Abstract
In quantum secure multi-party summation protocols, some attackers can impersonate legitimate participants in the summation process, and easily steal the summation results from the participants. This is often overlooked for existing secure multi-party summation protocols, thus rendering them insecure. Based on commutative encryption, a quantum secure multi-party summation protocol with identity authentication is proposed in this paper. In the protocol, each participant encodes a secret integer on photons via unitary operations. At the same time, a one-way hash function technique with a key is utilized to perform identity authentication operations for each participant. Finally, the summation is calculated with the help of a semi-trusted third party. The analysis of the protocol shows that the proposed protocol is correct and resistant to common and impersonation attacks. Compared to related protocols, the use and measurement of single photons makes the protocol easier to implement into existing technology. Furthermore, the simulation experiments on the IBM Q Experience cloud platform demonstrate the effectiveness of the presented protocol.
1. Introduction
With the rapid development of information technology, the demand for security and privacy of information transmission is increasing. The confidentiality of encryption is no longer reliable as classical communication encryption methods are gradually being breached. In order to ensure the security of information, quantum information and quantum computing have gradually become a hot topic of concern. Quantum mechanics, as the theoretical foundation of this information transmission method, is significantly different from classical physics. Its basic principles include the uncertainty principle, non-cloning, superposition principle, and quantum entanglement, etc. These principles provide theoretical support for quantum communication. Photons are the most versatile quantum carrier as they are easy to generate, manipulate, and transmit over long distances through free-space or fiber channels [1]. Moreover, they have unique properties such as non-cloning and measurement interference. The control and measurement of photon states are crucial to ensure the security and reliable transmission of information. Therefore, the role of photons in quantum communication is of great significance. Quantum communication includes various protocols and applications, such as quantum key distribution (QKD) [2,3,4,5,6,7,8,9,10,11,12], quantum secret sharing (QSS) [13,14,15], quantum key agreement (QKA) [16,17,18], quantum private query (QPQ) [19,20,21], quantum multi-party computation (QMC) [22,23,24,25,26], and so on.
Secure multi-party summation (SMS) is a special primitive of secure multi-party computing (MPC), which was proposed by Goldreich [27] in 1987. It aims to accomplish the task of correctly calculating the sum of the secret integers of multiple participants without exposing the secret integers. Heinrich et al. first studied sequence summation in the quantum environment [28,29,30]. Since then, an increasing number of researchers have begun to explore this topic, and various quantum secure multi-party summation (QSMS) protocols have been proposed [31,32,33,34,35,36,37,38,39,40,41,42,43,44,45,46]. In 2006, Hillery et al. [31] put forward the first multi-party summation protocol using two-particle n-dimensional entangled states. Later, Chen et al. [32] presented a secure summation protocol based on multi-particle GHZ entangled states. The protocol encodes the Bell-based measurements of all participants into a single classical bit, which reduces the overhead of the classical channel. In 2014, Zhang et al. [33] designed a quantum summation protocol based on single photons in both polarization and spatial-mode degrees of freedom. In the protocol, participants can independently encode their private information on the polarisation and spatial-mode states of single photons. Shi et al. [34] proposed summation and multiplication protocols using quantum Fourier transform in 2016. These two protocols utilized entangled state as information carrier, and also makes use of CNOT gates and oracle operators to implement modulo d operation. Subsequently, Liu et al. [37] presented a quantum secure summation, which utilizes 2-particle Bell states as information carrier. Immediately afterwards, Yang et al. [39] proposed a quantum security summation protocol using n-particle d-dimensional entangled states. In this protocol, the first participant is semi-honest. Unfortunately, Zhang et al. [42] pointed out that the protocol was insecure and proposed an improved protocol. Recently, depending on some properties of Grover’s search algorithm, Zhang et al. [45] put forward a quantum secure multi-party summation protocol. In this protocol, each participant’s secret input is encoded onto a unitary operation on the travelling two-qubit state, and a summation is achieved with the help of a semi-trusted third party.
However, the above proposed QSMS protocols ignore the issue of authentication in their design process. In an unauthenticated SMS protocol, a malicious attacker can impersonate a legitimate participant to execute the protocol together and send a forged message to the legitimate participant, thus stealing the summation result or the secret information of the other participants. This results in the disclosure of secret information and reduces the security of the protocol. Therefore, authentication is also an important part of ensuring the secure execution of SMS protocols. Various authentication schemes have been proposed in classical SMS or SMC protocols, such as [47,48]. Similarly, when exploiting quantum properties to improve the security of SMS protocols, the authentication security of the participants is also urgent to be enhanced. Furthermore, the above QSMS protocol utilises multi-particle entangled states in calculating the sum of participant secrets, and its preparation and storage is undoubtedly difficult with current technology. Consequently, it is worthwhile to investigate how to design a secure multi-party summation protocol with authentication and easy implementation in the current quantum technology background.
Considering existing technical conditions, we propose an authenticated QSMS protocol based on exchange encryption in this paper. In this protocol, each participant has an identification and shares an encryption key with a semi-trusted third party, who prepares single photos as information carriers. First, the third party performs an identity encoding operation on the photos using a one-way hash function technique with a key. Then, all participants encode the secret integer and perform the identity authentication operation on photons in order. Finally, with the help of the semi-trusted third party, the participants complete their identity authentication and obtain the summation result of their secret integers. Compared to related protocols, the proposed protocol is not only feasible with current technology, but can also resist impersonation attacks, which increases the practicality of the protocol.
The rest of the paper is organized as follows. In Section 2, we briefly introduce the idea of commutative encryption. Then, an authenticated QSMS protocol based on commutative encryption is described and given as an example in Section 3. In Section 4, the correctness and security of the proposed protocol are analyzed, and our protocol is compared with the existing protocols. In Section 5, simulation experiments are conducted on the IBM Q Experience cloud platform to confirm the feasibility of the proposed protocol. Finally, a brief conclusion is given in Section 6.
2. Quantum Commutative Encryption
In this section, we introduce the idea of quantum commutative encryption [49], which will be used in the proposed quantum secure multi-party summation protocol. In our protocol, the horizontally polarised photon signifies binary 0, the vertically polarised photon denotes binary 1. All transmitted polarised photons are encrypted before they are transmitted. The encryption key is defined as a set of angles for an N-bit message. Here the subscript j indicates the position in the message where the encryption with the angle is applied, and the encryption is defined as a rotation operation. represents data M is encrypted with a secret key K. In order to obtain the correct initial photon, the receiver has to rotate the encrypted photon with the opposite angle of to decrypt the encrypted photon. indicates the decryption of the data M using a secret key K. The process of encryption and decryption is described mathematically as follows.
For simplicity, we assume that the message M is a single photon encoded as . The rotation operation used can be represented by the following matrix.
After encrypting the quantum state with , we get the quantum state
where , . In order to recover the message M, we need to rotate the photon by the angle in the opposite direction of , and the decryption process is shown below.
Since - is a global phase which has no observable effect on the quantum state, it is neglected in the paper. Thus, Equation (3) can eventually be abbreviated to . That is, the decryption is carried out to obtain the initial quantum state .
The main advantage of this encryption/decryption scheme is that when the quantum state is encrypted j () times, we do not have to decrypt the ciphertext in exactly the opposite order as when it is encrypted with a different key, as follows.
Obviously, the encrypted data are independent of the order of encryption. The commutation relationship for decryption is also unimportant. In short, even if we first encrypt a message with and then encrypt it with , when decrypting it, we can first decrypt the ciphertext with and then decrypt it with , as shown in Equation (5).
It should be noted that for Equation (4), we need to calculate the final resulting quantum state based on the parity of N, which has the following form.
Furthermore, there is a commutative relationship between the rotation operation and the Pauli operator X:
where . It is worth noting that, when the values of are, respectively, , there exist four special rotation operations, which are
There exists an interesting property of these four rotation operations. That is, when , any two operations and are not fully distinguishable [50], where, . For example, two operations and are required to be discriminated. We can assume that is a given input state. According to the Refs. [51,52], it can be known that the minimum error probability of distinguishing and is
Here, we minimize the overlap of by choosing an appropriate . can be represented by using the eigenvector of as the basis [50], that is, . Then, we define
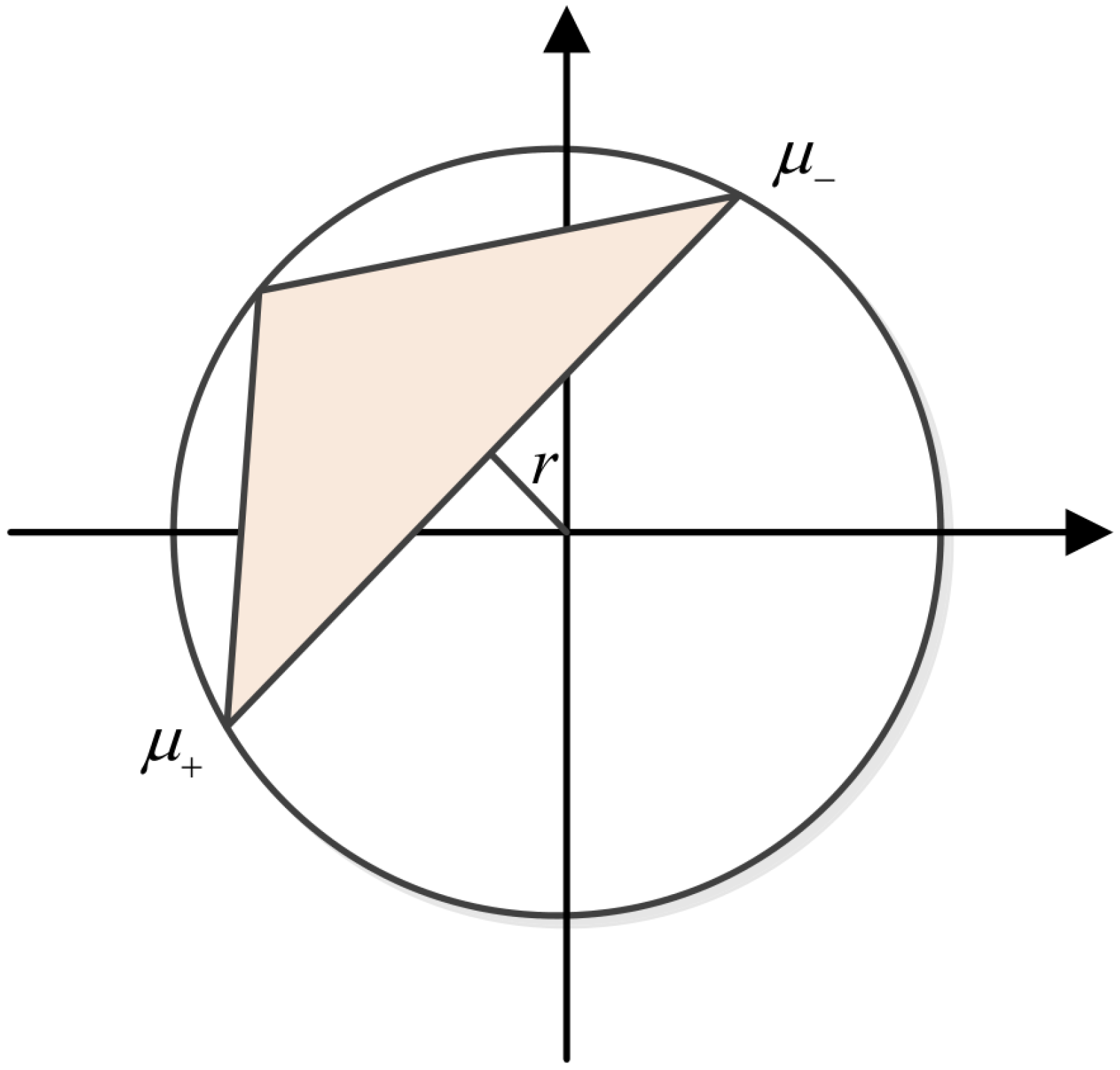
where, are the eigenvalues of . The normalization condition for is , and thus the subset ( is a plural) described by under varying is a convex polygon with points as its vertices. The minimum overlap
is the distance of from , as shown in Figure 1. Figure 1 illustrates in a simple way the best that can be done in distinguishing between and : if M contains the origin, then the two operations can be completely distinguished, otherwise the point in M closest to the origin must be found, and the minimum error probability is related to its distance from the origin. Once the best point in M is found, the best state are those corresponding that point by Equation (10).
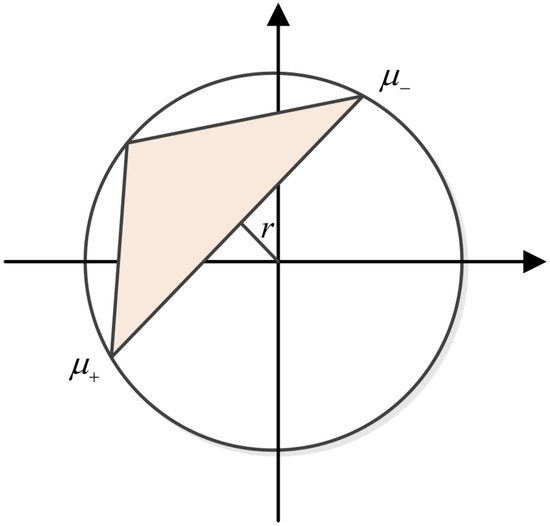
Figure 1.
r is the minimum distance between the origin and the polygon M.
If is the angular distribution of the eigenvalues of (see Figure 1, it is ), from Equation (9), for , we have
While for , we have and the discrimination is exact.
In order to acquire the minimum overlap , we first compute the eigenvalues of and get
Then, the following equation can be derived,
When , Equation (14) holds. Consequently, the minimum error probability of distinguishing between and is . In the same way, we can gain . Therefore, each set of rotation operations , , , cannot be completely distinguished from each other, and this property between them provides a safeguard against the leakage of secret information during the transmission of particles.
3. Quantum Secure Multi-Party Summation Protocol
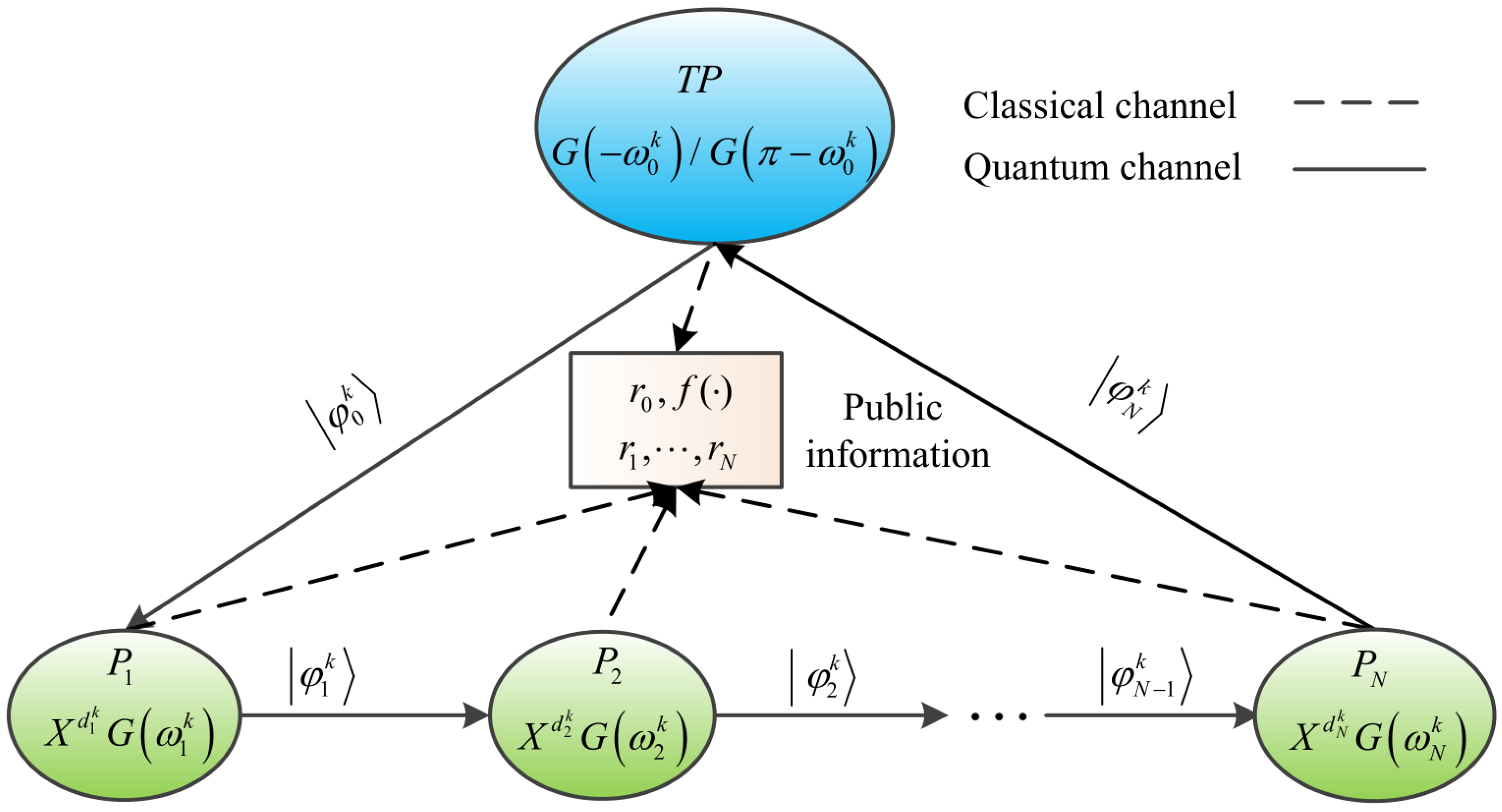
In the protocol, there is a third party TP and N mutually distrustful participants (). TP is semi-trusted [53], which means that they may misbehave alone, but will not collude with anyone. is dishonest [53] who tries to steal secret information from other honest participants. Each participant has a personal identification and a secret integer of length L. Here, is randomly generated and disclosed by each participant, and , . In order to ensure the legitimacy of the participants identity, it is necessary for to complete the authentication with the help of TP, who shares a private key with . Then, through performing the protocol, all participants are able to calculate the summation of their secret integers as shown Equation (15), without revealing their secret integers. The flowchart of the protocol is shown in Figure 2.
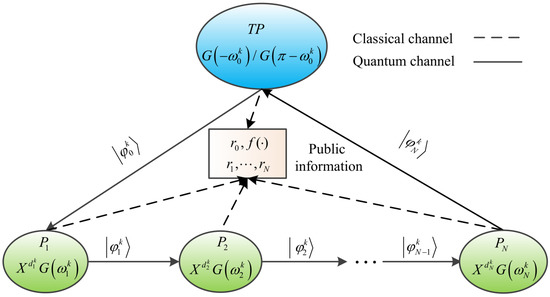
Figure 2.
The process of quantum secure multi-party summation protocol. First, TP performs authentication operation on quantum state () to get . Second, N participants can alternately complete encoding operation and authentication operation on the encrypted sequence while obtaining the operated encrypted sequence. Third, the last participant sends the operated encrypted sequence to TP. Finally, after the N participants have completed identity authentication, TP can calculate the secret summation result of the N participants. Here, () is the encoding operation, and () are authentication operations.
In the proposed protocol, photons are used as quantum bits to transmit information, and there are some quantum channels and classical channels that are used to transmitted particles and classical messages among the participants. Here, all quantum channels are public, and classical channels are almost public. In other words, the classical messages transmitted in the classical channels cannot be tampered, but the attacker is allowed to eavesdrop on the messages and to send fake messages by impersonating other participants. The specific steps of the protocol are described as follows.
Step 1: TP and () generate a random bit string and , respectively, while making these bit strings public. Then, TP selects a hash function from hash clusters and declares it. f is a one-way hash function that works in one direction. It is easy to compute its hash value from the pre-mapped value , but it is hard to generate a pre-mapped value such that its hash value (y is a fixed value). A good hash function is conflict-free, that is, it is hard to generate two different pre-mapped values and such that their hash values . In general, in order to ensure that a hash function does not collide, it is required to output a minimum length of 80 bits [18]. Here, some common hash functions (e.g., SHA-1 or MD5) are used to generate the identity information of TP and each participant . Subsequently, TP and compute their hash value . For binary bit string (), which is encoded as follows.
where, .
Step 2: TP and (), respectively, produces a random number and of length , with , . According to the bit string , TP prepares a sequence of quantum states . Concretely, if , then ; otherwise .
Step 3: TP calculates , where ⊞ denotes operation. Then, TP performs authentication encoding operation on the k-th photon in the sequence Q based on . Specifically, if N is odd, TP executes operation on the photon ; if N is even, TP carries out operation on . The sequence of quantum states after authentication encoding operation is labelled . After that, TP sends it to .
Step 4: Upon receiving the sequence , performs an encryption operation on the quantum state sequence based on . Concretely, if , he implements I operation on the k-th photon, otherwise, he performs X operation on the k-th photon. Then, in accordance with , executes identity authentication operation on the k-th quantum state in the sequence . The encrypted new quantum state sequence is marked as , which is sent to by .
Step 5: After receiving the sequence from , repeats the same procedure as does in step 4. That is, he encrypts the random number into the sequence , and then performs the identity encoding operation on the k-th photon in according to , obtaining a new sequence . Afterward, sends the sequence to . If , the last participant, , sends the sequence to TP.
Step 6: Once receiving the photon sequence , TP measures it using a set of base and gains the measurement . By computing
TP obtains the calculation results .
Step 7: () authenticates the identification of the other participants (), detects whether there is impersonal behaviour during the execution of the protocol. Specifically, randomly selects photons from photons as detection photons and announces their positions. Then, he asks TP to publish corresponding to the positions of the detection photons in U, while asking the participants to announce corresponding to the positions of the detected photons in . The order of publication of the participants is decided by at random. determines whether the equation holds, and calculates the error rate. If the error rate is lower than the pre-set threshold, considers that participants executing the protocol with them are indeed the participants ; otherwise, he considers that there is impersonal behaviour among the participants, and terminates the protocol.
Step 8: () removes corresponding to the detected photons in . The bits at the remaining positions are noted as . Subsequently, calculates and publishes , with , .
Step 9: TP discards the declared and records the remaining calculation as . Then, he calculates the summation
Finally, TP announces the summation result .
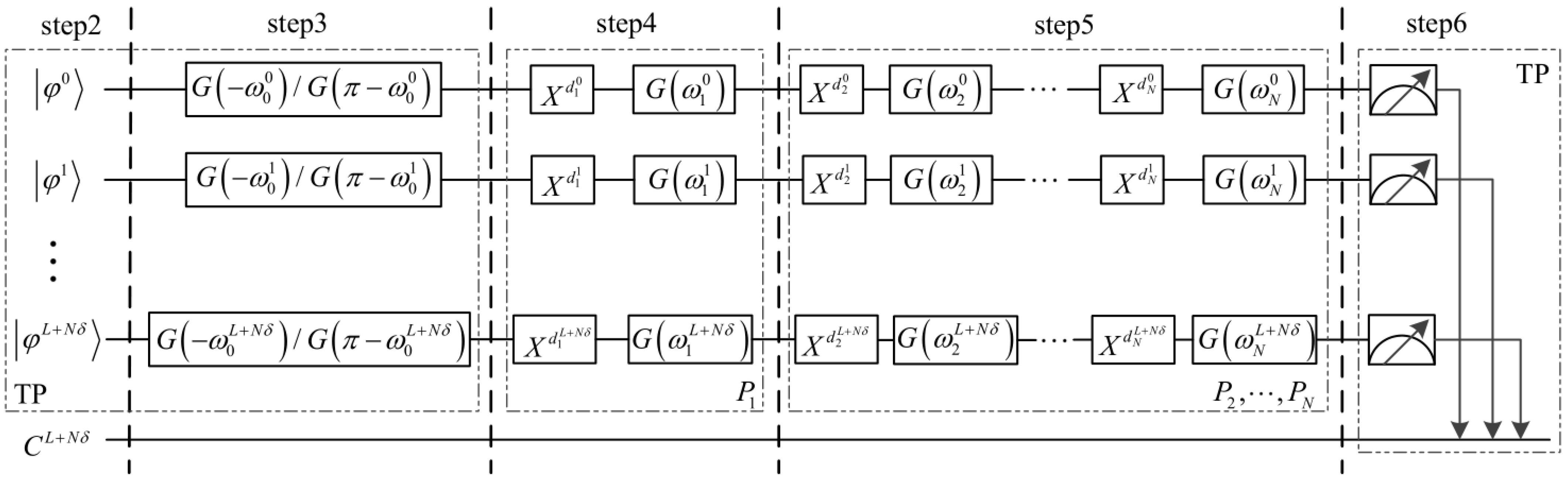
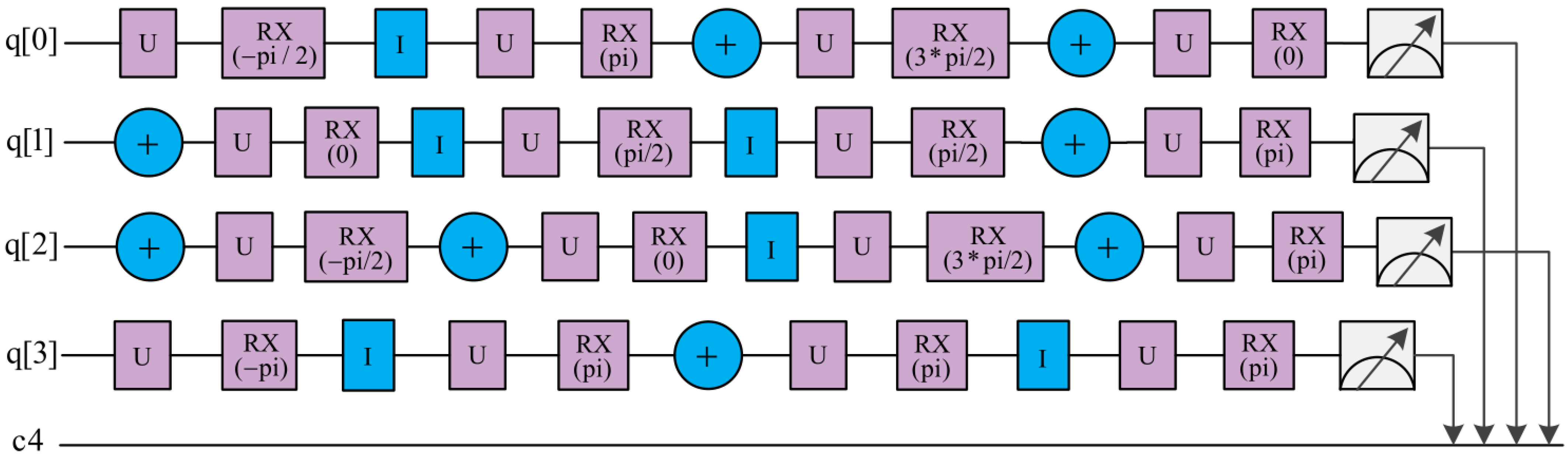
Through the above steps 1 to 9, all participants can obtain the sum of their secret integer. In order to better understand the process of the proposed protocol, we design its quantum circuit, as shown in Figure 3. Simultaneously, an example containing three participants (i.e., ) is given. For the sake of convenience, the detection particles in the protocol are ignored. In this example, there are three participants , and , who, respectively, have secret integer , , of length 4 (i.e., ) and identification , , with length 8. Through conducting the above protocol, they evaluate the sum of the secret integers. The relevant information involved in the example of the three participants is shown in Table 1.
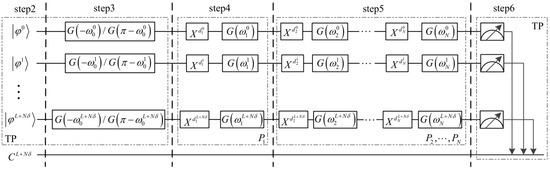
Figure 3.
The quantum circuit of the proposed protocol. First, TP performs authentication operations on the quantum sequence . Then, each participant encodes into the quantum sequence by performing the encoding operation, and applies the authentication operation to encrypt the sequence which is subsequently sent to the next participant. Finally, TP measures each qubit in the computational basis.

Table 1.
The relevant information involved in the examples of the three participants (- indicates no.).
In the protocol, TP prepares a quantum sequence based on . In step 3, TP calculates . Then, according to it, he executes the authentication operation on the sequence Q to yield the sequence . After that, TP sends to . In step 4, when receives the sequence from TP, he performs the corresponding encoding operations based on and . Similarly, and perform the corresponding encrypted operations. The encoding operations on the quantum sequence and the change of the quantum states are shown in Table 2.

Table 2.
Encoding operations on the quantum sequence.
4. Protocol Analysis
In this section, the correctness and security of the proposed protocol are firstly analyzed. Then, we compare the proposed protocol with the previous protocols.
4.1. Correctness
For a QSMS protocol, its correctness implies that all participants honestly execute the protocol and obtain the sum of their secret integer without revealing any secrets. Suppose the initial signal photon prepared by TP is , . In step 3, TP computes , and performs the identity encoding operation on the signal photon based on to obtain . In steps 4 and 5, when the N participants have completed encryption operation and the identity authentication operation on in turn according to and , the final signal photon is in state . Since TP needs to perform different identity authentication operations on the signal photon depending on the parity of N, we discuss the final quantum state in the following two cases.
(1) When N is an odd number, the identity authentication operation performed by TP on the signal photon is . Depending on Equation (6), it is known that the final quantum state evolves as
(2) When N is an even number, The identity authentication operation executed by TP on the signal photon is . Similarly, according to Equation (6), we can get the final quantum state as shown below.
It can be seen from the above analysis that without considering the global phase, no matter whether N is odd or even, TP can eventually gain the quantum state . Then, he measures it with the base and gets the measurement result . On the basis of Equations (17) and (18) and () published by all participants, we can gain the summation result , . In summary, the proposed protocol is correct.
4.2. Security
In this section, we first prove that the encoded quantum states in our protocol cannot be unambiguous discriminated (i.e., Theorem 1). Then, on that basis, the proposed protocol is shown to be secure under common external and internal attacks. Furthermore, it is demonstrated that our proposed protocol is resistant to Trojan horse attacks and impersonation attacks.
Theorem 1.
In this protocol, when four different authentication operations , , , are, respectively, applied to a certain quantum state of the transmission, the resulting quantum states cannot be unambiguous discriminated. That is, there is a linear correlation between the encrypted quantum states.
Proof of Theorem 1.
Since the initial quantum states change continuously and are in one of the four quantum states during the execution of the protocol, where . Without loss of generality, we assume that the k-th () particle in the hands of () is in state
Then, encodes the random number into the photon . After that, he executes the identity authentication operation on the photon depending on , and gets a new quantum state . Based on Equation (16), the new quantum state is in one of the following four quantum states.
By simple calculation, we gather that there are linear correlations between the above four encrypted quantum states:
As Chefles et al. [54] said, the necessary and sufficient condition for distinguishing the quantum states is that they are linearly independent. Therefore, these linearly correlated quantum states cannot be unambiguous discriminated. □
4.2.1. External Attack
Suppose Eve is an external attacker, and she wants to eavesdrop on the secret integer and the private key without being detected. In the proposed protocol, the private key is shared between TP and , and it is used to compute the hash value . Then, performs the identity encoding on the sequence based on . In the presented protocol, the hash function , the identification , the random bit strings and are publicly. Since does not disclose their hash value , Eve cannot infer any information about from these publicly available information. The secret integer , is exposed by in step 8, so Eve can only obtain information about that he first needs to obtain in order to obtain . Since is encoded in the traveling photon, Eve has to attack the travelling photon sequence to obtain and of . Next, we consider some common external attacks as well as Trojan Horse attacks.
- (1)
- Intercept resend attack
In this attack, suppose that Eve intercepts a sequence of photons sent by and resends a sequence of pseudo photons to . Since the detection photons are included in the sequence of travelling photons, these detection photons are randomly in one of the four states after the encoding operation. Eve does not know the position and state of these detection photons, thus her attack would inevitably introduce some errors and will be detected with a probability of in step 7. When is large enough, the probability converges to 1. Despite this, Eve still hopes to infer the secret key and of . However, this is unsuccessful. In the following, we analyse the case where Eve has access to and while avoiding detection.
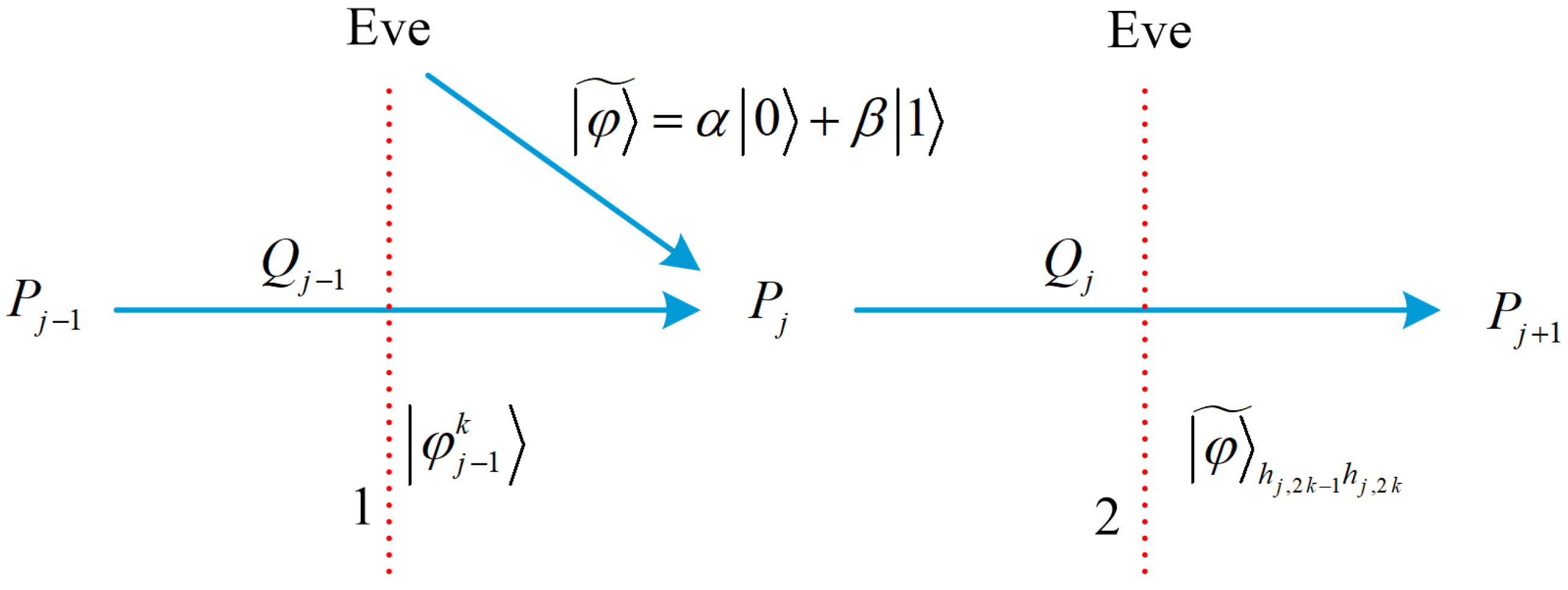
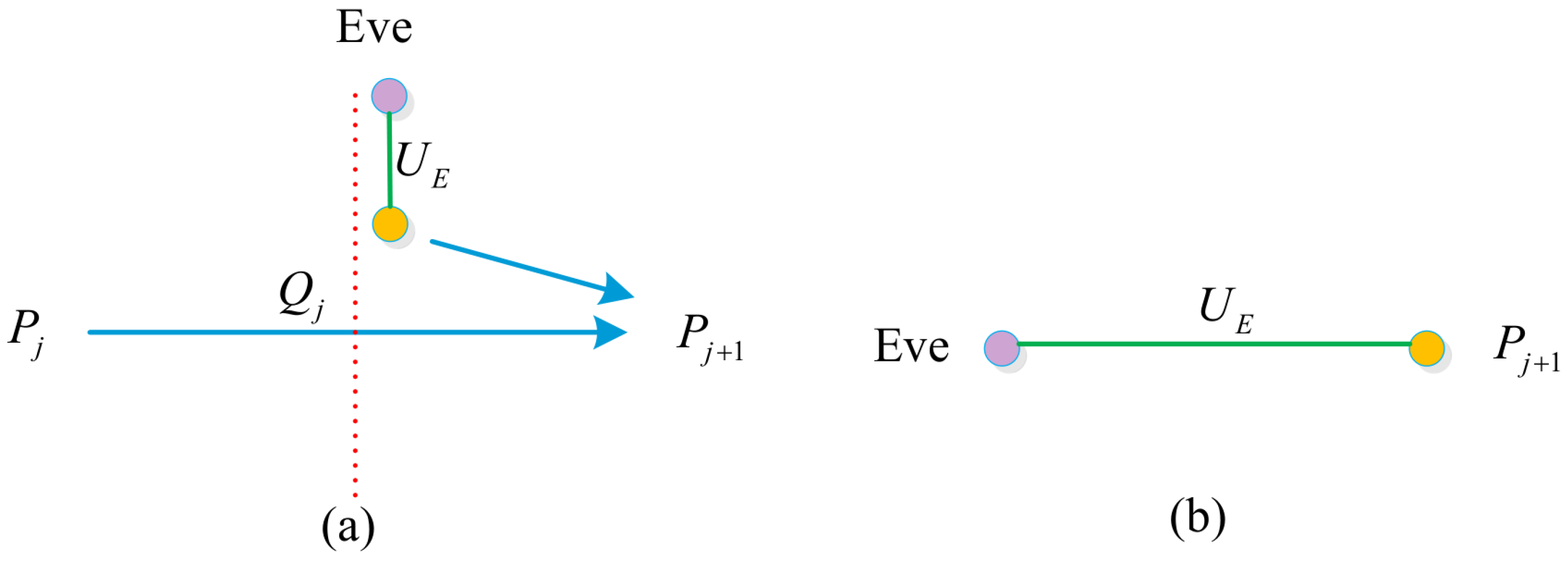
Since is encoded in the signal photons of the sequence , Eve can only obtain information about by attacking the signal photons of . Suppose that the k-th photon intercepted by Eve is the signal photon of , and resent a fake quantum state to . According to the random number and the hash value , executes the encryption operation and the identity authentication operation on the fake quantum state in turn. He gets a new quantum state , as shown in Table 3. Afterwards, Eve intercepts and measures it to distinguish which operation is performed by . The process of Eve performing intercept resend attack is shown in Figure 4.

Table 3.
Quantum states after different encoding operations on pseudo quantum state.
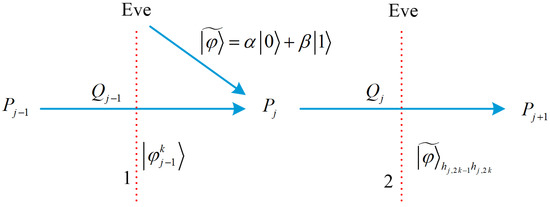
Figure 4.
The running process of Eve performing intercept resend attack. The red dashed lines 1 and 2 indicates that Eve intercepts photons and , respectively, the blue solid line indicates transmitting photons.
In order to distinguish the operation of , Eve first requires to distinguish the above four encrypted quantum states. From Theorem 1, the above four quantum states cannot be unambiguous discriminated. That is, Eve cannot distinguish between the encoded operation and the identity authentication operation performed by . Therefore, she cannot infer and , nor can she infer from the public information. In a word, the proposed protocol can resist intercept resend attack.
- (2)
- Entangle measure attack
In this attack, assume that Eve intercepts a signal photon sent by and prepares an additional photon . She then performs an entanglement operation on the signal photon and the additional photon , and sends the intercepted signal photon to . Subsequently, encodes their secret data into the signal photon, and performs an identity authentication operation on it based on . Finally, Eve deduces the private key and the secret message by measuring the additional photon. The process of entangle measure attack performed by Eve is shown in Figure 5. However, this attack is not possible, the detailed analysis is as follows.
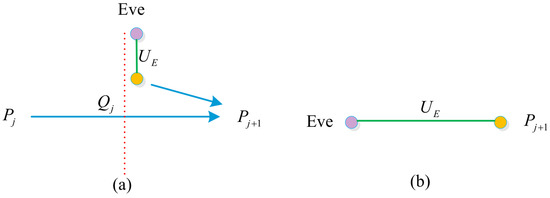
Figure 5.
The running process of Eve performing entangle measure attack. (a) Eve entangles an additional photon. (b) Eve and share an entangled state. The red dashed line indicates that Eve intercepts a photon , which is indicated by an orange dot. The purple dot indicates Eve’s additional particle . The blue solid line indicates the transmitting particle.
The effect of Eve’s unitary operation on the signal photons and additional photons as shown below.
Here, are the four states uniquely determined by unitary operation , and the four coefficients satisfy . If Eve does not introduce errors, then needs to satisfy the following conditions.
From the Equations (24) and (25), we can obtain that .
Without loss of generality, suppose the signal photon is shown in Equation (21). After acts on the signal photon and the additional photon , the resulting state of the whole system is
In step 5, when has completed the encryption operation and the identity authentication operation on the signal photon based on and , the whole quantum system is in one of the four states:
After a simple calculation, we can rewrite four states of Equation (27) as
We find that there are linear correlations between the four quantum states:
According to Theorem 1, these encrypted quantum states cannot be unambiguously distinguished. Therefore, Eve cannot obtain any information about the secret information and the private key through the entanglement measurement attack. In summary, the entangle measure attack is invalid for our protocol.
- (3)
- Trojan Horse attacks
Since the proposed protocol transports photons over more than once, it may be insecure against two types of Trojan horse attacks, namely, delayed photon attacks [55] and invisible photon attacks [56]. To prevent these two types of attacks, the participants can install some special quantum optical devices such as wavelength quantum filters and photon number splitters during the execution of the protocol. For invisible photons that appear during transmission, they can be filtered out using a wavelength quantum filter. Meanwhile, for the delayed photons that appear in it, the photon number splitters can be used to split each legitimate photon to discover it. In short, with the addition of the two devices, both the invisible photon attack and the delayed photon attack appearing in the presented protocol will fail.
4.2.2. Internal Attack
Compared to external attackers, internal participants are more destructive because they have greater privileges than external attackers to gain access to the secret information of other participants. In addition to analysing some common internal attacks, we also analyse impersonation attacks.
- (1)
- A dishonest participant’s attack
Since all participants play the same role in our protocol, we can assume that is dishonest, noted as . He tries to steal secret input from and sends a pseudophoton sequence F to . Then, performs the encoding and identity authentication operation on the sequence F and gets the photon sequence , then he sends it to . At this point, attacks the photon sequence to distinguish the operations. Since does not know the positions and states of the decoy photons in the sequence , their attack will be detected in step 7 just like the external attacker, Eve. Therefore, such an attack would be ineffective against our protocol.
- (2)
- Dishonest participants’ collusion attack
In this attack, there may be two or more dishonest participants who want to collectively steal the secret input of other honest participants. Without loss of generality, suppose and are dishonest participants, who are denoted as and . Obviously, it is easier for them to conspire to steal the secret integer of than that of other participants. In collusion attack, both and need to intercept the photons in the transmission sequence and retransmit a fake sequence to and , respectively. Since and do not know the positions and states of the decoy photons, their attack will be detected in the eavesdropping detection. Nevertheless, and still want to obtain the secret data of the other honest participants. However, they are unlikely to succeed. The situation where and conspire to attack is discussed as follows.
Here, we consider a more general attack strategy. Suppose the k-th photon in the sequence intercepted by is a signal photon, he keeps it in their hands. Then, he sends a pseudophoton to . encodes the secret data into , and performs the authentication operation on it according to . Subsequently, he sends the resulting new quantum state (as shown in Table 4) to . Since and do not know , they cannot determine which identity authentication operation executes. Therefore, can only distinguish which operation performs by measuring . Because there is a linear relationship similar to Equation (20) for the four quantum states in Table 4, so that cannot distinguish between these four quantum states. Therefore, even if and collude to attack , they cannot infer any information about ’s secret information and private key . To sum up, our protocol is immune to this attack.

Table 4.
Quantum states after different encoding operations on pseudo photons.
- (3)
- A semi-trusted third party’s attack
In the proposed protocol, TP is semi-trusted, which implies that he cannot conspire with the other participants to carry out bad activities, but he can misbehave himself. For convenience, the semi-trusted third party is denoted as , who hopes to gain ’s secret integer . In order to achieve this goal, can intercept the photons sent by and resend a fake photon sequence to . In this case, although can infer the identity encoding operation acting on the pseudo photon based on , he does not know the position of the detection photons in the travelling photon sequence. Therefore, their behaviour introduces errors as Eve does and is detected in step 7. As a conclusion, the proposed protocol is resistant to attacks by semi-trusted third party.
- (4)
- Impersonation attack
In addition to the above attacks, impersonation attack from an adversary should be considered. Depending on the function of the role in the protocol, we can analyze impersonation attack from two aspects.
Case 1: Impersonating the third party
In this attack, an adversary can impersonate a semi-trusted third-party TP to execute the protocol, in which he attempts to attack the participants and obtain their secret integers . For simplicity, the adversary is recorded as . In the semi-honest third-party attack, it has been shown that a genuine third-party TP cannot even gain access to the secret information of the participants, and hence it can be deduced that the impersonated cannot successfully eavesdrop as well. In a word, the proposed protocol is resistant to the attack of impersonating a semi-trusted third party.
Case 2: Impersonating a participant
Here, an adversary can impersonate a participant and executes the protocol with the other participants. The adversary is indicated by . His aim is to eavesdrop the private key , and compute the summation result S while successfully tricking the other participants. However, this is not possible. Because has no knowledge of ’s hash value , thus he cannot deduce the private key from the public information, nor can he perform the correct identity authentication operation. It will result in a change in the final particles obtained by TP, and the results obtained with the base measuring will also be random. Such the behaviour of will be detected in the eavesdropping detection in step 7. Consequently, this attack is ineffective against our protocol.
To sum up, the proposed protocol is resistant to impersonation attacks from the adversary.
4.3. Comparison
We compare the performance of the proposed protocol and the existing QSMS protocols [33,36,37,38,45] in terms of quantum resource, model, function and quantum efficiency, which is shown in Table 5.

Table 5.
Comparison with previous protocols.
As a convenience, we assume that the number of participants in all protocols is N, the semi-trusted third parties involved is TP, and the length of a secret integer is L. When eavesdropping detection is required between two parties, the number of decoy particles they make use of is . The quantum efficiency can be defined as
Here, c denotes the total number of bits in the classical plaintext message, q represents the total number of quantum bits used in the quantum protocol, and b indicates the number of exchanged classical bits used to decode the message.
Although the protocols of Zhang et al. [36] and Zhang et al. [45] initially prepare single-particle and two-particle states, respectively, they both require to generate multi-particle entangled states with unitary operations during the execution of the protocol. However, our protocol adopts quantum resources that exist as single particles throughout the execution of the protocol. In protocols [36,37,45], one of the particles of the entangled state needs to be kept in the hands of the preparer, and the other particles is transmitted as a travelling particle. It has the potential to become unentangled during transmission, which does not guarantee that the secret data of each participant acts on the quantum state to participate in the summation. Furthermore, it is easier to prepare a single-particle state than a multi-particle entangled state on the basis of current technology. Therefore, the proposed protocol has the advantage of quantum resources.
As with the protocols [33,37,38,45], our protocol also requires the help of a semi-trusted third party to implement the sum. However, our protocol has identity authentication function, which can resist impersonation attacks. Compared with Zhang et al.’s protocol [36], the proposed protocol still possesses that advantage. As can be seen from Table 5, even though the quantum efficiency of the proposed protocol is the same as that of the protocol [38], the proposed protocol implements the identity authentication function. The quantum efficiency of the proposed protocol is better with respect to the protocols [33,36,37,45].
To sum up, the proposed protocol has significant advantages in terms of both quantum resource, function and quantum efficiency.
5. Experiments on the IBM Q Experience
In order to confirm the correctness of the proposed protocol, we run the example of the three-party quantum secure summation protocol given in Section 3 on the cloud quantum computing platform provided by IBM Q Experience [57]. In the example, TP prepares a quantum sequence based on the bit string . Then, TP and three participants perform the operations shown in Table 2.
In order to better conduct the experiment, we first need to design the corresponding quantum circuits for the four quantum states of the quantum sequence Q according to Figure 3, which are illustrated in Figure 6.
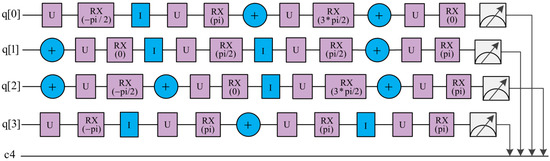
Figure 6.
Quantum circuits corresponding to the quantum sequence . The circuits of the quantum states q[0], q[1], q[2] and q[3] correspond to the initial states , , and in turn.
Here, + and I denote the Pauli operator X and I gates, respectively, and the operations U and are defined in the following form.
Therefore, based on Equation (31), the rotation operation used in the proposed QSMS protocol can be re-expressed as
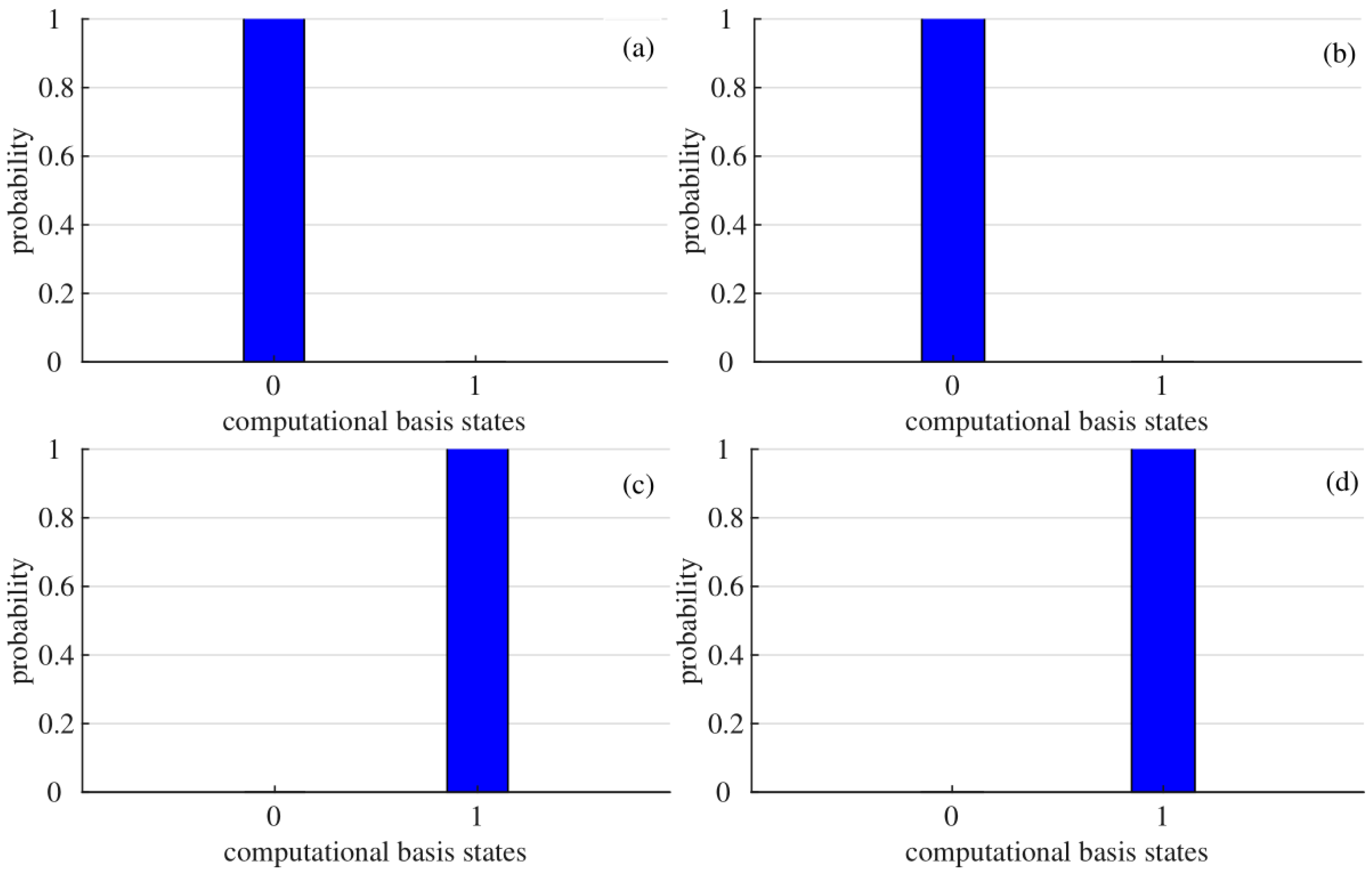
For the sake of improving the accuracy of the experiments, we, respectively, run five rounds for each quantum circuit in Figure 6, each round containing 8192 shots. The corresponding simulation statistics for each circuit are shown in Figure 7.
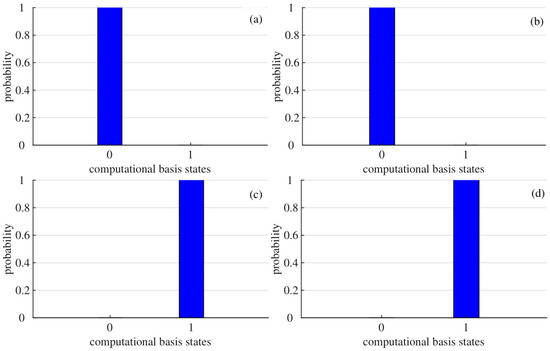
Figure 7.
The measurement results of quantum circuits in Figure 6. The horizontal coordinate indicates computational basis states, 1 denotes and 0 represents ; The vertical coordinate represents the probability of obtaining the computational basis states by measurement. The initial states corresponding to (a–d) are , , , , respectively.
As can be seen from Figure 7, the measured probabilities of obtaining the four final quantum states through simulation experiment, which are compared with the theoretically expected probabilities of gaining the final quantum states in the example given in Section 3, as shown in Table 6.

Table 6.
The comparison between the measured and expected quantum states.
Due to both the expected gained quantum state and the measured state are pure states, we can calculate the fidelity (F) between them based on the Refs. [58,59]. The fidelity between two pure states is defined as
The fidelity F takes the value in [0, 1], which represents the mode of overlap between two pure states [58]. The fidelity between the measured four quantum states and the expected quantum states as shown in Table 6.
From Table 6, it can be seen that the measured probabilities and theoretical expected probabilities of obtaining the final quantum states are consistent, and their fidelity values all equal 1.00. In other words, the simulated experimental results for the quantum sequence turns out to be 100% correct, and the final quantum states obtained by measurement are completely equivalent to the final quantum states obtained theoretically in the example given in Section 3. The measurement result for is . Evidently, depending on the data provided in Table 2, we can obtain . That is, the sum of the secret data of the participants can be correctly obtained by simulation experiments. Therefore, the proposed protocol is feasible.
6. Conclusions
Before deriving our conclusions, we briefly discuss some advantages of the proposed protocol compared with Refs. [33,36,37,38,45]. Firstly, the impersonation attacks that are inevitable in practical applications are considered. Therefore, we exploit the technique of one-way hash function with key, and combine identity information and random strings to achieve the authentication of participants. Secondly, the theory of quantum state indistinguishability guarantees the security of the protocol. Specifically, the encoded quantum states cannot be unambiguously distinguished, hence, the attacker cannot obtain any information about participants’ secret information. Thirdly, our protocol is feasible in technique. The implementation of the protocol only requires preparing single-photon states and performing single-photon measurements. As a result, it is easier to implement with the current technology. Finally, we conduct simulations on the IBM Q Experience cloud platform and confirm that the proposed protocol is effective.
In summary, we propose a QSMS protocol with identity authentication based on commutative encryption. In the protocol, the semi-trusted third party prepares single photons as information carriers, and shares a secret key with each participant. Depending on the calculated hash value, the semi-trusted third party performs the authentication operations on the prepared photons. All the participants then encode their secret integer and perform the authentication operation on the quantum sequence in turn. Finally, all participants calculate the sum of their secret integer with the help of the third party. The analysis of the protocol shows that the proposed protocol is correct, and can resist both common and impersonation attacks. In addition, we verify the proposed protocol on the IBM Q Experience cloud platform. The statistical results and the fidelity of the computed quantum states are 1, which demonstrates the feasibility of the proposed protocol.
Author Contributions
Methodology, N.W.; software, N.W.; validation, N.W.; formal analysis, N.W. and X.Z.; writing—original draft, N.W.; visualization, X.T.; writing—review and editing, S.L.; supervision, S.L.; project administration, S.L.; funding acquisition, S.L. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported by National Natural Science Foundation of China (Grants No. 61772134, No. 61976053, and No. 62171131), Fujian Province Natural Science Foundation (Grant No. 2022J01186), and Program for New Century Excellent Talents in Fujian Province University.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Paraiso, T.K.; Woodward, R.I.; Marangon, D.G.; Lovic, V.; Yuan, Z.; Shields, A.J. Advanced laser technology for quantum communications (tutorial review). Adv. Quantum Tech. 2021, 4, 2100062. [Google Scholar] [CrossRef]
- Ekert, A.K. Quantum cryptography based on Bell’s theorem. Phys. Rev. Lett. 1991, 67, 661. [Google Scholar] [CrossRef] [PubMed]
- Gisin, N.; Ribordy, G.; Tittel, W.; Zbinden, H. Quantum cryptography. Rev. Modern Phys. 2002, 74, 145. [Google Scholar] [CrossRef]
- Cao, Y.; Zhao, Y.; Wang, Q.; Zhang, J.; Ng, S.X.; Hanzo, L. The evolution of quantum key distribution networks: On the road to the qinternet. IEEE Comm. Surv. Tutor. 2022, 24, 839–894. [Google Scholar] [CrossRef]
- Sidhu, J.S.; Brougham, T.; McArthur, D.; Pousa, R.G.; Oi, D.K.L. Finite key effects in satellite quantum key distribution. npj Quantum Inf. 2022, 8, 18. [Google Scholar] [CrossRef]
- Bloom, Y.; Fields, I.; Maslennikov, A.; Rozenman, G.G. Quantum cryptography—A simplified undergraduate experiment and simulation. Physics 2022, 4, 104–123. [Google Scholar] [CrossRef]
- Liu, R.; Rozenman, G.G.; Kundu, N.K.; Chandra, D.; De, D. Towards the industrialisation of quantum key distribution in communication networks: A short survey. IET Quantum Comm. 2022, 3, 151–163. [Google Scholar] [CrossRef]
- Zhong, Z.Q.; Wang, S.; Zhan, X.H.; Yin, Z.-Q.; Chen, W.; Guo, G.-C.; Han, Z.-F. Realistic and general model for quantum key distribution with entangled-photon sources. Phys. Rev. A 2022, 106, 052606. [Google Scholar] [CrossRef]
- Shirko, O.; Askar, S. A novel security survival model for quantum key distribution networks enabled by software-defined networking. IEEE Access 2023, 11, 21641–21654. [Google Scholar] [CrossRef]
- Li, D.D.; Tang, Y.L.; Zhao, Y.K.; Zhou, L.; Zhao, Y.; Tang, S.-B. Security of optical beam splitter in quantum key distribution. Photonics 2022, 9, 527. [Google Scholar] [CrossRef]
- Mafu, M.; Sekga, C.; Senekane, M. Security of Bennett–Brassard 1984 quantum-key distribution under a collective-rotation noise channel. Photonics 2022, 9, 941. [Google Scholar] [CrossRef]
- Jiang, X.L.; Deng, X.Q.; Wang, Y.; Lu, Y.F.; Li, J.-J.; Zhou, C.; Bao, W.-S. Weak randomness analysis of measurement-device-independent quantum key distribution with finite resources. Photonics 2022, 9, 356. [Google Scholar] [CrossRef]
- Hillery, M.; Bužek, V.; Berthiaume, A. Quantum secret sharing. Phys. Rev. A 1999, 59, 1829–1834. [Google Scholar] [CrossRef]
- Karlsson, A.; Koashi, M.; Imoto, N. Quantum entanglement for secret sharing and secret splitting. Phys. Rev. A 1999, 59, 162–168. [Google Scholar] [CrossRef]
- Xiao, L.; Long, G.L.; Deng, F.G.; Pan, J.W. Efficient multiparty quantum-secret-sharing schemes. Phys. Rev. A 2004, 69, 052307. [Google Scholar] [CrossRef]
- Liu, B.; Gao, F.; Huang, W.; Wen, Q.Y. Multiparty quantum key agreement with single particles. Quantum Inf. Process. 2013, 12, 1797–1805. [Google Scholar] [CrossRef]
- Sun, Z.W.; Cheng, R.; Wu, C.H.; Zhang, C. New fair multiparty quantum key agreement secure against collusive attacks. Sci. Rep. 2019, 9, 17177. [Google Scholar] [CrossRef]
- Lin, S.; Zhang, X.; Guo, G.D.; Wang, L.L.; Liu, X.F. Multiparty quantum key agreement. Phys. Rev. A 2021, 104, 042421. [Google Scholar] [CrossRef]
- Liu, B.; Gao, Z.F.; Xiao, D.; Huang, W.; Zhang, Z.-Q.; Li, Y.; Xu, B.-J. QKD-based quantum private query protocol in the single-photon interference communication system. IEEE Access. 2019, 7, 104749–104758. [Google Scholar] [CrossRef]
- Liu, B.; Gao, F.; Huang, W.; Wen, Q.Y. QKD-based quantum private query without a failure probability. Sci. China Phys. Mech. Astr. 2015, 58, 100301. [Google Scholar] [CrossRef]
- Gao, F.; Liu, B.; Wen, Q.Y.; Chen, H. Flexible quantum private queries based on quantum key distribution. Opt. Exp. 2012, 20, 17411–17420. [Google Scholar] [CrossRef] [PubMed]
- Lo, H.K. Insecurity of quantum secure computations. Phys. Rev. A 1997, 56, 1154. [Google Scholar] [CrossRef]
- Chau, H.F. Quantum-classical complexity-security trade off in secure multiparty computations. Phys. Rev. A 2000, 61, 032308. [Google Scholar] [CrossRef]
- Ben-Or, M.; Crépeau, C.; Gottesman, D.; Hassidim, A.; Smith, A. Secure multiparty quantum computation with (only) a strict honest majority. In Proceedings of the 2006 47th Annual IEEE Symposium on Foundations of Computer Science (FOCS’06), Berkeley, CA, USA, 21–24 October 2006; IEEE: New York, NY, USA, 2006; pp. 249–260. [Google Scholar]
- Smith, A. Multi-party Quantum Computation. arXiv 2010, arXiv:quant-ph/0111030. [Google Scholar]
- Shi, R.H.; Li, Y.F. Quantum protocol for secure multiparty logical AND with application to multiparty private set intersection cardinality. IEEE Trans. Circuits Syst. I Reg. Pap. 2022, 69, 5206–5218. [Google Scholar] [CrossRef]
- Goldreich, O.; Micali, S.; Wigderson, A. How to play any mental game. In Proceedings of the Nineteenth Annual ACM Symposium on Theory of Computing; ACM: New York, NY, USA, 1987; p. 218. [Google Scholar]
- Heinrich, S. Quantum summation with an application to integration. J. Complex. 2002, 18, 1. [Google Scholar] [CrossRef]
- Heinrich, S.; Novak, E. On a problem in quantum summation. J. Complex. 2003, 19, 1. [Google Scholar] [CrossRef]
- Heinrich, S.; Kwas, H.; Wozniakowski, M. Quantum Boolean summation with repetitions in the worst-average setting. arXiv 2003, arXiv:quant-ph/0311036. [Google Scholar]
- Hillery, M.; Ziman, M.; Buzĕ˘k, V.; Bielikova, M. Towards quantum-based privacy and voting. Phys. Lett. A 2006, 349, 75. [Google Scholar] [CrossRef]
- Chen, X.B.; Xu, G.; Yang, Y.X.; Wen, Q.Y. An efficient protocol for the secure multi-party quantum summation. Int. J. Theor. Phys. 2010, 49, 2793. [Google Scholar] [CrossRef]
- Zhang, C.; Sun, Z.; Huang, Y.; Long, D. High-capacity quantum summation with single photons in both polarization and spatial-mode degrees of freedom. Int. J. Theor. Phys. 2014, 53, 933–941. [Google Scholar] [CrossRef]
- Shi, R.H.; Mu, Y.; Zhong, H.; Cui, J.; Zhang, S. Secure multiparty quantum computation for summation and multiplication. Sci. Rep. 2016, 6, 19655. [Google Scholar] [CrossRef] [PubMed]
- Shi, R.H.; Zhang, S. Quantum solution to a class of two-party private summation problems. Quantum Inf. Process. 2017, 16, 225. [Google Scholar] [CrossRef]
- Zhang, C.; Situ, H.; Huang, Q.; Yang, P. Multi-party quantum summation without a trusted third party based on single particles. Int. J. Quantum Inf. 2017, 15, 1750010. [Google Scholar] [CrossRef]
- Liu, W.; Wang, Y.B.; Fan, W.Q. An novel protocol for the quantum secure multi-party summation based on two-particle bell states. Int. J. Theor. Phys. 2017, 56, 2783. [Google Scholar] [CrossRef]
- Liu, W.; Ma, M.Y. An dynamic protocol for the quantum secure multi-party summation based on commutative encryption. In Proceedings of the International Conference on Artificial Intelligence and Security; Springer: Cham, Switzerland, 2019; pp. 537–547. [Google Scholar]
- Yang, H.Y.; Ye, T.Y. Secure multi-party quantum summation based on quantum Fourier transform. Quantum Inf. Process. 2018, 17, 129. [Google Scholar] [CrossRef]
- Sutradhar, K.; Om, H. Hybrid quantum protocols for secure multiparty summation and multiplication. Sci. Rep. 2020, 10, 9097. [Google Scholar] [CrossRef]
- Zhang, C.; Razavi, M.; Sun, Z.W.; Situ, H.Z. Improvementn “Secure multi-party quantum summation based on quantum Fourier transform”. Quantum Inf. Process. 2019, 18, 336. [Google Scholar] [CrossRef]
- Zhang, C.; Long, Y.X.; Li, Q. Quantum summation using d-level entanglement swapping. Quantum Inf. Process. 2021, 20, 137. [Google Scholar] [CrossRef]
- Wu, W.Q.; Ma, X.X. Multi-party quantum summation without a third party based on d-dimensional bell states. Quantum Inf. Process. 2021, 20, 200. [Google Scholar] [CrossRef]
- Wang, Y.L.; Hu, P.C.; Xu, Q.L. Quantum secure multi-party summation based on entanglement swapping. Quantum Inf. Process. 2021, 20, 319. [Google Scholar] [CrossRef]
- Zhang, X.; Lin, S.; Guo, G.D. Quantum secure multi-party summation based on Grover’s search algorithm. Int. J. Theor. Phys. 2021, 60, 3711–3721. [Google Scholar] [CrossRef]
- Sutradhar, K.; Om, H. A generalized quantum protocol for secure multiparty summation. IEEE Trans. Circuits Syst. II Exp. Briefs. 2020, 67, 2978–2982. [Google Scholar] [CrossRef]
- Goldreich, O. Secure multi-party computation. Manuscript. Prelim. Vers. 1998, 78, 110. [Google Scholar]
- Brandt, N.; Maier, S.; Müller, T.; Müller-Quade, J. Constructing Secure Multi-Party Computation with Identifiable Abort. Cryptology ePrint Archive. 2020. Available online: https://eprint.iacr.org/2020/153 (accessed on 30 April 2023).
- Kanamori, Y. Quantum Encryption and Authentication Protocols. Ph.D. Thesis, University of Alabama in Huntsville, Huntsville, AL, USA, 2006. [Google Scholar]
- Cai, B.B.; Guo, G.D.; Lin, S. Multi-party Quantum Key Agreement without Entanglement. Int. J. Theor. Phys. 2017, 56, 1039–1051. [Google Scholar] [CrossRef]
- D’Ariano, G.M.; Presti, P.L.; Paris, M.G.A. Improved discrimination of unitary transformations by entangled probes. J. Opt. B Quantum Semiclass. Opt. 2002, 4, 273. [Google Scholar]
- Helstrom, C.W. Quantum Detection and Estimation Theory; Academic Press: Cambridge, MA, USA, 1976. [Google Scholar]
- Huang, S.L.; Hwang, T.; Gope, P. Multi-party quantum private comparison with an almost-dishonest third party. Quantum Inf. Process 2015, 14, 4225–4235. [Google Scholar] [CrossRef]
- Chefles, A.; Barnett, S.M. Optimum unambiguous discrimination between linearly independent symmetric states. Phys. Lett. A 1998, 250, 223–229. [Google Scholar] [CrossRef]
- Deng, F.; Li, X.; Zhou, H.; Zhang, Z.-J. Improving the security of multiparty quantum secret sharing against Trojan horse attack. Phys. Rev. A 2005, 72, 044302. [Google Scholar] [CrossRef]
- Li, X.H.; Deng, F.G. Improving the security of secure direct communication based on the secret transmitting order of particles. Phys. Rev. A 2006, 74, 054302. [Google Scholar] [CrossRef]
- Lu, C.B.; Miao, F.Y.; Hou, J.P.; Su, Z.F.; Xiong, Y. Quantum multiparty cryptosystems based on ahomomorphic random basis encryption. Quantum Inf. Process. 2020, 19, 293. [Google Scholar] [CrossRef]
- Raynal, P. Unambiguous State Discrimination of two density matrices in Quantum Information Theory. arXiv 2006, arXiv:quant-ph/0611133. [Google Scholar]
- Zyczkowski, K.; Sommers, H.J. Average fidelity between random quantum states. Phys. Rev. A 2005, 71, 032313. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).