Using Quantum Nodes Connected via the Quantum Cloud to Perform IoT Quantum Network
Abstract
1. Introduction
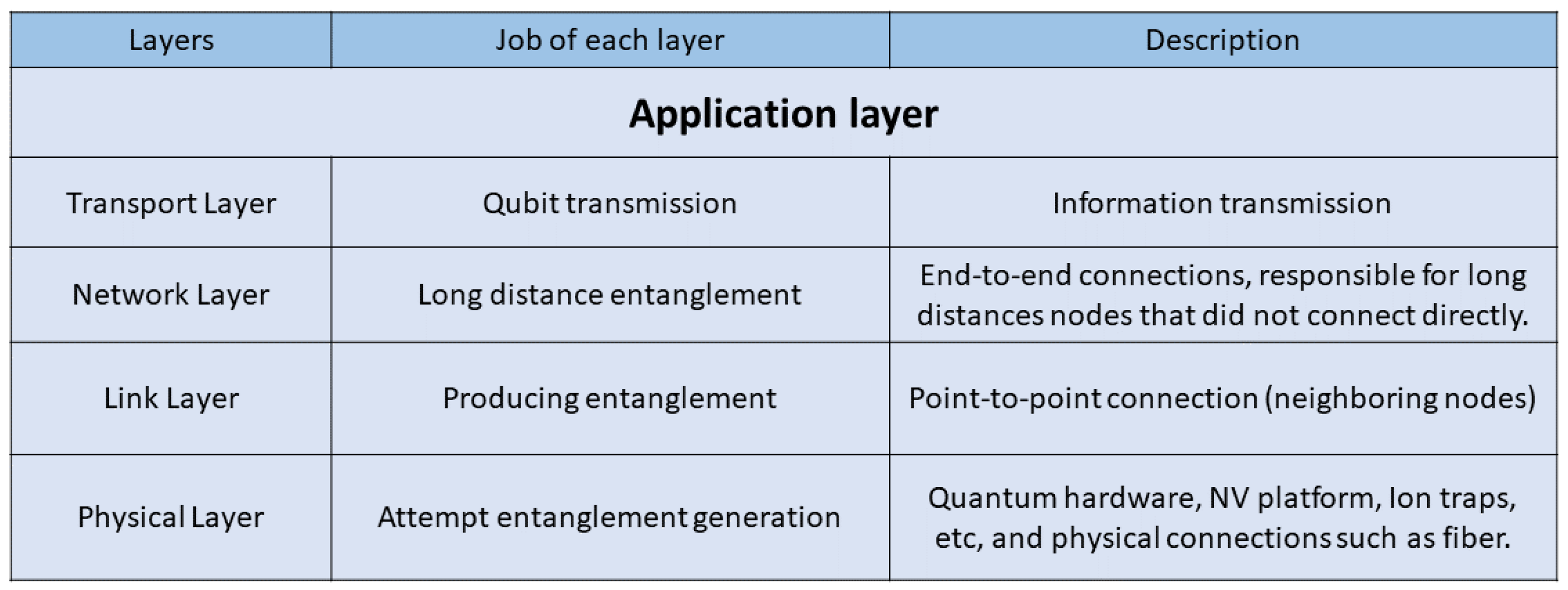
2. Quantum Information Theory
2.1. Overview of Quantum Communication
2.2. Quantum Communication Limitation
2.3. Solutions and Possibilities
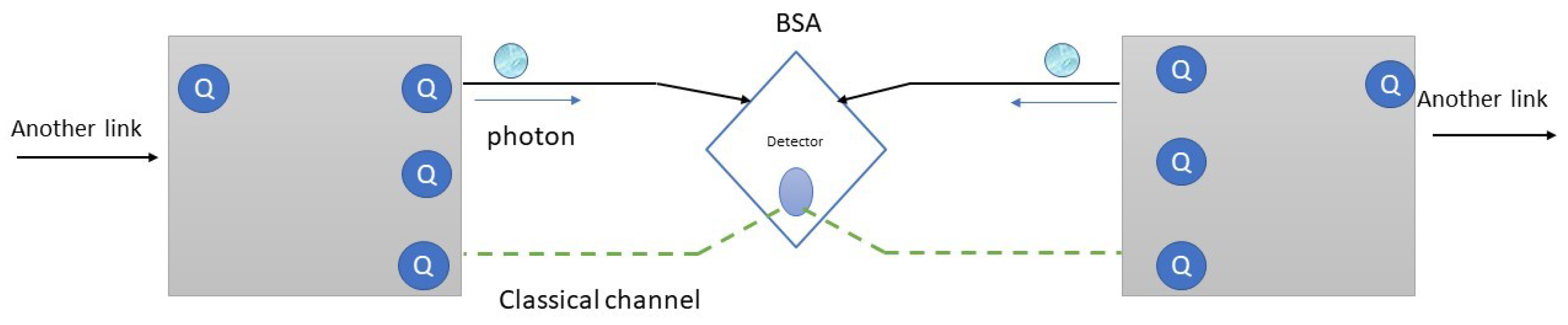
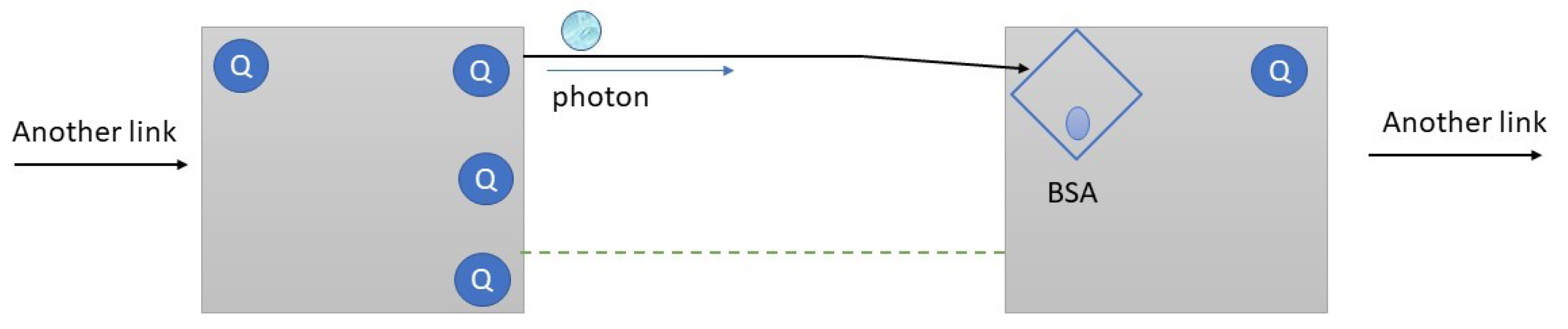
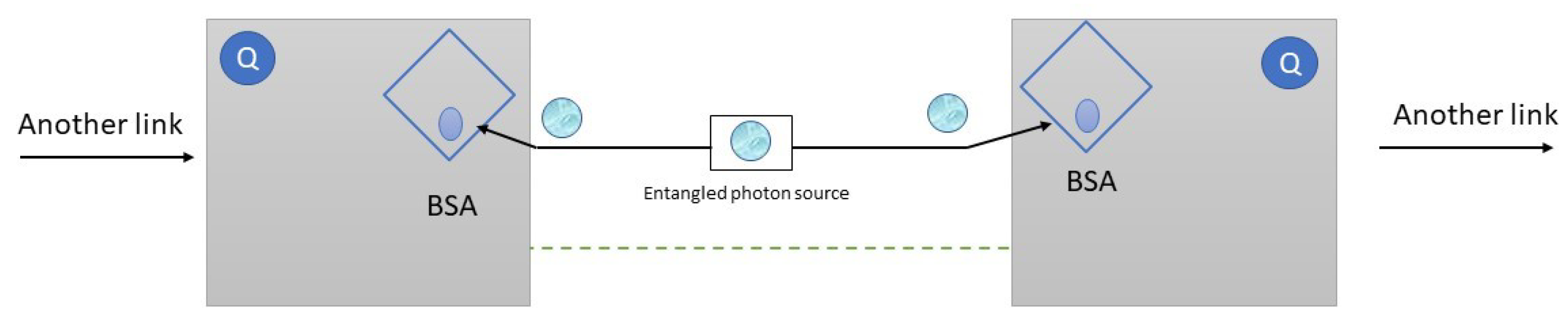
3. Quantum Protocols and Rules
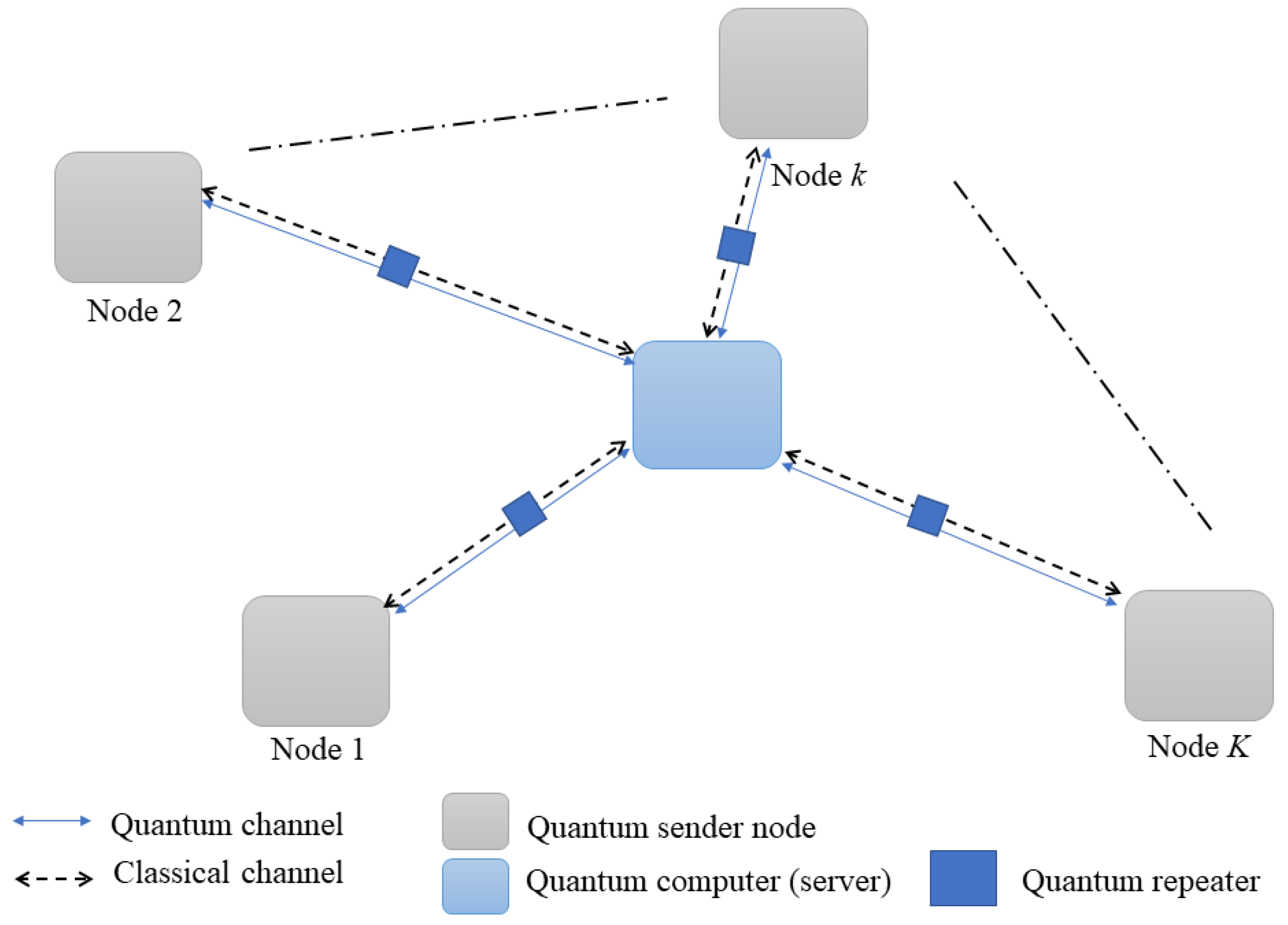
4. IoT Quantum Network Model
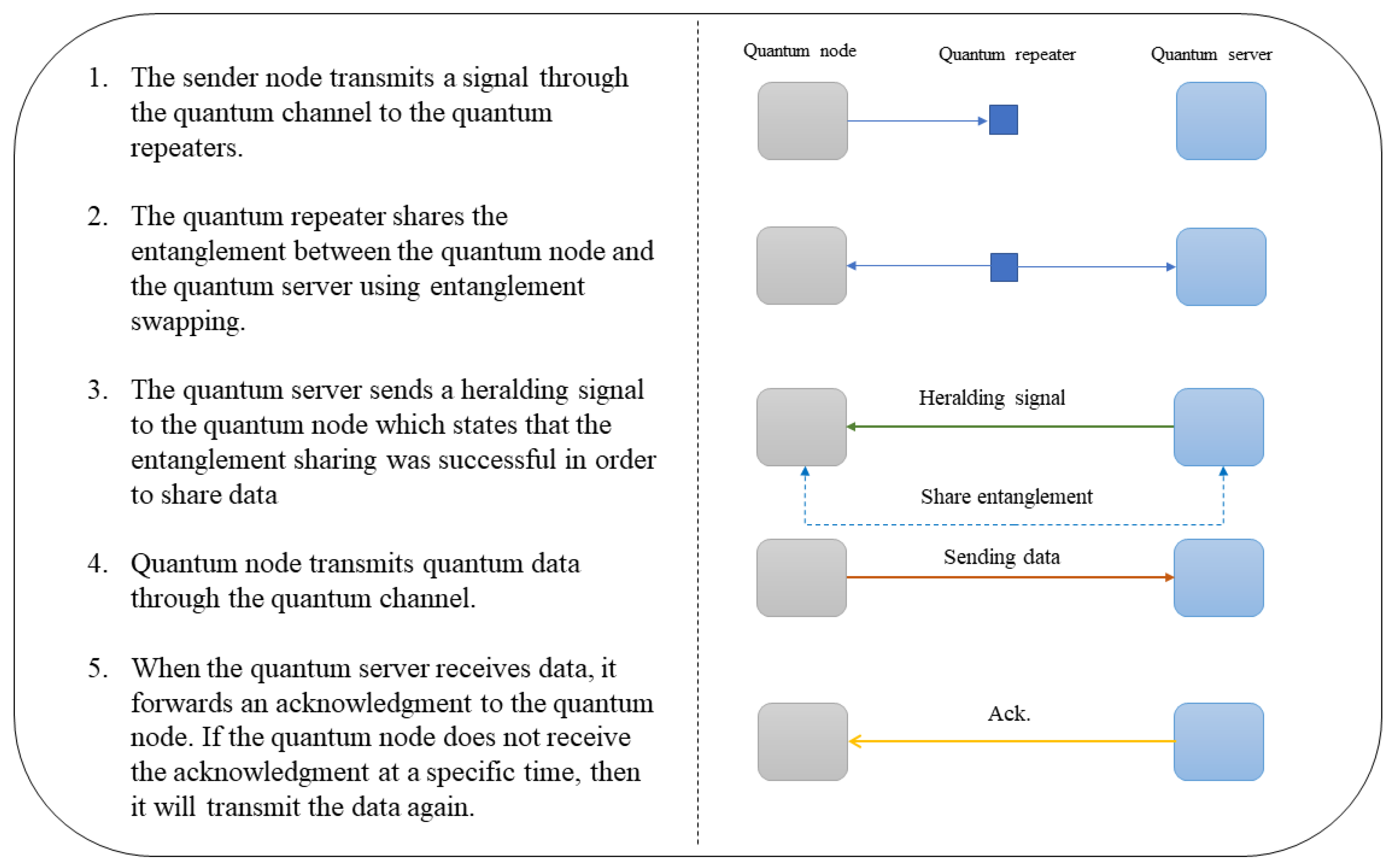
- First step: sharing entanglement
- The kth QN sends a qubit state to its corresponding QR in order to initiate entanglement generation.
- The BSA situated inside the kth QR performs some calculations according to the distance , photon emission timing (time required by each node to emit photon), and photon recovery timing (an essential property of a single-photon detector represents the desired time to recover the formal efficiency of the detector).
- The kth QR forwards the result (the aforementioned calculations) to the kth QN and the central QS using the classical channel in order to establish the entanglement swapping via the quantum channel between the kth QN and the central QS.
- The central QS notifies the kth QN that the entanglement sharing was successful.
- second step: sending information
- The kth QN forwards the information to the QS via the classical channel.
- When the QS receives the information, it sends an acknowledgment (ACK) signal to the kth QN. If the ACK does not reach the QN at a specific time, then the QN resends the information again.
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| BQC | Blind Quantum Computing. |
| BSA | Bell State Analyzer. |
| CP | Communication Procedure. |
| CSS | Calderbank–Shor–Steanes. |
| IoT | Internet of Thing. |
| MIM | Meet In the Middle. |
| NIC | Classical Network Interface Card. |
| NLAs | Noiseless Linear Amplifier. |
| QKD | Quantum Key Distribution. |
| QN | Quantum Node. |
| QNIC | Quantum Network Interface Card. |
| QoS | Quality of Surface. |
| QR | Quantum Repeater. |
| QS | Quantum Server. |
| QuISP | Quantum internet Simulation Package. |
References
- Homeland Security Research Corp (HSRC). 2018. Available online: https://homelandsecurityresearch.com/reports/quantum-computing-market-technologies/ (accessed on 1 September 2022).
- Grover, L.K. A fast quantum mechanical algorithm for database search. In Proceedings of the Twenty-Eighth Annual ACM Symposium on Theory of Computing, Philadelphia, PA, USA, 22–24 May 1996. [Google Scholar]
- Imre, S.; Balazs, F. Quantum Computing and Communications: An Engineering Approach; Wiley: Chichester, UK, 2005; pp. 81–169. [Google Scholar]
- Sara, E.G.; Imre, S. Implementation of a constrained quantum optimization method in resource distribution management with considering queuing scenarios. Int. J. Commun. Netw. Distrib. Syst. 2022, 28, 126–146. [Google Scholar]
- Teklu, B.; Olivares, S.; Paris, M.G.A. Bayesian estimation of one-parameter qubit gates. J. Phys. 2009, 42, 035502. [Google Scholar] [CrossRef]
- Brivio, D.; Cialdi, S.; Vezzoli, S.; Gebrehiwot, B.T.; Genoni, M.G.; Olivares, S.; Paris, M.G.A. Experimental estimation of one-parameter qubit gates in the presence of phase diffusion. Phys. Rev. 2010, 81, 012305. [Google Scholar] [CrossRef]
- Teklu, B.; Genoni, M.G.; Olivares, S.; Paris, M.G.A. Phase estimation in the presence of phase diffusion: The qubit case. Phys. Scr. 2010, 2010, 014062. [Google Scholar] [CrossRef]
- Llewellyn, D.; Ding, Y.; Faruque, I.I.; Paesani, S.; Bacco, D.; Santagati, R.; Qian, Y.J.; Li, Y.; Xiao, Y.F.; Huber, M.; et al. Chip-to-chip quantum teleportation and multi-photon entanglement in silicon. Nat. Phys. 2020, 16, 148–153. [Google Scholar] [CrossRef]
- Ruihong, Q.; Ying, M. Research Progress Of Quantum Repeaters. J. Phys. Conf. Ser. 2019, 1237, 052032. [Google Scholar] [CrossRef]
- Mehic, M.; Niemiec, M.; Rass, S.; Ma, J.; Peev, M.; Aguado, A.; Martin, V.; Schauer, S.; Poppe, A.; Pacher, C.; et al. Quantum Key Distribution: A Networking Perspective. ACM Comput. Surv. 2020, 53, 1–41. [Google Scholar] [CrossRef]
- Zhang, Y. Long-Distance Continuous-Variable Quantum Key Distribution over 202.81 km of Fiber. Phys. Rev. Lett. 2020, 125, 010502. [Google Scholar] [CrossRef]
- Fitzsimons, J.F. Private quantum computation: An introduction to blind quantum computing and related protocols. Npj Quantum Inf. 2017, 3, 23. [Google Scholar] [CrossRef]
- Xu, Q.; Tan, X.; Huang, R. Improved Resource State for Verifiable Blind Quantum Computation. Entropy 2020, 22, 996. [Google Scholar] [CrossRef]
- El Gaily, S.; Imre, S. Constrained Quantum Optimization Algorithm. In Proceedings of the 20th International Symposium INFOTECH-JAHORINA, East Sarajevo, Bosnia and Herzegovina, 17–19 March 2021. [Google Scholar]
- Castelvecchi, D. IBM’s quantum cloud computer goes commercial. Nature 2017, 543, 159. [Google Scholar] [CrossRef]
- Google Cloud. 2021. Available online: https://cloud.google.com/blog/products/compute/ionq-quantum-computer-available-through-google-cloud (accessed on 1 September 2022).
- Iggena, T.; Bin Ilyas, E.; Fischer, M.; Tönjes, R.; Elsaleh, T.; Rezvani, R.; Pourshahrokhi, N.; Bischof, S.; Fernbach, A.; Xavier Parreira, J.; et al. IoTCrawler: Challenges and Solutions for Searching the Internet of Things. Sensors 2021, 21, 1559. [Google Scholar] [CrossRef]
- Qiu, T.; Chi, J.; Zhou, X.; Ning, Z.; Atiquzzaman, M.; Wu, D.O. Edge Computing in Industrial Internet of Things: Architecture, Advances and Challenges. IEEE Commun. Surv. Tutor. 2020, 22, 2462–2488. [Google Scholar] [CrossRef]
- Zhang, L.; Huo, Y.; Ge, Q.; Ma, Y.; Liu, Q.; Ouyang, W. A Privacy Protection Scheme for IoT Big Data Based on Time and Frequency Limitation. Wirel. Commun. Mob. Comput. 2021, 2021, 1530–8669. [Google Scholar] [CrossRef]
- Mirani, A.A.; Velasco-Hernandez, G.; Awasthi, A.; Walsh, J. Key Challenges and Emerging Technologies in Industrial IoT Architectures: A Review. Sensors 2022, 22, 5836. [Google Scholar] [CrossRef]
- Gyongyosi, L.; Imre, S. Entanglement accessibility measures for the quantum Internet. Quantum Inf. Process 2020, 19, 115. [Google Scholar] [CrossRef]
- Briegel, H.-J.; Dür, W.J.; Cirac, J.I.; Zoller, P. Quantum Repeaters: The Role of Imperfect Local Operations in Quantum Communication. Phys. Rev. Lett. 1998, 81, 5932. [Google Scholar] [CrossRef]
- Jiang, L.; M, T.J.; Nemoto, K.; J, M.W.; Meter, R.V.; Lukin, M.D. Quantum repeater with encoding. Phys. Rev. 2009, 97, 032325. [Google Scholar] [CrossRef]
- DiAdamo, S.; Ghibaudi, M.; Cruise, J. Distributed Quantum Computing and Network Control for Accelerated VQE. IEEE Trans. Quantum Eng. 2021, 2, 1–21. [Google Scholar] [CrossRef]
- Trapani, J.; Teklu, B.; Olivares, S.; Paris, M.G.A. Quantum phase communication channels in the presence of static and dynamical phase diffusion. Phys. Rev. 2015, 92, 012317. [Google Scholar] [CrossRef]
- Adnane, H.; Teklu, B.; Paris, M.G.A. Quantum phase communication channels assisted by non-deterministic noiseless amplifiers. J. Opt. Soc. Am. B 2019, 36, 2938–2945. [Google Scholar] [CrossRef]
- Rosati, M.; Mari, A.; Giovannetti, V. Coherent-state discrimination via nonheralded probabilistic amplification. Phys. Rev. A 2016, 93, 062315. [Google Scholar] [CrossRef]
- Jones, C.; Kim, D.; Rakher, M.T.; Kwiat, P.G.; Ladd, T.D. Design and analysis of communication protocols for quantum repeater networks. New J. Phys. 2016, 18, 083015. [Google Scholar] [CrossRef]
- Dahlberg, A.; Skrzypczyk, M.; Coopmans, T.; Wubben, L.; Rozpędek, F.; Pompili, M.; Stolk, A.; Pawełczak, P.; Knegjens, R.; Filho, J.D.; et al. A Link Layer Protocol for Quantum Networks. arXiv 2008, arXiv:1903.09778. [Google Scholar]
- Takaaki, M. Simulation of a Dynamic, RuleSet-based Quantum Network. Master’s Thesis, Keio University, Tokyo, Japan, 2019. [Google Scholar]
- Satoh, R.; Hajdušek, M.; Benchasattabuse, N.; Nagayama, S.; Teramoto, K.; Matsuo, T.; Metwalli, S.A.; Pathumsoot, P.; Satoh, T.; Suzuki, S.; et al. QuISP: A Quantum Internet Simulation Package. arXiv 2021, arXiv:2112.07093. [Google Scholar]
- Nadlinger, D.P.; Drmota, P.; Nichol, B.C.; Araneda, G.; Main, D.; Srinivas, R.; Lucas, D.M.; Ballance, C.J.; Ivanov, K.; Tan, E.Z.; et al. Experimental quantum key distribution certified by Bell’s theorem. Nature 2022, 607, 682–686. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Subhi, D.; Bacsardi, L. Using Quantum Nodes Connected via the Quantum Cloud to Perform IoT Quantum Network. Condens. Matter 2023, 8, 24. https://doi.org/10.3390/condmat8010024
Subhi D, Bacsardi L. Using Quantum Nodes Connected via the Quantum Cloud to Perform IoT Quantum Network. Condensed Matter. 2023; 8(1):24. https://doi.org/10.3390/condmat8010024
Chicago/Turabian StyleSubhi, Doaa, and Laszlo Bacsardi. 2023. "Using Quantum Nodes Connected via the Quantum Cloud to Perform IoT Quantum Network" Condensed Matter 8, no. 1: 24. https://doi.org/10.3390/condmat8010024
APA StyleSubhi, D., & Bacsardi, L. (2023). Using Quantum Nodes Connected via the Quantum Cloud to Perform IoT Quantum Network. Condensed Matter, 8(1), 24. https://doi.org/10.3390/condmat8010024









