Research on Networking Protocols for Large-Scale Mobile Ultraviolet Communication Networks
Abstract
1. Introduction
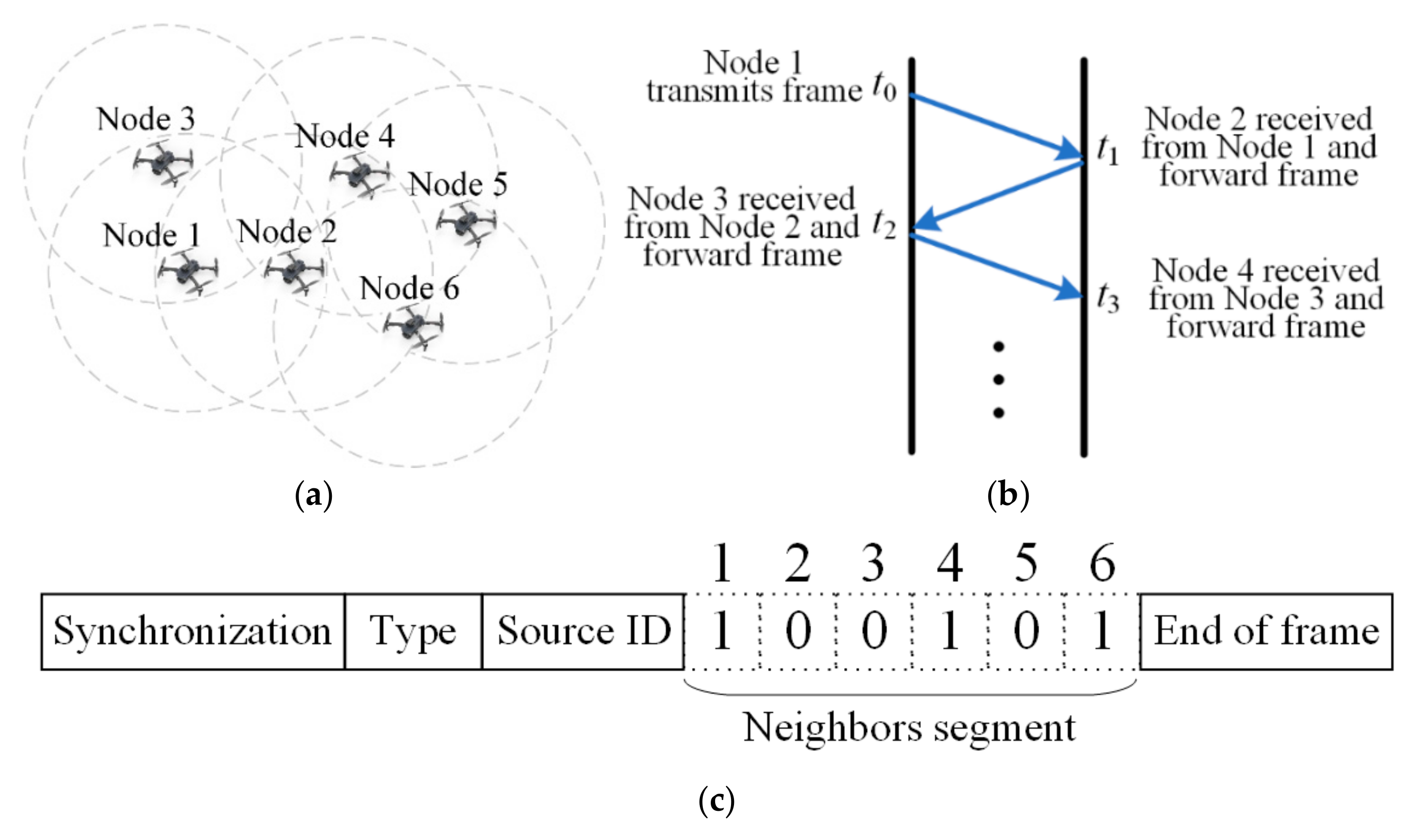
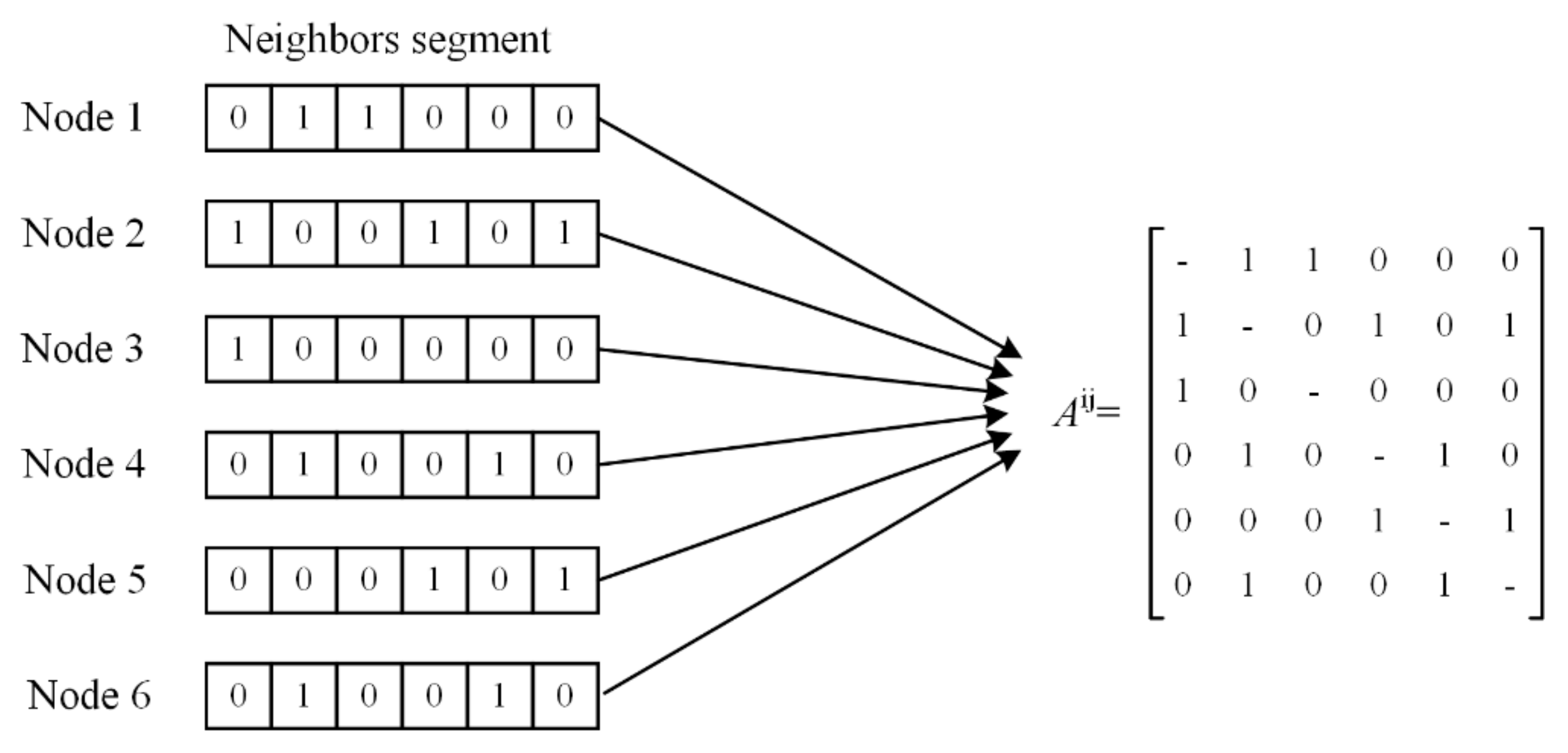
- In view of the bandwidth limitation of UV communication, a novel neighbor discovery algorithm is designed based on a lossless competition mechanism. The proposed neighbor discovery algorithm can generate a network connection matrix with extremely low control overhead, which covers the connection relationships of all nodes in the network.
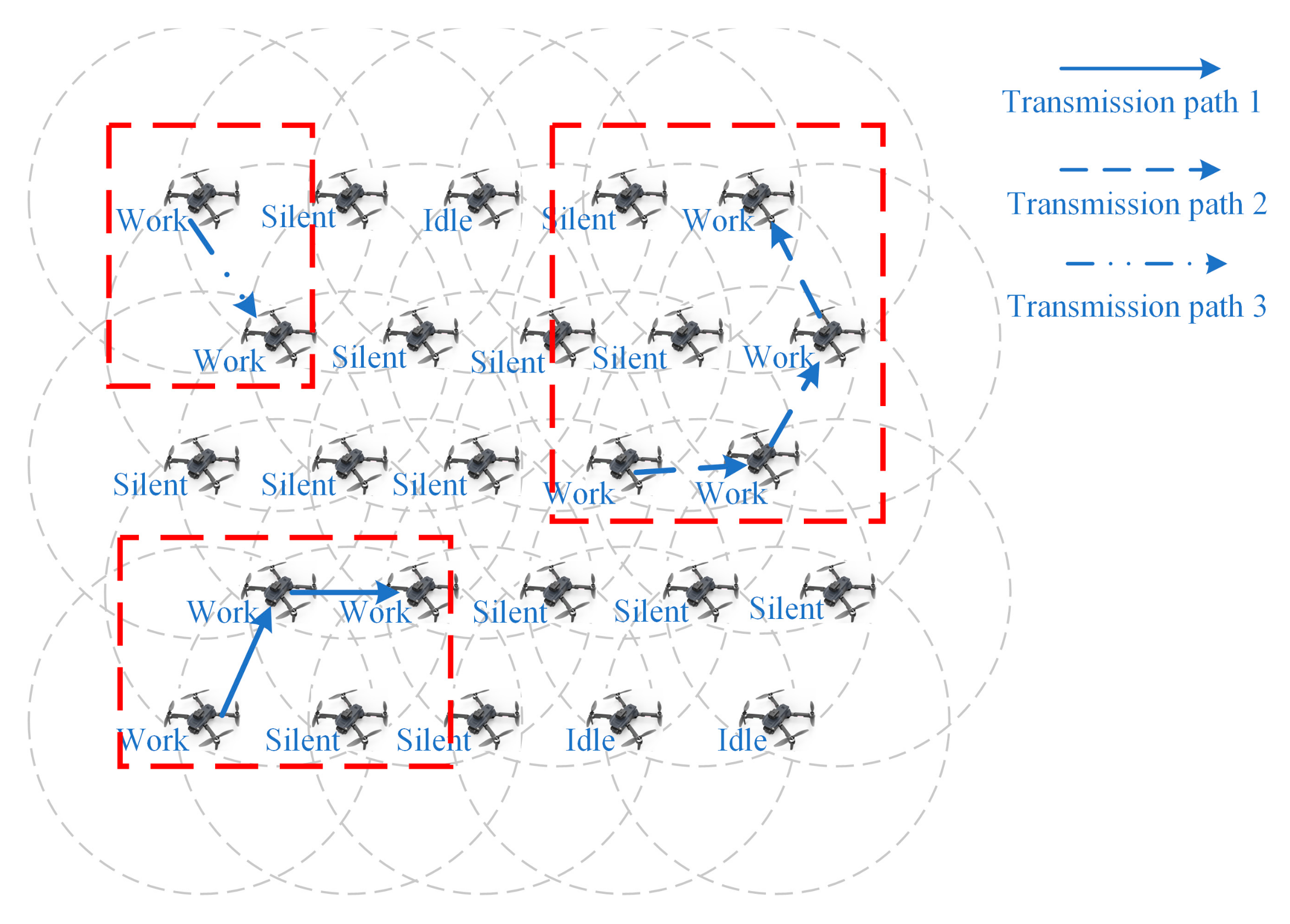
- A channel access mechanism of “competition-first-then-transmission” is designed. Based on the network connection matrix, the protocol establishes multiple transmission paths synchronously through multi-round competition, and prevents interference between adjacent transmission paths by setting interference isolation nodes, so as to realize spatial division multiplexing and further alleviate the problem of low throughput in ultraviolet communication networks.
- To address the issue of random changes in network topology in mobile networks, the proposed protocol, based on a neighbor discovery algorithm with low control overhead, can effectively reduce the adverse impact of frequent network topology changes on network performance by periodically updating the connection matrix.
2. LSM-UVCN
2.1. Neighbor Discovery Algorithm
2.2. Networking Protocol
2.3. Node State Transition
- The node is in the Idle state.
- The node has data to transmit.
- There is an available transmission path between the node and the destination node.
3. Network Performance Analysis
3.1. Basic Parameters
3.2. Network Performance
- As nodes move, the communicable links in the connection matrix may be disrupted, causing nodes to establish incorrect transmission paths.
- The non-interfering transmission paths established through multiple rounds of competition based on the connection matrix may cross due to node mobility. Interference may occur during the data transmission process, resulting in transmission failures.
- During the neighbor discovery process, nodes may experience transmission failures of neighbor discovery control frames due to errors such as bit errors. This can lead to the establishment of incorrect connection matrices in the nodes, preventing the nodes from functioning properly during subsequent data transmission cycles.
3.2.1. Path Break
3.2.2. Inter-Path Interference
3.2.3. Errors in Neighbor Discovery
3.2.4. Bit Errors
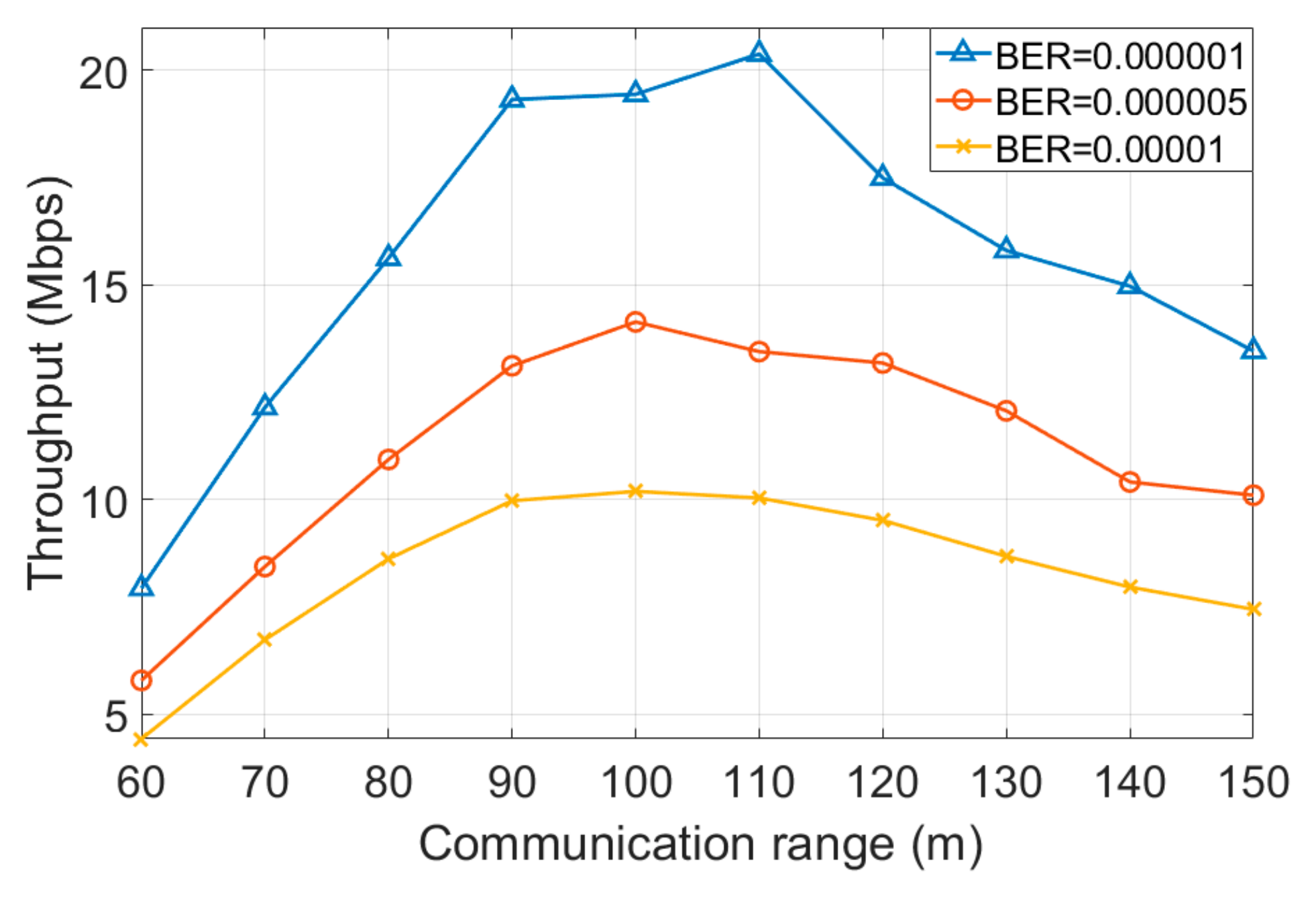
3.2.5. Throughput and Data Loss Rate
4. Simulations
4.1. Mobility Model
4.2. Basic Parameters
4.3. Channel Conditions
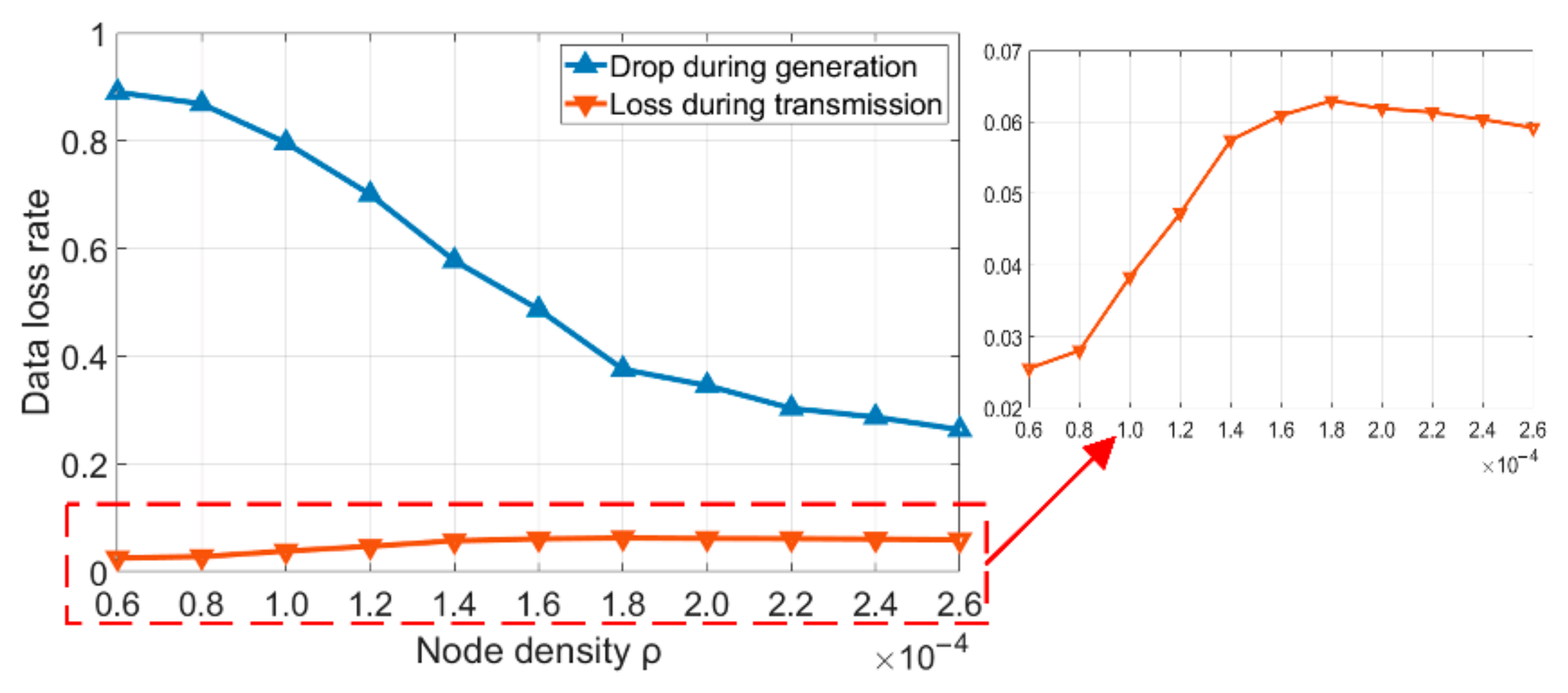
4.4. Node Density
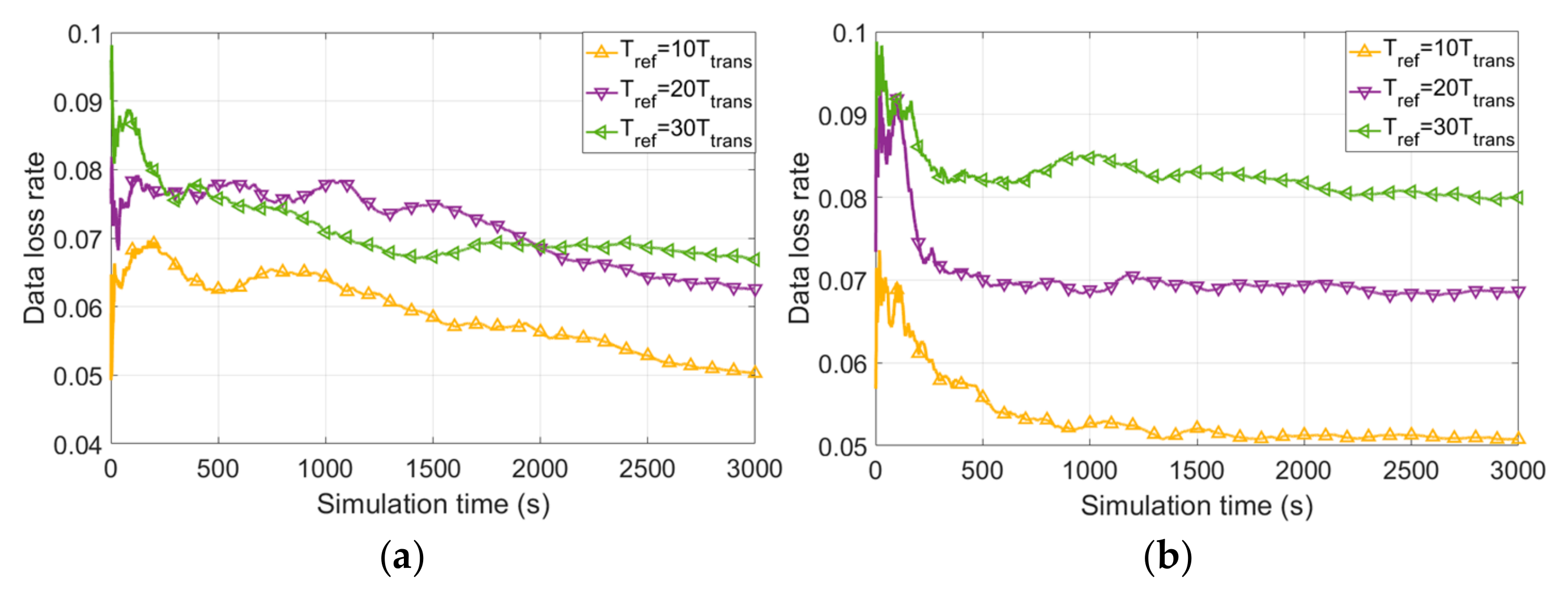
4.5. Node Speed and Tref
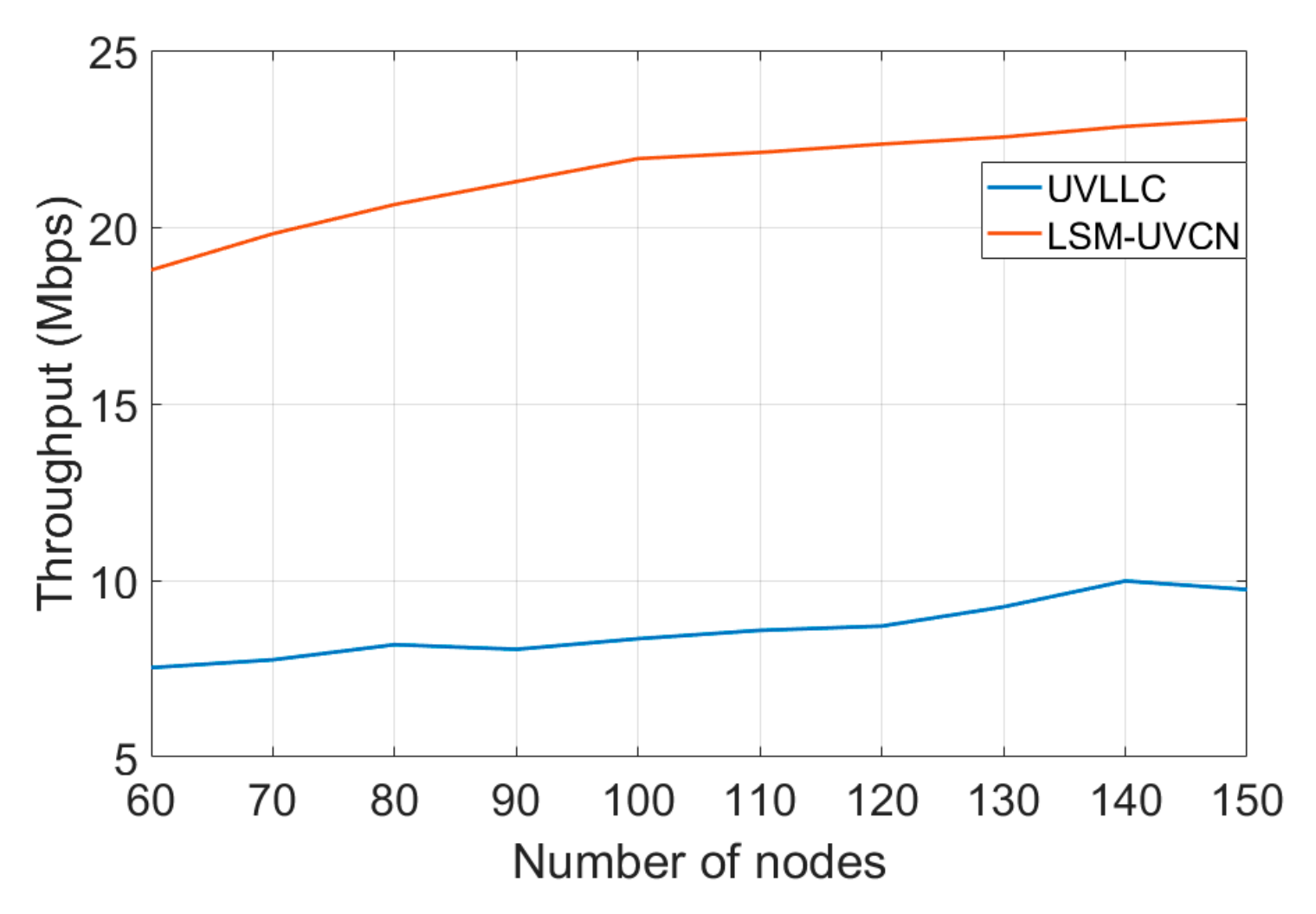
4.6. Protocol Performance Comparison
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Luo, P.; Zhang, M.; Liu, Y.; Han, D. A moving average filter based method of performance improvement for ultraviolet communication system. In Proceedings of the International Symposium on Communication Systems, Poznan, Poland, 18–20 July 2012; IEEE: New York, NY, USA, 2012. [Google Scholar] [CrossRef]
- Zhang, M.; Luo, P.; Guo, X.; Zhang, X.; Han, D.; Li, Q. Spread spectrum-based ultraviolet communication with experiments. Chin. Opt. Lett. 2014, 12, 100602. [Google Scholar] [CrossRef]
- Han, D.; Gu, Y.; Zhang, M. Experimental study of an optimized PSP-OSTBC scheme with m-PPM in ultraviolet scattering channel for optical MIMO system. Appl. Opt. 2017, 56, 6564. [Google Scholar] [CrossRef] [PubMed]
- Deng, Y.; Wang, Y.; Zhang, Y.; Du, A.; Liu, J. The realization of a wide-angle voice transmission non-line-of-sight ultraviolet communication system. J. Semicond. 2021, 42, 47–52. [Google Scholar] [CrossRef]
- Du, A.; Wang, Y.; Zhang, J.; Zhao, Y.; Sun, N.; Liu, J. Characteristic Study of Non-Line-of-Sight Scattering Ultraviolet Communication System at Small Elevation Angle. Photonics 2022, 9, 363. [Google Scholar] [CrossRef]
- Chen, X.; Han, D.; Zhang, M.; Ren, T.; Wan, T. Experimental research on image transmission over one hundred meters with limited bandwidth in a semantic ultraviolet communication system. In Proceedings of the 2024 14th International Symposium on Communication Systems, Networks and Digital Signal Processing (CSNDSP), Rome, Italy, 17–19 July 2024. [Google Scholar] [CrossRef]
- Du, A.; Wang, Y.; Zhang, J.; Zou, C.; Xiang, Z.; Liu, J.; Xue, C. Implementation of large angle low error non-line-of-sight ultraviolet communication system. Opt. Commun. 2024, 558, 130227. [Google Scholar] [CrossRef]
- Zhang, X.; Zhao, S.; Li, Y.; Deng, B.; Cheng, Z. A subsection Operation Back-off Algorithm of MAC Layer in Airborne Ultraviolet Communication Network. Semicond. Optoelectron. 2015, 36, 5. [Google Scholar] [CrossRef]
- Zhang, X.; Zhao, S.; Li, Y.; Deng, B.; Cheng, Z. Multi-channel directional media access control protocol for air borne ultraviolet communication based on space division multiplexing. Laser Technol. 2016, 40, 5. [Google Scholar] [CrossRef]
- Li, J.; Liu, X.; Wang, H.; Wu, X. Improved Ultraviolet Communication Time Division Multiplexing Network Method. Chin. J. Lasers 2014, 41, 1105003. [Google Scholar] [CrossRef]
- Li, C.; Xu, Z.; Wang, J.; Zhao, J.; Wang, L.; Wang, Y.; Li, J. Enhanced collaborative networking protocol based on clustering mechanism for UV networks. Opt. Commun. 2024, 560, 130464. [Google Scholar] [CrossRef]
- Yang, J.; Luo, J.L.; Chen, X.Y.; Cheng, F. UVAd-TDMA: An MAC Protocol for the solar blind ultraviolet Ad-Hoc network. Appl. Mech. Mater. 2014, 543–547, 2854–2857. [Google Scholar] [CrossRef]
- Pan, Y.; Zhang, Y.; Long, F.; Li, P.; Shi, H.; Shi, J. Beacon-enabled TDMA Ultraviolet Communication Network System Design and Realization. In Proceedings of the 2024 14th International Symposium on Communication Systems, Networks and Digital Signal Processing (CSNDSP), Rome, Italy, 23 August 2024; IEEE: New York, NY, USA, 2024. [Google Scholar] [CrossRef]
- Yang, J.; Li, X.Y.; Zhao, F.; Chen, X.Y.; Shao, P. An Algorithm of Channel Sharing for the Solar Blind NLOS Ultraviolet Ad-Hoc Network Based on the Hybrid Genetic Algorithm. Appl. Mech. Mater. 2014, 543–547, 2850–2853. [Google Scholar] [CrossRef]
- Li, C.; Li, J.; Xu, Z.; Wang, J. Research on the lossless contention MAC protocol and the performance of an ultraviolet communication network. Opt. Express 2021, 29, 31952–31962. [Google Scholar] [CrossRef] [PubMed]
- Li, C.; Li, J.; Wang, J.; Zhao, J.; Gao, G.; Wang, K.; Su, Y.; Xu, Z. QoS based enhanced lossless contention MAC protocol for ultraviolet network. Opt. Express 2022, 30, 31439–31455. [Google Scholar] [CrossRef] [PubMed]
- Li, C.; Xu, Z.; Li, J.; Wang, J.; Lin, Y.; Zhao, J.; Qi, A.; Shen, H. Performance of the UV Multi-node Network Under the Lossless Contention MAC Protocol. IEEE Photonics J. 2022, 14, 3156550. [Google Scholar] [CrossRef]
- Wang, L.; Xu, Z.; Wang, J.; Zhao, J.; Wang, Y.; Li, J. Lossless contention ultraviolet MAC protocol based on dynamic bandwidth allocation. J. Opt. Commun. Netw. 2024, 16, 941–955. [Google Scholar] [CrossRef]
- Wang, L.; Xu, Z.; Wang, J.; Zhao, J.; Wang, Y.; Ma, X.; Li, J. Ultraviolet collaborative networking method based on a novel neighbor discovery algorithm. Opt. Commun. 2024, 568, 12. [Google Scholar] [CrossRef]
- Wang, L.; Xu, Z.; Wang, J.; Li, C.; Hu, J.; Su, Y.; Li, J. MAC protocol for implementing SDM in large-scale ultraviolet networks. Opt. Express 2025, 33, 21584–21604. [Google Scholar] [CrossRef] [PubMed]





| Parameter | Meaning |
|---|---|
| n | Total number of nodes |
| L | Side length of the node distribution area, and the area of the distribution area is L × L |
| ρ | Node density, ρ = n/L2 |
| A | Maximum communication distance of nodes |
| BER | Bit error rate |
| Tclk | The time of each clock cycle |
| Parameter | Value | Meaning |
|---|---|---|
| Communication coverage | 100 m | The maximum communication distance from point to point |
| Tdata | 25 ms | The time of each data transmission time slot |
| Link rate | 10 Mbps | The maximum communication rate from point to point |
| Simulation time | 3000 s | The duration of the simulation |
| BER | 10−6 | Bit error rate |
| n | 100 | Number of nodes |
| A | - | Area of the distribution region |
| ρ | - | Node density, ρ = n/A |
| λ | - | At each node, the arrival of data follows a Poisson distribution with intensity λ. |
| Ttrans | - | The time required for a complete transmission cycle, Ttrans ≈ 5 ms |
| Tref | - | Network connection matrix update period |
| v | - | The moving speed of nodes, in meters per second (mps) |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, L.; Xu, Z.; Wang, J.; Zhao, J.; Su, Y.; Li, C.; Li, J. Research on Networking Protocols for Large-Scale Mobile Ultraviolet Communication Networks. Photonics 2025, 12, 710. https://doi.org/10.3390/photonics12070710
Wang L, Xu Z, Wang J, Zhao J, Su Y, Li C, Li J. Research on Networking Protocols for Large-Scale Mobile Ultraviolet Communication Networks. Photonics. 2025; 12(7):710. https://doi.org/10.3390/photonics12070710
Chicago/Turabian StyleWang, Leitao, Zhiyong Xu, Jingyuan Wang, Jiyong Zhao, Yang Su, Cheng Li, and Jianhua Li. 2025. "Research on Networking Protocols for Large-Scale Mobile Ultraviolet Communication Networks" Photonics 12, no. 7: 710. https://doi.org/10.3390/photonics12070710
APA StyleWang, L., Xu, Z., Wang, J., Zhao, J., Su, Y., Li, C., & Li, J. (2025). Research on Networking Protocols for Large-Scale Mobile Ultraviolet Communication Networks. Photonics, 12(7), 710. https://doi.org/10.3390/photonics12070710





