SMR–YOLO: Multi-Scale Detection of Concealed Suspicious Objects in Terahertz Images
Abstract
1. Introduction
2. Data Acquisition and Analysis
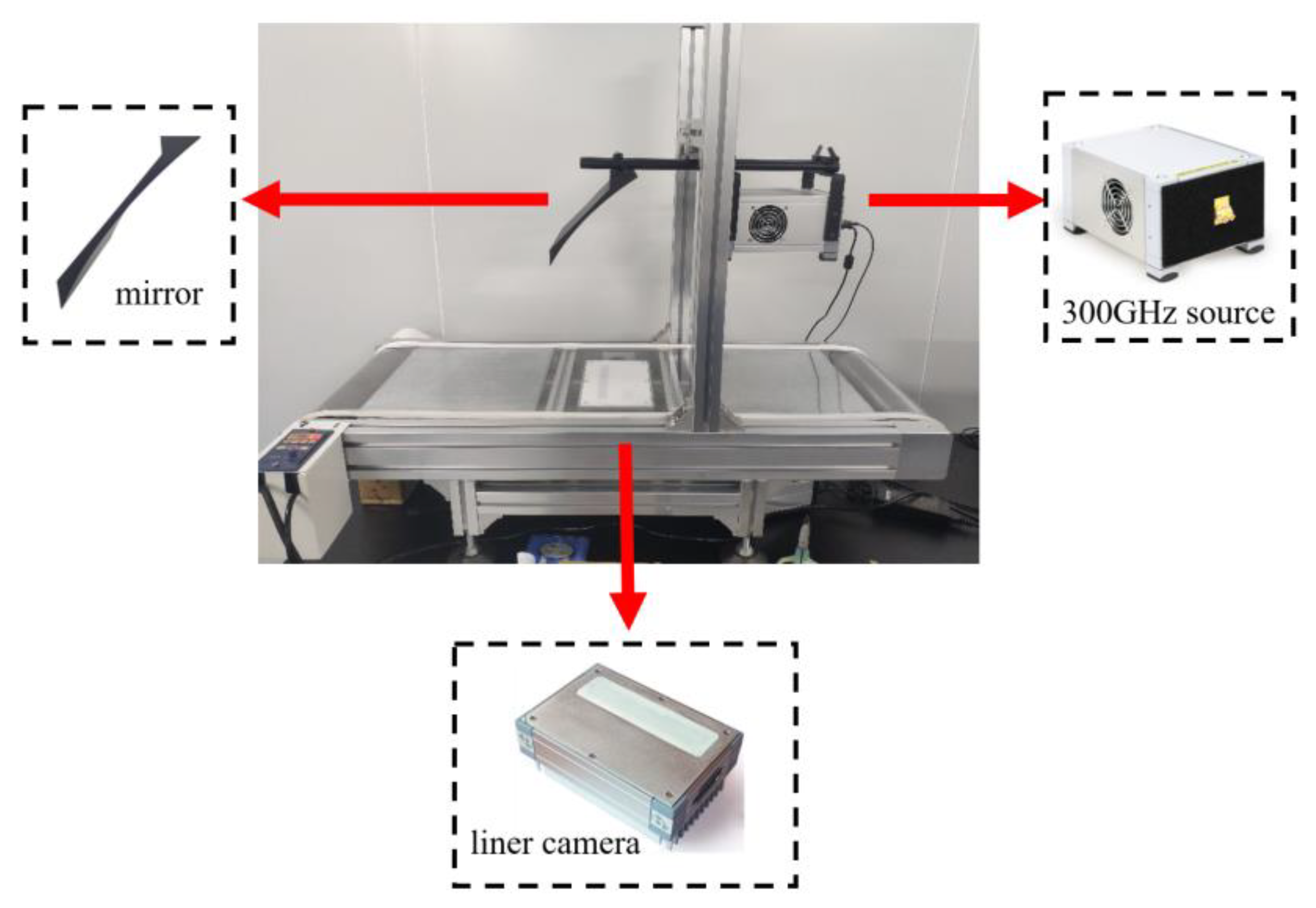
2.1. Experimental Setup
2.2. Terahertz Image Data Acquisition
3. Method
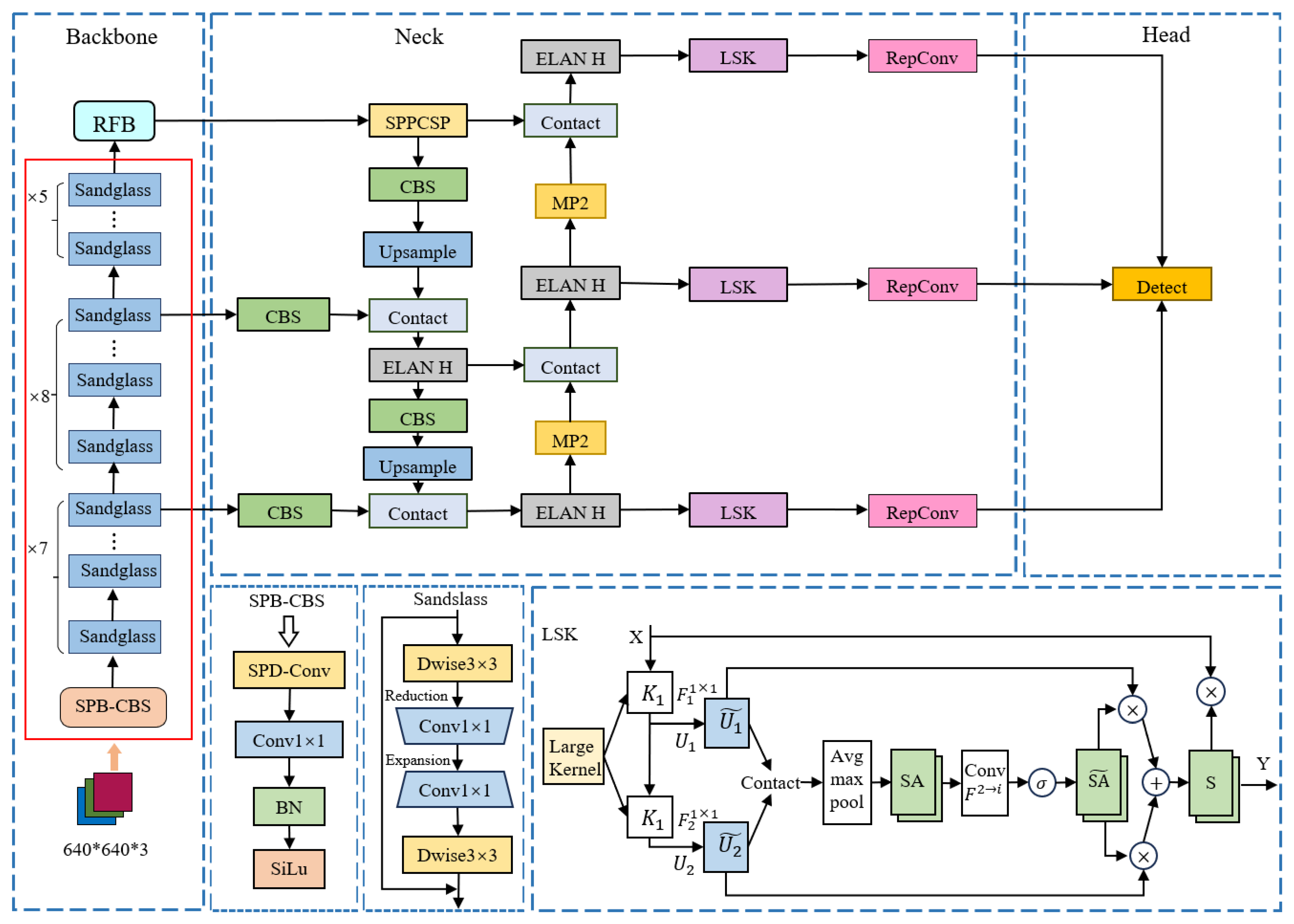
3.1. Overall Architecture
3.2. SPD_Mobile Structure
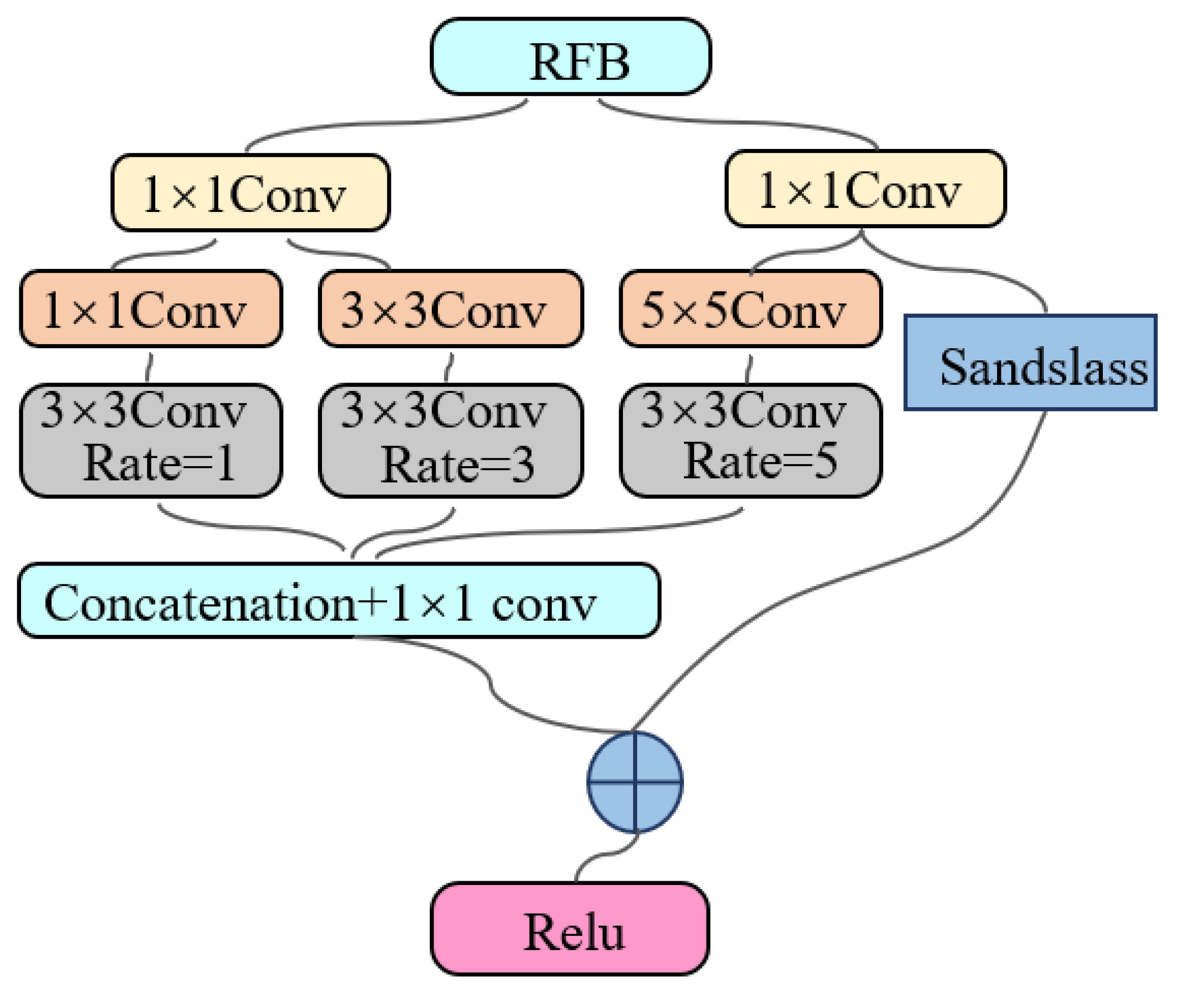
3.3. RFB Structure
3.4. EIOU Loss Function
4. Experimental Results and Discussion
4.1. Implementation Details
4.2. Evaluating Metric
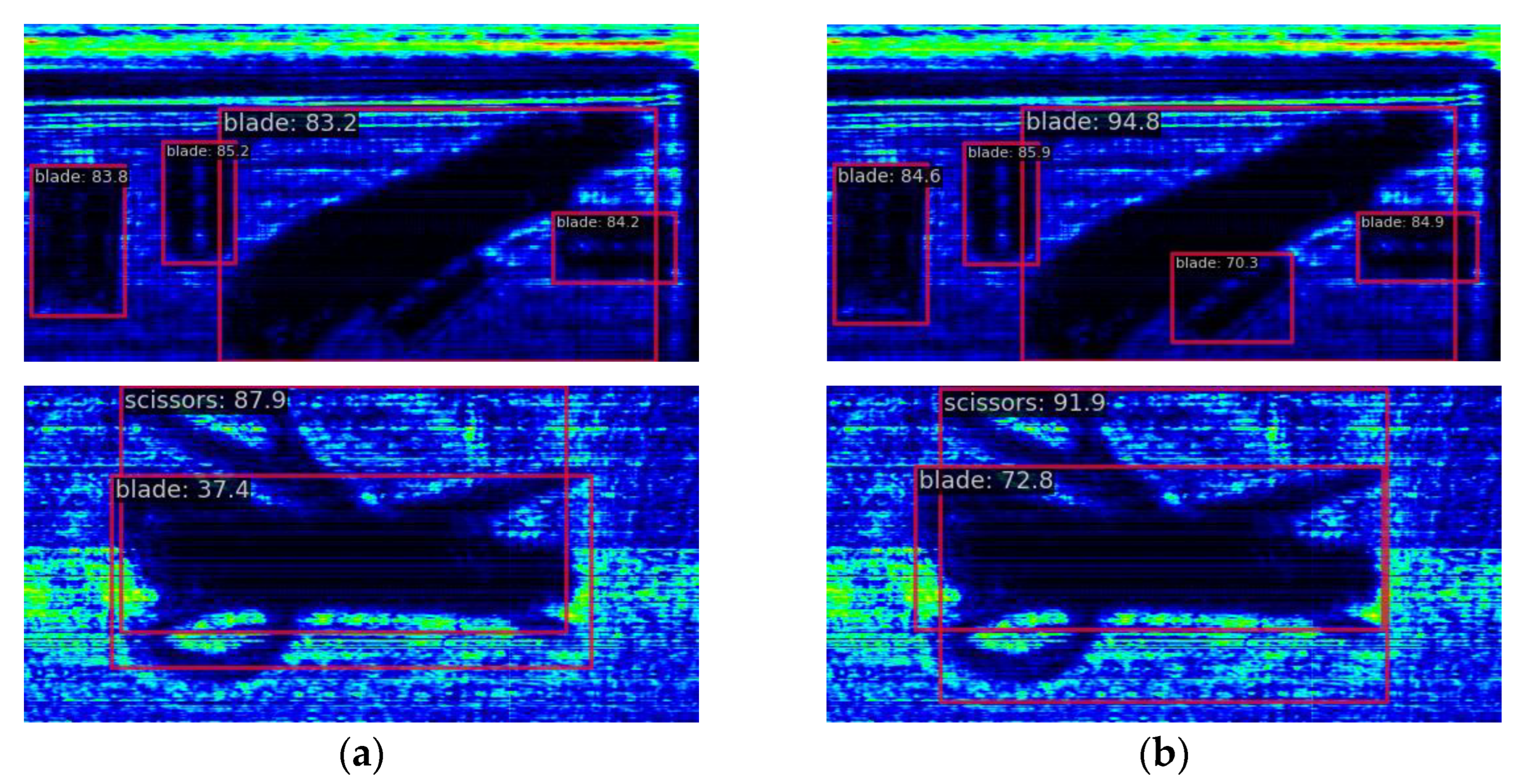
4.3. Experimental Results and Analysis
4.4. Ablation Study
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Saeedkia, D.; Safavi-Naeini, S. Terahertz Photonics: Optoelectronic Techniques for Generation and Detection of Terahertz Waves. J. Light. Technol. 2008, 26, 2409–2423. [Google Scholar] [CrossRef]
- Jiang, Y.; Ge, H.; Zhang, Y. Quantitative analysis of wheat maltose by combined terahertz spectroscopy and imaging based on Boosting ensemble learning. Food Chem. 2020, 307, 125533. [Google Scholar] [CrossRef]
- Ge, H.; Ji, X.; Jiang, Y.; Wu, X.; Li, L.; Jia, Z.; Sun, Z.; Bu, Y.; Guo, C.; Zhang, Y. Tri-band and high FOM THz metamaterial absorber for food/agricultural safety sensing applications. Opt. Commun. 2024, 554, 130173. [Google Scholar] [CrossRef]
- Wan, M.; Healy, J.J.; Sheridan, J.T. Terahertz phase imaging and biomedical applications. Opt. Laser Technol. 2020, 122, 105859. [Google Scholar] [CrossRef]
- Yang, Z.; Tang, D.; Hu, J.; Tang, M.; Zhang, M.; Cui, H.L.; Wang, L.; Chang, C.; Fan, C.; Li, J. Near-Field Nanoscopic Terahertz Imaging of Single Proteins. Small 2021, 17, 2005814. [Google Scholar] [CrossRef]
- Tribe, W.R.; Newnham, D.A.; Taday, P.F.; Kemp, M.C. Hidden object detection: Security applications of terahertz technology. In Terahertz and Gigahertz Electronics and Photonics III; SPIE: Philadelphia, PA, USA, 2004; pp. 168–176. [Google Scholar]
- Chen, Z.; Wang, C.; Feng, J.; Zou, Z.; Jiang, F.; Liu, H.; Jie, Y. Identification of blurred terahertz images by improved cross-layer convolutional neural network. Opt. Express 2023, 31, 16035–16053. [Google Scholar] [CrossRef]
- Jia, Y.; Fu, K.; Lan, H.; Wang, X.; Su, Z. Maize tassel detection with CA-YOLO for UAV images in complex field environments. Comput. Electron. Agric. 2024, 217, 108562. [Google Scholar] [CrossRef]
- YOLOv5 Code. Available online: https://github.com/ultralytics/yolov5 (accessed on 9 August 2024).
- Kang, L.; Lu, Z.; Meng, L.; Gao, Z. YOLO-FA: Type-1 fuzzy attention based YOLO detector for vehicle detection. Expert Syst. Appl. 2024, 237, 121209. [Google Scholar] [CrossRef]
- Su, P.; Han, H.; Liu, M.; Yang, T.; Liu, S. MOD-YOLO: Rethinking the YOLO architecture at the level of feature information and applying it to crack detection. Expert Syst. Appl. 2024, 237, 121346. [Google Scholar] [CrossRef]
- Li, X.; He, M.; Liu, Y.; Luo, H.; Ju, M. SPCS: A spatial pyramid convolutional shuffle module for YOLO to detect occluded object. Complex Intell. Syst. 2023, 9, 301–315. [Google Scholar] [CrossRef]
- Cheng, L.; Ji, Y.; Li, C.; Liu, X.; Fang, G. Improved SSD network for fast concealed object detection and recognition in passive terahertz security images. Sci. Rep. 2022, 12, 12082. [Google Scholar] [CrossRef] [PubMed]
- Simonyan, K.; Zisserman, A. Very deep convolutional networks for large-scale image recognition. arXiv 2014, arXiv:1409.1556. [Google Scholar]
- Danso, S.A.; Liping, S.; Hu, D.; Afoakwa, S.; Badzongoly, E.L.; Odoom, J.; Muhammad, O.; Mushtaq, M.U.; Qayoom, A.; Zhou, W. An optimal defect recognition security-based terahertz low resolution image system using deep learning network. Egypt. Inform. J. 2023, 24, 100384. [Google Scholar] [CrossRef]
- Zhang, H.; Chang, H.; Ma, B.; Shan, S.; Chen, X. Cascade RetinaNet: Maintaining consistency for single-stage object detection. arXiv 2019, arXiv:1907.06881. [Google Scholar]
- Xu, F.; Huang, X.; Wu, Q.; Zhang, X.; Shang, Z.; Zhang, Y. YOLO-MSFG: Toward real-time detection of concealed objects in passive terahertz images. IEEE Sens. J. 2021, 22, 520–534. [Google Scholar] [CrossRef]
- Wang, C.-Y.; Bochkovskiy, A.; Liao, H.-Y.M. YOLOv7: Trainable bag-of-freebies sets new state-of-the-art for real-time object detectors. In Proceedings of the IEEE/CVF Conference on Computer Vision and Pattern Recognition, Vancouver, BC, Canada, 17–24 June 2023; pp. 7464–7475. [Google Scholar]
- Liu, Y.-L.; Wang, J.; Chen, X.; Guo, Y.-W.; Peng, Q.-S. A robust and fast non-local means algorithm for image denoising. J. Comput. Sci. Technol. 2008, 23, 270–279. [Google Scholar] [CrossRef]
- Sunkara, R.; Luo, T. No more strided convolutions or pooling: A new CNN building block for low-resolution images and small objects. In Machine Learning and Knowledge Discovery in Databases; Springer: Cham, Switzerland, 2022; pp. 443–459. [Google Scholar]
- Zhou, D.; Hou, Q.; Chen, Y.; Feng, J.; Yan, S. Rethinking bottleneck structure for efficient mobile network design. In Proceedings of the Computer Vision–ECCV 2020: 16th European Conference, Glasgow, UK, 23–28 August 2020; Proceedings, Part III 16. pp. 680–697. [Google Scholar]
- Liu, S.; Huang, D. Receptive field block net for accurate and fast object detection. In Proceedings of the European Conference on Computer Vision (ECCV), Munich, Germany, 8–14 September 2018; pp. 385–400. [Google Scholar]
- Zhang, Y.; Ren, W.; Zhang, Z.; Jia, Z.; Wang, L.; Tan, T. Focal and efficient IOU loss for accurate bounding box regression. arXiv 2021, arXiv:2101.08158. [Google Scholar] [CrossRef]
- Shi, C.; Han, L.; Zhang, K.; Xiang, H.; Li, X.; Su, Z.; Zheng, X. Improved RepVGG ground-based cloud image classification with attention convolution. Atmos. Meas. Tech. 2024, 17, 979–997. [Google Scholar] [CrossRef]
- Li, Y.; Hou, Q.; Zheng, Z.; Cheng, M.-M.; Yang, J.; Li, X. Large selective kernel network for remote sensing object detection. In Proceedings of the IEEE/CVF International Conference on Computer Vision, Paris, France, 1–6 October 2023; pp. 16794–16805. [Google Scholar]
- Ge, Z.; Zhang, Y.; Jiang, Y.; Ge, H.; Wu, X.; Jia, Z.; Wang, H.; Jia, K. Lightweight YOLOv7 algorithm for multi-object recognition on contrabands in terahertz images. Appl. Sci. 2024, 14, 1398. [Google Scholar] [CrossRef]
- Zheng, Z.; Wang, P.; Liu, W.; Li, J.; Ye, R.; Ren, D. Distance-IoU loss: Faster and better learning for bounding box regression. In Proceedings of the AAAI Conference on Artificial Intelligence, New York, NY, USA, 7–12 February 2020; pp. 12993–13000. [Google Scholar]
- Lyu, C.; Zhang, W.; Huang, H.; Zhou, Y.; Wang, Y.; Liu, Y.; Zhang, S.; Chen, K. Rtmdet: An empirical study of designing real-time object detectors. arXiv 2022, arXiv:2212.07784. [Google Scholar]
- Ren, S.; He, K.; Girshick, R.; Sun, J. Faster R-CNN: Towards real-time object detection with region proposal networks. IEEE Trans. Pattern Anal. Mach. Intell. 2016, 39, 1137–1149. [Google Scholar] [CrossRef]




| Method | mAP@0.5(%) | mAP@0.5:0.95(%) | FPS |
|---|---|---|---|
| Faster–RCNN | 93.3 | 75.5 | 34.1 |
| RetinaNet | 84.8 | 71.4 | 46.5 |
| RTMDet | 97.1 | 84.1 | 32.7 |
| YOLOv5 | 97.5 | 84.7 | 87.4 |
| YOLOv7 | 98.7 | 87.6 | 85.5 |
| SMR–YOLO | 98.9 | 89.4 | 108.7 |
| Model | MobileNext | SPD-Conv | RFB | EIOU | LSK | P (%) | R (%) | mAP@0.5 (%) | mAP@0.5:0.95 (%) | FPS |
|---|---|---|---|---|---|---|---|---|---|---|
| 1 | × | × | × | × | × | 98.2 | 96.4 | 98.7 | 87.6 | 85.5 |
| 2 | √ | × | × | × | × | 96.2 | 92.9 | 97.5 | 82.0 | 116.3 |
| 3 | √ | √ | × | × | × | 96.5 | 94.0 | 97.7 | 82.2 | 116.3 |
| 4 | √ | √ | × | √ | × | 97.5 | 95.2 | 98.3 | 82.5 | 116.3 |
| 5 | √ | √ | √ | × | × | 97.5 | 97.0 | 98.6 | 86.1 | 116.3 |
| 6 | √ | √ | √ | √ | × | 97.9 | 97.4 | 98.8 | 87.2 | 116.3 |
| 7 | √ | √ | × | √ | √ | 98.9 | 96.4 | 98.6 | 86.1 | 111.1 |
| 8 | √ | √ | √ | √ | √ | 98.7 | 98.7 | 98.9 | 89.4 | 108.7 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhang, Y.; Chen, H.; Ge, Z.; Jiang, Y.; Ge, H.; Zhao, Y.; Xiong, H. SMR–YOLO: Multi-Scale Detection of Concealed Suspicious Objects in Terahertz Images. Photonics 2024, 11, 778. https://doi.org/10.3390/photonics11080778
Zhang Y, Chen H, Ge Z, Jiang Y, Ge H, Zhao Y, Xiong H. SMR–YOLO: Multi-Scale Detection of Concealed Suspicious Objects in Terahertz Images. Photonics. 2024; 11(8):778. https://doi.org/10.3390/photonics11080778
Chicago/Turabian StyleZhang, Yuan, Hao Chen, Zihao Ge, Yuying Jiang, Hongyi Ge, Yang Zhao, and Haotian Xiong. 2024. "SMR–YOLO: Multi-Scale Detection of Concealed Suspicious Objects in Terahertz Images" Photonics 11, no. 8: 778. https://doi.org/10.3390/photonics11080778
APA StyleZhang, Y., Chen, H., Ge, Z., Jiang, Y., Ge, H., Zhao, Y., & Xiong, H. (2024). SMR–YOLO: Multi-Scale Detection of Concealed Suspicious Objects in Terahertz Images. Photonics, 11(8), 778. https://doi.org/10.3390/photonics11080778





