BYOD Security: A Study of Human Dimensions
Abstract
:1. Introduction and Background
- RQ.1
- Are Australian businesses and employees sufficiently aware of BYOD security aspects in terms of risks involved (threats and attacks) and security mechanisms available to protect mobile devices?
- RQ.2
- How have employees responded to security mechanisms enforced by organisations?
- RQ.3
- Are there any potential weaknesses in Australian business internal networks from the perspective of end users which have a direct effect on BYOD security and what are they?
- RA.1
- Understand the security practices utilised by Australian businesses to protect resources and staff engaging in BYOD.
- RA.2
- Investigate how users practice BYOD security in regard to work, including typical working conditions and how work tasks are completed with mobile devices.
- RA.3
- Explore users’ perceptions, opinions, and reactions towards organizational BYOD security measures.
2. Literature Review
3. Methods
3.1. Survey Questionnaire Design
3.2. Data Analysis
4. Survey Results
4.1. Fundamental Demographic Information
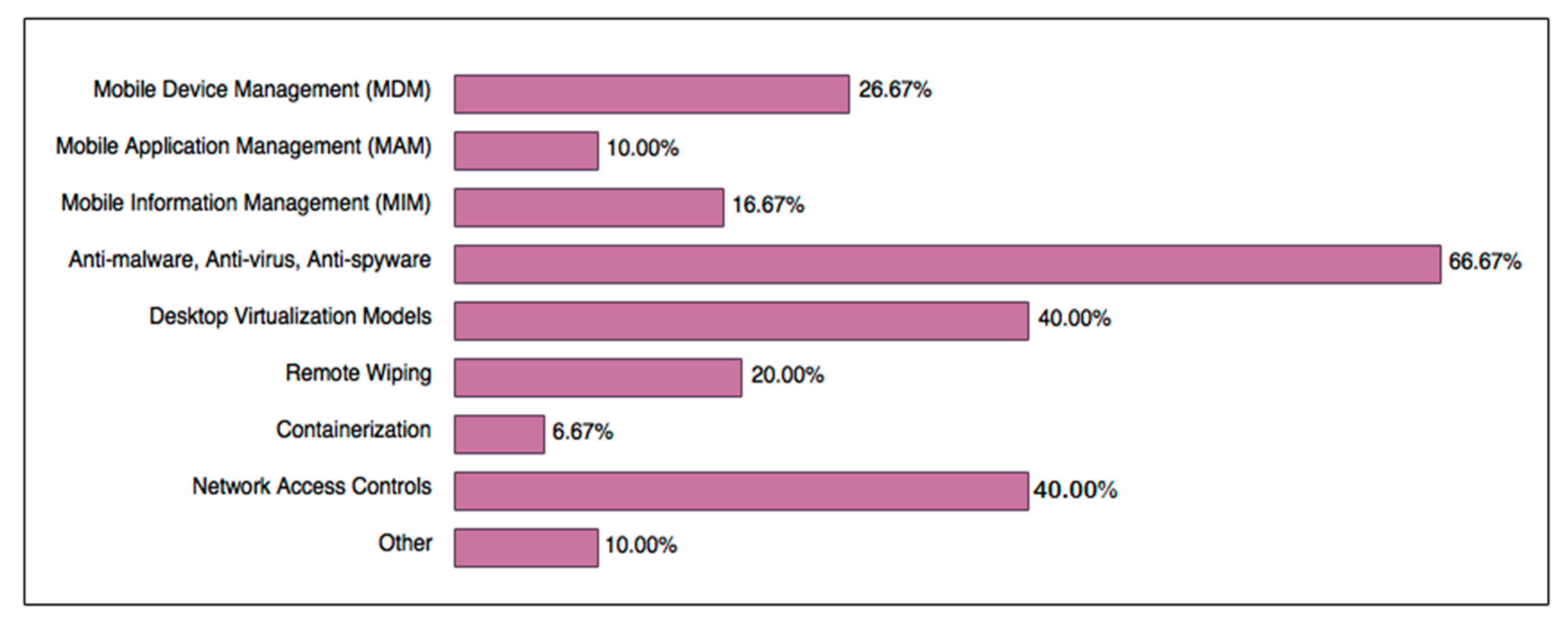
4.2. Business BYOD Security Practices
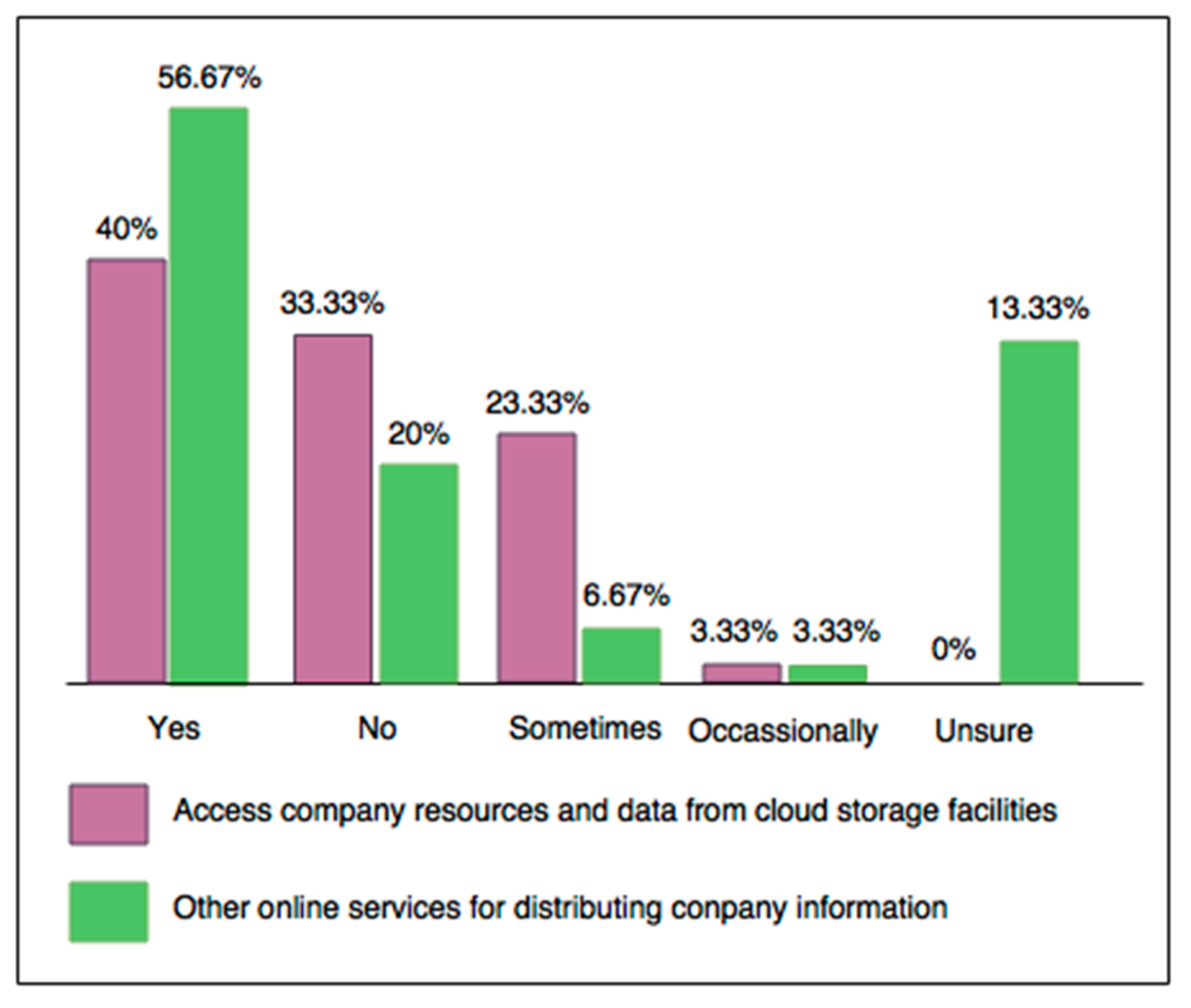
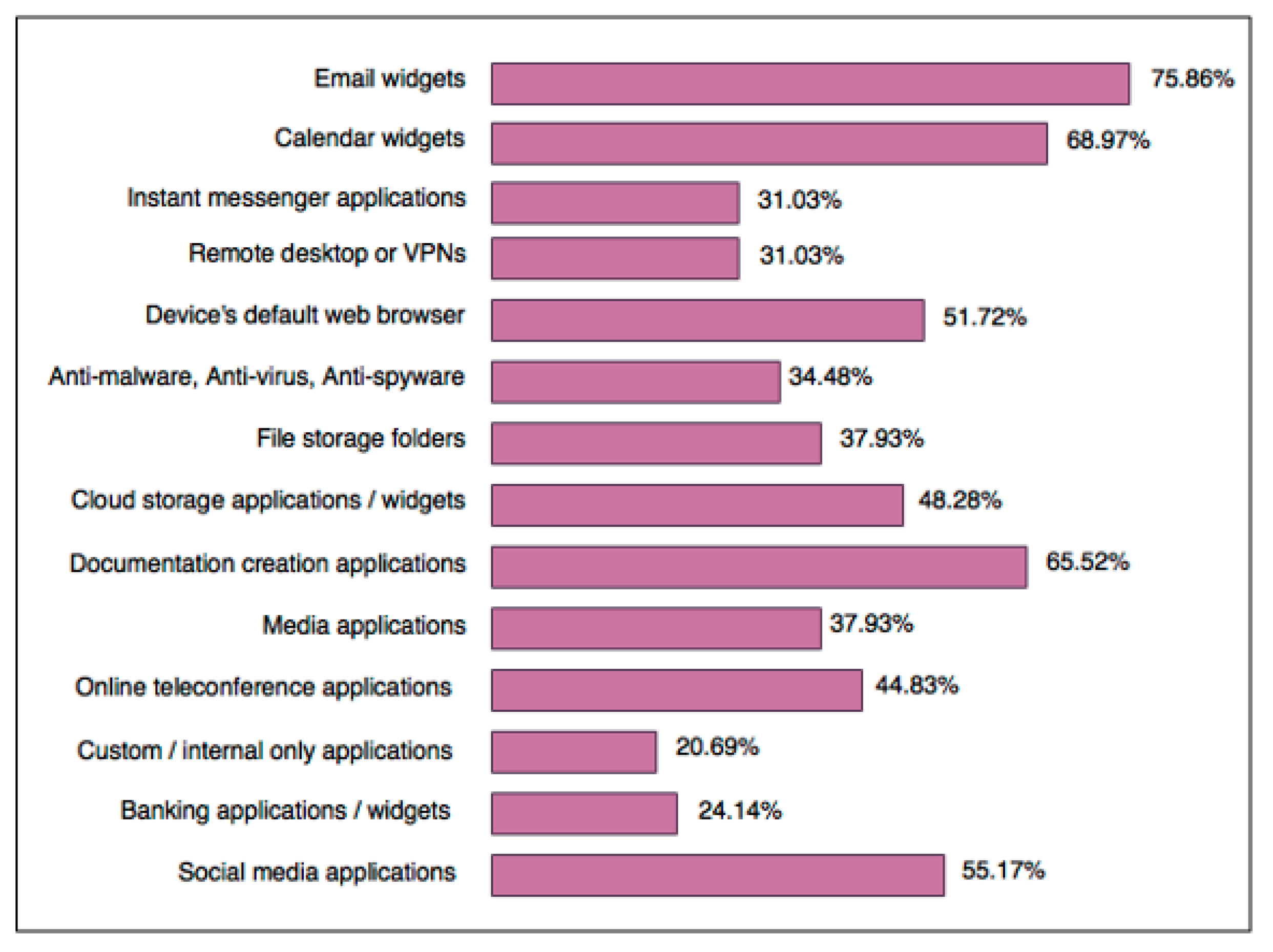
4.3. User Practices in Regard to BYOD at Work
- -
- It is permitted, though it is heavily monitored by MDM, MIM, or other strict monitoring policies—10.34%;
- -
- The company trusts employees enough to allow data to be stored on devices without supervision—31.03%;
- -
- Only publicly accessible data and resources are permitted on mobile devices—10.34%;
- -
- This condition is forbidden for all staff—20.69%;
- -
- No permission is granted, yet employees sometimes do this anyway to finish tasks after hours—6.9%.
4.4. User Perceptions of BYOD in the Workplace
- -
- More confidence interacting with sensitive data and resources—42.86%;
- -
- More trust is placed towards the organisation’s processes—42.86%;
- -
- Some resources and data are easier to access as a result—19.05%;
- -
- Some work processes are more efficient since BYOD security measures were implemented—23.81%;
- -
- Relief that staff is monitored and controlled more closely—14.29%.
- -
- BYOD security policies have restricted access to certain resources and data too much—28.57%;
- -
- Some methods have forbidden staff to use resources and data they once had access to—14.29%;
- -
- Security methods used for certain resources are too excessive—14.29%;
- -
- Employees tend to avoid some resources and data because of the security measures applied to them—35.72;
- -
- Security methods make access to resources too inconvenient—35.71%.
- -
- Some policies or procedures are too restrictive; therefore, it is inconvenient to complete certain tasks—7.41%;
- -
- They are too biased towards organisational interests and disregard employees—7.41%;
- -
- A policy does not suit my department or job role requirements—3.70%;
- -
- A policy is difficult to understand; therefore, there is resistance—3.70%;
- -
- The remaining 18.52% of respondents expressed the need for more BYOD-specific policies, especially in regard to data access and to ensure that security methods are compatible with their mobile devices.
5. Analysis and Discussion
5.1. Awareness of BYOD Security Aspects
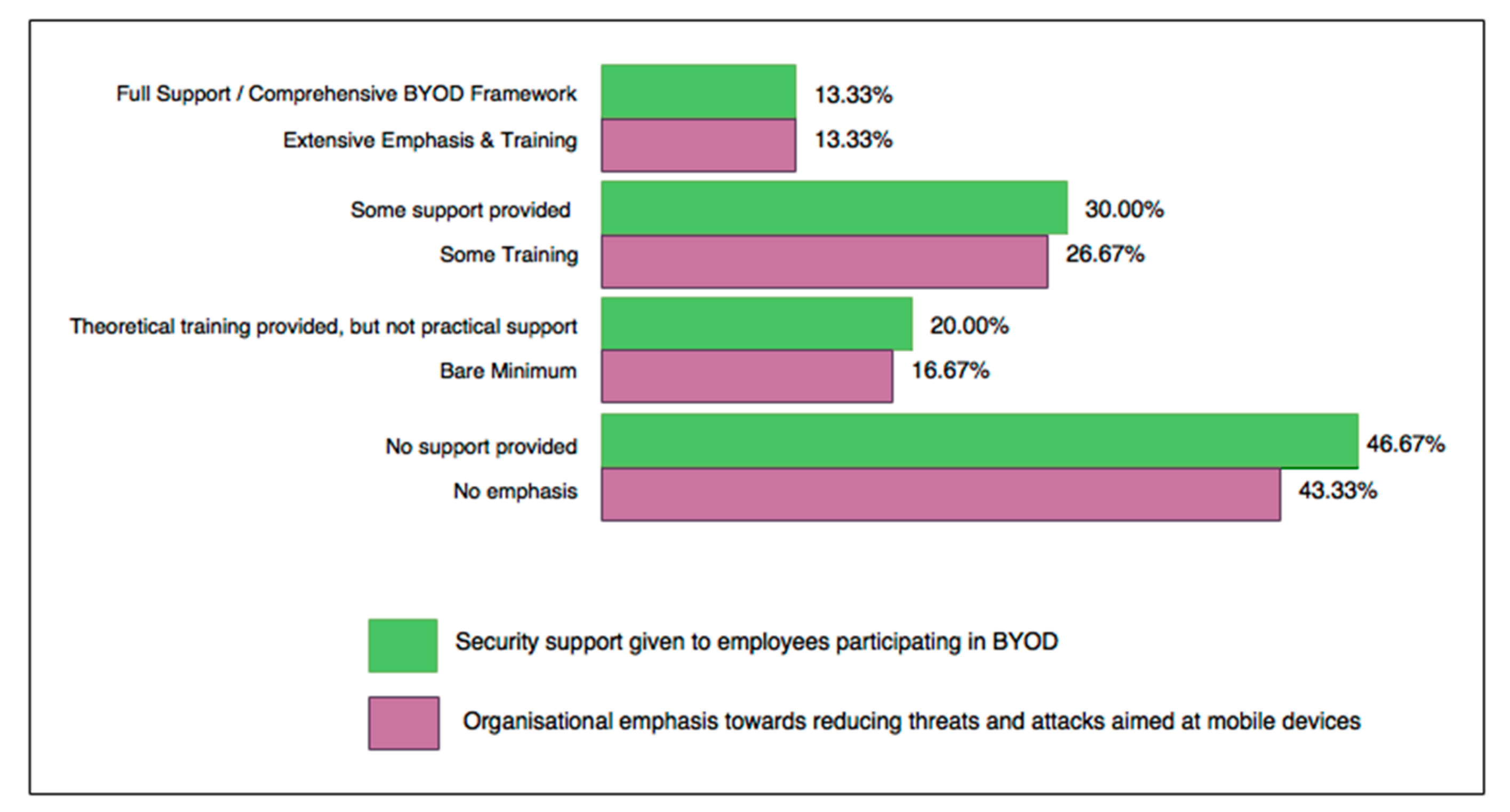
5.2. Employee Responses to Security Mechanisms Applied for BYOD
- -
- A monitoring policy that pauses or turns off BYOD security agents installed on mobile devices when employees are not working.
- -
- Explicitly publishing in usage and liability agreements exactly what is monitored, why and when, and provides descriptions of activities they may be investigated as suspicious [23].
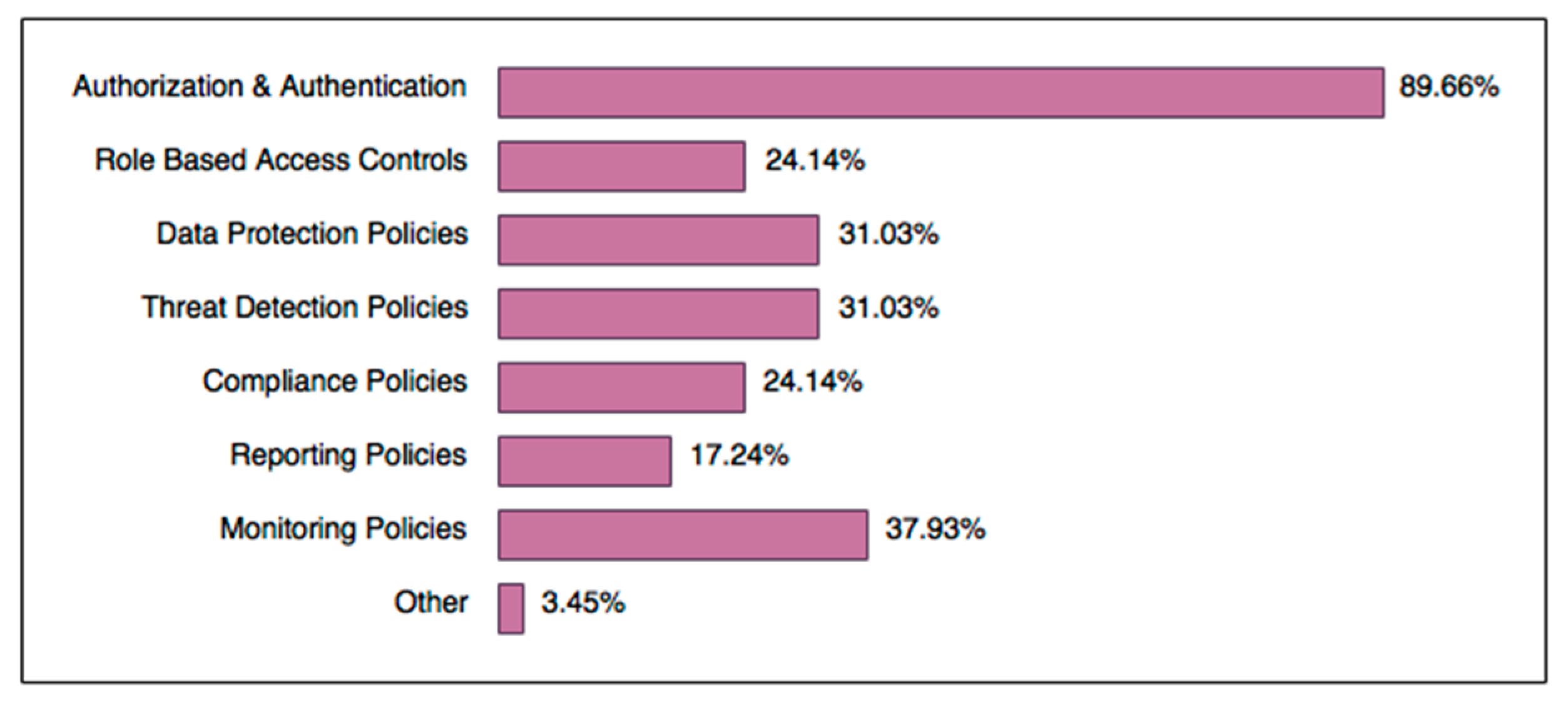
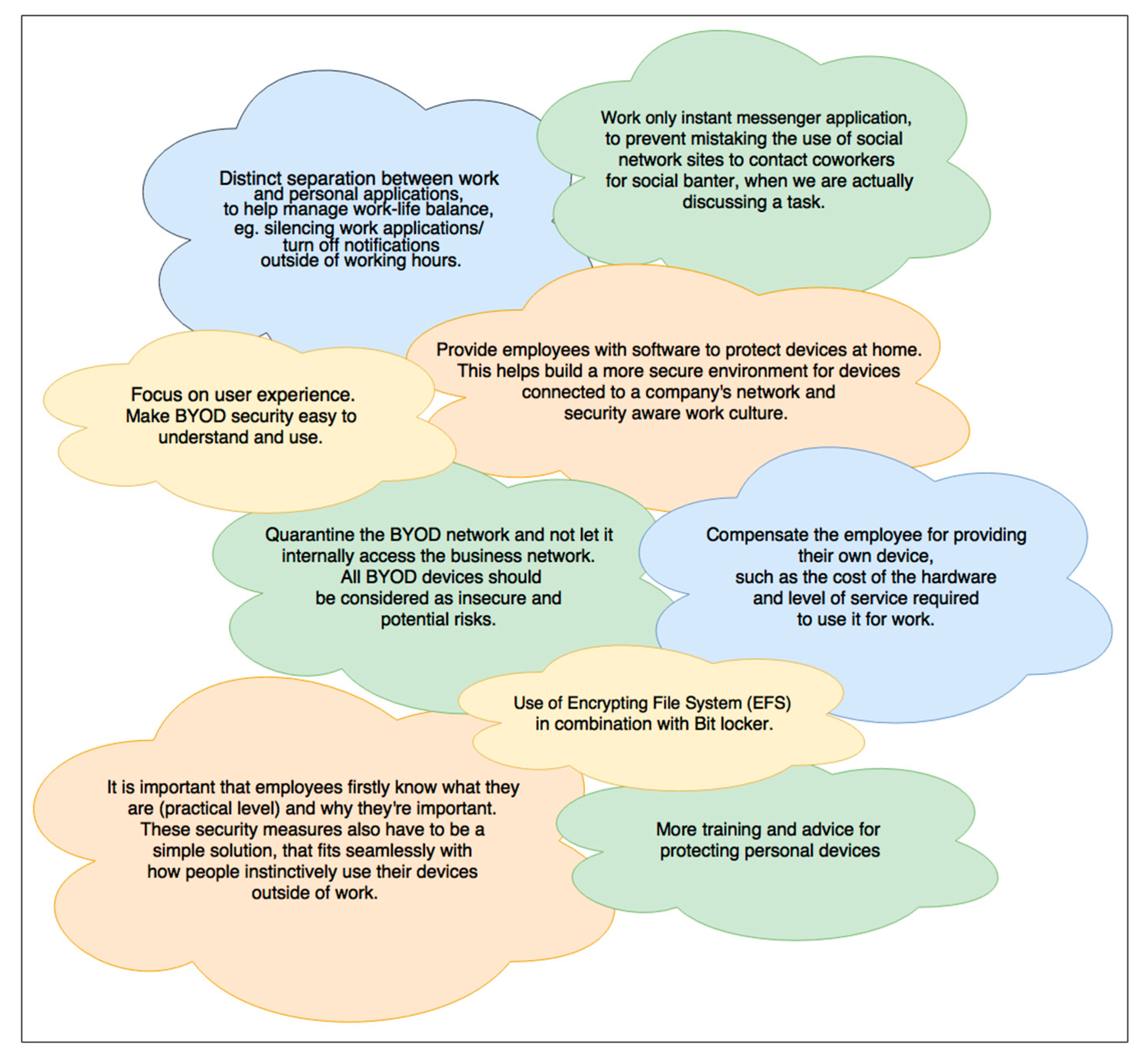
5.3. Weaknesses Affecting BYOD Security from the End Users Perspective
- -
- Explaining simply in acceptable usage and user agreements the goals of BYOD specific security policies, expected behaviours, permitted activities, and prohibited access rules whilst participating in BYOD initiatives [5].
- -
- -
- Base the aims of attack countermeasure policies on risk and threat assessments findings [51].
- -
6. Limitations of the Current Study
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Geoff, E. Bring Your Own Device-the New Normal: The NCSC View on BYOD and the Rise in Home Working. Available online: https://www.ncsc.gov.uk/blog-post/bring-your-own-device-the-new-normal (accessed on 20 August 2020).
- Ratchford, M.; El-Gayar, O.; Noteboom, C.; Wang, Y. BYOD security issues: A systematic literature review. Inf. Secur. J. Glob. Perspect. 2021, 1–21. [Google Scholar] [CrossRef]
- Romer, H. Best practices for BYOD security. Comput. Fraud Secur. 2014, 2014, 13–15. [Google Scholar] [CrossRef]
- Morrow, B. BYOD security challenges: Control and protect your most sensitive data. Netw. Secur. 2012, 2012, 5–8. [Google Scholar] [CrossRef]
- Dhingra, M. Legal Issues in Secure Implementation of Bring Your Own Device (BYOD). Procedia Comput. Sci. 2016, 78, 179–184. [Google Scholar] [CrossRef] [Green Version]
- Brodin, M. Combining ISMS with strategic management: The case of BYOD. In Proceedings of the 8th IADIS International Conference Information Systems, Madeira, Portugal, 14–16 March 2015; pp. 161–168. [Google Scholar]
- Palanisamy, R.; Norman, A.A.; Kiah, M.L.M. Compliance with Bring Your Own Device security policies in organizations: A systematic literature review. Comput. Secur. 2020, 98, 101998. [Google Scholar] [CrossRef]
- Bullock, L. The Future of BYOD: Statistics, Predictions and Best Practices to Prep for the Future; Forbes: Jersey City, NJ, USA, 2019; Available online: https://www.forbes.com/sites/lilachbullock/2019/01/21/the-future-of-byod-statistics-predictions-and-best-practices-to-prep-for-the-future/#1c6a1fa91f30 (accessed on 20 August 2020).
- Barker, J. Kensington Survey: Majority of Organizations Report BYOD Creates Greater Security Risks; Close-Up Media Inc.: Jacksonville, FL, USA, 2014; pp. 1–2. [Google Scholar]
- Malloy, M. Webroot Rolls out New BYOD Security Report. In Wireless News; Close-Up Media Inc.: Jacksonville, FL, USA, 2014; pp. 1–2. [Google Scholar]
- Johnson, K.; DeLaGrange, T. SANS Survey on Mobility/BYOD Security Policies and Practices. In Whitepaper; SANS Institute: Bethesda, MD, USA, 2012; pp. 1–21. [Google Scholar]
- Michelberger, P.; Fehér-Polgár, P. BYOD Security Strategy (Aspects of a Managerial Decision). J. Secur. Sustain. Issues 2020, 9, 1135–1144. [Google Scholar] [CrossRef]
- Weidman, J.; Grossklags, J. I like it, but I hate it: Employee perceptions towards an institutional transition to BYOD second-factor authentication. In Proceedings of the 33rd Annual Computer Security Applications Conference, Orlando, FL, USA, 4–8 December 2017; pp. 212–224. [Google Scholar]
- El Gbouri, A.; Mensch, S. Factors Affecting Information Security and the Widest Implementations of Bring Your Own Device (BYOD) Programs. ACET J. Comp. Edu. Res. 2020, 14, 1–13. [Google Scholar]
- Ameen, N.; Willis, R.; Shah, M.H. An examination of the gender gap in smartphone adoption and use in Arab countries: A cross-national study. Comp. Hum. Behav. 2018, 89, 148–162. [Google Scholar] [CrossRef] [Green Version]
- Palanisamy, R.; Norman, A.A.; Kiah, M.L.M. BYOD Policy Compliance: Risks and Strategies in Organizations. J. Comput. Inf. Syst. 2020, 62, 61–72. [Google Scholar] [CrossRef]
- Thomson, G. BYOD: Enabling the chaos. Netw. Secur. 2012, 2012, 5–8. [Google Scholar] [CrossRef]
- Wang, X.; Weeger, A.; Gewald, H. Factors driving employee participation in corporate BYOD programs: A cross-national comparison from the perspective of future employees. Australas. J. Inf. Syst. 2017, 21, 1–22. [Google Scholar] [CrossRef] [Green Version]
- Chigada, J.; Kyobe, M.E. Evaluating factors contributing to misalignment of the South African National Cybersecurity Policy Framework. In Proceedings of the 2018 International Conference on Information Resources Management (CONF-IRM 2018). Ningbo, China, 4–6 June 2018; pp. 1–16. [Google Scholar]
- Alotaibi, B.; Almagwashi, H. A Review of BYOD Security Challenges, Solutions and Policy Best Practices. In Proceedings of the 2018 1st International Conference on Computer Applications & Information Security (ICCAIS), Riyadh, Saudi Arabia, 4–6 April 2018; pp. 1–6. [Google Scholar]
- Ward, J.; Dogan, H.; Apeh, E.T.; Mylonas, A.; Katos, V. Using human factor approaches to an organisation’s Bring Your Own Device scheme. In Proceedings of the 5th International Conference on Human Aspects of Information Security, Privacy and Trust. Vancouver, BC, Canada, 8–14 April 2017; pp. 396–413. [Google Scholar]
- French, A.; Guo, C.; Schmidt, M.; Shim, J. An exploratory study on BYOD in class: Opportunities and concerns. In Proceedings of the Twenty-first Americas Conference on Information Systems, Fajardo, Puerto Rico, 13–15 August 2015; pp. 1–7. [Google Scholar]
- Pinchot, J. Bring your own device to work: Benefits, security risks, and governance issues. Issues Inf. Syst. 2015, 16, 237–244. [Google Scholar]
- Hallett, J.; Aspinall, D. Capturing Policies for BYOD. In Proceedings of the 32nd International Conference on ICT Systems Security and Privacy Protection—IFIP SEC 2017, Rome, Italy, 29–31 May 2017; pp. 310–323. [Google Scholar]
- Garba, A.; Armarego, J.; Murray, D. Bring Your Own Device Organisational Information Security and Privacy. ARPN J. Engg. Appl. Sci. 2015, 10, 1279–1287. [Google Scholar]
- Wang, W.; Wei, J.; Vangury, K. Bring Your Own Device Security Issues and Challenges. In Proceedings of the 11th Annual IEEE CCNC-Mobile Device, Platform and Communication, Las Vegas, NV, USA, 10–13 January 2014; pp. 80–85. [Google Scholar]
- Bello, A.G.; Murray, D.; Armarego, J. A systematic approach to investigating how information security and privacy can be achieved in BYOD environments. Inf. Comp. Security 2017, 25, 475–492. [Google Scholar] [CrossRef]
- Tu, Z.; Adkins, J.; Zhao, G.Y. Complying with BYOD security policies: A moderation model based on protection motivation theory. J. Midwest Assoc. Inf. Syst. 2019, 1, 11–28. [Google Scholar]
- Palanisamy, R.; Wu, Y. Users’ attitude on perceived security of enterprise systems mobility: An empirical study. Inf. Comp. Security. 2021, 29, 159–186. [Google Scholar] [CrossRef]
- Wani, T.A.; Mendoza, A.; Gray, K. BYOD in hospitals-Security issues and mitigation strategies. In Proceedings of the Australasian Computer Science Week Multiconference Proceedings (ACSW’19), Sydney, Australia, 29–31 January 2019; pp. 1–10. [Google Scholar]
- Yang, X.; Wang, X.; Yue, W.T.; Sia, C.L.; Luo, X. Security Policy Opt-in Decisions in Bring-Your-Own-Device (BYOD)–A Persuasion and Cognitive Elaboration Perspective. J. Organ. Comput. Electron. Commer. 2019, 29, 274–293. [Google Scholar] [CrossRef]
- Safa, N.S.; Maple, C.; Watson, T.; Von Solms, R. Motivation and opportunity based model to reduce information security insider threats in organisations. J. Inf. Secur. Appl. 2018, 40, 247–257. [Google Scholar] [CrossRef] [Green Version]
- Ameen, N.; Tarhini, A.; Shah, M.H.; Madichie, N.O. Employees’ behavioural intention to smartphone security: A gender-based, cross-national study. Comp. Hum. Behav. 2020, 104, 106184. [Google Scholar] [CrossRef]
- Chigada, J.; Daniels, N. Exploring information systems security implications posed by BYOD for a financial services firm. Bus. Inf. Rev. 2021, 38, 115–126. [Google Scholar] [CrossRef]
- Aguboshim, F.C.; Udobi, J.I. Security issues with mobile IT: A narrative review of Bring Your Own Device (BYOD). J. Inf. Eng. Appl. 2019, 8, 56–66. [Google Scholar]
- Downer, K.; Bhattacharya, M. BYOD Security: A New Business Challenge. In Proceedings of the Proceedings of the 5th International Symposium on Cloud and Service Computing, Chengdu, China, 19–21 December 2016; pp. 1128–1133. [Google Scholar]
- Agudelo-Serna, C.A.; Ahmad, A.; Bosua, R.; Maynard, S.B. Strategies to mitigate knowledge leakage risk caused by the use of mobile devices: A preliminary study. In Proceedings of the 38th International Conference on Information Systems (ICIS 2017), Seoul, Korea, 10–13 December 2017; pp. 1–24. [Google Scholar]
- Cho, V.; Ip, W.H. A study of BYOD adoption from the lens of threat and coping appraisal of its security policy. Enterp. Inf. Syst. 2018, 12, 659–673. [Google Scholar] [CrossRef]
- Crossler, R.E.; Bélanger, F. Why would I use location-protective settings on my smartphone? Motivating protective behaviors and the existence of the privacy knowledge–belief gap. Inf. Syst. Res. 2019, 30, 1–12. [Google Scholar] [CrossRef]
- Chen, H.; Li, Y.; Chen, L.; Yin, J. Understanding employees’ adoption of the Bring-Your-Own-Device (BYOD): The roles of information security-related conflict and fatigue. J. Enterp. Inf. Manag. 2020, 34, 770–792. [Google Scholar] [CrossRef]
- Bradford Networks. Ten Steps to Secure BYOD. In Whitepaper; Bradford Networks: Boston, MA, USA, 2012; pp. 1–4. [Google Scholar]
- Eslahi, M.; Naseri, M.; Hashim, H.; Tahir, N.M.; Mat Saad, E. BYOD: Current State and Security Challenges; Universitii Teknologi MARA: Shah Alam, Malaysia, 2013; pp. 1–4. [Google Scholar]
- Gajar, P.; Ghosh, A.; Rai, S. Bring Your Own Device (BYOD): Security risks and mitigating strategies. J. Glob. Res. Comp. Sci. 2013, 4, 62–70. [Google Scholar]
- Leavitt, N. Today’s Mobile Security Requires a New Approach. Technology News, Computer; IEEE Computer Society: Washington, DC, USA, 2013; pp. 16–19. [Google Scholar]
- Scarfo, A. New Security perspectives around BYOD. In Proceedings of the 2012 Seventh International Conference on Broadband, Wireless computing, Communication and Applications, Victoria, BC, Canada, 12–14 November 2012; pp. 446–451. [Google Scholar]
- Tokuyoshi, B. The security implications of BYOD. Network Sec. 2013, 4, 12–13. [Google Scholar] [CrossRef]
- Disterer, G.; Kleiner, C. BYOD Bring Your Own Device. Procedia Technol. 2013, 9, 43–53. [Google Scholar] [CrossRef] [Green Version]
- Armando, A.; Merlo, A.; Verderame, L. Security considerations related to the use of mobile devices in the operation of critical infrastructures. Int. J. Crit. Infras. Protectn. 2014, 7, 247–256. [Google Scholar] [CrossRef]
- Dang-Pham, D.; Pittayachawan, S. Comparing intention to avoid malware across contexts in a BYOD-enabled Australian university: A Protection Motivation Theory approach. Comp. Secur. 2014, 48, 281–297. [Google Scholar] [CrossRef]
- Pell, L. BYOD: Implementing the right policy. In IT Practices for SME Success Series: Book 1: The Role of IS Assurance & Security Management; University of Derby: Derby, UK, 2013; Volume 1, pp. 95–98. [Google Scholar]
- Kearns, G. Countering Mobile Device Threats: A mobile device security model. J. Forensic Investig. Account. 2016, 8, 36–48. [Google Scholar]
- Cisco–2014. Device Freedom without Compromising the IT Network; Whitepape: San Jose, CA, USA, 2014; pp. 1–23. [Google Scholar]
- Vignesh, U.; Asha, S. Modifying security policies towards BYOD. In Proceedings of the 2nd International Symposium on Big Data and Cloud Computing, Tetouan, Morocco, 29–39 March 2017; pp. 511–516. [Google Scholar]
- Australian Government, Department of Defence: Intelligence and Security. Bring Your Own Device (BYOD) For Executives. Paper Explaining Guidelines for Corporate BYOD Policies; Australian Cyber Security Centre: Canberra, Australia, 2014; pp. 1–3. [Google Scholar]
- Yeboah-Boateng, E.; Boaten, F. Bring Your own Device (BYOD): An evaluation of associated risks to corporate information security. Int. J. IT Eng. 2016, 4, 12–30. [Google Scholar]
- Oracle Corporation-2014. The Oracle Mobile Security Suite: Secure Adoption of BYOD. In Whitepaper; Oracle Corporation: Santa Clara, CA, USA, 2014; pp. 1–9. [Google Scholar]
- King, J. Identifying Best Practices for a BYOD Policy; University of Oregon: Eugene, Oregon, 2015; pp. 1–48. [Google Scholar]
- Agudelo, C.; Bosua, R.; Ahmad, A.; Maynard, S. Understanding knowledge leakage & BYOD (Bring Your Own device): A mobile worker perspective. In Proceedings of the Australasian Conference on Information Systems, Adelaide, Australia, 30 November–4 December 2015; pp. 1–13. [Google Scholar]
- CISCO–2008. Data Leakage Worldwide: The High Cost of Insider Threats. In White Paper; CISCO: San Jose, CA, USA, 2008; pp. 1–6. [Google Scholar]
- Koh, E.; Oh, J.; Im, C. A study on security threats and dynamic access control technology for BYOD, Smart-work Environment. In Proceedings of the International Conference of Engineers and Computer Scientists, Hong Kong, 12–14 March 2014; pp. 1–6. [Google Scholar]
- Reinfelder, L.; Weishaupl, E. A Literature Review on Smartphone Security in Organisations Using a New Theoretical Model-The Dynamic Security Success Model; University Erlangen-Nurnberg: Erlangen, Germany, 2015; pp. 1–17. [Google Scholar]
- Hemdi, M.; Deters, R. Data management in mobile enterprise applications. Procedia Comput. Sci. 2016, 94, 418–423. [Google Scholar] [CrossRef]
| Research | Focus | Limitations | Review (R)/Investigation (I) |
|---|---|---|---|
| French et al., 2015 [22] | Comparison of BYOD usage worldwide; mention of BYOD strengths and security challenges. | Superficial discussion of end users; no proposed recommendations. | R |
| Garba et al., 2015 [25] | Case study comparing BYOD security between technological, educational and financial organisations; introduction of a few attacks and threats targeting mobile devices and a summary of useful BYOD policies. | No discussion of existing security mechanisms for BYOD, despite discussions about how organisations handle security and policy suggestions. | R |
| Bradford Networks, 2012 [41] | Explanation of security challenges and general guidelines for forming BYOD policies. | Limited explanation about how to enhance access control solutions. | I |
| Eslahi et al., 2013 [42] | In depth discussion about MDM, MIM, and MAM, and Mobile bot nets. | Limitations of MDM, MIM, and MAM are not mentioned. | R |
| Gajar et al., 2013 [43] | Considerations and background information useful for understanding BYOD and some information about MDM and common security challenges. | The focus revolves exclusively around access control techniques for securing BYOD devices. | R |
| Leavitt, 2013 [44] | Explains mobile-specific security frameworks, cloud storage, and a few mobile device vulnerabilities. | Only acknowledges a few threats and MDM-related end point security methods. | I |
| Morrow, 2012 [4] | Mobile device vulnerabilities as challenges, supported by statistics that emphasise the weight of these issues. | Information about security is heavily influenced by statistics, thus is biased by trends reported years ago. | I |
| Romer, 2014 [3] | Explanation of access control methods that protect data from some threats and attack types. | Relatively limited number of security threats and attacks are presented, and advice given revolves around access control initiatives. | I |
| Scarfo, 2012 [45] | Presentation of trends and security frameworks favoured by businesses. | Biased towards desktop virtualisation, in comparison to other solutions presented. | I |
| Tokoyoshi, 2012 [46] | Explores issues that influence BYOD policies and offers suggestions to mitigate the risks. | Security frameworks are mentioned yet are not explained in detail. | I |
| Disterer et al., 2013 [47] | Opportunities and risks of BYOD and comparison of desktop virtualisation models. | Only discusses desktop virtualisation models with a mere mention of MDM. | I |
| Wang et al., 2014 [26] | Specific security frameworks and a wide range of attack types and challenges are discussed. | Frameworks suggested are limited to VPNs and MDM-based variations. | R |
| Factor | |||||
|---|---|---|---|---|---|
| Number of Employees | <100 | 100–250 | 250–500 | 500–1000 | >1000 |
| 42.86% | 11.43% | 11.43% | 2.86% | 31.43% | |
| BYOD Timeline | <1 year | 2–3 years | 3–5 years | >5 years | Unsure |
| 11.43% | 5.71% | 17.14% | 37.14% | 28.57% | |
| Working Conditions | Permanently remote | Daily travel to clients/sites | Sometimes out of office | On call after hours | Permanently in office |
| 2.86% | 5.71% | 31.43% | 20% | 40% | |
| Mobile Devices | Smartphone | Tablet | Laptop | Desktop PC | Other |
| 91.43% | 11.43% | 54.29% | 20% | 2.86% | |
| Operating Systems | Android | Apple iOS | Windows 8 | Windows 10 | Other |
| 54.29% | 34.29% | 14.29% | 28.57% | 2.86% |
| Factor | ||||
|---|---|---|---|---|
| Use of privately owned devices | Always | Sometimes | Rarely | Never (company-provided device) |
| 48.57% | 34.29% | 5.71% | 11.43% | |
| Dependence on devices for work | Extremely | Highly | Moderately | Casual use |
| 25.71% | 28.57% | 34.29% | 11.43% |
| Job Roles by Classification | |||
| Management 42.85% | Information Technology 34.31% | Retail 11.43% | MISC 25.74% |
| Industries | |||
| Retail 22.86% | Telecommunications 14.29% | Education 5.71% | Government Sector 11.43% |
| Health Care 8.57% | Finance 5.71% | Media and Arts 11.43% | Information Technology 8.57% |
| Law 2.87% | Hospitality 2.87% | Engineering 2.87% | Not for Profit 2.87% |
| Job Classification | Extremely Reliant | Highly Reliant | Moderate Use | Casual Use |
|---|---|---|---|---|
| Management | 14.28% | 11.43% | 11.43% | 0% |
| Information Technology | 5.72% | 8.58% | 8.58% | 2.86% |
| Other | 2.86% | 8.58% | 14.28% | 8.58% |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Downer, K.; Bhattacharya, M. BYOD Security: A Study of Human Dimensions. Informatics 2022, 9, 16. https://doi.org/10.3390/informatics9010016
Downer K, Bhattacharya M. BYOD Security: A Study of Human Dimensions. Informatics. 2022; 9(1):16. https://doi.org/10.3390/informatics9010016
Chicago/Turabian StyleDowner, Kathleen, and Maumita Bhattacharya. 2022. "BYOD Security: A Study of Human Dimensions" Informatics 9, no. 1: 16. https://doi.org/10.3390/informatics9010016
APA StyleDowner, K., & Bhattacharya, M. (2022). BYOD Security: A Study of Human Dimensions. Informatics, 9(1), 16. https://doi.org/10.3390/informatics9010016







