Crosstalk Classification Based on Synthetically Consider Crosstalk and Fragmentation RMCSA in Multi-Core Fiber-Based EONs
Abstract
1. Introduction
2. Related Works
3. System Model and the Enabling Technologies
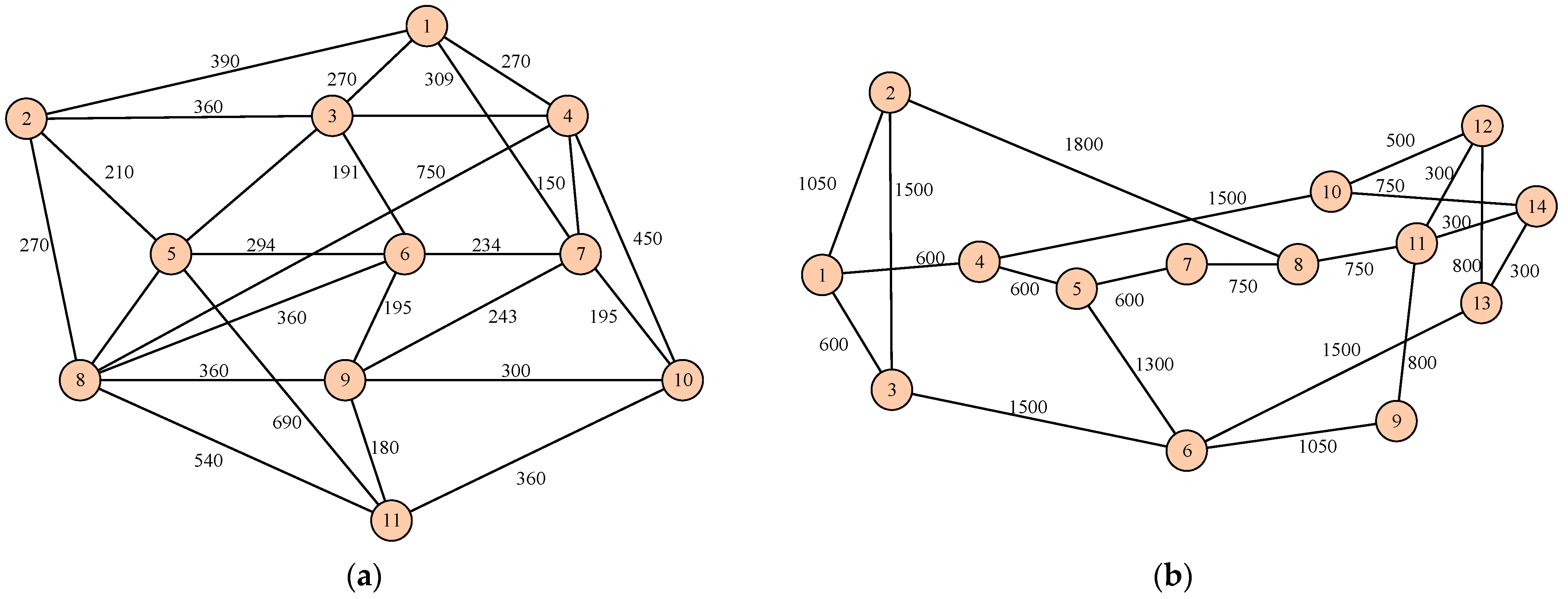
3.1. Network Model
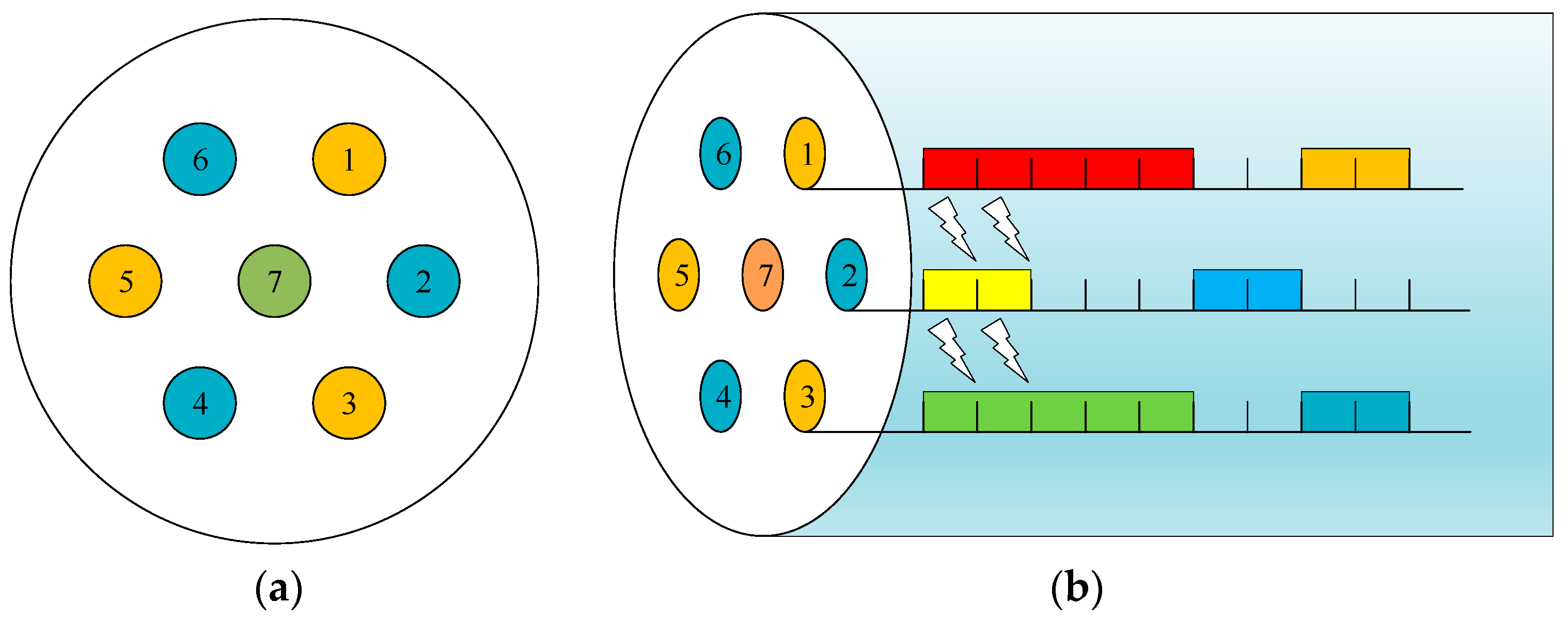
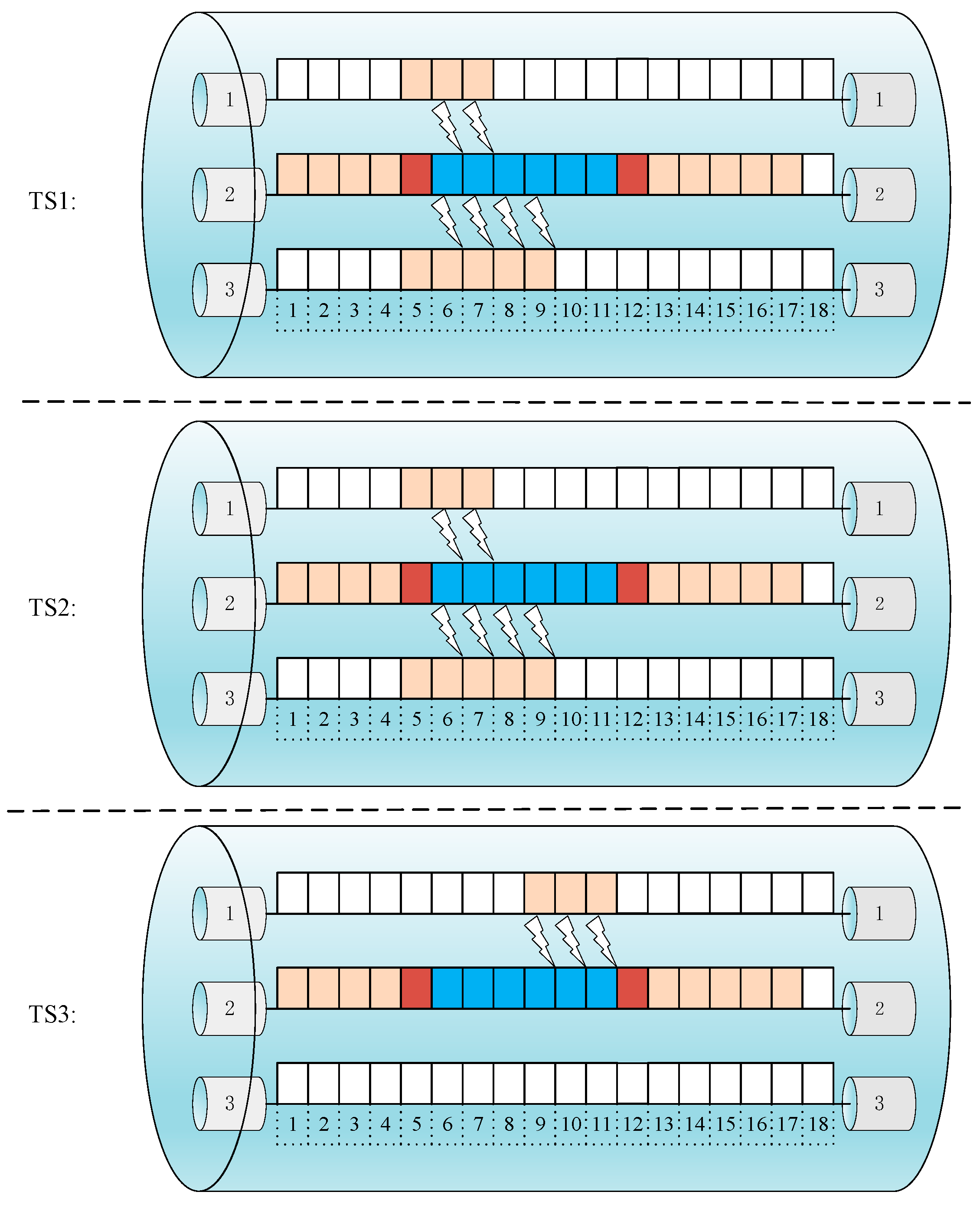
3.2. Three Domains XT-Fragmentation Metric Model
3.2.1. Spatial Domain
3.2.2. Frequency Domain
3.2.3. Time Domain
3.3. Routing and Modulation Format Selection
4. Crosstalk Classification Based on Synthetically Consider Crosstalk and Fragmentation Algorithm
4.1. Crosstalk Classification Algorithm
| Algorithm 1: CC algorithm | |
| Input: Arriving connection request Ri(si, d i, bi, , ). | |
| Output: Spectrum allocation. | |
| 1: | for each existing connection Rel(sel, del, bel, , ) do |
| 2: | if < then |
| 3: | Update Rel and release the occupied spectrum resources. |
| 4: | end if |
| 5: | end for |
| 6: | Select the k-shortest paths for Ri according to the KSP algorithm and store in the Pi |
| 7: | for each Pi do |
| 8: | Determine the highest modulation format level . |
| 9: | for each modulation level in [, ] do |
| 10: | Compute the number of FSs Fi requested by Equation (1). |
| 11: | end for |
| 12: | end for |
| 13: | CPi is numbered in ascending order of Fi |
| 14: | for each collaboration path CPi do |
| 15: | Set the XT stage as CSi. |
| 16: | for each CSi do |
| 17: | for each c of CPi do |
| 18: | According to the size of SBs and the crosstalk threshold, search the available SBs as Bi. |
| 19: | if Bi ≠ None then |
| 20: | for each Bi do |
| 21: | Compute XT based on Algorithm 2. |
| 22: | if Algorithm 2 returns 1 then |
| 23: | Store the Bi in ABi |
| 24: | Break. |
| 25: | end if |
| 26: | end for |
| 27: | end if |
| 28: | end for |
| 29: | if ABi ≠ None then |
| 30: | Select the SB with the first minimum of di and allocate the di for Ri. |
| 31: | end if |
| 32: | Reject connection request Ri |
| 33: | end for |
| 34: | end for |
4.2. Synthetically Consider Crosstalk and Fragmentation Algorithm
| Algorithm 2: SCCF algorithm | |
| Input: Pi, ci, , . | |
| Output: 1 or 0. | |
| 1: | XT = 0. |
| 2: | for FS fi in [, ] do |
| 3: | for (link ei, core ci) in Pi do |
| 4: | for each adjacent of ci do |
| 5: | if Rel ≠ None then |
| 6: | for each eel do |
| 7: | Calculate , , and . |
| 8: | end for |
| 9: | if > XTthreshold then |
| 10: | return 0 |
| 11: | end if |
| 12: | end if |
| 13: | end for |
| 14: | end for |
| 15: | Select the spectrum resource with minimal |
| 16: | if > XTthreshold then |
| 17: | return 0 |
| 18: | end if |
| 19: | end for |
| 20: | return 1 |
4.3. Complexity
5. Simulation Results and Analysis
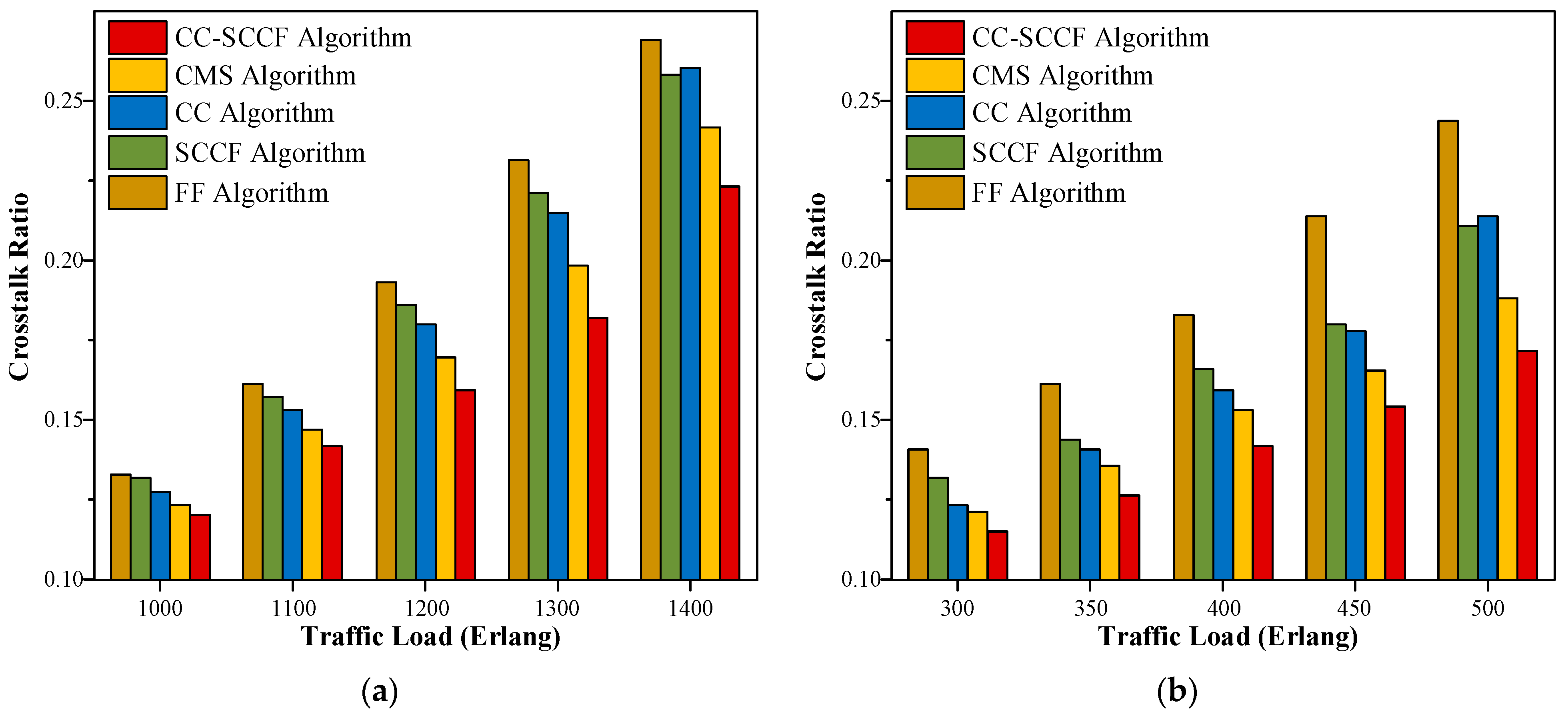
5.1. Performance Comparison of Blocking Probability
5.2. Network-Wide XT Effect Ratio
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Cisco. Annual Internet Report (2018–2023) White Paper. Available online: http://www.cisco.com (accessed on 20 January 2023).
- Gerstel, O.; Jinno, M.; Lord, A.; Yoo, S.B. Elastic optical networking: A new dawn for the optical layer? IEEE Commun. Mag. 2012, 50, s12–s20. [Google Scholar] [CrossRef]
- Chatterjee, B.C.; Sarma, N.; Oki, E. Routing and spectrum allocation in elastic optical networks: A tutorial. IEEE Commun. Surv. Tutor. 2015, 17, 1776–1800. [Google Scholar] [CrossRef]
- Saridis, G.M.; Alexandropoulos, D.; Zervas, G.; Simeonidou, D. Survey and evaluation of space division multiplexing: From technologies to optical networks. IEEE Commun. Surv. Tutor. 2015, 17, 2136–2156. [Google Scholar] [CrossRef]
- Cvijetic, M.; Djordjevic, I.B.; Cvijetic, N. Dynamic multidimensional optical networking based on spatial and spectral processing. Opt. Express 2012, 20, 9144–9150. [Google Scholar] [CrossRef]
- Richardson, D.J.; Fini, J.M.; Nelson, L.E. Space-division multiplexing in optical fibres. Nat. Photonics 2013, 7, 354–362. [Google Scholar] [CrossRef]
- Muhammad, A.; Zervas, G.; Forchheimer, R. Resource allocation for space-division multiplexing: Optical white box versus optical black box networking. J. Light. Technol. 2015, 33, 4928–4941. [Google Scholar] [CrossRef]
- Yang, M.; Zhang, Y.; Wu, Q. Routing, spectrum, and core assignment in SDM-EONS with MCF: Node-arc ILP/MILP methods and an efficient XT-aware heuristic algorithm. J. Opt. Commun. Netw. 2018, 10, 195–208. [Google Scholar] [CrossRef]
- Klinkowski, M.; Lechowicz, P.; Walkowiak, K. Survey of resource allocation schemes and algorithms in spectrally-spatially flexible optical networking. Opt. Switch. Netw. 2018, 27, 58–78. [Google Scholar] [CrossRef]
- Trindade, S.; da Fonseca, N.L.S. Machine learning for spectrum defragmentation in space-division multiplexing elastic optical networks. IEEE Netw. 2020, 35, 326–332. [Google Scholar] [CrossRef]
- Takeda, K.; Sato, T.; Chatterjee, B.C.; Oki, E. Joint Inter-Core Crosstalk-and Intra-Core Impairment-Aware Lightpath Provisioning Model in Space-Division Multiplexing Elastic Optical Networks. IEEE Trans. Netw. Serv. Manag. 2022, 19, 4323–4337. [Google Scholar] [CrossRef]
- Ahmed, I.; Oki, E.; Chatterjee, B.C. Crosstalk-Avoided Resource Allocation in Spectrally-Spatially Elastic Optical Networks: An Overview. Adv. Mod. Appl. Sci. 2022, 188, 188. [Google Scholar]
- Thangaraj, J. Multi-path provisioning in elastic optical network with dynamic on-request optimal defragmentation strategy. Opt. Switch. Netw. 2021, 41, 100607. [Google Scholar]
- Yadav, D.S. RDRSA: A reactive defragmentation based on rerouting and spectrum assignment (RDRSA) for spectrum convertible elastic optical network. Opt. Commun. 2021, 496, 127144. [Google Scholar] [CrossRef]
- Pan, M.; Qiu, Y.; Zhang, C. Multiple leaf-ringing based protection algorithm with spectrum defragmentation for multicast traffic in elastic optical network. Opt. Fiber Technol. 2021, 61, 102418. [Google Scholar] [CrossRef]
- Li, R.; Gu, R.; Jin, W.; Ji, Y. Learning-based cognitive hitless spectrum defragmentation for dynamic provisioning in elastic optical networks. IEEE Commun. Lett. 2021, 25, 1600–1604. [Google Scholar] [CrossRef]
- Selva Kumar, S.; Kamalakannan, J.; Seetha, R.; Asha, N.; Raja, K.T.; Sree Dharinya, S.; Sucharitha, M.; Kalaivani, S. The Effectual Spectrum Defragmentation Algorithm with Holding Time Sensitivity in Elastic Optical Network (EON). Int. J. Opt. 2022, 2022, 1–16. [Google Scholar] [CrossRef]
- Liu, H.; Ren, J.; Chen, Y.; Hu, J.; Tang, C.; Tang, M. Spectrum slicing-based fragmentation aware routing and spectrum allocation in elastic optical networks. Opt. Switch. Netw. 2022, 45, 100673. [Google Scholar] [CrossRef]
- Bao, B.; Yang, H.; Yao, Q.; Yu, A.; Chatterjee, B.C.; Oki, E.; Zhang, J. SDFA: A service-driven fragmentation-aware resource allocation in elastic optical networks. IEEE Trans. Netw. Serv. Manag. 2021, 19, 353–365. [Google Scholar] [CrossRef]
- Zhang, S.; Yeung, K.L.; Jin, A. LBFA: A Load-Balanced and Fragmentation-Aware Resource Allocation Algorithm in Space-Division Multiplexing Elastic Optical Networks. Photonics 2021, 8, 456. [Google Scholar] [CrossRef]
- Pourkarimi, E.; Rahbar, A.G. Novel fragmentation-aware algorithms in space division multiplexing elastic optical networks. Opt. Fiber Technol. 2021, 66, 102655. [Google Scholar] [CrossRef]
- Ahmed, I.; Oki, E.; Chatterjee, B.C. Crosstalk-aware vs. crosstalk-avoided approaches in spectrally-spatially elastic optical networks: Which is the better choice? In Proceedings of the 2022 Workshop on Recent Advances in Photonics (WRAP), Mumbai, India, 4–6 March 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 1–2. [Google Scholar]
- Klinkowski, M.; Zalewski, G. Dynamic crosstalk-aware lightpath provisioning in spectrally-spatially flexible optical networks. J. Opt. Commun. Netw. 2019, 11, 213–225. [Google Scholar] [CrossRef]
- Zhang, J.; Yao, Q.; Bao, B.; Ren, D.; Hu, J.; Yang, H.; Zhao, J. Resource-oriented RMCSA scheme with low crosstalk effect in multi-core fiber-based elastic optical networks. Opt. Fiber Technol. 2022, 68, 102796. [Google Scholar] [CrossRef]
- Xiong, Y.; Ye, Y.; Zhang, H.; He, J.; Wang, B.; Yang, K. Deep learning and hierarchical graph-assisted crosstalk-aware fragmentation avoidance strategy in space division multiplexing elastic optical networks. Opt. Express 2020, 28, 2758–2777. [Google Scholar] [CrossRef]
- Lira, C.J.N.; Almeida, J.R.C.; Chaves, D.A.R. Spectrum allocation using multiparameter optimization in elastic optical networks. Comput. Netw. 2023, 220, 109478. [Google Scholar] [CrossRef]
- Liu, H.L.; Hu, J.L.; Ren, J.; Hu, H.X.; Tang, C.; Chen, H.N. Crosstalk Aware Resource Allocation Method Based on Lightpath Load Balancing and Neighborhood Matching. Acta Electonica Sin. 2022, 50, 2746. [Google Scholar]
- Chatterjee, B.C.; Wadud, A.; Oki, E. Proactive fragmentation management scheme based on crosstalk-avoided batch processing for spectrally-spatially elastic optical networks. IEEE J. Sel. Areas Commun. 2021, 39, 2719–2733. [Google Scholar] [CrossRef]
- Su, J.; Zhang, J.; Wang, J.; Ren, D.; Hu, J.; Zhao, J. Dynamic impairment-aware RMCSA in multi-core fiber-based elastic optical networks. Opt. Commun. 2022, 518, 128361. [Google Scholar] [CrossRef]
- Tang, F.; Li, Y.; Shen, G.; Rouskas, G.N. Minimizing inter-core crosstalk jointly in spatial, frequency, and time domains for scheduled lightpath demands in multi-core fiber-based elastic optical network. J. Light. Technol. 2020, 38, 5595–5607. [Google Scholar] [CrossRef]
- Zhao, J.; Bao, B.; Chatterjee, B.C.; Oki, E.; Hu, J.; Ren, D. Dispersion based highest-modulation-first last-fit spectrum allocation scheme for elastic optical networks. IEEE Access 2018, 6, 59907–59916. [Google Scholar] [CrossRef]
- Yao, Q.; Yang, H.; Bao, B.; Yu, A.; Zhang, J.; Cheriet, M. Core and spectrum allocation based on association rules mining in spectrally and spatially elastic optical networks. IEEE Trans. Commun. 2021, 69, 5299–5311. [Google Scholar] [CrossRef]
- Yao, Q.; Yang, H.; Yu, A.; Zhang, J.; Ji, Y. Service provisioning based on association rules mining between crosstalk and fragmentization in multi-core elastic optical networks. In Proceedings of the 2019 24th OptoElectronics and Communications Conference (OECC) and 2019 International Conference on Photonics in Switching and Computing (PSC), Fukuoka, Japan, 1–11 July 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–3. [Google Scholar]
- Zhao, J.; Bao, B.; Yang, H.; Oki, E.; Chatterjee, B.C. Holding-time-and impairment-aware shared spectrum allocation in mixed-line-rate elastic optical networks. J. Opt. Commun. Netw. 2019, 11, 322–332. [Google Scholar] [CrossRef]
- Trindade, S.; da Fonseca, N.L.S. Proactive fragmentation-aware routing, modulation format, core, and spectrum allocation in EON-SDM. In Proceedings of the ICC 2019-2019 IEEE International Conference on Communications (ICC), Shanghai, China, 20–24 May 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–6. [Google Scholar]
- Zhao, J.; Yao, Q.; Liu, X.; Li, W.; Maier, M. Distance-adaptive routing and spectrum assignment in OFDM-based flexible transparent optical networks. Photonic Netw. Commun. 2014, 27, 119–127. [Google Scholar] [CrossRef]
- Zhang, J.; Bao, B.; Yao, Q.; Ren, D.; Hu, J.; Zhao, J. 3D fragmentation metric and RCSA scheme for space division multiplexing elastic optical networks. IEEE Access 2020, 8, 201595–201605. [Google Scholar] [CrossRef]
- Chatterjee, B.C.; Wadud, A.; Ahmed, I.; Oki, E. Priority-based inter-core and inter-mode crosstalk-avoided resource allocation for spectrally-spatially elastic optical networks. IEEE/ACM Trans. Netw. 2021, 29, 1634–1647. [Google Scholar] [CrossRef]


| Modulation Formats | Transmission Reach [km] | Capacity pFS [GHz] | XT Thresholds [dB] |
|---|---|---|---|
| BPSK | 4000 | 12.5 | −14 |
| QPSK | 2000 | 25 | −18.5 |
| 8-QAM | 1000 | 37.5 | −21 |
| 16-QAM | 500 | 50 | −25 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chen, Y.; Feng, N.; Zhou, Y.; Ren, D.; Zhao, J. Crosstalk Classification Based on Synthetically Consider Crosstalk and Fragmentation RMCSA in Multi-Core Fiber-Based EONs. Photonics 2023, 10, 340. https://doi.org/10.3390/photonics10030340
Chen Y, Feng N, Zhou Y, Ren D, Zhao J. Crosstalk Classification Based on Synthetically Consider Crosstalk and Fragmentation RMCSA in Multi-Core Fiber-Based EONs. Photonics. 2023; 10(3):340. https://doi.org/10.3390/photonics10030340
Chicago/Turabian StyleChen, Yanbo, Nan Feng, Yue Zhou, Danping Ren, and Jijun Zhao. 2023. "Crosstalk Classification Based on Synthetically Consider Crosstalk and Fragmentation RMCSA in Multi-Core Fiber-Based EONs" Photonics 10, no. 3: 340. https://doi.org/10.3390/photonics10030340
APA StyleChen, Y., Feng, N., Zhou, Y., Ren, D., & Zhao, J. (2023). Crosstalk Classification Based on Synthetically Consider Crosstalk and Fragmentation RMCSA in Multi-Core Fiber-Based EONs. Photonics, 10(3), 340. https://doi.org/10.3390/photonics10030340




