A Molecular Force Field-Based Optimal Deployment Algorithm for UAV Swarm Coverage Maximization in Mobile Wireless Sensor Network
Abstract
1. Introduction
- (1)
- In the traditional VFA-based algorithm, the magnitude of the virtual force is only inversely proportional to the distance between the UAVs. However, we found that the distance and the virtual force should not be in a linear relationship. The closer the distance between each pair of UAVs is, the greater the impact will be. Thus, we should give a higher weight to the closer UAVs, such that the interference of some of the farther UAVs can be filtered out.
- (2)
- The final coverage result is affected by the initialization result in a single test as, for most traditional VFA-based deployment algorithms, the initialization is random; the only requirement is that the UAVs must be deployed in the working area. In this case, the UAVs in some areas may be significantly denser or sparser than those in other areas due to the randomness. If the random initialization is applied to the convex polygon coverage, it may cause slower convergence or even become stuck in a local optimum. Only by repeating the experiments (re-initializing for each experiment) to obtain the optimal deployment scheme can the robustness of the traditional VFA-based algorithms be embodied.
- (3)
- Most traditional VFA-based algorithms can only be used to cover a rectangular area; some even do not have a boundary to constrain the position of the UAVs but just maximize the coverage area of the UAVs.
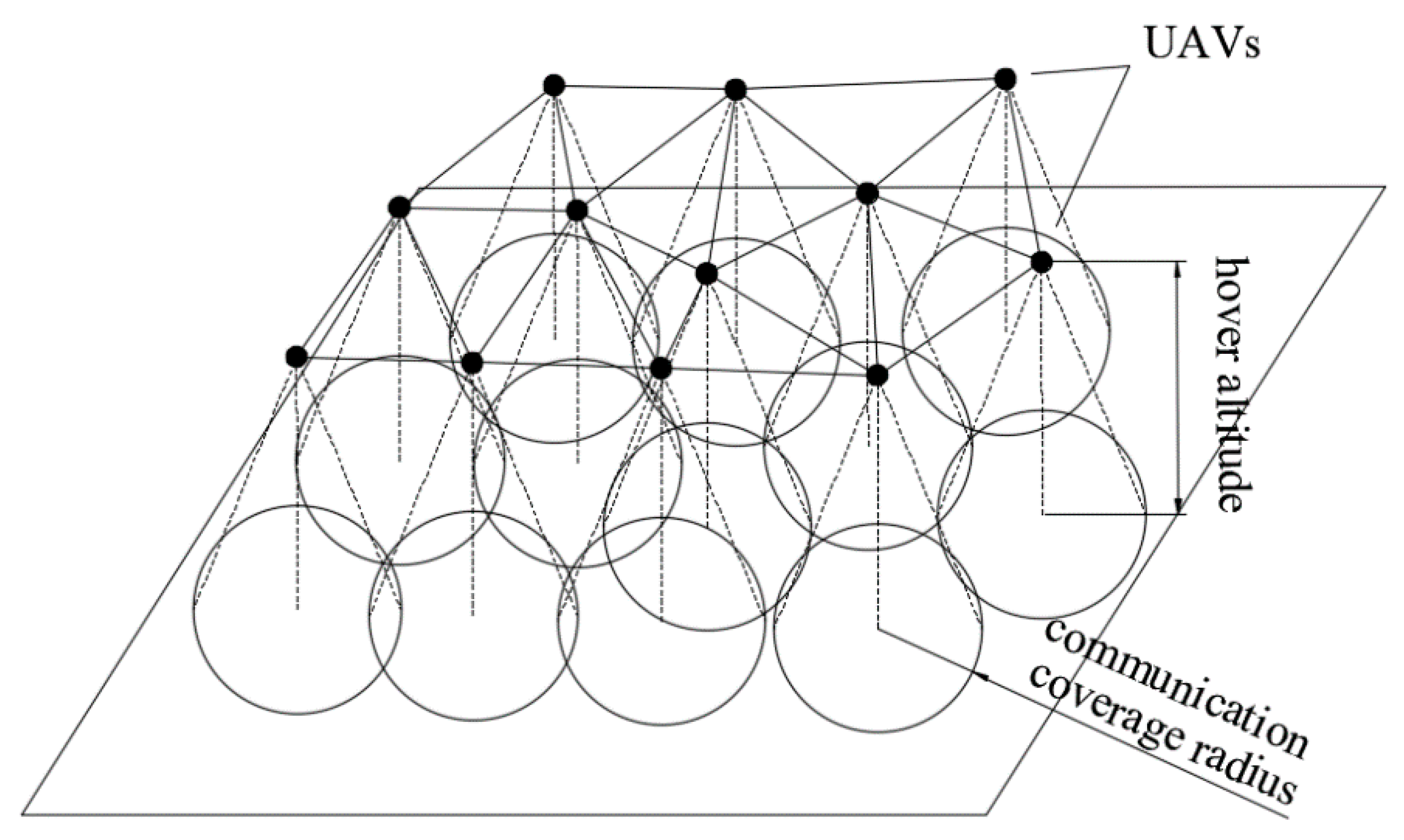
2. Formulation and Preliminaries
2.1. Problem Formulation
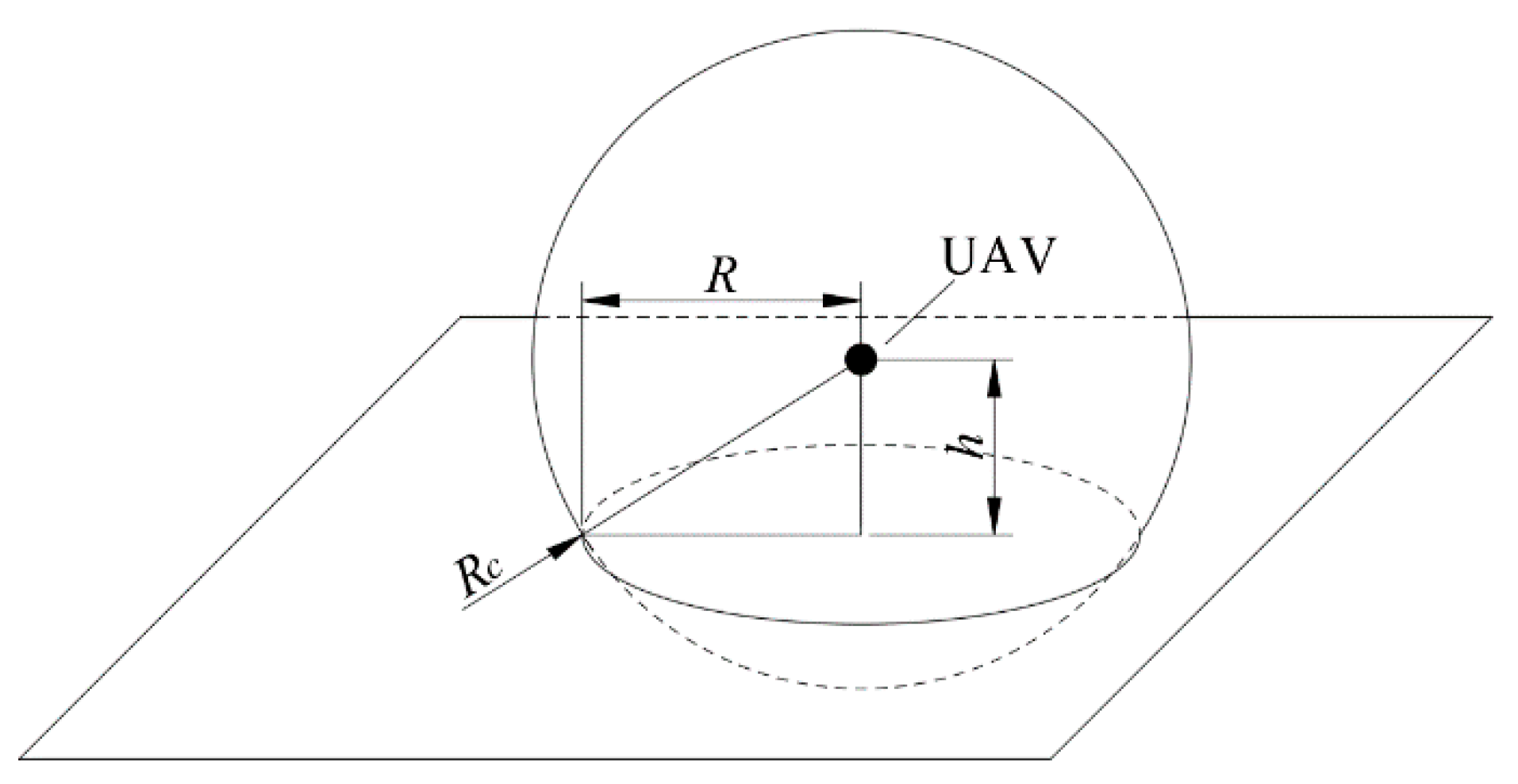
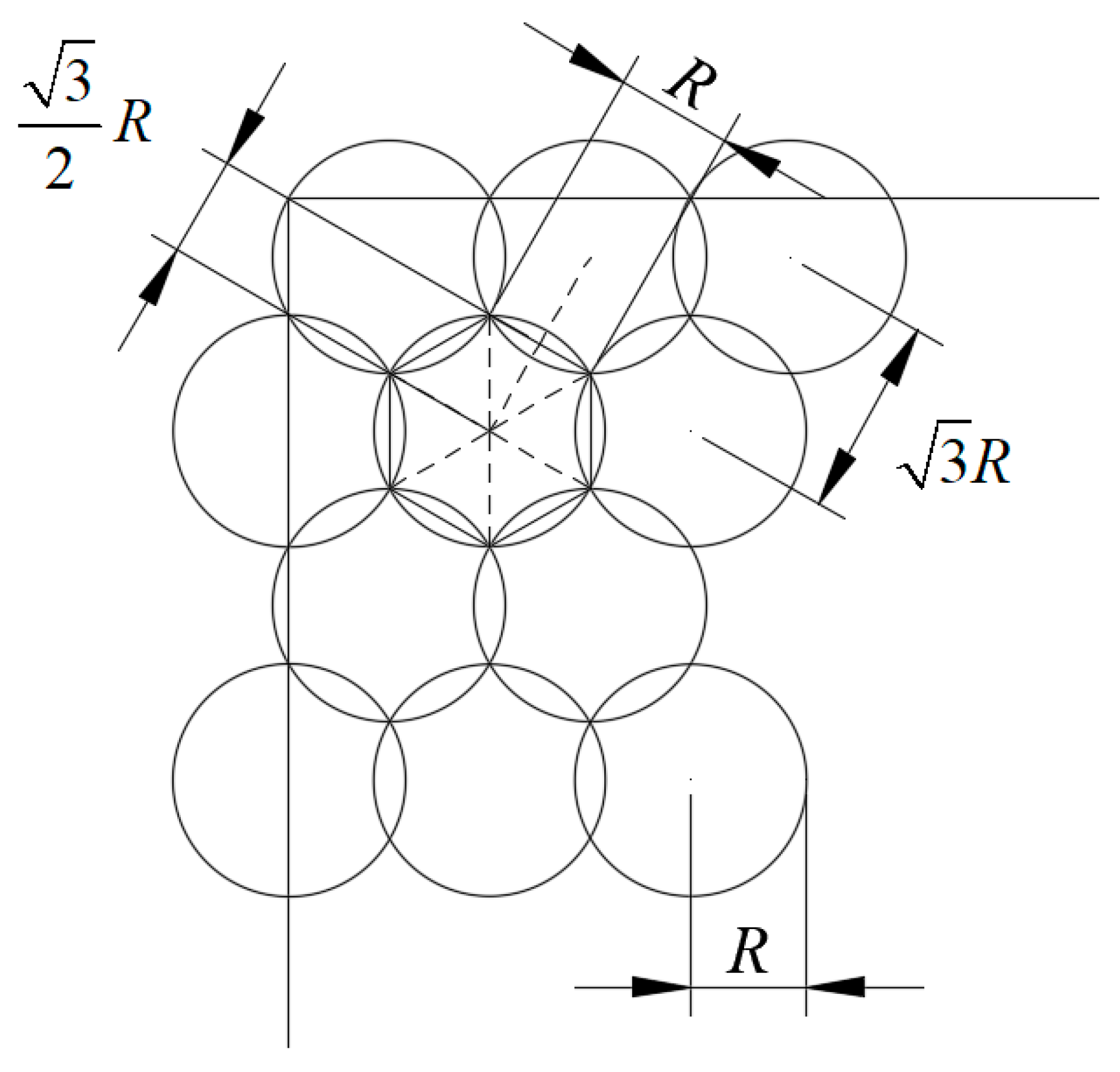
2.2. Coverage Ratio Calculation
2.3. Estimate of the Ideal Number of the UAVs
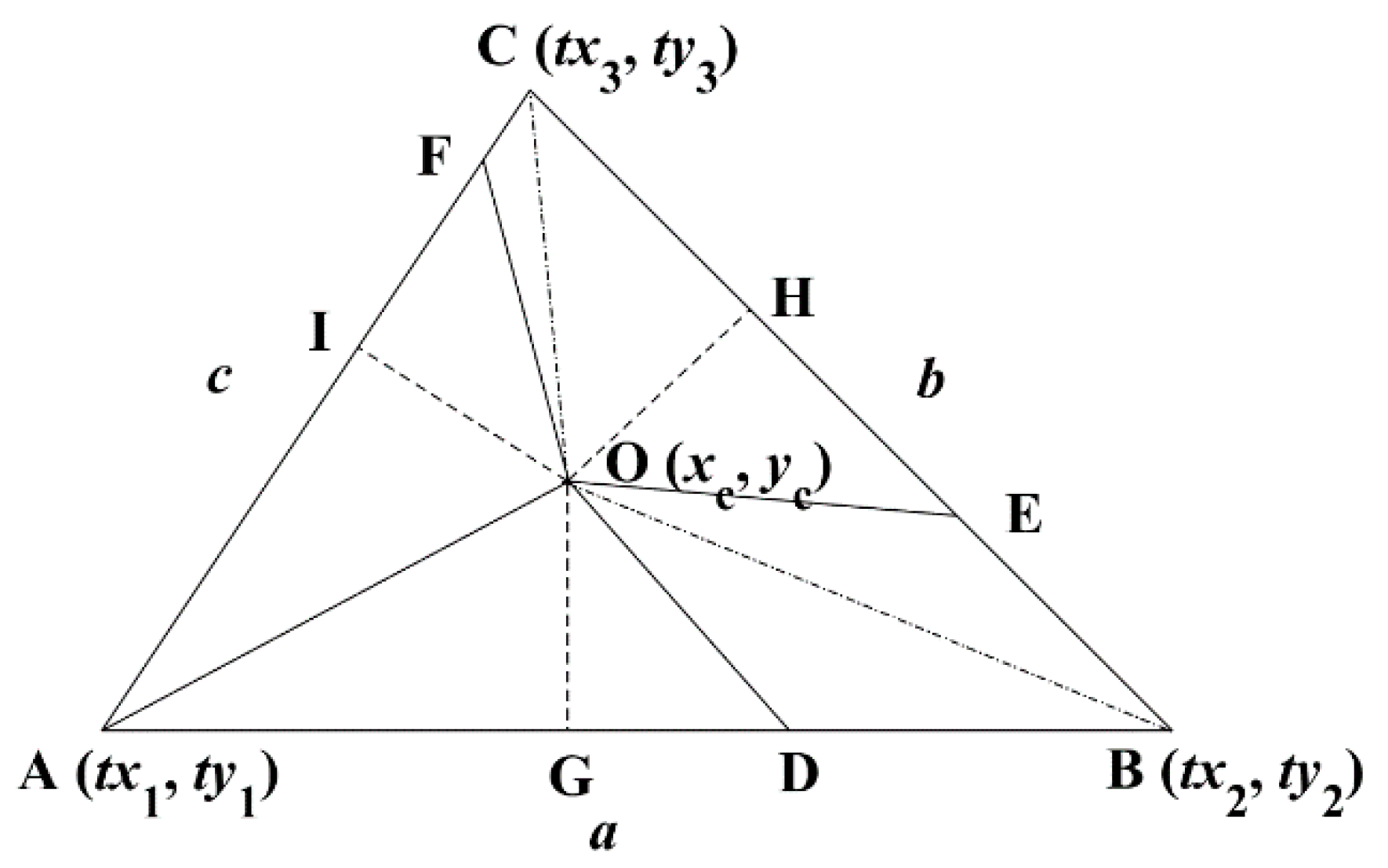
2.4. Centroid of the Convex Polygon
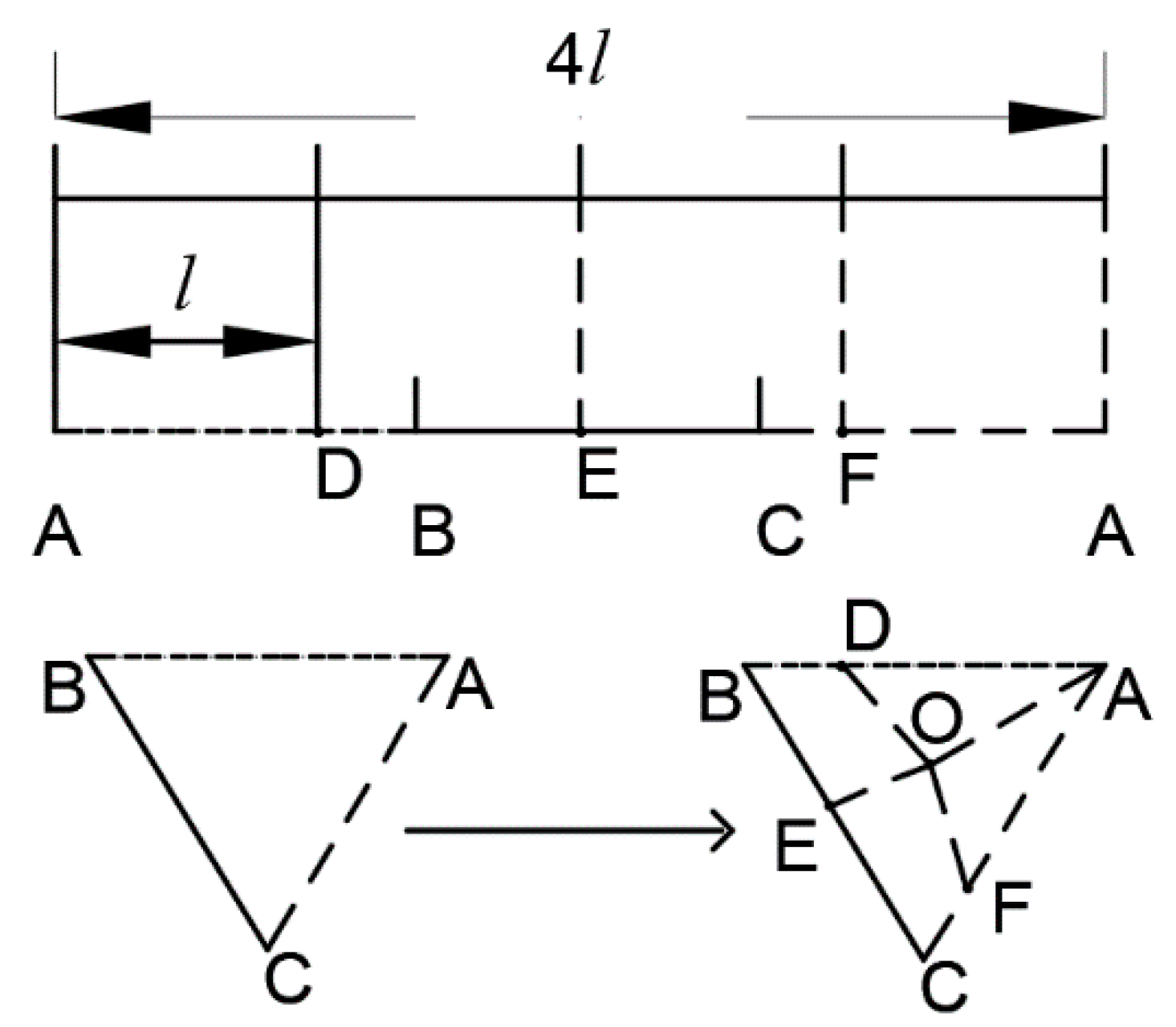
2.5. Equal Division Method of the Triangle
| Algorithm 1 Dividing a triangle into equal areas |
| 1: for I = 1: dn |
| 2: if 0 <l *I ≤ a |
| 3: if anum == 0 |
| 4: Calculate the co-ordinate of point D (i) on the line AB, where the distance between point D (i) and point A is l. |
| 5: poly (i) = polygon AOD (i); |
| 6: else |
| 7: Calculate the co-ordinate of point D (i) on the line AB, where the distance between point D (i) and point A is (l *i). |
| 8: Poly (i) = polygon OD (i) D (i-1); |
| 9: end |
| 10: anum = anum + 1; |
| 11: end |
| 12: if a < l *I ≤a + b |
| 13: if bnum == 0 |
| 14: Calculate the co-ordinate of point D (i) on the line BC, where the distance between point D (i) and point B is (l *i-a). |
| 15: if anum ≠ 0 |
| 16: poly (i) = polygon OD(i) BD (i-1); |
| 17: else |
| 18: poly (i) = polygon AOD (i) B; |
| 19: end |
| 20: else |
| 21: Calculate the co-ordinate of point D (i) on the line BC, where the distance between point D (i) and point D (i-1) is l. |
| 22: poly(i) = polygon OD (i) D (i-1); |
| 23: end |
| 24: bnum = bnum + 1; |
| 25: end |
| 26: if a + b < l *I ≤ a + b + c |
| 27: if cnum == 0 |
| 28: Calculate the co-ordinate of point D (i) on the line CA, where the distance between point D (i) and point C is (l *i-a-b). |
| 29: if bnum ≠ 0 |
| 30: poly (i) = polygon OD (i) CD (i-1); |
| 31: else |
| 32: poly(i) = polygon OD (i) CBD (i-1); |
| 33: end |
| 34: else |
| 35: Calculate the co-ordinate of the point D (i) on the line CA, where the distance between point D (i) and point D (i-1) is l. |
| 36: poly (i) = polygon OD (i) D (i-1); |
| 37: end |
| 38: cnum = cnum + 1; |
| 39: end |
| 40: end |
3. Molecular Force Field-Based Deployment Algorithm for UAV Swarm
3.1. Initialization
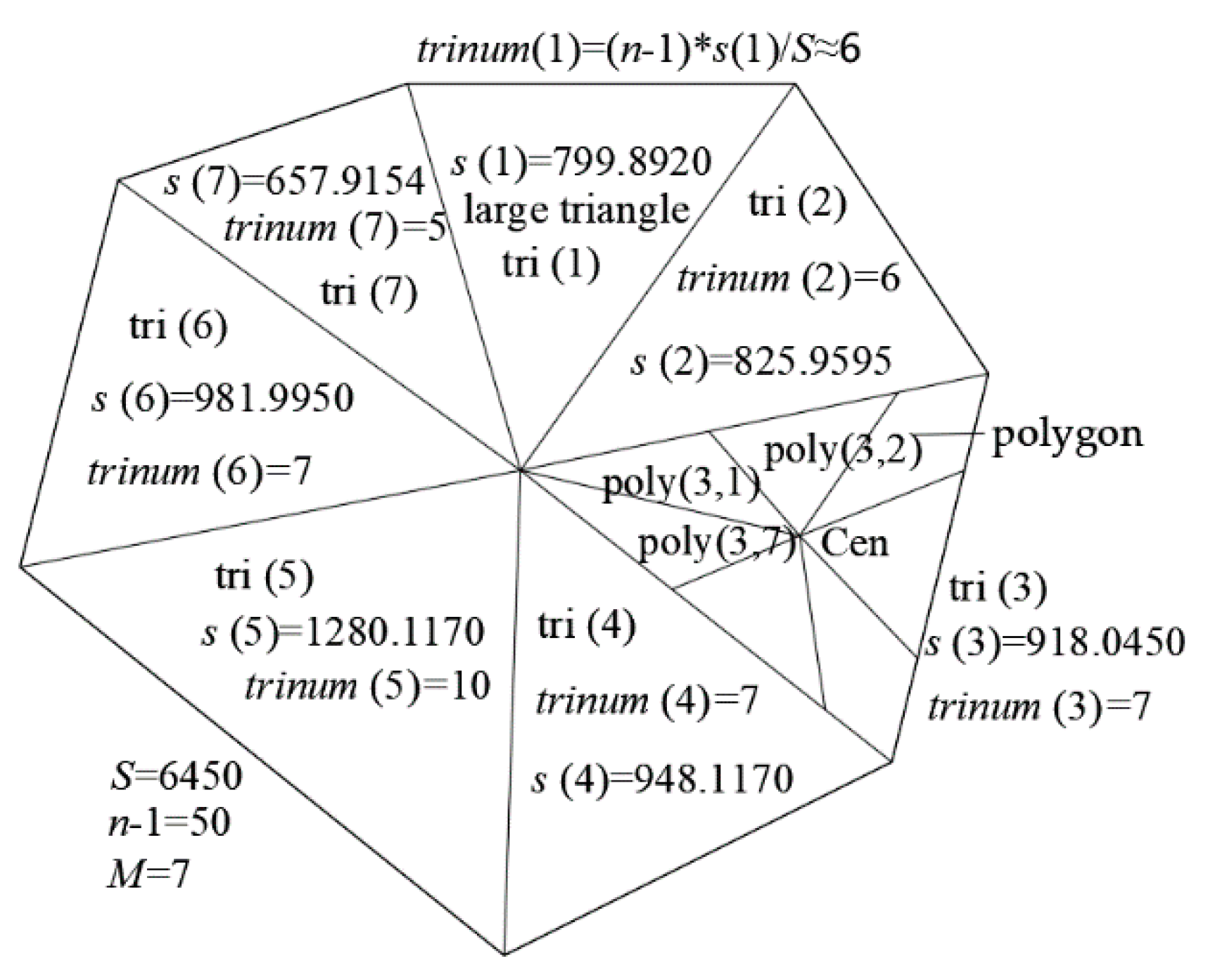
| Algorithm 2 The allocation method for the remaining n−1 UAVs |
| 1: for I = 1: M |
| 2: Compute the area (s(i)) of tri (i); |
| 3: Compute the number (trinum(i)) of UAVs in tri(i) by trinum (i)=round ((n2212;1) *s(i)/S); |
| 4: end |
| 5: na = sum (trinum(i)); |
| Algorithm 3 Obtain the initial deployment positions of the UAVs. |
| 1: Divide each of the M triangles into trinum (M) equal area polygons by the method in Section 2.5 (Algorithm 1). |
| 2: for i = 1: M |
| 3: Compute the perimeter of tri (i); |
| 4: Compute the incentre of tri (i); |
| 5: if trinum (i) == 1 |
| 6: poly (i,1) = tri (i); |
| 7: end |
| 8: if trinum (i) == 2 |
| 9: Connect the midpoint of the i-th side and Cen; |
| 10: Then, tri (i) is divided into two equal area triangles poly (i,1) and poly (i,2); |
| 11: end |
| 12: if trinum (i) > = 3 |
| 13: Compute the coordinates of the point that equally divides all sides of tri (i) into trinum (i) parts; |
| 14: Connect each division point to the inleft of tri (i); |
| 15: Then, tri (i) is divided into trinum (i) equal area polygons poly (i,1), poly (i,2), …, poly (i, trinum(i)); |
| 16: end |
| 17: end |
| 18: for i=1: M |
| 19: for j = 1: trinum (i) |
| 20: Randomly generate a set of two-dimensional coordinates in poly (i, j) as the position of the q-th UAV (only running in method 1); |
| 21: Place the q-th UAV in the centroid of poly (i, j) (only running in method 2); |
| 22: q=q + 1; |
| 23: End |
| 24: End |
3.2. Molecular Force Field Deployment Algorithm
- Step 1:
- Send the information about the working area from the base to the UAVs. According to Equations (2)–(4), the minimum number of UAVs required can be estimated.
- Step 2:
- Virtually deploy the UAVs in the working area using the proposed initialization method.
- Step 3:
- Calculate the resultant force of each UAV separately, which consists of three parts:
3.3. Computational Complexity of the Proposed Algorithm
4. Simulation and Results
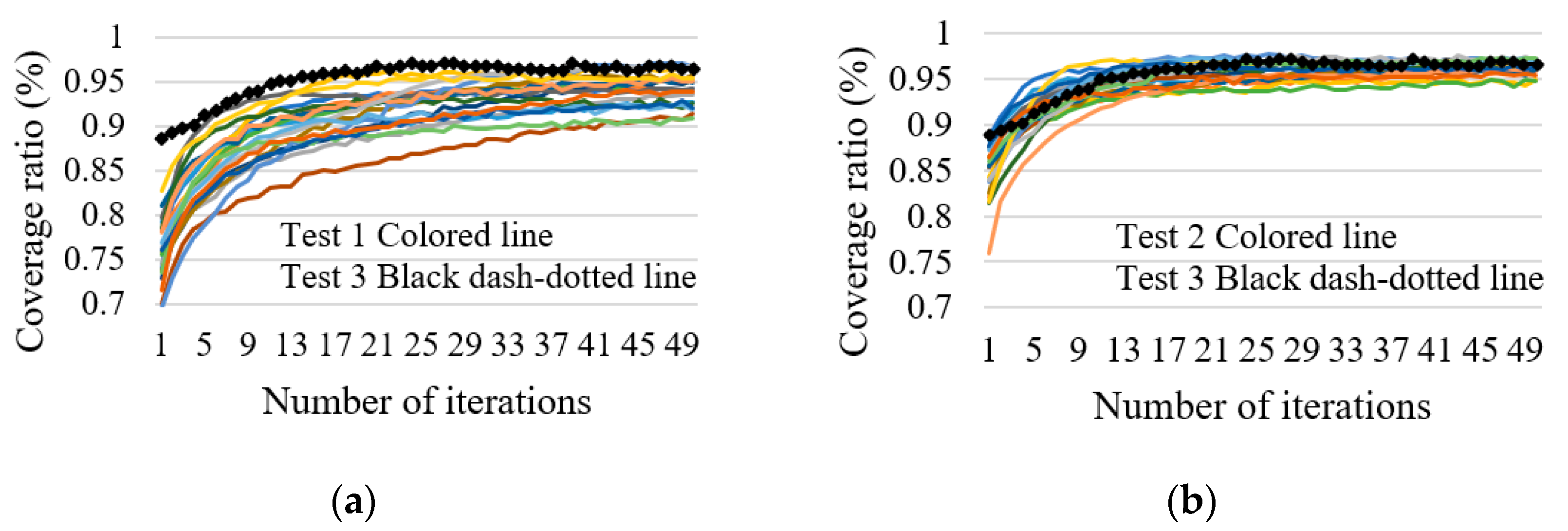
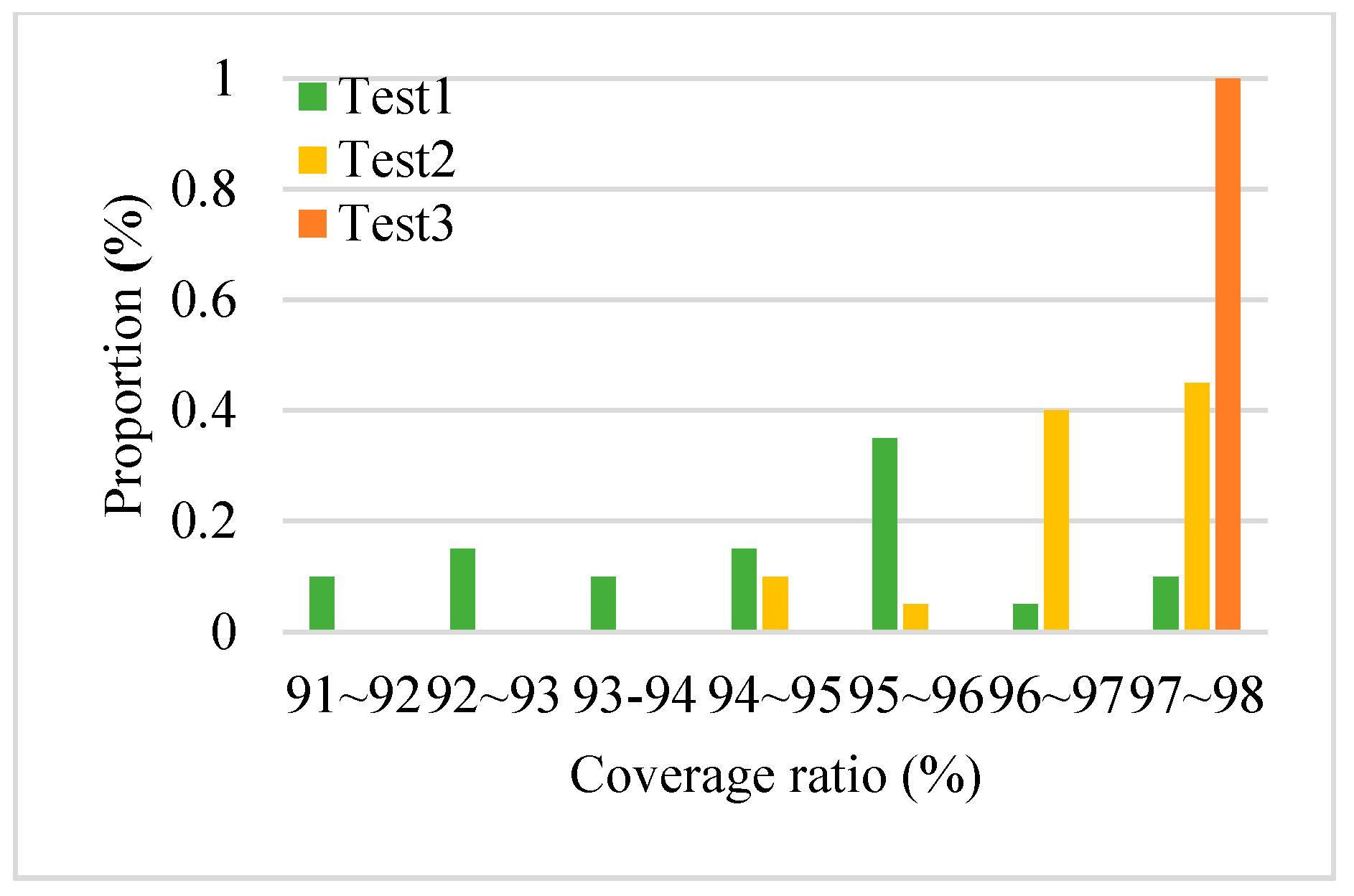
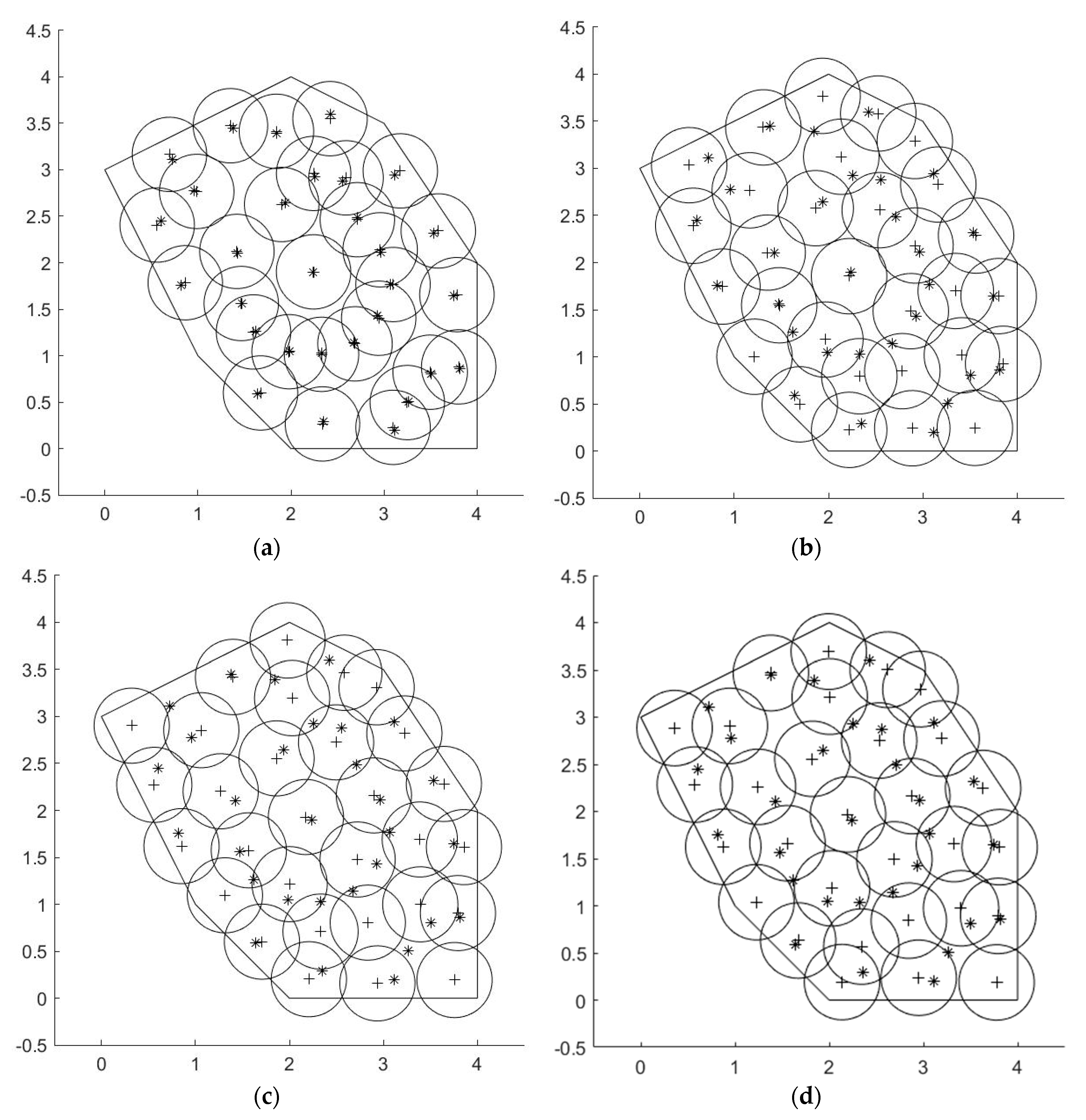
4.1. Performance of the Proposed Algorithm
4.2. Comparison with Related Algorithms in Terms of the Coverage Ratio
4.3. Results Analysis
5. Conclusions
Data Availability
Author Contributions
Funding
Conflicts of Interest
References
- Senouci, M.R.; Mellouk, A.; Asnoune, K.; Bouhidel, F.Y. Movement-Assisted Sensor Deployment Algorithms: A Survey and Taxonomy. IEEE Commun. Surv. Tutor. 2015, 17, 2493–2510. [Google Scholar] [CrossRef]
- Mohamed, S.M.; Hamza, H.S.; Saroit, I.A. Coverage in mobile wireless sensor networks (M-WSN): A survey. Comput. Commun. 2017, 110, 133–150. [Google Scholar] [CrossRef]
- Kothari, M.; Postlethwaite, I.; Gu, D.W. UAV path following in windy urban environments. J. Intell. Robot. Syst. 2014, 74, 1013–1028. [Google Scholar] [CrossRef]
- Kothari, M.; Postlethwaite, I. A probabilistically robust path planning algorithm for UAVs using rapidly-exploring random trees. J. Intell. Robot. Syst. 2013, 71, 231–253. [Google Scholar] [CrossRef]
- Kapoor, D.; Deb, D.; Bangar, H.; Sahai, A. Adaptive Failure Compensation for Coaxial Rotor Helicopter under Propeller Failure. In Proceedings of the American Control Conference 2012, Montreal, QC, Canada, 27–29 June 2012. [Google Scholar]
- Kapoor, D.; Sodhi, P.; Deb, D. Adaptive Failure Compensation of a Single Main-Rotor Helicopter. In Proceedings of the IFAC Workshop on Embedded Guidance, Navigation and Control (EGNCA), Bangalore, India, 13–15 February 2012. [Google Scholar]
- Kirichek, R.; Paramonov, A.; Koucheryavy, A. Swarm of public unmanned aerial vehicles as a queuing network. In Communications in Computer and Information Science; Springer: Cham, Switzerland, 2016; Volume 601, pp. 111–120. [Google Scholar]
- Spanogianopoulos, S.; Zhang, Q.; Spurgeon, S. Fast Formation of Swarm of UAVs in Congested Urban Environment. IFAC-PapersOnLine 2017, 50, 8031–8036. [Google Scholar] [CrossRef]
- Rosalie, M.; Dentier, J.E.; Danoy, G.; Bouvry, P.; Kannan, S.; Olivares-Mendez, M.A.; Voos, H. Area exploration with a swarm of UAVs combining deterministic chaotic ant colony mobility with position MPC. In Proceedings of the 2017 International Conference on Unmanned Aircraft Systems (ICUAS), Miami, FL, USA, 13–16 June 2017; pp. 1392–1397. [Google Scholar]
- Brust, M.R.; Zurad, M.; Hentges, L.; Gomes, L.; Danoy, G.; Bouvry, P. Target tracking optimization of UAV swarms based on dual-pheromone clustering. In Proceedings of the 2017 3rd IEEE International Conference on Cybernetics (CYBCONF), Exeter, UK, 21–23 June 2017. [Google Scholar]
- Koyuncu, E.; Khodabakhsh, R.; Surya, N.; Seferoglu, H. Deployment and trajectory optimization for UAVs: A quantization theory approach. In Proceedings of the Wireless Communications and Networking Conference (WCNC), Barcelona, Spain, 15–18 April 2018; pp. 1–6. [Google Scholar]
- Zou, Y.; Chakrabarty, K. Sensor Deployment and Target Localization Based on Virtual Forces. In Proceedings of the IEEE INFOCOM 2003. Twenty-second Annual Joint Conference of the IEEE Computer and Communications Societies (IEEE Cat. No.03CH37428), San Francisco, CA, USA, 30 March–3 April 2003; Volume 2, pp. 1293–1303. [Google Scholar] [CrossRef]
- Qu, Y.; Georgakopoulos, S.V. Relocation of wireless sensor network nodes using a genetic algorithm. In Proceedings of the Wireless and Microwave Technology Conference (WAMICON), Clearwater Beach, FL, USA, 18–19 April 2011; pp. 1–5. [Google Scholar]
- Jia, J.; Chen, J.; Chang, G.; Wen, Y.; Song, J. Multi-objective optimization for coverage control in wireless sensor network with adjustable sensing radius. Comput. Math. Appl. 2009, 57, 1767–1775. [Google Scholar] [CrossRef]
- Jin, L.; Jia, J.; Sun, D. Node Distribution Optimization in Mobile Sensor Network Based on Multi-Objective Differential Evolution Algorithm. In Proceedings of the 2010 Fourth International Conference on Genetic and Evolutionary Computing, Shenzhen, China, 13–15 December 2010; pp. 51–54. [Google Scholar] [CrossRef]
- Abo-Zahhad, M.; Ahmed, S.M.; Sabor, N.; Sasaki, S. Coverage maximization in mobile Wireless Sensor Networks utilizing immune node deployment algorithm. In Proceedings of the Canadian Conference on Electrical and Computer Engineering, Toronto, ON, Canada, 4–7 May 2014. [Google Scholar]
- Guo, Y.N.; Liu, D.; Liu, Y.; Chen, M. The coverage optimization for wireless sensor networks based on quantum-inspired cultural algorithm. In Lecture Notes in Electrical Engineering; Springer: Berlin, Heidelberg, 2013; Volume 254 LNEE, pp. 87–96. [Google Scholar]
- Lin, T.Y.; Santoso, H.A.; Wu, K.R.; Wang, G.L. Enhanced deployment algorithms for heterogeneous directional mobile sensors in a bounded monitoring area. IEEE Trans. Mob. Comput. 2017, 16, 744–758. [Google Scholar] [CrossRef]
- Zou, Y.; Chakrabarty, K. Sensor Deployment and Target Localization in Distributed Sensor Networks. ACM Trans. Embed. Comput. Syst. (TECS) 2004, 3, 61–91. [Google Scholar] [CrossRef]
- Loscrí, V.; Natalizio, E.; Mitton, N. Performance evaluation of novel distributed coverage techniques for swarms of flying robots. In Proceedings of the IEEE Wireless Communications and Networking Conference (WCNC), Istanbul, Turkey, 6–9 April 2014; pp. 3278–3283. [Google Scholar]
- Sallam, G.; Baroudi, U.; Al-Shaboti, M. Multi-Robot Deployment Using a Virtual Force Approach: Challenges and Guidelines. Electronics 2016, 5, 34. [Google Scholar] [CrossRef]
- Wang, X.; Tan, G.; Liu, X.; Zhao, Z. A Molecular Force-Based Deployment Algorithm for Flight Coverage Maximization of Multi-Rotor UAV. J. Intell. Robot. Syst. 2019, 95, 1063–1078. [Google Scholar] [CrossRef]
- Aurenhammer, F.; Klein, R.; Lee, D.-T.; Klein, R. Voronoi Diagrams and Delaunay Triangulations; World Scientific: Singapore, 2013. [Google Scholar]
- Han, Y.H.; Kim, Y.H.; Kim, W.; Jeong, Y.S. An energy-efficient self-deployment with the centroid-directed virtual force in mobile sensor networks. Simulation 2012, 88, 1152–1165. [Google Scholar] [CrossRef]
- Pavone, M.; Arsie, A.; Frazzoli, E.; Bullo, F. Distributed algorithms for environment partitioning in mobile robotic networks. IEEE Trans. Automat. Control 2011, 56, 1834–1848. [Google Scholar] [CrossRef]
- Qu, Y. Wireless Sensor Network Deployment, 2013. Ph.D. Thesis, FLORIDA International University, Miami, FL, USA, 2013. [Google Scholar]
- Qiu, C.; Shen, H. A delaunay-based coordinate-free mechanism for full coverage in wireless sensor networks. IEEE Trans. Parallel Distrib. Syst. 2014, 25, 828–839. [Google Scholar] [CrossRef]
- Sung, T.W.; Yang, C.S. Voronoi-based coverage improvement approach for wireless directional sensor networks. J. Netw. Comput. Appl. 2014, 39, 202–213. [Google Scholar] [CrossRef]
- Bartolini, N.; Bongiovanni, G.; La Porta, T.; Silvestri, S.; Vincenti, F. Voronoi-based deployment of mobile sensors in the face of adversaries. In Proceedings of the 2014 IEEE International Conference on Communications (ICC), Sydney, NSW, Australia, 10–14 June 2014; pp. 532–537. [Google Scholar]
- Wang, G.; Cao, G.; La Porta, T.F. Movement-assisted sensor deployment. Proc. IEEE INFOCOM 2004, 4, 2469–2479. [Google Scholar] [CrossRef]
- Lee, H.J.; Kim, Y.H.; Han, Y.H.; Park, C.Y. Centroid-based movement assisted sensor deployment schemes in wireless sensor networks. In Proceedings of the IEEE Vehicular Technology Conference, Anchorage, AK, USA, 20–23 September 2009. [Google Scholar]
- Fang, W.; Song, X.; Wu, X.; Sun, J.; Hu, M. Novel efficient deployment schemes for sensor coverage in mobile wireless sensor networks. Inf. Fusion 2018, 41, 25–36. [Google Scholar] [CrossRef]
- Aziz, N.A.B.A.; Mohemmed, A.W.; Alias, M.Y. A wireless sensor network coverage optimization algorithm based on particle swarm optimization and Voronoi diagram. In Proceedings of the 2009 International Conference on Networking, Sensing and Control, Okayama, Japan, 26–29 March 2009; pp. 602–607. [Google Scholar]
- Azlina, N.; Aziz, A. Wireless Sensor Networks Coverage-Energy Algorithms Based on Particle Swarm Optimization. Emir. J. Eng. Res. 2013, 18, 41–52. [Google Scholar]
- Mahboubi, H.; Vaezi, M.; Labeau, F. Mobile Sensors Deployment Subject to Location Estimation Error. IEEE Trans. Veh. Technol. 2017, 66, 668–678. [Google Scholar] [CrossRef]
- Abo-Zahhad, M.; Sabor, N.; Sasaki, S.; Ahmed, S.M. A centralized immune-Voronoi deployment algorithm for coverage maximization and energy conservation in mobile wireless sensor networks. Inf. Fusion 2016, 30, 36–51. [Google Scholar] [CrossRef]
- Habibi, J.; Mahboubi, H.; Aghdam, A.G. A gradient-based coverage optimization strategy for mobile sensor networks. IEEE Trans. Control Netw. Syst. 2017, 4, 477–488. [Google Scholar] [CrossRef]
- Mahboubi, H.; Moezzi, K.; Aghdam, A.G.; Sayrafian-Pour, K.; Marbukh, V. Distributed deployment algorithms for improved coverage in a network of wireless mobile sensors. IEEE Trans. Ind. Inform. 2014, 10, 163–174. [Google Scholar] [CrossRef]
- Guo, J.; Jafarkhani, H. Movement-efficient sensor deployment in wireless sensor networks. In Proceedings of the 2018 IEEE International Conference on Communications (ICC), Kansas City, MO, USA, 20–24 May 2018; pp. 1–6. [Google Scholar]
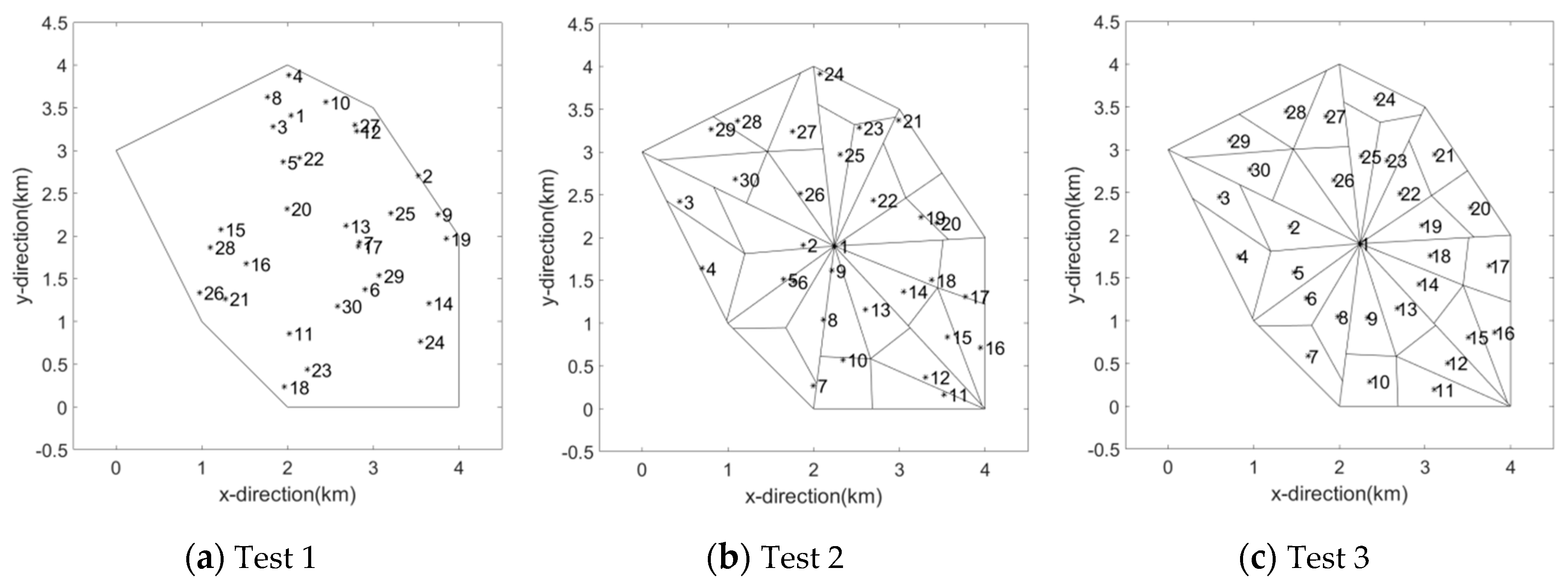

| Test | P (%) | ||
|---|---|---|---|
| Initial | Best | Avg | |
| 1 | 76.51 | 97.15 | 94.47 |
| 2 | 84.78 | 97.81 | 96.67 |
| 3 | 88.82 | 97.16 | - |
| Test | Size | n (used) | n (ideal) | Coverage Ratio (%) | ||||
|---|---|---|---|---|---|---|---|---|
| PSO Voronoi | WSNPSOcon | CIVA | Cr 1 | Cr 2 | ||||
| 1 | 50 × 50 | 10 | 21 | 58.36 | 57.96 | 60.24 | 56.97 | 59.83 |
| 2 | 50 × 50 | 20 | 21 | 94.23 | 93.34 | 93.55 | 95.17 | 94.75 |
| 3 | 50 × 50 | 30 | 21 | 98.80 | 98.64 | 97.37 | 100.00 | 100.00 |
| 4 | 100 × 100 | 60 | 86 | 77.62 | 73.56 | 78.59 | 83.48 | 81.74 |
| 5 | 100 × 100 | 80 | 86 | 88.13 | 81.66 | 88.94 | 97.66 | 96.68 |
| 6 | 100 × 100 | 100 | 86 | 92.70 | 84.90 | 92.47 | 99.87 | 99.91 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, X.; Tan, G.-z.; Lu, F.-L.; Zhao, J.; Dai, Y.-s. A Molecular Force Field-Based Optimal Deployment Algorithm for UAV Swarm Coverage Maximization in Mobile Wireless Sensor Network. Processes 2020, 8, 369. https://doi.org/10.3390/pr8030369
Wang X, Tan G-z, Lu F-L, Zhao J, Dai Y-s. A Molecular Force Field-Based Optimal Deployment Algorithm for UAV Swarm Coverage Maximization in Mobile Wireless Sensor Network. Processes. 2020; 8(3):369. https://doi.org/10.3390/pr8030369
Chicago/Turabian StyleWang, Xi, Guan-zheng Tan, Fan-Lei Lu, Jian Zhao, and Yu-si Dai. 2020. "A Molecular Force Field-Based Optimal Deployment Algorithm for UAV Swarm Coverage Maximization in Mobile Wireless Sensor Network" Processes 8, no. 3: 369. https://doi.org/10.3390/pr8030369
APA StyleWang, X., Tan, G.-z., Lu, F.-L., Zhao, J., & Dai, Y.-s. (2020). A Molecular Force Field-Based Optimal Deployment Algorithm for UAV Swarm Coverage Maximization in Mobile Wireless Sensor Network. Processes, 8(3), 369. https://doi.org/10.3390/pr8030369





