Potential Vulnerabilities of Cryptographic Primitives in Modern Blockchain Platforms
Abstract
1. Introduction
2. Materials and Methods
2.1. Statement of the Problem
- Identify the main cryptographic primitives used in modern blockchain systems, distributing them into functional groups.
- For each cryptographic primitive, provide a brief description of its operating modes and determine the purpose of its use within blockchain systems.
- Consider approaches to determining the cryptographic resistance of each of the cryptographic primitives under consideration in terms of computational costs in relation to the time of using the brute force tactic.
2.2. Object of Study
2.2.1. Keyless Cryptographic Primitives in Blockchain Technologies
2.2.2. Single-Key Cryptographic Primitives in Blockchain Technologies
2.2.3. Two-Key Cryptographic Primitives in Blockchain Technologies
| Algorithm 1. Addition of two different points of an elliptic curve |
| Tyte 1. Input: Elliptic curve in a prime field of the form of Equation (1). Two points of the elliptic curve are P(x1, y1) and Q(x2, y2), where P, Q ∈ Fp; P ≠ Q, x1 ≠ x2. Steps:
Tyte 2. Input: Elliptic curve in a prime field of the form of Equation (1). Two identical points of an elliptic curve are P(x1, y1) and P(x1, y1), where P ∈ Fp, y1≠ 0. Steps:
Tyte 3. Input: Elliptic curve in a prime field of the form of Equation (1). Two points of the elliptic curve are P(x1, y1) and Q(x2, y2), where P ≠ Q, x1 = x2. Output: Point R (x3, y3) = P + Q = ∞ (neutral element). Tyte 4. Input: Elliptic curve in a prime field of the form of Equation (1). Two points of the elliptic curve are P(x1, y1), with y1 = 0. Output: Point R (x3, y3) = 2P = ∞ (neutral element). Tyte 5. Input: Elliptic curve in a prime field of the form of Equation (1). Two points of the elliptic curve are P(x1, y1) and Q = ∞ (neutral element). Output: Point R (x3, y3) = P + Q = P + ∞ = P. |
| Algorithm 2. Multiplying a point on an elliptic curve by a scalar |
| Input: Elliptic curve in a prime field of the form of Equation (1). Elliptic curve point is P(x1, y1), where P ∈ Fp; scalar k is an integer that can be represented as a bit sequence k = (km − 1, km − 2, …, k1, k0). Steps: 1. Initialize data. Point R = (0, 0). Point S = (x1, y1). 2. For all i from 0 to m − 1 2.1 If ki = 0, then 2.1.1 If R = 0, then R = S otherwise R = R + S 2.2 S = S + S Output: Point R = kP, R ∈Fp. |
| Algorithm 3. Recovering the y-coordinate for a point on an elliptic curve |
| Input: Elliptic curve in a simple field of the form of Equation (1). The coordinate of the point of the elliptic curve is (b||x). Steps: 1. mod p. 2. If ((b = 2) and ((y & 1) = 1)), then y = p − y. Output: Point R = (x, y). |
| Algorithm 4. Elliptic curve digital signature algorithm (ECDSA) |
| Input: Elliptic curve in a simple field of the form of Equation (1) with a tuple of parameters T = (p, a, b, G, n, hc) common to two users of the system A and B, message M, h(M) is a given hash function. Key generation: 1. User A chooses a random number dA no greater than n. dA is the private key of user A. 2. User A calculates the point QA = dAG. The point QA is the public key of user A. 3. User A sends his public key QA to user B. Signature: 1. User A chooses a random number ks no greater than n. The number ks is a session key, different each time for signing messages M. 2. User A calculates the point ksG = (x1, y1) and r = x1 mod n. 3. If r = 0, then it is necessary to return to step 1 4. User A calculates t = ks−1 mod n (using the extended Euclidean algorithm). 5. User A calculates z = h(M) and represents the result as a large integer. 6. User A calculates s = t(z + rdA) mod n. 7. If s = 0, then return to step 1 8. User A sends message M to user B and a signature in the form of a pair of values (r, s). Output: Signature = (r, s). Signature verification: 1. User B checks that the numbers r and s are in the range from 1 to n − 1. 2. User B calculates z = h(M) and represents the result as a large integer. 3. User B calculates w = s−1 mod n (using the extended Euclidean algorithm). 4. User B calculates u = zw mod n. 5. User B calculates v = rw mod n. 6. User B calculates the uG + vQA 7. If r ≠ x mod n, then the signature is incorrect. Output: Point (x, y) = uG + vQA = uG + vdAG = (u + vdA)G = (zw + rwdA)G = (z + rdA)wG = (z + rdA)s−1G = (z + rdA)s−1G = st−1s−1G = t−1G = (ks−1)−1G = ksG |
2.2.4. Hybrid Cryptographic Primitives in Blockchain Technologies
3. Results and Discussions
3.1. Hash Functions and Their Strength When Used in Blockchain
| Algorithm 5. Determining an address in the Ethereum network |
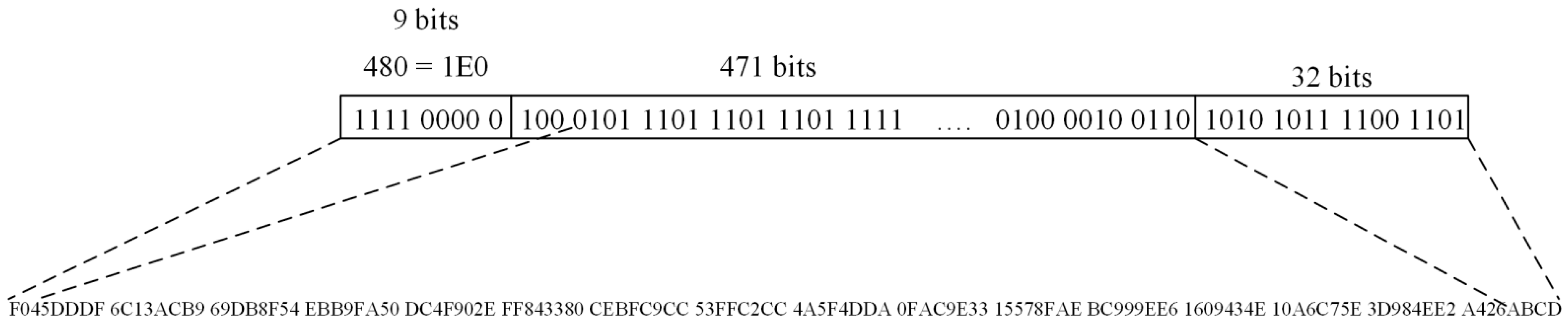
| For all x from 1 to 2256 − 1: 1. Determine the value of the Jacobian symbol 2. If the Jacobian symbol is not 1, then go back to step 1 3. Determine the values of y1 and y2 4. Compute h = Keccak-256(x||y1) 5. If the lower 20 bits of h are AE, then the solution is point (x||y1) 6. Compute h = Keccak-256(x||y2) 7. If the lower 20 bits of h are AE, then the solution is point (x||y2) A total of 2257 hash operations are required to compute the preimage of point Q = (x, y). |
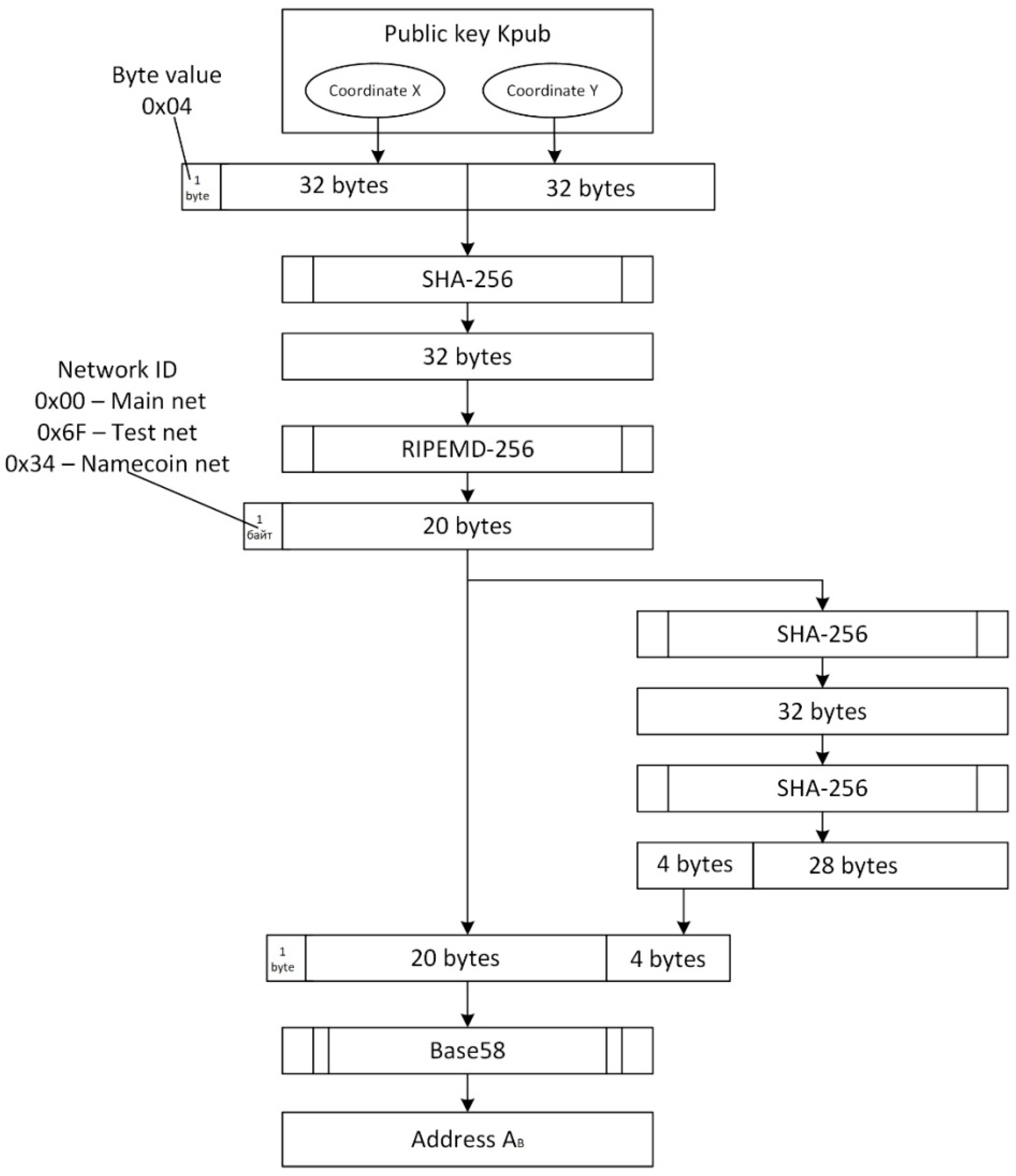
| Algorithm 6. Determining an address in the Bitcoin network. Version 1 |
| 1. For all x from 1 to 2256 − 1: 1.1 Determine the Jacobian symbol value 1.2 If the Jacobian symbol is not 1, then return to step 1 1.3 Determine the values of y1 and y2 1.4 Compute h1 = SHA-256(x||y1) 1.5 Compute h2 = RIPEMD-160(h1) 1.6 If (00||h2) = MSB21AB, then the solution is point (x||y1) 1.7 If (6F||h2) = MSB21AB, then the solution is point (x||y1) 1.8 If (34||h2) = MSB21AB, then the solution is point (x||y1) 1.9 Compute h1 = SHA-256(x||y2) 1.10 Compute h2 = RIPEMD-160(h1) 1.11 If (00||h2) = MSB21AB, then the solution is point (x||y2) 1.12 If (6F||h2) = MSB21AB, then the solution is point (x||y2) 1.13 If (34||h2) = MSB21AB, then the solution is point (x||y2) In total, 2258 hash operations are required to calculate the preimage of point Q = (x, y). |
| Algorithm 7. Determining an address in the Bitcoin network. Version 2 |
| 1. For all x from 1 to 2256 − 1: 1.1 Determine the Jacobian symbol value 1.2 If the Jacobian symbol is not 1, then return to step 1 1.3 Determine the values of y1 and y2 1.4 Calculate h1 = SHA-256(x||y1). Store the values (x||y1, h1) in Base1. 1.5 Calculate h2 = SHA-256(x||y2). Store the values (x||y2, h2) in Base1. 1.6 Calculate h3 = RIPEMD-160(x). 1.7 If (00||h3) = MSB21AB, then store the value of x in Base2. 1.8 If (6F||h3) = MSB21AB, then store the values of x in Base2. 1.9 If (34||h2) = MSB21AB, then store the values of x in Base2. 2. For all x from Base 2, compare them with the values of h1 and h2 from Base 1. If they match h1, the solution is the point (x||y1) from the corresponding entry in Base1. If they match h2, the solution is the point (x||y2) from the corresponding entry in Base1. |
3.2. PRS Generators and Their Strength When Used in Blockchain
| Algorithm 8. Determining the quality of the PRS generator |
| 1. Initialize variables k[0] = Gen(); Sum = 0; 2. For all i from 1 to n: 2.1. k[i] = Gen(); 2.2. For all j from 0 to i − 1: 2.2.1 If (|k[i] − k[j]| ≤ d), then Sum = Sum + 1; 3. p = . |
3.3. ECC and Its Strength When Used in Blockchain
| Algorithm 9. New algorithm for encrypting and decrypting data |
| Input: Elliptic curve in a prime field of the form of Equation (1) with a tuple of parameters T = (p, a, b, G, n, hc), common to two users of the system A and B, padded message M. Key generation:
Decryption:
|
| Algorithm 10. Finding a private key when using a bad PRS generator |
| 1. Generate k = Gen(). 2. Calculate point Q1 = kG; 3. If Q1 = QA, then dA = k; terminate the algorithm. 4. For all i from 1 to d: 4.1 Q1 = Q1 + G; 4.2 If Q1 = QA, then dA = k + i; terminate the algorithm. 5. If key not found, then return to step 1. |
| Algorithm 11. Finding a session key when using a bad PRS generator |
| 1. Generate k = Gen(). 2. Calculate point Q1 = kG = (x2, y2); 3. If r1 = x2, then ks = k; terminate the algorithm. 4. For all i from 1 to d: 4.1 Q1 = Q1 + G = (xi + 2, yi + 2); 4.2 If r1 = xi + 2, then ks = k + i; terminate the algorithm. 5. If ks is not found, then return to step 1. |
4. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| ACE | Advanced Cryptographic Engine |
| AES | Advanced Encryption Standard |
| ECC | Elliptic Curves Cryptography |
| ECDSA | Elliptic Curve Digital Signature Algorithm |
| ECIES | Curve Integrated Encryption Scheme |
| HMAC | Hash Message Authentication Code |
| NAEDD | New Algorithm for Encrypting and Decrypting Data |
| PoW | Proof of Work |
| PRS | Pseudo-Random Sequence |
| PSEC | Provably Secure Elliptic Curve Encryption Scheme |
| P2PKH | Pay To Public Key Hash |
| P2SH | Pay To Script Hash |
| RSA | Rivest–Shamir–Adleman |
References
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. In Proceedings of the 2018 National Seminar, San Antonio, TX, USA, 30 May–1 June 2018; pp. 1–9. [Google Scholar] [CrossRef]
- Romano, D.; Schmid, G. Beyond Bitcoin: A Critical Look at Blockchain-Based Systems. Cryptography 2017, 1, 15. [Google Scholar] [CrossRef]
- Hajar, D.; Afifi, N.; Hilal, I. Dynamic Sharding and Monte Carlo for Post-Quantum Blockchain Resilience. Cryptography 2025, 9, 22. [Google Scholar] [CrossRef]
- Sabrina, F.; Sohail, S.; Tariq, U.U. A Review of Post-Quantum Privacy Preservation for IoMT Using Blockchain. Electronics 2024, 13, 2962. [Google Scholar] [CrossRef]
- Shor, P.W. Polynomial-Time Algorithms for Prime Factorization and Discrete Logarithms on a Quantum Computer. SIAM J. Comput. 1997, 26, 1484–1509. [Google Scholar] [CrossRef]
- Regev, O. An Efficient Quantum Factoring Algorithm. J. ACM 2025, 72, 1–13. [Google Scholar] [CrossRef]
- Orman, H. Recent Progress in Quantum Computing Relevant to Internet Security; IACR Cryptology ePrint Archive: NV, USA, 2024; pp. 1–31. Available online: https://eprint.iacr.org/2024/410 (accessed on 20 April 2025).
- Soubra, H.; Elsayed, H.; Elbrolosy, Y.; Adel, Y.; Attia, Z. Comprehensive Review of Metrics and Measurements of Quantum Systems. Metrics 2025, 2, 9. [Google Scholar] [CrossRef]
- Ragavan, S.; Vaikuntanathan, V. Space-Efficient and Noise-Robust Quantum Factoring. In Proceedings of the 44th Annual International Cryptology Conference CRYPTO 2024, Santa Barbara, CA, USA, 18–22 August 2024; Part VI. pp. 107–140. [Google Scholar] [CrossRef]
- Wang, C.; Wang, Q.D.; Hong, C.L.; Hu, Q.Y.; Pei, Z. Quantum Annealing Public Key Cryptographic Attack Algorithm Based on D-Wave Advantage. Chin. J. Comput. 2024, 47, 1030–1044. Available online: http://cjc.ict.ac.cn/online/onlinepaper/wc-202458163113.pdf (accessed on 24 April 2025).
- Yang, Z.; Alfauri, H.; Farkiani, B.; Jain, R.; Di Pietro, R.; Erbad, A. A Survey and Comparison of Post-quantum and Quantum Blockchains. IEEE Commun. Surv. Tut. 2024, 26, 967–1002. [Google Scholar] [CrossRef]
- Bae, S.; Koh, S.-T. Optical Link Design for Quantum Key Distribution-Integrated Optical Access Networks. Photonics 2025, 12, 418. [Google Scholar] [CrossRef]
- Shannon, C.E. A Mathematical Theory of Communication. Bell Syst. Tech. J. 1948, 27, 379–423. [Google Scholar] [CrossRef]
- Almaraz Luengo, E.; Román Villaizán, J. Cryptographically Secured Pseudo-Random Number Generators: Analysis and Testing with NIST Statistical Test Suite. Mathematics 2023, 11, 4812. [Google Scholar] [CrossRef]
- Ishchukova, E.; Borlakov, R. Reliability of Information Conversion When Encrypting Graphic Images. In AISMA-2023: International Workshop on Advanced Information Security Management and Applications. AISMA 2023; Lecture Notes in Networks and Systems; Raza, Z., Babenko, M., Sajid, M., Lapina, M., Zolotarev, V., Eds.; Springer: Cham, Switzerland, 2024; Volume 1207. [Google Scholar] [CrossRef]
- Borges-Quintana, M.; Borges-Trenard, M.A.; Tito-Corrioso, O.; Rojas, O.; Sosa-Gómez, G. Combined and General Methodologies of Key Space Partition for the Cryptanalysis of Block Ciphers. Cryptography 2024, 8, 45. [Google Scholar] [CrossRef]
- Mouha, N.; Kolomeec, N.; Akhtiamov, D.; Sutormin, I.; Panferov, M.; Titova, K.; Bonich, T.; Ishchukova, E.; Tokareva, N.; Zhantulikov, B. Maximums of the Additive Differential Probability of Exclusive-Or. IACR Trans. Symmetric Cryptol. 2021, 2021, 292–313. [Google Scholar] [CrossRef]
- Wu, Z.; Qiao, K.; Wang, Z.; Cheng, J.; Zhu, L. Mixture Differential Cryptanalysis on Round-Reduced SIMON32/64 Using Machine Learning. Mathematics 2024, 12, 1401. [Google Scholar] [CrossRef]
- Muthavhine, K.D.; Sumbwanyambe, M. Blocking Linear Cryptanalysis Attacks Found on Cryptographic Algorithms Used on Internet of Thing Based on the Novel Approaches of Using Galois Field (GF (232)) and High Irreducible Polynomials. Appl. Sci. 2023, 13, 12834. [Google Scholar] [CrossRef]
- Amara, M.; Siad, A. Elliptic Curve Cryptography and its applications. In Proceedings of the International Workshop on Systems, Signal Processing and their Applications WOSSPA, Tipaza, Algeria, 9–11 May 2011; pp. 247–250. [Google Scholar] [CrossRef]
- Lara-Nino, C.A.; Diaz-Perez, A.; Morales-Sandoval, M. Elliptic Curve Lightweight Cryptography: A Survey. IEEE Access 2018, 6, 72514–72550. [Google Scholar] [CrossRef]
- Standards for Efficient Cryptography. SEC 2: Recommended Elliptic Curve Domain Parameters, Version 2.0. Available online: https://www.secg.org/sec2-v2.pdf (accessed on 26 April 2025).
- Al-Zubaidie, M.; Zhang, Z.; Zhang, J. Efficient and secure ECDSA algorithm and its applications: A survey. Int. J. Commun. Netw. Inf. Secur. 2019, 11, 7–35. Available online: https://www.ijcnis.org/index.php/ijcnis/article/view/3827/704 (accessed on 26 April 2025).
- Martínez, V.G.; Álvarez, F.H.; Encinas, L.H.; Ávila, C.S. Analysis of ECIES and other Cryptosystems based on Elliptic Curves. J. Inf. Assur. Secur. 2011, 6, 285–293. Available online: https://www.mirlabs.org/jias/secured/Volume6-Issue4/Paper30.pdf (accessed on 26 April 2025).
- Falk, J. On Pollard’s Rho Method for Solving the Elliptic Curve Discrete Logarithm Problem. Bachelor’s Thesis, Linnaeus University, Växjö, Sweden, 2019. Available online: https://urn.kb.se/resolve?urn=urn:nbn:se:lnu:diva-85516 (accessed on 25 April 2025).


| Elliptic Curve | Private Key Size for ECC, Bit | Private Key Size for RSA, Bit | Key Ratio |
|---|---|---|---|
| secp160k1 | 160 | 1024 | 1:6 |
| secp160r1 | 160 | 1024 | 1:6 |
| secp160r2 | 160 | 1024 | 1:6 |
| secp224k1 | 224 | 2048 | 1:9 |
| secp224r1 | 224 | 2048 | 1:9 |
| secp256k1 | 256 | 3072 | 1:12 |
| secp256r1 | 256 | 3072 | 1:12 |
| secp521r1 | 521 | 15,360 | 1:30 |
| Elliptic Curve | p | a | b | hc |
|---|---|---|---|---|
| secp160k1 | 2160-232-214-212-29-28-27-23-22-1 | 0 | 7 | 01 |
| secp224k1 | 2224-232-212-211-29-27-24-2-1 | 0 | 5 | 01 |
| secp256k1 | 2256-232-29-28-27-26-24-1 | 0 | 7 | 01 |
| Elliptic Curve | G | n |
|---|---|---|
| secp160k1 | 02 3B4C382C E37AA192 A4019E76 3036F4F5 DD4D7EBB | 01 00000000 00000000 0001B8FA 16DFAB9A CA16B6B3 |
| secp224k1 | 03 A1455B33 4DF099DF 30FC28A1 69A467E9 E47075A9 0F7E650E B6B7A45C | 01 00000000 00000000 00000000 0001DCE8 D2EC6184 CAF0A971 769FB1F7 |
| secp256k1 | 02 79BE667E F9DCBBAC 55A06295 CE870B07 029BCFDB 2DCE28D9 59F2815B 16F81798 | FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF BAAEDCE6 AF48A03B BFD25E8C D0364141 |
| Case | Description | Maximum Difficulty |
|---|---|---|
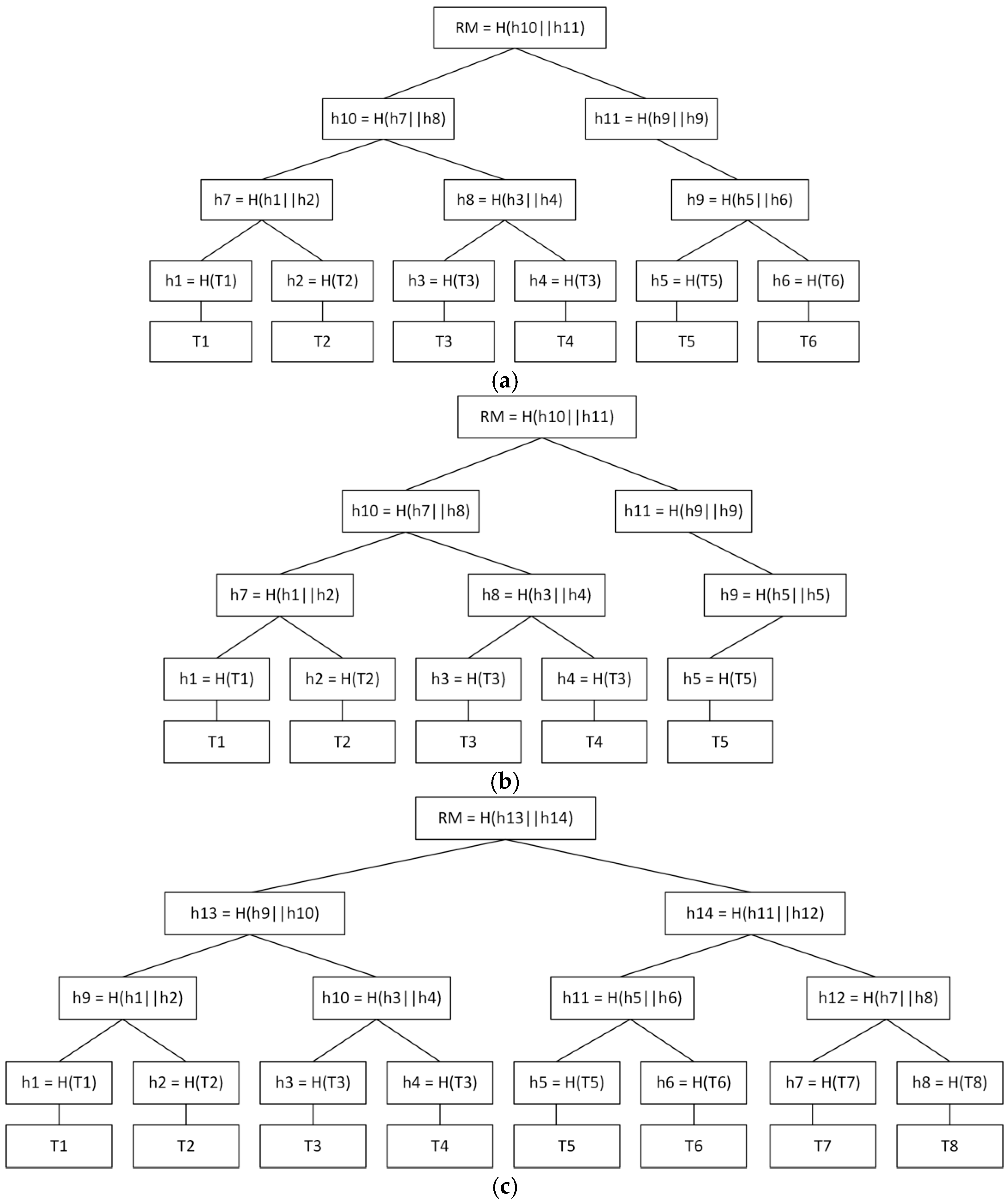
| 1 | It is necessary to replace one transaction in block M so that the root of the Merkle tree remains unchanged | 2n/2 steps, where n is the length of the generated hash sequence |
| 2 | It is necessary to replace block M with block M1 in compliance with all the rules for compiling a block (depending on the blockchain platform) | 2n/2 steps, where n is the length of the generated hash sequence |
| 3 | The Ethereum AE network address is known. Determine the user’s public key | 2257 hash operations are required |
| 4 | The Bitcoin network address AB is known. Determine the user’s public key | 2258 hash operations are required |
| 5 | Determine the probability p with which the PRG produces values k1 and k2 that are no more than d positions apart | , where n is the distance between two points |
| 6 | Determine the NAEDD private key of a user if his public key is known and the implementation of the key generation algorithm uses a weak PRS | , where n is the distance between two points |
| 7 | Determine the private key of a user if it is known that an error has been made in the implementation of the ECDSA: a constant value of the session key ks is used | It has no difficulty |
| 8 | Replace the signature of message M1 with the signature of message M2 in the ECDSA if it is known that ECDSA uses a weak PRS | , where n is the distance between two points |
| 9 | It is known that in the NAEDD, encryption is performed without using padding. It is required to recover the encrypted message M | It has no difficulty if the size of the encrypted message M does not exceed the length of the y coordinate |
| 10 | It is known that in the NAEDD, the padding of the message M is performed with an error. It is required to restore the encrypted message M | 210 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ishchukova, E.; Petrenko, S.; Petrenko, A.; Gnidko, K.; Nekrasov, A. Potential Vulnerabilities of Cryptographic Primitives in Modern Blockchain Platforms. Sci 2025, 7, 112. https://doi.org/10.3390/sci7030112
Ishchukova E, Petrenko S, Petrenko A, Gnidko K, Nekrasov A. Potential Vulnerabilities of Cryptographic Primitives in Modern Blockchain Platforms. Sci. 2025; 7(3):112. https://doi.org/10.3390/sci7030112
Chicago/Turabian StyleIshchukova, Evgeniya, Sergei Petrenko, Alexey Petrenko, Konstantin Gnidko, and Alexey Nekrasov. 2025. "Potential Vulnerabilities of Cryptographic Primitives in Modern Blockchain Platforms" Sci 7, no. 3: 112. https://doi.org/10.3390/sci7030112
APA StyleIshchukova, E., Petrenko, S., Petrenko, A., Gnidko, K., & Nekrasov, A. (2025). Potential Vulnerabilities of Cryptographic Primitives in Modern Blockchain Platforms. Sci, 7(3), 112. https://doi.org/10.3390/sci7030112









