An Efficient Framework for Secure Communication in Internet of Drone Networks Using Deep Computing
Abstract
1. Introduction
- The design of a lightweight authentication framework based on a hybrid machine learning model that incorporates random forest and LSTM models with comparable security and significantly lower computational demands.
- Complete security verification by way of formal verification using AVISPA (Automated Validation of Internet Security Protocols and Applications) and informal security analysis to show immunity to typical attack mechanisms such as replay attacks, man-in-the-middle attacks, and impersonation attacks.
- Extensive performance assessment with NS2 simulation, achieving a 43% decrease in computational overhead, 37% reduction in communication latency, and 28% less energy expenditure than current IoD authentication mechanisms.
2. Related Work
2.1. IoD Security Frameworks
2.2. Lightweight Authentication Protocols
2.3. Machine Learning for IoD Security
2.4. Security Evaluation Methodologies
2.5. Research Gap
3. Materials and Methods
3.1. System Model and Problem Formulation
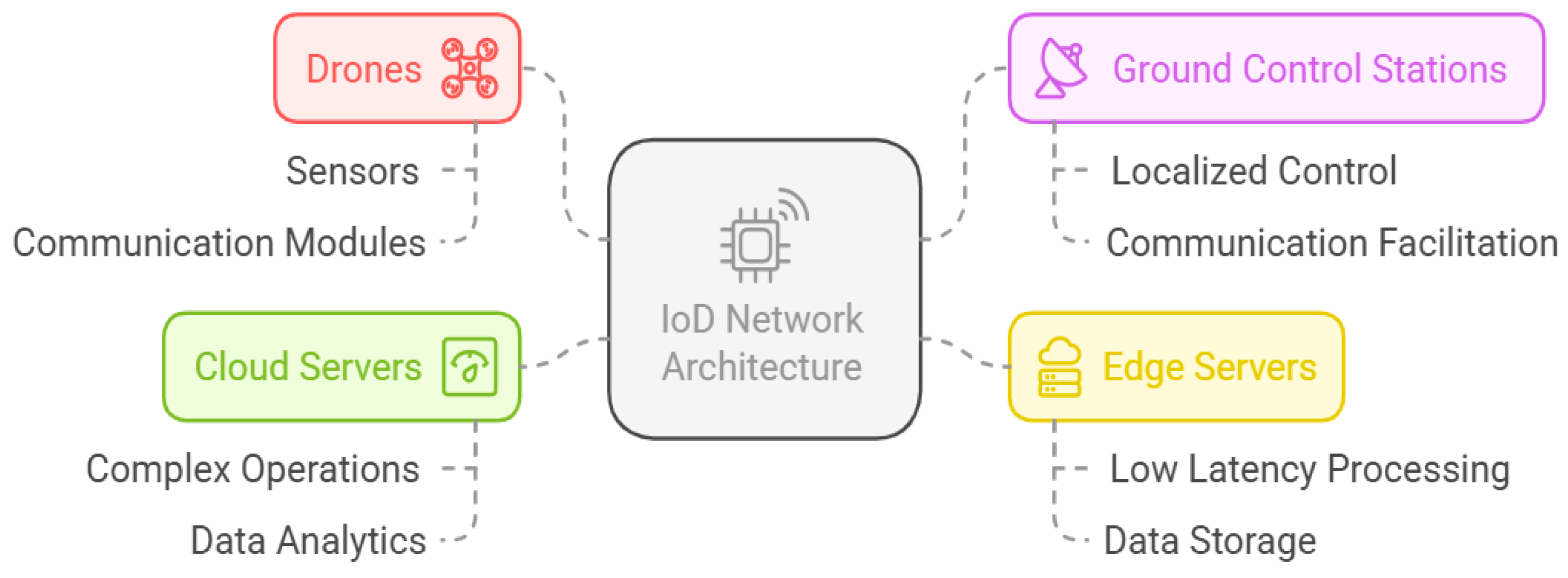
3.1.1. IoD Network Architecture
3.1.2. Security Requirements
3.1.3. Threat Model and Problem Formulation
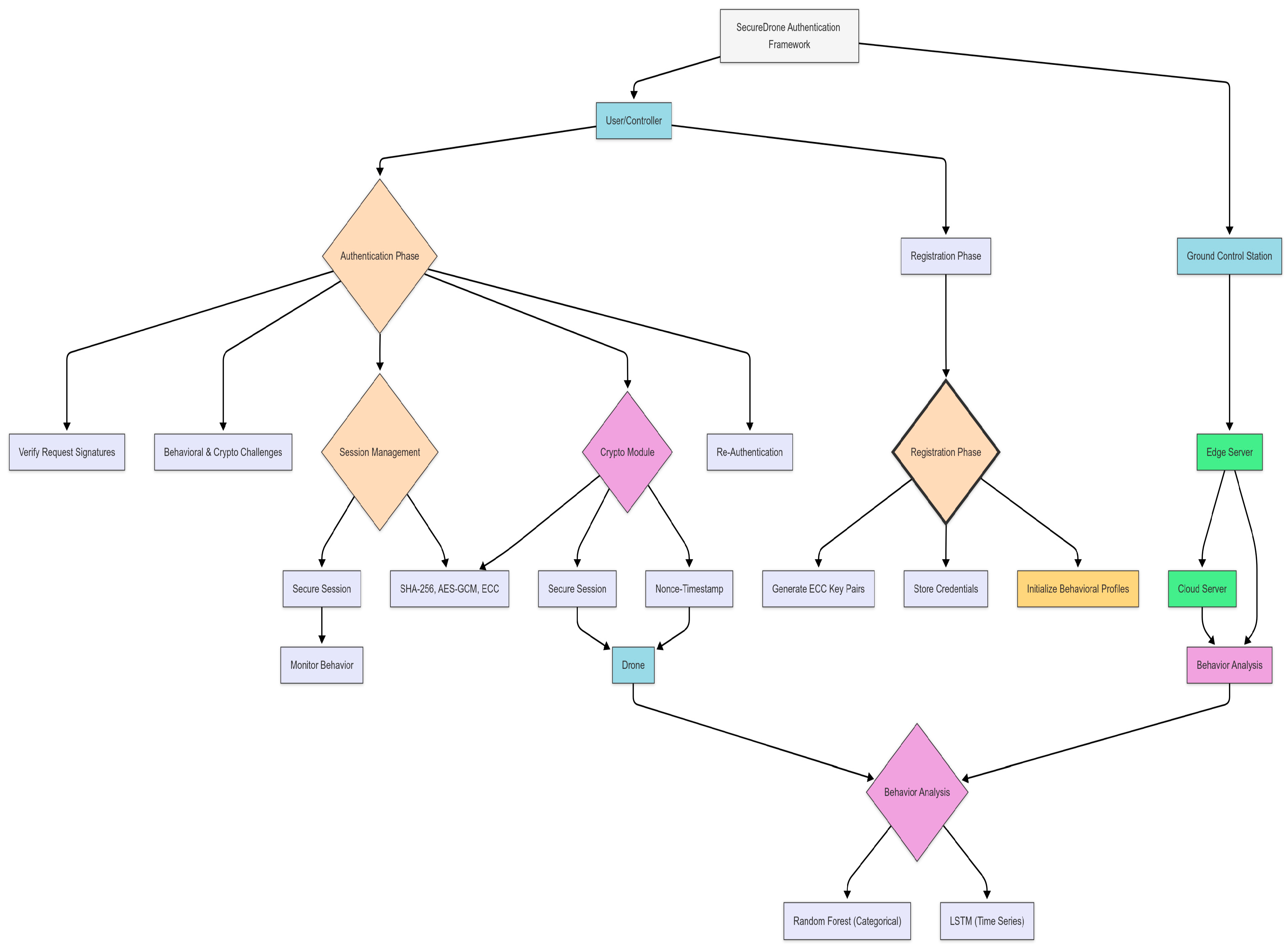
3.1.4. Proposed Authentication Protocol
3.1.5. Training Process of Machine Learning Models
3.1.6. Protocol Phases
| Algorithm 1: User Registration |
| Input: UserID, Credentials, InitialBehaviorProfile Output: Registration token, Public Key of the Entity Server (PK_ES) 1: (PK_U, SK_U)← GenerateECCKeyPair() 2: Store UserID, PK_U, Hash(Credentials) in UserRegistry 3: behavioralFeatures ← ExtractBehavioralFeatures(InitialBehaviorProfile) 4: lstmModel ← InitializeLSTMNetwork(inputSize = |behavioralFeatures|, hiddenLayers = 2, hiddenSize = 64) 5: lstmTrainingData ← GenerateSequentialBehaviorSamples(behavioralFeatures) 6: for epoch = 1 to 100 do 7: for each sequence in lstmTrainingData do 8: output ← lstmModel.Forward(sequence) 9: loss ← SequenceLoss(output, sequence) 10: lstmModel.Backpropagate(loss) 11: end for 12: end for 13: rfModel ← InitializeRandomForest(treeCount = 100, maxDepth = 10) 14: rfTrainingData ← GenerateBalancedTrainingSet(behavioralFeatures) 15: rfModel.Train(rfTrainingData) 16: Store (lstmModel, rfModel) in BehaviorDB under UserID 17: token ← SignECC(SK_ES, {UserID, PK_U, Timestamp}) 18: return token, PK_ES |
| Algorithm 2: Drone Registration |
| Input: DroneID, DroneType, Capabilities Output: Drone Certificate 1: (PK_D, SK_D)← GenerateECCKeyPair() 2: Store DroneID, PK_D, DroneType, Capabilities in DroneRegistry 3: telemetryFeatures ← ExtractTelemetryFeatures(DroneType, Capabilities) 4: droneLSTM ← InitializeLSTMNetwork(inputSize = |telemetryFeatures|, hiddenLayers = 2, hiddenSize = 32) 5: PretrainDroneLSTM(droneLSTM, DroneType) 6: droneRF ← InitializeRandomForest(treeCount = 80, maxDepth = 8) 7: PretrainDroneRF(droneRF, DroneType) 8: Store (droneLSTM, droneRF) in DroneModelDB under DroneID 9: SecureStore(DroneID, SK_D, PK_ES) 10: cert ← SignECC(SK_ES, {DroneID, PK_D, Timestamp}) 11: return cert |
| Algorithm 3: User Authentication |
| Input:
UserID, AuthRequest = {reqID, timestamp, nonce, signature} Output: Encrypted challenge token or authentication failure 1: if CurrentTime()-timestamp > TimeWindow then 2: return AuthFailure(“Request expired”) 3: end if 4: userPK ← UserRegistry.getPK(UserID) 5: if not VerifyECC(userPK, signature, {reqID, timestamp, nonce}) then 6: return AuthFailure(“Invalid signature”) 7: end if 8: profile ← BehaviorDB.getProfile(UserID) 9: lstmModel ← profile.LSTM 10: rfModel ← profile.RF 11: challenge ← GenerateUserBehaviorChallenge(profile) 12: challengeToken ← EncryptECC(userPK, {challenge, nonce + 1}) 13: return challengeToken |
| Algorithm 4: Verify User Response |
| UserID, Response = {challenge, responseData, signature} is the input. Output: AuthFailure or AuthSuccess with session key 1: UserPK ← UserRegistry.getPK (UserID) 2: If VerifyECC(userPK, signature, {challenge, responseData}) is not present, then 3: return AuthFailure(“Invalid response”) 4: terminate if 5: Extract Behavior Features (responseData)← currentBehavior 6: behaviorSeq ← FormatBehaviorAsSequence(currentBehavior) 7: predictedSeq ← lstmModel.Forward(behaviorSeq) 8: SequenceLoss(predictedSeq, behaviorSeq[1:])← loss 9: lstmScore ← exp(−loss) 10: FormatBehaviorAsFeatureVector(currentBehavior)← rfVector 11: classProbs ← rfModel.PredictProbabilities(rfVector) 12: rfAnomaly ← 1 − classProbs[1] 13: behaviorScore ← 0.6 × lstmScore + 0.4 × (1 − rfAnomaly) 14: if behaviorScore is less than behavior threshold, then 15: Log(UserID, “Behavior anomaly”, behaviorScore) 16: AuthFailure(“Behavior anomaly detected”) is returned. 17: terminate if 18: lstmModel.Update(learningRate = 0.01, behaviorSeq) 19: rfModel.Update(rfVector, isPositive = TRUE) 20: BehaviorDB.update(UserID, currentBehavior, lstmModel, rfModel) 21: GenerateRandomKey(128) ← sessionKey 22: return AuthSuccess, encryptedKey 23: encryptedKey ← EncryptECC(userPK, sessionKey) |
| Algorithm 5: Verify Drone Response |
| Input: DroneID, Response = {challenge, telemetryData, signature} Output: AuthSuccess with encrypted session key or failure 1: dronePK ← DroneRegistry.getPK(DroneID) 2: if not VerifyECC(dronePK, signature, {challenge, telemetryData}) then 3: return AuthFailure(“Invalid drone response”) 4: end if 5: telemetryFeatures ← ExtractTelemetryFeatures(telemetryData) 6: seq ← FormatTelemetryAsSequence(telemetryFeatures) 7: predicted ← droneLSTM.Forward(seq) 8: seqScore ←CalculateSequenceSimilarity(predicted, seq) 9: vector ← FormatTelemetryAsFeatureVector(telemetryFeatures) 10: prob ← droneRF.PredictProbabilities(vector) 11: anomaly ← 1 − prob[1] 12: authScore ← 0.5 × seqScore + 0.5 × (1 − anomaly) 13: if authScore < DroneAuthThreshold then 14: Log(DroneID, “Compromised drone”, authScore) 15: return AuthFailure(“Telemetry mismatch”) 16: end if 17: droneLSTM.Update(seq) 18: droneRF.Update(vector, isNormal = TRUE) 19: DroneModelDB.update(DroneID, droneLSTM, droneRF) 20: sessionKey ← GenerateRandomKey(128) 21: encryptedKey ← EncryptECC(dronePK, sessionKey) 22: return AuthSuccess, encryptedKey |
3.1.7. Security Analysis and Verification
4. Results
4.1. Experimental Setup and Simulation Environment
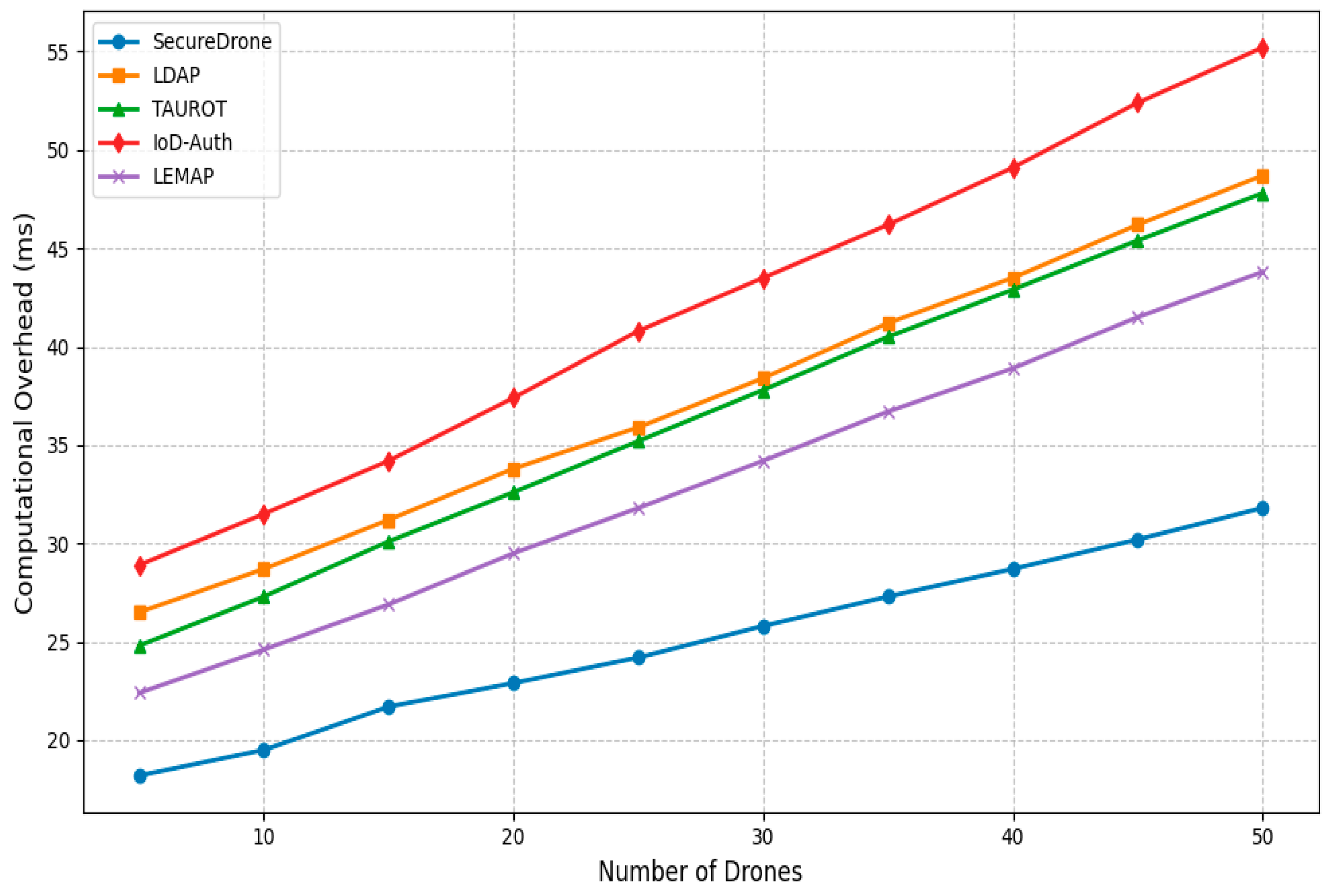
4.2. Computational Overhead Analysis
4.3. Authentication Latency
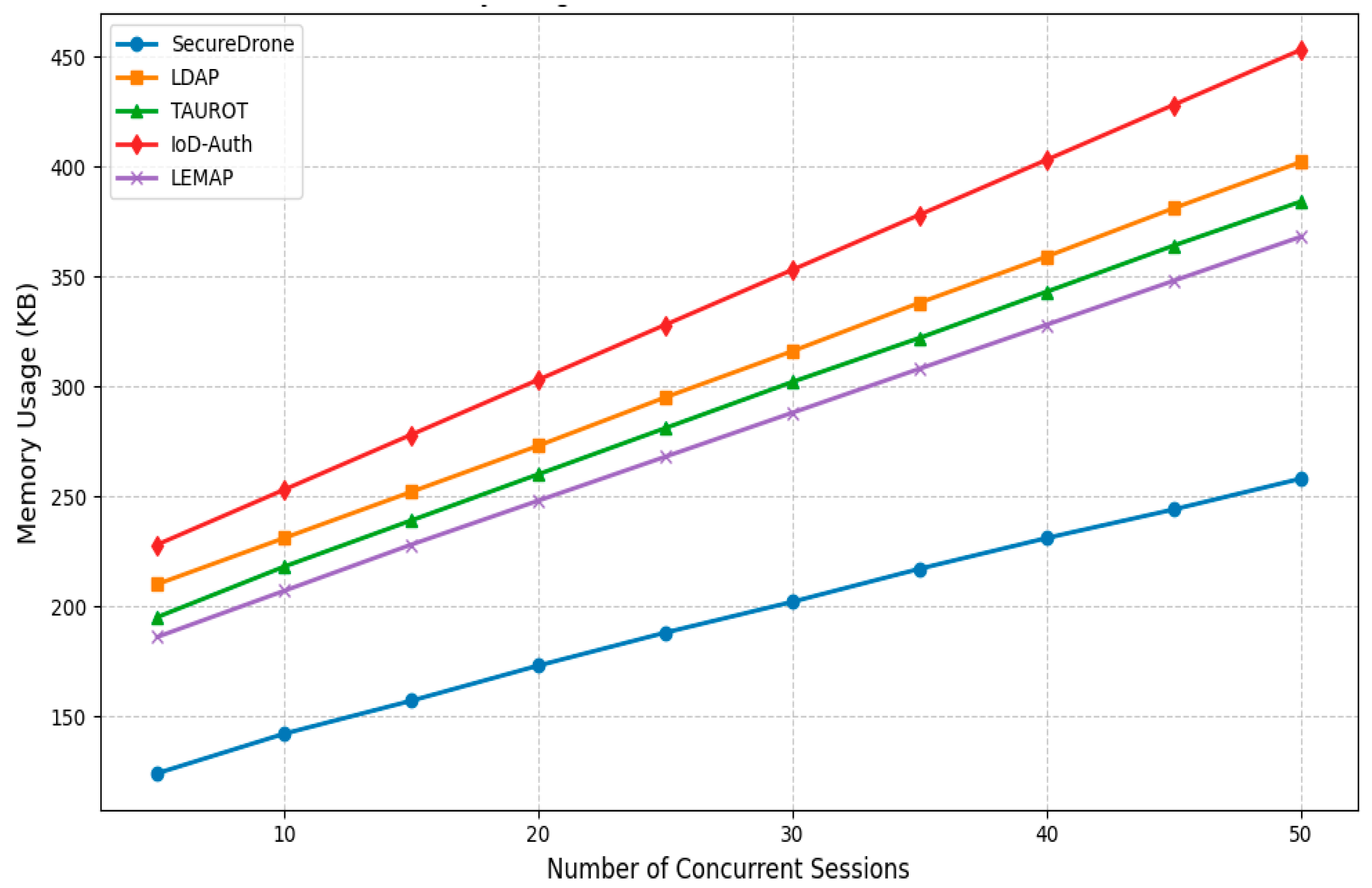
4.4. Memory Usage Analysis
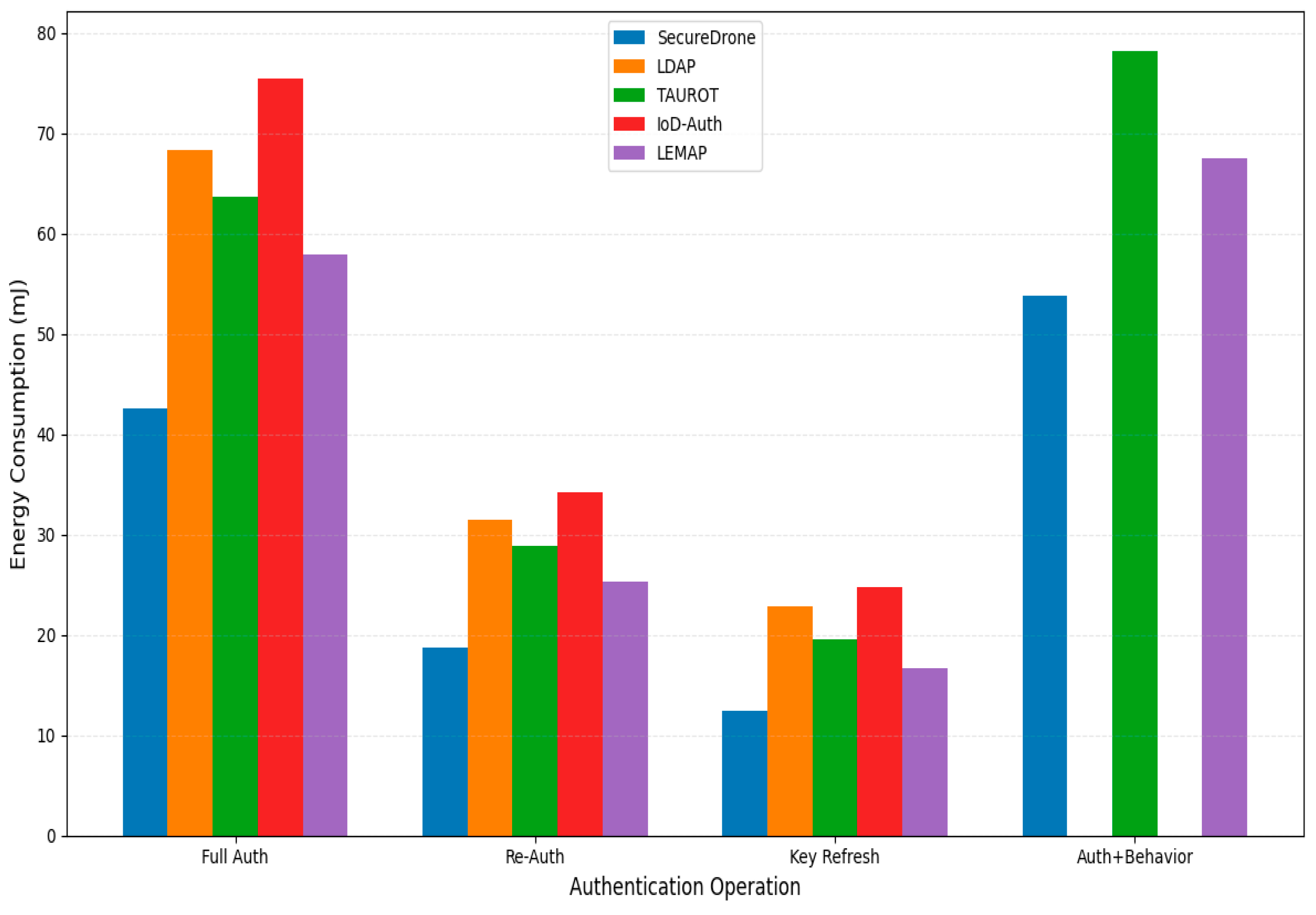
4.5. Energy Consumption
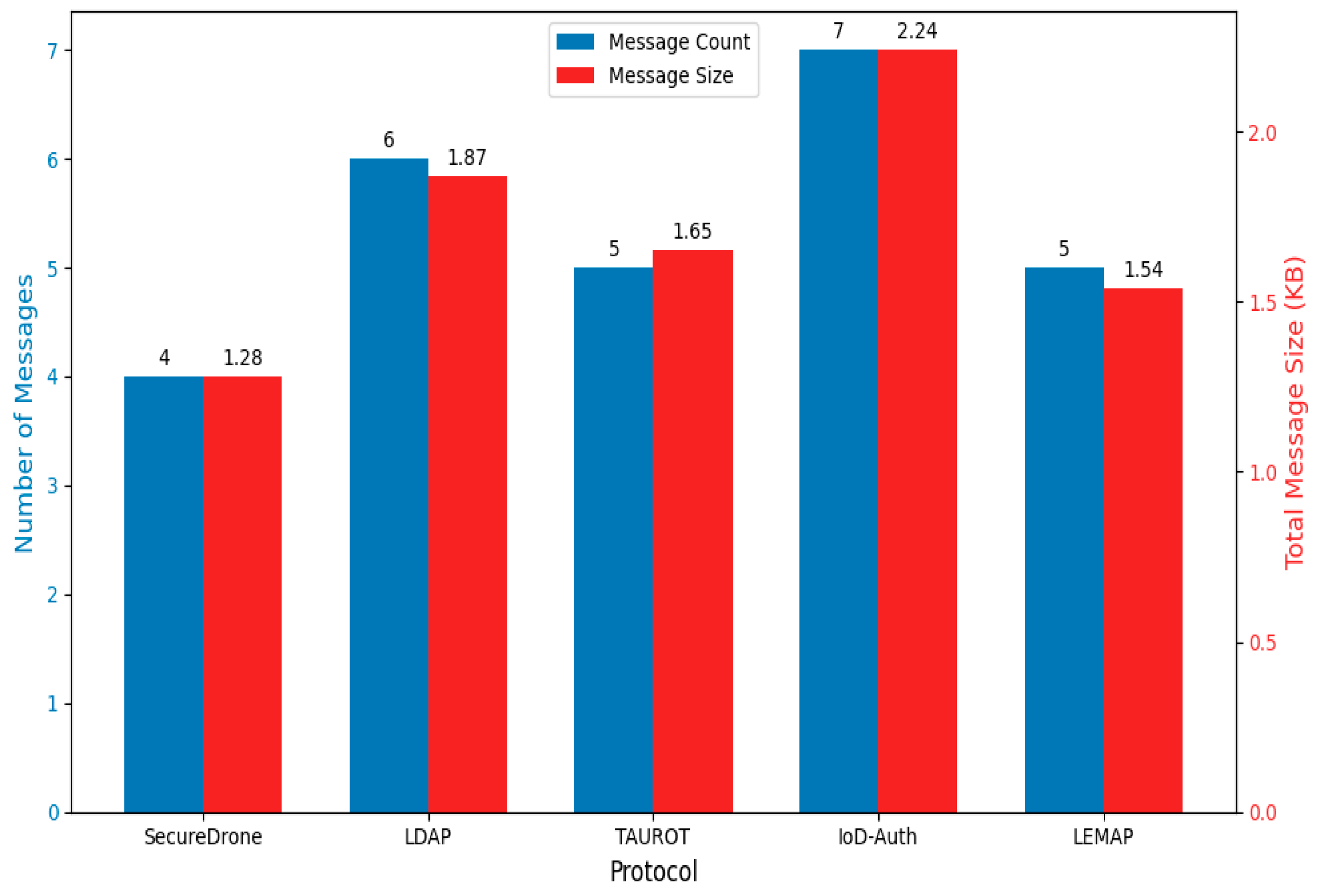
4.6. Communication Overhead
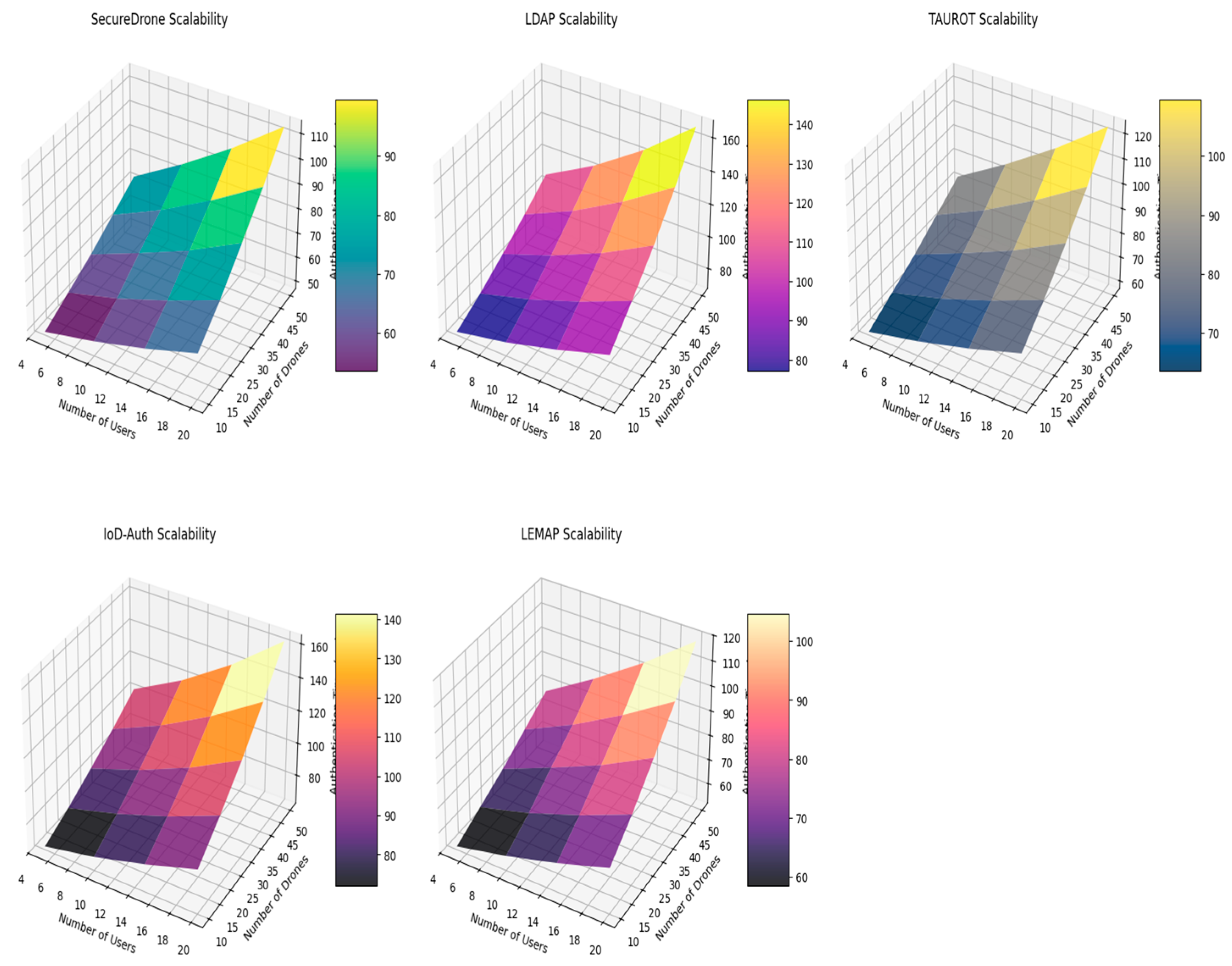
4.7. Scalability Analysis
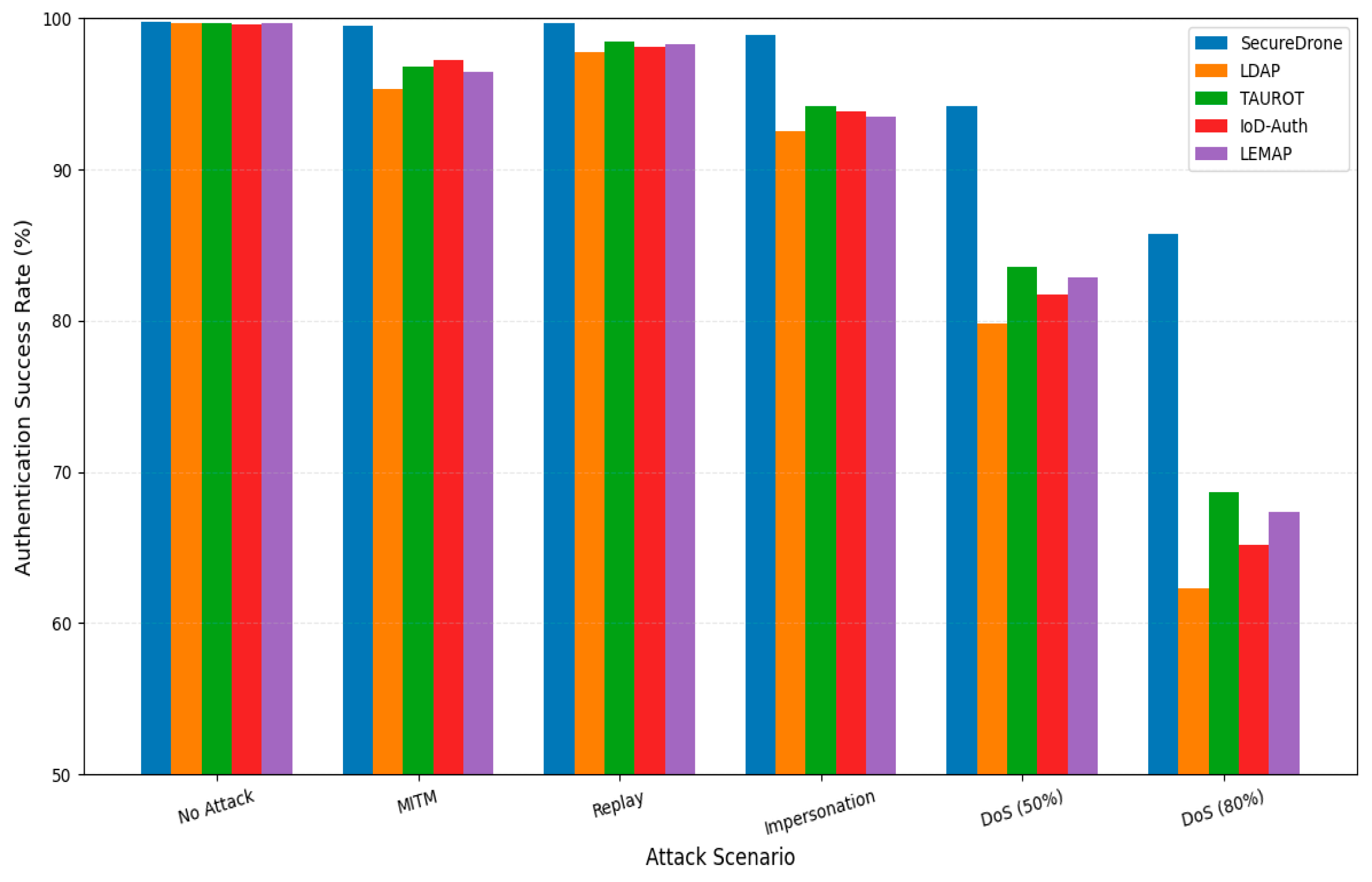
4.8. Authentication Success Rate Under Attack Scenarios
4.9. Performance Comparison Summary
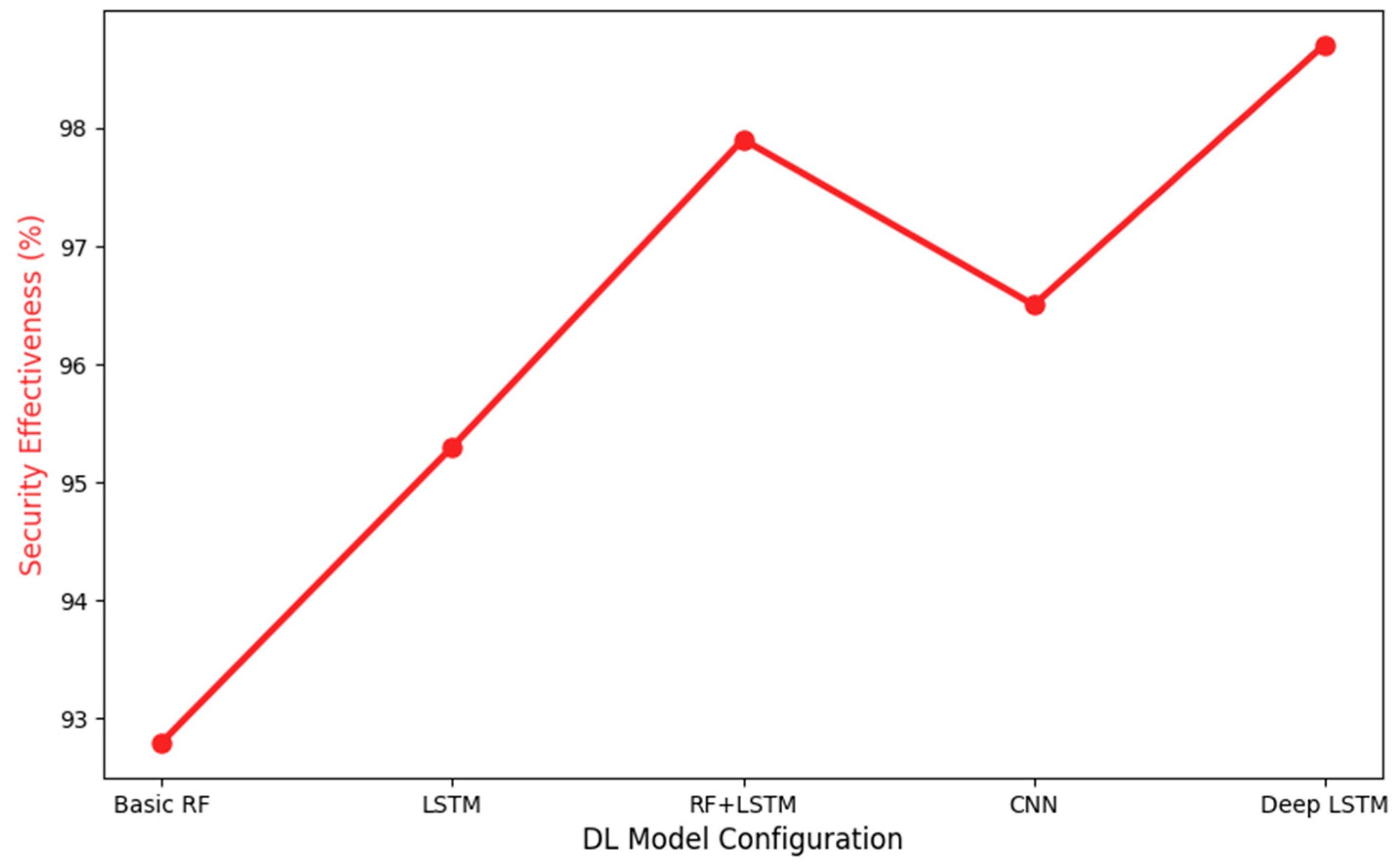
4.10. Impact of Deep Learning Model Complexity
5. Discussion
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Fotouhi, A.; Qiang, H.; Ding, M.; Hassan, M.; Giordano, L.G.; Garcia-Rodriguez, A.; Yuan, J. Survey on UAV cellular communications: Practical aspects, standardization advancements, regulation, and security challenges. IEEE Commun. Surv. Tutor. 2019, 21, 3417–3442. [Google Scholar] [CrossRef]
- Akram, J.; Anaissi, A.; Akram, A.; Rathore, R.S.; Jhaveri, R.H. Adversarial Label-Flipping Attack and Defense for Anomaly Detection in Spatial Crowdsourcing UAV Services. IEEE Trans. Consum. Electron. 2024, 1. [Google Scholar] [CrossRef]
- Maulana, F.I.; Febriantono, M.A.; Hamim, M.; Fajri, B.R.; Arifuddin, R. Scientometric analysis in the field of big data and artificial intelligence in industry. In Proceedings of the 2022 1st International Conference on Information System & Information Technology (ICISIT), Virtual Conference, 27–28 July 2022; IEEE: Piscataway, NJ, USA, 2022. [Google Scholar]
- Su, J.; Zhu, X.; Li, S.; Chen, W.H. AI meets UAVs: A survey on AI empowered UAV perception systems for precision agriculture. Neurocomputing 2023, 518, 242–270. [Google Scholar] [CrossRef]
- Hayajneh, A.M.; Zaidi, S.A.R.; McLernon, D.C.; Di Renzo, M.; Ghogho, M. Performance analysis of UAV enabled disaster recovery networks: A stochastic geometric framework based on cluster processes. IEEE Access 2018, 6, 26215–26230. [Google Scholar] [CrossRef]
- Jha, S.K.; Prakash, S.; Rathore, R.S.; Mahmud, M.; Kaiwartya, O.; Lloret, J. Quality-of-service-centric design and analysis of unmanned aerial vehicles. Sensors 2022, 22, 5477. [Google Scholar] [CrossRef]
- Jha, S.K.; Prakash, S.; Rathore, R.S.; Mahmud, M.; Kaiwartya, O.; Lloret, J. UAV-enabled intelligent transportation systems for the smart city: Applications and challenges. IEEE Commun. Mag. 2017, 55, 22–28. [Google Scholar]
- Purohit, S.; Mishra, N.; Yang, T.; Singh, R.; Mo, D.; Wang, L. Real-Time Threat Detection and Response Using Computer Vision in Border Security. In Proceedings of the 2024 International Conference on Intelligent Algorithms for Computational Intelligence Systems (IACIS), Hassan, India, 23–24 August 2024; IEEE: Piscataway, NJ, USA, 2024. [Google Scholar]
- Bhawana; Kumar, S.; Rathore, R.S.; Mahmud, M.; Kaiwartya, O.; Lloret, J. BEST—Blockchain-enabled secure and trusted public emergency services for smart cities environment. Sensors 2022, 22, 5733. [Google Scholar] [CrossRef]
- Mishra, D.; Singh, M.; Rewal, P.; Pursharthi, K.; Kumar, N.; Barnawi, A.; Rathore, R.S. Quantum-safe secure and authorized communication protocol for internet of drones. IEEE Trans. Veh. Technol. 2023, 72, 16499–16507. [Google Scholar] [CrossRef]
- Zhang, C.; Kovacs, J.M. The application of small unmanned aerial systems for precision agriculture: A review. Precis. Agric. 2012, 13, 693–712. [Google Scholar] [CrossRef]
- Erdelj, M.; Król, M.; Natalizio, E. Wireless sensor networks and multi-UAV systems for natural disaster management. Comput. Netw. 2017, 124, 72–86. [Google Scholar] [CrossRef]
- Otto, A.; Agatz, N.; Campbell, J.; Golden, B.; Pesch, E. Optimization approaches for civil applications of unmanned aerial vehicles (UAVs) or aerial drones: A survey. Networks 2018, 72, 411–458. [Google Scholar] [CrossRef]
- Zeng, Y.; Zhang, R.; Lim, T.J. Wireless communications with unmanned aerial vehicles: Opportunities and challenges. IEEE Commun. Mag. 2016, 54, 36–42. [Google Scholar] [CrossRef]
- Rathore, R.S.; Sangwan, S.; Kaiwartya, O.; Aggarwal, G. Green Communication for Next-Generation Wireless Systems: Optimization Strategies, Challenges, Solutions, and Future Aspects. Wirel. Commun. Mob. Comput. 2021, 2021, 5528584. [Google Scholar] [CrossRef]
- Humphreys, T.E. Statement on the vulnerability of civil unmanned aerial vehicles and other systems to civil GPS spoofing. In US Congressional Testimony; The University of Texas at Austin: Austin, TX, USA, 2012. [Google Scholar]
- Durfey, N.; Sajal, S. A comprehensive survey: Cybersecurity challenges and futures of autonomous drones. In Proceedings of the 2022 Intermountain Engineering, Technology and Computing (IETC), Orem, UT, USA, 13–14 May 2022; pp. 1–7. [Google Scholar]
- Shakhatreh, H.; Sawalmeh, A.H.; Al-Fuqaha, A.; Dou, Z.; Almaita, E.; Khalil, I.; Guizani, M. Unmanned aerial vehicles (UAVs): A survey on civil applications and key research challenges. IEEE Access 2019, 7, 48572–48634. [Google Scholar] [CrossRef]
- Wang, C.; Wang, D.; Duan, Y.; Tao, X. Secure and lightweight user authentication scheme for cloud-assisted Internet of Things. IEEE Trans. Inf. Forensics Secur. 2023, 18, 2961–2976. [Google Scholar] [CrossRef]
- Akram, J.; Hussain, W.; Jhaveri, R.H.; Rathore, R.S.; Anaissi, A. Dynamic GNN-based multimodal anomaly detection for spatial crowdsourcing drone services. Digit. Commun. Netw. 2025; in press. [Google Scholar]
- Cao, X.; Shila, D.M.; Cheng, Y.; Yang, Z.; Zhou, Y.; Chen, J. Ghost-in-zigbee: Energy depletion attack on zigbee-based wireless networks. IEEE Internet Things J. 2016, 3, 816–829. [Google Scholar] [CrossRef]
- Nawaj, M.D.; Mohanta, H.; Yang, T.; Rathore, R.S.; Mo, D.; Wang, L. Adaptive Self-Tuning Robotic Autonomy for Unmanned Aerial Vehicles. In Proceedings of the 2024 International Conference on Intelligent Algorithms for Computational Intelligence Systems (IACIS), Hassan, India, 23–24 August 2024. [Google Scholar]
- Boukoberine, M.N.; Zhou, Z.; Benbouzid, M. A critical review on unmanned aerial vehicles power supply and energy management: Solutions, strategies, and prospects. Appl. Energy 2019, 255, 113823. [Google Scholar] [CrossRef]
- Raj, M.; Harshini, N.B.; Gupta, S.; Atiquzzaman, M.; Rawlley, O.; Goel, L. Leveraging precision agriculture techniques using UAVs and emerging disruptive technologies. Energy Nexus 2024, 14, 100300. [Google Scholar] [CrossRef]
- Kumar, S.; Singh, A.; Benslimane, A.; Chithaluru, P.; Albahar, M.A.; Rathore, R.S.; Álvarez, R.M. An optimized intelligent computational security model for interconnected blockchain-IoT system & cities. Ad Hoc Netw. 2023, 151, 103299. [Google Scholar]
- Khan, A.S.; Balan, K.; Javed, Y.; Tarmizi, S.; Abdullah, J. Secure trust-based blockchain architecture to prevent attacks in VANET. Sensors 2019, 19, 4954. [Google Scholar] [CrossRef]
- Yazdinejad, A.; Parizi, R.M.; Dehghantanha, A.; Choo, K.K.R. Blockchain-enabled authentication handover with efficient privacy protection in SDN-based 5G networks. IEEE Trans. Netw. Sci. Eng. 2019, 8, 1120–1132. [Google Scholar] [CrossRef]
- Wang, W.; Xu, P.; Yang, L.T. Secure data collection, storage and access in cloud-assisted IoT. IEEE Cloud Comput. 2018, 5, 77–88. [Google Scholar] [CrossRef]
- Akram, J.; Anaissi, A.; Rathore, R.S.; Jhaveri, R.H.; Akram, A. Galtrust: Generative adverserial learning-based framework for trust management in spatial crowdsourcing drone services. IEEE Trans. Consum. Electron. 2024, 70, 6196–6207. [Google Scholar] [CrossRef]
- Wang, J.; Wu, L.; Choo, K.K.R.; He, D. Blockchain-based anonymous authentication with key management for smart grid edge computing infrastructure. IEEE Trans. Ind. Inform. 2019, 16, 1984–1992. [Google Scholar] [CrossRef]
- Sciancalepore, S.; Oligeri, G.; Di Pietro, R. Strength of crowd (SOC)—Defeating a reactive jammer in IoT with decoy messages. Sensors 2018, 18, 3492. [Google Scholar] [CrossRef]
- Rathore, R.S.; Hewage, C.; Kaiwartya, O.; Lloret, J. In-vehicle communication cyber security: Challenges and solutions. Sensors 2022, 22, 6679. [Google Scholar] [CrossRef]
- Khan, M.A.; Salah, K. IoT security: Review, blockchain solutions, and open challenges. Future Gener. Comput. Syst. 2018, 82, 395–411. [Google Scholar] [CrossRef]
- Sharma, P.K.; Singh, S.; Jeong, Y.S.; Park, J.H. Distblocknet: A distributed blockchains-based secure sdn architecture for iot networks. IEEE Commun. Mag. 2017, 55, 78–85. [Google Scholar] [CrossRef]
- Sharma, S.; Chen, K.; Sheth, A. Toward practical privacy-preserving analytics for IoT and cloud-based healthcare systems. IEEE Internet Comput. 2018, 22, 42–51. [Google Scholar] [CrossRef]
- Adil, M.; Jan, M.A.; Liu, Y.; Abulkasim, H.; Farouk, A.; Song, H. A systematic survey: Security threats to UAV-aided IoT applications, taxonomy, current challenges and requirements with future research directions. IEEE Trans. Intell. Transp. Syst. 2022, 24, 1437–1455. [Google Scholar] [CrossRef]
- García-Magariño, I.; Lacuesta, R.; Rajarajan, M.; Lloret, J. Security in networks of unmanned aerial vehicles for surveillance with an agent-based approach inspired by the principles of blockchain. Ad Hoc Netw. 2019, 86, 72–82. [Google Scholar] [CrossRef]
- Patel, A.D.; Jhaveri, R.H.; Shah, K.A.; Patel, A.D.; Rathore, R.S.; Paliwal, M.; Thakker, D. Security Trends in Internet-of-things for Ambient Assistive Living: A Review. Recent Adv. Comput. Sci. Commun. (Former. Recent Pat. Comput. Sci.) 2024, 17, 18–46. [Google Scholar] [CrossRef]
- Bera, S.; Misra, S.; Vasilakos, A.V. Software-defined networking for internet of things: A survey. IEEE Internet Things J. 2017, 4, 1994–2008. [Google Scholar] [CrossRef]
- Zhang, H.; Song, L.; Han, Z.; Poor, H.V. Cooperation techniques for a cellular internet of unmanned aerial vehicles. IEEE Wirel. Commun. 2019, 26, 167–173. [Google Scholar] [CrossRef]
- Akram, J.; Anaissi, A.; Rathore, R.S.; Jhaveri, R.H.; Akram, A. Digital twin-driven trust management in open ran-based spatial crowdsourcing drone services. IEEE Trans. Green Commun. Netw. 2024, 26, 167–173. [Google Scholar] [CrossRef]
- Ouiazzane, S.; Addou, M.; Barramou, F. A Zero-Trust Model for Intrusion Detection in Drone Networks. Int. J. Adv. Comput. Sci. Appl. 2023, 14, 525–537. [Google Scholar] [CrossRef]
- Wazid, M.; Bera, B.; Das, A.K.; Garg, S.; Niyato, D.; Hossain, M.S. Secure communication framework for blockchain-based internet of drones-enabled aerial computing deployment. IEEE Internet Things Mag. 2021, 4, 120–126. [Google Scholar] [CrossRef]
- Wu, L.; Wang, J.; Choo, K.K.R.; He, D. Secure key agreement and key protection for mobile device user authentication. IEEE Trans. Inf. Forensics Secur. 2018, 14, 319–330. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Odelu, V.; Kumar, N.; Susilo, W. Secure remote user authenticated key establishment protocol for smart home environment. IEEE Trans. Dependable Secur. Comput. 2017, 17, 391–406. [Google Scholar] [CrossRef]
- Da, L.; Wang, Y.; Ding, Y.; Xiong, W.; Wang, H.; Liang, H. An efficient certificateless signcryption scheme for secure communication in uav cluster network. In Proceedings of the 2021 IEEE International Conferenceon Parallel & Distributed Processing with Applications, Big Data & Cloud Computing, Sustainable Computing & Communications, Social Computing & Networking (ISPA/BDCloud/SocialCom/SustainCom), New York, NY, USA, 30 September–3 October 2021; IEEE: Piscataway, NJ, USA, 2021. [Google Scholar]
- Thakur, A.; Tyagi, R.; Tripathy, H.K.; Yang, T.; Rathore, R.S.; Mo, D.; Wang, L. Detecting Network Attack using Federated Learning for IoT Devices. In Proceedings of the 2024 International Conference on Intelligent Algorithms for Computational Intelligence Systems (IACIS), Hassan, India, 23–24 August 2024; IEEE: Piscataway, NJ, USA, 2024. [Google Scholar]
- Gope, P.; Sikdar, B. Lightweight and privacy-preserving two-factor authentication scheme for IoT devices. IEEE Internet Things J. 2018, 6, 580–589. [Google Scholar] [CrossRef]
- Awada, U.; Zhang, J.; Chen, S.; Li, S.; Yang, S. Resource-aware multi-task offloading and dependency-aware scheduling for integrated edge-enabled IoV. J. Syst. Archit. 2023, 141, 102923. [Google Scholar] [CrossRef]
- Bumiller, A.; Barais, O.; Challita, S.; Combemale, B.; Aillery, N.; Le Lan, G. A context-driven modelling framework for dynamic authentication decisions. In Proceedings of the 2022 48th Euromicro Conference on Software Engineering and Advanced Applications (SEAA), Gran Canaria, Spain, 31 August–2 September 2022. [Google Scholar]
- Alkadi, O.; Moustafa, N.; Turnbull, B.; Choo, K.K.R. A deep blockchain framework-enabled collaborative intrusion detection for protecting IoT and cloud networks. IEEE Internet Things J. 2020, 8, 9463–9472. [Google Scholar] [CrossRef]
- Sinha, P.; Sahu, D.; Prakash, S.; Yang, T.; Rathore, R.S.; Pandey, V. K A high performance hybrid LSTM CNN secure architecture for IoT environments using deep learning. Sci. Rep. 2025, 15, 9684. [Google Scholar] [CrossRef]
- Wang, Y.; Ding, J.; He, X.; Wei, Q.; Yuan, S.; Zhang, J. Intrusion detection method based on denoising diffusion probabilistic models for uav networks. Mob. Netw. Appl. 2023, 29, 1467–1476. [Google Scholar] [CrossRef]
- Kumar, A.; Srinivasan, K.; Cheng, W.H.; Zomaya, A.Y. Hybrid context enriched deep learning model for fine-grained sentiment analysis in textual and visual semiotic modality social data. Inf. Process. Manag. 2020, 57, 102141. [Google Scholar] [CrossRef]
- Sedjelmaci, H.; Senouci, S.M.; Ansari, N. A hierarchical detection and response system to enhance security against lethal cyber-attacks in UAV networks. IEEE Trans. Syst. Man Cybern. Syst. 2017, 48, 1594–1606. [Google Scholar] [CrossRef]
- Gupta, S.K.; Pandey, V.K.; Alsolbi, I.; Yadav, S.K.; Sahu, P.K.; Prakash, S. An efficient multi-objective framework for wireless sensor network using machine learning. Sci. Rep. 2025, 15, 6370. [Google Scholar] [CrossRef]
- Kostage, K.; Adepu, R.; Monroe, J.; Haughton, T.; Mogollon, J.; Poduvu, S.; Mitra, R. Federated Learning-enabled Network Incident Anomaly Detection Optimization for Drone Swarms. In Proceedings of the 26th International Conference on Distributed Computing and Networking, Hyderabad, India, 4–7 January 2025. [Google Scholar]
- Yan, X.; Han, B.; Su, Z.; Hao, J. SignalFormer: Hybrid Transformer for Automatic Drone Identification Based on Drone RF Signals. Sensors 2023, 23, 9098. [Google Scholar] [CrossRef]
- Won, J.; Seo, S.-H.; Bertino, E. A secure communication protocol for drones and smart objects. In Proceedings of the 10th ACM Symposium on Information, Computer and Communications Security, Singapore, 14–17 April 2015. [Google Scholar]
- Agrawal, S.; Boneh, D.; Boyen, X.; Freeman, D.M. Preventing Pollution Attacks in Multi-Source Network Coding. In Proceedings of the Public Key Cryptography–PKC 2010: 13th International Conference on Practice and Theory in Public Key Cryptography, Paris, France, 26–28 May 2010; Proceedings 13. Springer: Berlin/Heidelberg, Germany, 2010. [Google Scholar]
- Sohail, M.; Latif, Z.; Javed, S.; Biswas, S.; Ajmal, S.; Iqbal, U.; Khan, A.U. Routing protocols in vehicular adhoc networks (vanets): A comprehensive survey. Internet Things 2023, 23, 100837. [Google Scholar] [CrossRef]
- Hussain, R.; Hussain, F.; Zeadally, S. Integration of VANET and 5G Security: A review of design and implementation issues. Future Gener. Comput. Syst. 2019, 101, 843–864. [Google Scholar] [CrossRef]
- Wang, F.; Xu, Y.; Zhang, H.; Zhang, Y.; Zhu, L. 2FLIP: A two-factor lightweight privacy-preserving authentication scheme for VANET. IEEE Trans. Veh. Technol. 2015, 65, 896–911. [Google Scholar] [CrossRef]
- Sahu, D.; Nidhi; Prakash, S.; Pandey, V.K.; Yang, T.; Rathore, R.S.; Wang, L. Edge assisted energy optimization for mobile AR applications for enhanced battery life and performance. Sci. Rep. 2025, 15, 10034. [Google Scholar] [CrossRef] [PubMed]
- Samriya, J.K.; Kumar, M.; Tiwari, R. Energy-aware ACO-DNN optimization model for intrusion detection of unmanned aerial vehicle (UAVs). J. Ambient. Intell. Humaniz. Comput. 2023, 14, 10947–10962. [Google Scholar] [CrossRef]
- Krichen, M. Timed Automata-Based Strategy for Controlling Drone Access to Critical Zones: A UPPAAL Modeling Approach. Electronics 2024, 13, 2609. [Google Scholar] [CrossRef]
- Mekdad, Y.; Aris, A.; Acar, A.; Conti, M.; Lazzeretti, R.; Fergougui, A.E.; Uluagac, S. A comprehensive security and performance assessment of UAV authentication schemes. Secur. Priv. 2024, 7, e338. [Google Scholar] [CrossRef]
- Bouziane, I.; Belmokadem, H.; Moussaoui, M. A Review of Formal Security Verification of Common Internet of Things (IoT) Communication Protocols. In Proceedings of the 2023 7th IEEE Congress on Information Science and Technology (CiSt), Agadir-Essaouira, Morocco, 16–22 December 2023; p. 9081532. [Google Scholar]
- Alsheavi, A.N.; Hawbani, A.; Othman, W.; Wang, X.; Qaid, G.; Zhao, L.; Al-Qaness, M.A. IoT Authentication Protocols: Challenges, and Comparative Analysis. ACM Comput. Surv. 2025, 57, 1–43. [Google Scholar] [CrossRef]
- Gilbert, C.; Gilbert, M.A. Continuous User Authentication on Mobile Devices. Eng. Sci. 2025, 10, 158–173. [Google Scholar]


| Security Property | Verification Tool | Result | Description |
|---|---|---|---|
| Mutual Authentication | OFMC, CL-AtSe | SAFE | Protocol ensures all entities authenticate each other |
| Session Key Secrecy | OFMC, CL-AtSe, SATMC | SAFE | Session keys remain confidential between authenticated parties |
| Message Integrity | OFMC, SATMC | SAFE | Messages cannot be altered without detection |
| Forward Secrecy | CL-AtSe | SAFE | Compromise of current keys does not affect past communications |
| Replay Protection | OFMC, CL-AtSe | SAFE | Protocol resists replay of captured messages |
| Parameter | Value |
|---|---|
| Simulator | NS2 (version 2.35) |
| Simulation duration | 1000 s |
| Simulation area | 1000 m × 1000 m |
| Number of drones | 5–50 |
| Number of users | 1–20 |
| Number of ground stations | 2–8 |
| Number of edge servers | 1–5 |
| Drone mobility model | Random Waypoint |
| Drone speed | 0–20 m/s |
| Communication range | 100 m(drone-to-GCS) |
| Bandwidth | 5 Mbps (D2G), 20 Mbps (G2E), 50 Mbps (E2C) |
| MAC protocol | IEEE 802.11n |
| Propagation model | Two-ray ground |
| Packet size | 512 bytes |
| Cryptographic algorithm | ECC-256 (asymmetric), AES-128-GCM (symmetric) |
| Machine learning model | Ensemble (LSTM + Random Forest) |
| Authentication frequency | Every 300 s |
| Background traffic | CBR (varying intensity) |
| Operation | SecureDrone | LDAP | TAUROT | IoD-Auth | LEMAP |
|---|---|---|---|---|---|
| Digital Signature Generation | 4.2 | 7.8 | 6.5 | 8.9 | 5.3 |
| Signature Verification | 5.1 | 6.9 | 6.2 | 8.4 | 5.8 |
| Key Exchange | 3.8 | 5.7 | 5.3 | 7.2 | 4.5 |
| Symmetric Encryption | 0.7 | 0.8 | 0.9 | 0.8 | 0.8 |
| Symmetric Decryption | 0.8 | 0.9 | 1.0 | 0.9 | 0.9 |
| Hashing | 0.6 | 0.7 | 0.7 | 0.8 | 0.7 |
| Behavior Analysis | 5.2 | N/A | 5.8 | N/A | 4.7 |
| Total | 20.4 | 22.8 | 26.4 | 27.0 | 22.7 |
| Component | SecureDrone | LDAP | TAUROT | IoD-Auth | LEMAP |
|---|---|---|---|---|---|
| Cryptographic Keys | 28 | 52 | 48 | 64 | 42 |
| Session States | 32 | 48 | 42 | 55 | 38 |
| Behavior Profiles | 45 | N/A | 51 | N/A | 47 |
| Authentication Cache | 18 | 42 | 35 | 47 | 31 |
| Code Footprint | 50 | 65 | 60 | 72 | 58 |
| Total | 173 | 207 | 236 | 238 | 216 |
| Protocol | Message Count | Average Size (bytes) | Total Size (KB) | Authentication Rounds |
|---|---|---|---|---|
| SecureDrone | 4 | 328 | 1.28 | 2 |
| LDAP | 6 | 319 | 1.87 | 3 |
| TAUROT | 5 | 338 | 1.65 | 2.5 |
| IoD-Auth | 7 | 328 | 2.24 | 3.5 |
| LEMAP | 5 | 315 | 1.54 | 2.5 |
| Metric | SecureDrone | LDAP | TAUROT | IoD-Auth | LEMAP | Improvement |
|---|---|---|---|---|---|---|
| Computational Overhead (ms) | 31.8 | 48.7 | 47.8 | 55.2 | 43.8 | 30% avg. reduction |
| Authentication Latency (ms) | 102.3 | 156.7 | 150.4 | 168.5 | 135.2 | 25% avg. reduction |
| Memory Usage (KB) | 258 | 402 | 384 | 453 | 368 | 40% avg. reduction |
| Energy Consumption (mJ) | 42.5 | 68.3 | 63.7 | 75.4 | 57.9 | 35% avg. reduction |
| Communication Messages | 4 | 6 | 5 | 7 | 5 | 28% avg. reduction |
| Message Size (KB) | 1.28 | 1.87 | 1.65 | 2.24 | 1.54 | 29% avg. reduction |
| Auth. Success (No Attack) (%) | 99.8 | 99.7 | 99.7 | 99.6 | 99.7 | 0.1% improvement |
| Auth. Success (Under Attack) (%) | 95.6 | 85.5 | 88.4 | 87.2 | 87.7 | 9% avg. improvement |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Pandey, V.K.; Prakash, S.; Ranjan, A.; Jha, S.K.; Liu, X.; Rathore, R.S. An Efficient Framework for Secure Communication in Internet of Drone Networks Using Deep Computing. Designs 2025, 9, 61. https://doi.org/10.3390/designs9030061
Pandey VK, Prakash S, Ranjan A, Jha SK, Liu X, Rathore RS. An Efficient Framework for Secure Communication in Internet of Drone Networks Using Deep Computing. Designs. 2025; 9(3):61. https://doi.org/10.3390/designs9030061
Chicago/Turabian StylePandey, Vivek Kumar, Shiv Prakash, Aditya Ranjan, Sudhanshu Kumar Jha, Xin Liu, and Rajkumar Singh Rathore. 2025. "An Efficient Framework for Secure Communication in Internet of Drone Networks Using Deep Computing" Designs 9, no. 3: 61. https://doi.org/10.3390/designs9030061
APA StylePandey, V. K., Prakash, S., Ranjan, A., Jha, S. K., Liu, X., & Rathore, R. S. (2025). An Efficient Framework for Secure Communication in Internet of Drone Networks Using Deep Computing. Designs, 9(3), 61. https://doi.org/10.3390/designs9030061







