1. Introduction
Due to the expensive nature of fiber optics deployment and the limited spectrum resources in RF systems, FSO communication has emerged as an optimal technology for data transmission. It offers significant advantages such as high capacity, high speed, wide bandwidth, and adaptable deployment, making it highly promising for future development [
1,
2,
3,
4,
5]. FSO communication finds extensive applications in optical wireless communication, underwater communication, aviation platforms, high-altitude-to-ground communication, and various other fields [
6,
7,
8,
9,
10]. In aviation platforms and high-altitude ground communication, FSO systems can provide flexible and reliable communication links, especially in scenarios that require rapid response, demonstrating unique advantages. FSO communications require the atmosphere as the transmission channel, and atmospheric turbulence is the key bottleneck that constrains performance. Atmospheric turbulence arises from random fluctuations in localized temperature, pressure, and wind speed in the atmosphere. These fluctuations lead to inhomogeneous refractive index of the air. Inhomogeneous refractive index of the air, in turn, causes a series of problems in the optical signal. These problems can seriously degrade the stability of communications. To further enhance the performance of FSO communication systems, researchers have investigated various advanced technologies. For instance, adaptive optics technology is employed to mitigate beam disturbances caused by atmospheric turbulence, thereby enhancing the stability of communication links and improving the quality of data transmission [
11,
12]. Furthermore, leveraging multiple-input multiple-output technology significantly enhances the transmission capacity and immunity to interference in FSO systems [
13]. In the realm of relay transmission technology, researchers have proposed various relay schemes aimed at significantly improving communication distance and system reliability through strategic design of relay node positions and functions [
14,
15].
High-altitude platforms encompass a diverse array of application scenarios, such as satellite communications, airborne Internet nodes, and emergency communications [
16,
17]. The presence of atmospheric turbulence can cause signal attenuation and fluctuations, significantly affecting communication quality. By establishing precise channel models, researchers can gain better insights into and effectively address these challenges. Therefore, scholars are highly interested in modeling and analyzing HAPs. During this process, the influence of atmospheric turbulence is crucial, as it is the primary factor limiting the transmission performance of the link. The light intensity distribution under weak turbulence can be characterized by the Log-normal model. The Gamma–Gamma model serves as a versatile channel model for FSO communication systems, capable of simulating turbulent conditions ranging from weak to strong [
18,
19]. Ref. [
20] examined the outage probability across different atmospheric turbulence channel models, emphasizing the benefits for high-altitude satellite applications. Meanwhile, Ref. [
21] developed a communication system tailored for multiple HAPS, focusing on the uplink and leveraging research advancements to enhance overall network performance. Despite efforts by researchers to mitigate the effects of atmospheric turbulence and facilitate the transmission of critical data, there remains a notable gap in research concerning encrypted transmission of image information, particularly valuable in military and related domains.
To investigate the realizability of image transmission in FSO communication technology, Ref. [
22] realized the effective transmission of FSO communication technology in wireless video transmission based on FPGA chip using compression sensing to realize the transmission of massive video data streams. Ref. [
23] simulated the pixel encoding and decoding processes for image transmission in a 1 km horizontal turbulent channel, analyzing the impact of turbulence parameters and detector noise on system performance. While these studies enhanced system efficiency and analyzed influencing factors, there remain shortcomings in the security design of image transmission. Ref. [
24] proposed a solution employing chaotic mapping and a three-dimensional filtering algorithm (C-BM3D) to enhance image security in turbulent channels, highlighting the efficacy of chaotic mapping algorithms for encryption as a suitable approach.
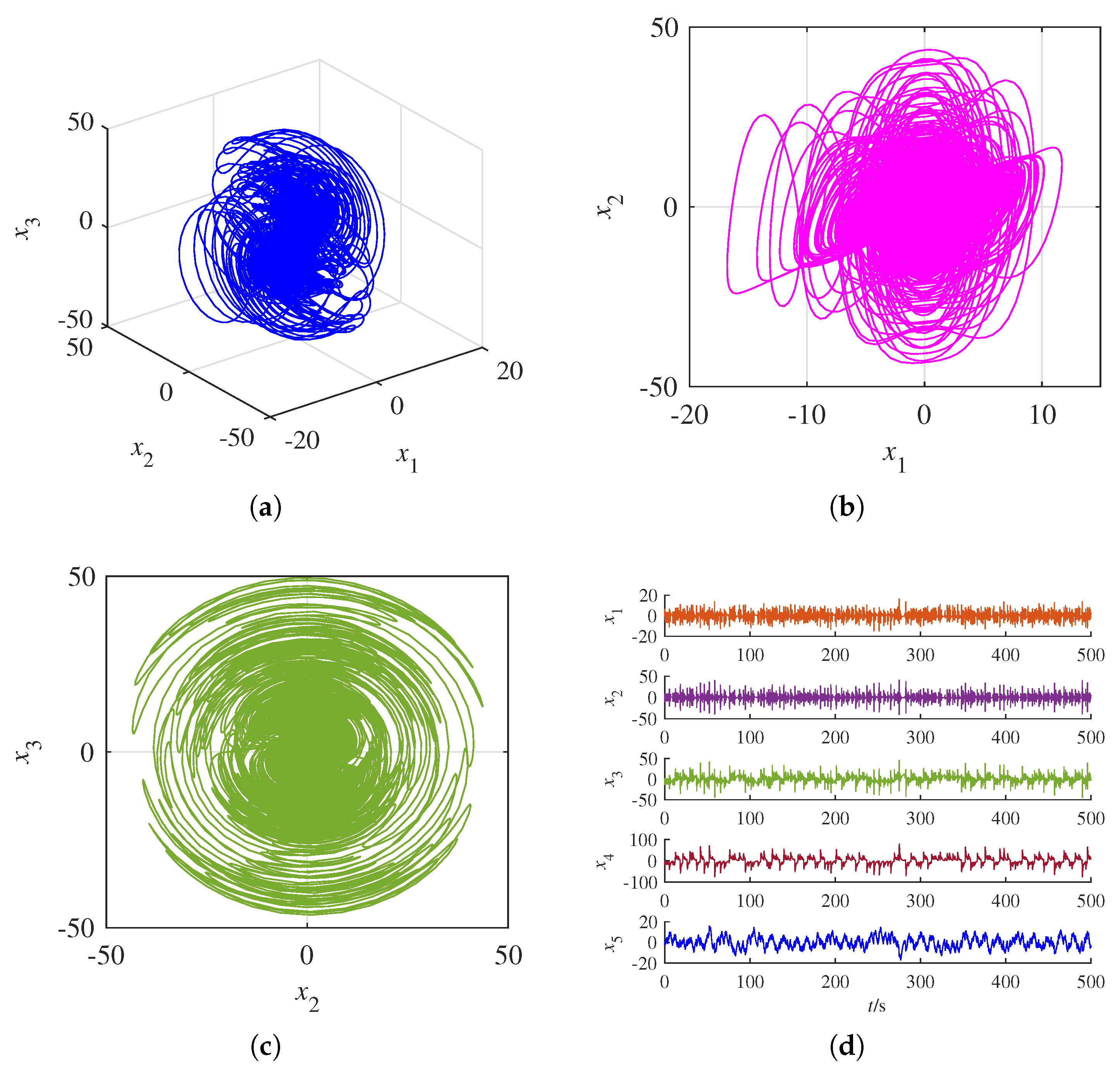
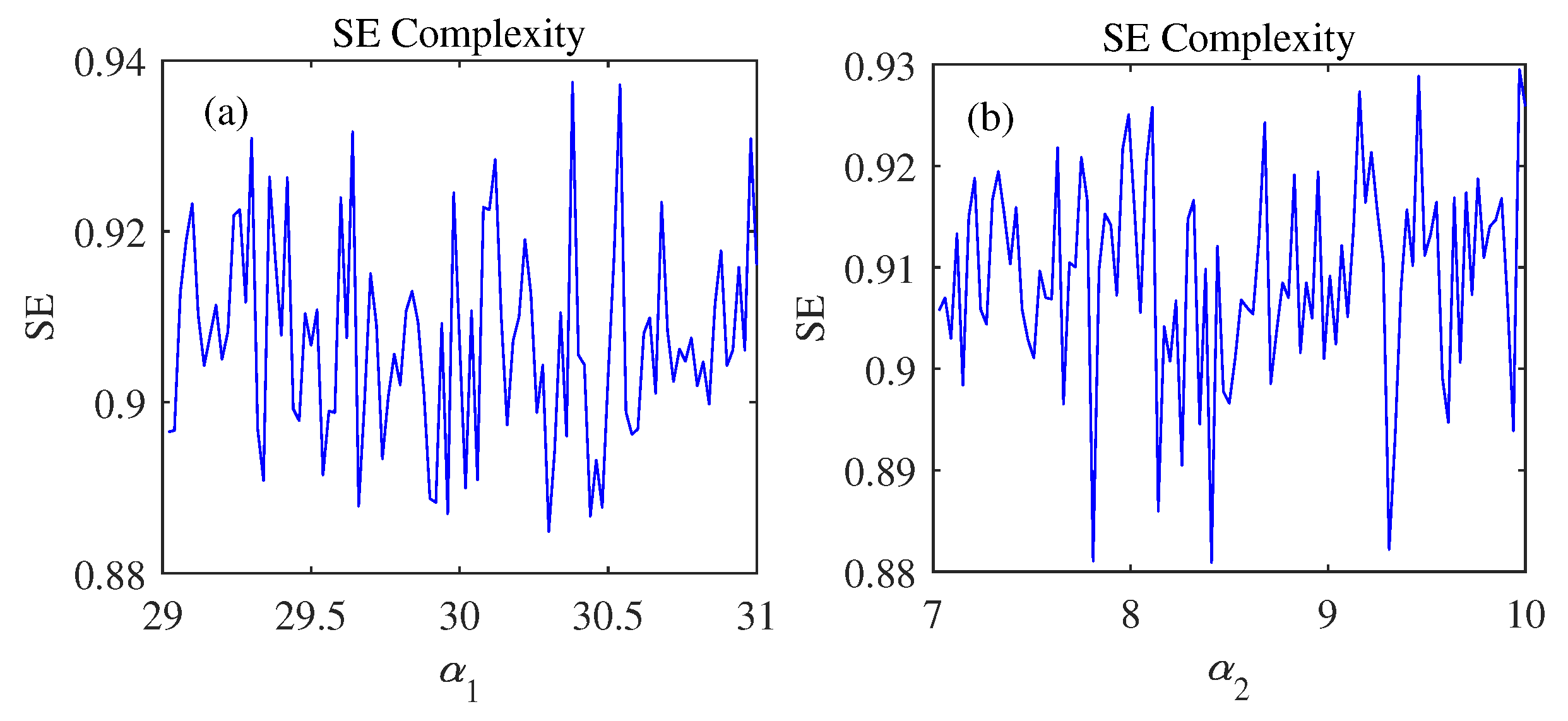
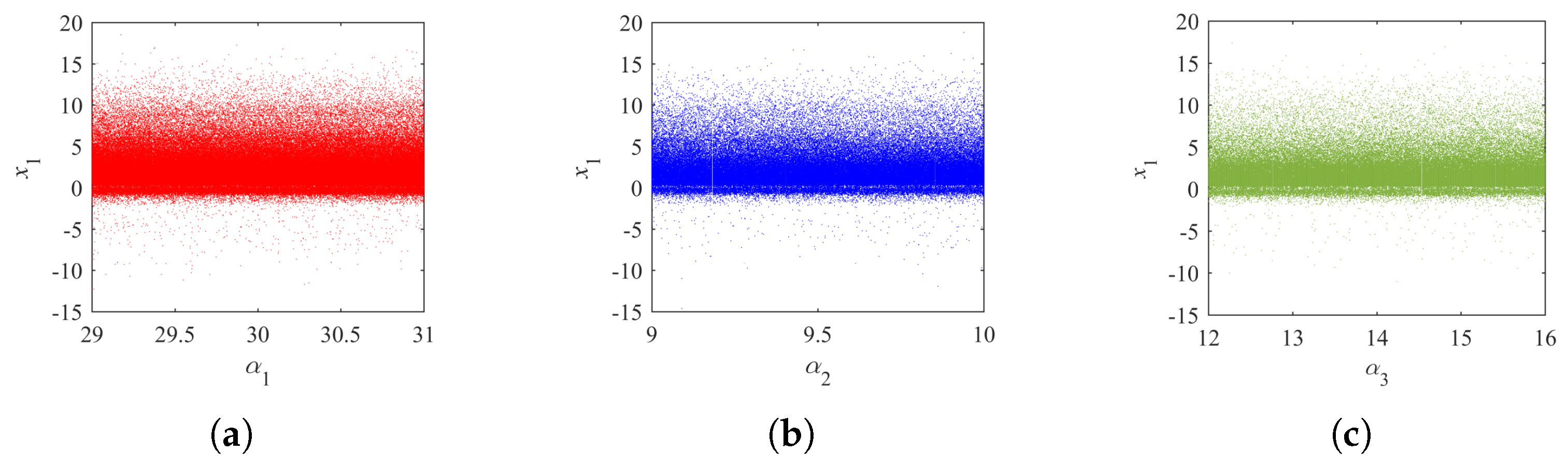
Chaotic systems possess intricate dynamic characteristics, including sensitivity to initial conditions, unpredictability, and complexity, which fulfill fundamental requirements for communication security [
25,
26,
27]. Chaos mapping offers advantages such as a straightforward mathematical form, ease of implementation and programming, low computational overhead, and the capability to exhibit complex chaotic behavior under specific conditions, making it widely adopted in image encryption systems. However, the simplicity of chaotic mapping renders it susceptible to decryption, given its relatively limited key space, thereby increasing vulnerability to brute force attacks. In contrast, high-dimensional chaotic systems refer to chaotic systems with a dimensionality of three or more. These systems exhibit more intricate dynamic behaviors and larger chaotic attractors. Compared to chaotic mapping, the complexity inherent in high-dimensional systems significantly enhances system security, thwarting decryption attempts through simple analysis or attacks. Moreover, high-dimensional systems offer a broader parameter space, enabling a wider range of key selections and further bolstering security. Additionally, these systems generate highly complex chaotic trajectories, rendering encrypted data more challenging to predict and decrypt. Furthermore, multiple encryption schemes can be implemented, such as employing multiple state variables for multi-layer encryption, thereby augmenting data protection even further.
The intricate dynamic behaviors and chaotic characteristics exhibited by high-dimensional chaotic systems provide enhanced security in chaotic image encryption applications. Currently, researchers have shown considerable interest in constructing chaotic image encryption systems using these advanced chaotic systems [
28,
29]. Ref. [
30] developed a sophisticated chaotic system to simulate chaotic image encryption using plaintext scrambling algorithms, demonstrating the effectiveness and security of their encryption approach. Ref. [
31] introduced a one-time one-class chaotic image cipher integrating data steganography, encompassing both encryption of plaintext images and embedding of encrypted images. Ref. [
32] proposed a fractional-order five-dimensional hyperchaotic system for generating chaotic sequences used in permutation and diffusion processes. They expanded DNA encoding rules and employed four DNA computation methods to enhance encryption scheme security. Additionally, Ref. [
33] presented a cross-channel pixel recombination color image encryption scheme based on asymptotic shape synchronization using a three-dimensional chaotic system. Simulation results validated the algorithm’s capability to effectively conceal plaintext images and accurately restore them through asymptotic shape synchronization.
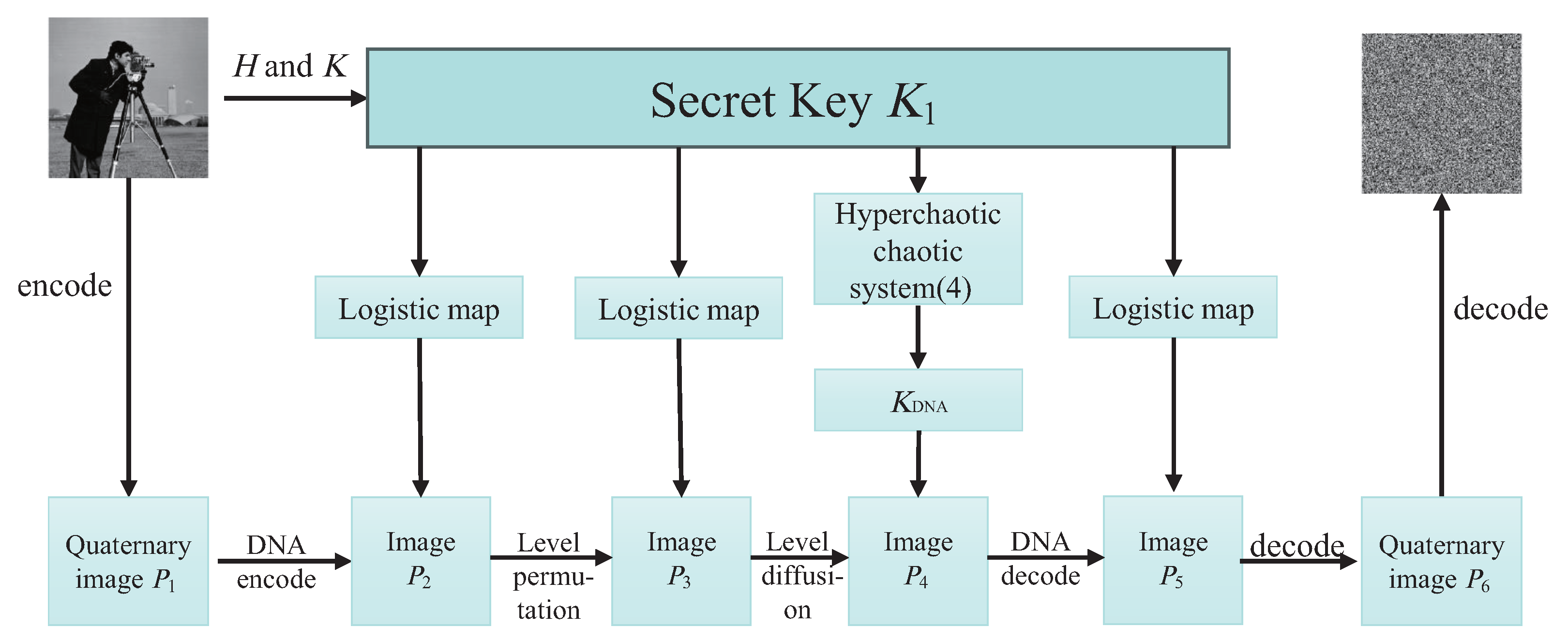
The aforementioned research outcomes clearly demonstrate that integrating high-dimensional chaotic systems with image encryption algorithms significantly expands the key space and enhances resistance against malicious attacks, thereby achieving robust security. The use of high-dimensional chaotic image encryption systems effectively filters out noise interference and mitigates malicious interception during both encryption and decryption processes, particularly beneficial in FSO communication to reduce transmission interferences. Furthermore, applying chaotic image encryption enhances image transmission security on aviation platforms by encrypting plaintext images. With the aim of enhancing performance and security in image transmission on FSO aviation platforms, this study proposes an enhanced five-dimensional hyperchaotic system combined with DNA coding technology to develop a chaotic image encryption algorithm. The research focuses on analyzing and evaluating the performance and security of image transmission within aviation platform environments. A novel image transmission modeling scheme is constructed by integrating these technologies, and its feasibility is demonstrated through comparative experiments.
The details of the study are as follows:
Section 2 introduces the improved five-dimensional hyperchaotic system model and dynamic behavior. The hyperchaotic system is applied to the image encryption algorithm, and the algorithm’s ability to resist attacks is tested.
Section 3 shows the experimental scheme and scheme parameters and explains the turbulence model used in the scheme. At the same time, the evaluation indicators of the quality of the original image and the restored image are given.
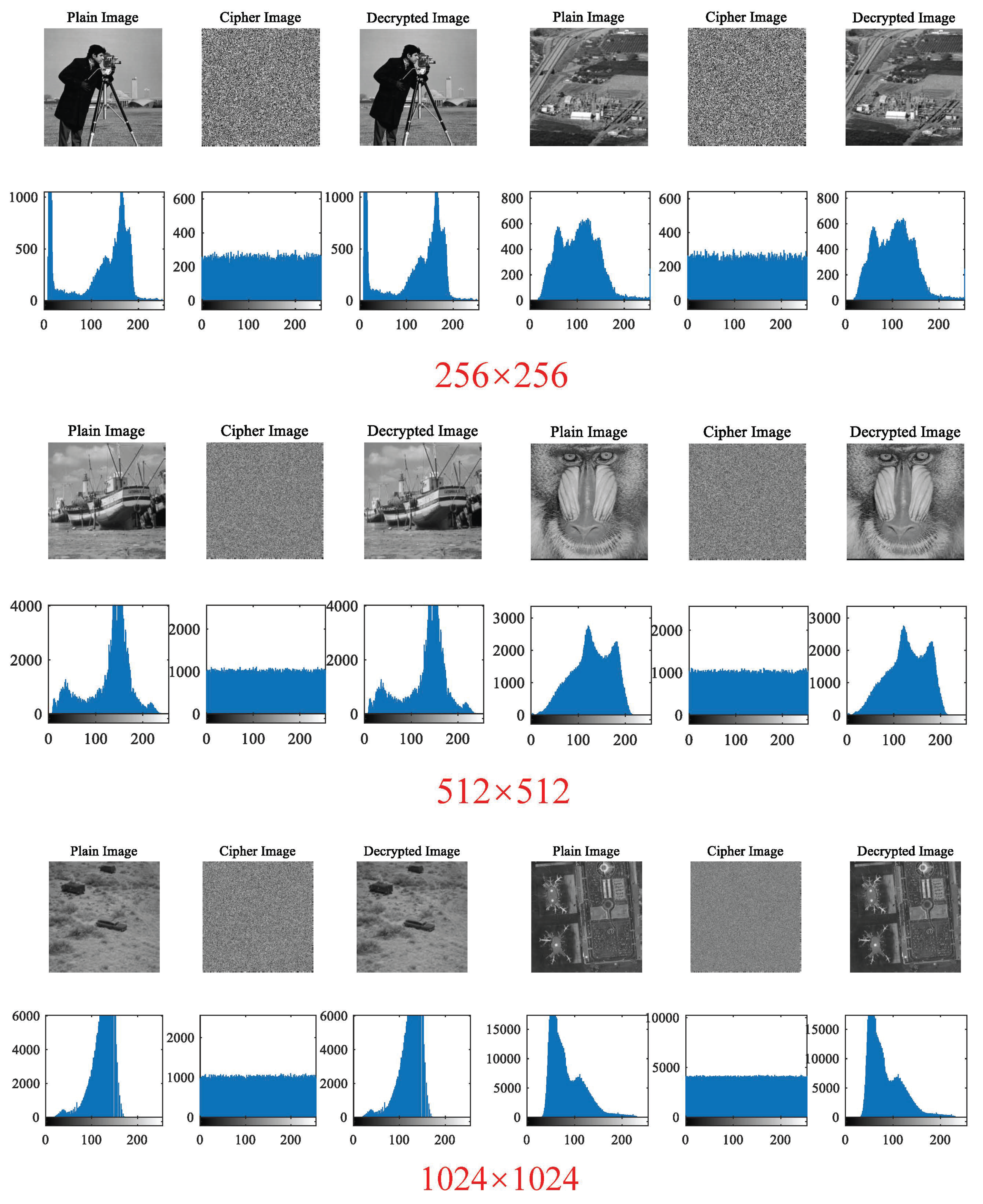
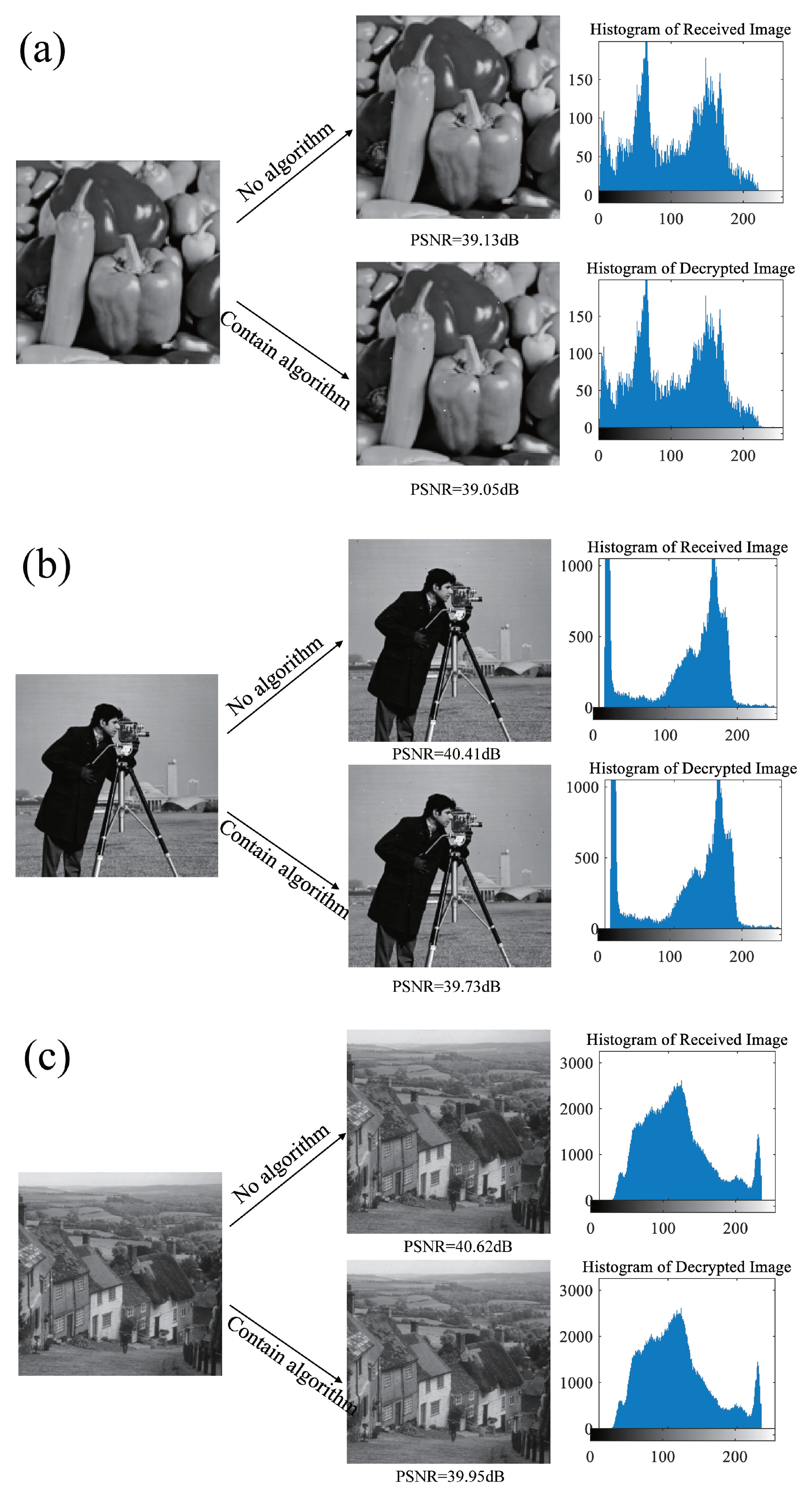
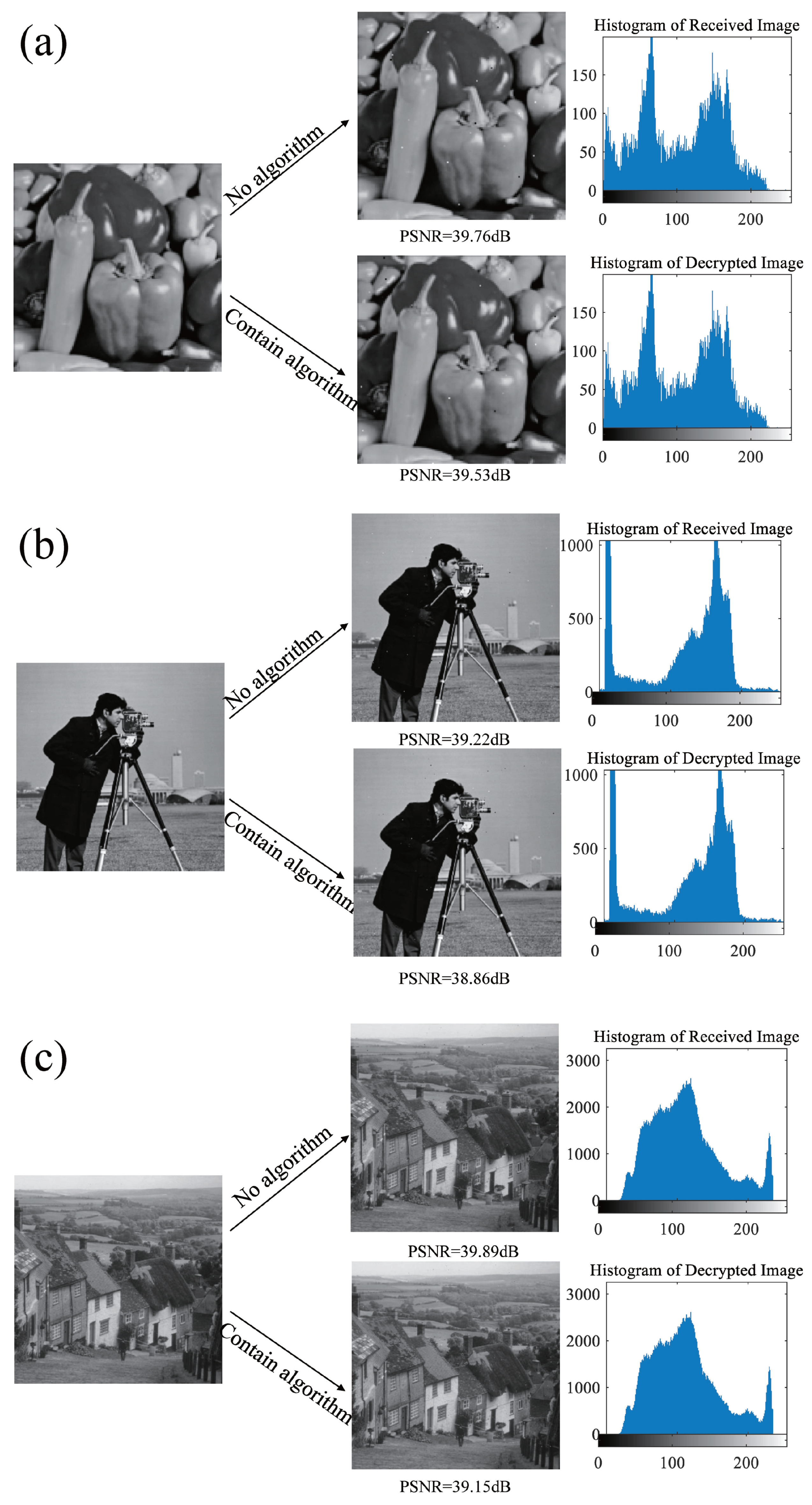
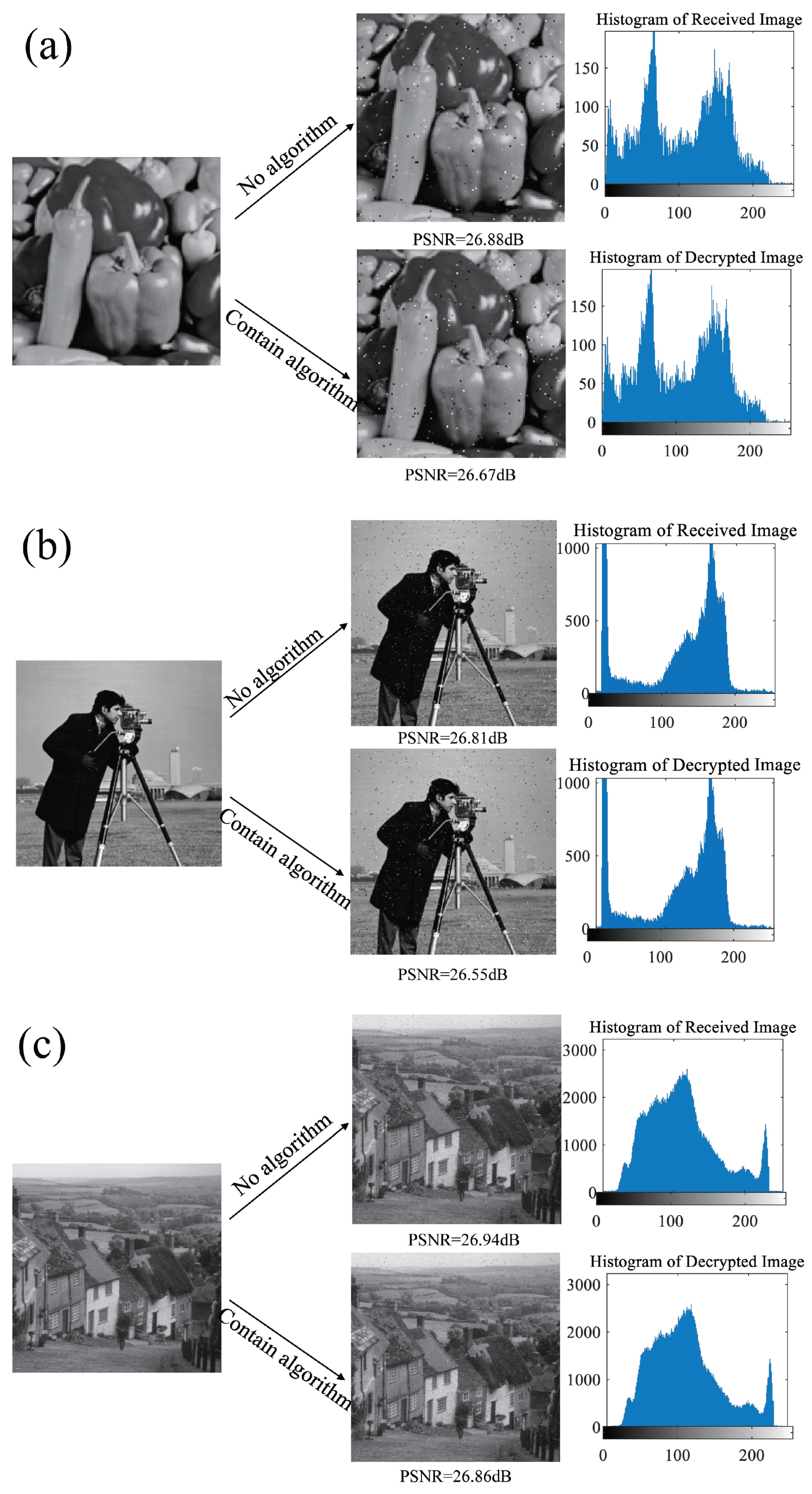
Section 4 provides simulation explanations from three aspects: transmission performance, transmission quality, and resistance to truncation attacks. Images of different sizes and turbulent channels of different intensities are used to verify the feasibility, turbulence resistance, security, and robustness of the scheme. Finally, the overall work of the article is summarized.
5. Conclusions
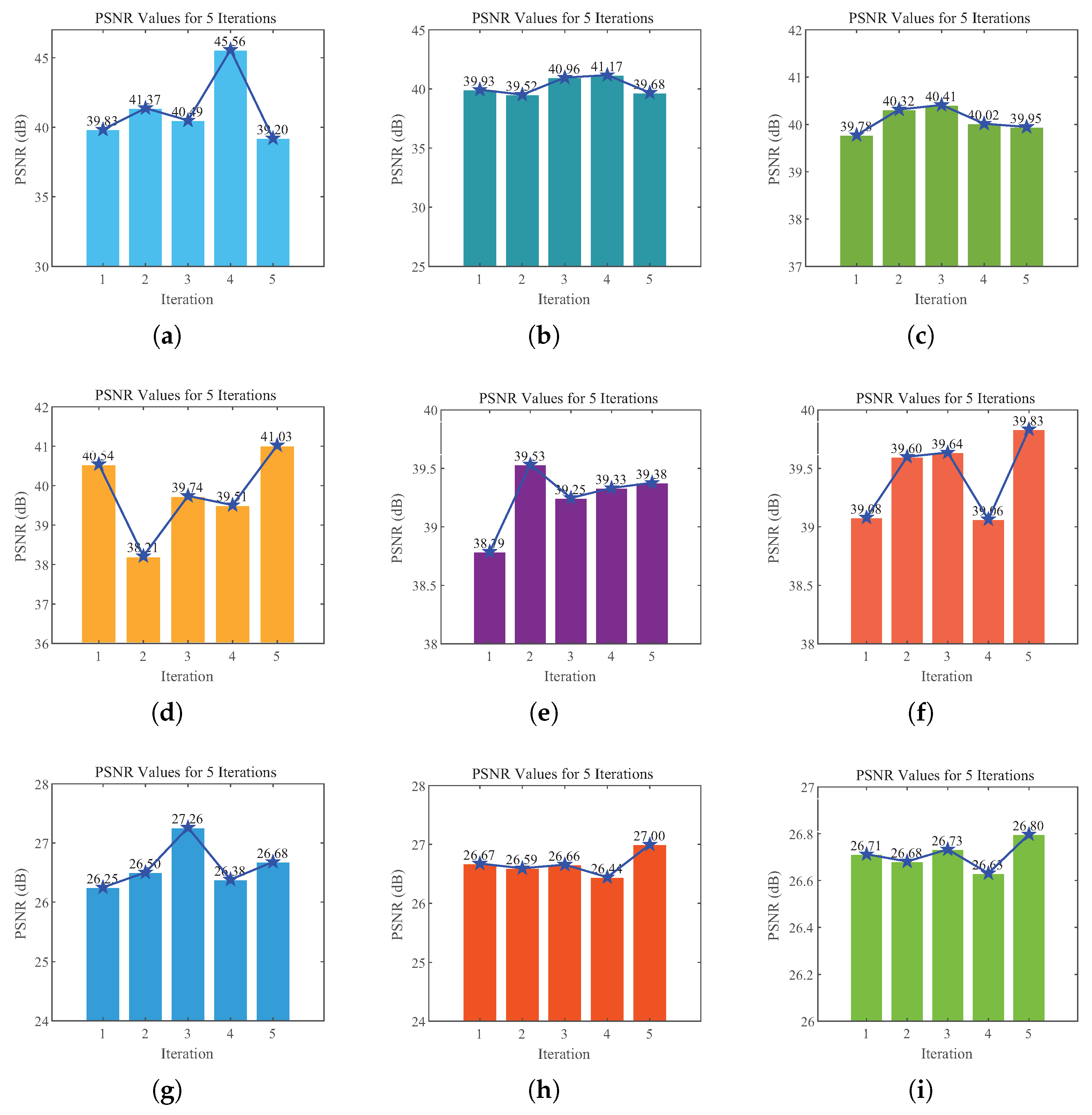
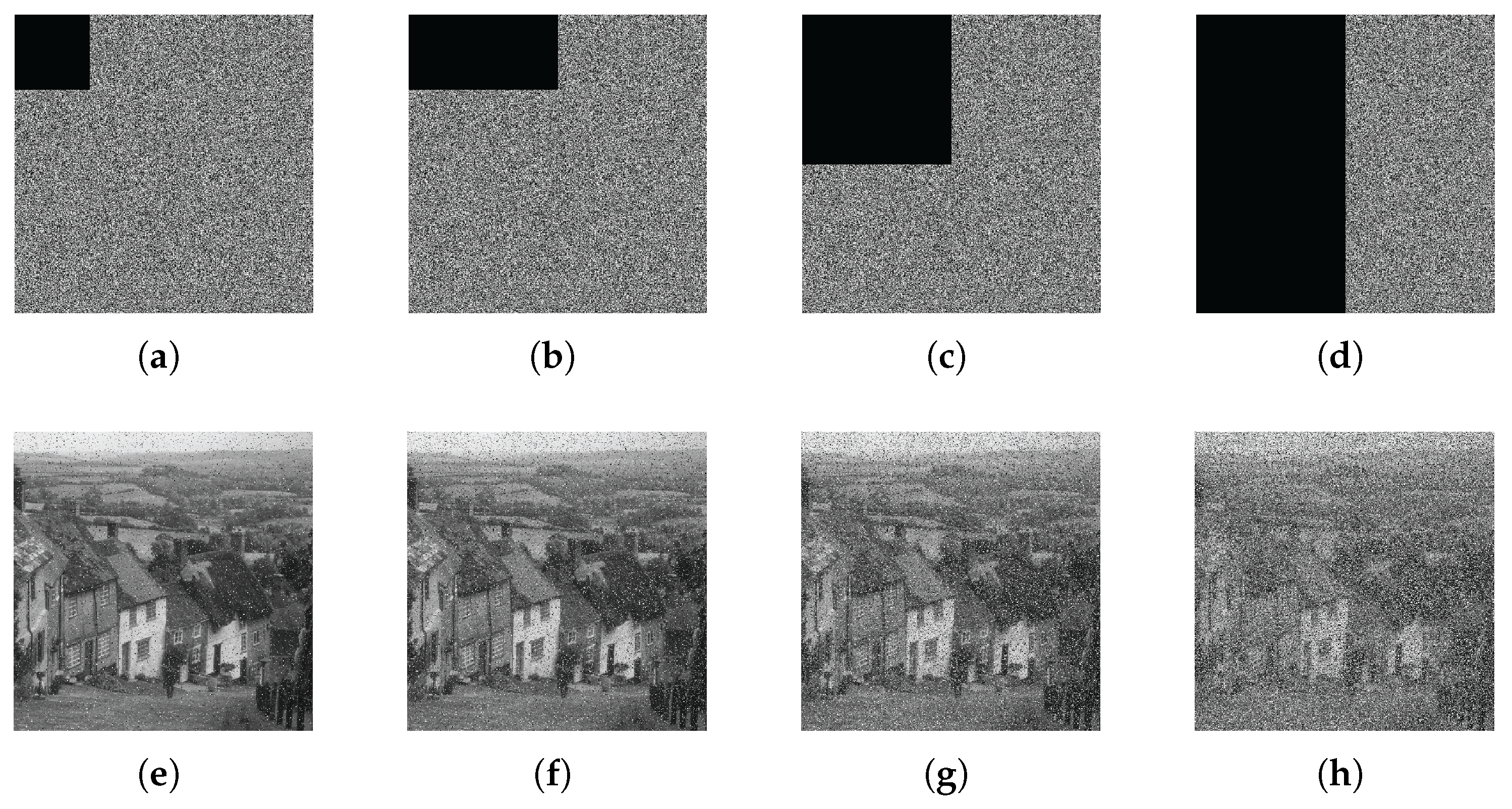
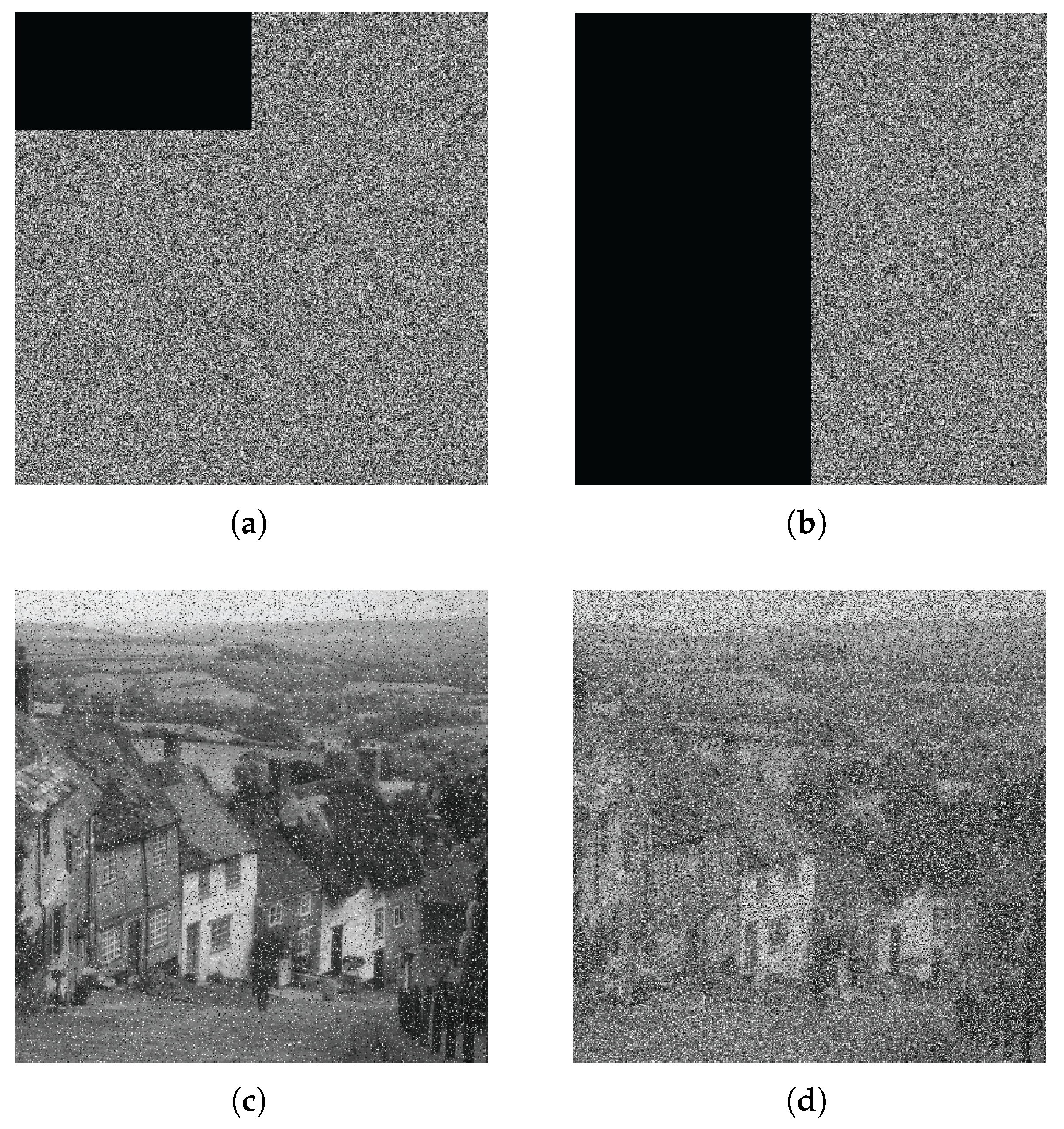
This article presents a methodology for constructing a system model by integrating unknown terms and vectors utilizing a practical three-dimensional system. This article proposes an integrity scheme based on the DNA chaotic image encryption algorithm combined with HAP for close-range image transmission. The encryption model in this scheme adopts an improved five-dimensional hyper chaotic system, chaotic mapping, and DNA encoding technology. The superiority of the encryption system is verified based on encryption and decryption effectiveness, encryption and decryption speed, information entropy, plaintext sensitivity test, and adjacent pixel correlation. Wet selected images with size , , and and compared the impact of using encryption algorithms and not using encryption algorithms on image transmission performance under different turbulence intensities. The results indicate that using encryption algorithms will not have adverse effects on transmission performance and can also successfully recover images. To a certain extent, it can improve the transmission quality of optical communication, and even in strong turbulence conditions, the PSNR value reaches 26.86 dB, further demonstrating great image transmission performance. We also evaluated the communication quality of image transmission using encryption algorithms based on PSNR and SSIM metrics. Under weak and moderate turbulence conditions, the distortion is minimal, resulting in high-quality reconstruction of the image. Although strong turbulence has a significant impact on image quality, the reconstructed image quality remains at a moderate level, indicating that the scheme has strong stability in terms of communication quality. In addition, under cropping attacks, even when up to 50% of the image data is lost and it passes through strong turbulent channels, the image can still be successfully decrypted. In summary, by improving the anti-turbulence and security of image transmission in HAP optical communication, a high degree of robustness has been demonstrated. The experiment verified that under different turbulence intensities, the scheme maintains a high level of transmission quality for images of different sizes, providing solid theoretical support for future research on the anti turbulence and safety performance of HAP optical communication.