Information Protection in Complexes with Unmanned Aerial Vehicles Using Moving Target Technology
Abstract
1. Introduction
- To consider the features and types of confidential information processed in complexes with UAV;
- To consider and analyze systems for protecting information from unauthorized access of complexes with UAV;
- To analyze the application of MTD technology to protect information in computer networks;
- To develop a way to improve the effectiveness of the system for protecting information from unauthorized access of complexes with UAV using MTD technology;
- To propose an approbation option for the proposed method for improving the effectiveness of the system for protecting information from unauthorized access of complexes with UAV using MTD technology.
2. Materials and Methods
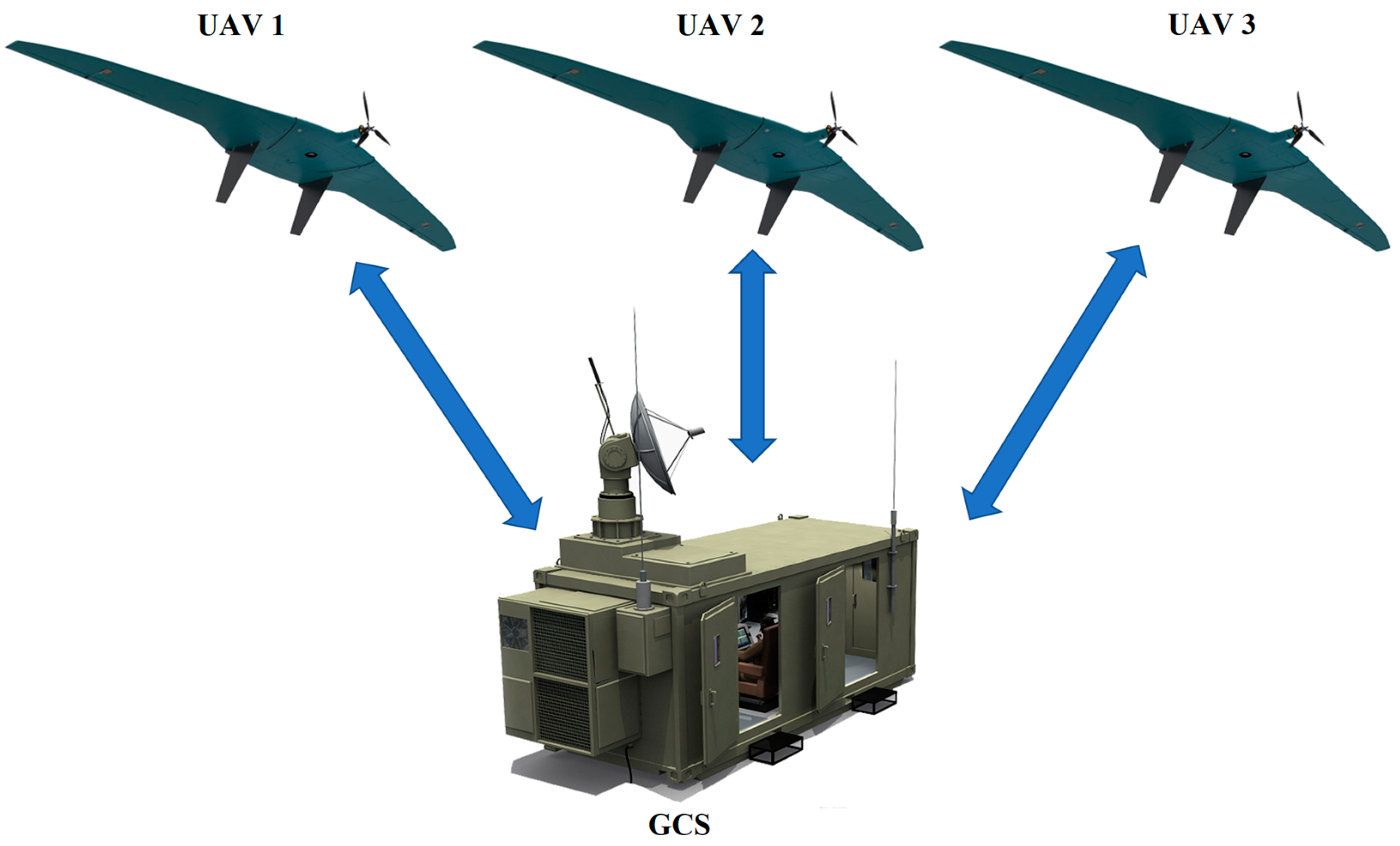
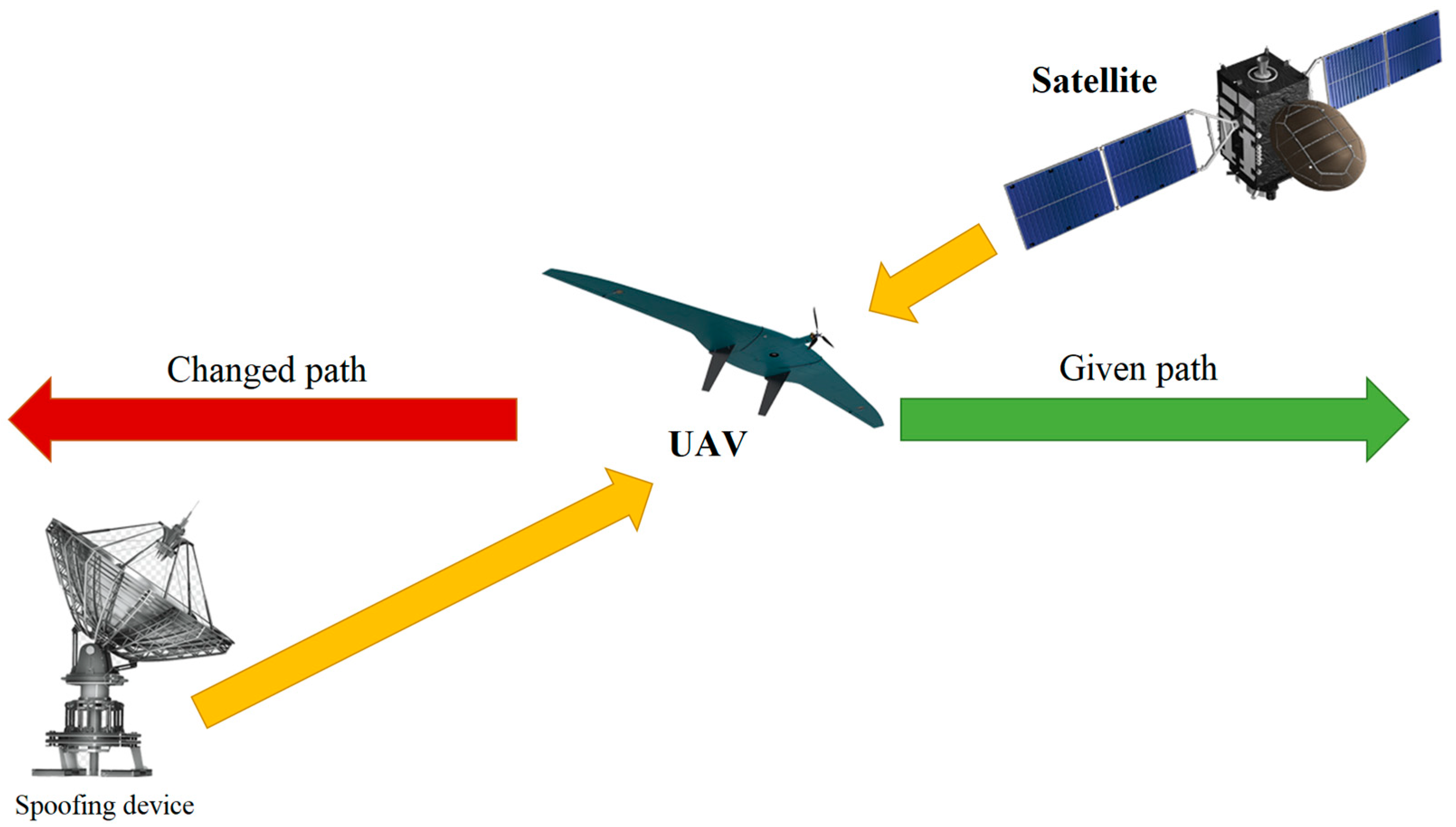
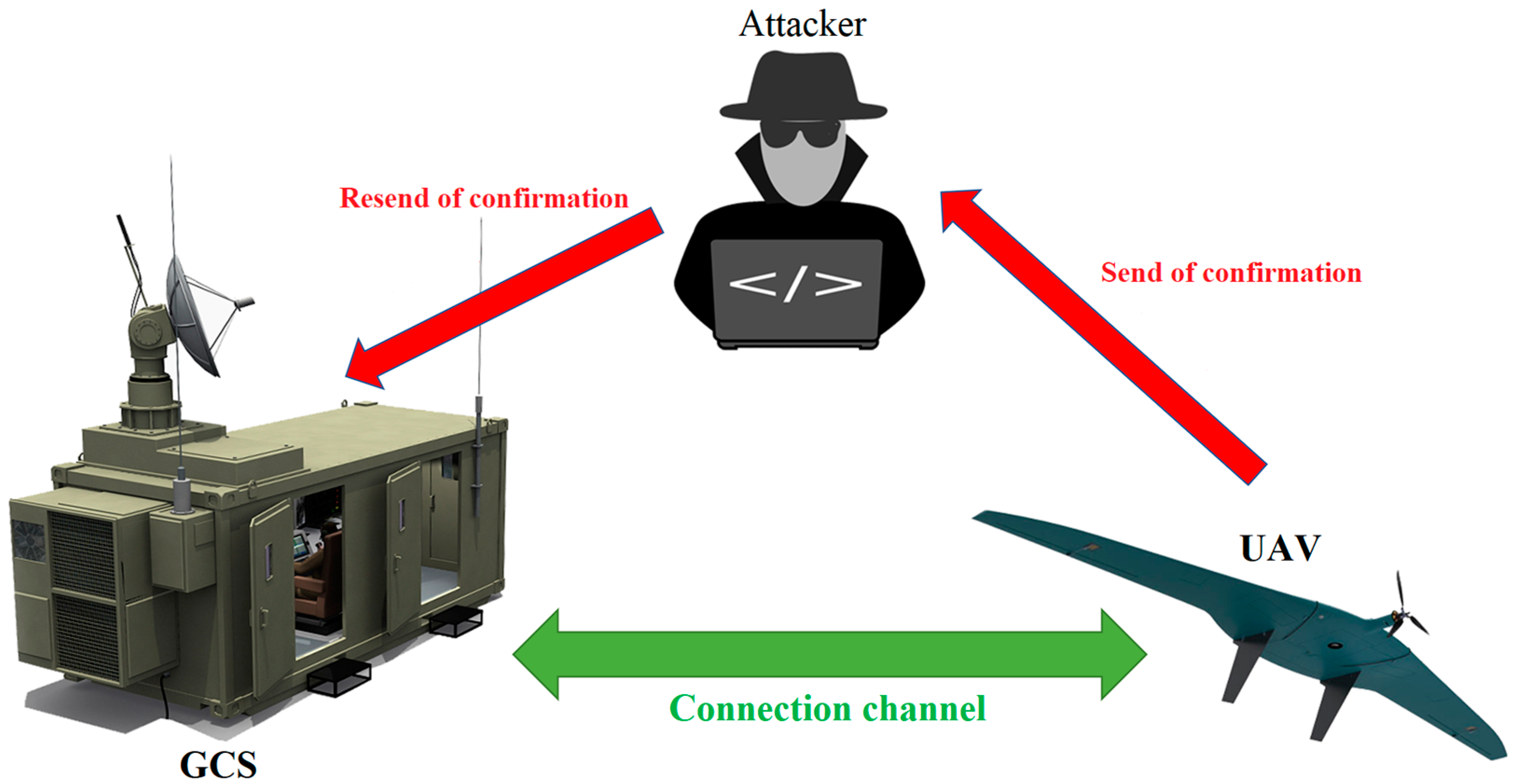
- “UAV—GCS”;
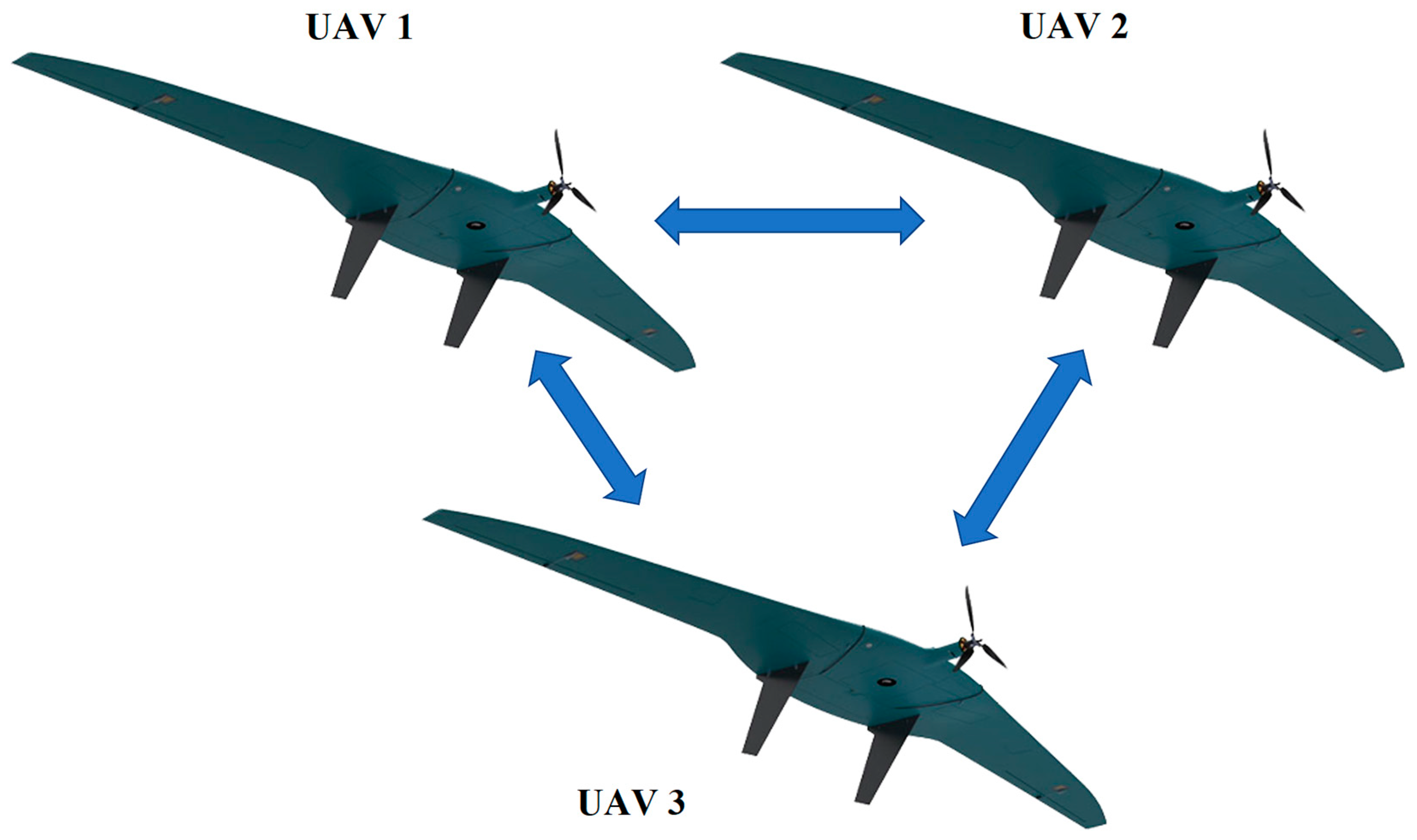
- “UAV—UAV”;
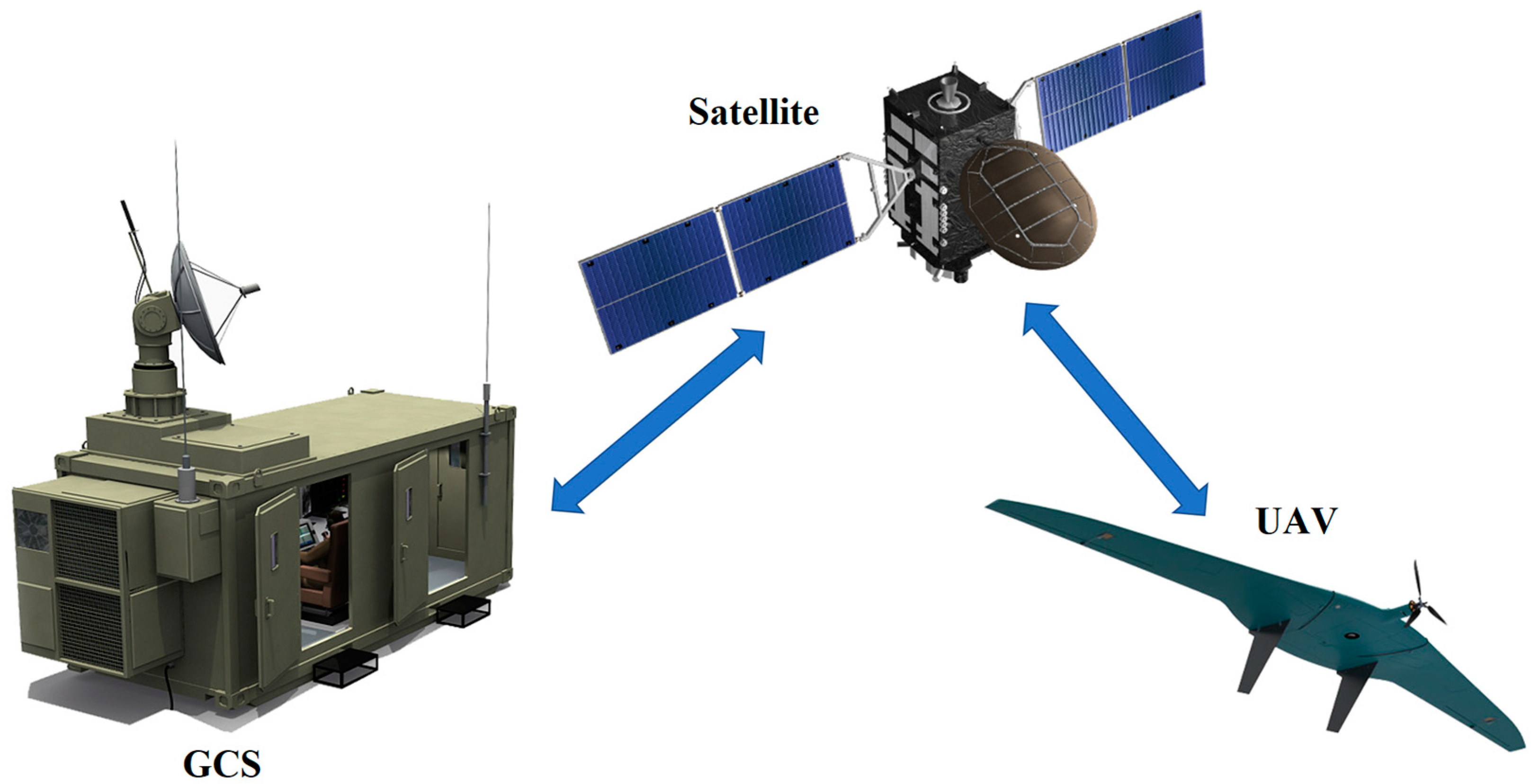
- “UAV—Sputnik”.
- Control traffic includes control and monitoring commands, commands relating to a specific mission, and real-time status of UAV (for example, telemetry data, battery level, etc.);
- Coordination traffic controls the interaction between several UAV during a flight mission and tasks performed independently of GCS, for example, collision avoidance processes;
- Sensing traffic includes readings from on-board sensors that are transmitted to GCS (telemetry);
- Special information includes photos and videos.
3. Results and Discussion
- A constant dynamic reconfiguration of the protected system;
- Taking countermeasures that make the attack impossible once it has been determined.
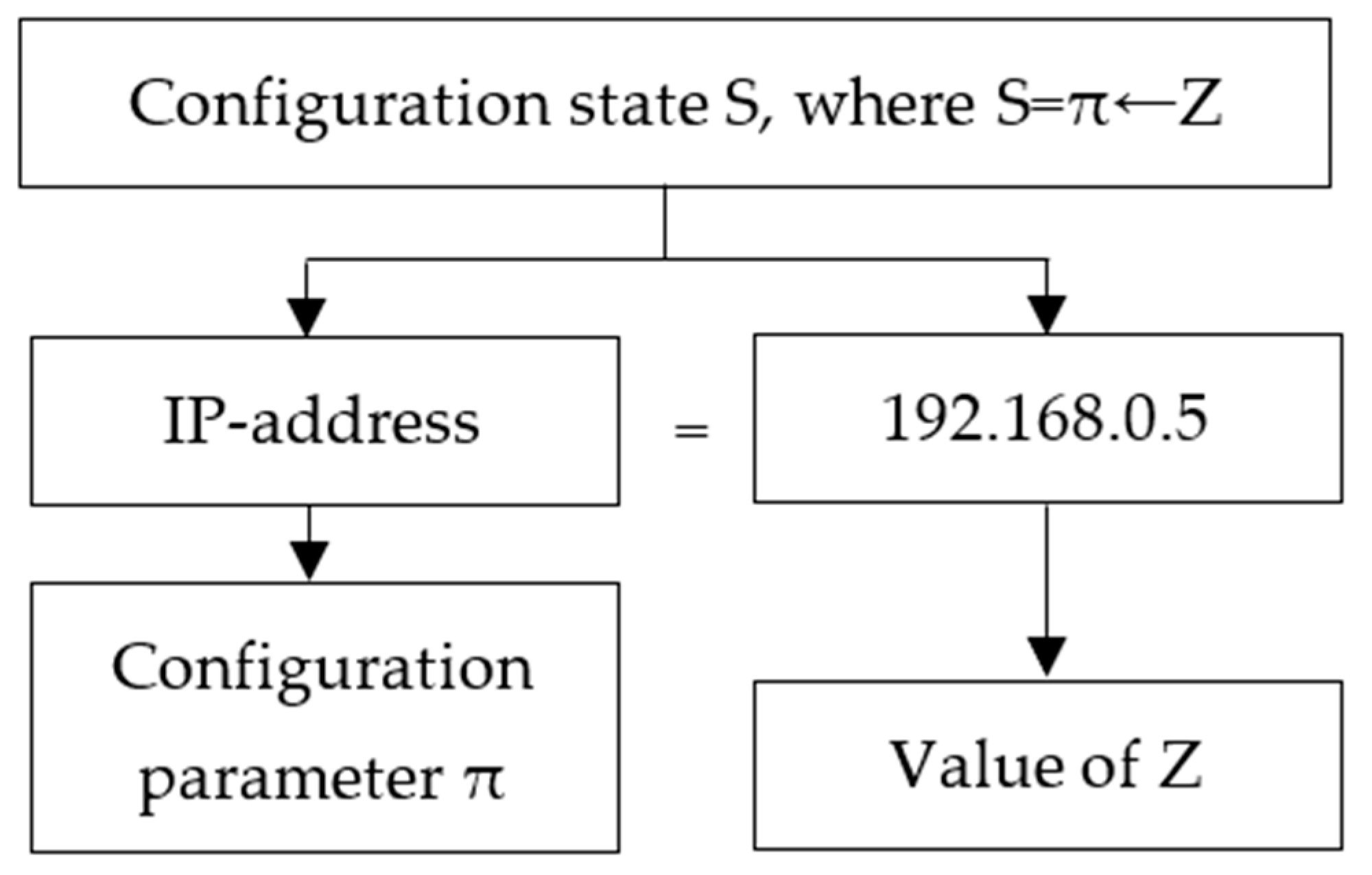
- MTD at the network level, which changes the way it functions, for example, using IP hopping technique, in which IP address changes periodically, or we use random port numbers and fake hosts;
- MTD at the host level is directed to changes in the host, for example, to a periodic change in configuration or name;
- MTD at the application level changes their types and versions and randomizes the location of address space layout randomization (ASLR) and the source code with compilation processes.
- Exploration surface;
- Attack surface;
- Detection surface;
- Prevention surface.
- Develop new or certify ready-made solutions using MTD technology;
- Adapt these solutions, taking into account the peculiarities of networks of complexes with UAV;
- Test previously adapted solutions in order to evaluate their effectiveness.
- The tool should demonstrate realistic network behavior;
- It is necessary to be able to use real network security or introduction testing tools on the network;
- It is necessary to be able to flexibly configure all the necessary parameters and elements of the network.
- Attacker’s network, which includes an attacker, a switch, and a router. In this topology, it is an attacker connected to UAV-1. At the same time, it is important to note that the question of the mechanism for the appearance of a malicious participant in network interaction remains outside the scope of this work;
- Network of the first UAV, which includes three hosts representing two sensors and a flight controller host; in addition, there is a switch and a router. It is connected to the ground control network;
- Network of the second UAV, similar to the network of the first UAV, which also includes two hosts that are sensors, a flight controller host, a switch, and a router. It is connected to a GCS network;
- GCS network includes a host of GCS, a switch, and a router connected for both drones.
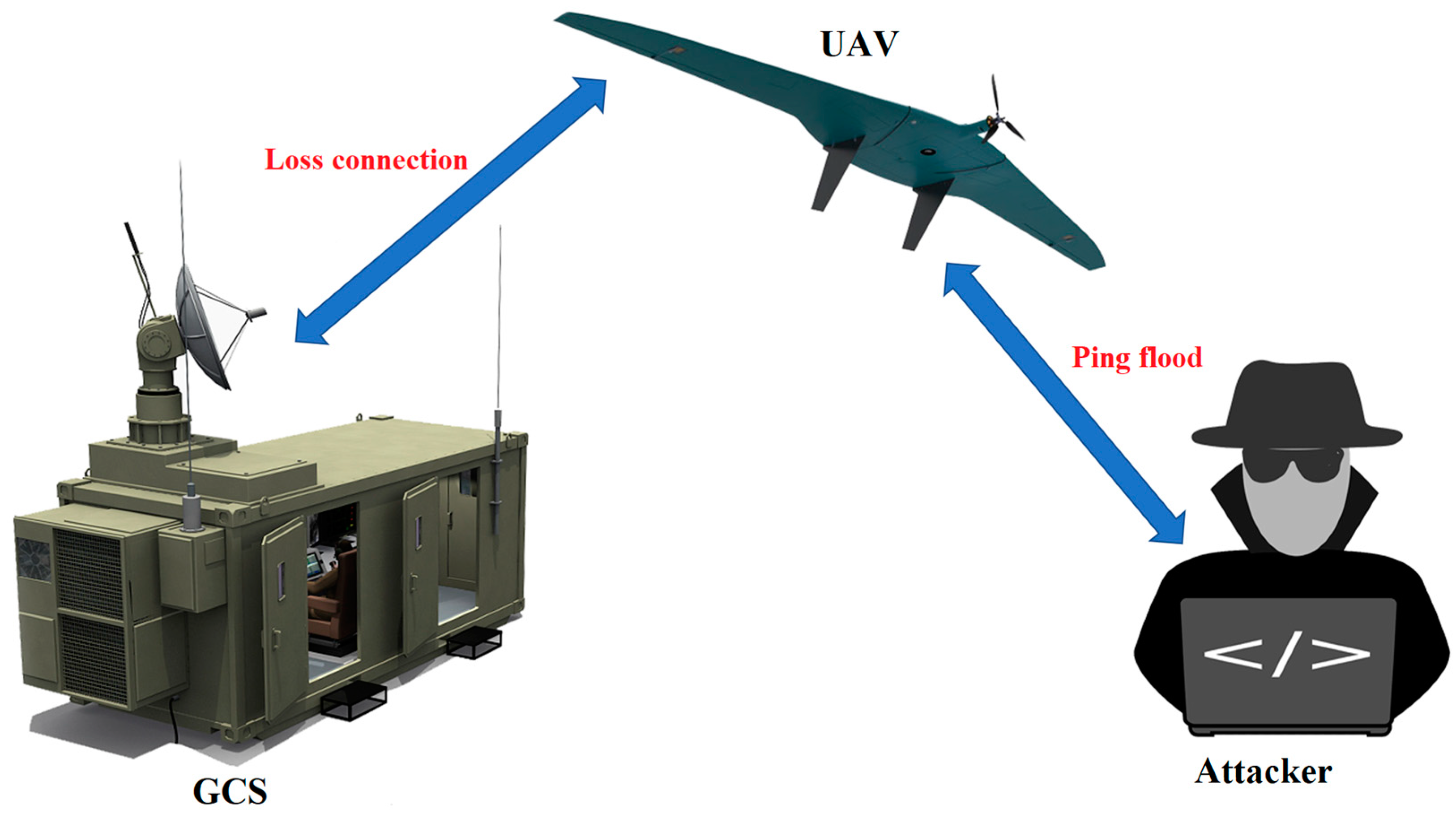
- Design implementation was installed on the host flight controller of subnet of UAV №1. Sensor hosts send simple ping requests to the host controller, and the host controller sends requests to GCS to emulate normal traffic and check the availability of devices;
- An UAV №2 subnetwork host flight controller has standard security settings, no design implementation has been installed on it, and these hosts communicate with each other in the same way as UAV №1 network;
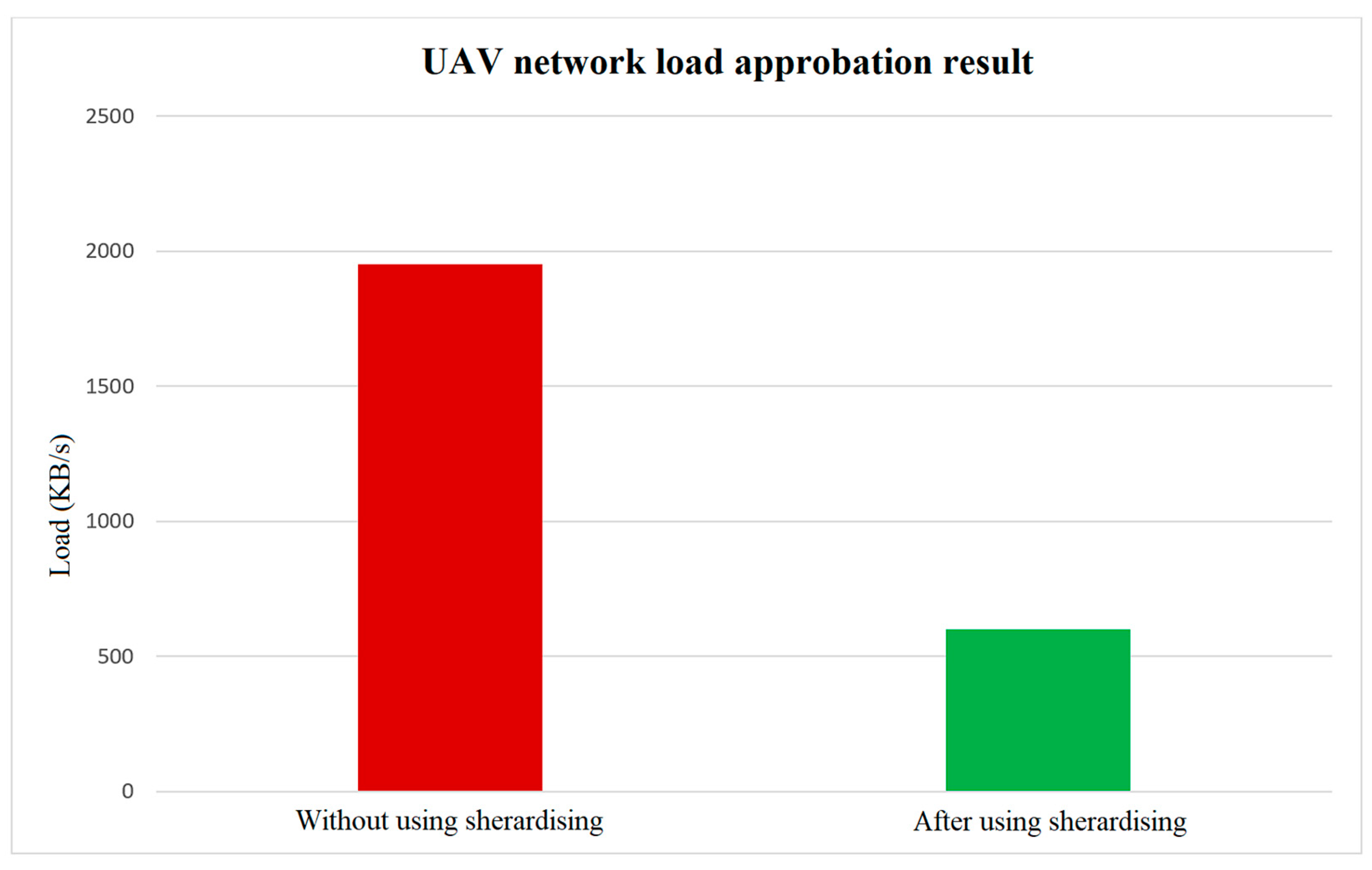
- At a random time, the attacker scans the network of UAV №1, determines the hosts, and launches an attack on the host flight controller; this process is repeated 10 times to obtain average results.
4. Conclusions
- The features and types of confidential information processed in telecommunication systems and networks of complexes with UAV are considered;
- The information security systems of telecommunication systems and networks of complexes with UAV are considered and analyzed;
- The application of MTD technology for information protection in computer networks is considered;
- The method to improve the effectiveness of the system for protecting information from unauthorized access of complexes with UAV using MTD technology has been developed;
- The variant of approbation for the proposed method for improving the effectiveness of the system for protecting information from unauthorized access of complexes with UAV using the technology of MTD is proposed.
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Ryapukhin, A.V.; Karpukhin, E.O.; Zhuikov, I.O. Method of Forming Various Configurations of Telecommunication System Using Moving Target Defense. Inventions 2022, 7, 83. [Google Scholar] [CrossRef]
- Breakthrough Technologies 2014. MIT Technology Review. Available online: https://www.technologyreview.com/10-breakthrough-technologies/2014/ (accessed on 15 November 2022).
- Global Drones Market Report. TechSciResearch. Available online: https://www.techsciresearch.com/report/global-drones-market/1345.html (accessed on 15 November 2022).
- Andre, T.; Hummel, K.A.; Schoellig, A.P.; Yanmaz, E.; Asadpour, M.; Bettstetter, C.; Grippa, P.; Hellwagner, H.; Sand, S.; Zhang, S. Application-driven design of aerial communication networks. IEEE Comm. Mag. 2014, 52, 129–137. [Google Scholar] [CrossRef]
- Dinger, J.; Hartenstein, H. Defending the sybil attack in p2p networks: Taxonomy, challenges, and a proposal for self-registration. In Proceedings of the First International Conference on Availability, Reliability and Security (ARES’06), Vienna, Austria, 20–22 April 2006; pp. 1–8. [Google Scholar] [CrossRef]
- Mushtaq, M.F.; Jamel, S.; Deris, M.M. Triangular Coordinate Extraction (TCE) for Hybrid Cubes. J. Eng. Appl. Sci. 2017, 12, 2164–2169. [Google Scholar]
- Rowaihy, H.; Enck, W.; McDaniel, P.; La Porta, T. Limiting sybil attacks in structured p2p networks. In Proceedings of the IEEE INFOCOM 2007—26th IEEE International Conference on Computer Communications, Anchorage, AK, USA, 6–12 May 2007; pp. 2596–2600. [Google Scholar]
- Naoumov, N.; Ross, K. Exploiting p2p systems for ddos attacks. In Proceedings of the 1st International Conference on Scalable Information Systems, Hong Kong, China, 30 May–1 June 2006; p. 47-es. [Google Scholar]
- Podkorytov, A.; Ryapukhin, A. The reduction of computational cost in GNSS data network processing. AIP Conf. Proc. 2022, 2467, 030028. [Google Scholar]
- Burova, A.; Ryapukhin, A. Reduction of the number of multiplication operations in digital signal processing algorithms by classical methods of discrete Fourier transform. AIP Conf. Proc. 2021, 2402, 040002. [Google Scholar]
- Alladi, T.; Chamola, V.; Zeadally, S. Industrial control systems: Cyberattack trends and countermeasures. Comp. Comm. 2020, 155, 1–8. [Google Scholar] [CrossRef]
- Chen, J.; Feng, Z.; Wen, J.Y.; Liu, B.; Sha, L. A container-based DoS attack-resilient control framework for real-time UAV systems. In Proceedings of the 2019 Design, Automation & Test in Europe Conference & Exhibition (DATE), Grenoble, France, 25–29 March 2019; pp. 1222–1227. [Google Scholar]
- Hping3. Available online: https://www.kali.org/tools/hping3 (accessed on 15 November 2022).
- Vattapparamban, E.; Güvenç, I.; Yurekli, A.I.; Akkaya, K.; Uluağaç, S. Drones for smart cities: Issues in cybersecurity, privacy, and public safety. In Proceedings of the 2016 International Wireless Communications and Mobile Computing Conference (IWCMC), Paphos, Cyprus, 5–9 September 2016; pp. 216–221. [Google Scholar]
- Gaspar, J.; Ferreira, R.; Sebastião, P.; Souto, N. Capture of UAVs through GPS spoofing. In Proceedings of the 2018 Global Wireless Summit (GWS), Chiang Rai, Thailand, 25–28 November 2018; pp. 21–26. [Google Scholar]
- Iran Hijacked US Drone, Says Iranian Engineer. Available online: https://www.csmonitor.com/World/Middle-East/2011/1215/Exclusive-Iran-hijacked-US-drone-says-Iranian-engineer (accessed on 15 November 2022).
- Conti, M.; Dragoni, N.; Lesyk, V. A Survey of Man in the Middle Attacks. IEEE Comm. Surv. Tutor. 2016, 18, 2027–2051. [Google Scholar] [CrossRef]
- Rodday, N.M.; Schmidt, R.D.O.; Pras, A. Exploring security vulnerabilities of unmanned aerial vehicles. In Proceedings of the NOMS 2016—2016 IEEE/IFIP Network Operations and Management Symposium, Istanbul, Turkey, 25–29 April 2016; pp. 993–994. [Google Scholar]
- VideoJak: Hijacking IP Video Calls. Available online: http://videojak.sourceforge.net (accessed on 15 November 2022).
- Ozmen, M.O.; Yavuz, A.A. Dronecrypt-an efficient cryptographic framework for small aerial drones. In Proceedings of the MILCOM 2018—2018 IEEE Military Communications Conference (MILCOM), Los Angeles, CA, USA, 29–31 October 2018; pp. 1–6. [Google Scholar]
- Rango, A.; Laliberte, A.; Steele, C.; Herrick, J.E.; Bestelmeyer, B.; Schmugge, T.; Roanhorse, A.; Jenkins, V. Using unmanned aerial vehicles for rangelands: Current applications and future potentials. Environ. Pract. 2006, 8, 159–168. [Google Scholar] [CrossRef]
- Jumaat, N.F.H.; Ahmad, B.; Dutsenwai, H.S. Land cover change mapping using high resolution satellites and unmanned aerial vehicle. IOP Conf. Ser.: Earth Environ. Sci. 2018, 169, 012076. [Google Scholar] [CrossRef]
- Yaacoub, J.P.A.; Noura, M.; Noura, H.N.; Salman, O.; Yaacoub, E.; Couturier, R.; Chehab, A. Securing internet of medical things systems: Limitations, issues and recommendations. Future Gener. Comput. Syst. 2020, 105, 581–606. [Google Scholar] [CrossRef]
- Johnson, L.K.; Dorn, A.W.; Webb, S.; Kreps, S.; Krieger, W.; Schwarz, E.; Shpiro, S.; Walsh, P.F.; Wirtz, J.J. An INS Special Forum: Intelligence and drones/Eyes in the sky for peacekeeping: The emergence of UAVs in UN operations/The democratic deficit on drones/The German Approach to Drone Warfare/Pursuing peace: The strategic limits of drone warfare/Seeing but unseen: Intelligence drones in Israel/Drone paramilitary operations against suspected global terrorists: US and Australian perspectives/The ‘Terminator Conundrum’and the future of drone warfare. Intell. Natl. Secur. 2017, 32, 411–440. [Google Scholar]
- Cavoukian, A. Privacy and Drones: Unmanned Aerial Vehicles; Information and Privacy Commissioner of Ontario: Toronto, ON, Canada, 2012. [Google Scholar]
- Mekdad, Y.; Aris, A.; Babun, L.; Fergougui, A.E.; Conti, M.; Lazzeretti, R.; Uluagac, A.S. A Survey on Security and Privacy Issues of UAVs, 2021. Available online: https://arxiv.org/abs/2109.14442 (accessed on 15 November 2022).
- Majeed, R.; Abdullah, N.A.; Mushtaq, M.F.; Kazmi, R. Drone security: Issues and challenges. Int. J. Adv. Comput. Sci. Appl. 2021, 12. Available online: https://www.researchgate.net/publication/352086927_Drone_Security_Issues_and_Challenges (accessed on 15 November 2022). [CrossRef]
- Hassija, V.; Chamola, V.; Agrawal, A.; Goyal, A.; Luong, N.C.; Niyato, D.; Yu, F.R.; Guizani, M. Fast, reliable, and secure drone communication: A comprehensive survey. IEEE Commun. Surv. Tutor. 2021, 23, 2802–2832. [Google Scholar] [CrossRef]
- Lei, C.; Ma, D.H.; Zhang, H.Q. Optimal strategy selection for moving target defense based on Markov game. IEEE Access 2017, 5, 156–169. [Google Scholar] [CrossRef]
- Gartner’s Top 10 Security Predictions 2016. Available online: https://www.gartner.com/smarterwithgartner/top-10-security-predictions-2016/ (accessed on 15 November 2022).
- Lei, C.; Zhang, H.Q.; Tan, J.L.; Zhang, Y.C.; Liu, X.H. Moving Target Defense Techniques: A Survey. Secur. Commun. Netw. 2018, 2018, 3759626. [Google Scholar] [CrossRef]
- Al-Shaer, E.; Duan, Q.; Jafarian, J.H. Random host mutation for moving target defense. In Proceedings of the International Conference on Security and Privacy in Communication Systems, Berlin, Germany, 3 September 2012; pp. 310–327. [Google Scholar]
- Carter, K.M.; Riordan, J.F.; Okhravi, H. A game theoretic approach to strategy determination for dynamic platform defenses. In Proceedings of the First ACM Workshop on Moving Target Defense, Scottsdale, AZ, USA, 3 November 2014; pp. 21–30. [Google Scholar]
- Thompson, M.; Evans, N.; Kisekka, V. Multiple OS rotational environment an implemented moving target defense. In Proceedings of the 2014 7th International Symposium on Resilient Control Systems (ISRCS), Denver, CO, USA, 19–21 September 2014; pp. 1–6. [Google Scholar]
- Chowdhary, A.; Pisharody, S.; Huang, D. SDN based scalable MTD solution in cloud network. In Proceedings of the 2016 ACM Workshop on Moving Target Defense, Vienna, Austria, 24 October 2016; pp. 27–36. [Google Scholar]
- El Mir, I.; Chowdhary, A.; Huang, D.; Pisharody, S.; Kim, D.S.; Haqiq, A. Software defined stochastic model for moving target defense. In Proceedings of the International Afro-European Conference for Industrial Advancement, 18 August 2017; pp. 188–197. [Google Scholar]
- Debroy, S.; Calyam, P.; Nguyen, M.; Stage, A.; Georgiev, V. Frequency-minimal moving target defense using software-defined networking. In Proceedings of the 2016 International Conference on Computing, Networking and Communications (ICNC), Kauai, HI, USA, 15–18 February 2016; pp. 1–6. [Google Scholar]
- Venkatesan, S.; Albanese, M.; Cybenko, G.; Jajodia, S. A moving target defense approach to disrupting stealthy botnets. In Proceedings of the 2016 ACM Workshop on Moving Target Defense, Vienna, Austria, 24 October 2016; pp. 37–46. [Google Scholar]
- Sengupta, S.; Chowdhary, A.; Huang, D.; Kambhampati, S. Moving target defense for the placement of intrusion detection systems in the cloud. In Proceedings of the International Conference on Decision and Game Theory for Security, Seattle, WA, USA, 29–31 October 2018; pp. 326–345. [Google Scholar]
- Colbaugh, R.; Glass, K. Predictability-oriented defense against adaptive adversaries. In Proceedings of the 2012 IEEE International Conference on Systems, Man, and Cybernetics (SMC), Seoul, Korea, 14–17 October 2012; pp. 2721–2727. [Google Scholar]
- Chowdhary, A.; Pisharody, S.; Alshamrani, A.; Huang, D. Dynamic game based security framework in SDN-enabled cloud networking environments. In Proceedings of the ACM International Workshop on Security in Software Defined Networks & Network Function Virtualization, Scottsdale, AZ, USA, 24 March 2017; pp. 53–58. [Google Scholar]
- The Software that Empowers Network Professionals. Available online: https://gns3.com (accessed on 15 November 2022).
- OMNeT++ 6.0. Available online: https://omnetpp.org (accessed on 15 November 2022).
- NS-3 Network Simulator. Available online: https://www.nsnam.org (accessed on 15 November 2022).
- Virtual PC Simulator. SourceForge. Available online: https://sourceforge.net/projects/vpcs/?source=directory (accessed on 15 November 2022).
- Parrot Security Os. Available online: https://www.parrotsec.org (accessed on 15 November 2022).
- Nmap. Available online: https://nmap.org (accessed on 15 November 2022).
- Wang, C.N.; Yang, F.C.; Vo, N.T.; Nguyen, V.T.T. Wireless Communications for Data Security: Efficiency Assessment of Cybersecurity Industry—A Promising Application for UAVs. Drones 2022, 6, 363. [Google Scholar] [CrossRef]

Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Pikov, V.; Ryapukhin, A.; Veas Iniesta, D. Information Protection in Complexes with Unmanned Aerial Vehicles Using Moving Target Technology. Inventions 2023, 8, 18. https://doi.org/10.3390/inventions8010018
Pikov V, Ryapukhin A, Veas Iniesta D. Information Protection in Complexes with Unmanned Aerial Vehicles Using Moving Target Technology. Inventions. 2023; 8(1):18. https://doi.org/10.3390/inventions8010018
Chicago/Turabian StylePikov, Vitaly, Anatoly Ryapukhin, and Daniela Veas Iniesta. 2023. "Information Protection in Complexes with Unmanned Aerial Vehicles Using Moving Target Technology" Inventions 8, no. 1: 18. https://doi.org/10.3390/inventions8010018
APA StylePikov, V., Ryapukhin, A., & Veas Iniesta, D. (2023). Information Protection in Complexes with Unmanned Aerial Vehicles Using Moving Target Technology. Inventions, 8(1), 18. https://doi.org/10.3390/inventions8010018





