1. Introduction
The worldwide demand for electricity is expected to rise by 1.3% per year until 2040, primarily due to the effect of globalization [
1]. This surge in demand has led to the interconnection of a wide range of distributed energy resources and electricity infrastructures, which are primarily the different electricity generation sites and the distribution channels. This inter-connectivity is commonly known as the Internet of Energy (IoE). The data generated from the various elements of IoE need to be managed securely as they are subject to hacking and cyberattacks, which include jamming, false data injection, and distributed denial-of-service attacks [
2]. For example, a cyberattack on the U.S. grid in Western US created periodic blind spots at a grid control center and several small power generation sites for about 10 h on 5 March 2019. Contemporary power systems encountered remarkable advancement of data security in recent years. Contrary to traditional power systems, the NZEM is yet to adopt the advancement. One of the reasons is governing administration issues about company fixed revenues for line companies. There are distributed generation and several regional power suppliers in NZEM. Data security of the suppliers is an important term for any power market, and NZME is not an exception.
Supervisory Control and Data Acquisition (SCADA) systems are an integral part of the physical infrastructure of NZEM that monitors and stores real-time data of the grid network. A SCADA system is generally composed of a centralized control module and associated field level devices, i.e., sensors and actuators. The control module of SCADA provides a decision support platform that performs the related control task of the system. Given the dynamics of the SCADA system, the key features that make the SCADA system more susceptible to cyberattacks lie within its architecture and standard communication protocols. In many cases, the SCADA system adopts standardized technologies without enhancing the default security protocols. This practice can allow malicious agents to take over the SCADA system easily by exploiting the known vulnerabilities of the default security protocols. Subsequently, the usage of an unsecured network to connect multiple control modules also makes the system open for malicious attacks. Recently, most of the technical information about the specific SCADA control modules have been widely available as open-source content. This information, however, can be used to compromise the security of the entire SCADA system. Currently, there are many methods in place to reinforce SCADA network security that range from improved authentication for the user for access control, better firewalls, and intrusion detection system, protocol vulnerability assessment, and improved security for the connected devices and platforms operating system. However, all the typical vulnerabilities are still being exploited by the adversaries utilizing improved malicious agents and approaches. An example of a cyberattack aiming at SCADA system vulnerabilities in recent years was the Ukrainian power outage in 2015.
Blockchain technology, equipped with the key features of digital, chronological, time-stamped, distributed ledger, consensus-based, and cryptographically sealed, is considered as a potential tool to provide the data security of the electricity market. The smart contract in blockchain can be used not only to enhance the speed and security of a smart grid [
3] but also to prevent the retroactive alteration of data. Blockchain technology has immense prospects in better and secured streamlining of management of SCADA data transactions and peer-to-peer data transactions. The prospect of implementing blockchain technology for a regulated electricity market is investigated in this paper, and a decentralized end-to-end Ethereum Blockchain prototype is proposed to enhance the data security between the different layers of the current SCADA systems used in regulated electricity market like NZEM. In comparison to other existing blockchain protocols, Ethereum has more durability, which implies that it has reduced possibility of becoming obsolete since it stores data immutably. Its decentralized and distributed peer-to-peer data transaction is unique compared to other existing cryptocurrencies. Moreover, Ethereum’s smart contracts feature eradicates the demand for a third-party payment system. Moreover, it provides users with a platform and programming language for building the applications. Therefore, in this work we have considered the Ethereum blockchain to address the following major research inquiries for a regulated market using SCADA system:
(1) How can blockchain smart contracts support the state-owned regulated market?
(2) How can blockchain safe-guard grid data for the communication level of the SCADA system which is sensitive to cyber-threat?
(3) What are the prospective privacy and safety regulation for applying blockchain to NZEM?
The remaining paper is structured as follows. While
Section 2 presents a review of the data security in power systems, the current status of data security in regulated and deregulated electricity markets is presented in
Section 3.
Section 4 discusses the decentralized Ethereum blockchain-based end-to-end data security prototype, and the paper concludes in
Section 5.
2. A Review of Data Security in Power System and introduction of Blockchain
Data security in power system offers new prospects to maximize the energy performance of the power market. It provides the efficiency, and security for the fundamental detailed facilities of energy suppliers [
4]. Modern cyber-security systems for power systems have turned complex and the cyberattacks are becoming smarter every day. The profound incorporation of cyberattacks can deliver false information to the control management facility team and eventually can result in system disorder, fiscal impairment, or critical consequences such as long hour’s blackouts. A current severe example of cyberattack was the 2015 Ukraine blackout [
5].
False data injection attack refers to the manipulation of system data to trick away the control center without the flag service [
6]. There are several studies [
5,
7] that exhibit the effect of False Data Injection Attacks (FDIA) on the modern grid system. However, in reality, grid security can be compromised not only by FDIAs but also by other forms of cyberattack namely denial of service (Dos), cyber topology attacks and data framing attacks [
8,
9]. Hence it is very essential to ensure the integrity and consistency of data to make the grid more secure and reliable. Several strategies have been suggested to identify and prevent cyberattacks depending on traditional centralized data communication and storage process [
10]. Moreover, currently existing communication and measured meter data storage mechanisms are not fully protected against a cyberattacks. In some cases, even if the meters have been upgraded to PMU (phase measurement systems), they are still vulnerable to cyber-threats due to their dependency on global positioning system. Enhancing the self-defensive capabilities of modern power systems against cyberattacks requires the adoption of state-of-the-art innovations in distributed system security technologies. In this regard a modern distributed power system can be viewed as distributed advanced measurement infrastructure that includes distributed data acquisition, data monitoring, and storage on both grid side and demand side [
11].
First, introduced in 2008, blockchain is designed to facilitate peer to peer electronic transactions directly without the involvement of a third party [
12]. In blockchain, each peer works as a node to form a distributed network where they participate in estimating the solution to a hash-based mathematical problem to ensure the integrity of the transaction. Each time when a transaction is made, it is encapsulated in a block and added to the blockchain framework. The recorded block contents are called as ledgers, and all the information is updated synchronously to the entire network so that the record of the ledger is kept by each peer in the network. Since the advent of blockchain, technology has been mostly focused on the financial domain in the form of maintaining virtual currency, cross border payments and settlements, security issuance, and payments. The most prominent application of blockchain technology is the Bitcoin system, a cryptocurrency framework which maintains a global distributed ledger for peer to peer transaction. Following the Bitcoin system, some companies, such as Etherium, Coinbase, Ripple, Chain, Circle, etc., have been set up in recent years. Among other works, the blockchain swarm system by Ferrer [
13] and Sharples and Domingue [
14] is mentionable and has good prospects to be implemented for power systems.
Recently, there has been a shift observed in the energy market towards a distributed market structure [
15] with increased number of prosumers and increase volume of data. In a centralized market structure, storing this large volume of data has higher costs, and the risk of compromising all data is very high under any cyberattack. It is also difficult for the market entity to access the previous data if they are stored in one organization under a centralized market. Hence, transparency issues also arise for the market operators. Addressing this problem, many authors have provided different techniques on adopting blockchain technology in the energy market to ensure better data security and market operation.
In [
16], a distributed blockchain based protection framework has been proposed to improve the data security by resisting external network attacks in a modern power system. This proposed framework utilizes distributed security features of the blockchain system and uses smart energy meter as node to keep the recorded power data with a distributed ledger which ensures the integrity and consistency of the data.
In [
17], a sovereign blockchain based smart grid management system is being proposed to protect the data of the consumers for ensuring the transparency and integrity of the data. It also protects the data from tampering under any cyberattack. This proposed system uses smart contacts to detect the grid operation and identify any malicious agents in the system.
In [
18] a distributed blockchain based power market trading platform is proposed to provide P2P secured transactions. In this blockchain based P2P transaction model, all the participating nodes and all transaction are stored. Since the data are stored in the blockchain and they are connected to all the nodes, they are more secure and transparent.
The security risks for a deregulated electricity market are therefore recognized and well defined. The security threat for regulated market is obvious, unknown, and meaningful to investigate. In this paper, the proposed Ethereum blockchain network deals with data security features of the regulated market system indicated as follows:
Decentralization: The fundamental element of this Ethereum blockchain signifies the data confidentiality on a distributing system (for any kind of data capturing, recording, updating or storing). It discharges the data-dependency on central node, which has high data security risk.
Transparency: In this work, the data script in each node written and updated transparently with trusted source in blockchain system.
Open Sourcing: Ethereum Blockchain system is very public. All data tracking can be verified publicly, and people and new applications in the system are easy to create. It itself can transfer and store revenue like a retail outlet. A transaction concerning two parties can exchange the transaction details.
Autonomous: Autonomy Chain Cloud of Ethereum Blockchain network controls the node by trusting a single head source for the entire system. The system ensures the data confidentiality so that no one can intercept it.
Immutability: In the used system, the transaction records are saved permanently and cannot be modified without having control on at least more than half of the nodes simultaneously.
Anonymity: Ethereum blockchain technologies solved the trust problem between node and node, so data transfer or even transaction can be anonymous, only needing to know the person’s blockchain address.
Anonymousness: Ethereum blockchain system data transaction can be done anonymously. Knowing blockchain address suffice for any transaction.
4. An Ethereum Blockchain Based End-to-End Security Prototype
In this section, an Ethereum blockchain prototype is presented to provide end-to-end security for the SCADA based regulated energy market. Hence, this section discusses the basic elements of a SCADA system and provides details about blockchain construction.
4.1. Overview of SCADA System
SCADA is a system of software and hardware elements used to monitor and control the NZEM. SCADA consists of different modules for monitoring, gathering, and analyzing real time system data. Functional modules of SCADA include hardware for process monitoring and process control, data acquisition module, user interface, communication modules, and software platform. The process control system of SCADA basically consists of remote terminal units (RTU’s) and programmable logic controllers (PLC) that connect a series of sensors for real time monitoring and data collection.
Remote terminal unit or RTUs is a microprocessor controlled electronic device, which interfaces physical objects (such as circuit breakers) in the power grid to a SCADA system.
Figure 2a illustrates the functional architecture of a SCADA system. In a high-level architecture, the functional components of SCADA can be described as below:
(1) Operational Equipment: Operational equipment of SCADA in a smart energy network perspective is the circuit breakers, which can be operated by actuators or relays.
(2) Local processors: These may have multiple inputs from instruments (e.g., programmable logic controller, remote control unit, intelligent electronic devices, etc.) and outputs to the operational equipment. They include PLC, RTUs, intelligent electronic devices, and automation controller for monitoring and control.
(3) Communication Module: This can be wired or wireless and facilitates communication (through analog or discrete signals) between all the different functional modules using a predefined communication protocol. On a larger scale, a long-range communication module can utilize phone network, satellites, microwave, or cellular packet data.
(4) Host Computer: It acts as the central monitoring and control point and also hosts the software platform to facilitate the monitoring and interaction.
4.2. SCADA Configuration and Smart RTU
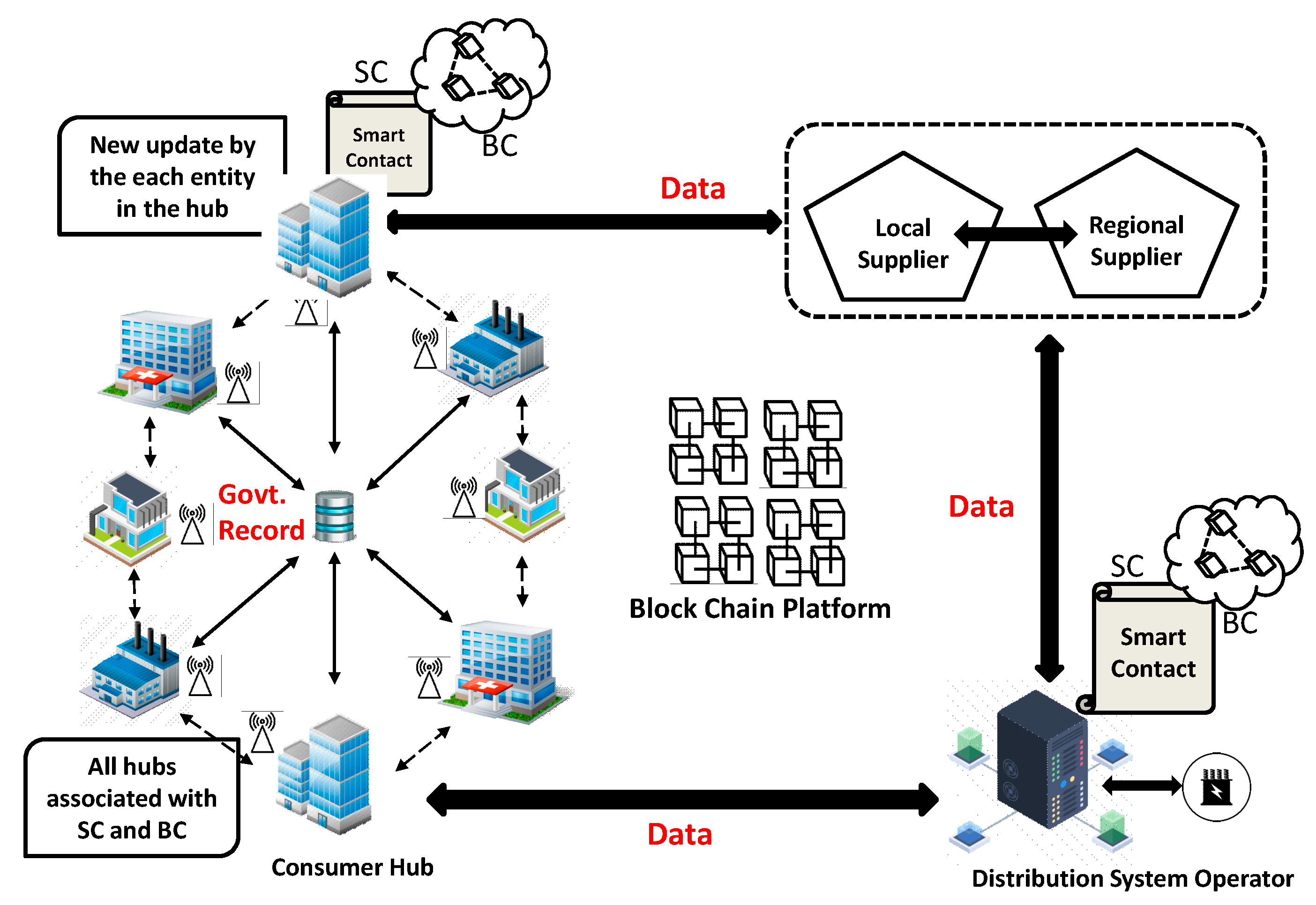
In this proposed blockchain prototype, the Smart RTUs in the physical layer of SCADA are considered as nodes for a decentralized network. Using a cloud simulation environment, we show the effectiveness of the proposed prototype in protecting the system from cyberattacks. In the simulation, a cloud-based SCADA network is used to accumulate, broadcast, and store data in the proposed prototype. Customized collection, transmission, and receival of signal data between the communication and physical layer are done through the smart RTUs of SCADA. The communication path is linked through the RTU-nodes. Only authorized users, who have access to the communication, are able to certify the data acquisition and process for the reports or signaling of different process used in the production environment. Advanced metering infrastructure (AMI) plays an important role in the proposed decentralized data security system. It is envisioned that AMI should contain the following key features:
(1) Individual smart RTU with distinctive IP address, data storage and process drive, RAM, signal sender–receiver device. All RTUs of the same layer need to be inter-channeled.
(2) A public–private key must be used to encrypt each smart RTU.
(3) Accessibility of bidirectional information gateway for related parties and associated systems.
In the following subsection, we are going to discuss an Ethereum blockchain prototype to facilitate an end-to-end data protection. The proposed Ethereum blockchain has three elements: (i) Block, (ii) Smart Contract, and (iii) Miner.
4.3. Block Construction
The literal meaning of blockchain is chain of blocks. A block is a container data structure, which stores key transaction information, like day and time of transaction, amount of transaction, participant in transaction, and so on. Internally, the blocks are linked by the cryptographic and hashing concepts. A hash function routes random data to meaningful preset sized data. In summary, each block is connected with one-way (i.e., data is irreversible) hash string-links and the resultant hash value is different from the previous hash values. In the process, the blocks are collision resistant, which means that if any transaction in the block is changed by an unauthorized entry, it invalidates all hash addresses of the block sequences one by one. The communication amid the client-nodes is routinely carried out without individual intervention.
Figure 3 shows the construction of the chain along with the details of the contents of block connections.
4.4. Development of Ethereum Smart Contract
Smart contracts help a customer (or miner) to trade data of any value via a transparent, conflict-free system whilst preventing any third-party access. Initially, a single ledger is offered to the customer as a source of trust from blockchain, and data exchange then happens between nodes. Smart contracts are a collection set of elaborated logic, which are developed in JavaScript platform. Protected data are stored in blockchain database and can be retrieved only by authorized users.
Figure 4 shows the construction flowchart of Smart Contract and its interaction with a different layer of the SCADA system. The data monitoring is developed in Python Zerynth IDE environment [
22], and the communication layer for smart RTUs is made with microchips of espressif [
23].
Zerynth is designed to link the IoT platforms of smart RTU to cloud services.
Figure 5 shows sample of a smart contract script developed for the local Ethereum node operation in blockchain. Verified smart contract data is then transferred to Rinkeby (refer to
Figure 4), which is a platform of the Ethereum blockchain test network (test net) [
24]. Rinkeby test net, in contrast to Ethereum main network (main net) is an authorized network.
For the console panel, Web3-Ethereum JavaScript API is used in the project [
25]. “Web3.js” is a selection of libraries that facilitates communication with local Ethereum node via IPC or HTTP connection. A deploy file and script codes are developed using HD wallet provider and web3. The HD wallet, with a public/private key tree feature, represented a master node (Meta Mask). Meta Mask is a crypto wallet for blockchain, which offers a risk-free approach on a unique decentralized web platform to link up to blockchain-based programs [
26]. Moreover, Application Binary Interface (ABI) specification is used as a standard approach to communicate with contracts in the Ethereum environment.
4.5. Data Transaction Process for Mining
Ethereum is an electronic currency used for funds exchange in an encrypted system which does not depend on any legalized central banking system. The blockchain transaction system in Ethereum data framework as online payment system is described in this section.
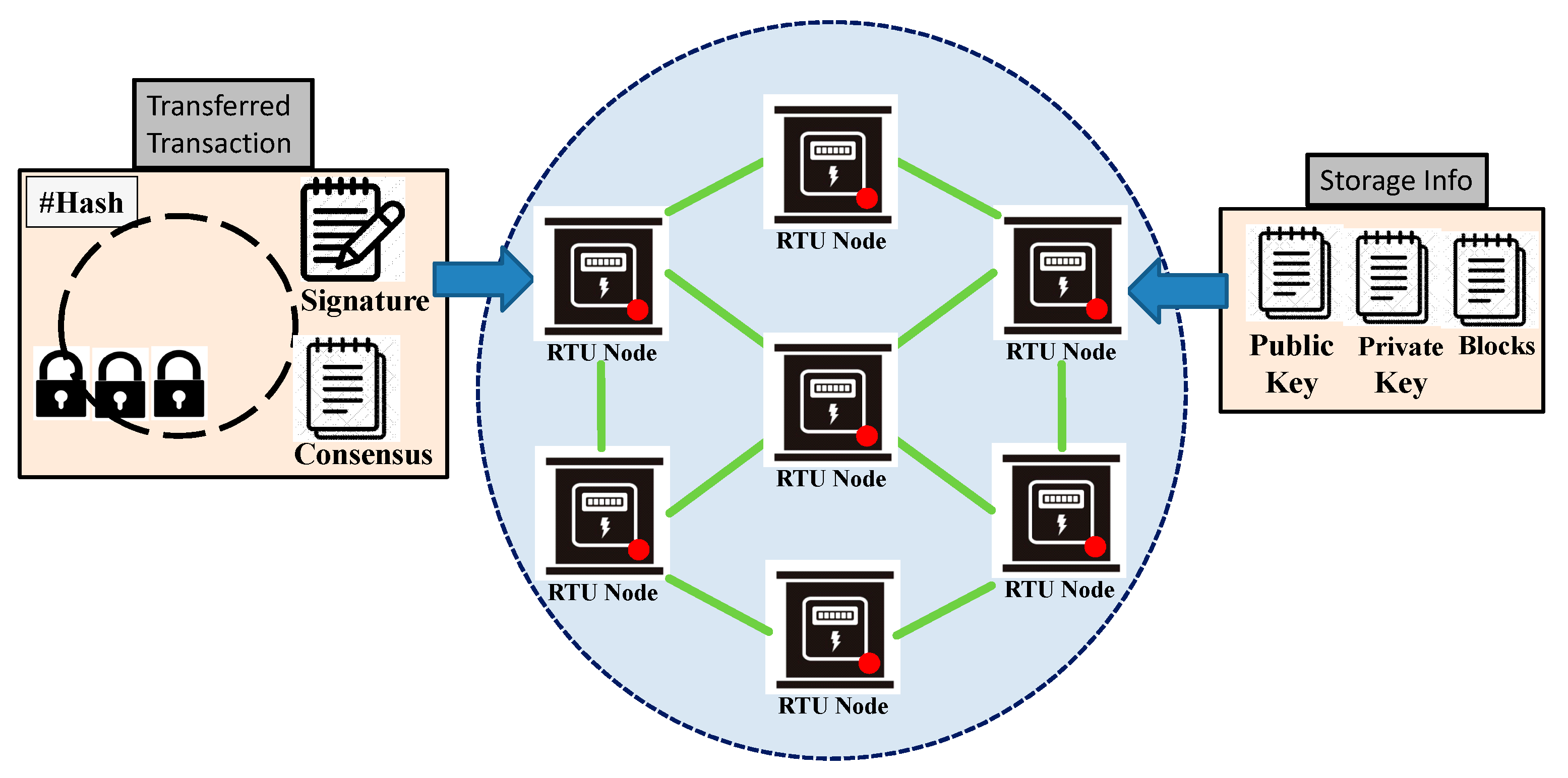
Ethereum employs public keys to address deposits and send currency. The public keys also track the transaction details. In Ethereum blockchain systems, data exchanges or transactions are usually unseen and anonymous. The system fixes the “trust” issue in between nodes with its anonymity feature. Knowing a blockchain address provides the transaction details, which have two major sections:
Principal data: It features the details of transaction files, records, dealing, contract history, and bank clearing information.
Public data: Anyone can verify some transaction data at permitted level and can also participate in the process of getting consensus. As Ethereum is a Public Blockchain, permitted transaction details will be public, and the system can be involved in the progression of getting consensus. In
Figure 6, an Encrypted process in active RTU nodes during transaction with public and private key details is shown.
The transaction procedure confirms the computing potentiality to get hold of consensus and subsequently files the transaction details to network. For any authorized or unauthorized party, the unique ID is kept as necessitated. In
Figure 7a, a Coinbase account for an authorized user is shown. The user can see the transaction details along with main Ethereum network details as shown in
Figure 7b. The Metamask Ropsten Test Network and its transaction details are shown in
Figure 7c. According to the transaction operation, there are four scenarios for transaction experienced:
- -
Old RTU node confirms identity and sends details to new RTU node.
- -
Old RTU node cannot confirm identity and failed details to new RTU node.
- -
New RTU node confirms identity and sends details to old RTU node.
- -
New RTU node cannot confirm identity and failed details to old RTU node.
4.6. Miner Status
In blockchain technology, blocks are formed, and their content verified by miners, who compete between themselves in the process (so-called mining) of appending new blocks to the blockchain. This subsection examines the miner status based on different power data of different nodes of smart RTUs as shown in
Figure 8. Etherscan, which is a block analytics as well as a block manager decentralized smart contracts platform for Ethereum, is used for this purpose. Ethers examine and browse the Ethereum platform for transaction details like encrypted data, block number, miner address, currency details, etc. (refer to
Figure 9). The Meta Mask wallet uses the storing keys (like Ether and ERC20 tokens) for the Ethereum platform [
27]. Samples of transactions added to the Rinkeby server are shown in
Figure 9a, in which the access is given to the miner only.
The monitoring status of the application layer of the SCADA system is indicated by the status OUT. Moreover,
Figure 9b shows the detailed analysis of the transaction in which the miner sends the request for transactions to the Rinkeby server. The hash and miner address details can be derived from the Rinkeby server address. The integer Ether values and transaction fees show the Ether balance used for the individual transaction.
Figure 8 shows the power data of different companies and
Figure 9 examines the associated transaction details for the same. It is found that peer-to-peer data transaction is secured through hash transaction. Any unauthorized party can just view the transaction as hashed message but cannot retain the original values or written text. It is evident from the miner status that the addresses are unique and can be accessed only by permitted parties. Moreover, peer-to-peer data transaction of
Figure 9b shows that the Rinkby server addresses for all five power data of the three different companies are unique. Therefore, any unauthorized entry has no chance of false data injection through the RTUs/Rinkeby address.