A New Quantum Sealed-Bid Auction Protocol with a Set of Local Indistinguishable Orthogonal Product States
Abstract
1. Introduction
2. Preliminary Information
2.1. Sealed-Bid Auction
- (1)
- Anonymity: Each bidder who participates in an auction can keep anonymity. In a secure auction, no one can obtain any bidder’s identity information except the auctioneer.
- (2)
- Public verifiability: The winning bid can be validated by any bidder. Every bidder is able to confirm the winning bid, which is determined by the auctioneer during the verification step. This implies that the attack may be immediately detected if there is collusion between a malicious bidder and a dishonest auctioneer.
- (3)
- Accountability of bidder: Any malicious bidder with a fake bid cannot interrupt the auction without being detected.
- (4)
- Fairness: Each bidder performs the same operations in the auction. The auctioneer cannot help a dishonest bidder to win the auction illegally without being found by other bidders.
- (5)
- Traceability: The winning bidder and the highest bid can be verified even after the auction has finished.
- (6)
- Non-repudiation: The bidder cannot deny that he has cast his bid, and accordingly, the auctioneer cannot deny that he has received the bid from the bidder.
2.2. LIOP States
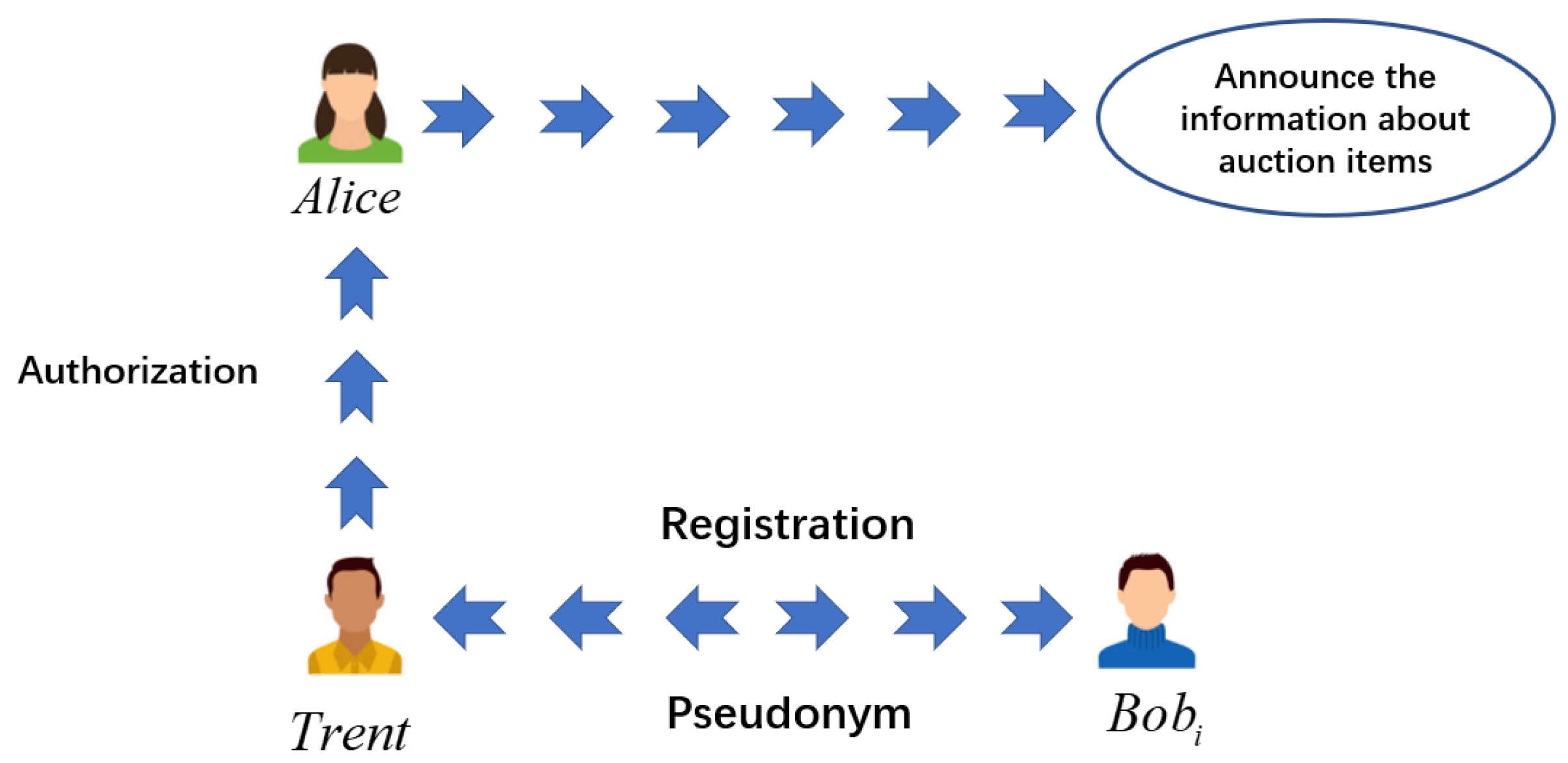
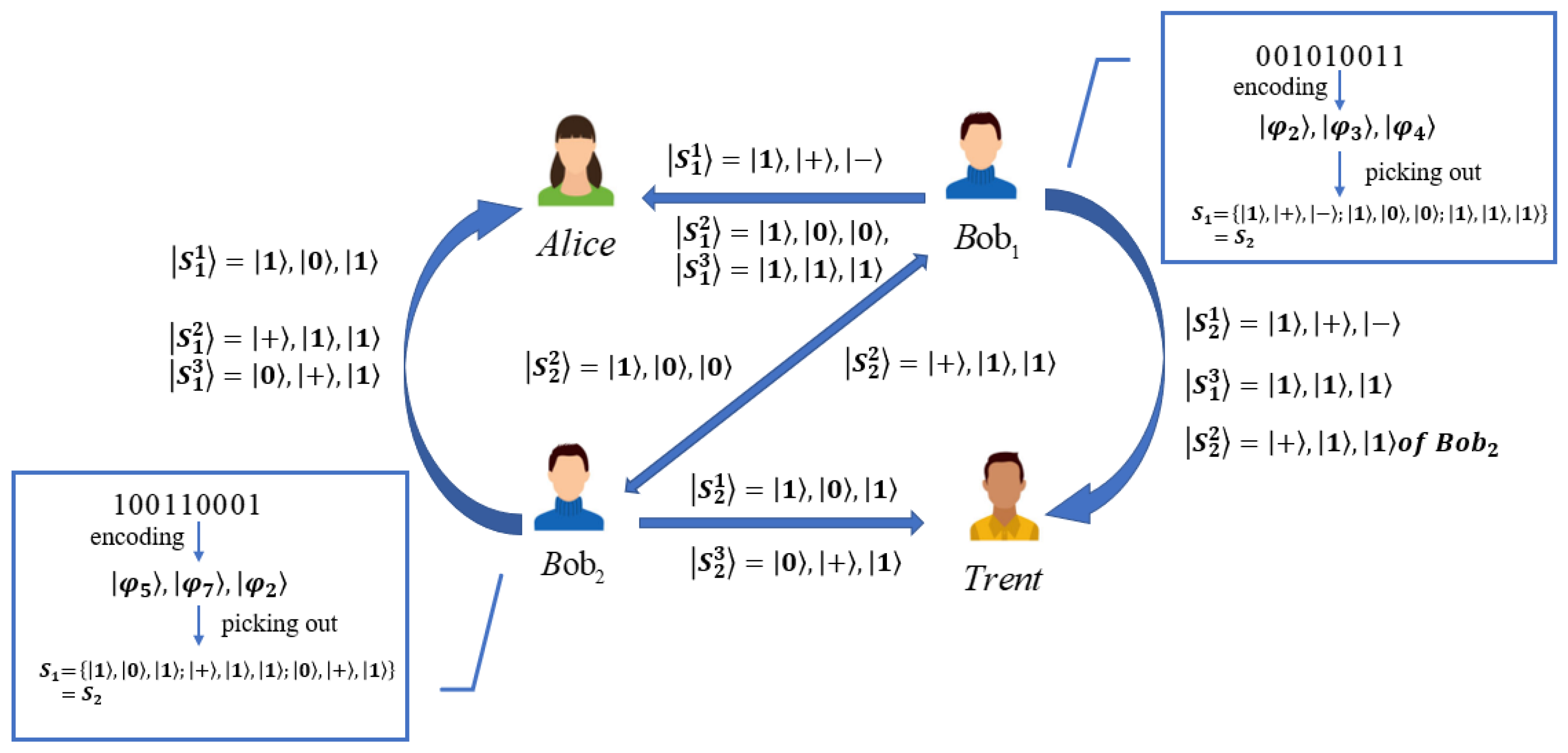
3. The Proposed Protocol
3.1. Stage of Preparation
3.2. Stage of Auction
3.3. Stage of Verification
4. Analysis of the Protocol
4.1. Analysis of Correctness
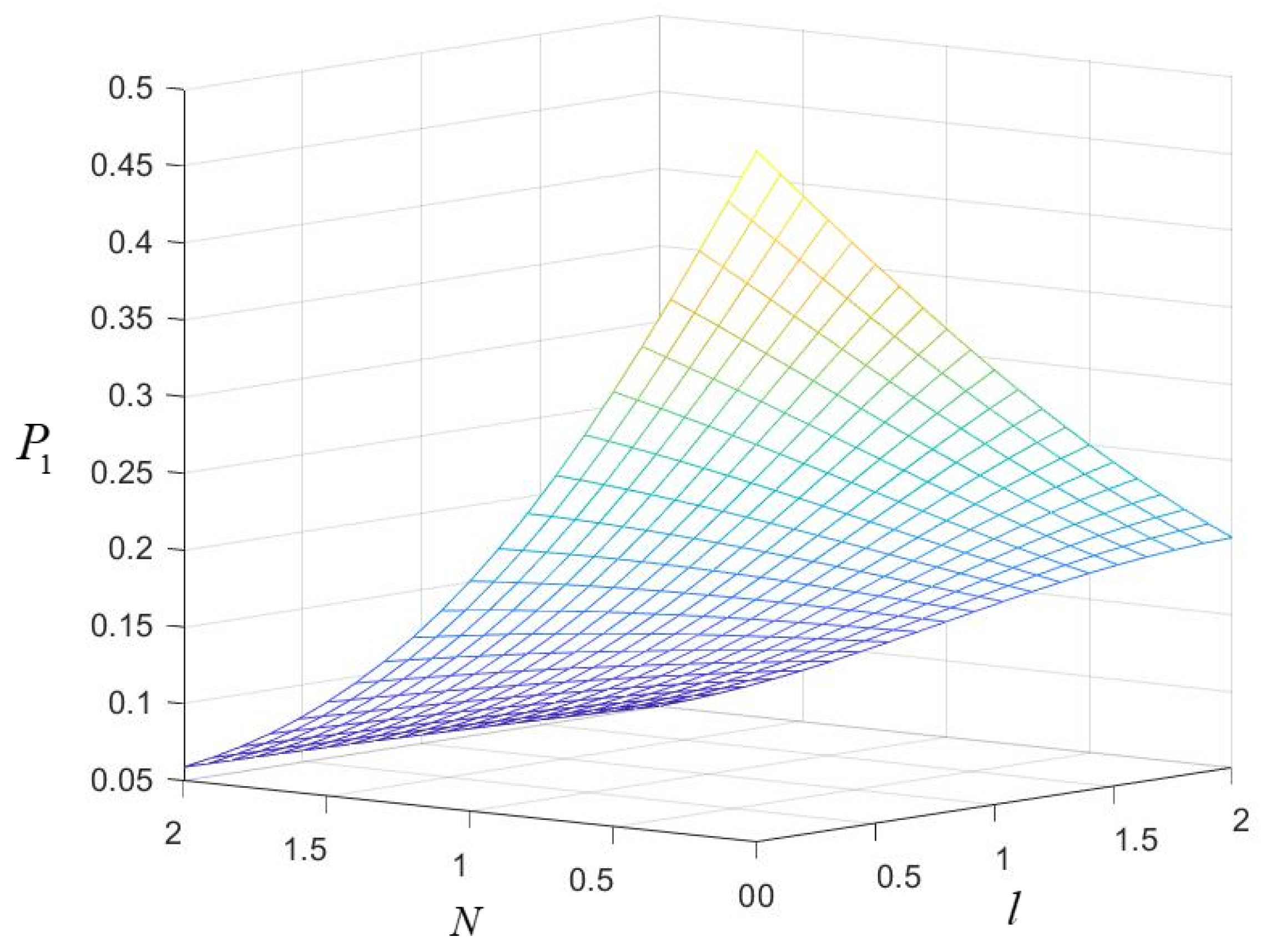
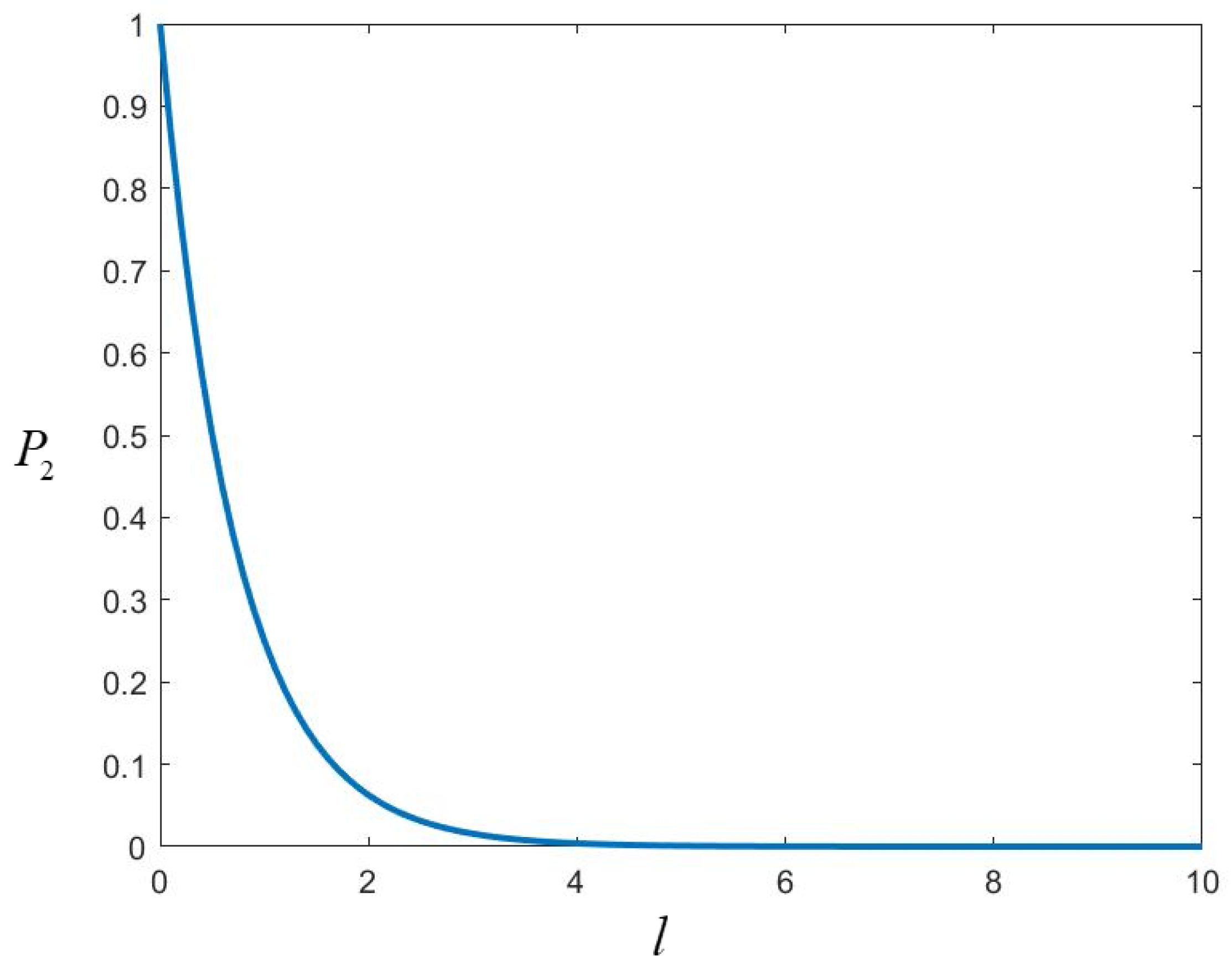
4.2. Analysis of Security
4.2.1. Intercept-Resend Attack
4.2.2. TP’s Attack
4.2.3. Collusion Attack
4.2.4. Entangle-Measure Attack
4.3. Analysis of Completeness
- (1)
- AnonymityIn our protocol, the bidder applies and registers with the auction center before the auction starts, and bidders use pseudonyms to participate in the entire auction process. As a result, except for the auction center, no one can obtain any information about the bidder’s identity.
- (2)
- Public verifiabilityOur proposed protocol incorporates a semi-honest auction center for verifying that a bidder has legitimately won the auction, and any bidder can participate in the verification process of the winner. In Step 7 of the auction stage, each bidder is required to send the same sequence to all other bidders. Finally, they assist the auction center during the verification process, confirming that the winning bidder’s price has not changed in the verification stage. Thus, our protocol is able to satisfy public verifiability.
- (3)
- Accountability of bidderBy analyzing the security of the collusion attack, where the semi-honest third party and other bidders serve as monitors, it is clear that any malicious fake bidders cannot interrupt the auction without being detected. That is, it meets accountability of bidder.
- (4)
- FairnessAll bidders perform the same auction procedure before the bid opening, so there is no bias. In addition, under case 2 of the collusive attack analysis, the auctioneer cannot collude with any malicious bidders to help him win the auction legally.
- (5)
- TraceabilitySince the auction center records the correspondence between the pseudonym and the real identity of the bidder, can verify the identity of the winner during the verification phase.
- (6)
- Non-repudiationIn our protocol, the post-confirmation mechanism ensures that the bidder cannot deny having placed a bid on . Concurrently, auctioneer cannot deny having received bids from bidders. Whether a group of bidders conspires or a dishonest bidder and a dishonest auctioneer conspire, the non-repudiation of the participants is satisfied.
5. Conclusions and Perspectives
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| QSA | Quantum Sealed-bid Auction |
| LIOP | Locally Indistinguishable Orthogonal Product |
| LOCC | Local Operations and Classical Communication |
| TP | Third Party |
References
- Li, D.D.; Tang, Y.L.; Zhao, Y.K.; Zhou, L.; Zhao, Y.; Tang, S.-B. Security of optical beam splitter in quantum key distribution. Photonics 2022, 9, 527. [Google Scholar] [CrossRef]
- Mafu, M.; Sekga, C.; Senekane, M. Security of Bennett–Brassard 1984 quantum-key distribution under a collective-rotation noise channel. Photonics 2022, 9, 941. [Google Scholar] [CrossRef]
- Jiang, X.L.; Deng, X.Q.; Wang, Y.; Lu, Y.F.; Li, J.J.; Zhou, C.; Bao, W.S. Weak randomness analysis of measurement-device independent quantum key distribution with finite resources. Photonics 2022, 9, 356. [Google Scholar] [CrossRef]
- Wang, N.; Tian, X.; Zhang, X.; Lin, S. Quantum Secure Multi-Party Summation with Identity Authentication Based on Commutative Encryption. Photonics 2023, 10, 558. [Google Scholar] [CrossRef]
- Paraiso, T.K.; Woodward, R.I.; Marangon, D.G.; Lovic, V.; Yuan, Z.; Shields, A.J. Advanced laser technology for quantum communications (tutorial review). Adv. Quantum Technol. 2021, 4, 2100062. [Google Scholar] [CrossRef]
- Montenegro, J.; Fischer, M.; Lopez, J.; Peralta, R. Secure sealed-bid online auctions using discreet cryptographic proofs. Math. Comput. Mode 2013, 57, 2583–2595. [Google Scholar] [CrossRef]
- Naseri, M. Secure quantum sealed-bid auction. Opt. Commun. 2009, 282, 1939–1943. [Google Scholar] [CrossRef]
- Qin, S.J.; Gao, F.; Wen, Q.Y.; Meng, L.M.; Zhu, F.C. Cryptanalysis and improvement of a secure quantum sealed-bid auction. Opt. Commun. 2009, 282, 4014–4016. [Google Scholar] [CrossRef]
- Yang, Y.G.; Naseri, M.; Wen, Q.Y. Improved secure quantum sealed-bid auction. Opt. Commun. 2009, 282, 4167–4170. [Google Scholar] [CrossRef]
- Zhao, Z.W.; Naseri, M.; Zheng, Y.Q. Secure quantum sealed-bid auction with post confirmation. Opt. Commun. 2010, 283, 3194–3197. [Google Scholar] [CrossRef]
- Xu, G.A.; Zhao, Z.W.; Chen, X.B.; Yang, Y.X. Cryptanalysis and improvement of the secure quantum sealed-bid auction with postconfirmation. Int. J. Theor. Phys. 2011, 9, 1383–1392. [Google Scholar] [CrossRef]
- He, L.B.; Huang, L.S.; Yang, W.; Xu, R.; Han, D.Q. Cryptanalysis and melioration of secure quantum sealed-bid auction with post-confirmation. Quantum Inf. Process. 2012, 11, 1359–1369. [Google Scholar] [CrossRef]
- Wang, Z.Y. Quantum secure direct communication and quantum sealed bid auction with EPR pairs. Commun. Theor. Phys. 2010, 54, 997–1002. [Google Scholar] [CrossRef]
- Liu, W.J.; Wang, F.; Sai, J.; Qu, Z.G.; Wang, X.J. Attacks and improvement of quantum sealed-bid auction with EPR pairs. Commun. Theor.Phys. 2014, 61, 686–690. [Google Scholar] [CrossRef]
- Liu, W.J.; Wang, H.B.; Yuan, G.L.; Xu, Y.; Chen, Z.Y.; An, X.X.; Ji, F.G.; Gnitou, G.T. Multiparty quantum sealed-bid auction using single photons as message carrier. Quantum Inf. Process. 2015, 15, 869–879. [Google Scholar] [CrossRef]
- Zhang, K.J.; Kwek, L.C.; Ma, C.G.; Zhang, L.; Sun, H.W. Security analysis with improved design of post-confirmation mechanism for quantum sealed-bid auction with single photons. Quantum Inf. Process. 2018, 17, 38. [Google Scholar] [CrossRef]
- Han, X.Q. Quantum Sealed-Bid Auction Protocol Based on Semi-honest Model. Int. J. Theor. Phys. 2020, 59, 3778–3788. [Google Scholar] [CrossRef]
- Gao, W.; Shi, R.H.; Wu, M. A privacy-preserving quantum sealed-bid auction protocol with EPR pairs. Quantum Inf. Process. 2022, 21, 1. [Google Scholar] [CrossRef]
- Luo, Y.; Zhao, Z.W.; Zhao, Z.J.; Long, H.M.; Su, W.; Yang, Y.X. The loophole of the improved secure quantum sealed-bid auction with post confirmation and solution. Quantum Inf. Process. 2013, 12, 295–302. [Google Scholar] [CrossRef]
- Wang, Q.L.; Zhang, W.W.; Su, Q. Revisiting “The loophole of the improved secure quantum sealed-bid auction with post-confirmation and solution”. Int. J. Theor. Phys. 2014, 53, 3147–3153. [Google Scholar] [CrossRef]
- Wang, J.T.; Chen, X.B.; Xu, G.; Meng, X.H.; Yang, Y.X. A new quantum sealed-bid auction protocol with secret order in post-confirmation. Quantum Inf. Process. 2015, 14, 3899–3911. [Google Scholar] [CrossRef]
- Zhang, R.; Shi, R.H.; Qin, J.Q. An economic and feasible Quantum Sealed-bid Auction protocol. Quantum Inf. Process. 2018, 17, 35. [Google Scholar] [CrossRef]
- Shi, R.H.; Li, Y.F. A Feasible Quantum Sealed-Bid Auction Scheme without an Auctioneer. IEEE Trans. Quantum Eng. 2022, 3, 2100212. [Google Scholar] [CrossRef]
- Wang, J.T.; Pan, Y.; Liu, W.; Li, Z.Z. Quantum sealed-bid auction protocol based on quantum secret sharing. Quantum Inf. Process. 2022, 21, 278. [Google Scholar] [CrossRef]
- Yu, S.; Oh, C.H. Detecting the local indistinguishability of maximally entangled states. arXiv 2015, arXiv:1502.01274. [Google Scholar]
- Guo, G.P.; Li, C.F.; Shi, B.S.; Li, J.; Guo, G.C. Quantum key distribution scheme with orthogonal product states. Phys. Rev. A 2001, 64, 042301. [Google Scholar] [CrossRef]
- Jiang, D.H.; Wang, J.; Liang, X.Q.; Xu, G.B.; Qi, H.F. Quantum voting scheme based on locally indistinguishable orthogonal product states. Int. J. Theor. Phys. 2020, 59, 436–444. [Google Scholar] [CrossRef]
- Jiang, D.H.; Hu, Q.Z.; Liang, X.Q.; Xu, G.B. A trusted third-party E-payment protocol based on locally indistinguishable orthogonal product states. Int. J. Theor. Phys. 2020, 59, 1442–1450. [Google Scholar] [CrossRef]
- Fu, S.J.; Zhang, K.J.; Zhang, L.; Hou, K.C. A new non-entangled quantum secret sharing protocol among different nodes in further quantum networks. Front. Phys. 2022, 10, 1021113. [Google Scholar] [CrossRef]
- Liu, G.; Zhang, J.Z.; Xie, S.C. Multiparty Sealed-Bid Auction Protocol Based on the Correlation of Four-Particle Entangled State. Int. J. Theor. Phys. 2018, 57, 3141–3148. [Google Scholar] [CrossRef]
- Bennett, C.H.; DiVincenzo, D.P.; Fuchs, C.A.; Mor, T.; Rains, E.; Shor, P.W.; Smolin, J.A.; Wootters, W.K. Quantum nonlocality without entanglement. Phys. Rev. A 1999, 59, 1070. [Google Scholar] [CrossRef]
- Hogg, T.; Harsha, P.; Chen, K.Y. Quantum auctions. Int. J. Theor. Phys. 2007, 5, 751–780. [Google Scholar] [CrossRef]

| The Quantum Sequence of Encoding | |
|---|---|
| 000 | |
| 001 | |
| 010 | |
| 011 | |
| 100 | |
| 101 | |
| 110 | |
| 111 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, S.; Zhang, L.; Sun, Z.; Dai, D.; Hou, K. A New Quantum Sealed-Bid Auction Protocol with a Set of Local Indistinguishable Orthogonal Product States. Photonics 2023, 10, 807. https://doi.org/10.3390/photonics10070807
Wang S, Zhang L, Sun Z, Dai D, Hou K. A New Quantum Sealed-Bid Auction Protocol with a Set of Local Indistinguishable Orthogonal Product States. Photonics. 2023; 10(7):807. https://doi.org/10.3390/photonics10070807
Chicago/Turabian StyleWang, Sainan, Long Zhang, Zhiwei Sun, Daxin Dai, and Kunchi Hou. 2023. "A New Quantum Sealed-Bid Auction Protocol with a Set of Local Indistinguishable Orthogonal Product States" Photonics 10, no. 7: 807. https://doi.org/10.3390/photonics10070807
APA StyleWang, S., Zhang, L., Sun, Z., Dai, D., & Hou, K. (2023). A New Quantum Sealed-Bid Auction Protocol with a Set of Local Indistinguishable Orthogonal Product States. Photonics, 10(7), 807. https://doi.org/10.3390/photonics10070807






