the anticipated usefulness of technology in the sense of an individual who thinks that using a specific system will be effortless [26,90]. The adoption of fog technology came with the use of TAM; however, this development indicates insufficiency since it does not consider the present technology features of diffusion and acceptance. This theory was proposed a while ago, and since then, various developments have occurred that may impact technology adoption.
The DOI will be used as the principal theoretical structure underlying the development of the framework by researchers throughout this research stage. Due to the novelty of fog technology, as this technology is still at the primary stages of diffusion, the DOI has been chosen to examine the diffusion and acceptance of this type of technology, which is considered an innovation in this research. The research framework will combine elements from the DOI and TAM and other important factors from the literature review that impact the adoption of any new technology, including technological considerations such as privacy and security [23,41,42]; economic factors such as cost [23,28,30,33,34]; cultural factors such as socio-cultural [38,40]; contextual factors such as awareness, infrastructure, and information intensity [45,46,91]; and organizational factors such as size, employee knowledge, and location [29,35,36,38].
Innovation adaptation research, which primarily considers the acceptance of IT/IS, has formed a variety of complementary and technology adoption models to study the adoption process [88]. Consequently, the DOI [25] and TAM [26] signify the most powerful theoretical insight that focuses on the innovation literature, which is also comprehensively applied by different scholars to explore a variety of technological innovations [92]. A review of different IT adoption studies illustrates that the structures of any innovations mostly belong to the technology adoption literature [92,93]. Both the TAM and DOI are based on the assumption that adopters evaluate innovations based on their perceived attributes, or that innovations with attractive aspects are more likely to be accepted [25,27]. Furthermore, there are value-oriented characteristics, such as perceived utility and relative benefit [25,27], and features that require effort, such as perceived ease of use and complexity [25,27], that make a significant theoretical contribution to the previous TAM with DOI studies in different sectors [94]. As a result, the DOI and TAM, which are similar in certain components and hence complement each other, are used to analyze IS/IT adoption. According to researchers, the TAM uses categories that are essentially a subset of perceived innovation features. Thus, merging these two theories can result in a more powerful model [95,96]. According to the extant research, investigations that included both of these theories yielded good findings [96,97].
In this research, this theoretical combination will be used to examine the suitability of fog technology by expert consumers and decision-makers depending on the perceived value and convenience of its use. The proposed framework in this research will also explore the mediating effects of DOI characteristics on some TAM factors. Limited studies have emerged to understand the organizational implementation and use of emerging innovations, including fog technology, through modeling and assembling constructions from the TAM and DOI. Triangulation of both theories and the simulation of technological, economic, cultural, contextual, and organizational variables provide a new viewpoint and perspective on the understanding, distribution, adoption, and application of fog technology.
4. Research Framework and Hypotheses
4.1. Research Framework Development
Considering the theoretical conceptual framework and constructs extracted from the DOI and TAM, it is possible for researchers to present a conceptual research framework, as presented in Figure 1. As part of this research framework, the associations between the independent variable and the dependent variables were assessed. The independent variables are the combined effect of fog technology diffusion and adoption, while the dependent variable is fog technology use and adoption intention, as shown in Figure 1. Although the adoption and use of fog technology are the dependent variables in the framework, they can be tested explicitly for businesses where fog technology is currently implemented and for businesses that plan or search to adopt this technology. In the meantime, the use of the TAM has been hypothesized and empirically verified in previous studies [98,99,100,101,102]. Variables from both the DOI and TAM have been considered inadequate for tackling the prevailing problems with technological implementation, particularly fog technology implementation in organizations from different sectors. The research framework also offers additional contextual, economic, organizational, cultural, and technological factors that can affect the implementation of fog technology within organizations.
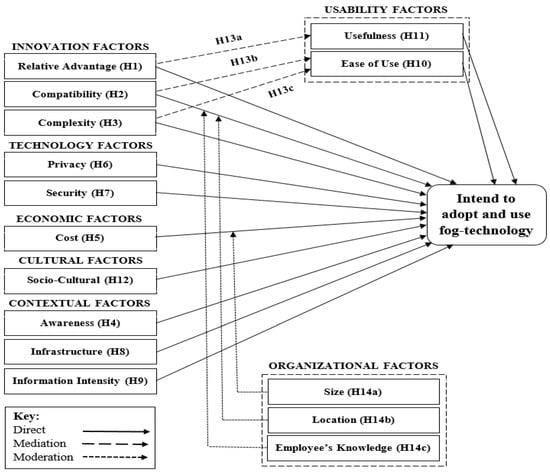
Figure 1.
The fog conceptual research framework.
The use of intentions hypothesized by the TAM, which have been empirically verified in previous studies, serves as a predictor for the practical usage of fog technology by organizations [26,98,99,100]. Competing intentions for the implementation of fog technology would be concurrently assessed with emerging technology values and behaviors [103]. Earlier studies have reported that behavioral intention to utilize a system offers a fair measure of the possible potential use of the system [104,105,106].
One fundamental tenet of the TAM is that conviction affects the acceptability and utilization of new ISs [103,107]. The conceptual research framework suggests the use, in disseminating and embracing fog computing, of variables resulting from the TAM as mediating factors for DOI behaviors. The TAM’s ease-of-use construct mediates the compatibility and complexity characteristics of the DOI, as seen in the proposed research framework, while the TAM’s usefulness construct mediates the relative advantages of the DOI. Even the spread of fog technology can be mediated by contextual factors such as infrastructure. It can also be modeled in terms of a mediator of innovation parameters. Researchers have concluded that the functionality of fog technology is mediated by infrastructural influences.
The size of an organization must take into account two considerations. The first consideration is economic, such as expenses; larger organizations will find it easier to pay for fog technology. The second consideration is size, which is a complex construct. Many studies, including that of Frambach and Schillewaert [36], concluded that larger organizations felt more of a desire to embrace innovation to sustain them and maximize their profitability and productivity. In the meantime, others found that, due to the versatility and innovation of smaller organizations, they are more creative, enabling them to decide whether to try emerging technology sooner [37,108]. These opposing roles of organizational size and other organizational factors, including structure, strategy, and culture, affect the implementation of new technologies [38,40]. A meta-analysis of IT-related factors in organizations found that organizational assistance, as a variable in the adoption process, was poor [39,109]. Even so, researchers feel that the scale of other innovations, such as cost, may have a moderating impact. There are other different technological attributes of fog technology, including data security and privacy, that are likely to have direct implications in the implementation, as well as the use, of fog technology [23].
Demographic influences such as awareness and employee knowledge have been found to affect human behavioral interest in embracing and adopting emerging technologies as a moderating variable [23,35,110,111]. Through validating the UTAUT theory, Venkatesh, Morris, Davis, and Davis [35] identified that by using models based on a variety of usages of the IS model, such as the DOI and TAM, 70% of the variation in the purpose of implementing new technology could be understood, and some variables, such as employee expertise or experience, were influenced. While their study focused on individual acceptance and use of the technology, in this research, we also contend that an organization’s demographic features such as location and size would minimize the influence of innovative features, economic variables, and technical factors on the acceptance of fog technology.
Considering an organization’s position with respect to another comparable organization and its geographic location, fog technology providers will moderate the implementation of new techniques. Unsurprisingly, locations have a geographic effect, so management teams with more varied knowledge and expertise are usually found in commercial centers and cities, which evaluate the potential effects of ICT adoption in contrast to rural organizations [112]. Circumstances among companies from the same sector and located close to each other can often affect technological acceptance, helping them to make informed acceptance choices by observing the effect of new technology in other businesses [37]. Although the location of the fog technology provider is unrelated to the services and efficiency of fog technology, proximity can affect propagation and decision-making by future adopters of fog technology [23,113]. The provision of resources such as exposure to skilled staff, rapid internet accessibility, and a secure power supply can also have effects [114], which, in turn, moderate decision-making on emerging technologies.
The proposed research framework helps to determine the direct variable effect on fog technology within various organizations in several sectors, keeping in mind the contextual variables, technical variables, economic variables, usability features, and innovation propagation attributes. This research framework would also help to assess the TAM variables and the contextual variables’ ability to mediate technology dissemination, such as fog technology, along with the ability of the demographics of the organization to reduce the influence on diffusion and the assessment of the acceptance variables.
4.2. Research Hypotheses Development
The assumptions that represent the first steps forward are taken by applying the positivist deterministic testing framework and statistical tests in a rigorous data analysis study to verify the proposed research framework and provide a framework that offers a solution to our research question. Hypotheses in this research address the relationships among the independent variables of the perceived features of fog technology, the DOI, and the TAM with the dependent variable being “intent to adopt and use fog technology”.
The disruptive features of any new technology indicate an influence on the integration of future innovation. Innovation diffusion research does not completely present the value of the associated benefits, which indicates the perceived advantages of innovation compared to the current technology [115,116]. The advantages relate to innovation adoption costs, popularity, economy, and efficiency [117]. If the user realizes that, compared to the existing technology, a novel innovation would be more advantageous, then this innovation will be adopted [117,118]. A significant number of research studies have been presented based on the concept of compatibility. These studies focus on the role of compatibility and its importance as an IT innovation feature [1,119,120,121]. The adoption of any new technology can be significantly hindered by complexity [115,122]. When complexity is high, then there are issues of technology utilization and information availability. Furthermore, the cost of adoption also increases based on the time acquired to make use of the innovation interface [123,124]. If the new technology is simple or interacts simply, then it would be adopted easily [117,125]. The mentioned variables help indicate the organization’s propensity for adopting new technology [126,127]. Hence, the current research presents the following hypotheses.
H1.
Fog technology adoption intent and relative advantage are positively correlated.
H2.
Fog technology adoption intent and compatibility are positively correlated.
H3.
Fog technology adoption intent and complexity are negatively correlated.
Fog technology information and utilization levels will be used as the primary sources for the analysis of adoption and use. For new technology and the process of technology adoption, the first stage is awareness [127] since it affects the intention of adoption and perception of users [128]. When an organization decides to adopt advanced technology, the two issues that should be considered are security and data privacy. Within the current research, security is referred to as media, data centers, and services security. The construct includes the organization’s data confidentiality and privacy [41,42]. The presence of online protection flaws in fields such as e-commerce and, more notably, internet banking has been a problem for users over the years [129,130]. As fog technology is categorized as internet technology-based, its implementation has been hindered by the same security issues identified in previous studies related to technological adoption. However, the main distinguishing features of fog technology have been described as cost-effectiveness and the sophisticated protection algorithms used in fog technology [131,132] that can influence its adoption. Therefore, this research hypothesizes the following:
H4.
Fog technology adoption intent and awareness are positively correlated.
H5.
Fog technology adoption intent and cost-effectiveness are positively correlated.
H6.
Fog technology adoption intent and privacy are negatively correlated.
H7.
Fog technology adoption intent and security are negatively correlated.
A national infrastructure with an effective telecommunications network and a high-speed network plays an ongoing and critical role in the development of the innovation process [37]. It is usually considered in areas that rely on effective infrastructure to ensure effective and adequate operation [43,44]. For example, poor infrastructure in companies has compelled them to address different problems such as electricity diffusion and unstable communication [133,134]. Thus, the availability of stable infrastructure would have a positive impact on fog technology and its usage with the adoption of innovation in the fog technology system.
H8.
Fog technology adoption intent and the presence of appropriate and advanced ICT infrastructure are positively correlated.
Companies that make use of sophisticated and relevant IT technologies are more sought after and are more capable of obtaining information in the initial stages of information processing from both internal and external data sources [45,46,91]. These organizations also have more compelling information with effective potential that has been used for ISs in the organizations [135].
H9.
Fog technology adoption intent and information intensity are positively correlated.
The adoption and usage of technology in an organization have both been largely impacted and driven by intention and changes in behavior [26]. They have also been influenced by the use of new technology, which affects task performance [82,100,102]. The phrase “perceived ease of use” refers to consumers’ perceptions of how simple or straightforward a system is to use [25]. This phrase is used in this study to refer to users’ thoughts on how to use the fog technology system to improve their experiences and performance. Other academics have pointed out that this phrase is defined in terms of the amount of effort required to use a certain system [25,136]. Furthermore, ‘perceived usefulness’ is a phrase that refers to how users view a system’s ability to improve their performance [25]. The intention to use the fog technology system was found to be influenced by perceived usefulness [136,137]. Therefore, the adoption and usage of advanced technology in a firm are based on a decision that must be made by IT experts in the organization [99,101]. The behavioral intention of decision-making will influence the recommendation that is made for its adoption in the correct manner [138]. The hypotheses corresponding to this aspect of the research are as follows:
H10.
Fog technology adoption intent and perceived ease of use are positively correlated.
H11.
Fog technology adoption intent and perceived usefulness are positively correlated.
Organizations in various fields constitute a community of people with varied social and cultural backgrounds. The differences in employees’ social and cultural backgrounds cause the organization to have different opinions about the use and adoption of technology [37]. The necessity to use innovative technology becomes clear, given the different types of traditional, cultural, and social beliefs [139,140]. In culturally cohesive communities, different cultural and social aspects serve as the determining factors that impact innovation and its use in organizations [141,142]. Thus, such factors would affect innovation and decision-making that correlate to the implementation of fog technology within the organization.
H12.
Fog technology adoption intent has a negative correlation with socio-cultural.
The construct of relative advantage is used in this study to refer to the point to which users believe that the utility of fog technology can enhance the performance of their organization. The intention to adopt and utilize fog technology influenced by perceived relative advantage has been reported in the previous literature [97,143]. The relationship between relative advantage and perceived usefulness within TAM and DOI research has received little attention from scholars, and only a few studies have looked into this and ascertained that perceived higher relative advantages mean that organizations would also perceive a higher level of usefulness of fog technology.
Compatibility is related to the situation in which users feel that the new innovation is compatible with their existing project standards, previous IT projects, and the desires of probable adopters. Moore and Benbasat [126] agreed that if the fog technology is in accordance with users’ beliefs, requirements, and experiences, then the level of compatibility is considered high. This phrase is used in this study to refer to users’ perceptions of the advantages of utilizing fog technology. Compatibility has been utilized as a measure of users’ intention to embrace the adoption and use of IS in the previous literature [35]. Compatibility has also been demonstrated to have a significant impact on perceived ease of use [97,144]. A number of users believe that the relationship between similar technologies and prior experience is positively related to the ease of use of technological innovation [103]. Some prior research ascertained that compatibility has a significant effect on perceived ease of use [145,146], indicating that the more users found fog technology to be consistent and compatible with their values, beliefs, lifestyles, and needs, the more likely they would see fog technology as easy to use, flexible, and useful for accomplishing organizational IT goals quickly.
The amount of difficulty in comprehending innovations and their ease of use as assessed by the end user is referred to as complexity. Based on this concept, this research refers to users’ perceptions of the degree of difficulty, which influences their performance. According to a previous study, when end users view the fog technology system to be difficult, they are less likely to accept and use it [147]. Furthermore, Hardgrave, Davis, and Riemenschneider [144] found that perceived ease of use is negatively correlated with complexity. Other empirical research, such as that by Lee [143] and Shih [148], found that the complexity of a new system has a negative impact on the intention to adopt and utilize it. Furthermore, Thompson [149] showed that when a system’s perceived technological implicitness grows, it is seen as more difficult to comprehend and utilize. As a result, perceived implicitness is one characteristic of a system’s complexity and one of the quantifiable components of effort expectation [35]. The ease with which the system can be used is referred to as effort expectancy. As the level of technical implicitness rises, the technology becomes more difficult to comprehend and utilize; as a result, this characteristic might be factored into the perceived ease of use.
H13a.
The impact of relative advantage on fog technology adoption intent is mediated by usefulness.
H13b.
The influence of compatibility on fog-technology adoption intent is mediated by ease of use.
H13c.
The influence of complexity on fog-technology adoption intent is mediated by ease of use.
The use of moderators is important to consider key determinants in terms of dynamic effects, therefore enabling the improvement of quality for adopting the research models as suggested by [36]. The means of moderator analyses can help to model and test for the possible cause of heterogeneity [36]. Three construct relationships can be affected positively or negatively due to the variables known as moderators [36]. This research concentrated on fog technology adoption by organizations in different sectors; thus, it theorized new moderators to address the hypotheses of the research study.
At an organizational level, innovation can be implemented only if the employees of the specific organization recognize this innovation, referred to as intra-organizational acceptance [36]. The implementation of any advanced technology within an organization is influenced by various determination levels of the organization. Several organizational features, such as organizational innovation, structure, location, and size, impact the decision on technology adoption [36]. Hence, the decision-making of IT experts that correlates to the implementation of fog technology within the organization is influenced by organizational features, including size [36,37], location [112], and employees’ knowledge about fog technology [111].
H14a.
The relationship between the cost-effectiveness and adoption of fog technology is moderated by the organization’s size.
H14b.
The relationship between the compatibility and adoption of fog technology is moderated by the organization’s location.
H14c.
The relationship between the compatibility and adoption of fog technology is moderated by employees’ knowledge of fog technology.
5. Research Methodology
The research philosophy developed by researchers should take ontology into account so that a relevant method for the research is extracted [150]. Knowledge development and assessment are carried out through a theoretically based system referred to as the methodology [151]. The current research implements a quantitative methodology where the data were gathered using formal surveys from a significant number of respondents. Data collection can be directed by several techniques, such as mail, face-to-face, and online surveys. All of these techniques are different, and no technique is superior to any other technique. Therefore, the technique is carefully chosen according to the type and aims of the research. The incorrect choice of survey techniques can result in unanswered research questions [152]. This research chose to use the online survey method. Through this method, the results can be generalized and are statistically significant [152].
The current research employed an online survey that takes into account literature related to the acceptance of novel technology within organizations [153,154,155]. The hypotheses listed above will be fully explored. An online survey is a low-cost, flexible, and quick method of data collection, which is why it was chosen for this methodology [156,157]. It offers an adaptable method of questioning respondents where respondents can include their dispositions, knowledge, and qualities within their answers [158]. Through the questionnaire, the measurement framework can be tested, and the conceptual framework can be proposed. This online survey was designed to have three sections. Part 1 included several questions about the respondent’s demographic and employer information. Part 2 investigated the participants’ organizational status in relation to the adoption and use of fog technology. Part 3 concentrated on the specific factors that might influence the adoption of fog technology. For each measure, a seven-point Likert scale, in which ‘7’ indicates strong agreement and ‘1’ shows strong disagreement, was employed. Through the 7-point Likert scale, a more granular evaluation of the respondent is reflected compared to the 5-point item scale [159]. The sensitivity of the 7-point Likert scale is appropriate and reduces interpolations. It is also quite compact so that efficient responses will be generated. The objective and perceived accuracy and ease of use of the 7-point Likert scale are also advantageous [159].
In this research, all employees of the IT department and senior executives within the participating organizations from different sectors had business email addresses. Because of the low cost of sending e-mails and the ease of doing so with online survey tools, the researcher can increase the survey response rate by sending email reminders. As a result of that, an online survey was designated as the best technique for this research. To maximize reach and accessibility, online delivery of the survey was executed [1]. An invitation email was sent to IT managers and senior executives within the participating organizations. In addition, we requested them to forward the invitation to all their professional employees and encourage them to participate. The online survey link was available 24/7 for a three-month time period between 14 May and 13 August 2020.
Information from prior research studies on the adoption of IS was used to form survey questions. In previous studies, item reliability and validity were already established [160,161]. Four university academic staff members, specifically IS academic staff members, conducted and validated a pre-study. They presented recommendations for structural alterations of a small number of questions and the removal of uncertainty. Keeping in mind the alterations presented by the academic staff, a pilot test was carried out where 47 IT staff and senior executives from various industries were asked to complete the survey. Thirty-nine complete surveys, or 82.97%, were received. Research instrument item reliability as part of the conceptual framework was evaluated with Cronbach’s alpha by using the IBM Statistical Package for the Social Sciences (SPSS) software (IBM, Armonk, NY, USA) because the reliability allows us to check the properties of the scales and the measurement items that compose the scales. The reliability process calculates a number of commonly used measures of scale reliability and offers information about the relationships among individual items in the scale [162,163]. A Cronbach’s alpha value of 0.7 or more shows that the items’ internal consistency is acceptable over the entire scale [164]. It is excellent to have a Cronbach’s alpha value of 0.9 or more, 0.8 and more is good, 0.7 and more is acceptable, 0.6 is questionable, 0.5 is poor, and less than 0.5 is not acceptable, as stated by Warmbrod [165] and George and Mallery [166].
According to the value of Cronbach’s alpha, the survey instrument related to testing the model was reduced from 89 items to 76 items. Using Cronbach’s alpha scores, the table below compares the internal consistency levels. After refinement, the scores ranged from acceptable to high (0.702 to 0.936), showing that, for all measures, there was an appropriate level of internal consistency [162,167] (see Table 2).

Table 2.
Reliability Indicators.
When the survey technique was used, data collection was subject to two kinds of bias. These are the common method and nonresponse biases. First, the nonresponse problem was resolved by creating two groups of samples: early and late [168]. The responses from both groups were then compared through demographics, for instance, experience and role. According to the statistical test, the two groups had no significant difference, which confirms that the responses were not affected by nonresponse bias. Second, the common method was tested using Harman’s one-factor test statistical analysis [169]. According to the test, the significance level of variance cannot be indicated by a single factor. The single-factor highest covariance is nearly 33%. Hence, it has been confirmed that common-method bias does not significantly threaten the study’s measurement validity [169].
The research respondents were targeted by various organizations that had been planning on using or had previously used fog technology within various sectors. Various organizations were taken into consideration to analyze whether the infrastructure base for effective communication is present for fog-based solution adoption and decisions toward adoption. In Figure 2, the organization’s adoption stages of the fog-based solution are presented. The fog-based solution was not adopted by 46.5% of the respondent organizations. Pilot testing for the adoption of fog-based solutions was carried out by 8% of the research respondents. The adoption of fog-based solutions has been explored by 14% of the participating organizations. Fog-based services were used by nearly 31.5% of the respondent organizations. Hence, the respondent organizations were mostly experienced and knowledgeable (53%) in the adoption of fog-based solutions in their businesses. Figure 2 shows further details regarding the adoption stages of fog-based solutions.
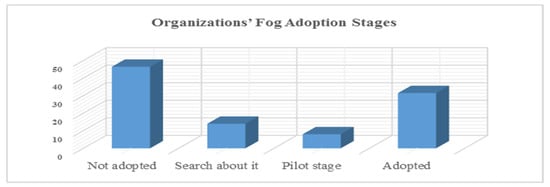
Figure 2.
Organizations’ fog adoption stages.
The target demographic for our investigation is professional employees who worked in IT departments and the senior executives of the chosen organizations. These organizations’ top management was asked to forward the survey link to their employees via email. To ensure that nobody completed the anonymous survey more than once, the online service saved each participant’s unique identifier (IP address of survey response devices) as login details for audit.
Research Demographic Data
As mentioned, the research survey was distributed electronically (online) to numerous organizations across various industries, from which 43 organizations responded to the survey. From these 43 participating organizations, 216 individual IT- and management-related employees responded. Table 3 shows descriptive data about the demographics of the respondents.

Table 3.
Sample demographics (N = 216).
The role and knowledge of fog technology and IT experience were among the main demographic data that were collected from participants. The majority of the respondents (as seen in Table 3) were in a system analyst role (30.55%), and thus, respondents most commonly reported having ‘good knowledge’ of fog technology (34.26%). More than half of the participants (55.09%) said that they had 6–10 years of IT experience, while 25% said that they had 2–5 years of experience.
6. Research Results
6.1. Measurement Model
The current research applies a number of statistical techniques to measure the validity, reliability, and fit of the recommended fog adoption conceptual framework. Factor analysis and confirmatory factor analysis (CFA) was applied to measure the validity of the scale. To check for internal consistency, the scale validity and reliability were also tested.
6.1.1. Factor Analysis
Scale validity can be ensured using the essential factor analysis technique. Scales and tests can be assessed and improved as well [170]. In this technique, CFA was also included in the research. Theory assessment is the objective of CFA. Structural equation modeling (SEM) is used because it is an arithmetical methodology [171]. Exploratory factor analysis (EFA) and CFA are different since current theories are used to identify prospects and suppositions regarding factor relevance and number [149]. For the current research, Analysis of Moment Structures (AMOS) Graphics 22 (IBM-SPSS-Amos) was used to conduct CFA. There are, broadly, three types of measurement models: Tau-equivalent, parallel, and congeneric measurement. The current research uses congeneric measurement since it helps to refine the measurements through fit measures. Through the technique, separate testing was carried out for the fifteen constructs. For the one-factor congeneric measurement model, it was possible to attain fitness. As part of the process, the number of items was reduced from 76 to 68. For the remaining constructs, measurement model tests were carried out [172]. During refinement, eight items were removed. Hence, the recommended research framework is presented in the following manner: Goodness-of-Fit (GFI) = 0.93, Adjusted Goodness-of-Fit (AGFI) = 0.86, Root Mean Square Error of Approximation (RMSEA) = 0.060, Root Mean Square Residual (RMR) = 0.050, Chi-sq/DF = 3.527 and Comparative Fit Index (CFI) = 0.95).
6.1.2. Validity and Reliability
The constructs’ validity and reliability were assessed using a variety of methods with SEM-Amos as the main instrument used in this research for data analysis. The recommended acceptable level for Cronbach’s alpha was ≥0.70 [167]; the construct values were between 0.874 and 0.996. Standardized regression weights (SRWs) were utilized to assess convergent validity. Here, the factor loading was proposed to be 0.50 or higher [173]. The values returned ranged from 0.598 to 0.933, which indicated convergent validity. The recommended level for the squared multiple correlation (SMC) is 0.30 or more. The SMC shows the dependency between items present within factor determination [174]. The returned values of the SMC test were in the range of 0.561 to 0.923. Lastly, 1.96 is the recommended standard value for the critical ratio (CR) [175], and the values that returned were between 12.249 and 26.927. Hence, we can conclude that the measures indicated that the research model has high regression validity.
6.2. Structural Equation Model
The conceptual framework’s objective is to categorize the key variables that impact the adoption of fog technology by various organizations in several industries. The impact of fourteen factors on the adoption and application of fog technology was tested. Based on [176], a methodology section was introduced for SEM in which the association among latent variables is stated. Byrne [177] characterized SEM as an approach for extracting variables that may affect the values of other latent variables directly or indirectly. A moderate level of good fit was determined after assessing the structural model fit indices (GFI = 0.92, AGFI = 0.90, RMSEA = 0.061, RMR = 0.051, Chi-sq/DF = 4.723 and CFI = 0.91).
Table 4, Table 5 and Table 6 show the regression analysis results for the variables that were utilized in the adoption model, along with indications of whether the findings confirm the fourteen hypotheses. The path coefficient (β) value, standard error (SE), R square (R2), critical ratio (t-value), and p-value were used to determine the SEM results. For a t-value greater than 1.96 and a p-value of 0.01 or 0.05, the standard decision rules are used.

Table 4.
Results of the hypothesized path relationships.

Table 5.
Hypothesis tests for the mediating effects.

Table 6.
Hypothesis tests for the moderating effects.
Table 4 shows the regression test results. For eight of the twelve hypotheses, these results support the idea that these constructs are strongly and favorably associated with fog technology adoption. These eight constructs are relative advantage, compatibility, awareness, cost effectiveness, security, infrastructure, ease of use, and usefulness. Complexity, privacy, and information intensity are three of the remaining constructs that were found to be non-significant. The socio-cultural was the only construct that was found to be important but negatively associated with the adoption of fog technology. Figure 3 shows the path diagram for these final relationships in detail.
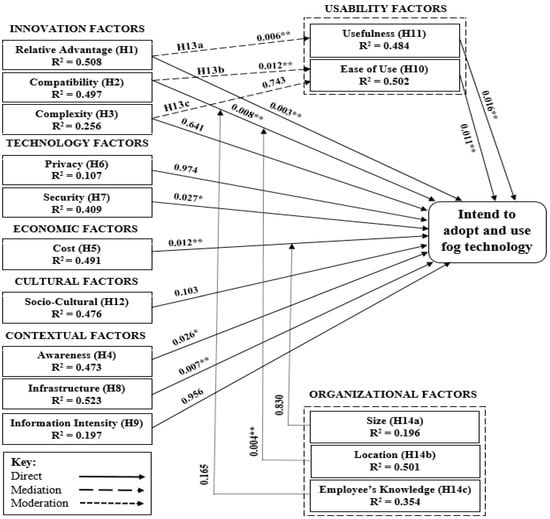
Figure 3.
Fog technology adaption framework. * Significant at p < 0.05, ** Significant at p < 0.01.
6.3. Hypotheses Results Discussion
Despite the assertion that fog technology saves time and costs during recent technology rollouts in businesses, to our knowledge, few studies have studied the factors that may affect fog technology adoption within organizations. This research explores a variety of factors that are more likely to affect fog technology adoption. According to the findings of this research, the effect of these variables is discussed next.
Relative advantage: The research framework predicted a significant positive correlation between the adoption of fog technology and relative advantage. The analysis generated a standardized coefficient (β) of 0.134 along with a t-value of 2.405, an R2 of 0.508, and a 0.003 ** p-value level. These values show a significant correlation among the mentioned variables (see Table 4). Relative advantage represents the point at which fog technology is more effective, cost-saving, and requires less maintenance than existing technology solutions [25,178]. The studies conducted by Tsai, Lee, and Wu [117] state that recognizing the importance of usage and benefits over the former motivates organizations to adopt new technology. Therefore, the research results affirm the presence of a substantial correlation between relative advantage and the organization’s implementation of advanced technologies. Moreover, there is an important mediation association between fog technology’s usefulness and relative advantage. A path coefficient of 0.006 ** was generated from the analysis, prompting the importance of usefulness as a mediator between relative advantages and the adoption of fog technology (see Table 5). Based on the literature, usefulness portrays the point at which a person believes that using a certain approach may increase his or her work efficiency [26]. Furthermore, it has been shown to have a strong influence on the action of use and to be a significant determinant in the intention for technology use. The TAM has been analyzed thoroughly in past research; consequently, advantages are now the most significant factors in a person’s choice to use a new technology [35,179], implying that organizations perceive more performance benefits in the use of fog technology than other platforms. This view is also advanced by other studies [148] that reveal that relative advantage positively affects users’ intentions to adopt ISs.
Compatibility: The research framework presented a significant positive correlation between compatibility and fog technology adoption. The analysis generated a standardized coefficient (β) of 0.577 along with a t-value of 3.540, an R2 of 0.497, and a 0.008 ** p-value level. These values show a significant correlation among the mentioned variables (see Table 4). From the literature, compatibility is characterized as the point at which technology is considered consistent with users’ current opinions, past perceptions, and desires [178,180]. Previous works state that the more consistent an innovation is with current procedures and structures, the simpler it is to introduce and integrate the new technology into the organization [178]. According to [181,182], compatibility was identified as a significant determinant for innovation diffusion in the postadoption process. Consequently, the findings of this research are consistent with those of past studies. In addition, the research framework revealed that fog technology’s compatibility and ease of use have a substantial mediation relationship. A path coefficient of 0.012 ** was found through statistical analysis, indicating that the importance of ease of use is a mediator between compatibility and the adoption of fog technology (see Table 5). Based on the literature review, some earlier studies, such as Kristensen [145], established that compatibility has significant effects on ease of use. The literature review indicates that when users feel that fog technology is consistent and compatible with their values, beliefs, and needs, they will likely see fog technology as easy to adopt, flexible, and useful for accomplishing organizations’ objectives effectively.
Regarding location, the research framework revealed a positively moderated relationship between location and compatibility that supports fog technology adoption. The statistical analysis revealed that the path coefficient is 0.004 **. The findings indicate a significant association between the two variables (see Table 6). Research conducted by Forman and van Zeebroeck [183] identified location as one of the key factors that need to be investigated in the adoption process of any new technology. Moreover, choosing locations allows for the pooling of resources, which lowers the costs of technology adoption [184]. In addition, different organizational characteristics, such as location and structure, affect the decision to adopt technology [36]. Fog technology is a technology where location is an important factor because organizations located in remote or rural areas might have poor internet infrastructure that might not be compatible with fog technology. Adopting fog technology in these areas might thus be useless and not benefit organizations.
Related to employees’ knowledge, the research framework showed a moderated negative impact of employees’ knowledge on fog technology’s compatibility and adoption. A path coefficient of 0.165 was obtained through statistical analysis. According to the findings, the impact of this variable on the adoption of fog technology is negatively moderated (see Table 6). The ability of an organization’s employees to cooperate and participate in the development and implementation of any emerging technology-based system, as well as their previous IT experience, increases the likelihood of the organization introducing a new technology [111]. These factors assist teams in comprehending the tasks needed for effective adoption and improvement of their ISs [45,136]. Many studies have found a correlation between prior IT experience and the adoption of new technology [122,185,186]. Accordingly, the findings of this study do not match those of previous studies because adopting fog technology allows organizations to focus on their core business, while the technology solutions partner addresses any technical problems.
Complexity: The framework revealed no substantial relationship between the complexity of fog technology implementation and its usability. The analysis found a standardized coefficient (β) of 0.240 along with a t-value of −1.690, an R2 of 0.256, and a 0.641 p-value level. These results portray a negative and insignificant relationship between the variables (see Table 4). Complexity, according to the literature, refers to how challenging an invention is to comprehend and implement [180]. Hameed and Counsell [178] pointed out that the complexities of innovation can stymie the adoption of new technological advances. Other studies Seyal and Rahman [187] stated that complexity has a negative influence on the acceptability of advancements in technology. However, according to other research, in the decision-making process for technological adoption within an organization, the complexity of technology plays a significant role [188,189]. According to the findings of this research, the complexity of technology is not a significant factor. In particular, in terms of relatedness to organizations across various industries, there is a negative impact on fog technology adoption. This result supports the findings of former research that highlighted the adverse effect of complexity on decisions related to the adoption of technology advancements [25,45]. However, the findings of this research do not support the claims made by Tiwana and Bush [188]. Furthermore, the research framework showed there is no significant mediation association between fog technology’s ease of use and complexity. A path coefficient of 0.743 was generated through statistical analysis, indicating that less ease of use as a mediator between complexity and the adoption of fog technology (see Table 5) is less important. According to earlier research, when customers perceive a technology or system as complex, they tend to have a low intention to adopt it [147]. In addition, Hardgrave et al. [144] identified that complexity has a negative relationship with perceived ease of use. Other studies, such as those by Shih [148], have highlighted that the intention to adopt and use are negatively influenced by the complexity of new systems. Thus, our current research results are consistent with these previous findings.
Awareness: The framework showed a significant positive correlation between awareness and fog technology adoption. The analysis generated a standardized coefficient (β) of 0.269 along with a t-value of 2.619, an R2 of 0.473, and a 0.026 * p-value level. Consequently, the research analysis shows that the two variables have a significant relationship (see Table 4). Awareness has been described as a key factor that positively contributes to the implementation of emerging technologies at both the organizational (environment and work context) and individual (training, knowledge, and skills) levels [190,191]. Research conducted by Hargittai [192] identified the lack of awareness as a barrier to implementing any new advanced technology. Moreover, other studies have confirmed that lack of awareness decreased the ability to use new technology [193,194]. Therefore, the findings of this research confirmed that awareness is a significant factor in the acceptance and adoption of emerging technologies. Therefore, organizations need to provide professional training to their staff to increase their knowledge and ability to utilize advanced technologies.
Cost-effectiveness: The research framework showed a significant positive correlation between the cost-effectiveness and adoption of fog technology. The analysis generated a standardized coefficient (β) of 0.071 along with a t-value of 4.252, an R2 of 0.491, and a 0.012 * p-value level (<0.05). Accordingly, the research analysis indicates a significant relationship between the mentioned variables (see Table 4). According to Thiesse et al. [195], organizations focus on anticipated financial gains when they consider advanced technologies’ acceptability to operational models. Research conducted by Modrák and Moskvich [196] pointed out that fog technology implementation could significantly reduce an organization’s total cost of ISs. Several previous researchers have addressed the degree of adaptability with advanced technologies, while cost-effectiveness has been a major topic of debate [110,132,197]. In terms of the adoption of advanced technologies, the results of this research hence concur with the conclusions of prior research. In addition, the research framework revealed no substantial association between an organization’s size and the expenses of implementing fog technology. A path coefficient of 0.274 was generated through statistical analysis, indicating that the two variables have a negative relationship (see Table 6). In previous research, the size of the company has been the most commonly studied factor [198]. Since the organization’s size determines several organizational characteristics, such as resources, structure, and decision-making, it is the most critical aspect influencing the implementation of IS within the organization [25]. According to previous research findings, such as those by Ali et al. [182], the size of an organization and the acceptance of current technological advances have a positive impact and are significantly correlated. Other scholars, for example, Goode and Stevens [199], concluded that the size of an organization has a negative correlation with the expense of implementing fog technology. Furthermore, other studies by Aiken et al. [200] showed that the correlation was significant. Some IS studies have indicated that the size of an organization is a subject of concern [185,186,197,201].
Larger organizations have significantly more resources, experience, and skillsets than smaller organizations, allowing them to take advantage of recent technological advances. According to Jambekar and Pelc [108], smaller companies benefit from stability, and changes can be made quickly to meet organizational goals. Hence, these companies are able to be highly creative and make rapid changes in response to their needs. This research framework discovered that there is no positive and significant moderated association between an organization’s size and the cost of adopting fog technology. This finding supports that organizations do not focus on size if they have a solid infrastructure that allows them to develop or implement any new technology easily. In addition, organizations can concentrate on the types of processes or activities that they perform instead of just their size.
Privacy: The research framework showed an insignificant correlation between privacy and fog technology adoption. The analysis showed a standardized coefficient (β) of 0.003 along with a t-value of 0.093, an R2 of 0.107, and a 0.974 p-value level. These results indicate a negative relationship between the mentioned variables (see Table 4). In the research conducted by Wang et al. [115], privacy is recognized as a major obstacle to the adoption of any technology. The security level of an entity depends on the confidentiality and privacy of its records [42,132]. Consequently, the conclusions of this research confirm that privacy is not supported as a significant factor for fog technology adoption.
Security: The research framework showed a significant positive correlation between security and the adoption of fog technology. The analysis generated a standardized coefficient (β) of 0.254 along with a t-value of −4.815, an R2 of 0.409, and a 0.027 * p-value level (see Table 4). The security issue is addressed in the context of fog technology with the aim of delivering and retaining a higher degree of security than other technical models such as cloud technology [67]. Security is critical to fog technology, as well as other IS domains [42,202]. The impact of security issues on the adoption of new technologies has been investigated by several studies, such as that by Zhu and Kraemer [186]. On a similar note, security is supported as a significant factor for fog technology adoption, according to the findings of this research.
Infrastructure: The research framework showed an important positive association between infrastructure and fog technology adoption. The analysis generated a standardized coefficient (β) of 0.678 along with a t-value of 2.692, an R2 of 0.523, and a 0.007 ** p-value (see Table 4). From previous literature, the extent to which an organization has the expertise, funding, commitment, and governance to execute IS technologies is measured by organizational IS infrastructure [109]. The adoption of new technology has also been positively correlated with organizational infrastructure. To provide effective incorporation of and reap the benefits from any IS adoption, IS technology and computer resources are necessary [203]. Previous research outcomes have identified a positive correlation between the current involvement of organizational infrastructure and the adoption of new technology [109]. In this research, we claim that the presence of IS infrastructure and its availability, together with an organization’s financial and technical tools, will impact the implementation of new technologies. The results of this research are consistent with those of earlier studies, and they support the research argument that infrastructure is a major factor in fog technology adoption.
Information intensity: According to the research framework, there is no significant association between information intensity and fog technology acceptance. A standardized coefficient (β) of −0.012 along with a t-value of −0.056, an R2 of 0.197, and a p-value level of 0.956 were found through the analysis, indicating a negative relationship among the mentioned variables (see Table 4). According to the literature, information intensity refers to the ability of organizations to implement and use more sophisticated technology [45,46,91]; the larger the information intensity is, the better an organization’s ability to strategically use IS [135]. Consequently, the results of this research differ from those of previous studies [45,46], largely because fog technology is adopted to boost an organization’s overall efficiency rather than merely access information resources. Undoubtedly, other emerging technologies such as Big Data, AI, and analytics tools could be more relevant to information intensity than fog technology in this adoption context, and this remains an interesting future research consideration.
Ease of use: The research framework revealed that fog technology’s compatibility and ease of use have a substantial and constructive mediation relationship. A standardized coefficient (β) of 0.585 along with a t-value of 5.963, an R2 of 0.502, and a p-value level of 0.011 ** was found through analysis, indicating a significant correlation among the mentioned factors (see Table 4). According to the literature, ease of use refers to a person’s perception that using a particular device or procedure is free of effort [26]. According to the TAM, perceived ease of use has a substantial effect on the practical use of innovation, behavioral mindset, perceived utility, and purpose [27].
Usefulness: According to the research framework, there is a significant and constructive mediation association between fog technology usefulness and relative advantage. The standardized coefficient (β) was 0.678, the t-value was 2.472, the R2 was 0.484, and the p-value level was 0.016 ** was found through analysis, indicating an important correlation among the mentioned variables (see Table 4). According to the literature, usefulness portrays the degree to which a person’s belief in using a certain approach may increase his or her work efficiency [26]. Furthermore, it has been shown to have a strong influence on the action of use and is a significant determinant of the desire for invention use. The TAM has been analyzed thoroughly in past research; consequently, utility is the most significant factor in a person’s choice to use any new technology [35,179].
It has been found that human acceptance and usage of advanced technologies are greatly impacted by behavioral intentions that are influenced by the new technology’s ease of use and usefulness in executing tasks [82,100,102]. Specific decision-makers and IT experts in the company will determine whether to introduce and use innovations, and their behavioral intentions toward innovation will influence their recommendations on whether to adopt an innovation [99,101,138]. Thus, the results of this research indicate that the ease of use and usefulness of fog technology are both important factors that affect the decision to adopt fog technology.
Socio-cultural: The research framework revealed that the sociocultural environment had a substantial negative effect on fog technology adoption. The analysis indicated that the standardized coefficient (β) was 0.294, the t-value was 2.007, the R2 was 0.476, and the p-value level was 0.103. These results indicate that this variable negatively impacts the adoption of fog technology (see Table 4). The difference in the social and cultural backgrounds of the employees creates differences of opinion in the organization related to the use and adoption of technology [37]. The necessity to use innovative technology is determined by considering the different traditional, cultural, and social beliefs held by employees [139,140]. In culturally cohesive communities, different cultural and social aspects, and subsequent social capital, serve as determining factors that impact innovation and its use in organizations [141,142]. In this research, the sociocultural environment is significantly negative because the adoption of fog technology aims to enhance the overall performance of the organization’s system rather than to change the whole ecosystem. Consequently, socio-cultural is negatively related to the changes that fog technology introduces to the organization’s IS.
7. Research Discussions and Implications
This paper has addressed the research question directed toward finding the key factors that should be considered by organizations when adopting fog technology. The research findings have considerable implications for studies on fog technology adoption. However, this research also has some limitations. The contributions and limitations of this research are presented in the following sections.
7.1. Research Contributions
This research makes a number of contributions to both academia and industry. Fog technology was initially proposed as a supplement to cloud technology to overcome some key limitations of cloud technology, such as the low latency of applications that support IoT devices. First, as these devices are likely to be more physically dispersed, the fog technology architecture can increase the response time of cloud technology. This research outlines the primary adoption factors for fog technology that will be useful to understand the trade-off of the identified technology factor of security with the longer response time of fog technology. Cloud security factors are heavily researched, and security is often considered an inhibiting factor for cloud adoption [182]. This research shows that fog technology could be an effective solution for organizations’ system architecture compared to cloud technology for security-sensitive industries, where the response time may not be a significant issue, but the security of information exchange is critical, e.g., defense, medicine, and government services. This research presents adoption factors that may be useful for future research in the context of adoption in security-critical businesses.
Second, the overload issue of cloud technology can be reduced by fog technology, which offloads many computing processes requiring minimal computations. Nevertheless, studies on the successful adoption of fog technology remain scarce. This study provides strong quantitative empirical data on this untested phenomenon that could be foundational for the future development of new understandings and expanded theory [204]. The research framework and measures established in this study can help companies expand their understanding of fog adoption and provide initial tools for assessing and managing the adoption of fog technology. Consequently, this research study can be identified as one of the first efforts to investigate the factors that may either enable or complicate the adoption of fog technology, as future studies on other technologies (such as 5G) have yet to be conducted in this context. The contributions of this research are further explained with respect to five areas of research implications, as follows.
7.1.1. Innovation Implications
Stemming from the DOI, this study advocates innovation as a key factor for organizations considering adopting fog technology, as fog architecture can still be considered to be in its initial phase of adoption. Innovation is critical to expanding businesses’ scope and growth. Therefore, any organization considering fog technology should have robust and resilient processes for managing innovative practices. As discussed by Aljawarneh et al. [205], the implementation of fog technology coupled with innovative practices has boosted organizational productivity because this combination enhances customer service, primarily due to the ease of access to services. This finding is well-supported by our proposed model, as the factors associated with innovation, namely, relative advantage and compatibility, are positively supported. Likewise, there is a negative association between fog technology and complexity, meaning that fog technology can reduce the perceived complexities of the delivery of technology-enabled services. This study is also supported by the positive mediating role of the innovation dimension toward the usability factors, i.e., usefulness and ease of use. A key contribution of this research is strong empirical support for the DOI, as it confirms the authenticity of this widely accepted theory toward technology adoption in the organizational innovation discipline. Likewise, Tortonesi et al. [206] advocated for fog technology as the computing paradigm that will continue to play a critical role in innovative smart city initiatives. These researchers designed a fog-as-a-service platform to promote innovative and flexible services that can be supported on edge devices, as well as by cloud technology. This study contributes to supporting the flexibility of fog technology, therefore permitting the delivery of innovative services for the industry. This study has strong industry implications for supporting the practical adoption of fog-as-a-service platforms.
7.1.2. Contextual Implications
Similarly, fog technology has a strong affinity with the contextual dimensions of technology adoption, as supported by our study. Thus, it is not surprising that fog technology supports technology awareness and infrastructure in the same way as cloud technology when it was first adopted and in its early stages [207]. Discussions on the technology infrastructure architecture by Prokhorenko and Babar [208] also confirm the consistency of studies across cloud and fog technology and report that they can both support resilient distributed systems. Preden et al. [209] proposed that self-awareness will be an increasingly important factor for efficiently distributed sensing and computing networks that enable IoT. This premise can be supported by situational awareness of fog technology. Therefore, the contextual dimension of awareness can be viewed from two perspectives: Organizational and technological. From the organizational perspective, awareness relates to how people gain knowledge about fog technology. Our study supports the premise that fog technology can arguably support stronger organizational awareness than cloud technology because fog technology supports edge devices that are more visible and user-friendly for operational use. Likewise, from the technological perspective, connections offered by fog technology are scalable and supportive of self-awareness traits. Hence, the applications of fog technology to IoT services can extend to implementing deep learning on the IoT network akin to the experiments byAttiya and Zhang [210].
While awareness and infrastructure factors have strong support, an interesting finding from our study is that fog technology does not have strong support in relation to information intensity. This finding is significant because, from a technology standpoint, fog technology can support more information-intensive services and applications [209], which demonstrates a disconnect between technology capability and user perception, as captured in this study. Fog technology, given that it is a new computing paradigm, is largely understood as a special type of cloud technology. This classification is accurate, but a significant difference is that, in contrast to cloud technology, fog technology allows for greater computing processing at the edge. While this feature allows for more scalable services, it can be seen that fog technology, especially for edge devices, is limited by being able to implement only a small number of information-intensive applications. From a technology standpoint, this argument holds little weight because fog technology also supports low latency; therefore, information intensity should be supported. Since our survey captures participants’ understanding that fog technology can support information intensity, perhaps this argument can be viewed in terms of the way information intensity is handled by the edge devices of fog technology. We can safely assume that a particular edge machine in fog technology is unable to support information-intensive applications compared to a centralized cloud-technology infrastructure. However, overall, fog technology is capable of supporting information-intensive suites of applications. In this case, a more critical factor is the information and infrastructure architecture of fog technology. For instance, the combination of fog, cloud, and IoT devices built with a platform-independent framework and using services to support data integrity (such as the blockchain) can support information-intensive applications, such as a prototype application for sleep apnea analysis [211]. This research contributes to the body of knowledge that advocates for the consideration of fog technology as a complete architecture rather than the study of specific edge devices or services. Research on fog technology should also adopt a holistic view of technology adoption rather than focusing on specific aspects of fog architecture.
7.1.3. Economic Implications
It is a well-accepted idea that fog technology will continue to drive down costs, similar to what cloud technology has previously achieved, and this prediction is a major driver of its adoption. Our proposed research model supports this view, and fog technology is well-received primarily because it is perceived as a special type of cloud technology, and most recent innovations in this area bundle cloud, fog, and IoT services together, e.g., Prokhorenko and Babar [208]. Therefore, from an economic perspective, it is clear that fog technology can enable cost-effective services. However, from an economic viewpoint, it is worth discussing the overall value of the services, not just the cost. The edge computing and scalability of cloud-technology architecture that is supported by fog technology may in fact increase the cost of the service, but it is possible to increase the overall value of the service to the customer more substantially. This research contributes to the view that fog technology can be considered a factor in the economic dimension because a wider adoption of fog technology will continue to drive costs down. This view is consistent with most IoT-based business case research, as suggested by Brous et al. [212] in their systematic literature review on the advantages of adopting the IoT.
7.1.4. Technology Implications
In terms of the technology dimension, our study found that fog technology is perceived to support information security but does not uphold information privacy. A significant body of research on cloud technology security has emerged since information security continues to be the most significant aspect of cloud computing [213]. A substantial number of technology and process solutions for cloud technology security have been adopted in recent years [181,214]. It is therefore not surprising that there have been an increasing number of cloud technology security measures that have also benefited from the adoption of fog technology. However, trust issues continue to be a significant barrier amid rising cybersecurity threats in the cloud computing area [215], and this fact is reflected in the corresponding technology architectures emerging from cloud technologies, such as fog technology. This research supports a consolidated view of cloud technology security that encapsulates not only technology enablers of clouds (such as fog technology) but also adoption enablers of clouds (such as addressing privacy concerns). Future research should consider privacy issues by not only addressing the granular needs of fog technology but also adopting a more holistic view of the privacy architecture for cloud technology and its wider application in the IoT [213]. This research finding is significant, as it highlights that while users are showing increasing confidence in the security of fog technology, privacy in fog technology is beyond the technology architecture of fog technology [215]. Privacy should be examined in relation to a top-level architecture of cloud technology and IoT. If we can offer assurance on privacy issues at a holistic level for IoT applications, the cloud, fog, and edge computing technologies will be addressed together since this research extends the knowledge that privacy cannot be confined to the technology dimension alone.
7.1.5. Organizational and Socio-Cultural Implications
Finally, our study has highlighted the challenges of fog technology in considering sociocultural and organizational dimensions. These findings are consistent with new technology adoption challenges when innovative approaches are introduced in an organization. Fog technology was not found to have significant dependencies on the organization’s sociocultural setting, organization size, or employee knowledge. These results are valid because they reflect the signature benefit of cloud technology for organizations. Regardless of organization size or employee knowledge, cloud technology offers superior IT services. These benefits are transferrable to fog technology because of the similarity between fog technology and cloud technology in terms of technology adoption from an organizational perspective. There is, however, one notable difference: Fog technology services depend on the location of the organization. Even though fog technology reduces latency in information processing, providing services to geographically dispersed locations with edge devices that are physically located at manifold locations will have an impact on fog technology services. Further research on the impact of location spread on fog technology adoption is necessary. Likewise, a relevant implication is that while considering the latency benefits of fog technology, the location ranges of edge devices to be connected to the fog network should be reviewed so that services can be optimized.
Future research should be conducted to validate our findings and investigate other potential factors that are derived from the distinctive attributes of the fog technology environment. Likewise, on a practical level, providers of fog technology systems need to consider how to apply relevant factors when operating fog-enabled services. For instance, if fog systems are not compatible, are costly, or do not meet the required security levels, then organizations will not be inclined to adopt such a service. The same can be true for other factors; however, as a distinct contribution of this research, we found that it is important to understand how fog technology is perceived and implemented based on the business needs of adoption.
7.2. Research Limitations and Future Work
It is common for empirical studies of this nature to have several limitations. As such, this research has some limitations that should be contemplated when examining the study findings. Since the adoption of fog technology is still in its earliest stage, it was a challenge for the researchers to collect the sample for this study. This list may not be comprehensive because there are other possible constructs that should be included. Future research may consider a larger number of responses. Moreover, since fog technology extends cloud technology, most identified constructs were based on similar studies applied in the context of cloud technology. Fog technology has unique attributes that differ from those of the cloud, such as its distribution and heterogeneous nature. Such features are commonly examined in empirical studies in this area; hence, more factors and metrics can be discovered and tested in this context. It must be noted, however, that the measures used in this study were tested in many studies in the context of IS adoption, which makes them valid for the purpose of this study. Moreover, a rigorous, multiphase methodology was employed to test and validate these measures; however, in research future directions we encourage researchers to investigate and focus on conducting a qualitative case study with technology officials on the validity of the proposed framework and revise the framework accordingly.
From a long-term perspective, many opportunities exist for expanding our framework beyond the adoption limitations and issues but toward studying user experience aspects such as loyalty. Furthermore, this framework can be extended to study the adoption of fog technology when integrating it with other technologies, for example, this framework can be extended to cover the integration of fog computing with blockchain.
8. Conclusions
To address the heavy computing processes and time latency requirements related to cloud technology, fog technology has been proposed as a way to meet these requirements and overcome the limitations of cloud technology. However, fog technology adoption is still in its initial stages. This research study has shed light on this particular technology and has empirically investigated the factors that may enhance or hinder fog technology adoption within the organization.
While most of the investigated factors (i.e., relative advantage, compatibility, awareness, cost-effectiveness, security, infrastructure, ease of use, usefulness, and location) were found to significantly and positively impact the decision of whether to adopt fog technology, other factors (i.e., complexity, privacy, and information intensity) were found to have no significant and negative impact on the decision to adopt fog technology. Other factors (i.e., employees’ knowledge and sociocultural environment) were found to have a significant but negative impact on the decision to adopt. Thus, a key implication to explore is to consider fog technology at a broad and holistic level where cloud, fog, and edge computing architectures are consolidated to offer solutions in broader areas of technology adoption, such as addressing privacy issues and considering the overall value of services provided by fog technology to organizations. Likewise, businesses that plan to adopt fog technology are recommended to not only leverage the benefits of fog technology derived from cloud technology but also acknowledge the unique benefits and issues that fog technology can bring, for example, the business benefits of low latency vs. the challenges of location diversity for edge devices. Based on these implications for research and practice, this research study supports the call for further empirical studies on the adoption of fog technology to validate the findings from this research and to further investigate other cultural and organizational contexts related to the adoption of this technology. This research study is the first step in taking into account the unique technology adoption variables for researchers, as well as providing useful information for fog technology practitioners.
Author Contributions
Conceptualization, O.A. and A.S.; methodology, O.A.; software, A.A.-A.; validation, A.S., A.J. and A.A.-A.; formal analysis, O.A.; investigation, O.A.; resources, O.A. and A.J.; data curation, O.A.; writing—original draft preparation, O.A. and A.S.; writing—review and editing, A.J. and A.A.-A.; visualization, A.J. and A.A.-A.; supervision, O.A.; project administration, O.A.; funding acquisition, O.A. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Institutional Review Board Statement
The study was conducted in accordance with the Declaration of Helsinki, and approved by the Institutional Review Board (or Ethics Committee) of American University of the Middle East (protocol code B-2020-76 and date of approval on 12 March 2020).
Informed Consent Statement
Informed consent was obtained from all subjects involved in the study.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Ali, A.; Ahmed, M.; Imran, M.; Khattak, H.A. Security and Privacy Issues in Fog Computing. In Fog Computing: Theory and Practice; John Wiley & Sons: Hoboken, NJ, USA, 2020; pp. 105–137. [Google Scholar]
- Peng, L.; Dhaini, A.R.; Ho, P.-H. Toward integrated Cloud–Fog networks for efficient IoT provisioning: Key challenges and solutions. Future Gener. Comput. Syst. 2018, 88, 606–613. [Google Scholar] [CrossRef]
- Oliveira, T.; Thomas, M.; Espadanal, M. Assessing the determinants of cloud computing adoption: An analysis of the manufacturing and services sectors. Inf. Manag. 2014, 51, 497–510. [Google Scholar] [CrossRef]
- Bhattacherjee, A.; Park, S.C. Why end-users move to the cloud: A migration-theoretic analysis. Eur. J. Inf. Syst. 2014, 23, 357–372. [Google Scholar] [CrossRef]
- Hashem, I.A.T.; Yaqoob, I.; Anuar, N.B.; Mokhtar, S.; Gani, A.; Khan, S.U. The rise of “big data” on cloud computing: Review and open research issues. Inf. Syst. 2015, 47, 98–115. [Google Scholar] [CrossRef]
- Ali, O.; Soar, J.; Shrestha, A. Perceived potential for value creation from cloud computing: A study of the Australian regional government sector. Behav. Inf. Technol. 2018, 37, 1157–1176. [Google Scholar] [CrossRef]
- Aazam, M.; Zeadally, S.; Harras, K.A. Fog computing architecture, evaluation, and future research directions. IEEE Commun. Mag. 2018, 56, 46–52. [Google Scholar] [CrossRef]
- Hu, P.; Dhelim, S.; Ning, H.; Qiu, T. Survey on fog computing: Architecture, key technologies, applications and open issues. J. Netw. Comput. Appl. 2017, 98, 27–42. [Google Scholar] [CrossRef]
- Ali, O.; Soar, J.; Yong, J.; Tao, X. Factors to be considered in cloud computing adoption. Web Intell. 2016, 14, 309–323. [Google Scholar] [CrossRef]
- Al-Ahmad, A.S.; Kahtan, H. Cloud Computing Review: Features And Issues. In Proceedings of the 2018 International Conference on Smart Computing and Electronic Enterprise (ICSCEE), Shah Alam, Malaysia, 11–12 July 2018; pp. 1–5. [Google Scholar]
- Al-Ahmad, A.S.; Aljunid, S.A.; Ismail, N.K. Mobile Cloud Computing Applications Penetration Testing Model Design. Int. J. Inf. Comput. Secur. 2020, 13, 210–226. [Google Scholar]
- Xue, C.T.S.; Xin, F.T.W. Benefits and challenges of the adoption of cloud computing in business. Int. J. Cloud Comput. Serv. Archit. 2016, 6, 1–15. [Google Scholar] [CrossRef]
- Upadhyay, N. Fogology: What is (not) Fog Computing? Procedia Comput. Sci. 2018, 139, 199–203. [Google Scholar] [CrossRef]
- Al-Ahmad, A.S.; Kahtan, H.; Hujainah, F.; Jalab, H.A. Systematic Literature Review on Penetration Testing for Mobile Cloud Computing Applications. IEEE Access 2019, 7, 173524–173540. [Google Scholar] [CrossRef]
- Almutiry, O.; Wills, G.; Alwabel, A.; Crowder, R.; WaIters, R. Toward a framework for data quality in cloud-based health information system. In Proceedings of the International Conference on Information Society (i-Society 2013), Toronto, ON, Canada, 24–26 June 2013; pp. 153–157. [Google Scholar]
- Ouf, S.; Nasr, M. Cloud computing: The future of big data management. Int. J. Cloud Appl. Comput. 2015, 5, 53–61. [Google Scholar] [CrossRef]
- Inmor, S.; Suwannahong, R. The acceptance of cloud computing for IT workers in Thailand. Procedia Comput. Sci. 2017, 121, 1039–1046. [Google Scholar] [CrossRef]
- Anawar, M.R.; Wang, S.; Azam Zia, M.; Jadoon, A.K.; Akram, U.; Raza, S. Fog computing: An overview of big IoT data analytics. Wirel. Commun. Mob. Comput. 2018, 2018, 7157192. [Google Scholar] [CrossRef]
- Tian, H.; Nan, F.; Chang, C.-C.; Huang, Y.; Lu, J.; Du, Y. Privacy-preserving public auditing for secure data storage in fog-to-cloud computing. J. Netw. Comput. Appl. 2019, 127, 59–69. [Google Scholar] [CrossRef]
- Ardagna, D.; Cappiello, C.; Samá, W.; Vitali, M. Context-aware data quality assessment for big data. Future Gener. Comput. Syst. 2018, 89, 548–562. [Google Scholar] [CrossRef]
- Liu, S.; Chan, F.T.; Yang, J.; Niu, B. Understanding the effect of cloud computing on organizational agility: An empirical examination. Int. J. Inf. Manag. 2018, 43, 98–111. [Google Scholar] [CrossRef]
- Malic, N.H.A.; Izhar, T.A.T.; Kadir, M.R.A. Factors Influencing Fog Computing Adoption Based on Quality of Results (QoR) For Heterogeneous Data Analysis: A Proposed Framework. Int. J. Recent Technol. Eng. 2019, 8, 2760–2766. [Google Scholar]
- Yousefpour, A.; Fung, C.; Nguyen, T.; Kadiyala, K.; Jalali, F.; Niakanlahiji, A.; Kong, J.; Jue, J.P. All one needs to know about fog computing and related edge computing paradigms: A complete survey. J. Syst. Archit. 2019, 98, 289–330. [Google Scholar] [CrossRef]
- Bellavista, P.; Berrocal, J.; Corradi, A.; Das, S.K.; Foschini, L.; Zanni, A. A survey on fog computing for the Internet of Things. Pervasive Mob. Comput. 2019, 52, 71–99. [Google Scholar] [CrossRef]
- Rogers, E.M. Diffusion of Innovations, 4th ed.; Simon and Schuster: New York, NY, USA, 1995. [Google Scholar]
- Davis, F.D. Perceived usefulness, perceived ease of use, and user acceptance of information technology. MIS Q. 1989, 13, 319–340. [Google Scholar] [CrossRef]
- Davis, F.D.; Bagozzi, R.P.; Warshaw, P.R. User acceptance of computer technology: A comparison of two theoretical models. Manag. Sci. 1989, 35, 982–1003. [Google Scholar] [CrossRef]
- Firdhous, M.; Ghazali, O.; Hassan, S. Fog Computing: Will It Be the Future of Cloud Computing? In Proceedings of the Third International Conference on Informatics & Applications, Kuala Terengganu, Malaysia, 8–10 October 2014.
- Moens, N.P.; Broerse, J.E.; Gast, L.; Bunders, J.F. A constructive technology assessment approach to ICT planning in developing countries: Evaluating the first phase, the Roundtable workshop. Inf. Technol. Dev. 2009, 16, 34–61. [Google Scholar] [CrossRef]
- Avgerou, C. Discourses on ICT and development. Inf. Technol. Int. Dev. 2010, 6, 1–18. [Google Scholar]
- Goi, C.-L. The impact of technological innovation on building a sustainable city. Int. J. Qual. Innov. 2017, 3, 6. [Google Scholar] [CrossRef]
- Eseonu, C.I.; Egbue, O. Socio-Cultural Influences on Technology Adoption and Sustainable Development. In Proceedings of the 2014 Industrial and Systems Engineering Research Conference, Montréal, QC, Canada, 31 May–3 June 2014. [Google Scholar]
- Sultan, N. Cloud computing for education: A new dawn? Int. J. Inf. Manag. 2010, 30, 109–116. [Google Scholar] [CrossRef]
- Saad, M. Fog computing and its role in the internet of things: Concept, security and privacy issues. Int. J. Comput. Appl. 2018, 975, 8887. [Google Scholar] [CrossRef]
- Venkatesh, V.; Morris, M.G.; Davis, G.B.; Davis, F.D. User acceptance of information technology: Toward a unified view. MIS Q. 2003, 27, 425–478. [Google Scholar] [CrossRef]
- Frambach, R.T.; Schillewaert, N. Organizational innovation adoption: A multi-level framework of determinants and opportunities for future research. J. Bus. Res. 2002, 55, 163–176. [Google Scholar] [CrossRef]
- Sabi, H.M.; Uzoka, F.-M.E.; Langmia, K.; Njeh, F.N. Conceptualizing a model for adoption of cloud computing in education. Int. J. Inf. Manag. 2016, 36, 183–191. [Google Scholar] [CrossRef]
- Dholakia, R.R.; Kshetri, N. Factors impacting the adoption of the Internet among SMEs. Small Bus. Econ. 2004, 23, 311–322. [Google Scholar] [CrossRef]
- Grover, V.; Goslar, M.D. The initiation, adoption, and implementation of telecommunications technologies in US organizations. J. Manag. Inf. Syst. 1993, 10, 141–164. [Google Scholar] [CrossRef]
- Hong, W.; Zhu, K. Migrating to internet-based e-commerce: Factors affecting e-commerce adoption and migration at the firm level. Inf. Manag. 2006, 43, 204–221. [Google Scholar] [CrossRef]
- Paquette, S.; Jaeger, P.T.; Wilson, S.C. Identifying the security risks associated with governmental use of cloud computing. Gov. Inf. Q. 2010, 27, 245–253. [Google Scholar] [CrossRef]
- Subashini, S.; Kavitha, V. A survey on security issues in service delivery models of cloud computing. J. Netw. Comput. Appl. 2011, 34, 1–11. [Google Scholar] [CrossRef]
- Gómez-Cruz, N.A.; Saa, I.L.; Hurtado, F.F.O. Agent-based simulation in management and organizational studies: A survey. Eur. J. Manag. Bus. Econ. 2017, 26, 313–328. [Google Scholar] [CrossRef]
- Borracci, R.A.; Giorgi, M.A. Agent-based computational models to explore diffusion of medical innovations among cardiologists. Int. J. Med. Inform. 2018, 112, 158–165. [Google Scholar] [CrossRef]
- Thong, J.Y. An integrated model of information systems adoption in small businesses. J. Manag. Inf. Syst. 1999, 15, 187–214. [Google Scholar] [CrossRef]
- Chong, A.Y.-L.; Lin, B.; Ooi, K.-B.; Raman, M. Factors affecting the adoption level of c-commerce: An empirical study. J. Comput. Inf. Syst. 2009, 50, 13–22. [Google Scholar]
- Alzoubi, Y.I.; Al-Ahmad, A.; Jaradat, A. Fog computing security and privacy issues, open challenges, and blockchain solution: An overview. Int. J. Electr. Comput. Eng. 2021, 11, 5081–5088. [Google Scholar] [CrossRef]
- Guo, R.; Zhuang, C.; Shi, H.; Zhang, Y.; Zheng, D. A lightweight verifiable outsourced decryption of attribute-based encryption scheme for blockchain-enabled wireless body area network in fog computing. Int. J. Distrib. Sens. Netw. 2020, 16, 1550147720906796. [Google Scholar] [CrossRef]
- Achouri, M.; Alti, A.; Derdour, M.; Laborie, S.; Roose, P. Smart fog computing for efficient situations management in smart health environments. J. Inf. Commun. Technol. 2018, 17, 537–567. [Google Scholar]
- Chiang, M.; Ha, S.; Chih-Lin, I.; Risso, F.; Zhang, T. Clarifying fog computing and networking: 10 questions and answers. IEEE Commun. Mag. 2017, 55, 18–20. [Google Scholar] [CrossRef]
- Alzoubi, Y.I.; Osmanaj, V.H.; Jaradat, A.; Al-Ahmad, A. Fog computing security and privacy for the Internet of Thing applications: State-of-the-art. Secur. Priv. 2021, 4, e145. [Google Scholar] [CrossRef]
- Elazhary, H. Internet of Things (IoT), mobile cloud, cloudlet, mobile IoT, IoT cloud, fog, mobile edge, and edge emerging computing paradigms: Disambiguation and research directions. J. Netw. Comput. Appl. 2019, 128, 105–140. [Google Scholar] [CrossRef]
- Alzoubi, Y.; Al-Ahmad, A.; Jaradat, A.; Osmanaj, V. Fog computing architecture, benefits, security, and privacy, for the internet of thing applications: An overview. J. Theor. Appl. Inf. Technol. 2021, 99, 436–451. [Google Scholar] [CrossRef]
- Ali, O.; Shrestha, A.; Ghasemaghaei, M.; Beydoun, G. Assessment of complexity in cloud computing adoption: A case study of local governments in Australia. Info. Syst. Front. 2022, 24, 595–617. [Google Scholar] [CrossRef]
- Dastjerdi, A.V.; Gupta, H.; Calheiros, R.N.; Ghosh, S.K.; Buyya, R. Fog computing: Principles, architectures, and applications. In Internet of Things; Elsevier: Amsterdam, The Netherlands, 2016; pp. 61–75. [Google Scholar]
- Khalid, T.; Abbasi, M.A.K.; Zuraiz, M.; Khan, A.N.; Ali, M.; Ahmad, R.W.; Rodrigues, J.J.; Aslam, M. A survey on privacy and access control schemes in fog computing. Int. J. Commun. Syst. 2021, 34, e4181. [Google Scholar] [CrossRef]
- Alaba, F.A.; Othman, M.; Hashem, I.A.T.; Alotaibi, F. Internet of Things security: A survey. J. Netw. Comput. Appl. 2017, 88, 10–28. [Google Scholar] [CrossRef]
- Guan, Y.; Shao, J.; Wei, G.; Xie, M. Data security and privacy in fog computing. IEEE Netw. 2018, 32, 106–111. [Google Scholar] [CrossRef]
- Kumar, R.A. Possible Solutions on Security and Privacy Issues in Fog Computing. In Proceedings of the Second International Conference on Emerging Trends in Science & Technologies For Engineering Systems (ICETSE-2019), Chickballapur, India, 17–18 May 2019. [Google Scholar]
- Toor, A.; ul Islam, S.; Sohail, N.; Akhunzada, A.; Boudjadar, J.; Khattak, H.A.; Din, I.U.; Rodrigues, J.J. Energy and performance aware fog computing: A case of DVFS and green renewable energy. Future Gener. Comput. Syst. 2019, 101, 1112–1121. [Google Scholar] [CrossRef]
- Amor, A.B.; Abid, M.; Meddeb, A. Secure fog-based e-learning scheme. IEEE Access 2020, 8, 31920–31933. [Google Scholar] [CrossRef]
- Tariq, N.; Asim, M.; Al-Obeidat, F.; Zubair Farooqi, M.; Baker, T.; Hammoudeh, M.; Ghafir, I. The security of big data in fog-enabled IoT applications including blockchain: A survey. Sensors 2019, 19, 1788. [Google Scholar] [CrossRef]
- Ni, J.; Zhang, K.; Lin, X.; Shen, X.S. Securing fog computing for internet of things applications: Challenges and solutions. IEEE Commun. Surv. Tutor. 2017, 20, 601–628. [Google Scholar] [CrossRef]
- Zhang, P.; Zhou, M.; Fortino, G. Security and trust issues in Fog computing: A survey. Future Gener. Comput. Syst. 2018, 88, 16–27. [Google Scholar] [CrossRef]
- Skarlat, O.; Schulte, S.; Borkowski, M.; Leitner, P. Resource provisioning for IoT services in the fog. In Proceedings of the 2016 IEEE 9th International Conference on Service-Oriented Computing and Applications (SOCA), Macau, China, 4–6 November 2016; pp. 32–39. [Google Scholar]
- Hussain, M.; Alam, M.S.; Beg, M. Fog assisted cloud models for smart grid architectures-comparison study and optimal deployment. arXiv 2018, arXiv:1805.09254. [Google Scholar]
- Khan, S.; Parkinson, S.; Qin, Y. Fog computing security: A review of current applications and security solutions. J. Cloud Comput. 2017, 6, 19. [Google Scholar] [CrossRef]
- Brogi, A.; Forti, S.; Ibrahim, A. How to best deploy your fog applications, probably. In Proceedings of the 2017 IEEE 1st International Conference on Fog and Edge Computing (ICFEC), Madrid, Spain, 14–15 May 2017; pp. 105–114. [Google Scholar]
- Song, F.; Ai, Z.-Y.; Li, J.-J.; Pau, G.; Collotta, M.; You, I.; Zhang, H.-K. Smart collaborative caching for information-centric IoT in fog computing. Sensors 2017, 17, 2512. [Google Scholar] [CrossRef]
- Souza, V.B.; Masip-Bruin, X.; Marín-Tordera, E.; Sànchez-López, S.; Garcia, J.; Ren, G.-J.; Jukan, A.; Ferrer, A.J. Towards a proper service placement in combined Fog-to-Cloud (F2C) architectures. Future Gener. Comput. Syst. 2018, 87, 1–15. [Google Scholar] [CrossRef]
- Nunes, D.; Silva, J.S.; Figueira, A.; Dias, H.; Rodrigues, A.; Pereira, V.; Boavida, F.; Sinche, S. FoTSeC—Human Security in Fog of Things. In Proceedings of the 2016 IEEE International Conference on Computer and Information Technology (CIT), Nadi, Fiji, 8–10 December 2016; pp. 743–749. [Google Scholar]
- Lee, K.; Lee, C.; Hong, C.-H.; Yoo, C. Enhancing the isolation and performance of control planes for fog computing. Sensors 2018, 18, 3267. [Google Scholar] [CrossRef] [PubMed]
- Khan, S.; Shiraz, M.; Boroumand, L.; Gani, A.; Khan, M.K. Towards port-knocking authentication methods for mobile cloud computing. J. Netw. Comput. Appl. 2017, 97, 66–78. [Google Scholar] [CrossRef]
- Sarkar, S.; Misra, S. Theoretical modelling of fog computing: A green computing paradigm to support IoT applications. Iet Netw. 2016, 5, 23–29. [Google Scholar] [CrossRef]
- Chiang, M.; Zhang, T. Fog and IoT: An overview of research opportunities. IEEE Internet Things J. 2016, 3, 854–864. [Google Scholar] [CrossRef]
- Zhang, J.; Chen, B.; Zhao, Y.; Cheng, X.; Hu, F. Data security and privacy-preserving in edge computing paradigm: Survey and open issues. IEEE Access 2018, 6, 18209–18237. [Google Scholar] [CrossRef]
- Steinmueller, W.E. ICTs and the possibilities for leapfrogging by developing countries. Int. Labour Rev. 2001, 140, 193. [Google Scholar] [CrossRef]
- James, J. The diffusion of IT in the historical context of innovations from developed countries. Soc. Indic. Res. 2013, 111, 175–184. [Google Scholar] [CrossRef][Green Version]
- Herbig, P.; Dunphy, S. Culture and innovation. Cross Cult. Manag. 1998, 5, 13–21. [Google Scholar] [CrossRef]
- Ali, O.; Soar, J. Technology innovation adoption theories. In Technology Adoption and Social Issues: Concepts, Methodologies, Tools, and Applications; IGI Global: Hershey, PA, USA, 2018; pp. 821–860. [Google Scholar]
- Ajzen, I. The Theory of Planned Behaviour. Organ. Behav. Hum. Decis. Process. 1991, 50, 179–211. [Google Scholar] [CrossRef]
- Lai, P. The literature review of technology adoption models and theories for the novelty technology. J. Inf. Syst. Technol. Manag. 2017, 14, 21–38. [Google Scholar] [CrossRef]
- Dwivedi, Y.K.; Rana, N.P.; Jeyaraj, A.; Clement, M.; Williams, M.D. Re-examining the unified theory of acceptance and use of technology (UTAUT): Towards a revised theoretical model. Inf. Syst. Front. 2019, 21, 719–734. [Google Scholar] [CrossRef]
- Fishbein, M.; Ajzen, I. Belief, Attitude, Intention, and Behavior: An Introduction to Theory and Research. Philos. Rhetor. 1977, 10, 130–132. [Google Scholar]
- Hossain, M.A.; Quaddus, M. The adoption and continued usage intention of RFID: An integrated framework. Inf. Technol. People 2011, 24, 236–256. [Google Scholar] [CrossRef]
- Tornatzky, L.; Fleischer, M. The process of technology innovation. In Lexington Books; Rowman & Littlefield: Lexington, MA, USA, 1990; Volume 165. [Google Scholar]
- López-Nicolás, C.; Molina-Castillo, F.J.; Bouwman, H. An assessment of advanced mobile services acceptance: Contributions from TAM and diffusion theory models. Inf. Manag. 2008, 45, 359–364. [Google Scholar] [CrossRef]
- Al-Rahmi, W.M.; Yahaya, N.; Aldraiweesh, A.A.; Alamri, M.M.; Aljarboa, N.A.; Alturki, U.; Aljeraiwi, A.A. Integrating technology acceptance model with innovation diffusion theory: An empirical investigation on students’ intention to use E-learning systems. IEEE Access 2019, 7, 26797–26809. [Google Scholar] [CrossRef]
- Wibowo, M.P. Technology Acceptance Models and Theories in Library and Information Science Research. Libr. Philos. Pract. 2019, 3674. Available online: https://digitalcommons.unl.edu/libphilprac/3674 (accessed on 23 June 2021).
- Venkatesh, V.; Davis, F.D. A model of the antecedents of perceived ease of use: Development and test. Decis. Sci. 1996, 27, 451–481. [Google Scholar] [CrossRef]
- Chau, P.Y.; Tam, K.Y. Factors affecting the adoption of open systems: An exploratory study. MIS Q. 1997, 21, 1–24. [Google Scholar] [CrossRef]
- Hameed, M.A.; Counsell, S.; Swift, S. A conceptual model for the process of IT innovation adoption in organizations. J. Eng. Technol. Manag. 2012, 29, 358–390. [Google Scholar] [CrossRef]
- Puklavec, B.; Oliveira, T.; Popovič, A. Unpacking business intelligence systems adoption determinants: An exploratory study of small and medium enterprises. Econ. Bus. Rev. 2014, 16, 185–213. [Google Scholar] [CrossRef]
- Al-Rahmi, W.M.; Othman, M.S.; Yusuf, L.M. The effectiveness of using e-learning in Malaysian higher education: A case study Universiti Teknologi Malaysia. Mediterr. J. Soc. Sci. 2015, 6, 625. [Google Scholar] [CrossRef]
- Wu, J.-H.; Wang, S.-C. What drives mobile commerce?: An empirical evaluation of the revised technology acceptance model. Inf. Manag. 2005, 42, 719–729. [Google Scholar] [CrossRef]
- Gillenson, M.L.; Sherrell, D.L. Enticing online consumers: An extended technology acceptance perspective. Inf. Manag. 2002, 39, 705–719. [Google Scholar]
- Lee, Y.-H.; Hsieh, Y.-C.; Hsu, C.-N. Adding innovation diffusion theory to the technology acceptance model: Supporting employees’ intentions to use e-learning systems. J. Educ. Technol. Soc. 2011, 14, 124–137. [Google Scholar]
- Karahanna, E.; Straub, D.W.; Chervany, N.L. Information technology adoption across time: A cross-sectional comparison of pre-adoption and post-adoption beliefs. MIS Q. 1999, 23, 183–213. [Google Scholar] [CrossRef]
- Gefen, D. TAM or just plain habit: A look at experienced online shoppers. J. Organ. End User Comput. 2003, 15, 1–13. [Google Scholar] [CrossRef]
- Yoh, E.; Damhorst, M.L.; Sapp, S.; Laczniak, R. Consumer adoption of the Internet: The case of apparel shopping. Psychol. Mark. 2003, 20, 1095–1118. [Google Scholar] [CrossRef]
- Lee, M.K.; Cheung, C.M.; Chen, Z. Acceptance of Internet-based learning medium: The role of extrinsic and intrinsic motivation. Inf. Manag. 2005, 42, 1095–1104. [Google Scholar] [CrossRef]
- Pituch, K.A.; Lee, Y.-k. The influence of system characteristics on e-learning use. Comput. Educ. 2006, 47, 222–244. [Google Scholar] [CrossRef]
- Agarwal, R.; Prasad, J. Are individual differences germane to the acceptance of new information technologies? Decis. Sci. 1999, 30, 361–391. [Google Scholar] [CrossRef]
- Jackson, C.M.; Chow, S.; Leitch, R.A. Toward an understanding of the behavioral intention to use an information system. Decis. Sci. 1997, 28, 357–389. [Google Scholar] [CrossRef]
- Gu, J.-C.; Lee, S.-C.; Suh, Y.-H. Determinants of behavioral intention to mobile banking. Expert Syst. Appl. 2009, 36, 11605–11616. [Google Scholar] [CrossRef]
- Jeong, B.K.; Yoon, T.E. An empirical investigation on consumer acceptance of mobile banking services. Bus. Manag. Res. 2013, 2, 31–40. [Google Scholar] [CrossRef]
- Pynoo, B.; van Braak, J. Predicting teachers’ generative and receptive use of an educational portal by intention, attitude and self-reported use. Comput. Hum. Behav. 2014, 34, 315–322. [Google Scholar] [CrossRef]
- Jambekar, A.B.; Pelc, K.I. Managing a manufacturing company in a wired world. Int. J. Inf. Technol. Manag. 2002, 1, 131–141. [Google Scholar] [CrossRef]
- Hameed, M.A.; Counsell, S.; Swift, S. A meta-analysis of relationships between organizational characteristics and IT innovation adoption in organizations. Inf. Manag. 2012, 49, 218–232. [Google Scholar] [CrossRef]
- Kuan, K.K.; Chau, P.Y. A perception-based model for EDI adoption in small businesses using a technology–organization–environment framework. Inf. Manag. 2001, 38, 507–521. [Google Scholar] [CrossRef]
- Lippert, S.K.; Forman, H. Utilization of information technology: Examining cognitive and experiential factors of post-adoption behavior. IEEE Trans. Eng. Manag. 2005, 52, 363–381. [Google Scholar] [CrossRef]
- Awa, H.O.; Emecheta, B.C.; Ukoha, O. Location factors as moderators between some critical demographic characteristics and ICT adoption: A study of SMEs. In Proceedings of the Informing Science and IT Education Conference (InSITE), Wollongong, Australia, 30 June–4 July 2014; pp. 39–52. [Google Scholar]
- da Silva, R.A.C.; da Fonseca, N.L.S. On the location of fog nodes in fog-cloud infrastructures. Sensors 2019, 19, 2445. [Google Scholar] [CrossRef]
- Pavon, F.; Brown, I. Factors influencing the adoption of the World Wide Web for job-seeking in South Africa. S. Afr. J. Inf. Manag. 2010, 12, 1–9. [Google Scholar] [CrossRef]
- Wang, Y.-M.; Wang, Y.-S.; Yang, Y.-F. Understanding the determinants of RFID adoption in the manufacturing industry. Technol. Forecast. Soc. Chang. 2010, 77, 803–815. [Google Scholar] [CrossRef]
- Bhattacharya, M. A conceptual framework of RFID adoption in retail using Rogers stage model. Bus. Process Manag. J. 2015, 21, 517–540. [Google Scholar] [CrossRef]
- Tsai, M.-C.; Lee, W.; Wu, H.-C. Determinants of RFID adoption intention: Evidence from Taiwanese retail chains. Inf. Manag. 2010, 47, 255–261. [Google Scholar] [CrossRef]
- Wang, R.; Fu, Z.; Duan, Y. Understanding ICTs adoption from an evolutionary process perspective. In Proceedings of the 2011 International Conference on Management and Service Science, Bangkok, Thailand, 7–9 May 2011; pp. 1–4. [Google Scholar]
- Premkumar, G. A meta-analysis of research on information technology implementation in small business. J. Organ. Comput. Electron. Commer. 2003, 13, 91–121. [Google Scholar] [CrossRef]
- Ching, H.L.; Ellis, P. Marketing in cyberspace: What factors drive e-commerce adoption? J. Mark. Manag. 2004, 20, 409–429. [Google Scholar] [CrossRef]
- Daylami, N.; Ryan, T.; Olfman, L.; Shayo, C. Determinants of application service provider (ASP) adoption as an innovation. In Proceedings of the 38th Annual Hawaii International Conference on System Sciences, Big Island, HI, USA, 3–6 January 2005; p. 259b. [Google Scholar]
- Low, C.; Chen, Y.; Wu, M. Understanding the determinants of cloud computing adoption. Ind. Manag. Data Syst. 2011, 111, 1006–1023. [Google Scholar] [CrossRef]
- Shi, P.; Yan, B. Factors affecting RFID adoption in the agricultural product distribution industry: Empirical evidence from China. SpringerPlus 2016, 5, 2029. [Google Scholar] [CrossRef] [PubMed]
- Harindranath, G.; Dyerson, R.; Barnes, D. ICT in Small Firms: Factors Affecting the Adoption and Use of ICT in Southeast England SMEs. In Proceedings of the 16th European Conference on Information Systems (ECIS 2008 ), Galway, Ireland, 9–11 June 2008. [Google Scholar]
- Lin, A.; Chen, N.-C. Cloud computing as an innovation: Percepetion, attitude, and adoption. Int. J. Inf. Manag. 2012, 32, 533–540. [Google Scholar] [CrossRef]
- Moore, G.C.; Benbasat, I. Development of an instrument to measure the perceptions of adopting an information technology innovation. Inf. Syst. Res. 1991, 2, 192–222. [Google Scholar] [CrossRef]
- Rogers, E.M. Diffusion of Innovations, 5th ed.; Simon and Schuster: New York, NY, USA, 2003. [Google Scholar]
- Mottaleb, K.A. Perception and adoption of a new agricultural technology: Evidence from a developing country. Technol. Soc. 2018, 55, 126–135. [Google Scholar] [CrossRef]
- Liebermann, Y.; Stashevsky, S. Perceived risks as barriers to Internet and e-commerce usage. Qual. Mark. Res. Int. J. 2002, 5, 291–300. [Google Scholar] [CrossRef]
- Yousafzai, S.; Pallister, J.; Foxall, G. Multi-dimensional role of trust in Internet banking adoption. Serv. Ind. J. 2009, 29, 591–605. [Google Scholar] [CrossRef]
- Saya, S.; Pee, L.G.; Kankanhalli, A. The Impact of Institutional Influences on Perceived Technological Characteristics and Real Options in Cloud Computing Adoption. In Proceedings of the International Conference on Information Systems (ICIS 2010), Saint Louis, MI, USA, 12–15 December 2010. [Google Scholar]
- Reyes, P.M.; Li, S.; Visich, J.K. Determinants of RFID adoption stage and perceived benefits. Eur. J. Oper. Res. 2016, 254, 801–812. [Google Scholar] [CrossRef]
- Aker, J.C.; Mbiti, I.M. Mobile phones and economic development in Africa. J. Econ. Perspect. 2010, 24, 207–232. [Google Scholar] [CrossRef]
- Mbarika, V.W. Re-thinking information and communications technology policy focus on Internet versus teledensity diffusion for Africa’s least developed countries. Electron. J. Inf. Syst. Dev. Ctries. 2002, 9, 1–13. [Google Scholar] [CrossRef]
- Porter, M.E.; Millar, V.E. How information gives you competitive advantage. Harv. Bus. Rev. 1985, 63, 149–160. [Google Scholar]
- Hunter, G.K. Sales Technology, Relationship-Forging Tasks, and Sales Performance in Business Markets; University of North Carolina at Chapel Hill: Chapel Hill, NC, USA, 1999. [Google Scholar]
- Alharbi, S.; Drew, S. Using the technology acceptance model in understanding academics’ behavioural intention to use learning management systems. Int. J. Adv. Comput. Sci. Appl. 2014, 5, 143–155. [Google Scholar] [CrossRef]
- Vagnani, G.; Volpe, L. Innovation attributes and managers’ decisions about the adoption of innovations in organizations: A meta-analytical review. Int. J. Innov. Stud. 2017, 1, 107–133. [Google Scholar] [CrossRef]
- Alsaif, M. Factors Affecting Citizens’ Adoption of e-Government Moderated by Socio-Cultural Values in Saudi Arabia; University of Birmingham: Birmingham, UK, 2014. [Google Scholar]
- Pantano, E.; Di Pietro, L. Understanding consumer’s acceptance of technology-based innovations in retailing. J. Technol. Manag. Innov. 2012, 7, 1–19. [Google Scholar] [CrossRef]
- Thowfeek, M.H.; Jaafar, A. The influence of cultural factors on the adoption of e-learning: A reference to a public University in Sri Lanka. Appl. Mech. Mater. 2013, 263, 3424–3434. [Google Scholar] [CrossRef]
- Tian, M.; Deng, P.; Zhang, Y.; Salmador, M.P. How does culture influence innovation? A systematic literature review. Manag. Decis. 2018, 56, 1088–1107. [Google Scholar] [CrossRef]
- Lee, Y. Exploring Key Factors That Affect Consumers to Adopt e-Reading Services. Unpublished Master’s Thesis, Huafan University, Taipei, Taiwan, 2007. [Google Scholar]
- Hardgrave, B.C.; Davis, F.D.; Riemenschneider, C.K. Investigating determinants of software developers’ intentions to follow methodologies. J. Manag. Inf. Syst. 2003, 20, 123–151. [Google Scholar]
- Kristensen, S. Understanding Factors Influencing Danish Consumers’ Intention to Use Mobile Payment at Point-of-Sale’. Master’s Thesis, Aarhus University, Aarhus, Denmark, 2016. [Google Scholar]
- Koenig-Lewis, N.; Palmer, A.; Moll, A. Predicting young consumers’ take up of mobile banking services. Int. J. Bank Mark. 2010, 28, 410–432. [Google Scholar] [CrossRef]
- Tobbin, P.E. Modeling adoption of mobile money transfer: A consumer behaviour analysis. In Proceedings of the 2nd International Conference on Mobile Communication Technology for Development, Kampala, Uganda, 10–11 November 2010. [Google Scholar]
- Shih, C. Integrating Innovation Diffusion Theory and UTAUT to Explore the Influencing Factors on Teacher Adopt e-Learning System–with MOODLE as an Example. Unpublished Master’s Thesis, Dayeh University, Changhua, Taiwan, 2007. [Google Scholar]
- Thompson, B. Exploratory and Confirmatory Factor Analysis; American Psychological Association: Worcester, MA, USA, 2004. [Google Scholar]
- Mkansi, M.; Acheampong, E.A. Research philosophy debates and classifications: Students’ dilemma. Electron. J. Bus. Res. Methods 2012, 10, 132–140. [Google Scholar]
- Venkatesh, V.; Brown, S.A.; Bala, H. Bridging the qualitative-quantitative divide: Guidelines for conducting mixed methods research in information systems. MIS Q. 2013, 37, 21–54. [Google Scholar] [CrossRef]
- Duffy, M.; Chenail, R.J. Values in qualitative and quantitative research. Couns. Values 2009, 53, 22–38. [Google Scholar] [CrossRef]
- Thompson, R.L.; Higgins, C.A.; Howell, J.M. Personal computing: Toward a conceptual model of utilization. MIS Q. 1991, 15, 125–143. [Google Scholar] [CrossRef]
- Beatty, R.C.; Shim, J.P.; Jones, M.C. Factors influencing corporate web site adoption: A time-based assessment. Inf. Manag. 2001, 38, 337–354. [Google Scholar] [CrossRef]
- Soliman, K.S.; Janz, B.D. An exploratory study to identify the critical factors affecting the decision to establish Internet-based interorganizational information systems. Inf. Manag. 2004, 41, 697–706. [Google Scholar] [CrossRef]
- Fan, W.; Yan, Z. Factors affecting response rates of the web survey: A systematic review. Comput. Hum. Behav. 2010, 26, 132–139. [Google Scholar] [CrossRef]
- Nayak, M.; Narayan, K. Strengths and weakness of online surveys. IOSR J. Humanit. Soc. Sci. 2019, 24, 31–38. [Google Scholar]
- Zikmund, W.; Babin, B.; Carr, J.; Griffin, M. Business Research Methods, 9th ed.; South-Western Cengage Learning: Mason, OH, USA, 2013. [Google Scholar]
- Finstad, K. Response interpolation and scale sensitivity: Evidence against 5-point scales. J. Usability Stud. 2010, 5, 104–110. [Google Scholar]
- Waters, D.; Waters, C.D.J. Quantitative Methods for Business; Pearson Education Limited: London, UK, 2011. [Google Scholar]
- Kothari, C.R. Research Methodology: Methods and Techniques; New Age International: New Delhi, India, 2004. [Google Scholar]
- Field, A. Discovering Statistics Using SPSS: (and Sex and Drugs and Rock’n’Roll); Sage: London, UK, 2009. [Google Scholar]
- Coolican, H. Research Methods and Statistics in Psychology, 6th ed.; Routledge: London, UK, 2014. [Google Scholar]
- Gliem, J.A.; Gliem, R.R. Calculating, Interpreting, and Reporting Cronbach’s Alpha Reliability Coefficient for Likert-Type Scales. In Proceedins of the 2003 Midwest Research to Practice Conference in Adult, Continuing, and Community Education, Columbus, OH, USA, 8–10 October 2003. [Google Scholar]
- Warmbrod, J. Conducting, Interpreting, and Reporting Quantitative Research. In Proceedins of the Annual National Agricultural Education Research Conference (Pre-Session), New Orleans, LA, USA, 12 December 2001. [Google Scholar]
- George, D.; Mallery, M. Using SPSS for Windows Step by Step: A Simple Guide and Reference; Pearson Education: London, UK, 2003. [Google Scholar]
- Stafford, T.F.; Turan, A.H. Online tax payment systems as an emergent aspect of governmental transformation. Eur. J. Inf. Syst. 2011, 20, 343–357. [Google Scholar] [CrossRef]
- Sivo, S.A.; Saunders, C.; Chang, Q.; Jiang, J.J. How low should you go? Low response rates and the validity of inference in IS questionnaire research. J. Assoc. Inf. Syst. 2006, 7, 17. [Google Scholar] [CrossRef]
- Podsakoff, P.M.; MacKenzie, S.B.; Lee, J.-Y.; Podsakoff, N.P. Common method biases in behavioral research: A critical review of the literature and recommended remedies. J. Appl. Psychol. 2003, 88, 879. [Google Scholar] [CrossRef] [PubMed]
- Williams, B.; Onsman, A.; Brown, T. Exploratory factor analysis: A five-step guide for novices. Australas. J. Paramed. 2010, 8, 990399. [Google Scholar] [CrossRef]
- Jalil, K.; Zainuddin, Y. Validation of the theoretical framework for adoption of accounting information system using structural equation modelling. Int. J. Ind. Manag. 2015, 1, 1–10. [Google Scholar]
- Byrne, B.M. Structural Equation Modelling with AMOS: Basic Concepts, Applications, and Programming; Lawrence Erlbaum Associates: Mahwah, NJ, USA, 2001. [Google Scholar]
- Hair, J.; Black, B.; Babin, B.; Anderson, R.; Tatham, R. Multivariate Data Analysis; Pearson Prentice Hall: Upper Saddle River, NJ, USA, 2006. [Google Scholar]
- Holmes-Smith, P. Advanced Structural Equation Modelling Using AMOS. 2011. Available online: https://www.acspri.org.au/courses/advanced-structural-equation-modelling-using-amos (accessed on 11 April 2021).
- Holmes-Smith, P. Introduction to Structural Equation Modeling Using LISREL; ACSPRI-Winter Training Program: Perth, Australia, 2001. [Google Scholar]
- Arbuckle, J. AMOS 6.0 User’s Guide, Volume 541; AMOS Development Corporation: Chicago, IL, USA, 2005. [Google Scholar]
- Byrne, B.M. Structural Equation Modeling with LISREL, PRELIS, and SIMPLIS: Basic Concepts, Applications, and Programming; Psychology Press: London, UK, 1998. [Google Scholar]
- Hameed, M.A.; Counsell, S. Establishing relationships between innovation characteristics and IT innovation adoption in organisations: A meta-analysis approach. Int. J. Innov. Manag. 2014, 18, 1450007. [Google Scholar] [CrossRef]
- Venkatesh, V.; Davis, F.D. A theoretical extension of the technology acceptance model: Four longitudinal field studies. Manag. Sci. 2000, 46, 186–204. [Google Scholar] [CrossRef]
- Safa, N.S.; Sookhak, M.; Von Solms, R.; Furnell, S.; Ghani, N.A.; Herawan, T. Information security conscious care behaviour formation in organizations. Comput. Secur. 2015, 53, 65–78. [Google Scholar] [CrossRef]
- Ali, O.; Shrestha, A.; Chatfield, A.; Murray, P. Assessing information security risks in the cloud: A case study of Australian local government authorities. Gov. Inf. Q. 2020, 37, 101419. [Google Scholar] [CrossRef]
- Ali, O.; Shrestha, A.; Osmanaj, V.; Muhammed, S. Cloud computing technology adoption: An evaluation of key factors in local governments. Inf. Technol. People 2020, 34, 666–703. [Google Scholar] [CrossRef]
- Forman, C.; van Zeebroeck, N. Digital technology adoption and knowledge flows within firms: Can the Internet overcome geographic and technological distance? Res. Policy 2019, 48, 103697. [Google Scholar] [CrossRef]
- Gorman, S.P. Where are the Web factories: The urban bias of e–business location. Tijdschr. Voor Econ. Soc. Geogr. 2002, 93, 522–536. [Google Scholar] [CrossRef]
- Lin, H.-F.; Lin, S.-M. Determinants of e-business diffusion: A test of the technology diffusion perspective. Technovation 2008, 28, 135–145. [Google Scholar] [CrossRef]
- Zhu, K.; Kraemer, K.L. Post-adoption variations in usage and value of e-business by organizations: Cross-country evidence from the retail industry. Inf. Syst. Res. 2005, 16, 61–84. [Google Scholar] [CrossRef]
- Seyal, A.H.; Rahman, M.N.A. A preliminary investigation of e-commerce adoption in small & medium enterprises in Brunei. J. Glob. Inf. Technol. Manag. 2003, 6, 6–26. [Google Scholar]
- Tiwana, A.; Bush, A.A. A comparison of transaction cost, agency, and knowledge-based predictors of IT outsourcing decisions: A US-Japan cross-cultural field study. J. Manag. Inf. Syst. 2007, 24, 259–300. [Google Scholar] [CrossRef]
- Chaudhury, A.; Bharati, P. IT outsourcing adoption by small and medium enterprises: A diffusion of innovation approach. In Proceedings of the Americas Conference on Information Systems (AMCIS 2008), Toronto, ON, Canada, 14–17 August 2008. [Google Scholar]
- Hamad, F.; Farajat, S.; Hamarsha, A. Awareness and adoption of mobile technologies in the delivery of services in academic libraries in Jordan. Glob. Knowl. Mem. Commun. 2018, 67, 438–457. [Google Scholar] [CrossRef]
- Berkowsky, R.W.; Sharit, J.; Czaja, S.J. Factors predicting decisions about technology adoption among older adults. Innov. Aging 2017, 1, igy002. [Google Scholar] [CrossRef]
- Hargittai, E. Second-level digital divide: Mapping differences in people’s online skills. arXiv 2001, arXiv:0109068. [Google Scholar] [CrossRef]
- Czaja, S.J.; Charness, N.; Fisk, A.D.; Hertzog, C.; Nair, S.N.; Rogers, W.A.; Sharit, J. Factors predicting the use of technology: Findings from the center for research and education on aging and technology enhancement (CREATE). Psychol. Aging 2006, 21, 333. [Google Scholar] [CrossRef] [PubMed]
- Siren, A.; Knudsen, S.G. Older adults and emerging digital service delivery: A mixed methods study on information and communications technology use, skills, and attitudes. J. Aging Soc. Policy 2017, 29, 35–50. [Google Scholar] [CrossRef] [PubMed]
- Thiesse, F.; Staake, T.; Schmitt, P.; Fleisch, E. The rise of the “next-generation bar code”: An international RFID adoption study. Supply Chain. Manag. Int. J. 2011, 16, 328–345. [Google Scholar] [CrossRef]
- Modrák, V.; Moskvich, V. Impacts of RFID implementation on cost structure in networked manufacturing. Int. J. Prod. Res. 2012, 50, 3847–3859. [Google Scholar]
- Ghobakhloo, M.; Arias-Aranda, D.; Benitez-Amado, J. Adoption of e-commerce applications in SMEs. Ind. Manag. Data Syst. 2011, 111, 1238–1269. [Google Scholar] [CrossRef]
- Premkumar, G.; Roberts, M. Adoption of new information technologies in rural small businesses. Omega 1999, 27, 467–484. [Google Scholar] [CrossRef]
- Goode, S.; Stevens, K. An analysis of the business characteristics of adopters and non-adopters of World Wide Web technology. Inf. Technol. Manag. 2000, 1, 129–154. [Google Scholar] [CrossRef]
- Aiken, M.; Bacharach, S.B.; French, J.L. Organizational structure, work process, and proposal making in administrative bureaucracies. Acad. Manag. J. 1980, 23, 631–652. [Google Scholar]
- Nkhoma, M.Z.; Dang, D.; De Souza-Daw, A. Contributing factors of cloud computing adoption: A technology-organisation-environment framework approach. In Proceedings of the Proceedings of the European Conference on Information Management & Evaluation, Gdansk, Poland, 12–13 September 2013; pp. 180–188. [Google Scholar]
- Osyk, B.A.; Vijayaraman, B.; Srinivasan, M.; Dey, A. RFID adoption and implementation in warehousing. Manag. Res. Rev. 2012, 35, 904–926. [Google Scholar]
- Premkumar, G.; Ramamurthy, K. The role of interorganizational and organizational factors on the decision mode for adoption of interorganizational systems. Decis. Sci. 1995, 26, 303–336. [Google Scholar]
- Hambrick, D.C. The field of management’s devotion to theory: Too much of a good thing? Acad. Manag. J. 2007, 50, 1346–1352. [Google Scholar] [CrossRef]
- Aljawarneh, N.M.; Sokiyna, M.; Obeidat, A.M.; Alomari, K.A.K.; Alradaideh, A.T.; Alomari, Z.S. The Role of CRM fog computing on innovation and customer service quality: An empirical study. Mark. Manag. Innov. 2020, 2, 286–297. [Google Scholar] [CrossRef]
- Tortonesi, M.; Govoni, M.; Morelli, A.; Riberto, G.; Stefanelli, C.; Suri, N. Taming the IoT data deluge: An innovative information-centric service model for fog computing applications. Future Gener. Comput. Syst. 2019, 93, 888–902. [Google Scholar] [CrossRef]
- Saharan, K.; Kumar, A. Fog in comparison to cloud: A survey. Int. J. Comput. Appl. 2015, 122, 10–12. [Google Scholar]
- Prokhorenko, V.; Babar, M.A. Architectural resilience in cloud, fog and edge systems: A survey. IEEE Access 2020, 8, 28078–28095. [Google Scholar] [CrossRef]
- Preden, J.S.; Tammemäe, K.; Jantsch, A.; Leier, M.; Riid, A.; Calis, E. The benefits of self-awareness and attention in fog and mist computing. Computer 2015, 48, 37–45. [Google Scholar]
- Attiya, I.; Zhang, X. Cloud Computing Technology: Promises and Concerns. Int. J. Comput. Appl. 2017, 159, 32–37. [Google Scholar]
- Tuli, S.; Mahmud, R.; Tuli, S.; Buyya, R. FogBus: A blockchain-based lightweight framework for edge and fog computing. J. Syst. Softw. 2019, 154, 22–36. [Google Scholar] [CrossRef]
- Brous, P.; Janssen, M.; Herder, P. The dual effects of the Internet of Things (IoT): A systematic review of the benefits and risks of IoT adoption by organizations. Int. J. Inf. Manag. 2020, 51, 101952. [Google Scholar] [CrossRef]
- Tabrizchi, H.; Rafsanjani, M.K. A survey on security challenges in cloud computing: Issues, threats, and solutions. J. Supercomput. 2020, 76, 9493–9532. [Google Scholar] [CrossRef]
- Sharma, R.; Gourisaria, M.K.; Patra, S. Cloud Computing—Security, Issues, and Solutions. In Communication Software and Networks; Springer: Berlin/Heidelberg, Germany, 2021; pp. 687–700. [Google Scholar]
- Mthunzi, S.N.; Benkhelifa, E.; Bosakowski, T.; Guegan, C.G.; Barhamgi, M. Cloud computing security taxonomy: From an atomistic to a holistic view. Future Gener. Comput. Syst. 2020, 107, 620–644. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).