Food Fraud Vulnerability Assessment in the Chinese Baijiu Supply Chain
Abstract
1. Introduction
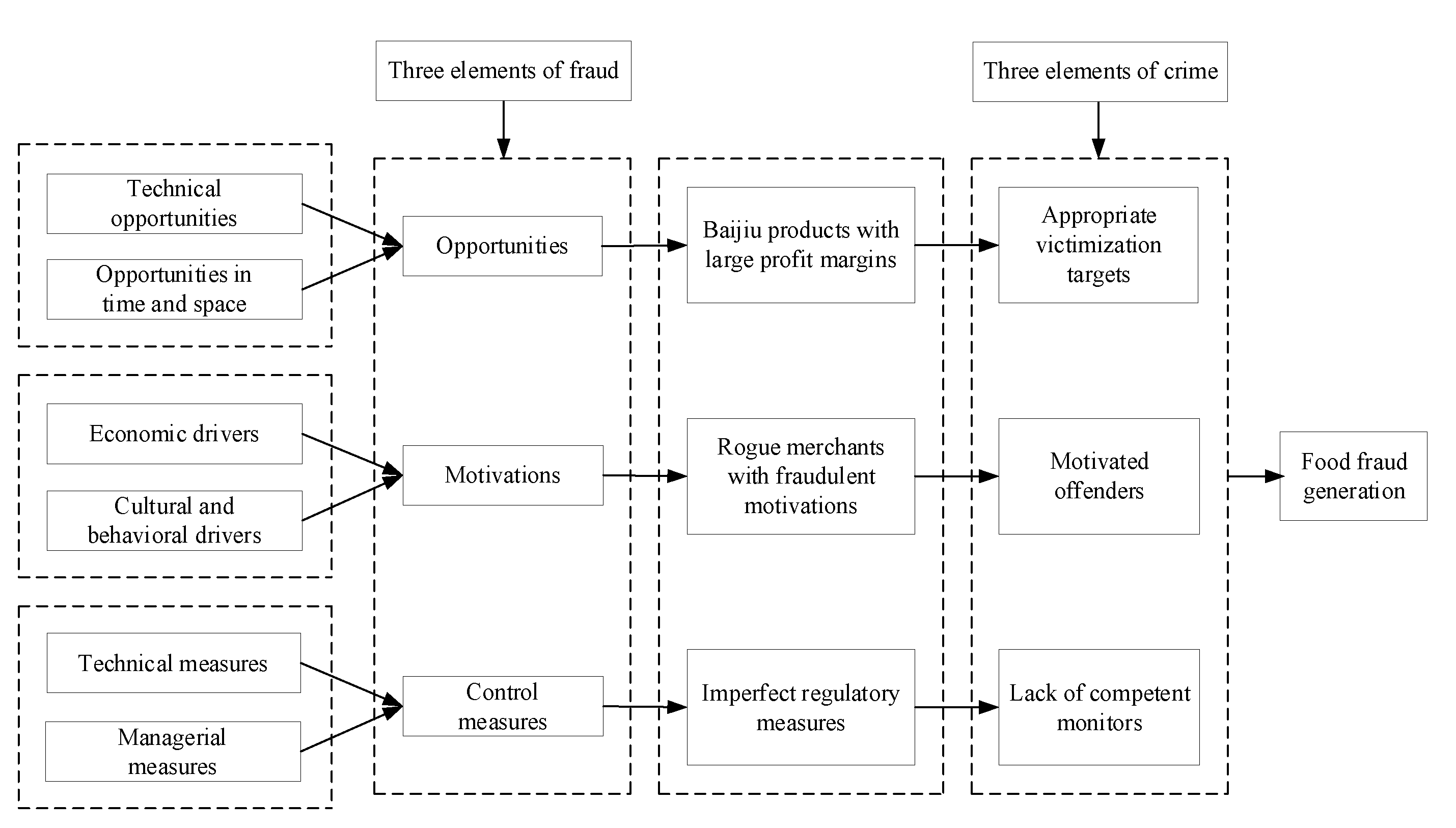
2. Theoretical Analysis
3. Materials and Methods
3.1. The Food Fraud Vulnerability Assessment (FFVA) Tool
3.2. Data Collection
3.3. Data Analysis
3.3.1. Frequency and Weighted Frequency Analysis
3.3.2. Multiple Correspondence Analysis
3.3.3. Mann-Whitney U Test
4. Results and Discussion
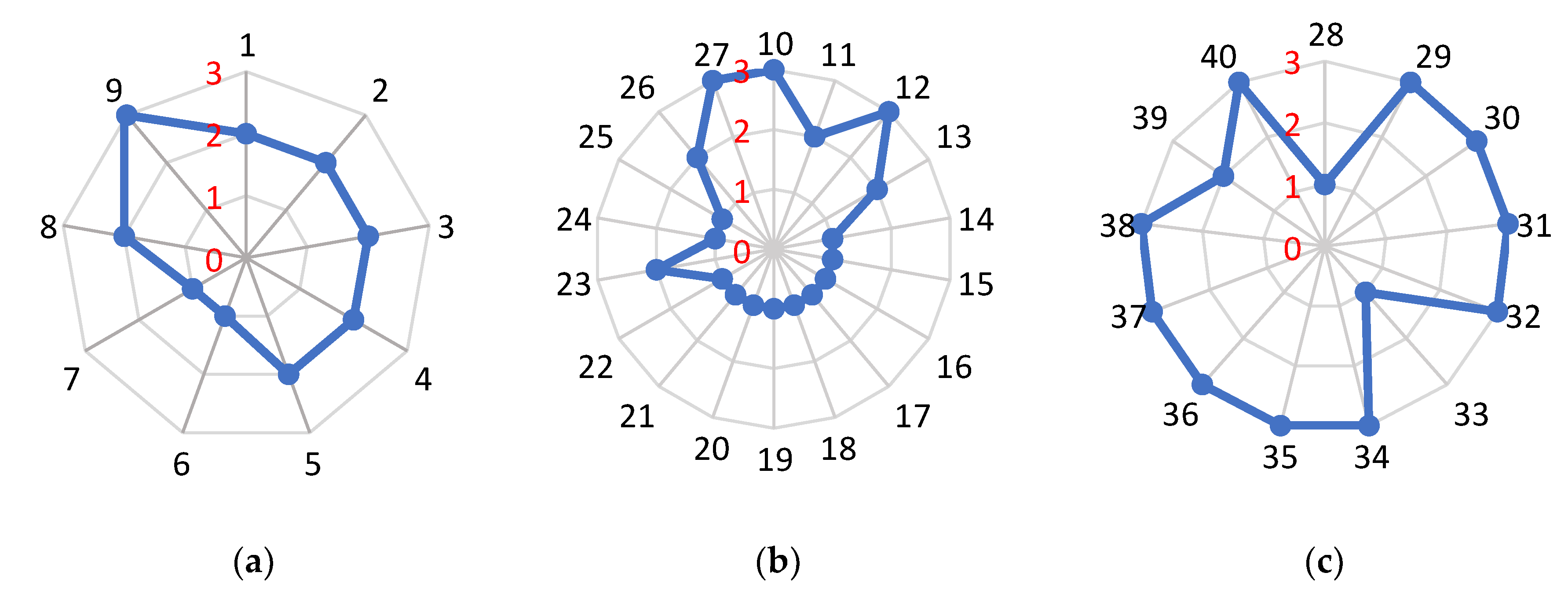
4.1. FFVA in the Baijiu Supply Chain: Overall Results
4.1.1. Opportunities
Technical Opportunities
Opportunities in Time and Space
4.1.2. Motivations
Economic Drivers
Cultural and Behavioral Drivers
4.1.3. Control Measures
Technical Measures
Managerial Measures
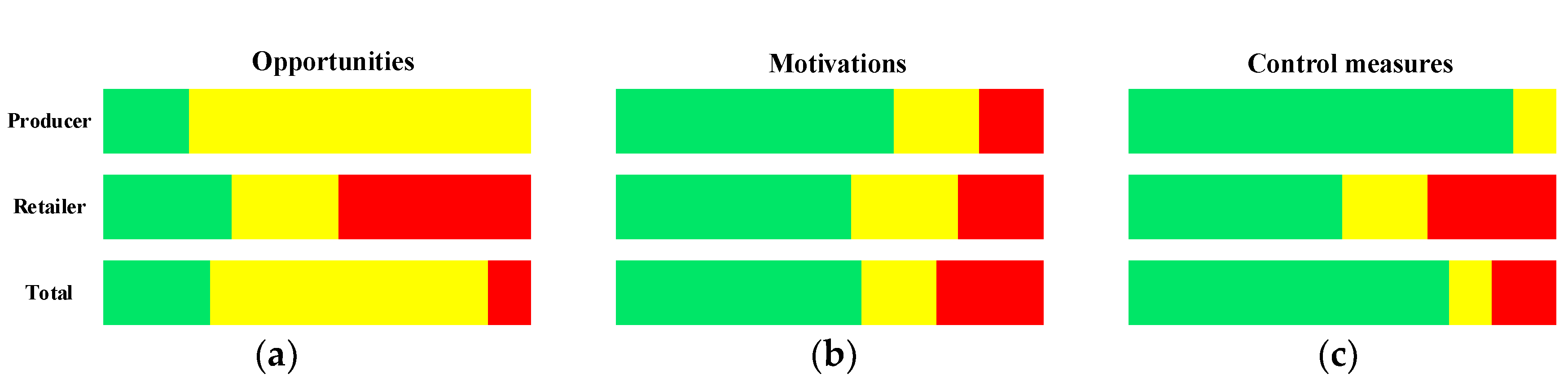
4.2. FFVA in the Baijiu Supply Chain: Differences between Producers and Retailers
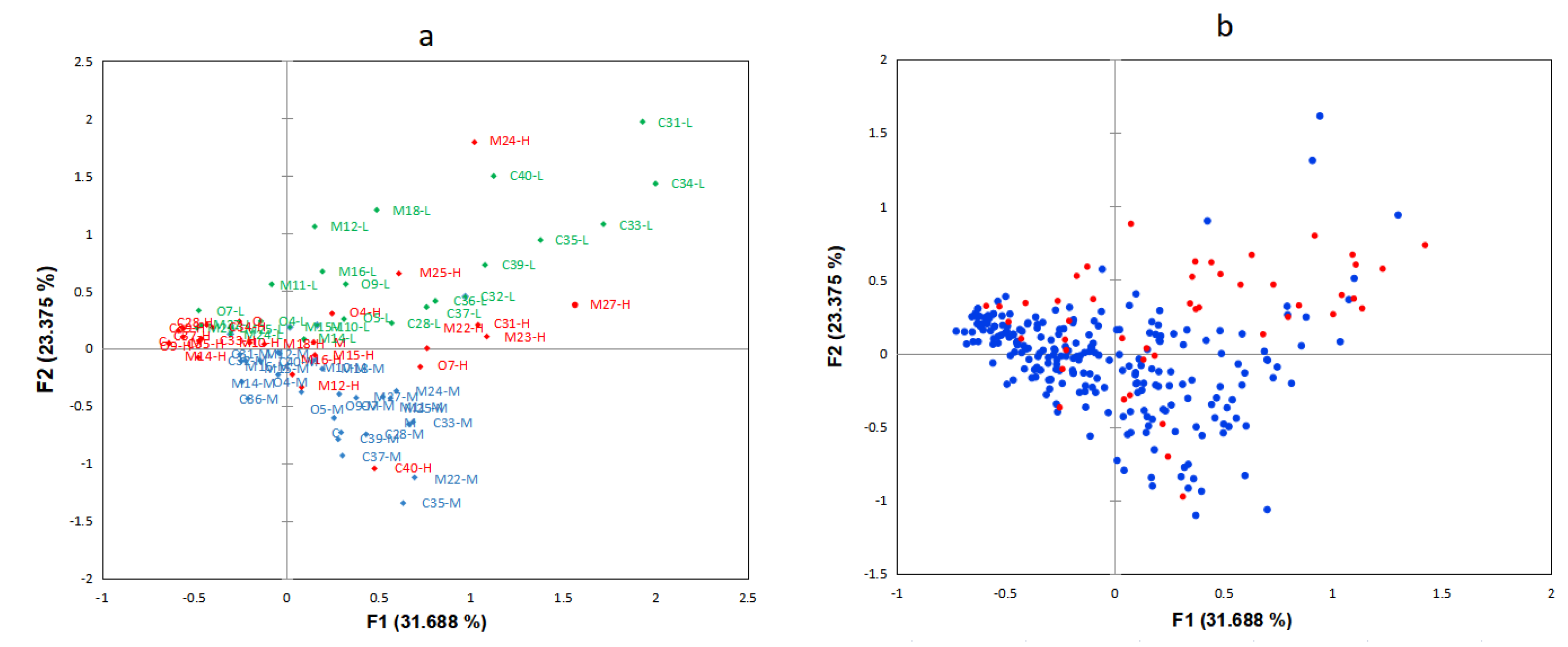
4.2.1. Difference Analysis of Multiple Correspondence Analysis
4.2.2. Mann-Whitney U Test
Opportunities
Motivations
Control Measures
5. Conclusions and Implications
5.1. Conclusions
5.2. Theoretical Implications
5.3. Practice Implications
5.4. Limitations
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Yin, S.J.; Wang, Y.Q.; Li, K. Pre-certification or retrospective?—The study of consumer preferences for food safety information labels and their interactive relationships. China Rural Surv. 2019, 5, 127–144. (In Chinese) [Google Scholar]
- Chen, M.; Wang, Y.Q.; Yin, S.J. Research on the Reformation Path of China’s Food Safety Certifification Policy: From the Perspective of Consumer Preference; Economy and Management Publishing House: Beijing, China, 2019. (In Chinese) [Google Scholar]
- Robson, K.; Dean, M.; Haughey, S.; Elliott, C. A comprehensive review of food fraud terminologies and food fraud mitigation guides. Food Control 2021, 120, 107516. [Google Scholar] [CrossRef]
- Spink, J.; Moyer, D.C.; Park, H.; Wu, Y.N.; Fersht, V.; Shao, B.; Hong, M.; Paek, S.Y.; Edelev, D. Introducing food fraud including translation and interpretation to Russian, Korean, and Chinese languages. Food Chem. 2015, 189, 102–107. [Google Scholar] [CrossRef] [PubMed]
- Spink, J.; Ortega, D.L.; Chen, C.; Wu, F. Food fraud prevention shifts the food risk focus to vulnerability. Trends Food Sci. Technol. 2017, 62, 215–220. [Google Scholar] [CrossRef]
- Zou, Z.S.; Zhang, Y.L.; Wang, X.L. Exchange Rate Exchanges, Trade Structure and Trade Benefit; China Social Sciences Press: Beijing, China, 2019. (In Chinese) [Google Scholar]
- Yang, Z.H.; Zhou, Q.; Wu, W.L.; Zhang, D.; Mo, L.F.; Liu, J.L.; Yang, X.F. Food fraud vulnerability assessment in the edible vegetable oil supply chain: A perspective of Chinese enterprises. Food Control 2022, 138, 109005. [Google Scholar] [CrossRef]
- Kendall, H.; Kuznesof, S.; Dean, M.; Chan, M.Y.; Clark, B.; Home, R.; Stolz, H.; Zhong, Q.D.; Liu, C.H.; Brereton, P. Chinese consumer’s attitudes, perceptions and behavioural responses towards food fraud. Food Control 2019, 95, 339–351. [Google Scholar] [CrossRef]
- Van Ruth, S.M.; Luning, P.A.; Silvis, I.C.J.; Yang, Y.; Huisman, W. Differences in fraud vulnerability in various food supply chains and their tiers. Food Control 2018, 84, 375–381. [Google Scholar] [CrossRef]
- Robson, K.; Dean, M.; Brooks, S.; Haughey, S.; Elliott, C. A 20-year analysis of reported food fraud in the global beef supply chain. Food Control 2020, 116, 107310. [Google Scholar] [CrossRef]
- Nhle, U. Food fraud, food crime oder kalter kaffee? J. Consum. Prot. Food Saf. 2017, 12, 197–199. [Google Scholar] [CrossRef]
- Yang, Y.; Huisman, W.; Hettinga, K.A.; Zhang, L.; Van Ruth, S.M. The Chinese milk supply chain: A fraud perspective. Food Control 2020, 113, 107211. [Google Scholar] [CrossRef]
- Manning, L.; Soon, J.M. Food fraud vulnerability assessment: Reliable data sources and effective assessment approaches. Trends Food Sci. Technol. 2019, 91, 159–168. [Google Scholar] [CrossRef]
- Cavin, C.; Cottenet, G.; Blancpain, C.; Bessaire, T.; Frank, N.; Zbinden, P. Food adulteration: From vulnerability assessment to new analytical solutions. Chimia 2016, 70, 329–333. [Google Scholar] [CrossRef] [PubMed]
- Van Ruth, S.M.; Huisman, W.; Luning, P.A. Food fraud vulnerability and its key factors. Trends Food Sci. Technol. 2017, 67, 70–75. [Google Scholar] [CrossRef]
- Silvis, I.C.J.; Van Ruth, S.M.; Van der Fels-Klerx, H.J.; Luning, P.A. Assessment of food fraud vulnerability in the spices chain: An explorative study. Food Control 2017, 81, 80–87. [Google Scholar] [CrossRef]
- Yang, Y.; Huisman, W.; Hettinga, K.A.; Liu, N.; Heck, J.; Schrijver, G.H.; Gaiardoni, L.; Van Ruth, S.M. Fraud vulnerability in the Dutch milk supply chain: Assessments of farmers, processors and retailers. Food Control 2019, 95, 308–317. [Google Scholar] [CrossRef]
- Yan, J.; Erasmus, S.W.; Aguilera Toro, M.; Huang, H.X.; Van Ruth, S.M. Food fraud: Assessing fraud vulnerability in the extra virgin olive oil supply chain. Food Control 2020, 111, 107081. [Google Scholar] [CrossRef]
- Sheldon, I.M. Certification mechanisms for credence attributes of foods: Does it matter who provides diagnosis? Annu. Rev. Resour. Econ 2017, 9, 33–51. [Google Scholar] [CrossRef]
- Spink, J.; Hegarty, P.V.; Fortin, N.D.; Elliott, C.T.; Moyer, D.C. The application of public policy theory to the emerging food fraud risk: Next steps. Trends Food Sci. Technol. 2019, 85, 116–128. [Google Scholar] [CrossRef]
- Wang, J.N.; Zhang, Y.H.; Wang, Y.T.; Chen, T.Q. Evolutionary dynamics of food safety riskby driven of economic interest. Chin. J. Manag. Sci. 2019, 27, 113–126. (In Chinese) [Google Scholar]
- Cao, Y.; Yu, Z.Y.; Wan, G.Y. Evolutionary game study between government and enterprises in food adulteration under the new media environment. Chin. J. Manag. Sci. 2017, 25, 179–187. (In Chinese) [Google Scholar]
- Power, A.C.; Jones, J.; NiNeil, C.; Geoghegan, S.; Warren, S.; Currivan, S.; Cozzolino, D. What’s in this drink? Classification and adulterant detection in Irish whiskey samples using near infrared spectroscopy combined with chemometrics. J. Sci. Food Agric. 2021, 101, 5256–5263. [Google Scholar] [CrossRef] [PubMed]
- Marvin, H.J.P.; Hoenderdaal, W.; Gavai, A.K.; Mu, W.J.; Van Den Bulka, L.M.; Liu, N.J.; Frasso, G.; Ozen, N.; Elliott, C.; Manning, L.; et al. Global media as an early warning tool for food fraud; an assessment of MedISys-FF. Food Control 2022, 137, 108961. [Google Scholar] [CrossRef]
- Burns, R.L.; Alexander, R.; Snaychuk, L.; Edwards, J.C.; Fitzgerald, N.; Gao, P.; Quan, D.H.; Douvris, C.; Vaughan, T.; Bussan, D.D. A fast, straightforward and inexpensive method for the authentication of baijiu spirit samples by fluorescence spectroscopy. Beverages 2021, 7, 65. [Google Scholar] [CrossRef]
- Li, H.L.; Luo, J.Y.; Li, L.; Xiang, N.; Wu, Y.N. Research and analysis of food fraud based on network data statistics. J. Food Saf. Qual. 2020, 11, 7. (In Chinese) [Google Scholar]
- Muhammad, A.; Countryman, A.M. In vino ‘No’ veritas: Impacts of fraud on wine imports in China. Aust. J. Agr. Resour. Econ. 2019, 63, 742–758. [Google Scholar] [CrossRef]
- Kirezieva, K.; Jacxsens, L.; Uyttendaele, M.; Van Boekel, M.A.J.S.; Luning, P.A. Assessment of food safety management systems in the global fresh produce chain. Food Res. Int. 2013, 52, 230–242. [Google Scholar] [CrossRef]
- Yin, S.J.; Li, R.; Wu, L.H.; Chen, X.J. Introduction to 2018 China Development Report on Food Safety; Peking University Press: Beijing, China, 2018. (In Chinese) [Google Scholar]
- Yang, Z.; Paudel, K.P.; Wen, X.X.; Sun, S.L.; Wang, Y. Food safety risk informationseeking intention of WeChat users in China. Int. J. Environ. Res. Public Health 2020, 17, 2376. [Google Scholar] [CrossRef] [PubMed]
- Fionn, M. Multiple correspondence analysis and related methods. Psychometrika 2007, 72, 275–277. [Google Scholar] [CrossRef]
- Coleman, J.W. Toward an integrated theory of white-collar crime. Am. J. Sociol. 1987, 93, 406–439. [Google Scholar] [CrossRef]
- Darby, M.R.; Karni, E. Free competition and the optimal amount of fraud. J. Law Econ. 1973, 16, 67–88. [Google Scholar] [CrossRef]
- Van Ruth, S.M.V.; De Pagter-de Witte, L. Integrity of organic foods and their suppliers: Fraud vulnerability across chains. Foods 2020, 9, 188. [Google Scholar] [CrossRef] [PubMed]
- Ehmke, M.D.; Bonanno, A.; Boys, K.; Smith, T. Food fraud: Economic insights into the dark side of incentives. Aust. J. Agr. Resour. Econ. 2019, 63, 685–700. [Google Scholar] [CrossRef]
| Opportunities | Motivations | Control |
|---|---|---|
| Technical opportunities | Economic drivers | Technical measures |
| 1. The degree of difficulty of adulteration of raw materials | 10. Raw material price | 28. Raw material counterfeit detection system |
| 2. Raw material adulteration technology and knowledge accessibility | 11. Raw material supply | 29. Final product counterfeit detection system |
| 3. Ability to detect adulteration of raw materials | 12. The special composition or properties of raw materials | 30. Traceability system for enterprises |
| 4. The degree of difficulty in counterfeiting the final product | 13. The economic situation of the enterprise | 35. Fraud prevention management process for suppliers |
| 5. Ability to detect final product counterfeiting | 17. Financial pressure on suppliers | 36. Supplier’s traceability system |
| Opportunities in time and place | 18. Economic situation of suppliers | 40. Fraud contingency programs |
| 6. Control of production and processing process | 23. The economic situation of the supply chain sector | Managerial measures |
| 7. Supply chain transparency | 26. Historical events of fraud in the supply chain | 31. Integrity screening of employees |
| 8. Historical events of raw material counterfeiting | 27. Competition level in the supply chain | 32. Ethical and cultural code of conduct for enterprises |
| 9. Historical events of final product counterfeiting | Cultural and behavioral drivers | 33. Internal whistleblowing system of the enterprise |
| 14. Organizational strategy of enterprises | 34. Contract requirements with suppliers | |
| 15. The ethical culture of enterprises | 37. The degree of social control of the supply chain | |
| 16. Violation of laws and regulations of enterprises | 38. Fraud prevention measures in the supply chain | |
| 19. Supplier’s organizational strategy | 39. Local enforcement against food fraud | |
| 20. Ethical culture of suppliers | ||
| 21. Violations of laws and regulations of suppliers | ||
| 22. Suppliers’ exposure to food fraud | ||
| 24. Crime situation in the downstream chain | ||
| 25. The ethical culture of fraud in the supply chain |
| Research Links | Interviewee Position | Number | Percentage |
|---|---|---|---|
| Producer | Middle and senior managers | 172 | 70.8% |
| Employees in the production departments | 37 | 15.2% | |
| Employees in other departments | 34 | 14.0% | |
| Retailers | Middle and senior managers | 45 | 100.0% |
| Key Elements | Fraud Factors | Producers | Retailers | Rank Average of Producers | Rank Average of Retailers | Z-Value | Sig. (2-Tailed) |
|---|---|---|---|---|---|---|---|
| Opportunities | Factor 1 | M | NA | ||||
| Factor 2 | M | NA | |||||
| Factor 3 | M | NA | |||||
| Factor 4 | M | H | 134.49 | 198.56 | −5.252 | 0.000 *** | |
| Factor 5 | M | M | 147.63 | 127.62 | −2.006 | 0.013 ** | |
| Factor 6 | L | NA | |||||
| Factor 7 | L | L | 145.03 | 141.66 | −2.774 | 0.005 *** | |
| Factor 8 | M | NA | |||||
| Factor 9 | M | H | 159.97 | 60.94 | −7.820 | 0.000 *** | |
| Motivations | Factor 10 | L | H | 146.44 | 134.00 | −2.001 | 0.027 ** |
| Factor 11 | M | M | 146.51 | 133.66 | −3.206 | 0.000 *** | |
| Factor 12 | H | NA | |||||
| Factor 13 | M | M | 150.84 | 110.28 | −4.517 | 0.000 *** | |
| Factor 14 | L | NA | |||||
| Factor 15 | L | NA | |||||
| Factor 16 | L | NA | |||||
| Factor 17 | L | L | 143.60 | 149.37 | −3.568 | 0.000 *** | |
| Factor 18 | M | L | 146.90 | 131.53 | −2.229 | 0.009 ** | |
| Factor 19 | L | L | 142.55 | 155.03 | −2.007 | 0.022 ** | |
| Factor 20 | L | L | 139.35 | 172.32 | −2.862 | 0.004 *** | |
| Factor 21 | L | L | 141.06 | 163.06 | −1.990 | 0.047 ** | |
| Factor 22 | L | L | 143.14 | 151.83 | −2.775 | 0.004 *** | |
| Factor 23 | M | M | 152.36 | 102.04 | −4.126 | 0.000 *** | |
| Factor 24 | L | NA | |||||
| Factor 25 | L | L | 139.60 | 170.93 | −2.697 | 0.007 *** | |
| Factor 26 | NA | M | |||||
| Factor 27 | H | H | 142.66 | 154.41 | −2.029 | 0.019 ** | |
| Control measures | Factor 28 | L | H | 150.14 | 114.07 | −2.891 | 0.004 *** |
| Factor 29 | L | NA | |||||
| Factor 30 | L | NA | |||||
| Factor 31 | L | L | 149.27 | 118.72 | −2.639 | 0.008 *** | |
| Factor 32 | L | L | 152.54 | 101.09 | −4.644 | 0.000 *** | |
| Factor 33 | M | H | 149.69 | 116.48 | −2.608 | 0.009 *** | |
| Factor 34 | L | L | 145.91 | 136.91 | −2.725 | 0.006 *** | |
| Factor 35 | L | M | 144.82 | 142.78 | −4.231 | 0.000 *** | |
| Factor 36 | L | L | 142.78 | 142.70 | −3.233 | 0.000 *** | |
| Factor 37 | L | NA | |||||
| Factor 38 | L | H | 154.93 | 88.20 | −5.449 | 0.000 *** | |
| Factor 39 | L | M | 143.19 | 151.60 | −1.993 | 0.049 ** | |
| Factor 40 | L | L | 152.13 | 103.28 | −4.382 | 0.000 *** |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, Y.; Liu, J.; Xiong, Y.; Liu, X.; Wen, X. Food Fraud Vulnerability Assessment in the Chinese Baijiu Supply Chain. Foods 2023, 12, 516. https://doi.org/10.3390/foods12030516
Wang Y, Liu J, Xiong Y, Liu X, Wen X. Food Fraud Vulnerability Assessment in the Chinese Baijiu Supply Chain. Foods. 2023; 12(3):516. https://doi.org/10.3390/foods12030516
Chicago/Turabian StyleWang, Yiqin, Jiali Liu, Yanling Xiong, Xuefan Liu, and Xiaowei Wen. 2023. "Food Fraud Vulnerability Assessment in the Chinese Baijiu Supply Chain" Foods 12, no. 3: 516. https://doi.org/10.3390/foods12030516
APA StyleWang, Y., Liu, J., Xiong, Y., Liu, X., & Wen, X. (2023). Food Fraud Vulnerability Assessment in the Chinese Baijiu Supply Chain. Foods, 12(3), 516. https://doi.org/10.3390/foods12030516




