Visualization and Cybersecurity in the Metaverse: A Survey
Abstract
1. Introduction
- An investigation of cybersecurity issues, in particular, cyber threats faced by the Metaverse in relation to the use of visualization technologies;
- A discussion of existing work and open research directions on the development of countermeasures against such threats.
2. Related Work
3. Background
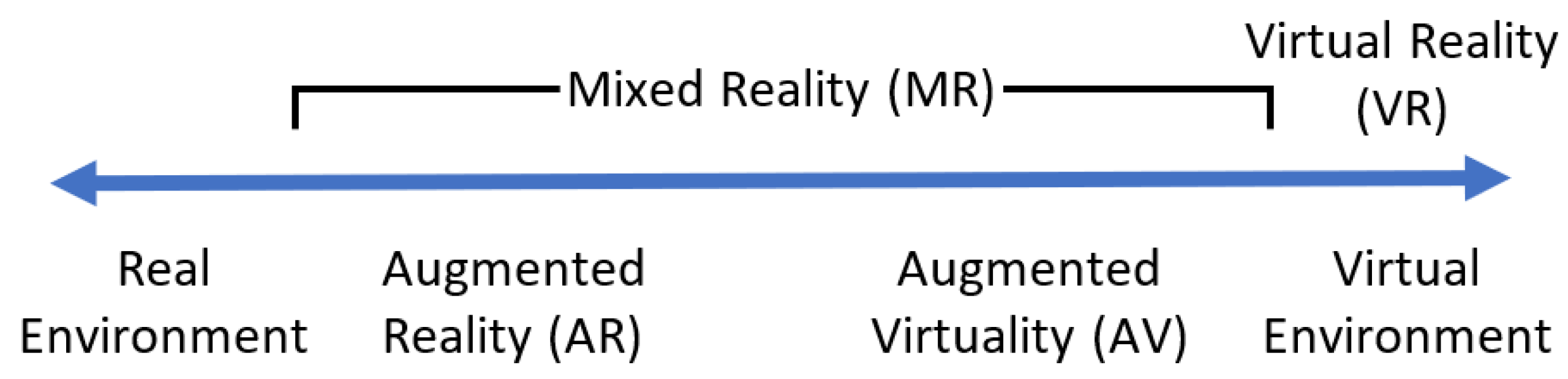
3.1. Metaverse Technologies
3.2. Visualization Technologies
4. Visualization and Cybersecurity Issues
4.1. Authentication and Identity
4.2. Privacy Issues
4.3. Social Issues
4.4. Physical Threats
5. Countermeasures
5.1. XR Authentication
5.2. AI-Driven Cybersecurity
5.3. Rules and Governance
5.4. Cybersickness Mitigation
5.5. XR Forensics
6. Open Research Directions
6.1. Continuous Authentication
6.2. Automated Detection and Mitigation
6.3. Cybersecurity Awareness
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Cheng, R.; Wu, N.; Chen, S.; Han, B. Will Metaverse Be NextG Internet? Vision, Hype, and Reality. IEEE Netw. 2022, 36, 197–204. [Google Scholar] [CrossRef]
- Gartner Incorporated. What Is a Metaverse? And Should You Be Buying In? Available online: https://www.gartner.com/en/articles/what-is-a-metaverse (accessed on 1 December 2022).
- Park, S.M.; Kim, Y.G. A Metaverse: Taxonomy, Components, Applications, and Open Challenges. IEEE Access 2022, 10, 4209–4251. [Google Scholar] [CrossRef]
- Wang, Y.; Su, Z.; Zhang, N.; Xing, R.; Liu, D.; Luan, T.H.; Shen, X. A Survey on Metaverse: Fundamentals, Security, and Privacy. IEEE Commun. Surv. Tutor. 2022, 24, 1. [Google Scholar] [CrossRef]
- Kaplan, A.M.; Haenlein, M. The fairyland of Second Life: Virtual social worlds and how to use them. Bus. Horizons 2009, 52, 563–572. [Google Scholar] [CrossRef]
- Meta. Meta Horizon Workrooms. Available online: https://www.meta.com/work/workrooms/ (accessed on 1 December 2022).
- Microsoft Incorporated. AltspaceVR. Available online: https://altvr.com/ (accessed on 1 December 2022).
- Nvidia Corporation. NVIDIA Omniverse. Available online: https://www.nvidia.com/omniverse/ (accessed on 1 December 2022).
- Arafat, A.A.; Guo, Z.; Awad, A. VR-Spy: A Side-Channel Attack on Virtual Key-Logging in VR Headsets. In Proceedings of the 2021 IEEE Virtual Reality and 3D User Interfaces (VR), Lisboa, Portugal, 27 March–1 April 2021; pp. 564–572. [Google Scholar] [CrossRef]
- Meteriz-Yıldıran, U.; Yıldıran, N.F.; Awad, A.; Mohaisen, D. A Keylogging Inference Attack on Air-Tapping Keyboards in Virtual Environments. In Proceedings of the 2022 IEEE Conference on Virtual Reality and 3D User Interfaces (VR), Christchurch, New Zealand, 12–16 March 2022; pp. 765–774. [Google Scholar] [CrossRef]
- Shang, J.; Chen, S.; Wu, J.; Yin, S. ARSpy: Breaking Location-Based Multi-Player Augmented Reality Application for User Location Tracking. IEEE Trans. Mob. Comput. 2022, 21, 433–447. [Google Scholar] [CrossRef]
- Casey, P.; Baggili, I.M.; Yarramreddy, A. Immersive Virtual Reality Attacks and the Human Joystick. IEEE Trans. Dependable Secur. Comput. 2021, 18, 550–562. [Google Scholar] [CrossRef]
- Odeleye, B.; Loukas, G.; Heartfield, R.; Spyridonis, F. Detecting framerate-oriented cyber attacks on user experience in virtual reality. In Proceedings of the VR4Sec: 1st International Workshop on Security for XR and XR for Security, Virtual, 27 May 2021. [Google Scholar]
- Yang, Q.; Zhao, Y.; Huang, H.; Xiong, Z.; Kang, J.; Zheng, Z. Fusing Blockchain and AI With Metaverse: A Survey. IEEE Open J. Comput. Soc. 2022, 3, 122–136. [Google Scholar] [CrossRef]
- Huang, H.; Zeng, X.; Zhao, L.; Qiu, C.; Wu, H.; Fan, L. Fusion of Building Information Modeling and Blockchain for Metaverse: A Survey. IEEE Open J. Comput. Soc. 2022, 3, 195–207. [Google Scholar] [CrossRef]
- Fu, Y.; Li, C.; Yu, F.R.; Luan, T.H.; Zhao, P.; Liu, S. A Survey of Blockchain and Intelligent Networking for the Metaverse. IEEE Internet Things J. 2022, 9, 1. [Google Scholar] [CrossRef]
- Huynh-The, T.; Pham, Q.V.; Pham, X.Q.; Nguyen, T.T.; Han, Z.; Kim, D.S. Artificial intelligence for the metaverse: A survey. Eng. Appl. Artif. Intell. 2023, 117, 105581. [Google Scholar] [CrossRef]
- Fernandez, C.B.; Hui, P. Life, the Metaverse and Everything: An Overview of Privacy, Ethics, and Governance in Metaverse. In Proceedings of the 2022 IEEE 42nd International Conference on Distributed Computing Systems Workshops (ICDCSW), Bologna, Italy, 10 July 2022; pp. 272–277. [Google Scholar] [CrossRef]
- Di Pietro, R.; Cresci, S. Metaverse: Security and Privacy Issues. In Proceedings of the 2021 Third IEEE International Conference on Trust, Privacy and Security in Intelligent Systems and Applications (TPS-ISA), Atlanta, GA, USA, 13–15 December 2021; pp. 281–288. [Google Scholar] [CrossRef]
- Odeleye, B.; Loukas, G.; Heartfield, R.; Sakellari, G.; Panaousis, E.; Spyridonis, F. Virtually secure: A taxonomic assessment of cybersecurity challenges in virtual reality environments. Comput. Secur. 2023, 124, 102951. [Google Scholar] [CrossRef]
- Böhm, F.; Dietz, M.; Preindl, T.; Pernul, G. Augmented Reality and the Digital Twin: State-of-the-Art and Perspectives for Cybersecurity. J. Cybersecur. Priv. 2021, 1, 519–538. [Google Scholar] [CrossRef]
- De Guzman, J.A.; Thilakarathna, K.; Seneviratne, A. Security and Privacy Approaches in Mixed Reality: A Literature Survey. ACM Comput. Surv. 2019, 52, 110. [Google Scholar] [CrossRef]
- Tang, F.; Chen, X.; Rodrigues, T.K.; Zhao, M.; Kato, N. Survey on Digital Twin Edge Networks (DITEN) Toward 6G. IEEE Open J. Commun. Soc. 2022, 3, 1360–1381. [Google Scholar] [CrossRef]
- Zhang, J.; Zong, M.; Li, W. A Truthful Mechanism for Multibase Station Resource Allocation in Metaverse Digital Twin Framework. Processes 2022, 10, 2601. [Google Scholar] [CrossRef]
- Milgram, P.; Kishino, F. A Taxonomy of Mixed Reality Visual Displays. IEICE Trans. Inf. Syst. 1994, E77-D, 1321–1329. [Google Scholar]
- Meta. Quest 2. Available online: https://www.meta.com/quest/products/quest-2/ (accessed on 27 December 2022).
- Microsoft Incorporated. Microsoft HoloLens 2. Available online: https://www.microsoft.com/en-us/hololens (accessed on 27 December 2022).
- VIVE. VIVE Pro 2. Available online: https://www.vive.com/us/product/vive-pro2-full-kit/overview/ (accessed on 27 December 2022).
- Valve Corporation. Valve Index. Available online: https://www.valvesoftware.com/en/index (accessed on 27 December 2022).
- Rebenitsch, L.; Owen, C. Review on Cybersickness in Applications and Visual Displays. Virtual Real. 2016, 20, 101–125. [Google Scholar] [CrossRef]
- Ling, Z.; Li, Z.; Chen, C.; Luo, J.; Yu, W.; Fu, X. I Know What You Enter on Gear VR. In Proceedings of the 7th IEEE Conference on Communications and Network Security, CNS 2019, Washington, DC, USA, 10–12 June 2019; pp. 241–249. [Google Scholar] [CrossRef]
- Luo, S.; Hu, X.; Yan, Z. HoloLogger: Keystroke Inference on Mixed Reality Head Mounted Displays. In Proceedings of the 2022 IEEE Conference on Virtual Reality and 3D User Interfaces (VR), Christchurch, New Zealand, 12–16 March 2022; pp. 445–454. [Google Scholar] [CrossRef]
- Olade, I.; Liang, H.N.; Fleming, C.; Champion, C. Exploring the Vulnerabilities and Advantages of SWIPE or Pattern Authentication in Virtual Reality (VR). In Proceedings of the 2020 4th International Conference on Virtual and Augmented Reality Simulations, ICVARS 2020, Sydney, Australia, 14–16 February 2020; Association for Computing Machinery: New York, NY, USA, 2020; pp. 45–52. [Google Scholar] [CrossRef]
- Stephenson, S.; Pal, B.; Fan, S.; Fernandes, E.; Zhao, Y.; Chatterjee, R. SoK: Authentication in Augmented and Virtual Reality. In Proceedings of the 2022 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 22–26 May 2022; pp. 267–284. [Google Scholar] [CrossRef]
- Mathis, F.; Williamson, J.H.; Vaniea, K.; Khamis, M. Fast and Secure Authentication in Virtual Reality Using Coordinated 3D Manipulation and Pointing. ACM Trans. Comput.-Hum. Interact. 2021, 28, 6. [Google Scholar] [CrossRef]
- Abdelrahman, Y.; Mathis, F.; Knierim, P.; Kettler, A.; Alt, F.; Khamis, M. CueVR: Studying the Usability of Cue-Based Authentication for Virtual Reality. In Proceedings of the 2022 International Conference on Advanced Visual Interfaces, AVI 2022, Rome, Italy, 6–10 June 2022; Association for Computing Machinery: New York, NY, USA, 2022. [Google Scholar] [CrossRef]
- Kupin, A.; Moeller, B.; Jiang, Y.; Banerjee, N.K.; Banerjee, S. Task-Driven Biometric Authentication of Users in Virtual Reality (VR) Environments. In MultiMedia Modeling; Kompatsiaris, I., Huet, B., Mezaris, V., Gurrin, C., Cheng, W.H., Vrochidis, S., Eds.; Springer International Publishing: Cham, Switzerland, 2019; pp. 55–67. [Google Scholar]
- Pfeuffer, K.; Geiger, M.J.; Prange, S.; Mecke, L.; Buschek, D.; Alt, F. Behavioural Biometrics in VR: Identifying People from Body Motion and Relations in Virtual Reality. In Proceedings of the 2019 CHI Conference on Human Factors in Computing Systems, CHI’19, Glasgow, UK, 4–9 May 2019; Association for Computing Machinery: New York, NY, USA, 2019; pp. 1–12. [Google Scholar] [CrossRef]
- Olade, I.; Fleming, C.; Liang, H.N. BioMove: Biometric User Identification from Human Kinesiological Movements for Virtual Reality Systems. Sensors 2020, 20, 2944. [Google Scholar] [CrossRef]
- Yu, P.; Xia, Z.; Fei, J.; Lu, Y. A Survey on Deepfake Video Detection. IET Biom. 2021, 10, 607–624. [Google Scholar] [CrossRef]
- Bose, A.J.; Aarabi, P. Virtual Fakes: DeepFakes for Virtual Reality. In Proceedings of the 2019 IEEE 21st International Workshop on Multimedia Signal Processing (MMSP), Kuala Lumpur, Malaysia, 27–29 September 2019; p. 1. [Google Scholar] [CrossRef]
- Aliman, N.M.; Kester, L. Malicious Design in AIVR, Falsehood and Cybersecurity-oriented Immersive Defenses. In Proceedings of the 2020 IEEE International Conference on Artificial Intelligence and Virtual Reality (AIVR), Utrecht, The Netherlands, 14–18 December 2020; pp. 130–137. [Google Scholar] [CrossRef]
- Nirkin, Y.; Wolf, L.; Keller, Y.; Hassner, T. DeepFake Detection Based on Discrepancies Between Faces and Their Context. IEEE Trans. Pattern Anal. Mach. Intell. 2022, 44, 6111–6121. [Google Scholar] [CrossRef]
- Chen, L.; Zhang, Y.; Song, Y.; Liu, L.; Wang, J. Self-supervised Learning of Adversarial Example: Towards Good Generalizations for Deepfake Detection. In Proceedings of the 2022 IEEE/CVF Conference on Computer Vision and Pattern Recognition (CVPR), New Orleans, LA, USA, 18–24 June 2022; pp. 18689–18698. [Google Scholar] [CrossRef]
- Ge, S.; Lin, F.; Li, C.; Zhang, D.; Wang, W.; Zeng, D. Deepfake Video Detection via Predictive Representation Learning. ACM Trans. Multimedia Comput. Commun. Appl. 2022, 18, 115. [Google Scholar] [CrossRef]
- Lin, Y.; Chen, H.; Li, B.; Wu, J. Towards Generalizable DEEPFAKE Face Forgery Detection with Semi-Supervised Learning and Knowledge Distillation. In Proceedings of the 2022 IEEE International Conference on Image Processing (ICIP), Bordeaux, France, 16–19 October 2022; pp. 576–580. [Google Scholar] [CrossRef]
- Falchuk, B.; Loeb, S.; Neff, R. The Social Metaverse: Battle for Privacy. IEEE Technol. Soc. Mag. 2018, 37, 52–61. [Google Scholar] [CrossRef]
- Yarramreddy, A.; Gromkowski, P.; Baggili, I. Forensic Analysis of Immersive Virtual Reality Social Applications: A Primary Account. In Proceedings of the 2018 IEEE Security and Privacy Workshops (SPW), San Francisco, CA, USA, 24 May 2018; pp. 186–196. [Google Scholar] [CrossRef]
- Vondrek, M.; Baggili, I.; Casey, P.; Mekni, M. Rise of the Metaverse’s Immersive Virtual Reality Malware and the Man-in-the-Room Attack & Defenses. Comput. Secur. 2022, 102923. [Google Scholar] [CrossRef]
- Casey, P.; Lindsay-Decusati, R.; Baggili, I.M.; Breitinger, F. Inception: Virtual Space in Memory Space in Real Space—Memory Forensics of Immersive Virtual Reality with the HTC Vive. Digit. Investig. 2019, 29, S13–S21. [Google Scholar] [CrossRef]
- Pearlman, K. Virtual Reality Brings Real Risks: Are We Ready? Available online: https://www.usenix.org/conference/enigma2020/presentation/pearlman (accessed on 1 December 2022).
- Leenes, R. Privacy in the Metaverse. In The Future of Identity in the Information Society; Fischer-Hübner, S., Duquenoy, P., Zuccato, A., Martucci, L., Eds.; Springer: Boston, MA, USA, 2008; pp. 95–112. [Google Scholar]
- Humphreys, S. Ruling the virtual world: Governance in massively multiplayer online games. Eur. J. Cult. Stud. 2008, 11, 149–171. [Google Scholar] [CrossRef]
- Sharma, V. Introducing a Personal Boundary for Horizon Worlds and Venues. Available online: https://about.fb.com/news/2022/02/personal-boundary-horizon/ (accessed on 1 December 2022).
- Basu, T. The Metaverse Has a Groping Problem Already. Available online: https://www.technologyreview.com/2021/12/16/1042516/the-metaverse-has-a-groping-problem/ (accessed on 1 December 2022).
- Le, T. Sexual Assault in the Metaverse is Part of a Bigger Problem that Technology Alone Won’t Solve. Available online: https://lens.monash.edu/@politics-society/2022/07/22/1384871/sexual-assault-in-the-metaverse-theres-nothing-virtual-about-it (accessed on 1 December 2022).
- Soon, W. A Researcher’s Avatar Was Sexually Assaulted on a Metaverse Platform Owned by Meta, Making Her the Latest Victim of Sexual Abuse on Meta’s Platforms, Watchdog Says. Available online: https://www.businessinsider.com/researcher-claims-her-avatar-was-raped-on-metas-metaverse-platform-2022-5 (accessed on 1 December 2022).
- Blackwell, L.; Ellison, N.; Elliott-Deflo, N.; Schwartz, R. Harassment in Social Virtual Reality: Challenges for Platform Governance. Proc. ACM Hum.-Comput. Interact. 2019, 3, 100. [Google Scholar] [CrossRef]
- Schneider, N.; De Filippi, P.; Frey, S.; Tan, J.Z.; Zhang, A.X. Modular Politics: Toward a Governance Layer for Online Communities. Proc. ACM Hum.-Comput. Interact. 2021, 5, 16. [Google Scholar] [CrossRef]
- Valluripally, S.; Gulhane, A.; Hoque, K.A.; Calyam, P. Modeling and Defense of Social Virtual Reality Attacks Inducing Cybersickness. IEEE Trans. Dependable Secur. Comput. 2022, 19, 4127–4144. [Google Scholar] [CrossRef]
- Tseng, W.J.; Bonnail, E.; McGill, M.; Khamis, M.; Lecolinet, E.; Huron, S.; Gugenheimer, J. The Dark Side of Perceptual Manipulations in Virtual Reality. In Proceedings of the 2022 CHI Conference on Human Factors in Computing Systems, CHI’22, New Orleans, LA, USA, 30 April–6 May 2022; Association for Computing Machinery: New York, NY, USA, 2022. [Google Scholar] [CrossRef]
- Gao, Y.; Wang, W.; Phoha, V.V.; Sun, W.; Jin, Z. EarEcho: Using Ear Canal Echo for Wearable Authentication. Proc. ACM Interact. Mob. Wearable Ubiquitous Technol. 2019, 3, 81. [Google Scholar] [CrossRef]
- Zhao, T.; Wang, Y.; Liu, J.; Cheng, J.; Chen, Y.; Yu, J. Robust Continuous Authentication Using Cardiac Biometrics From Wrist-Worn Wearables. IEEE Internet Things J. 2022, 9, 9542–9556. [Google Scholar] [CrossRef]
- Ryu, J.; Son, S.; Lee, J.; Park, Y.; Park, Y. Design of Secure Mutual Authentication Scheme for Metaverse Environments Using Blockchain. IEEE Access 2022, 10, 98944–98958. [Google Scholar] [CrossRef]
- Alqahtani, H.; Kavakli-Thorne, M. Design and Evaluation of an Augmented Reality Game for Cybersecurity Awareness (CybAR). Information 2020, 11, 121. [Google Scholar] [CrossRef]

| Category | Reference | Contribution |
|---|---|---|
| General | Cheng et al. [1] | Describes the positions of major tech companies and the requirements of the Metaverse. |
| Park and Kim [3] | Discusses concepts and essential techniques for realizing the Metaverse. | |
| Technology | Yang et al. [14] | Provides a survey of how blockchain and AI technologies can be fused with the Metaverse. |
| Huang et al. [15] | Presents a survey on integrating building information modeling and blockchain technologies with the Metaverse. | |
| Fu et al. [16] | Reviews the role of blockchain and intelligent networking in providing immersive Metaverse experiences. | |
| Huynh-The et al. [17] | Investigates the role of AI and its integration in the development of the Metaverse. | |
| Security | Wang et al. [4] | Presents a survey on the fundamentals, security, and privacy of the Metaverse. |
| Fernandez and Hui [18] | Provides an overview of privacy, governance, and ethical design, in the development of the Metaverse. | |
| Di Pietro and Cresci [19] | Discusses several security and privacy issues, and risks in the context of the Metaverse. | |
| Odeleye et al. [20] | Creates a taxonomy of cybersecurity challenges faced in VR environments. | |
| Böhm et al. [21] | Systematizes knowledge on AR and digital twin technology and discusses how cybersecurity can benefit from them. | |
| De Guzman et al. [22] | Presents a systematic literature survey of security and privacy approaches in mixed reality (MR). |
| Category | Issues | Countermeasures |
|---|---|---|
| Authentication and identity | Inference attacks [9,10,31,32,33,34] | XR authentication [35,36,37,38,39] |
| Identity theft and impersonation attacks [40,41,42] | AI-driven detection [40,43,44,45,46] | |
| Privacy issues | Location privacy [11,47] | Privacy strategies [47] |
| Behavior privacy [47,48,49] | XR forensics [48,49,50] | |
| Video feed leakage [12,51] | ||
| Social issues | Virtual spying and stalking [52] | Rules and system control [18,53,54] |
| Virtual harassment and abuse [55,56,57,58] | Community-led governance [58,59] | |
| Physical threats | Immersive attacks [12] | AI-driven detection [13] |
| Cybersickness attacks [13] | Cybersickness mitigation [60] | |
| Puppetry and mismatch attacks [61] |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chow, Y.-W.; Susilo, W.; Li, Y.; Li, N.; Nguyen, C. Visualization and Cybersecurity in the Metaverse: A Survey. J. Imaging 2023, 9, 11. https://doi.org/10.3390/jimaging9010011
Chow Y-W, Susilo W, Li Y, Li N, Nguyen C. Visualization and Cybersecurity in the Metaverse: A Survey. Journal of Imaging. 2023; 9(1):11. https://doi.org/10.3390/jimaging9010011
Chicago/Turabian StyleChow, Yang-Wai, Willy Susilo, Yannan Li, Nan Li, and Chau Nguyen. 2023. "Visualization and Cybersecurity in the Metaverse: A Survey" Journal of Imaging 9, no. 1: 11. https://doi.org/10.3390/jimaging9010011
APA StyleChow, Y.-W., Susilo, W., Li, Y., Li, N., & Nguyen, C. (2023). Visualization and Cybersecurity in the Metaverse: A Survey. Journal of Imaging, 9(1), 11. https://doi.org/10.3390/jimaging9010011










