Disaster-Resilient Optical Network Survivability: A Comprehensive Survey
Abstract
1. Introduction
2. Protection and Restoration
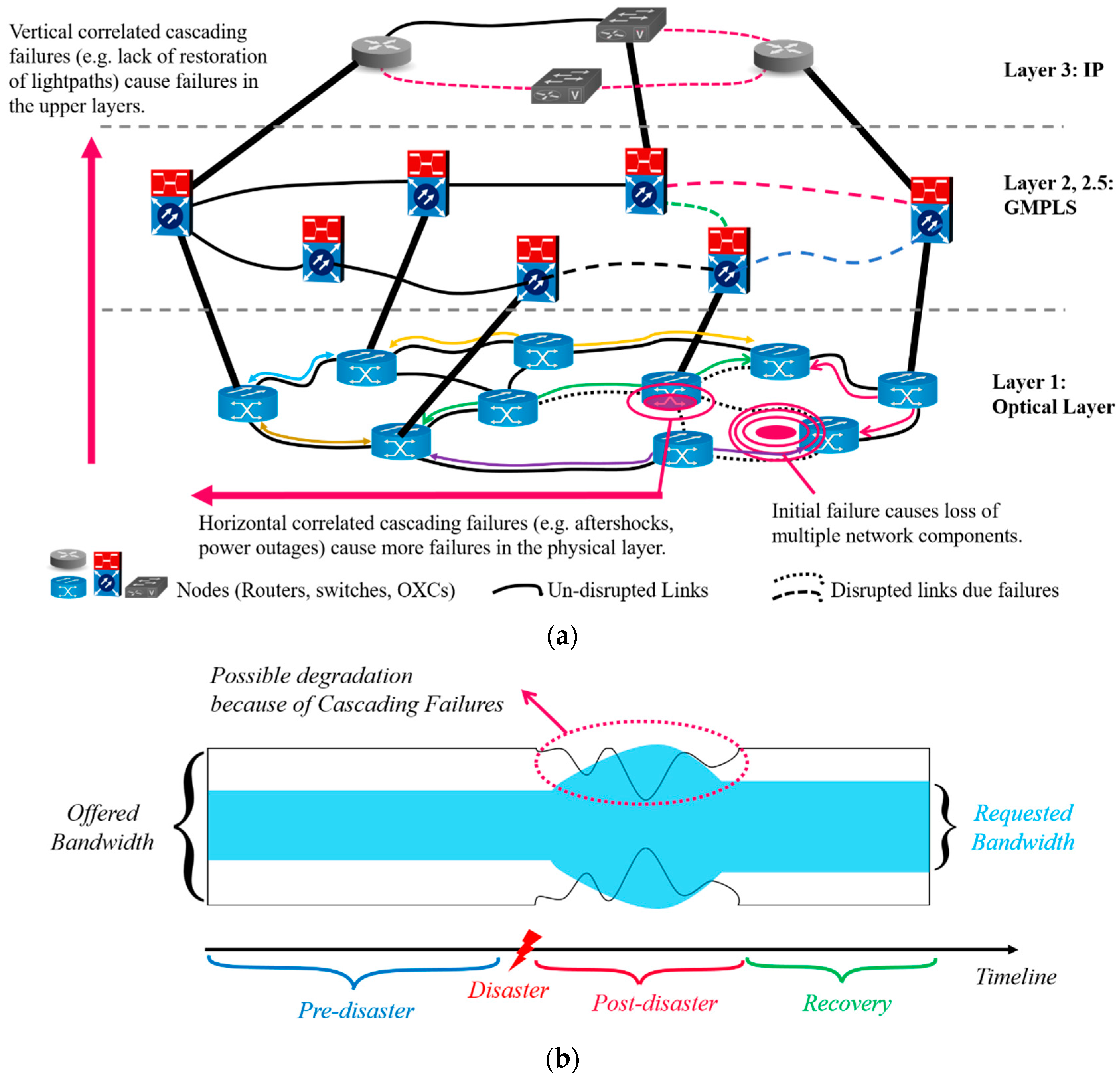
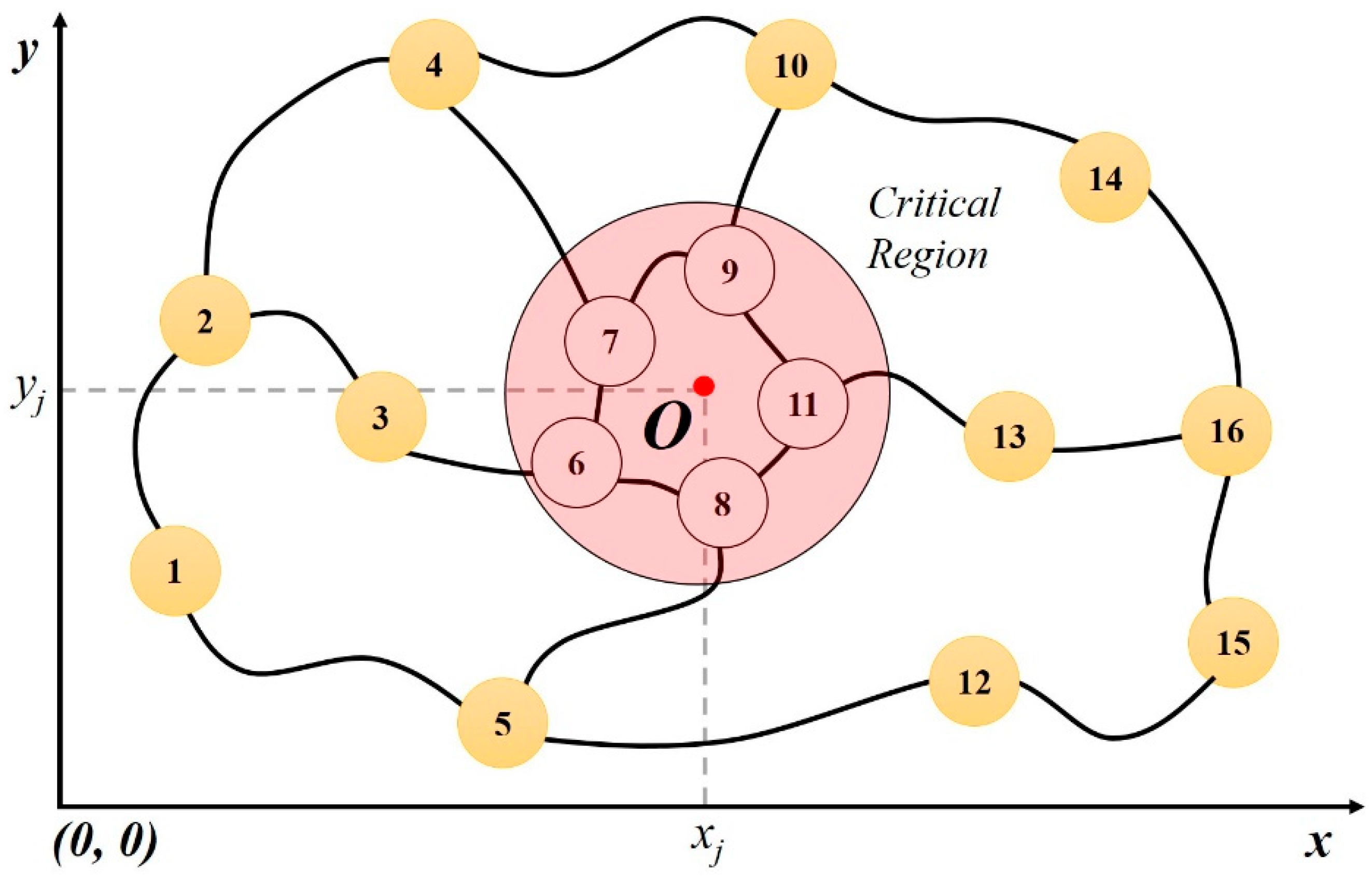
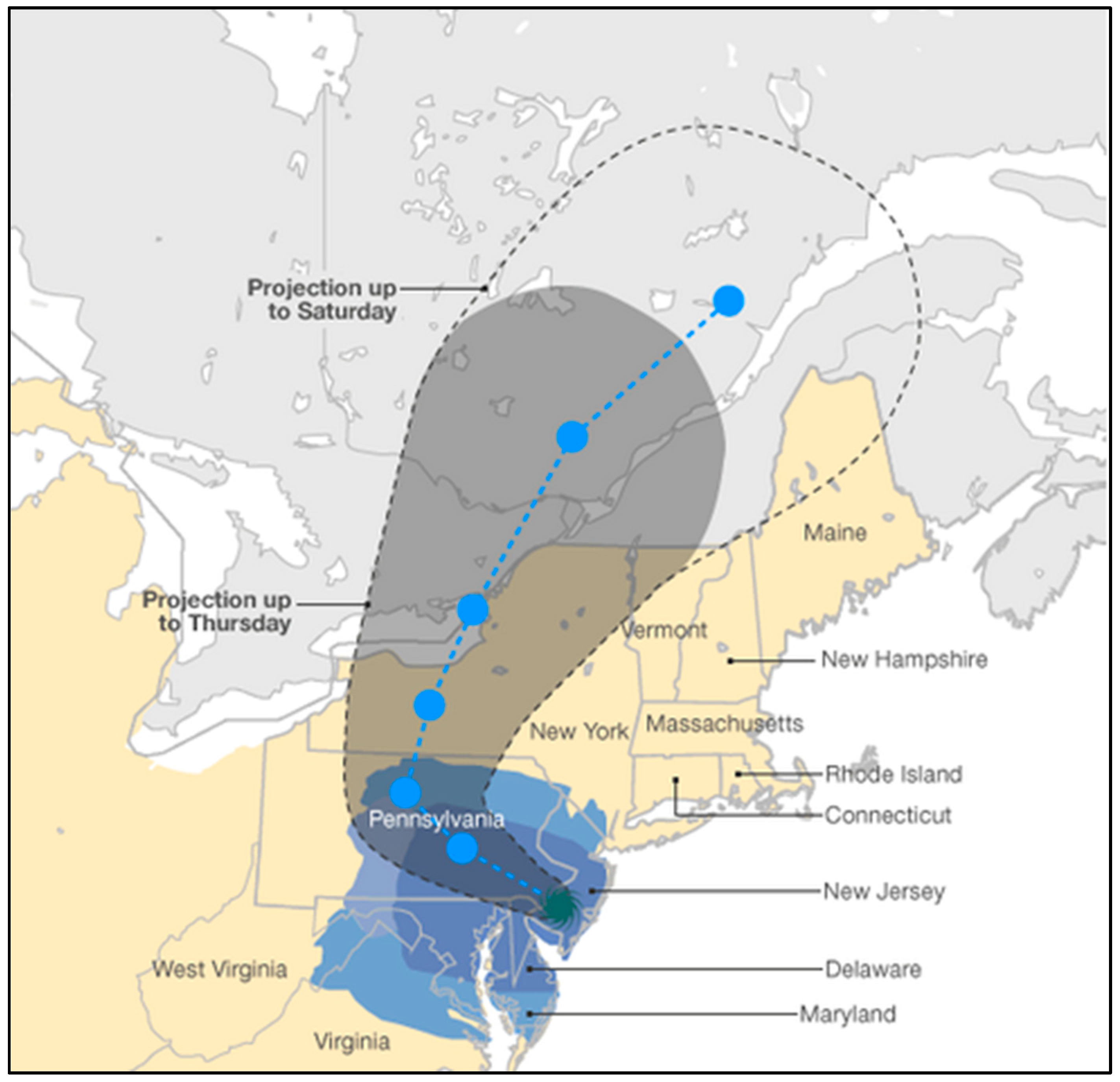
3. Disaster-Based Correlated Cascading Failures
4. Disaster-Aware Network Survivability
5. Congestion-Aware Routing and Wavelength Assignment
6. Challenges in Disaster-Resilient Optical Network Survivability
7. Conclusions
Funding
Conflicts of Interest
Acronyms
| ASR | Availability Satisfaction Ratio |
| ATM | Asynchronous Transfer Mode |
| BTS | Base Transceiver Station |
| CASPaR | Congestion Avoidance Shortest Path Routing |
| cTGGD | Compensated Total Geographical Graph Diversity |
| DAL | Distributed Lightpath Allocation |
| DLBSPP | Dynamic Load Balancing Shared Path Protection |
| DRG | Distinct Risk Groups |
| DWDM | Dense Wavelength Division Multiplexing |
| EMP | Electromagnetic Pulse |
| FTBCP | Fault Tolerance Method Based on Cheapest Paths |
| GeoDivRP | Geodiverse Routing Protocol |
| GIS | Geographic Information System |
| GMPLS | Generalized Multi-Protocol Label Switching |
| HCA | Hybrid Connection Algorithm |
| ICT | Information Communication Technology |
| ILP | Integer Linear Programming |
| IP Layer | Internet Protocol Layer |
| ISIS | Intermediate System to Intermediate System |
| LC-DAL | Least-Congested Distributed Lightpath Allocation |
| MILP | Mixed Integer Linear Programming |
| MPLS | Multi-Protocol Label Switching |
| OSPF | Open Shortest Path First |
| OXCs | Optical Cross-Connects |
| PCE | Path Computation Element |
| PDP | Packet Delivery Probability |
| QoS | Quality of Service |
| QoT | Quality of Transmission |
| RECODIS | Resilient Communication services protecting end-user applications from Disaster-based failures |
| RWA | Routing and Wavelength Assignment |
| SDH | Synchronous Digital Hierarchy |
| SDON | Software-Defined Optical Networking |
| SFPP | Short Full Path Protection |
| SLA | Service Level Agreement |
| SONET | Synchronous Optical Network |
| SPPP | Shortest Path Pair Protection |
| STAR | Self-Tuned Adaptive Routing |
| WDM | Wavelength Division Multiplexing |
| WMD | Weapon of Mass Destruction |
| WRT | Wavelength Retuning |
References
- Agrawal, A.; Sharma, P.; Bhatia, V.; Prakash, S. Survivability improvement against earthquakes in backbone optical networks using actual seismic zone information. arXiv, 2017; arXiv:1703.02358. [Google Scholar]
- How Much Bandwidth Do We Need? Available online: https://arstechnica.com/business/2012/05/bandwidth-explosion-as-internet-use-soars-can-bottlenecks-be-averted/ (accessed on 13 April 2017).
- Saleh, A.A.; Simmons, J.M. Technology and architecture to enable the explosive growth of the internet. IEEE Commun. Mag. 2011, 49, 126–132. [Google Scholar] [CrossRef]
- Awduche, D.; Chiu, A.; Elwalid, A.; Widjaja, I.; Xiao, X. Overview and Principles of Internet Traffic Engineering; RFC 3272; IETF: Fremont, CA, USA, 2002. [Google Scholar]
- Bouillet, E.; Ellinas, G.; Labourdette, J.F.; Ramamurthy, R. Mesh routing and recovery framework. In Path Routing in Mesh Optical Networks; John Wiley & Sons Ltd.: Chichester, UK, 2007; pp. 61–80. [Google Scholar]
- Sivalingam, K.M.; Subramaniam, S. Emerging Optical Network Technologies: Architectures, Protocols and Performance; Springer Science & Business Media: New York, NY, USA, 2005. [Google Scholar]
- Rak, J.; Hutchison, D.; Calle, E.; Gomes, T.; Gunkel, M.; Smith, P.; Tapolcai, J.; Verbrugge, S.; Wosinska, L. Recodis: Resilient communication services protecting end-user applications from disaster-based failures. In Proceedings of the 18th International Conference on Transparent Optical Networks (ICTON), Trento, Italy, 10–14 July 2016; pp. 1–4. [Google Scholar]
- Adachi, T.; Ishiyama, Y.; Asakura, Y.; Nakamura, K. The restoration of telecom power damages by the great east japan earthquake. In Proceedings of the IEEE 33rd International Telecommunications Energy Conference (INTELEC), Amsterdam, The Netherlands, 9–13 October 2011; pp. 1–5. [Google Scholar]
- Urushidani, S.; Aoki, M.; Fukuda, K.; Abe, S.; Nakamura, M.; Koibuchi, M.; Ji, Y.; Yamada, S. Highly available network design and resource management of SINET4. Telecommun. Syst. 2014, 56, 33–47. [Google Scholar] [CrossRef]
- Okumura, H. The 3.11 disaster and data. J. Inf. Process. 2014, 22, 566–573. [Google Scholar] [CrossRef]
- Seismonepal Website. Available online: http://seismonepal.gov.np/ (accessed on 12 January 2018).
- Dawadi, B.R.; Shakya, S. Ict implementation and infrastructure deployment approach for rural nepal. In Recent Advances in Information and Communication Technology; Springer: Cham, Switzerland, 2016; pp. 319–331. [Google Scholar]
- Mexico Earthquake Fact Sheet #5 (29 September 2017). Available online: https://www.usaid.gov/sites/default/files/documents/1866/mexico_eq_fs05_09-29-2017.pdf (accessed on 12 January 2018).
- Undersea Internet Cables Off Egypt Disrupted as Navy Arrests Three. Available online: https://www.theguardian.com/technology/2013/mar/28/egypt-undersea-cable-arrests (accessed on 12 January 2018).
- Koshimura, S.; Kayaba, S.; Matsuoka, M. Integrated approach to assess the impact of tsunami disaster. In Safety, Reliability and Risk of Structures, Infrastructures and Engineering Systems; Taylor & Francis Group: London, UK, 2010; pp. 2302–2307. [Google Scholar]
- Lin, Z.; Levy, J.K.; Lei, H.; Bell, M.L. Advances in disaster modeling, simulation and visualization for sandstorm risk management in North China. Remote Sens. 2012, 4, 1337–1354. [Google Scholar] [CrossRef]
- Habib, M.F.; Tornatore, M.; Dikbiyik, F.; Mukherjee, B. Disaster survivability in optical communication networks. Comput. Commun. 2013, 36, 630–644. [Google Scholar] [CrossRef]
- Goścień, R.; Walkowiak, K. Modeling and optimization of data center location and routing and spectrum allocation in survivable elastic optical networks. Opt. Switch. Netw. 2017, 23, 129–143. [Google Scholar] [CrossRef]
- Davis, D.A.; Vokkarane, V.M. Generalized survivability models for many-to-many communication. In Proceedings of the 2018 International Conference on Computing, Networking and Communications (ICNC), Maui, HI, USA, 5–8 March 2018; pp. 729–735. [Google Scholar]
- Zhang, W.; Tang, J.; Wang, C.; de Soysa, S. Reliable adaptive multipath provisioning with bandwidth and differential delay constraints. In Proceedings of the IEEE INFOCOM, San Diego, CA, USA, 14–19 March 2010; pp. 1–9. [Google Scholar]
- Mauthe, A.; Hutchison, D.; Cetinkaya, E.K.; Ganchev, I.; Rak, J.; Sterbenz, J.P.; Gunkelk, M.; Smith, P.; Gomes, T. Disaster-resilient communication networks: Principles and best practices. In Proceedings of the 2016 8th International Workshop on Resilient Networks Design and Modeling (RNDM), Halmstad, Sweden, 13–15 September 2016; pp. 1–10. [Google Scholar]
- Gomes, T.; Tapolcai, J.; Esposito, C.; Hutchison, D.; Kuipers, F.; Rak, J.; de Sousa, A.; Iossifides, A.; Travanca, R.; André, J. A survey of strategies for communication networks to protect against large-scale natural disasters. In Proceedings of the 8th International Workshop on Resilient Networks Design and Modeling (RNDM), Halmstad, Sweden, 13–15 September 2016; pp. 11–22. [Google Scholar]
- Kmiecik, W.; Rak, J.; Medeiros, C.; Heegaard, P.E.; Mas Machuca, C.; André, J.; Jorge, L.; Musumeci, F.; Voyiatzis, A.; Pasic, A. A survey on network resiliency methodologies against weather-based disruptions. In Proceedings of the 2016 8th International Workshop on Resilient Networks Design and Modeling (RNDM), Halmstad, Sweden, 13–15 September 2016. [Google Scholar]
- Tornatore, M.; André, J.; Babarczi, P.; Braun, T.; Følstad, E.; Heegaard, P.; Hmaity, A.; Furdek, M.; Jorge, L.; Kmiecik, W.; et al. A survey on network resiliency methodologies against weather-based disruptions. In Proceedings of the 2016 8th International Workshop on Resilient Networks Design and Modeling (RNDM), Halmstad, Sweden, 13–15 September 2016; pp. 23–34. [Google Scholar]
- Shiraiwa, M.; Yoshikane, N.; Xu, S.; Tsuritani, T.; Miyata, N.; Mori, T.; Miyabe, M.; Katagiri, T.; Yoshida, S.; Tanaka, M. Experimental demonstration of disaggregated emergency optical system for quick disaster recovery. J. Lightw. Technol. 2018, 36, 3083–3096. [Google Scholar] [CrossRef]
- Shiraiwa, M.; Yoshikane, N.; Xu, S.; Tsuritani, T.; Miyata, N.; Mori, T.; Miyabe, M.; Katagiri, T.; Yoshida, S.; Tanaka, M. First experimental demonstration of disaggregated emergency optical system for quick disaster recovery. In Proceedings of the Optical Fiber Communication Conference, San Diego, CA, USA, 11–15 March 2018; p. Th2A.29. [Google Scholar]
- Zhou, D.; Subramaniam, S. Survivability in optical networks. IEEE Netw. 2000, 14, 16–23. [Google Scholar]
- Zhang, J.; Mukherjee, B. A review of fault management in wdm mesh networks: Basic concepts and research challenges. IEEE Netw. 2004, 18, 41–48. [Google Scholar] [CrossRef]
- Mukherjee, B. Optical WDM Networks; Springer Science & Business Media: New York, NY, USA, 2006. [Google Scholar]
- Rani, S.; Sharma, A.K.; Singh, P. Survivability strategy with congestion control in wdm optical networks. In Proceedings of the International Symposium on High Capacity Optical Networks and Enabling Technologies (HONET 2007), Dubai, UAE, 18–20 November 2007; pp. 1–4. [Google Scholar]
- Zhang, Z.; Li, Z.; He, Y. Network capacity analysis for survivable WDM optical networks. In Proceedings of the International Conference on Instrumentation, Measurement, Circuits, and Systems (IMCCC 2012), Harbin, China, 8–10 December 2012; pp. 291–296. [Google Scholar]
- Sengupta, S.; Ramamurthy, R. From network design to dynamic provisioning and restoration in optical cross-connect mesh networks: An architectural and algorithmic overview. IEEE Netw. 2001, 15, 46–54. [Google Scholar] [CrossRef]
- Gupta, R.; Chi, E.; Walrand, J. Different algorithms for normal and protection paths. J. Netw. Syst. Manag. 2005, 13, 13–33. [Google Scholar] [CrossRef]
- Ramamurthy, S.; Mukherjee, B. Survivable wdm mesh networks. Part I—Protection. In Proceedings of the Eighteenth Annual Joint Conference of the IEEE Computer and Communications Societies INFOCOM’99, New York, NY, USA, 21–25 March 1999; pp. 744–751. [Google Scholar]
- Saini, H.; Garg, A.K. Protection and restoration schemes in optical networks: A comprehensive survey. Int. J. Microw. Appl. 2013, 2, 5–11. [Google Scholar]
- Chatterjee, B.C.; Sarma, N.; Sahu, P.P.; Oki, E. Literature survey. In Routing and Wavelength Assignment for WDM-Based Optical Networks; Springer: Cham, Switzerland, 2017; pp. 17–34. [Google Scholar]
- Gill, P.; Jain, N.; Nagappan, N. Understanding network failures in data centers: Measurement, analysis, and implications. In Proceedings of the ACM SIGCOMM Computer Communication Review, Toronto, ON, Canada, 15–19 August 2011; pp. 350–361. [Google Scholar]
- Mohan, N.; Seema. Network protection and restoration in optical networks: A comprehensive study. Int. J. Res. Eng. Technol. (IJERT) 2013, 2, 50–54. [Google Scholar]
- Ramamurthy, S.; Sahasrabuddhe, L.; Mukherjee, B. Survivable WDM mesh networks. J. Lightw. Technol. 2003, 21, 870. [Google Scholar] [CrossRef]
- Vasseur, J.-P.; Pickavet, M.; Demeester, P. Network Recovery: Protection and Restoration of Optical, SONET-SDH, IP, and MPLS; Elsevier: San Francisco, CA, USA, 2004. [Google Scholar]
- Maier, G.; Pattavina, A.; De Patre, S.; Martinelli, M. Optical network survivability: Protection techniques in the wdm layer. Photonic Netw. Commun. 2002, 4, 251–269. [Google Scholar] [CrossRef]
- Binti Halida, S.N.F.; Idrus, S.; Farabi, M.; Zulkifli, N. Dedicated protection scheme for optical networks survivability. In Proceedings of the 2011 4th International Conference on Modeling, Simulation and Applied Optimization (ICMSAO), Kuala Lumpur, Malaysia, 19–21 April 2011; pp. 1–5. [Google Scholar]
- Bouillet, E. Path Routing in Mesh Optical Networks; John Wiley & Sons: Chichester, UK, 2007. [Google Scholar]
- Alshaer, H. Dynamic connection provisioning with shared protection in IP/WDM networks. Int. J. Commun. Syst. 2014, 27, 2832–2850. [Google Scholar] [CrossRef]
- Ou, C.; Zang, H.; Singhal, N.K.; Zhu, K.; Sahasrabuddhe, L.H.; MacDonald, R.A.; Mukherjee, B. Subpath protection for scalability and fast recovery in optical wdm mesh networks. IEEE J. Sel. Areas Commun. 2004, 22, 1859–1875. [Google Scholar] [CrossRef]
- Choi, H.; Subramaniam, S.; Choi, H.-A. On double-link failure recovery in wdm optical networks. In Proceedings of the Twenty-First Annual Joint Conference of the IEEE Computer and Communications Societies INFOCOM, New York, NY, USA, 23–27 June 2002; pp. 808–816. [Google Scholar]
- Ramasubramanian, S.; Chandak, A. Dual-link failure resiliency through backup link mutual exclusion. IEEE/ACM Trans. Netw. 2008, 16, 157–169. [Google Scholar] [CrossRef]
- Guo, Y.; Kuipers, F.; Van Mieghem, P. Link-disjoint paths for reliable qos routing. Int. J. Commun. Syst. 2003, 16, 779–798. [Google Scholar] [CrossRef]
- Kim, S.-I.; Lumetta, S. Multiple Failure Survivability in WDM Mesh Networks; Report No. UILU-ENG-06-2205; Coordinated Science Laboratory: Urbana, IL, USA, 2006. [Google Scholar]
- Sivakumar, M.; Maciocco, C.; Mishra, M.; Sivalingam, K.M. A hybrid protection-restoration mechanism for enhancing dual-failure restorability in optical mesh-restorable networks. In Proceedings of the OptiComm 2003: Optical Networking and Communications, Dallas, TX, USA, 1 October 2003; pp. 37–48. [Google Scholar]
- Ruan, L.; Feng, T. A hybrid protection/restoration scheme for two-link failure in wdm mesh networks. In Proceedings of the Global Telecommunications Conference (GLOBECOM 2010), Miami, FL, USA, 6–10 December 2010; pp. 1–5. [Google Scholar]
- Feng, T.; Long, L.; Kamal, A.E.; Ruan, L. Two-link failure protection in WDM mesh networks with p-cycles. Comput. Netw. 2010, 54, 3068–3080. [Google Scholar] [CrossRef]
- Jaumard, B.; Bui, M.; Mukherjee, B.; Vadrevu, C.S. Ip restoration vs. Optical protection: Which one has the least bandwidth requirements? Opt. Switch. Netw. 2013, 10, 261–273. [Google Scholar] [CrossRef]
- Zhao, Y.; Li, X.; Li, H.; Wang, X.; Zhang, J.; Huang, S. Multi-link faults localization and restoration based on fuzzy fault set for dynamic optical networks. Opt. Express 2013, 21, 1496–1511. [Google Scholar] [CrossRef] [PubMed]
- Kadohata, A.; Tanaka, T.; Imajuku, W.; Inuzuka, F.; Watanabe, A. Rapid restoration sequence of fiber links and communication paths from catastrophic failures. IEICE Trans. Fundam. Electron. Commun. Comput. Sci. 2016, 99, 1510–1517. [Google Scholar] [CrossRef]
- Yadav, D.S.; Rana, S.; Prakash, S. Hybrid connection algorithm: A strategy for efficient restoration in wdm optical networks. Opt. Fiber Technol. 2010, 16, 90–99. [Google Scholar] [CrossRef]
- Rani, S.; Sharma, A.K.; Singh, P. Restoration approach in wdm optical networks. Optik 2007, 118, 25–28. [Google Scholar] [CrossRef]
- Chen, B.; Zhang, J.; Zhao, Y.; Lv, C.; Zhang, W.; Huang, S.; Zhang, X.; Gu, W. Multi-link failure restoration with dynamic load balancing in spectrum-elastic optical path networks. Opt. Fiber Technol. 2012, 18, 21–28. [Google Scholar] [CrossRef]
- Jara, N.; Rubino, G.; Vallejos, R. Alternate paths for multiple fault tolerance on dynamic wdm optical networks. In Proceedings of the 2017 IEEE 18th International Conference on High Performance Switching and Routing (HPSR), Campinas, Brazil, 18–21 June 2017; pp. 1–6. [Google Scholar]
- Brodkin, J. Why Gmail Went Down: Google Misconfigured Load Balancing Servers. Available online: https://arstechnica.com/information-technology/2012/12/why-gmail-went-down-google-misconfigured-chromes-sync-server/ (accessed on 2 February 2018).
- Pescaroli, G.; Alexander, D. A definition of cascading disasters and cascading effects: Going beyond the toppling dominos metaphor. Planet@ Risk 2015, 3, 58–67. [Google Scholar]
- Mukherjee, B.; Habib, M.; Dikbiyik, F. Network adaptability from disaster disruptions and cascading failures. IEEE Commun. Mag. 2014, 52, 230–238. [Google Scholar] [CrossRef]
- Erjongmanee, S.; Ji, C. Large-scale network-service disruption: Dependencies and external factors. IEEE Trans. Netw. Serv. Manag. 2011, 8, 375–386. [Google Scholar] [CrossRef]
- Savla, K.; Como, G.; Dahleh, M.A. Robust network routing under cascading failures. IEEE Trans. Netw. Sci. Eng. 2014, 1, 53–66. [Google Scholar] [CrossRef]
- Zhao, J.; Li, D.; Sanhedrai, H.; Cohen, R.; Havlin, S. Spatio-temporal propagation of cascading overload failures in spatially embedded networks. Nat. Commun. 2016, 7, 10094. [Google Scholar] [CrossRef] [PubMed]
- Zhou, Z.; Lin, T.; Thulasiraman, K.; Xue, G.; Sahni, S. Cross-layer network survivability under multiple cross-layer metrics. J. Opt. Commun. Netw. 2015, 7, 540–553. [Google Scholar] [CrossRef]
- Papanikolaou, P.; Christodoulopoulos, K.; Varvarigos, E. Joint multi-layer survivability techniques for ip-over-elastic-optical-networks. J. Opt. Commun. Netw. 2017, 9, A85–A98. [Google Scholar] [CrossRef]
- Dikbiyik, F.; Tornatore, M.; Mukherjee, B. Minimizing the risk from disaster failures in optical backbone networks. J. Lightwave Technol. 2014, 32, 3175–3183. [Google Scholar] [CrossRef]
- Prucnal, P.R.; Fok, M.P.; Deng, Y.; Wang, Z. Physical layer security in fiber-optic networks using optical signal processing. In Proceedings of the 2009 Asia Communications and Photonics Conference and Exhibition (ACP), Shanghai, China, 2–6 November 2009; pp. 1–10. [Google Scholar]
- Rejeb, R.; Leeson, M.S.; Machuca, C.M.; Tomkos, I. Control and management issues in all-optical networks. J. Netw. 2010, 5, 132–139. [Google Scholar] [CrossRef]
- Kitayama, K.-I.; Sasaki, M.; Araki, S.; Tsubokawa, M.; Tomita, A.; Inoue, K.; Harasawa, K.; Nagasako, Y.; Takada, A. Security in photonic networks: Threats and security enhancement. J. Lightwave Technol. 2011, 29, 3210–3222. [Google Scholar] [CrossRef]
- Fok, M.P.; Wang, Z.; Deng, Y.; Prucnal, P.R. Optical layer security in fiber-optic networks. IEEE Trans. Inf. Forensics Secur. 2011, 6, 725–736. [Google Scholar] [CrossRef]
- Peng, Y.; Sun, Z.; Du, S.; Long, K. Propagation of all-optical crosstalk attack in transparent optical networks. Opt. Eng. 2011, 50, 085002. [Google Scholar]
- Furdek, M.; Skorin-Kapov, N.; Zsigmond, S.; Wosinska, L. Vulnerabilities and security issues in optical networks. In Proceedings of the 2014 16th International Conference on Transparent Optical Networks (ICTON), Graz, Austria, 6–10 July 2014; pp. 1–4. [Google Scholar]
- Furdek, M.; Skorin-Kapov, N.; Wosinska, L. Attack-aware dedicated path protection in optical networks. J. Lightw. Technol. 2016, 34, 1050–1061. [Google Scholar] [CrossRef]
- Mukherjee, B. Network Adaptability from WMD Disruption and Cascading Failures; California Univ Davis: Fort Belvoir, VA, USA, 2016. [Google Scholar]
- Lamb, S.; Davis, P. Cenozoic climate change as a possible cause for the rise of the Andes. Nature 2003, 425, 792–797. [Google Scholar] [CrossRef] [PubMed]
- Emanuel, K.; Sundararajan, R.; Williams, J. Hurricanes and global warming: Results from downscaling IPCC AR4 simulations. Bull. Am. Meteorol. Soc. 2008, 89, 347–367. [Google Scholar] [CrossRef]
- Ferdousi, S.; Dikhiyik, F.; Habib, M.F.; Mukherjee, B. Disaster-aware data-center and content placement in cloud networks. In Proceedings of the 2013 IEEE International Conference on Advanced Networks and Telecommunications Systems (ANTS), Kattankulathur, India, 15–18 December 2018; pp. 1–3. [Google Scholar]
- Das, A.; Sen, A.; Qiao, C.; Ghani, N.; Mitton, N. A network planning and management tool for mitigating the impact of spatially correlated failures in infrastructure networks. In Proceedings of the 2016 12th International Conference on the Design of Reliable Communication Networks (DRCN), Paris, France, 15–17 March 2016; pp. 71–78. [Google Scholar]
- Le, Q.; Piarabutr, P.; Sawangving, N.; Mahadthai, P.; Wuttisittikulkij, L.; Vanichchanunt, P.; Saengudomlert, P. Optical network optimization tool with network survivability. Electron. Eng. Soc. Korea 2017, 1, 228–231. [Google Scholar]
- Matrood, Z.M.; George, L.E.; Mahmood, F.H. A simple gis based method for designing fiber-network. Int. J. Eng. Innov. Technol. 2014, 4, 49–57. [Google Scholar]
- Wang, X. Network recovery and augmentation under geographically correlated region failures. In Proceedings of the Global Telecommunications Conference (GLOBECOM 2011), Kathmandu, Nepal, 5–9 December 2011; pp. 1–5. [Google Scholar]
- Fay, D.; Haddadi, H.; Thomason, A.; Moore, A.W.; Mortier, R.; Jamakovic, A.; Uhlig, S.; Rio, M. Weighted spectral distribution for internet topology analysis: Theory and applications. IEEE/ACM Trans. Netw. 2010, 18, 164–176. [Google Scholar] [CrossRef]
- Long, X.; Tipper, D.; Gomes, T. Measuring the survivability of networks to geographic correlated failures. Opt. Switch. Netw. 2014, 14, 117–133. [Google Scholar] [CrossRef]
- Cheng, Y.; Sterbenz, J.P. Critical region identification and geodiverse routing protocol under massive challenges. In Proceedings of the 7th International Workshop on Reliable Networks Design and Modeling (RNDM), Munich, Germany, 5–7 October 2015; pp. 14–20. [Google Scholar]
- Iqbal, F.; Kuipers, F. On centrality-related disaster vulnerability of network regions. In Proceedings of the 9th International Workshop on Resilient Networks Design and Modeling (RNDM), Alghero, Italy, 4–6 September 2017; pp. 1–6. [Google Scholar]
- Gardner, M.T.; Beard, C. Evaluating geographic vulnerabilities in networks. In Proceedings of the 2011 IEEE International Workshop Technical Committee on Communications Quality and Reliability (CQR), Naples, FL, USA, 10–12 May 2011; pp. 1–6. [Google Scholar]
- Trajanovski, S.; Kuipers, F.A.; Ilić, A.; Crowcroft, J.; Van Mieghem, P. Finding critical regions and region-disjoint paths in a network. IEEE/ACM Trans. Netw. 2015, 23, 908–921. [Google Scholar] [CrossRef]
- Saito, H. Analysis of geometric disaster evaluation model for physical networks. IEEE/ACM Trans. Netw. 2015, 23, 1777–1789. [Google Scholar] [CrossRef]
- Saito, H. Spatial design of physical network robust against earthquakes. J. Lightw. Technol. 2015, 33, 443–458. [Google Scholar] [CrossRef]
- Tran, P.N.; Saito, H. Enhancing physical network robustness against earthquake disasters with additional links. J. Lightw. Technol. 2016, 34, 5226–5238. [Google Scholar] [CrossRef]
- Iqbal, F.; Kuipers, F. Spatiotemporal risk-averse routing. In Proceedings of the IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), San Francisco, CA, USA, 10–14 April 2016; pp. 395–400. [Google Scholar]
- Iqbal, F.; Trajanovski, S.; Kuipers, F. Detection of spatially-close fiber segments in optical networks. In Proceedings of the 12th International Conference on the Design of Reliable Communication Networks (DRCN), Paris, France, 15–17 March 2016; pp. 95–102. [Google Scholar]
- Ashraf, M.W.; Idrus, S.M.; Iqbal, F. Maximally spatial-disjoint lightpaths. In Proceedings of the International Conference on Electrical, Electronics, Communication and Control Engineering (ICEECC), Kuala Lumpur, Malaysia, 5–6 December 2017; UTM: Kuala Lumpur, Malaysia, 2017. [Google Scholar]
- Awaji, Y.; Furukawa, H.; Xu, S.; Shiraiwa, M.; Wada, N.; Tsuritani, T. Resilient optical network technologies for catastrophic disasters. J. Opt. Commun. Netw. 2017, 9, A280–A289. [Google Scholar] [CrossRef]
- Al Mamoori, S.; Jaekel, A.; Bandyopadhyay, S. Disaster-aware wdm network design for data centres. In Proceedings of the 18th International Conference on Distributed Computing and Networking, Hyderabad, India, 5–7 January 2017; p. 38. [Google Scholar]
- Cheng, Y.; Li, J.; Sterbenz, J.P. Path geo-diversification: Design and analysis. In Proceedings of the 2013 5th International Congress on Ultra Modern Telecommunications and Control Systems and Workshops (ICUMT), Almaty, Kazakhstan, 10–13 September 2013; pp. 46–53. [Google Scholar]
- Cheng, Y.; Gardner, M.T.; Li, J.; May, R.; Medhi, D.; Sterbenz, J.P. Analysing geopath diversity and improving routing performance in optical networks. Comput. Netw. 2015, 82, 50–67. [Google Scholar] [CrossRef]
- De Sousa, A.; Santos, D.; Monteiro, P. Determination of the minimum cost pair of d-geodiverse paths. In Proceedings of the 13th International Conference Design of Reliable Communication Networks, Munich, Germany, 8–10 March 2017; pp. 1–8. [Google Scholar]
- Wang, J.; Bigham, J.; Phillips, C. A geographical proximity aware multi-path routing mechanism for resilient networking. IEEE Commun. Lett. 2017, 21, 1533–1536. [Google Scholar] [CrossRef]
- Jacobson, V. Congestion avoidance and control. ACM SIGCOMM Comput. Commun. Rev. 1988, 18, 314–329. [Google Scholar] [CrossRef]
- Chiu, D.; Jain, R. Analysis of the increase and decrease algorithms for congestion avoidance in computer networks. Comput. Netw. ISDN Syst. 1989, 17, 1–14. [Google Scholar] [CrossRef]
- Floyd, S.; Jacobson, V. Random early detection gateways for congestion avoidance. IEEE/ACM Trans. Netw. 1993, 1, 397–413. [Google Scholar] [CrossRef]
- Brakmo, L.S.; O’Malley, S.W.; Peterson, L.L. TCP Vegas: New Techniques for Congestion Detection and Avoidance; ACM: London, UK, 1994. [Google Scholar]
- Mathis, M.; Mahdavi, J. Forward acknowledgement: Refining TCP congestion control. ACM SIGCOMM Comput. Commun. Rev. 1996, 26, 281–291. [Google Scholar] [CrossRef]
- Sisalem, D.; Schulzrinne, H. Congestion control in TCP: Performance of binary congestion notification enhanced TCP compared to Reno and Tahoe TCP. In Proceedings of the 1996 International Conference on Network Protocols, Columbus, OH, USA, 29 October–1 November 1996; pp. 268–275. [Google Scholar]
- Stevens, W.; Paxson, V.; Allman, M. TCP Congestion Control; RFC 2581; IETF: Fremont, CA, USA, 1999. [Google Scholar]
- Floyd, S.; Handley, M.; Padhye, J.; Widmer, J. Equation-based congestion control for unicast applications. ACM SIGCOMM Comput. Commun. Rev. 2000, 30, 43–56. [Google Scholar] [CrossRef]
- Jin, C.; Wei, D.X.; Steven, H. Low FAST TCP: Motivation, Architecture, Algorithms, Performance. In Proceedings of the INFOCOM, Hong Kong, China, 7–11 March 2004. [Google Scholar]
- Tang, A.; Wang, J.; Low, S.H. Understanding choke: Throughput and spatial characteristics. IEEE/ACM Trans. Netw. (ToN) 2004, 12, 694–707. [Google Scholar] [CrossRef]
- Zulkifli, N.; Idrus, S.M.; Supa’at, A.S.M.; Farabi, M. Network performance improvement of all-optical networks through an algorithmic based dispersion management technique. J. Netw. Syst. Manag. 2012, 20, 401–416. [Google Scholar] [CrossRef]
- Wu, J.; Zhang, J.; von Bochmann, G.; Savoie, M. Forward-looking wdm network reconfiguration with per-link congestion control. J. Netw. Syst. Manag. 2012, 20, 6–33. [Google Scholar] [CrossRef]
- Wason, A.; Kaler, R. Blocking in wavelength-routed all-optical WDM networks. Optik 2010, 121, 903–907. [Google Scholar] [CrossRef]
- Wason, A.; Kaler, R. Blocking probability calculation in wavelength-routed all-optical networks. Optik 2011, 122, 1638–1641. [Google Scholar] [CrossRef]
- Wason, A.; Kaler, R. Blocking probability optimization in wavelength routed optical wdm networks. Optik 2013, 124, 3131–3133. [Google Scholar] [CrossRef]
- Singal, A.; Kaler, R. Blocking probability of algorithms for different wavelength assignment in optical ring network. Optik 2013, 124, 147–151. [Google Scholar] [CrossRef]
- Sohal, E.S.K.; Kaur, E.S. Blocking probability of dijkstra shortest and least congestion routing algorithm in wavelength-routed WDM network. Int. J. Recent Innov. Trends Comput. Commun. 2014, 2, 1374–1379. [Google Scholar]
- Zanjani, S.B.; Rahbar, A.G. Least-congested distributed lightpath allocation. In Proceedings of the 2010 5th International Symposium on Telecommunications (IST), Tehran, Iran, 4-6 December 2010; pp. 151–156. [Google Scholar]
- Stewart, M.F.; Kannan, R.; Dvir, A.; Krishnamachari, B. Caspar: Congestion avoidance shortest path routing for delay tolerant networks. In Proceedings of the IEEE 2016 International Conference on Computing, Networking and Communications (ICNC), Kauai, HI, USA, 15–18 February 2016; pp. 1–5. [Google Scholar]
- Hu, R.Q.; Hu, W.; Jin, M.; Qian, Y. Wavelength retuning without service interruption in an all-optical survivable network. Int. J. Commun. Syst. 2009, 22, 719–738. [Google Scholar] [CrossRef]
- Hao, F.; Jansen, A.; Kodialam, M.; Lakshman, T.V. Path Computation for IP Network Optimization. Available online: https://insight.nokia.com/path-computation-ip-network-optimization (accessed on 25 November 2017).
- Nasralla, Z.H.; El-Gorashi, T.E.; Musa, M.O.; Elmirghani, J.M. Routing post-disaster traffic floods in optical core networks. In Proceedings of the 2016 International Conference on Optical Network Design and Modeling (ONDM), Cartagena, Spain, 9–12 May 2016; pp. 1–5. [Google Scholar]
- Thyagaturu, A.S.; Mercian, A.; McGarry, M.P.; Reisslein, M.; Kellerer, W. Software defined optical networks (SDONS): A comprehensive survey. IEEE Commun. Surv. Tutor. 2016, 18, 2738–2786. [Google Scholar] [CrossRef]
- Fraustino, J.D.; Liu, B.; Jin, Y. Social Media Use during Disasters: A Review of the Knowledge Base and Gaps; National Consortium for the Study of Terrorism and Responses to Terrorism: College Park, MD, USA, 2012. [Google Scholar]
- Ungerleider, N. Why Your Phone Doesn’t Work during Disasters—And How to Fix It; Fast Company: Vineland, NJ, USA, 2013; Volume 17. [Google Scholar]
- Baklan, P.; Yamori, K.; Tanaka, Y. Measure of user behaviour before and during disaster congestion. In Proceedings of the 2014 16th International Conference on Advanced Communication Technology (ICACT), Pyeongchang, Korea, 16–19 February 2014; pp. 135–140. [Google Scholar]
- Fukuda, K.; Aoki, M.; Abe, S.; Ji, Y.; Koibuchi, M.; Nakamura, M.; Yamada, S.; Urushidani, S. Impact of tohoku earthquake on R&E network in Japan. In Proceedings of the Special Workshop on Internet and Disasters, Tokyo, Japan, 6–9 December 2011; p. 1. [Google Scholar]


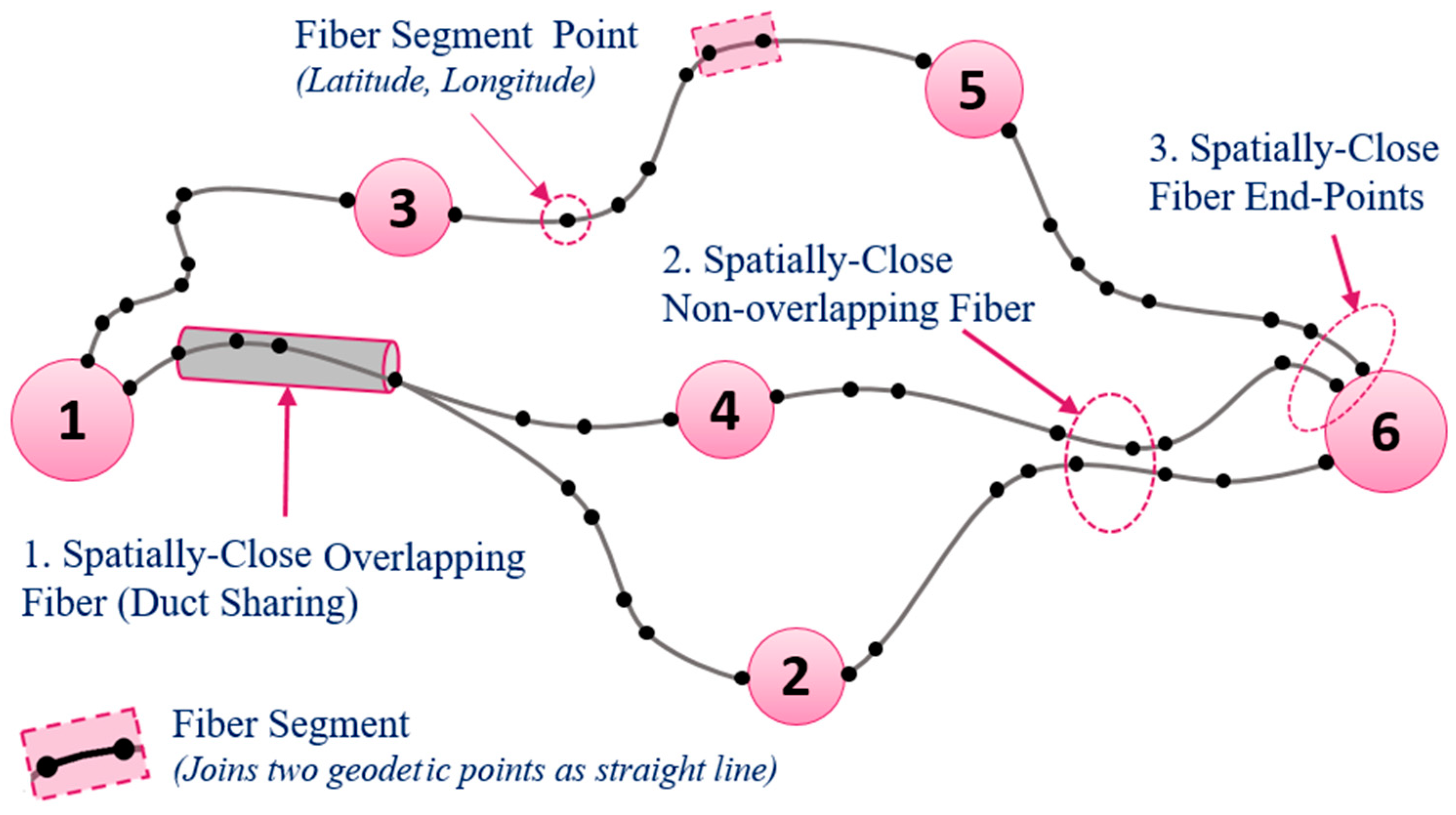
| Ref | Techniques/Formulation | Objectives | Assessments/Limitations |
|---|---|---|---|
| [76] | Protection from WMD attacks (a technical report). | Combating the terrorist attacks like WDM to assess the impacts of catastrophic failures on critical infrastructures. | Characterizing the impact of WMD attacks in WDM networks. Re-provisioning algorithms, multi-path routing, data replication, WMD-risk-aware virtual-network mapping & re-mapping and service recovery. Addresses the network preparedness for upcoming attacks. |
| [83] | Algorithms for network recovery and augmentation under geographically correlated region failures. | Effective connection recovery in the event of regional failures. | Addressed two NP-hard problems and proposed the integer programming formulations as their solutions. Also proposed corresponding greedy algorithms to approximate the optimal solutions. |
| [85] | Network metrics: weighted spectrum (WS) and network criticality (NC) | To enumerate the network survivability against geographically correlated failures. | Assessed the network survivability in the event of geographically correlated failures. Solved an optimization problem to determine the most vulnerable geographic nodes and cuts in the networks. |
| [86] | Critical Region Identification Model, GeoDivRP | Finding the most vulnerable regions at fiber-level and enhancing the performance of GeoDivRP. | Considered the regionally correlated failures and attacks and proposed a model to identify the critical region. The effectiveness of the model is evaluated using both weighted and unweighted topologies. The obtained results are used to enhance the performance of routing using GeoDivRP. |
| [87] | Disaster-affected Region Identification Model Metrics for evaluation of model predicted areas (1) Region Betweenness-centrality (2) Risk Impact | Characterizing the heterogeneous areas affected by different types of disasters. Introduced two metrics RBC to represent the region importance in terms of all-node pair shortest paths and Risk Impact to enumerate the threat posed by disasters within a region. | Proposed a model to identify disaster-affected areas with different shapes and sizes using Poisson distribution, and analyzed the effect of link existence and disaster area size on these metrics. |
| [89] | Polynomial-time algorithm to find the critical region Heuristic to find the region disjoint paths | Finding critical region and region disjoint paths | Determined the vulnerability of a network to the failure of a certain region embedded in a plane. The methodology was applicable to different geometries of the critical region. The critical region may include disconnected pairs of nodes, average shortest path length etc. |
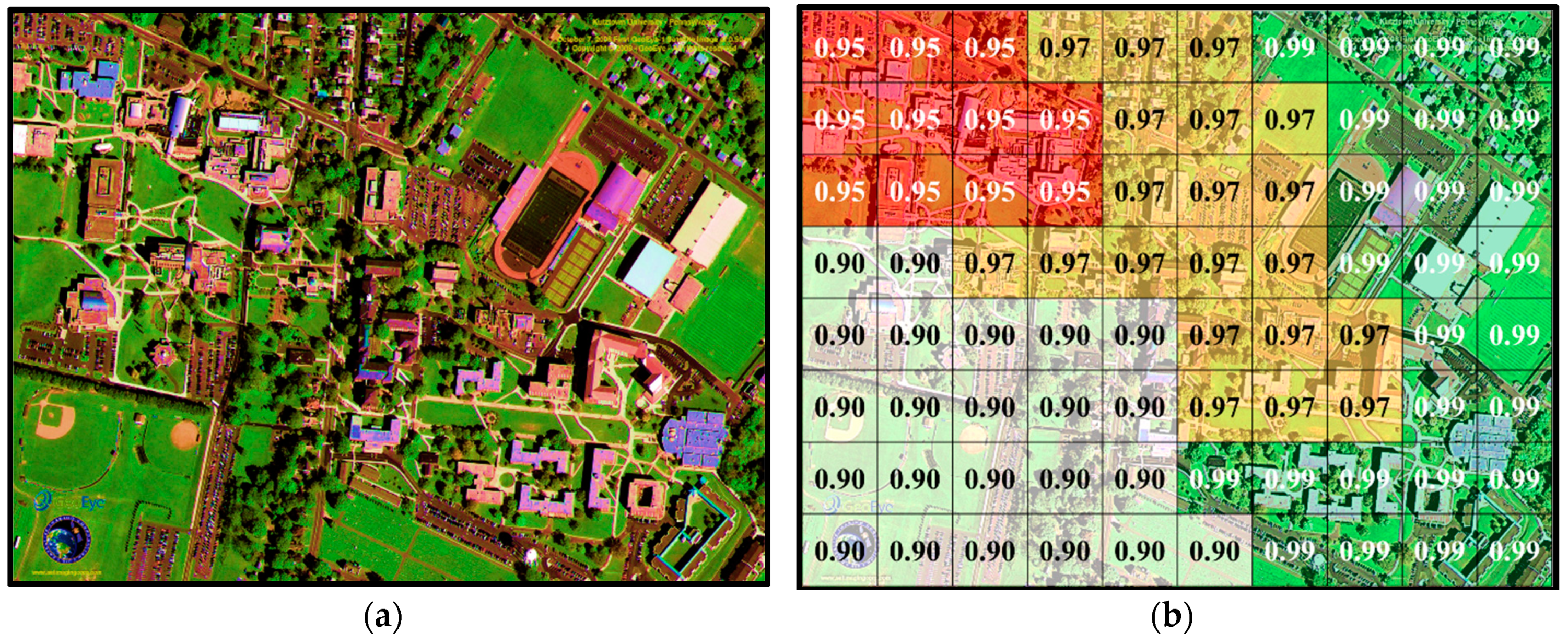
| [93] | Risk profiling for spatiotemporal characteristics of disasters (link availability values) | Finding risk profile of disasters at different areas of the network at different times. | Preventative measures can be taken if risk profile of spatiotemporal disaster impact is predicted. The most risk-averse path is obtained via the shortest path algorithm using as weights the –log of the link availabilities. |
| [94] | Polynomial-time algorithms Implementing kD-Tree and R-Tree Data Structures | Detection of spatially close fibers and spatially close risk groups. | Considered the geography of links to detect spatially close fibers. Minimum separation distance relies on α which represent the radius of construction-level and large-scale failures. Identified the spatially close risk groups using the minimum number of DRG. |
| [97] | ILP Formulation | A robust scheme that minimizes the network resources (wavelength links) needed to handle the requests for communication in data center networks. | Prioritized the minimization of resource utilization and the number of disasters. However, resource utilization increases with the increase in a number of disasters as disasters reduces the capacity. |
| [99] | Path Geo-Diversification cTGGD | Impact of Path Geo-Diversification on the routing performance | Performance of the proposed mechanism compared with that of when the network was subject to area-based challenge. cTGGD used to distinguish the GeoPath diversity of different network topologies. |
| [100] | ILP | Path geo-diversification where a demand between two network nodes supported by a pair of geographically separated paths of a minimum distance. | ILP is complex in computation and includes all unnecessary path computations which are time-consuming. Preferably, proposed heuristic algorithms in the literature may provide acceptable solutions of the problem. |
| [101] | Brute force approach and enhanced K-shortest path algorithm | Geographic aware route selection algorithm to find alternative paths with appropriate geographical separation referred to as the proximity factor. | Work based on the grid-based network and do not consider any real network. Further, PF based on node-to-node separation whereas fiber links should also be considered for alternate/disjoint path computation. |
| Ref | Techniques | Objectives | Limitations |
|---|---|---|---|
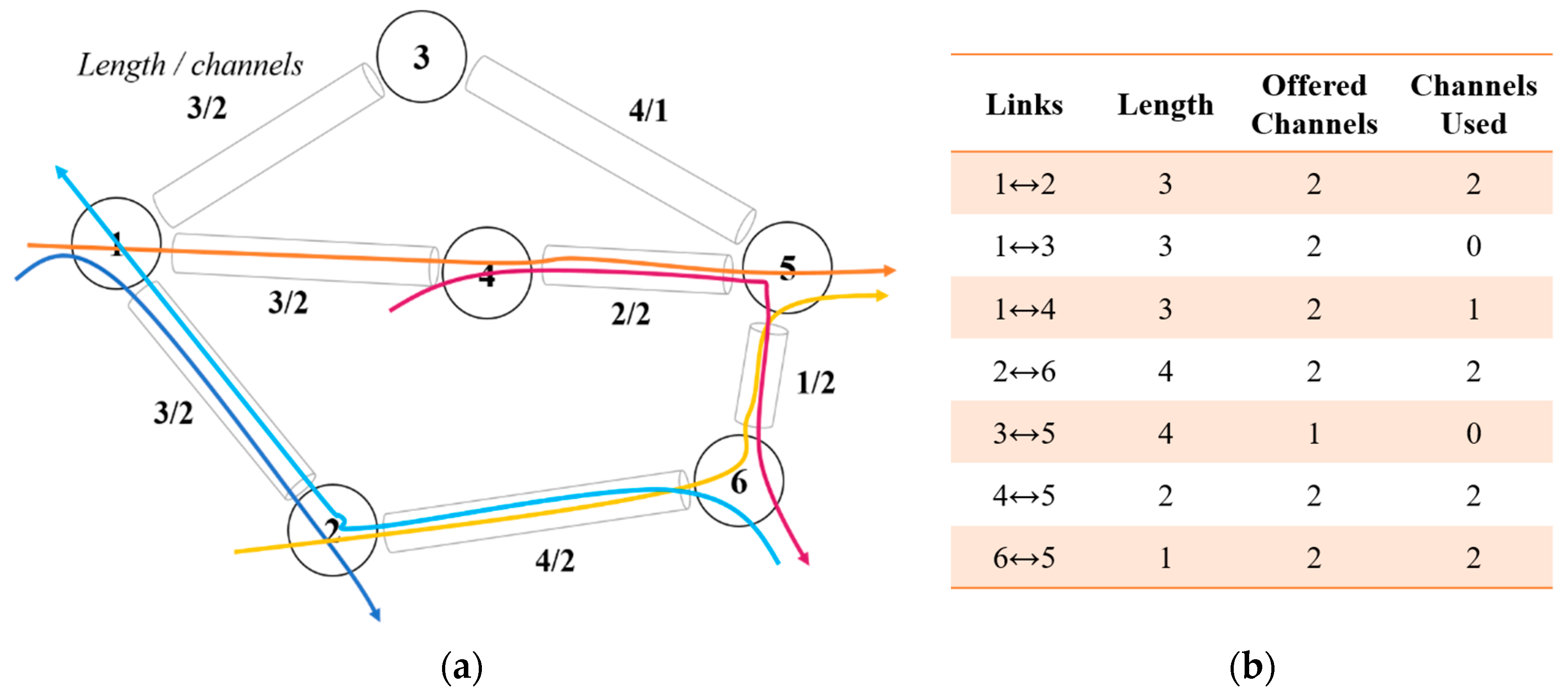
| [30] | Congestion control strategy in WDM networks | Dynamic strategy symmetrically distributes the traffic on the links according to the channels available on the link. | Criteria for most and least used links not defined before distribution of data that may be based on a number of connection requests, connection establishment strategy or path lengths. |
| [117] | Analysis of blocking performance in Ring optical network | Computing and analyzing the node-by-node blocking performance in the ring optical network using wavelength conversion algorithms | Whole work is based on the 8-node ring network. Results showed that blocking probability decreases with the increase of a number of wavelengths. |
| [118] | Dijkstra Algorithm and Least Congested Path Routing Algorithm | Studied the performance of these algorithms in terms of blocking probability and path lengths | Only focused on the routing algorithm of the RWA problem. |
| [119] | LC-DLA routing algorithm | Resource allocation on the decision of network congestion in large-scale networks taking a huge number of connection requests and heavy traffic load in the account. | Proposed LC-DLA provisions least congested lightpaths as compared to other DLA and shortest path algorithms. Existing algorithms may introduce the traffic jam/bottlenecks while accumulating congestion and hence upsurge the blocking probability. It is observed that LC-DLA tries to balance the network congestion and resultantly avoid the traffic jams. |
| [120] | CASPaR Algorithm | Pursued to enhance the PDP and reduced the latency by selecting the shortest path. | CASPaR shows improved performance than that of other protocols but in terms of packet delivery only. |
| [122] | Centralized PCE with STAR (Self-Tuned Adaptive Routing) algorithm | Efficient path computation avoiding underutilization of capacity over links and congestion. | Introduced a novel centralized PCE with STAR algorithm that discovers the paths considering available link capacity and load balancing. Separate path computing and path signaling functions which give operators more control over their network. |
| [123] | MILP Model to handle capacity exhaustion problem | Investigate post-disaster static traffic floods in several scenarios to reduce traffic blocking. | The arrival of connection requests is random so network traffic and lightpath establishment are also dynamic in real-life networks. Should be investigated with dynamic traffic floods. |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ashraf, M.W.; Idrus, S.M.; Iqbal, F.; Butt, R.A.; Faheem, M. Disaster-Resilient Optical Network Survivability: A Comprehensive Survey. Photonics 2018, 5, 35. https://doi.org/10.3390/photonics5040035
Ashraf MW, Idrus SM, Iqbal F, Butt RA, Faheem M. Disaster-Resilient Optical Network Survivability: A Comprehensive Survey. Photonics. 2018; 5(4):35. https://doi.org/10.3390/photonics5040035
Chicago/Turabian StyleAshraf, Muhammad Waqar, Sevia M. Idrus, Farabi Iqbal, Rizwan Aslam Butt, and Muhammad Faheem. 2018. "Disaster-Resilient Optical Network Survivability: A Comprehensive Survey" Photonics 5, no. 4: 35. https://doi.org/10.3390/photonics5040035
APA StyleAshraf, M. W., Idrus, S. M., Iqbal, F., Butt, R. A., & Faheem, M. (2018). Disaster-Resilient Optical Network Survivability: A Comprehensive Survey. Photonics, 5(4), 35. https://doi.org/10.3390/photonics5040035






