Abstract
This study examines the balance between urban transportation security and supply chain efficiency amid global disruptions like the COVID-19 pandemic, attacks on maritime lanes, and geopolitical conflicts. The authors combine bibliometric network analysis and natural language processing (NLP) to review scholarly literature from 2017 to 2023. This approach identifies and visualizes evolving thematic trends. Findings reveal a shift towards integrating advanced technologies, such as blockchain, AI, and IoT, to enhance security without compromising efficiency. This study highlights the significance of integrating urban planning principles and sustainable practices to enhance transportation security and supply chain efficiency within urban environments. Actionable insights for policymakers and supply chain managers emphasize the adoption of integrated, technology-driven security solutions to foster resilient and sustainable supply chains. This research contributes to academic discourse by refining the understanding of evolving priorities in transportation security and supply chain management, offering both theoretical and practical implications for secure and efficient global supply chains.
1. Introduction
The secure and uninterrupted transportation of goods is vital for global supply chains. Efficiency is not just an operational goal but a key determinant of economic vitality and competitiveness [1]. Urban planning and development are crucial for optimizing transportation routes, reducing congestion, and enhancing supply chain efficiency in metropolitan areas. Global supply chains form a complex network involving diverse stakeholders, including businesses, governments, non-profit organizations, and individuals. These stakeholders operate from local communities to international trade corridors. In this multifaceted network, transportation threats have escalated, necessitating security as an integral part of supply chain management. Hence, there is a critical need to continually bolster urban resilience through strategic planning and advanced security measures, ensuring the well-being of urban populations during disruptions. Ensuring the safe transit of goods, protecting sensitive information, and maintaining confidentiality are crucial for safeguarding the entire supply chain ecosystem [2].
This study employs bibliometric network analysis and natural language processing (NLP) techniques to uncover thematic trends in the intersection of transportation security and supply chain efficiency. This novel approach to systematic reviews provides a comprehensive analysis of existing literature, identifying the evolving priorities and gaps in the field. Globalization has created a modern supply chain that is a complex network of activities, resources, and technologies aimed at producing and moving goods efficiently. Multimodal transportation and security are central to this network, facilitating the physical flow of goods across geographic boundaries. Figure 1 illustrates how transportation security integrates into supply chains, highlighting the dynamic flow of materials and products essential for both efficiency and security. Secure transportation ensures product delivery to stakeholders and significantly enhances supply chain agility and resilience. Urban mobility solutions, including sustainable transport options, play a vital role in maintaining efficient and secure supply chains. Transportation security includes physical security protocols and cybersecurity measures to mitigate risks of theft, tampering, and disruptions. Transportation security, therefore, is not just about asset protection but is instrumental in maintaining the seamless operation of global supply chains, influencing efficiency, reliability, and stakeholder trust.
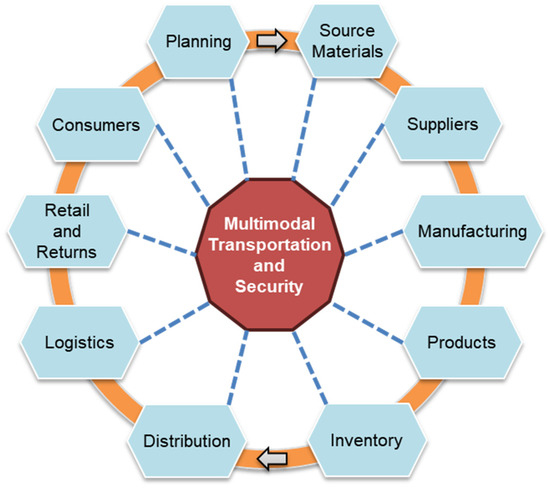
Figure 1.
Depiction of how transport security relates to supply chains.
Recent global disruptions, like the COVID-19 pandemic, have exposed vulnerabilities in supply chains. Delays in critical medical supplies during the pandemic highlighted the fragility of these networks [3]. These challenges emphasize the need for strategies that are robust, secure, resilient, and adaptable, especially during crises [4]. Stringent security protocols are essential but can lead to operational delays, increased costs, and complexity in supply chain operations [5]. Hence, balancing security and efficiency is crucial to mitigate vulnerabilities and maintain supply chain responsiveness and profitability.
Traditionally, transportation has focused on speed and cost-effectiveness, emphasizing rapid delivery times and minimizing expenses [6]. However, global interconnectedness has introduced complexities and threats, prompting a shift in foundational assumptions about the logistics of transportation. Current security concerns include piracy, geopolitical conflicts, and escalating cyber threats, necessitating a reconfiguration of transportation strategies to balance efficiency, cost, and security.
This study aims to decipher the interplay between transportation security and supply chain efficiency. The methodology combines bibliometric network analysis and bigram distribution analysis using NLP to visualize and recognize thematic trends and patterns. The study hypothesizes an intrinsic interdependency between supply chain efficiency and transportation security, with decisions and policies in one area significantly impacting the other.
This research contributes academically and practically by examining how transportation security has evolved and its impact on supply chain efficiency. Reviewing security measures from the pre-COVID era (2017–2019) to the more recent landscape (2020–2023) helps understand their symbiotic relationship. By not restricting the analysis to specific geographic locations or transportation modes, the study presents a generalized overview applicable across various contexts and scales. Existing literature lacks a comprehensive understanding of how transportation security directly correlates with supply chain efficiency. This study addresses this gap by employing an algorithmic workflow that includes text cleaning and bigram analysis, unveiling thematic shifts and priorities in recent literature. The insights provide clear directions for policymakers and practitioners in developing resilient, secure, and efficient supply chains in today’s volatile global market.
The structure of the remainder of this study is as follows: Section 2 synthesizes the literature on supply chain management, focusing on efficiency and security. Section 3 explains the methodological approach. Section 4 presents the findings with visual depictions of the thematic landscape. Section 5 offers a deeper interpretation of the results. Section 6 concludes the study, reflecting on its implications and suggesting pathways for future research.
2. Literature Review
This section reviews the literature on supply chain management, focusing on the interplay between transportation security and supply chain efficiency.
2.1. Themes and Theories
The literature reveals several key themes and theories relevant to this intersection:
Transportation Security: This involves safeguarding goods and raw materials within the supply chain from threats and disruptions [2]. Dynamic security measures are essential for adapting to evolving threats. Crisis response is a critical component of transportation security, encompassing contingency plans for various incidents to minimize supply chain impacts. Supply chain security practices include customizable policies and protocols unique to each organization, aimed at preventing, detecting, and responding to threats within the supply chain [2].
Risk Management: This area focuses on identifying, assessing, and mitigating risks in transportation to minimize the occurrence and impact of disruptions. Effective risk management strategies are crucial for maintaining supply chain efficiency while ensuring security [7].
Supply Chain Resilience: This concept refers to the ability to withstand and recover from disruptions. Strategies for resilience include alternative routes, redundant infrastructure, and enhanced collaboration among supply chain partners [8].
Supply Chain Efficiency: This involves optimizing operational procedures for timely, cost-effective, and robust production and distribution. Key efficiency metrics include inventory turnover, fill rate, order fulfilment, lead time, cost per order, return on assets, and environmental metrics like carbon footprint [9]. Reliable transportation is crucial for the cost-effective movement within supply chains, facilitating business operations, growth, and competitiveness.
2.2. Historical Perspective
Transportation security has evolved significantly over time, influenced by technological advancements, global events, and changing threats [10]. Initially, physical security measures such as roadblocks for caravans and marshals for trains were predominant [11,12,13]. The rise of air travel introduced basic measures like metal detectors [14]. Post-9/11, the Federal Aviation Administration (FAA) overhauled security systems to include advanced metal detectors and X-ray machines [15,16,17].
Modern Security Measures: Modern transportation security incorporates technologies like Transport Layer Security (TLS) and Datagram Transport Layer Security (DTLS) for data protection [18] and the Internet of Things (IoT) for real-time infrastructure monitoring [19]. Emerging technologies like artificial intelligence (AI) and machine learning (ML) are reshaping security, with applications such as robotic dogs for substance detection and uncrewed vehicles for threat management [20,21,22,23,24]. Blockchain-based smart contracts offer promising solutions for enhanced transportation security through real-time monitoring and efficient information sharing [25,26,27,28,29].
Organizational Culture and Standardization: An organizational culture centered on security, along with effective policies, can mitigate security breaches and disruptions [30]. However, security measures vary across industries and regions, necessitating tailored approaches [31,32,33]. Collaborative efforts and information sharing among stakeholders are vital for supply chain security [5]. Standardization driven by organizations like the International Civil Aviation Organization (ICAO) and the International Maritime Organization (IMO) is crucial for harmonizing global transportation security measures [34]. Adherence to standards like ISO 28001 helps identify and address security vulnerabilities [35,36,37].
Technological Innovations: The literature highlights the potential for innovation and technology in enhancing security and efficiency in supply chains [38]. Intellectualization, innovation, and modern technologies are key to addressing modern supply chain complexities [39,40,41]. Blockchain and IoT are pivotal in enhancing security and efficiency, offering real-time monitoring and data collection.
Key Performance Indicators (KPIs): Specific KPIs quantify the efficacy of transportation security protocols. These include incident rates of theft and tampering, percentage of on-time deliveries unaffected by security issues, frequency of security audits, and number of security breaches successfully identified and thwarted [42]. The ratio of security-related costs to the value of protected goods provides insight into the economic impact of security investments.
Despite extensive research on transportation security and supply chain efficiency, there is a notable gap in empirical studies that quantitatively measure the impact of security measures on supply chain performance metrics. This gap indicates a need for further research to provide a systematic and quantitative understanding of transport security within the supply chain narrative.
3. Methodology
The study complies with the Preferred Reporting Items for Systematic Reviews and Meta-Analyses (PRISMA) statement [43]. The study additionally employs bibliometric analysis to examine the interplay between transportation security and supply chain efficiency. The methodology includes database selection, search strategy, inclusion and exclusion criteria, bibliometric analysis, and advanced natural language processing (NLP) techniques.
3.1. Database Selection and Search Strategy
The study utilized Scopus and Web of Science as the core databases for their extensive repositories of scholarly works on transportation security and supply chain efficiency. Systematic literature reviews (SLRs) widely use these databases because of their high-quality content, comprehensive indexing, citation tracking, and advanced search capabilities. This review also utilized Google Scholar to identify any relevant literature not covered by the core databases. The search strategy employed the Boolean command “supply chain” AND “security” and “transportation” OR “transport” to retrieve articles. The search focused on literature from 2017 to 2023 to capture trends and developments pre- and post-COVID. This yielded 1228 articles, which a filter narrowed down to 680 by focusing on journal articles and books written in English.
3.2. Inclusion and Exclusion Criteria
The initial screening prioritized journal articles that directly addressed the interplay between transportation security and supply chain efficiency. The authors reviewed titles and abstracts for relevance, and removed duplicates, resulting in 59 relevant articles. A detailed review of the introductory and concluding sections of these articles further reduced the number to 32, which met the criteria of discussing both transportation security and supply chain efficiency. Table 1 in the results section enumerates the articles forming the basis of this thematic review.
3.3. Bibliometric Analysis
The study employed VOSviewer software (version 1.6.20) to conduct a bibliometric analysis of the initial search results [44]. The bibliometric analysis produced a network map visualization based on the co-occurrence of important terms. This map illustrated the frequency and relationships of keywords within the literature, helping to identify key themes and sub-themes. The advanced clustering algorithms of the tool grouped related terms into clusters, with the size of nodes and thickness of links indicating the frequency and strength of relationships. This analysis highlighted the overall thematic structure and trends within the research fields of transportation security and supply chain efficiency.
3.4. Thematic Categorization
The study categorized the corpus into pre- and post-COVID temporal cohorts to facilitate a comparative thematic analysis. This division allowed for an examination of trends and shifts due to the pandemic’s impact. Thematic categorization employed bigram analysis, a method in text analytics that identifies pairs of adjacent words to illuminate syntactic and semantic relationships. This method surpasses single-word extraction by providing a deeper understanding of recurring themes within the literature corpus. The thematic categorization utilized advanced NLP techniques through the Python programming language, leveraging libraries such as ‘re’ for regular expressions, NLTK for language processing tasks, and PyPDF2 for handling PDF files [45]. The NLP protocol involved several steps:
- Stop Word Removal: Filtering out common stop words and irrelevant terms to enhance analytical precision.
- Bigram Extraction: Identifying the top five bigrams by frequency for each article after applying lemmatization to convert words to their root forms.
- Bigram Aggregation: Pooling extracted bigrams across all articles within each document group and ranking them by frequency.
- Frequency Analysis: Highlighting the most prominent themes and terms within the literature corpus.
- Distribution Analysis: Examining the frequency and context of top bigrams to reveal thematic shifts over time.
- Visualization: Generating word clouds and distribution graphs to visually represent the predominant themes within each temporal cohort.
The visualization of bigrams facilitated a nuanced understanding of the interplay between terms, highlighting the interconnected conceptual landscape of transportation security and supply chain efficiency. The analysis extended beyond frequency counts to include contextual examinations of sentences containing these bigrams, ensuring qualitative relevance.
3.5. Algorithmic Workflow
The algorithmic workflow depicted in Figure 2 represents the methodological sequence crafted to assess and interpret the literature.
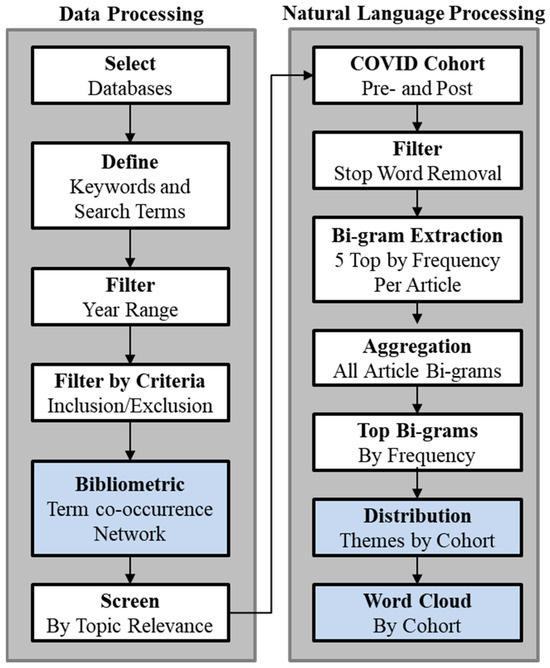
Figure 2.
Algorithmic workflow to identify and visualize themes.
This workflow comprised two key analytical sections: Data Processing and NLP with Visualization.
Data Processing:
- Step 1: Database Identification—identifying databases rich in relevant research articles.
- Step 2: Keyword Formulation—creating a list of search terms.
- Step 3: Temporal Filter—conducting searches within the specified year range.
- Step 4: Criteria-Based Filtering—screening search results based on inclusion and exclusion criteria.
- Step 5: Bibliometric Analysis—generating term co-occurrence networks.
- Step 6: Topical Relevance Filtering—ensuring selected literature contributes meaningfully to the objectives of the study.
NLP and Visualization:
- Step 1: Corpus Bifurcation—segmenting literature into pre- and post-COVID temporal cohorts for trend analysis.
- Step 2: Stop Word Removal—enhancing focus on content-rich words.
- Step 3: Bigram Extraction—identifying significant word pairs.
- Step 4: Bigram Aggregation—aggregating and ranking bigrams by frequency.
- Step 5: Frequency Analysis—highlighting prominent themes.
- Step 6: Distribution Analysis—identifying thematic shifts over time.
- Step 7: Visualization—creating word cloud visual representations of thematic data.
This detailed methodology enables a reproducible approach to extracting and analyzing data, providing a robust understanding of the thematic landscape within transportation security and supply chain efficiency.
4. Results
This section synthesizes the key findings from the literature, highlighting recurrent themes and patterns that explain the intricate interplay between transportation security and supply chain efficiency. Figure 3 presents a co-occurrence term map for the filtered corpus, generated using the VOSviewer tool. The map visualizes the relationships and frequencies of key terms within the dataset, illustrating the thematic structure of the combined research fields.
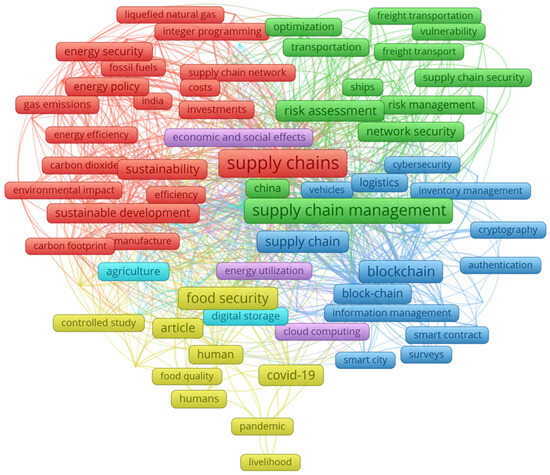
Figure 3.
Keyword network of the filtered corpus.
The map displays six clusters, each representing a different thematic area within the research fields:
- Red Cluster: the main themes are sustainability and energy with key terms including “energy security”, “sustainable development”, “carbon footprint”, and “environmental impact”.
- Green Cluster: the main themes are risk and security within the supply chain with key terms being “supply chain security”, “risk assessment”, “network security”, and “freight transportation”.
- Blue Cluster: the main themes are technology and data management with key terms being “blockchain”, “cybersecurity”, “internet of things”, and “smart contract”.
- Yellow Cluster: the main themes are food security and the impacts of the COVID-19 pandemic with key terms being “food quality”, “pandemic”, and “livelihood”.
- Purple Cluster: the main themes are economic and social effects with key terms being “energy utilization” and “health care”.
- Light Blue Cluster: as the smallest cluster, setting the minimum cluster size parameter merged it with the other clusters; specifically, “agriculture” merged with the yellow cluster and “digital storage” merged with the purple cluster.
The terms “supply chain”, “supply chains”, and “supply chain management” appear centrally in the map, reflecting the search criteria and indicating their high frequency of occurrence within the corpus. These terms connect to multiple clusters, reflecting their interdisciplinary nature and centrality to the research field. The lines connecting the terms represent the co-occurrence relationships, with thicker lines indicating higher co-occurrence frequencies, representing stronger connections. The dense network of connections highlights the interrelatedness of various topics within the field. The presence of terms like “blockchain”, “smart contract”, and “cybersecurity” suggests the growing importance of digital technologies and data security in supply chain management and transportation security. The variety of terms and clusters depicted in the map highlights the diverse research focus areas within these fields, ranging from sustainability and energy efficiency to risk management, technological advancements, and the socio-economic impacts of the COVID-19 pandemic.
The thematic analysis revealed a progression from a primary focus on balancing technology-driven security with operational efficiency to a more integrated approach that encompasses environmental sustainability and cyber resilience. Figure 4 visually represents this shift, which illustrates the predominant keywords from the articles published in both the pre- and post-COVID cohorts. The word cloud in Figure 4 highlights the frequency of specific terms, providing a visual representation of thematic saturation across different periods.
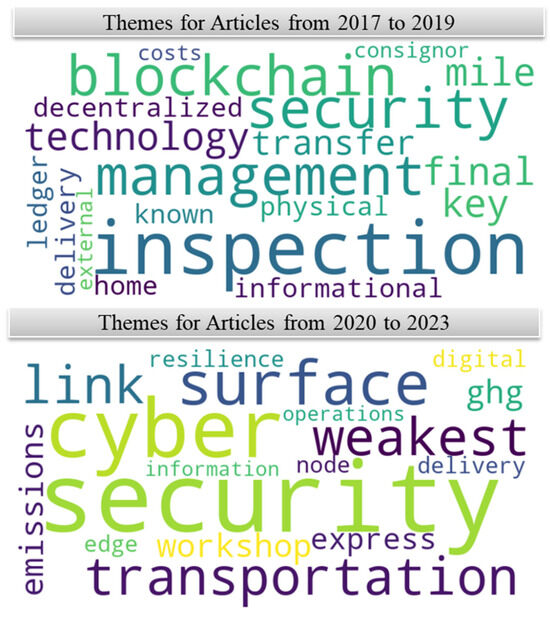
Figure 4.
Word cloud of keywords from articles published in the pre- and post-COVID cohort.
The study categorized themes into five main areas, summarized in Table 1.

Table 1.
Themes revealed and their representative literature.
Table 1.
Themes revealed and their representative literature.
| Category | Theme | Sample Articles |
|---|---|---|
| Emerging Technologies | Blockchain and biometrics are pivotal in enhancing security and transparency in transportation | [1,4,5,26,27,28,29,39,40,41,46,47,48] |
| Environmental Considerations | Integrating environmental sustainability with security in transportation is crucial for resilient supply chains. | [49,50] |
| E-commerce Challenges | The surge in e-commerce demands innovative security strategies for efficient and safe package delivery. | [51,52] |
| Standardization and Regulation Needs | Consistent standards and regulations are vital for ensuring security, especially in international supply chains. | [30,35,36,37,53,54] |
| Practical Insights from Real-World Scenarios | Empirical studies offer valuable insights into the practical challenges and potentials of transportation security systems. | [10,31,32,33,34,55,56,57] |
In the pre-COVID cohort, the predominant themes centered on integrating technology and data analytics to balance transportation security and supply chain efficiency. Figure 5 presents the top bigrams from the pre-COVID cohort, highlighting the key themes and their contextual relationships during this period. This visualization aids in understanding the primary concerns and focus areas of research before the pandemic. Discussions focused on advanced technologies like blockchain, security key transfers, effective management practices, and comprehensive inspection protocols. The focus was on leveraging these elements to enhance security measures in transportation while optimizing supply chain operations.
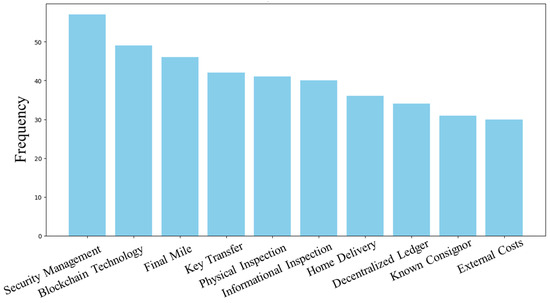
Figure 5.
Top bigrams from articles published in the pre-COVID cohort.
In the post-COVID cohort, the themes evolved to include environmental sustainability (e.g., keywords include “emissions”, and “ghg” meaning greenhouse gas) and cyber resilience. Figure 6 showcases the top bigrams from the post-COVID cohort, highlighting the thematic shifts and new priorities that emerged in the literature. This figure helps illustrate how the pandemic influenced the focus of research towards more holistic and resilient supply chain strategies. That is, the literature expanded to address not only the dual objectives of security and efficiency but also the broader goal of creating a resilient and sustainable supply chain ecosystem. This shift reflects a growing recognition of the need to adapt transportation security strategies to contemporary challenges like environmental sustainability and the increasing threat of cyberattacks.
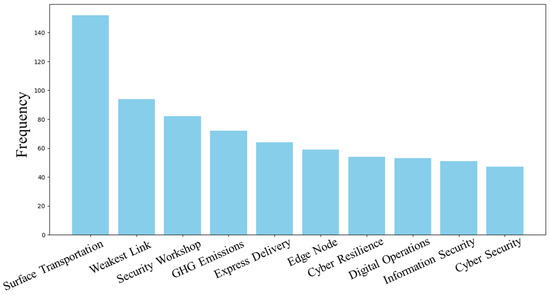
Figure 6.
Top bigrams from articles published in the post-COVID cohort.
These visualizations serve as integral algorithmic tools that distill complex data into visual formats, enabling humans to immediately recognize predominant keywords that encapsulate themes within the literature. The word cloud emphasizes the frequency of specific terms, providing a visual representation of thematic saturation. The bigram distribution highlights the contextual relationships between key terms, offering insights into the interplay of concepts relevant to transportation security and supply chain efficiency.
Overall, the thematic analysis revealed a shift from a focus on technology-driven security and operational efficiency to an integrated approach that includes sustainability and cyber resilience. The need to continuously evolve in response to technological advancements and environmental considerations compounds the challenges of managing a secure, efficient, and adaptable supply chain and transportation system.
5. Discussion
This analysis goes beyond merely aggregating existing studies to provide a refined and detailed examination of the complex interplay between transportation security and supply chain efficiency. By employing NLP techniques, the study dissected the literature to reveal prevailing themes and the intricate relationships and impacts these areas have on one another. This approach uncovered the subtle dynamics that underpin the interaction between robust security measures and the pursuit of operational efficiency within supply chains.
The co-occurrence term map of the bibliometric analysis enriches this analysis by visually representing the relationships and frequencies of key terms within the dataset. Central themes such as “supply chains”, “supply chain management”, and “supply chain security” illustrate their interdisciplinary connections and importance within the research field. The identified clusters, color-coded to distinguish different thematic areas, reveal the intricate links among sustainability, risk management, and technological advancements related to transportation security and supply chain efficiency.
The identified themes advocate for a harmonized approach to transportation security and supply chain efficiency. The selected literature reveals a spectrum of themes from conventional security measures to innovative technologies. Strategies for adapting supply chains to evolving market conditions were diverse, with thorough analyses of various supply chain efficiency metrics. However, a notable gap was the infrequent integration of security and efficiency perspectives, with most studies focusing on one aspect. The bibliometric map highlights the diverse research focus areas within the field, ranging from sustainability and energy efficiency to risk management, technological advancements, and the socio-economic impacts of the COVID-19 pandemic. The central position of terms related to digital transformation, such as “blockchain” and “cybersecurity”, indicates the growing importance of integrating advanced technologies into supply chain strategies.
The methodologies in the reviewed literature varied from empirical data analysis to theoretical explorations. This diversity, while enriching the discourse, posed challenges in synthesizing a unified understanding. Notably, literature from 2017–2019 demonstrated a limited focus on environmental sustainability. The growing concern for environmental sustainability necessitates that policymakers align transportation security measures with green initiatives. Incorporating urban green spaces and sustainable land use practices can mitigate the environmental impact of transportation activities, promoting a healthier urban climate. As sustainability gains prominence, organizations must align their supply chain and transportation security strategies with eco-friendly practices, such as optimizing delivery routes and utilizing renewable energy sources.
Effective transportation security should be comprehensive, blending traditional measures with advanced technologies like blockchains and drones. Urban energy solutions, such as renewable energy sources for transportation, are essential for creating sustainable and resilient urban supply chains. Policymakers need to craft policies that encompass these diverse elements. The shift in scholarly focus toward technologies that bolster both security and efficiency, particularly in publications from 2020 to 2023, highlights the need for integrated frameworks. With the rapid evolution of technology, organizations must develop dynamic security measures to address emerging threats. A multi-layered security approach, combining novel technologies with traditional methods can provide robust protection. Integrating circular economy principles within urban logistics can further enhance the sustainability and resilience of supply chains. The concept of the “weakest link” in supply chain security suggests the need for proactive risk assessments and security audits, extending beyond mere legal compliance.
The literature suggests that organizations should prioritize digital transformation to enhance both efficiency and security. This includes cybersecurity training, secure data exchange protocols, and regular updates to digital infrastructure. With the rise of e-commerce and digital supply chains, threats have increasingly become technological. Investments in advanced technologies are crucial for countering these evolving digital threats. Furthermore, the complexity of supply chain security calls for collaborative efforts. Public-private partnerships can share resources and knowledge, foster innovation, and enhance overall security. However, regional limitations and a scarcity of empirical studies further restrict the generalizability and practical applicability of these findings.
This research had some limitations. The bigram-based thematic analysis, while foundational, depends on the depth of the existing literature and lacks direct real-world case studies linking transportation security and supply chain efficiency. The absence of data to measure the impact of transportation security on common supply chain efficiency metrics limits the conclusiveness of the thematic analysis. The compartmentalization of technology, business operations, and economic factors hinders a holistic perspective, creating interdisciplinary gaps.
The focus on peer-reviewed material was deliberate to ensure the scientific rigor and reliability of the findings, and to identify gaps in the academic literature that would inform future research directions. The authors acknowledge that while industry reports and white papers can provide valuable practical perspectives, they often lack the scientific validation necessary for a rigorous academic review. Additionally, industry literature may sometimes be based on proprietary data or emphasize opinions and experiences that, while valuable, are not universally applicable or scientifically verified. Concentrating on peer-reviewed sources avoided the risk of incorporating biased or anecdotal evidence that could dilute the scientific rigor of this review.
Future research should focus on conducting empirical studies to validate the findings and explore new algorithms to evaluate the benefits and costs of implementing advanced security technologies in various supply chain contexts. These recommendations aim to fill the remaining gaps and contribute to a holistic understanding of the strategic importance of transportation security in sustaining efficient and resilient supply chains. This review sets the stage for future iterations to incorporate emerging studies. Furthermore, surveys and case studies documenting organizational experiences with enhanced transport security measures could provide qualitative insights into this dynamic.
6. Conclusions
This study demonstrates that transportation security and supply chain efficiency are not inherently conflicting. Properly implemented security strategies can enhance supply chain efficiency, while inadequate security measures can hinder it. The findings highlight the importance of urban planning and sustainable city initiatives in creating resilient and efficient transportation networks. Exploring the influence of environmental sustainability on transportation security and supply chain efficiency is increasingly pertinent. Urban resilience and climate adaptation strategies should be integral to future transportation and supply chain policies to address the challenges posed by urbanization and environmental changes. The bibliometric analysis reinforces these insights by visually representing the relationships and frequencies of key terms within the literature, highlighting central themes such as “supply chain management”, “sustainability”, and “blockchain”. This visualization highlights the interdisciplinary connections and the importance of integrating advanced technologies and sustainable practices into supply chain strategies. A key finding is that traditional security practices, such as physical and informational inspections, are indispensable but can sometimes impede supply chain velocity. A balance is essential to ensure security without significantly sacrificing efficiency. Advanced technologies like blockchain offer innovative approaches to enhancing security without undermining efficiency. They facilitate transparent and secure monitoring to streamline operations and reduce audit-related expenses. Bigrams like “Final Mile” and “Known Consignor” highlight the link between security effectiveness and operational efficiency. Streamlined operations can bolster security by minimizing vulnerabilities. Balancing security measures with economic viability and environmental sustainability adds complexity. While security implementations incur costs, they can yield efficiency gains, reducing losses from theft, fraud, and regulatory penalties.
The findings of this study illuminate several avenues through which policymakers can draft more effective regulations, standards, and action plans to bolster transportation security and supply chain efficiency. By identifying key technological innovations and security practices that enhance supply chain resilience without compromising efficiency, this research offers a foundation for developing comprehensive policies to integrate the latest advancements in security technologies. Moreover, this study highlights the limitations of existing policies, particularly in adapting to the rapidly evolving landscape of global trade and technology. The research suggests that an agile, technology-forward approach to policy formulation could bridge these gaps, facilitating more resilient and efficient supply chains. Stakeholders, from government regulators to supply chain managers and technology providers, stand to benefit from these insights. By leveraging the findings of this study, policymakers can create a more secure, efficient, and sustainable global supply chain network. In particular, policymakers could encourage the adoption of advanced security technologies through incentives or subsidies, especially in critical supply chain sectors. Supply chain managers should consider adopting a layered security approach and investing in continuous training to keep pace with technological advancements.
Author Contributions
Conceptualization, E.J. and R.B.; methodology, E.J. and R.B.; software, E.J. and R.B.; validation, E.J. and R.B.; formal analysis, E.J. and R.B.; investigation, E.J. and R.B.; resources, E.J. and R.B.; data curation, E.J. and R.B.; writing—original draft preparation, R.B.; writing—review and editing, E.J. and R.B.; visualization, E.J. and R.B.; supervision, R.B.; project administration, R.B. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
This article includes the original contributions presented in the study.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Kulik, V.A.; Marchuk, V.Y.; Harmash, O.M.; Karpun, O.V.; Perederii, N.M. Security Management of Intermodal Transportation in Conditions of Sustainable Development of Global Supply Chains. Electron. Sci. Pract. Publ. Econ. Sci. 2022, 12, 45–56. [Google Scholar] [CrossRef]
- Zailani, S.H.; Subaramaniam, K.S.; Iranmanesh, M.; Shaharudin, M.R. The impact of supply chain security practices on security operational performance among logistics service providers in an emerging economy: Security culture as moderator. Int. J. Phys. Distrib. Logist. Manag. 2015, 45, 652–673. [Google Scholar] [CrossRef]
- Okafor, U.G.; Olalaye, M.A.; Asobara, H.C.; Umeodinka, E.F. Global impact of COVID-19 pandemic on public health supply chains. In Science-Based Approaches to Respond to COVID and Other Public Health Threats; Guerrero, E., Ed.; IntechOpen: London, UK, 2021; p. 280. [Google Scholar]
- Nanda, S.K.; Panda, S.K.; Dash, M. Medical supply chain integrated with blockchain and IoT to track the logistics of medical products. Multimed. Tools Appl. 2023, 82, 32917–32939. [Google Scholar] [CrossRef] [PubMed]
- Koliousis, I.G.; Tanveer, U.; Ishaq, S. A Conceptual Information Sharing Framework to Improve Supply Chain Security Collaboration. Int. J. Value Chain. Manag. 2020, 11, 346–365. [Google Scholar] [CrossRef]
- Stank, T.P.; Goldsby, T.J. A Framework for Transportation Decision Making in an Integrated Supply Chain. Supply Chain. Manag. Int. J. 2000, 5, 71–78. [Google Scholar] [CrossRef]
- Yang, Y.-C. Impact of the container security initiative on Taiwan’s shipping industry. Marit. Policy Manag. 2010, 37, 699–722. [Google Scholar] [CrossRef]
- Gould, J.E.; Macharis, C.; Haasis, H.-D. Emergence of security in supply chain management literature. J. Transp. Secur. 2010, 3, 287–302. [Google Scholar] [CrossRef]
- Chopra, S.; Meindl, P. Supply Chain Management: Strategy, Planning, and Operation; Pearson: London, UK, 2014; p. 516. [Google Scholar]
- Alshurideh, M.T.; Kurdi, B.A.; Alzoubi, A.A.; Al-Okaily, M. The Impact of Transportation Reliability on Supply Chain Efficiency at UAE Maritime Industry. Int. J. Bus. Anal. Secur. 2022, 2, 141–154. [Google Scholar] [CrossRef]
- Schivelbusch, W. The Railway Journey: The Industrialization of Time and Space in the Nineteenth Century; University of California Press: Oakland, CA, USA, 2014; p. 248. [Google Scholar]
- Casadevall, A. Antibody-based vaccine strategies against intracellular pathogens. Curr. Opin. Immunol. 2018, 53, 74–80. [Google Scholar] [CrossRef]
- Candra, E.; Azmi, A.; Gunawati, A. Position and Protection of Association Rights Security Unit in Human Rights Perspective According to the Basic State Law of the Republic of Indonesia Year 1945. JHR (J. Huk. Replik) 2021, 9, 157–171. [Google Scholar] [CrossRef]
- Flitton, G.; Breckon, T.P.; Megherbi, N. A 3D extension to cortex like mechanisms for 3D object class recognition. In Proceedings of the 2012 IEEE Conference on Computer Vision and Pattern Recognition, Providence, RI, USA, 16–21 June 2012. [Google Scholar]
- Blalock, G.; Kadiyali, V.; Simon, D.H. The impact of post-9/11 airport security measures on the demand for air travel. J. Law Econ. 2007, 50, 731–755. [Google Scholar] [CrossRef]
- Seidenstat, P. Terrorism, airport security, and the private sector. Rev. Policy Res. 2004, 21, 275–291. [Google Scholar] [CrossRef]
- Karşigil, E.; Savaş, A.T.E.Ş. Security Control Process Modeling during the COVID-19 Pandemic: Example of Esenboğa Airport. Akıllı Ulaşım Sist. Uygulamaları Derg. 2022, 5, 188–199. [Google Scholar] [CrossRef]
- Holz, R.; Sheffer, Y.; Saint-Andre, P. Recommendations for Secure Use of Transport Layer Security (TLS) and Datagram Transport Layer Security (DTLS); RFC 7525; RFC Editor: Marina del Rey, CA, USA, 2015. [Google Scholar]
- Nižetić, S.; Šolić, P.; Gonzalez-De, D.L.-D.-I.; Patrono, L. Internet of Things (IoT): Opportunities, issues and challenges towards a smart and sustainable future. J. Clean. Prod. 2020, 274, 122877. [Google Scholar] [CrossRef] [PubMed]
- Wang, F.; Casalino, L.P.; Khullar, D. Deep learning in medicine—Promise, progress, and challenges. JAMA Intern. Med. 2019, 179, 293–294. [Google Scholar] [CrossRef] [PubMed]
- Morosan, C. Theoretical and empirical considerations of guests’ perceptions of biometric systems in hotels: Extending the technology acceptance model. J. Hosp. Tour. Res. 2012, 36, 52–84. [Google Scholar] [CrossRef]
- Nyale, D.; Angolo, S.M. A Survey of Artificial Intelligence in Cyber Security. Int. J. Comput. Appl. Technol. Res. 2022, 11, 474–477. [Google Scholar] [CrossRef]
- Nikita, M.; Kashyap, L.; Singh, B.P.; Tyagi, D. AI Enabled Advance Surveillance System. Int. Res. J. Mod. Eng. Technol. Sci. 2023, 5, 6056–6061. [Google Scholar] [CrossRef]
- Yu, Y.; Lee, S. Remote driving control with real-time video streaming over wireless networks: Design and evaluation. IEEE Access 2022, 10, 64920–64932. [Google Scholar] [CrossRef]
- Lou, M.; Dong, X.; Cao, Z.; Shen, J. SESCF: A Secure and Efficient Supply Chain Framework via Blockchain-Based Smart Contracts. Secur. Commun. Netw. 2021, 2021, 8884478. [Google Scholar] [CrossRef]
- Shahzad, A.; Zhang, K.; Gherbi, A. Intuitive development to examine collaborative IoT supply chain system underlying privacy and security levels and perspective powering through proactive blockchain. Sensors 2020, 20, 3760. [Google Scholar] [CrossRef] [PubMed]
- Zhang, X.; Sun, P.; Xu, J.; Wang, X.; Yu, J.; Zhao, Z.; Dong, Y. Blockchain-based safety management system for the grain supply chain. IEEE Access 2020, 8, 36398–36410. [Google Scholar] [CrossRef]
- Nair, V.V. Drones as Futuristic Crime Prevention Strategy: Situational Review During COVID-19 Lockdown. J. Soc. Sci. 2020, 64, 22–29. [Google Scholar] [CrossRef]
- Kunovjanek, M.; Wankmüller, C. Containing the COVID-19 pandemic with drones-Feasibility of a drone enabled back-up transport system. Transp. Policy 2021, 106, 141–152. [Google Scholar] [CrossRef] [PubMed]
- Asamoah, D.; Nuertey, D.; Agyei-Owusu, B.; Acquah, I.N. Antecedents And Outcomes of Supply Chain Security Practices: The Role of Organizational Security Culture and Supply Chain Disruption Occurrence. Int. J. Qual. Reliab. Manag. 2022, 39, 1059–1082. [Google Scholar] [CrossRef]
- Solfa, F.D.G. Impacts of Cyber Security and Supply Chain Risk on Digital Operations: Evidence from the Pharmaceutical Industry. Int. J. Technol. Innov. Manag. 2022, 2, 18–32. [Google Scholar] [CrossRef]
- Alshurideh, M.T.; Alquqa, E.K.; Alzoubi, H.M.; Kurdi, B.A.; Hamadneh, S. The effect of information security on e-supply chain in the UAE logistics and distribution industry. Uncertain Supply Chain. Manag. 2023, 11, 145–152. [Google Scholar] [CrossRef]
- Kang, P.; Song, G.; Xu, M.; Miller, T.R.; Wang, H.; Zhang, H.; Liu, G.; Zhou, Y.; Ren, J.; Zhong, R.; et al. Low-carbon pathways for the booming express delivery sector in China. Nat. Commun. 2021, 12, 450. [Google Scholar] [CrossRef] [PubMed]
- Szyliowicz, J.S. International transportation security. Rev. Policy Res. 2004, 21, 351–368. [Google Scholar] [CrossRef]
- Kusrini, E.; Hanim, K. Analysis of compliance and supply chain security risks based on ISO 28001 in a logistic service provider in Indonesia. Int. J. Saf. Secur. Eng. 2021, 11, 135–142. [Google Scholar] [CrossRef]
- Jażdżewska-Gutta, M.; Borkowski, P. As strong as the weakest link. Transport and supply chain security. Transp. Rev. 2022, 42, 762–783. [Google Scholar] [CrossRef]
- Pourakbar, M.; Zuidwijk, R.A. The role of customs in securing containerized global supply chains. Eur. J. Oper. Res. 2018, 271, 331–340. [Google Scholar] [CrossRef]
- Zhao, J.; Liu, X.; Yan, Q.; Li, B.; Shao, M.; Peng, H.; Sun, L. Automatically predicting cyber attack preference with attributed heterogeneous attention networks and transductive learning. Comput. Secur. 2021, 102, 102152. [Google Scholar] [CrossRef]
- Pozniak, O.; Yurchenko, K. Formation of the optimal business model of a logistics company. Intellectualiz. Logist. Supply Chain. Manag. 2021, 10, 19–36. [Google Scholar] [CrossRef] [PubMed]
- De Liso, N.; Zamparini, L. Innovation, transport security and supply chains: A review. Transp. Rev. 2022, 42, 725–738. [Google Scholar] [CrossRef]
- Zamparini, L. A review of models for transport security and of their relevance for supply chains. Transp. Rev. 2022, 42, 784–800. [Google Scholar] [CrossRef]
- Edwards, F.L.; Goodrich, D.C. Introduction to Transportation Security, 2nd ed.; CRC Press: Boca Raton, FL, USA, 2024. [Google Scholar]
- Page, M.J.; McKenzie, J.E.; Bossuyt, P.M.; Boutron, I.; Hoffmann, T.C.; Mulrow, C.D.; Shamseer, L.; Tetzlaff, J.M.; Akl, E.A.; Brennan, S.E.; et al. The PRISMA 2020 statement: An updated guideline for reporting systematic reviews. BMJ 2021, 372, n71. [Google Scholar] [CrossRef] [PubMed]
- Eck, N.J.V.; Waltman, L. VOSviewer. Leiden University, 1 July 2024. Available online: https://www.vosviewer.com/ (accessed on 30 June 2024).
- Aggarwal, C.C. Data Mining; Springer International Publishing: New York, NY, USA, 2015; p. 734. [Google Scholar]
- Lei, A.; Cruickshank, H.; Cao, Y.; Asuquo, P.; Ogah, C.P.A.; Sun, Z. Blockchain-based dynamic key management for heterogeneous intelligent transportation systems. IEEE Internet Things J. 2017, 4, 1832–1843. [Google Scholar] [CrossRef]
- Ajao, L.A.; Agajo, J.; Adedokun, E.A.; Karngong, L. Crypto hash algorithm-based blockchain technology for managing decentralized ledger database in oil and gas industry. J (Multidiscip. Sci. J.) 2019, 2, 300–325. [Google Scholar] [CrossRef]
- Reeb, T. (Ed.) Empowering the New Mobility Workforce: Educating, Training, and Inspiring Future Transportation Professionals; Elsevier: Amsterdam, The Netherlands, 2019. [Google Scholar]
- Zavitsas, K.; Zis, T.; Bell, M.G. The impact of flexible environmental policy on maritime supply chain resilience. Transp. Policy 2018, 72, 116–128. [Google Scholar] [CrossRef]
- Pintea, C.-M.; Calinescu, A.; Sitar, C.P.; Pop, P.C. Towards secure & green two-stage supply chain networks. Log. J. IGPL 2019, 27, 137–148. [Google Scholar]
- Seaton, H.E. The new e-commerce/home delivery retail distribution paradigm. J. Transp. Manag. 2018, 29, 7–25. [Google Scholar] [CrossRef]
- Arnold, F.; Cardenas, I.; Sörensen, K.; Dewulf, W. Simulation of B2C e-commerce distribution in Antwerp using cargo bikes and delivery points. Eur. Transp. Res. Rev. 2018, 10, 2. [Google Scholar] [CrossRef]
- Urciuoli, L. The risk of standards proliferation–An analysis of differences between private and public transport standards. Transp. Res. Part A Policy Pract. 2018, 116, 591–602. [Google Scholar] [CrossRef]
- Tong, X.; Lo, C.K.; Lai, K.-H.; Cheng, T.C.E. Supply chain security management: A citation network analysis. Int. J. Shipp. Transp. Logist. 2019, 11, 508–532. [Google Scholar] [CrossRef]
- Sidebottom, A.; Thornton, A.; Tompson, L.; Belur, J.; Tilley, N.; Bowers, K. A systematic review of tagging as a method to reduce theft in retail environments. Crime Sci. 2017, 6, 7. [Google Scholar] [CrossRef] [PubMed]
- Khaslavskaya, A.; Roso, V. Outcome-driven supply chain perspective on dry ports. Sustainability 2019, 11, 1492. [Google Scholar] [CrossRef]
- Fokum, D.T.; Frost, V.S.; Kuehnhausen, M.; DePardo, D.; Oguna, A.N.; Searl, L.S.; Komp, E.; Zeets, M.; Deavours, D.D.; Evans, J.B.; et al. An open-system transportation security sensor network: Field-trial experiences. IEEE Trans. Veh. Technol. 2010, 59, 3942–3955. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).