4.1. Social Demography Characteristic
Four-hundred-and-seventeen (
n = 417) participants took part in the study. Of these, there were 384 documented owners and 33 issuance officers. Seventy-four percent of the respondents were male and 26% were female in case of the document owners; 69.7% and 30.3% were male and female in case of the officers; 65% were generally of older age, above 30; and 35% were amongst the age range of 21–30. The reason for this was to have an idea of the overall populace regarding the usage of the biometric technology. The main respondents came from the university community, who have an educational qualification higher than “Advanced” level in the case of passport owners (BSc, MSc and PhD), and officers at the regional centers in the case of issuance officers. Forty-point-six (40.6%) were students, 37.2% were teaching staff and 22.1% were employees. This was to assess if the participants were mindful and know of the new technology implemented in the biometric passport. No significant differences in participant’s characteristics were observed (
p-value = 0.002). The broader knowledge of the experience of biometric technology features was analyzed. The purpose was to identify if prior knowledge of the biometric characteristics had an impact on the adoption of the biometric technology. Fort-eight-point-five percent (48.5%) and 53% of the respondents have broad knowledge and experience of a fingerprint, 31.3% and 36% facial image, 9% and 4% Iris, 5% and 3% palm image, and 6.2% and 4% voice. The biometric technology was used at the workplace, nationwide identification and registration authority (NIRA) [
20]. Despite broader knowledge and experience by the participants, 69.3% agreed that the biometric technology plays a great role in increasing security in the Information technology (IT) sector; 30.7% disagreed, citing that the biometric technology can be infringed and misused by an imposter. Therefore, there is a need for individual’s awareness on the security and privacy of the information they give during the multiple registration in the day-to-day activities. The findings from the analysis were summarized as shown in
Table 1.
4.1.1. Factors Influencing the Adoption of Biometric Technology
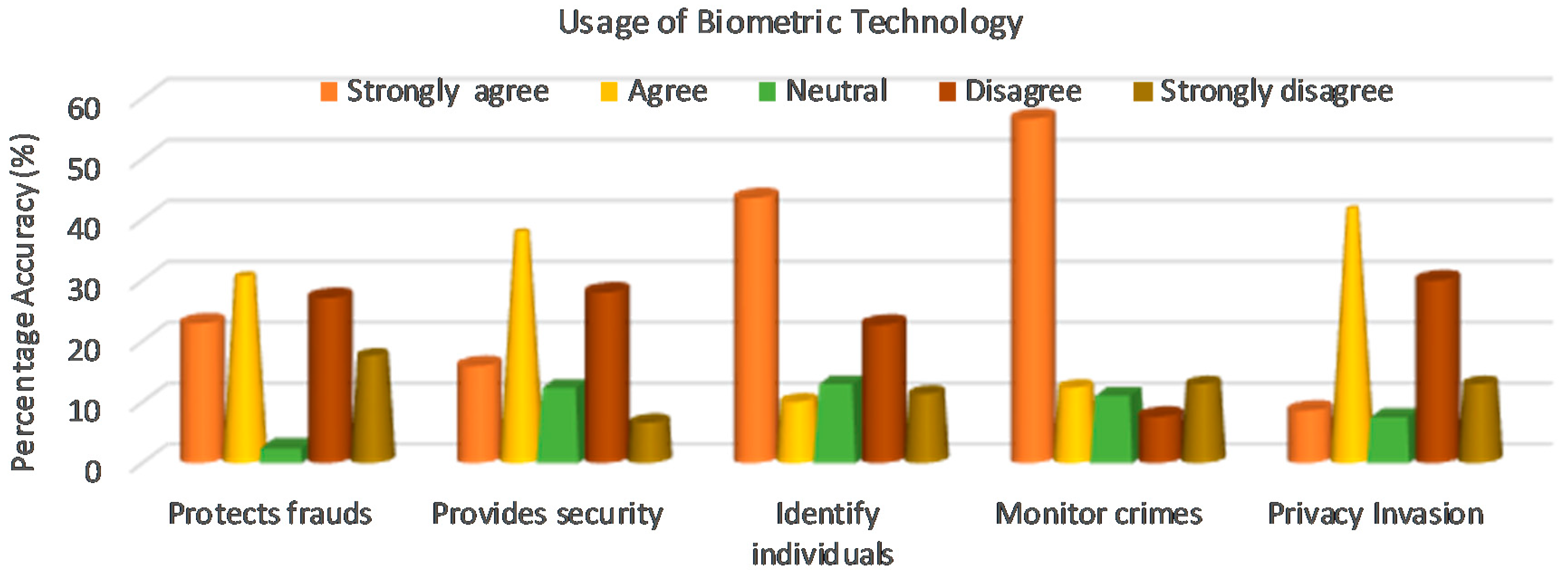
This section establishes a connection between the reasons and feelings of the respondents about the perception of the biometric technology. This helps the investigator to determine the main concerns behind the usage of the biometric technology as well as educate the scientist in understanding the preference of the general public (See
Figure 1). Thirty-point-two percent (30.2%) of the respondents’ agreed that the biometric passports help in protecting the individual’s information from frauds and crimes such as identity theft. However, 17.4% strongly disagreed with the proclamation pointing that the biometric passport would not help in protecting frauds and crime, because the information could be counterfeited by any imposter. Two-point-four percent (2.4%) were neutral (neither agree nor disagree), although there was a mixed perception of the respondents, those who agreed considered it as a measure against crime and fraud, while those who strongly disagreed said the technology cannot help in preventing fraud and crime against humanity.
Since direct protection from frauds and crimes was not comprehensive enough, participants were questioned about the security provided by the usage of biometric passports. Twenty-eight percent (28%) disagreed. They believed that the technology does not provide any security, because the tools for protection from terrorism were not strong enough arguments to be convincing. However, 37.4% agreed and cited that the biometric passport technology provides strong authentication, prevents identity fraud and controls security at the border passage. Twelve-point-two percent (12.2%) were neutral (neither agree nor disagree). These results revealed that the provision of security innovativeness were the most important factors influencing the adoption of biometric technology.
Additionally, respondents were questioned of the biometric passport usage; 43.5% strongly agreed that the biometric passport is used to recognize and authenticate a traveler at the border control, because it uses an embedded microprocessor chip that contains the owner’s biometric information for identification. Eleven-point-two percent (11.2%) strongly disagreed, they believed that using biometrics could hinder the identification process at the airports, since the process takes time to correctly identify the passport holder against his/her identifiers, hence, creating a chance for a terrorist to invade the system. Fifty-six-point-five (56.5%) believed that biometric technology is used as surveillance to constantly monitor crimes against humanity, which can help prevent a terrorist attack. Seven-point-six percent (7.6%) disagreed with the statement. Given the privacy invasion aspect of the biometric technology adoption, 41.2% of the respondents agreed that the usage of the technology could result in the invasion of privacy, because the biometric information is stored in the passports minus the owner’s knowledge. Thirty percent (30%) disagreed and 7.4% neither agreed nor disagreed. Therefore, the issuance officers and technology operators should make informed decisions to recommend the adoption of the biometric technology that helps protect and guarantee user’s information from fraudsters. The findings from the analysis are presented in
Figure 1.
4.1.2. Biometric Data Privacy
A significant effect of biometric data privacy and security compliance was investigated based on the five-point Likert scale measure, scaling from ‘Strongly agree’ to ‘Strongly Disagree’ as shown in
Table 2. Data recording was done in the range of 1 to 5. The weighted average and
t-statistics for the central tendency with
p-values below 0.05 were computed. Eighty-point-two percent (80.2%) of the respondents showed that individual datum shouldn’t be violated without the owners’ consent, because personal data are of great economic value. Therefore, one needs to know whom to share his/her information with and what would happen with his/her information. The
t-statistics value obtained were 0.000 and had a weighted average of 1.20. Therefore, the respondent’s statement was accepted and statistically significant.
Furthermore, 57.8% strongly agreed that personal data must be kept secret, because personal information is confidential and should be protected. People should learn to follow the regulations against their personal information [
21]. With any information posted online in a public forum, one cannot assume it’s private or safety. Our
t-value obtained was 0.000 and had a weighted middling of 1.48. Thus, it is statistically significant.
The likely abuses of new technology by criminals were discussed by the participants for justification. Sixty-four-point-eight percent (64.8%) strongly agreed that new technologies would be abused and exploited by criminals, because identity theft, fraud, and terrorism are the real harms. Although biometrics technologies help protect against these attacks, the potential misuse is obvious. Anybody unknown can engage him/herself with strangers and exchange data files. Yet, the greatest number of users do not fully understand the threats and attacks associated with the use of new biometric technology. One should understand that a compromised biometric trait cannot be revoked once stolen. The t-statistics value obtained was 0.001 and had a weighted middling 1.51. Therefore, respondents’ statements were accepted and statistically significant.
Participants were asked if scanning an individual’s biometric data from a template database without authorization was a privacy-infringement; 54.2% strongly agreed with the affirmation, because the infringement of one’s confidential secrecy could lead to personal exposer of health issues [
21]. It is suggested that transparency and good conduct of the operation and management of the biometric systems strictly be followed based on the appropriate regulations with respect to fundamental ethical principles and civil liberties. The data should be used only for the purpose specified. The
t-statistics value obtained was 0.002 and had a weighted middling of 2.12. Therefore, the respondents’ statements were statistically significant.
In addition, respondents were questioned to determine if database information used for other purposes other than the original aim is a privacy offence; 66.1% strongly agreed and cited the 2016 Uganda election as the greatest fear, because the citizen’s biometric fingerprint was extracted from the national identification and registration authority (NIRA) database without owners’ consent. Because most of the lawful status of biometric information is unclear, no court has addressed whether the law enforcement should allow collection of biometric data without a person’s knowledge. The
t-value obtained was 0.000 and had a weighted middling of 1.64. Therefore, respondents’ statements were statistically significant. We therefore recommend the users to be extra vigilant about their privacy and personal information sharing. They should ensure that the information is encrypted with a strong authentication key before putting them on the online platform. The findings of the analysis are shown in
Table 2.
4.2. Factors Impacting Users Fear of the Biometric Technology
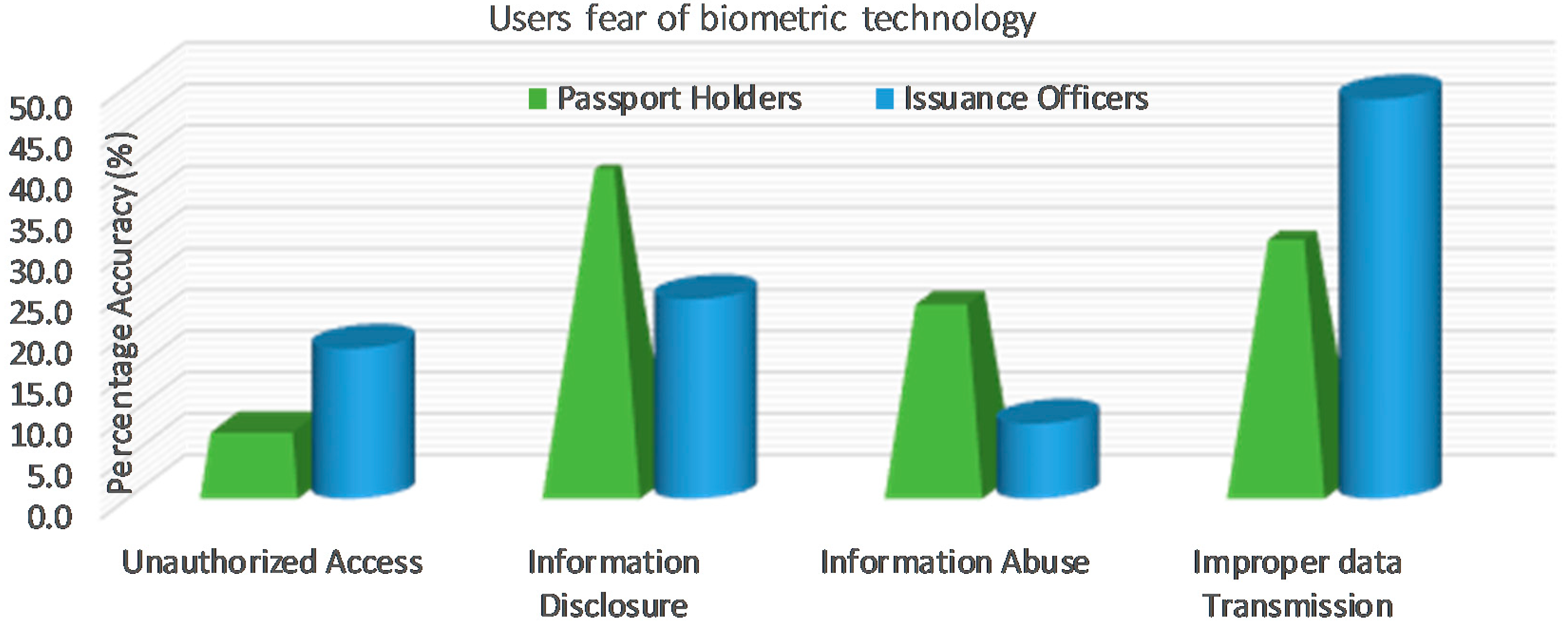
The study intended to understand the determinants of users’ concerns and knowledge on biometric passport technology. We focused our analysis on identifying if those surveyed have been impacted with fears of the biometric technology (See
Figure 2). Thirty-eight-point-eight percent (38.8%) and 24.2% of the participants feared disclosure of personal information, because the biometric information could be used for something else other than its intended purpose. For instance, immigration officers at the airport scan the bodies of the travelers for detection against the threat and need a hard disk and internet connection to store the information, thus odours for function creep. Forty-eight-point-five percent (48.5%) and 30.5% feared improper data transmission, because the specific document of an individual could be revealed which causes the individuals to become more vulnerable to document fraud against the security linkages. Although the travel records outside the workplace may be traced, the files are provided in reaction to a data protection demand. Therefore, the data transmission needs to be monitored using a tracking scheduled and duplicated pertinent documents than issuing the original information.
Additionally, 22.9% and 9.1% showed abuse of information, because a compromised biometric data stored in the database cannot be revoked. For instance, the DNA information could reveal a person’s health and exposure to disease. Suggested is a need for everybody to be vigilant on how to safeguard the identity and the storage level of the biometric database. It is safe to say that biometrics is the future of human identification, however, this future would stay uncertain unless rigorous methods are employed to protect it against any misuse or security occurrences.
Nevertheless, 18.2% and 7.8% indicated unauthorized access to individual data, because an unknown user could access the identity credentials of somebody else’s information and misuse it without his/her consent. For instance, a recent case of Pharmacy2U being fined £130,000 by the data administrator for vending the clients’ details to third parties without consent [
22]. This situation raised fear of the citizens’ secrecy and several alterations in government lawmaking. The federal government sector, IPP 1, required that personal information collection should be for lawful purposes and by lawful means. Therefore, unless awareness and user’s concerns are addressed, they shall still have the fears and trust of the biometric technology acceptance. This study, therefore, helps technology developers understand the significance perception of the end-user’s concerns and fears on the adoption of the biometric technology to make informed decisions.
4.3. The Security Threats And Challenges of the Biometric Technology
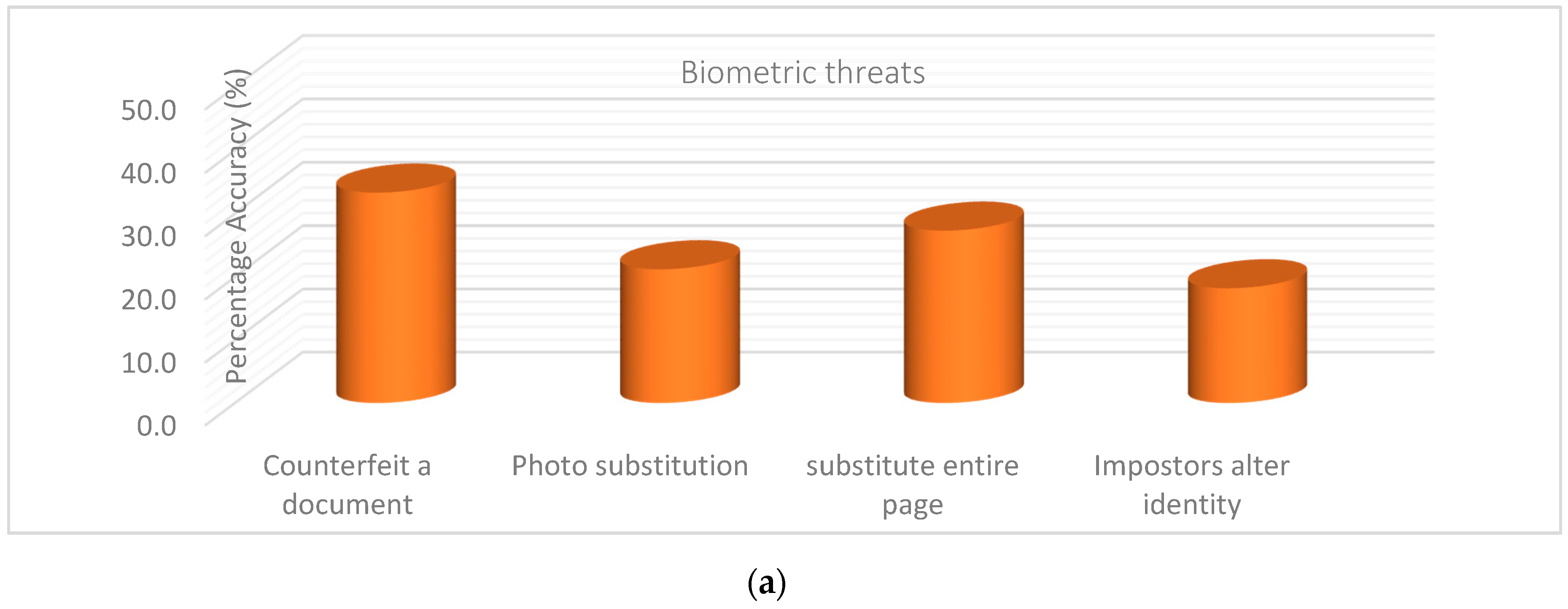
This section explains the important fundamental element of the threats experienced in issuance of the biometric passport: the attacks regarding the biometric template database. From the analysis, 33.3% of the participants stated counterfeit of their travel document as the greatest encountered threat. This is because identity fraud of travel documents are commonly experienced threats to the security of the national economy of the citizens globally It facilitates a wider range of crimes and terrorism. An imposter can make a false or fake passport to carry out unlawful fraudulent activity. The counterfeit documents comprised of unlawful duplicates of genuine permits illegally factory-made, neither issued nor verified by the authorized officer. With numerous dissimilar identity and travel documents in existence, it can be a challenging task to differentiate amongst false and genuine documents. Therefore, INTERPOL provides several specialized tools for the law enactment to help detect fraudulent documents and works with different partners to improve the level of security of official documents.
Additionally, 27.3% revealed the elimination and substitution of passport pages. These threats were related to the fraudsters seeking to tamper with legitimate passport data pages of the genuine document owners at the production stage. Rules should be followed by the public authorities to make the biometric passport pages harder for the fraudsters not to predict where, when, how, and by whom the identity should be checked.
Furthermore, 21.2% presented threats related to photo substitution. Photo substitution is removing the biometric data image from the genuine individual’s document and exchanging it with an imposter’s biometric data image. Likewise, 18.2% revealed an imposters alteration of their identity as another threat, because the impostor can modify the biometric features to change the data in a genuine document to obtain high verification scores. For instance, modification of the biographical data in the optical or MRZ.
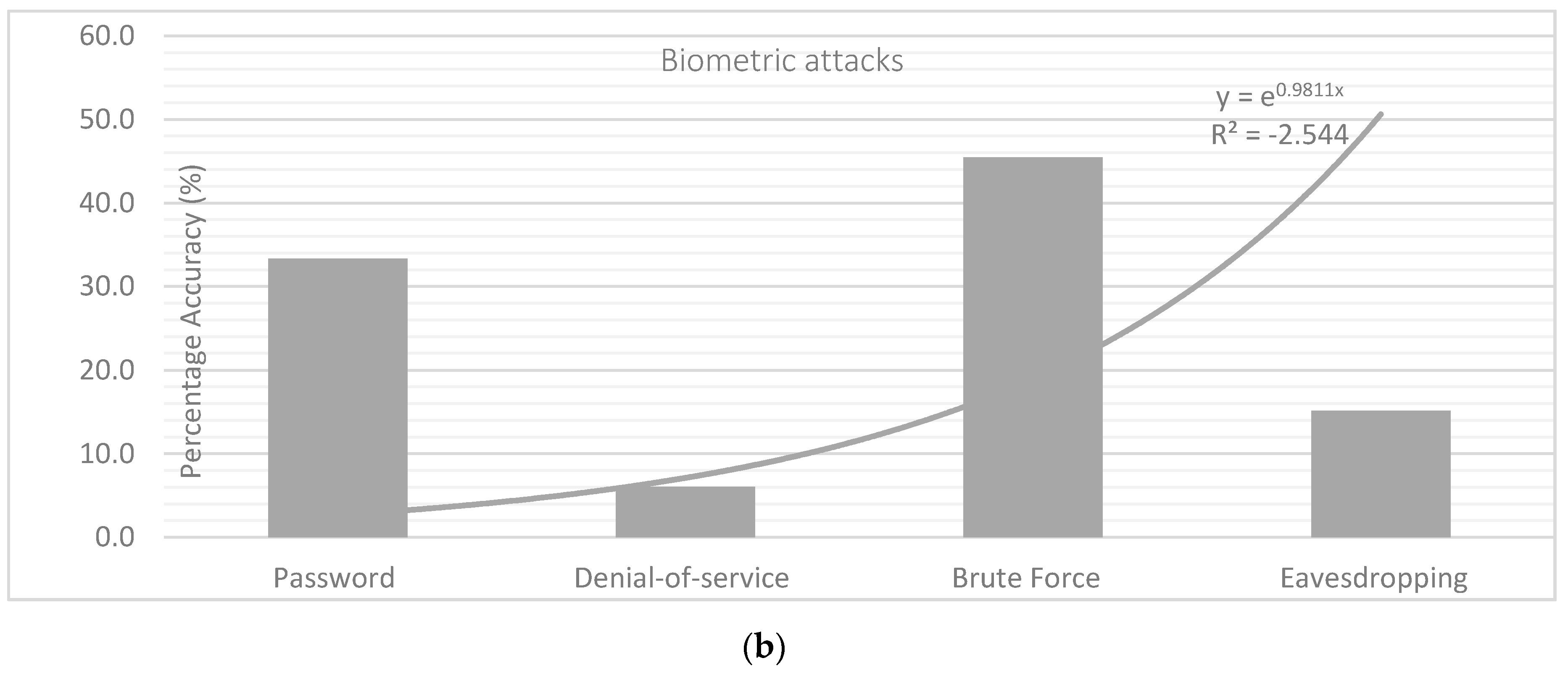
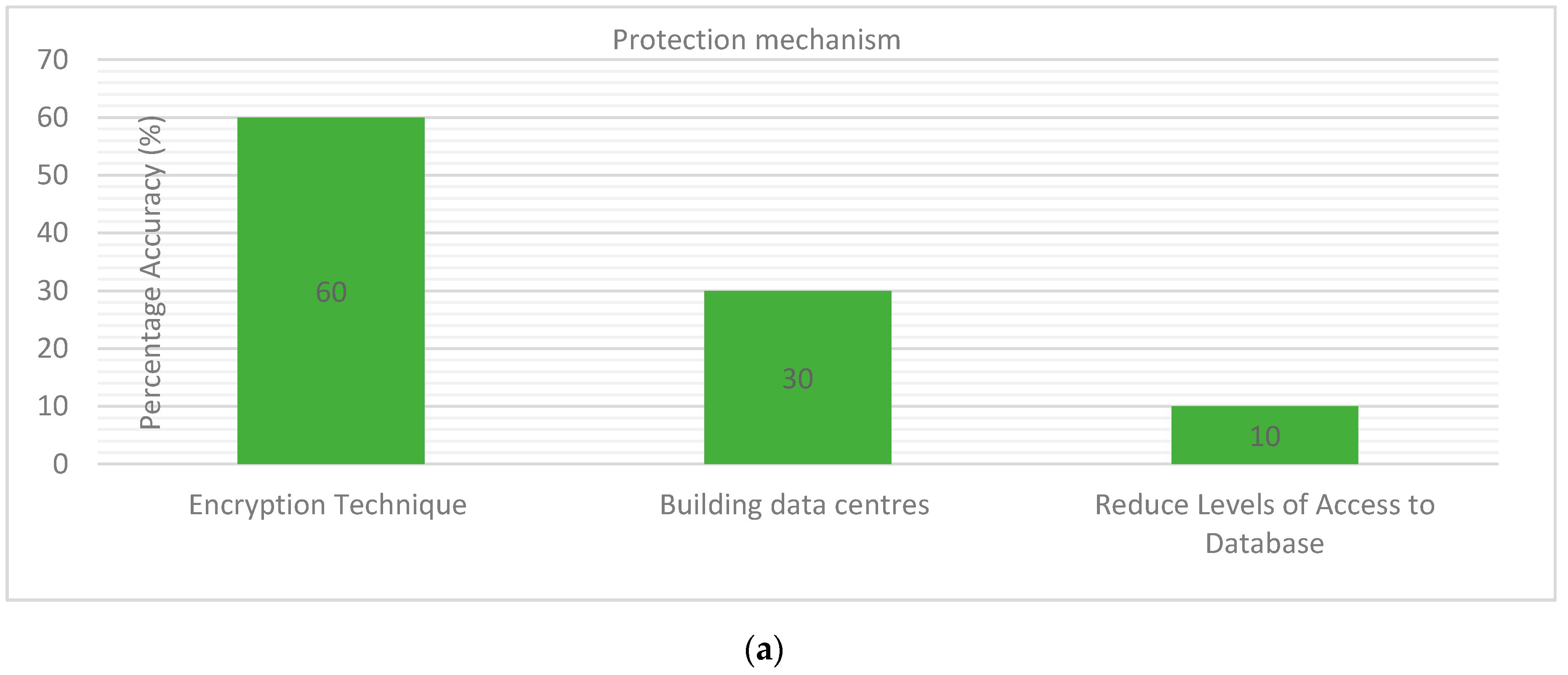
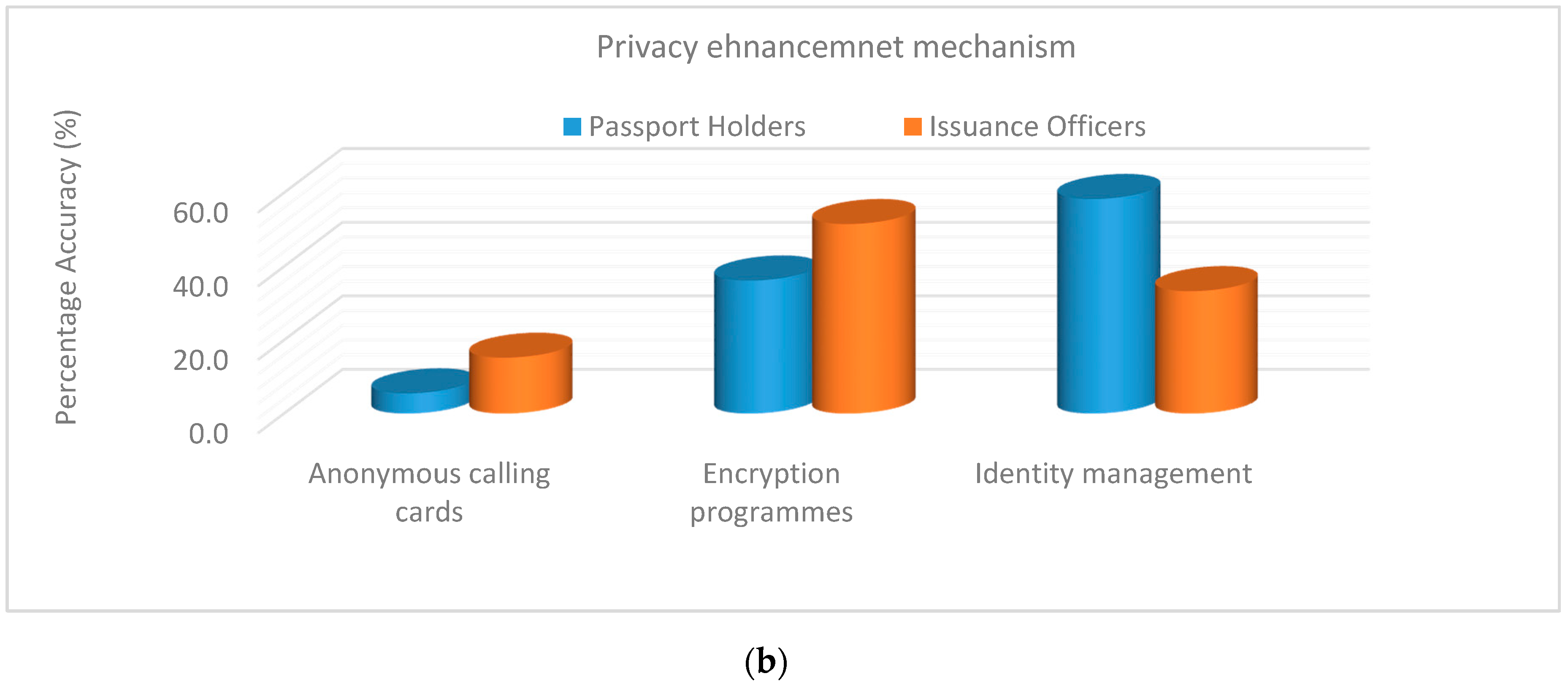
Additionally, attacks to the biometric template database were discussed. Foty-five-point-five percent (45.5%) of the respondents revealed brute force attack as the greatest vulnerability, because the imposter can attack the server system to acquire the biometric template database. Thirty-three-point-three percent (33.3%) showed password recovering, because an imposter can crack and recovers password from the stored system to access unauthorized files. Fifteen-point-two percent (15.2%) showed eavesdropping. Eavesdropping is where an invader clandestinely listens to the communiqué link and interrupts the message using digital devices such as the RFID chips. Six-point-one percent (6.1%) revealed denial-of-service. This is because an attacker tried to prevent genuine users from obtaining access to the server system. These exposures in the technology can permit an invader to remotely spy on a user’s information. Therefore, three-factor authentication is required to generate a pre-determined pin code to prevent an attacker from compromising an individual account. The findings of the analysis are presented in
Figure 3a, b.
Several types of individual information connected to bodily, biological or behavioral features of end-user’s acceptance were discussed. Fingerprint and face identifiers received the highest preference from the respondents with 44% and 32%, respectively. The fingerprints have been used as an additional identification mechanism in many national ID systems, and thus, are found to be more acceptable. They are used in an indoor access control, workers’ identification, gate pass attendance, and customer identification. They do not need the user to stay firm, which is different from the iris or retina. The person simply needs to touch the sensor screen of the authentication device and is done. The face modalities for recognition and verification were the most acceptable modality by travelers. We recognize and verify our family, friends, colleagues, and neighbors by looking at their face on an everyday basis. Ten percent (10%) preferred iris recognition, because the iris system is the most reliable, secure to use, and is hard to forge. The modality has been installed in many countries and no record has shown its data breach. Six percent (6%) preferred the signature scan, because the digital signatures are much more difficult to forge than normal handwriting and protect the integrity of one’s official documents. Four percent (4%) preferred a voice scan, because they are used remotely unlike other types of biometrics that could not remotely be used, such as fingerprints, retina biometrics or iris biometrics. Four percent (4%) preferred Hand Scan.
The modalities parameters were compared for the acceptance–rejection of the biometric technology. For instance, the false acceptance rate, false rejection rate, crossover error rate, receiver capture characteristics, and the sensor subject distance. The false rejection rate is the degree of possibility that the biometric technology would mistakenly refuse access to a lawful individual. In other words, the likelihood that biometric technology would fail to identify an enrollee or confirm the lawful claimed identity of an enrollee. It is estimated as FRR = NFR ÷ NEVA (NIA). Where FRR is the false rejection rate, NFR is the number of false rejections, NEVA is the number of enrollee verification attempts, and NIA is the number of identification attempts. The estimate assumed that the enrollee identification/verification attempts are symbolic of those entire enrollees of the people. The false rejection rate excludes “failure to acquire” errors. Nevertheless, the false acceptance rate is the degree of probability that the biometric system would wrongly agree with the unlawful user. In other words, the possibility that a biometric system would mistakenly identify a person or fail to reject a fraud. The ratio assumed passive impostor attempts. It is projected as FAR = NFA ÷ NIIA (NIVA). The FAR is the false acceptance rate, NFA is the number of false acceptances, NIIA is the number of impostor identification attempts, and NIVA is the number of impostor verification attempts. The findings of the analysis are shown in
Table 3.
4.5. Implementation of the Proposed Biometric Passport System
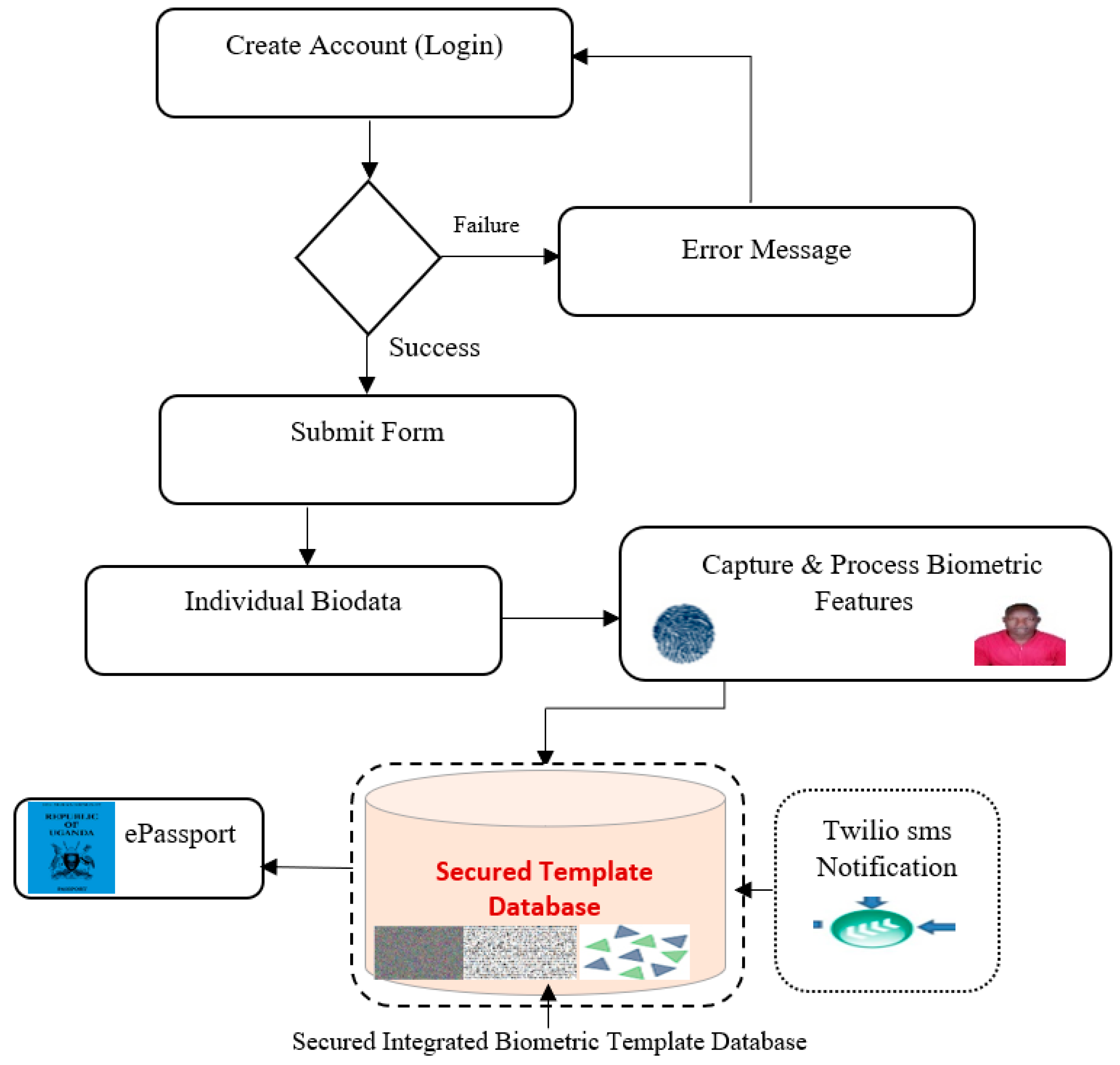
The python flash framework was used for the development, because it facilities for designing web applications and built-in development servers, and provides simplicity, flexibility and fine-grained control as well as a fast debugger. It allows one to quickly add common security mechanisms to the application such as Session-based authentication, Role management password hashing, Basic hypertext transfer protocol (HTTP), and Token-based authentication. Five steps were involved in the application system. Step 1: Create login credentials and choose the regional center. Step 2 and Step 3: Auto generate the regional code and fill the form. The regional code is a unique code for each center and applicant. For instance, [AR33200031920] code for Arua region and [MB66200011920] for Mbale region. The application identification (ID) helped identify the region/center of the applied applicant. It included the regional code, year, month, and personal unique ID. This guaranteed the security of the personal information to track the record. Step 4: Adding documents. The passport photo was automatically encrypted once uploaded into the system and decrypted upon verifying and approving the applicant document. This helped to prevent the data linkage and fraudster from infringing on personal information and counterfeiting the document. Step 5: Declaration statement and submission. This generated individual data entry to print a copy of the submission form and send it to the regional officer. The verified and approved form were automatically sent to the headquarter. The Small Message Service (SMS) notification was then received by the applicant. For instance, (Hello John [AR33200031920] your application has been verified and has been forwarded to headquarters, we shall contact you to come for biometric scans).
The regional officer from the headquarter can view the applicant’s details, decrypt the passport photo to verify the applicant, and then invite the applicant for the biometric scan. Immediately after a click of the application button, an automatic SMS reaches the applicant. For example, “Hello John (AR3320003192), we are inviting you for a biometric scan. Please come to our office Kampala (Headquarter)”. The integrated biometric features such as the face image and fingerprint were captured to generate two encrypted template files. For instance, the byte file and the text file. These files were saved securely into a central database. Several authentication processes were involved. Windows Authentication: to validate and permit resources. Forms Authentication: creates username and password. Biometric feature authentication: to encrypt the biometric data and storage database with security privileges. This successful deployment and operation depended highly upon the present existing technology and the resources in place. Many countries are adopting a biometric passport application program with the combination of a paper and electronic passport system to store biometric data in the central server. The system is designed to be non-traceable by the imposter, it also contains protection mechanisms to avoid hacking and despicable attacks that can compromise the user’s information and individual rights to privacy during the personal information transmission.
As biometric technologies are not designed fully with security or privacy capabilities, technology inventors need to address the provisions of the deployed application. The user populace needs to talk in the planning process to guarantee and reassure the end-user’s acceptance. Our proposed application system involved security tools such as Jinja2, Wtforms, Cryptography, and Twilio programmable sms among others. Jinja2 were used as a template engine that contained variables and tags to control the logic of the information flow. It provides a protection framework for automation of testing the application and helps prevent cross-site scripting (XSS) attacks. The Wtforms were used to generate a passport applicant’s form, instead of writing Hypertext Markup Language (HTML) directly. This provided protection from Cross Site Reference Forgery (CSRF) through Wtforms CSRF module. The cryptography modules were used to encrypt the face scan and the fingerprint image based on Fernet instance. The Fernet ensured that the message encrypted would not be read lacking the key. The Twilio programmable sms was used to alert users and authority through sms messages in case of unauthorized access to the system and the database template of the application. With these security tools implemented, we were able to address users’ concerns of privacy and security of the biometric information. Of the concerned addressed were, the passport was issued by the correct person who applied and followed the procedures. The individual information was secured and encrypted with Twilio sms notification that assured the person of his/her information safety. Two encrypted files were produced that make it computationally complex for any impostor to break into the template database server to access any individual data. The digital data on the passport were only readable by an authorized officer. The application could detect, monitor, signal, and report illegal attempts of the template database linkage. The proposed system provided faster, more reliable and easier processing of biometric documents. The system was able to control the individual information and provided feedback immediately as well as increased accuracy and efficiency. The system was able to reduce fraud and forgery of documents. Thus, it could build public acceptance, confidence and trust in the system itself and in those operating the applications. The proposed framework for the biometric passport application system is presented in
Figure 5.