Improving DFT-Based Image Watermarking Using Particle Swarm Optimization Algorithm
Abstract
:1. Introduction
2. Background and Contributions
- Instead of using the metrics peak signal to noise ratio (PSNR)/structural similarity index (SSIM) in the fitness function of PSO algorithm, we employ the metric visual information fidelity (VIF) in conjunction with BCR criterion. It is known in the literature [29] that the VIF value reflects perceptual distortions more precisely than the PSNR. The range of VIF values is [0, 1], where the closer value to 1 represents the better fidelity with respect to the original image;
- To improve the robustness, we consider a set of geometric and signal processing attacks in the fitness function of the PSO algorithm, each one with aggressive image distortion;
- Instead of performing the imperceptibility and robustness testing using the classic images such as Lena, Baboon, etc., the proposed method is tested on 1000 color images extracted from COCO dataset [30], which contains images of complex everyday scenes with common objects in their natural context;
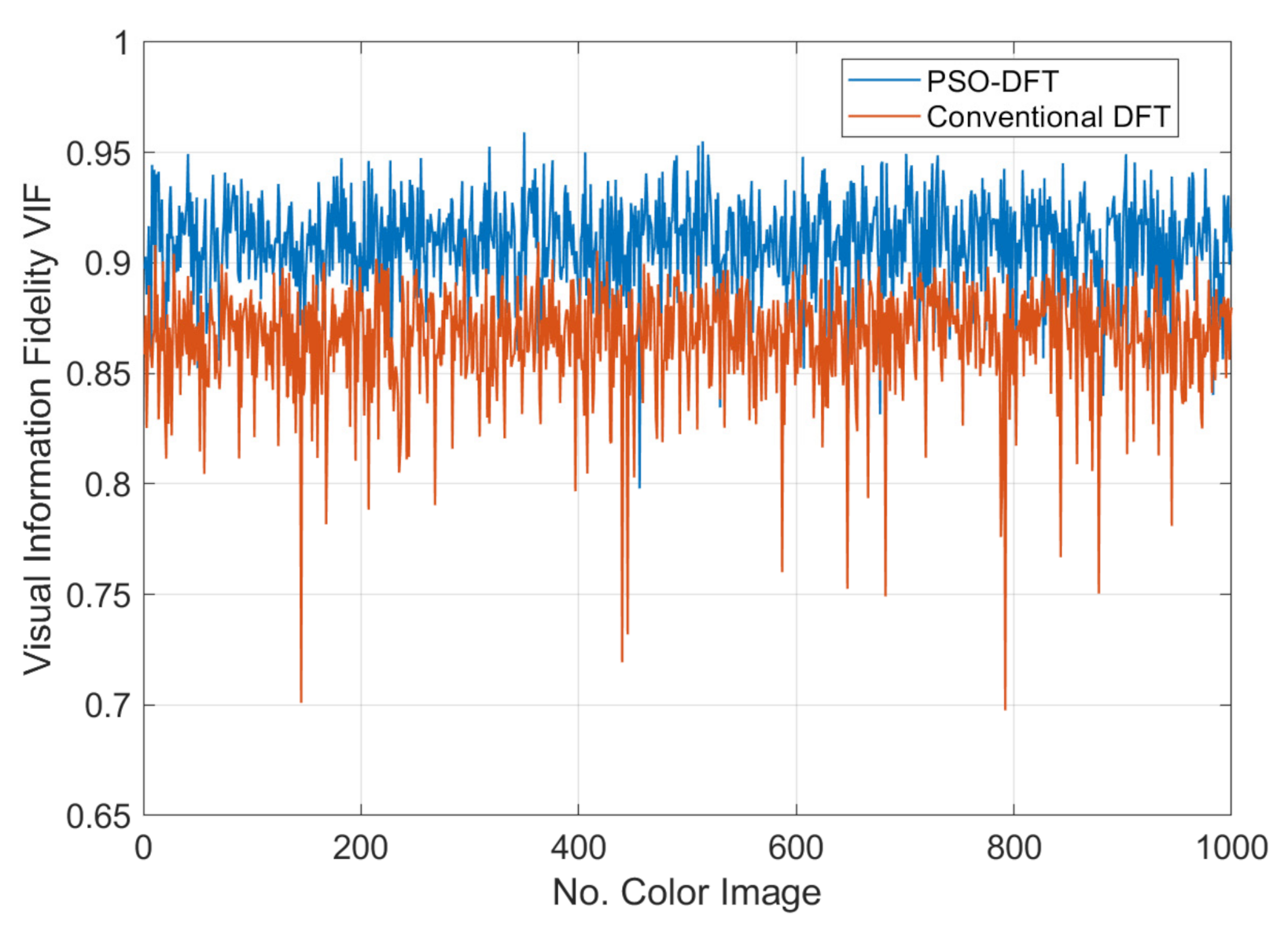
- Imperceptibility testing is performed using PSNR and VIF metrics;
- Robustness testing is performed considering a wide range of geometric, common signal processing and combined distortions;
- Detailed performance comparison with the conventional 2D DFT-based invisible watermarking is performed to show the improvements in terms of imperceptibility and robustness when the PSO optimization is adopted.
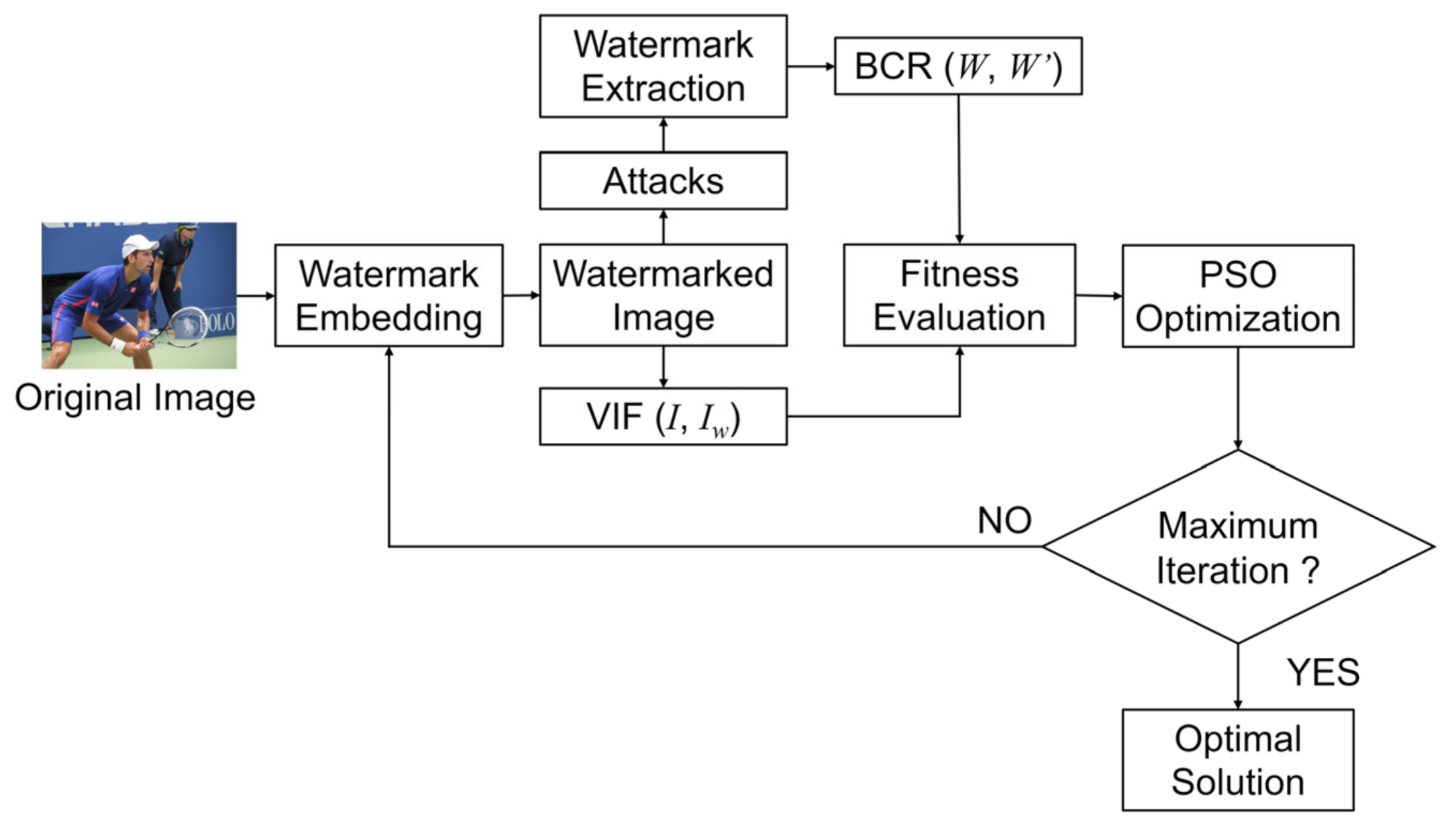
3. Proposed Method
3.1. Embedding Process
- Perform RGB-YCbCr color model transformation and isolates the luminance component Y(x,y) from YCbCr transformation;
- Supported by a secret key k1, generate a watermark which is a 1-D binary {1, 0} pseudo-random pattern with zero mean, W = {wb|b = 1, …, L}, where L is the length of the watermark;
- Apply the 2D DFT transform F(u,v) defined by (1) to the original luminance component Y(x,y) and obtain the magnitude M(u,v) and phase P(u,v) information;
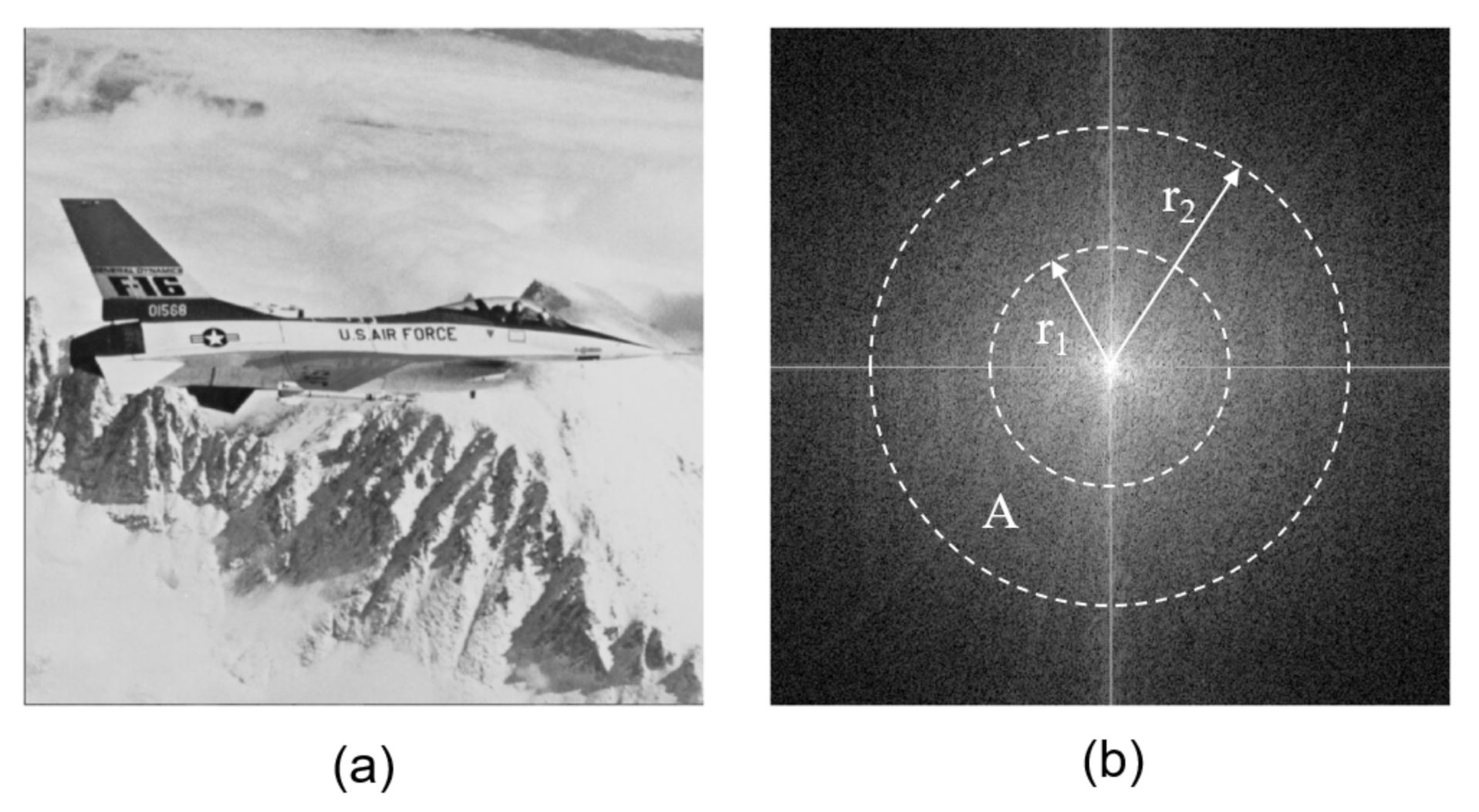
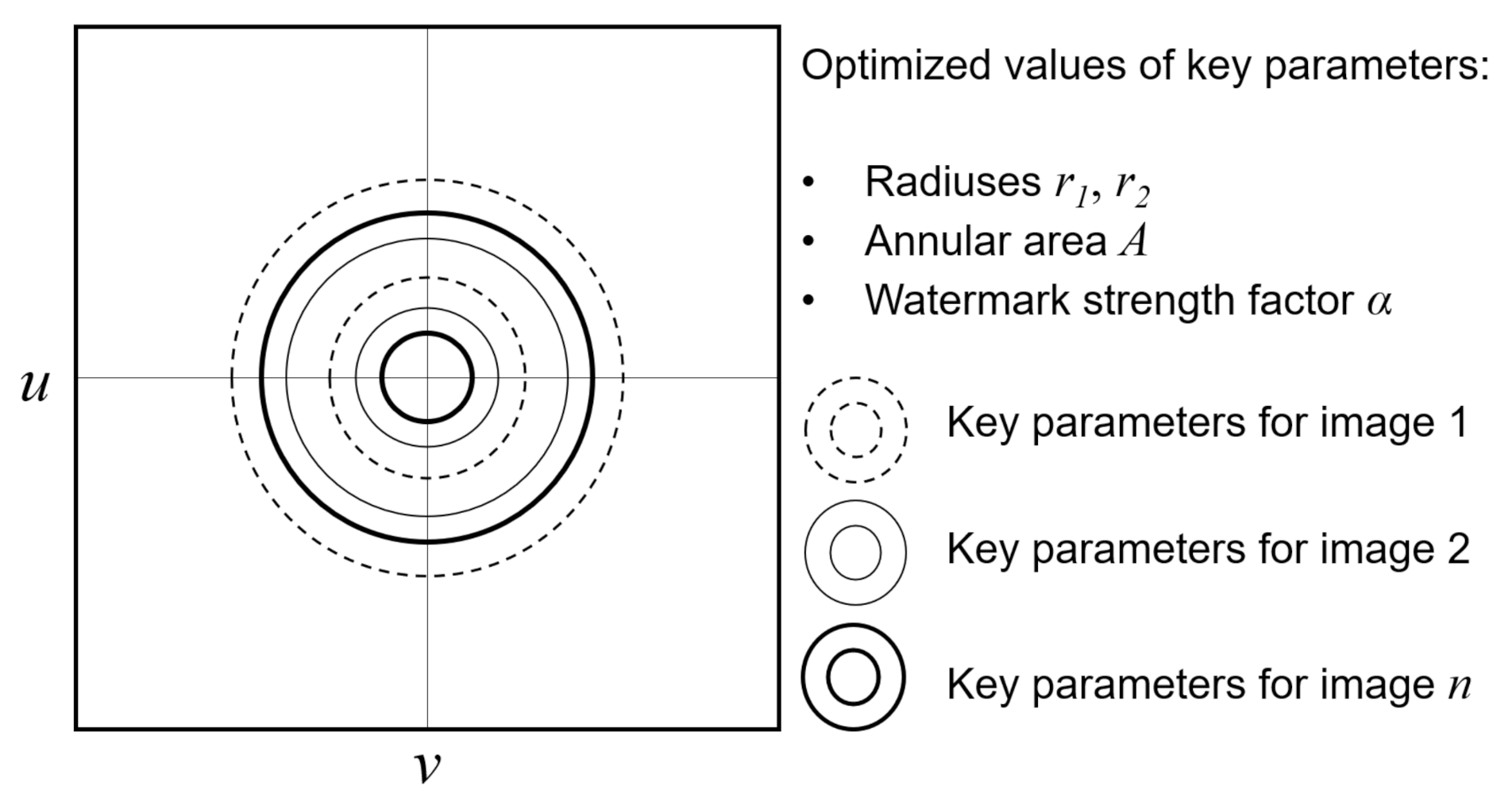
- Select a pair of radiuses r1 and r2 in M(u,v) and the annular area A = π(r22 − r12) between r1 and r2 should cover the middle frequency in M(u,v) around the zero frequency coefficient M(0,0);
- To guarantee the security of W, scramble its data bits using a secret key k2;
- Encode W using the spread spectrum modulation DS-CDMA: with a predefined secret key k3, assign to each watermark data bit wb a pseudorandom binary {−1, 1} sequence with length A/2. Each sequence is dependent on in the following way:
- Embed the encoded watermark WDS-CDMA in the coefficients of the upper half of M(u,v) in the annular area A/2 that cover the middle frequency, in an additive manner:where α is the watermark strength factor and M, M′, are the original and the watermarked DFT magnitude, respectively. According to DFT symmetrical properties, to produce real values after the watermark embedding, the lower half part of the middle frequency band of M(u,v) should be modified symmetrically.
- Return the watermarked luminance component Y′(x,y) to spatial domain using the inverse DFT (IDFT) employing M′(u,v) and the corresponding initial phase P(u,v) as shown in (8):
- Finally, using the watermarked luminance Y′(x,y) and the original chrominance information, perform YCbCr to RGB color model transformation and obtain the watermarked image Iw.
3.2. Extraction Process
- Considering the color watermarked image Iw, perform RGB-YCbCr color model transformation and obtain the watermarked luminance Y′(x,y);
- Compute the 2D DFT transform F′(u,v) from Y′(x,y) and get the watermarked magnitude M′(u,v);
- The annular area A is computed employing the values of radiuses r1 and r2 used in the embedding process;
- Split M′(u,v) in two parts, the upper half, and the lower half respectively;
- By symmetrical DFT properties, considering only the information from the upper half part of M′(u,v), the embedded watermark can be extracted using the secret key k3, computing the linear correlation cb between the normalized watermarked magnitude coefficients M′ normalized and b-th pseudorandom pattern as follows:where is the average of all values in and M′normalized = M′ − M′av, where M′av is the average of all values in M′(u,v);
- Recover the watermark data bits of W′ = { |b = 1, …, L} using the sign function as follows:
- Finally, rearrange W′ using the secret key k2.
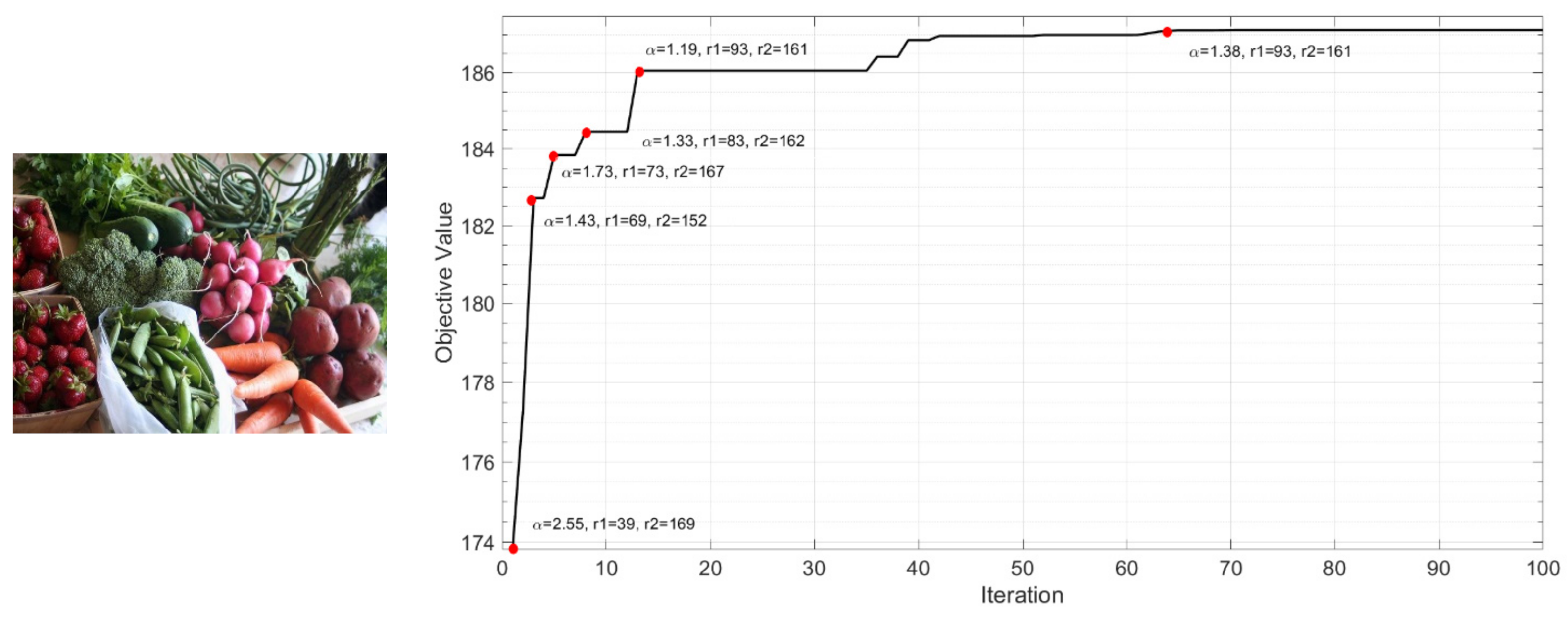
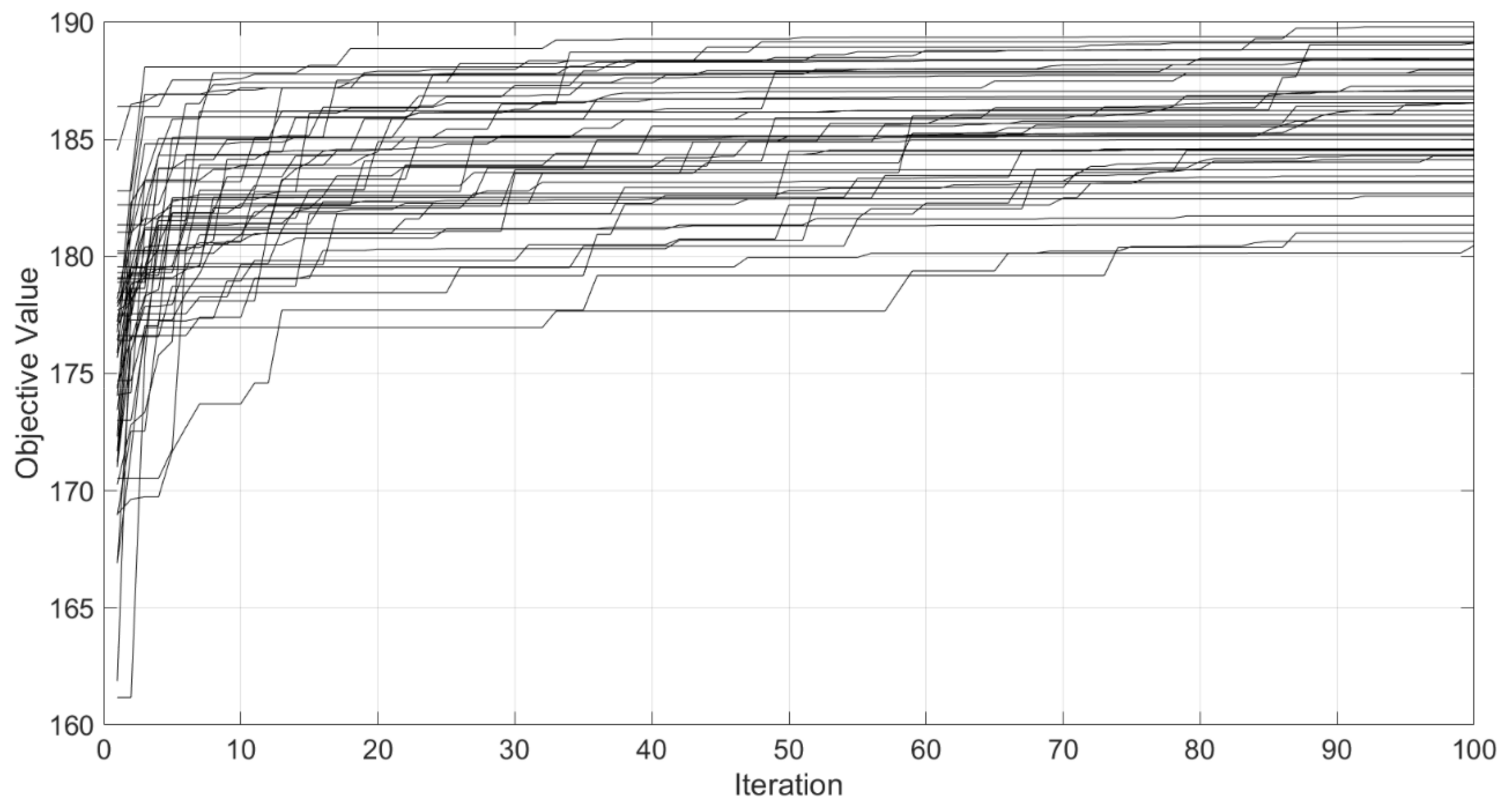
4. Optimization Key Parameters by Particle Swarm Optimization (PSO)
- Subscript i denotes the particle index 1 ≤ i ≤ population size N;
- Subscript j denotes the dimension of feature space index;
- ω is the inertia coefficient;
- C1 is the personal speedup coefficient;
- C2 is the social speedup coefficient;
- rand() is a pseudo-random number generator (PRNG) with uniform distribution in the range [0, 1];
- t denotes time;
- pi,j(t) is the position that provides the minimum cost of the j-th element of the i-th particle;
- ηj(t) is the position that provides the minimum cost of all existent particles.
5. Experimental Results and Discussion
5.1. Watermark Imperceptibility
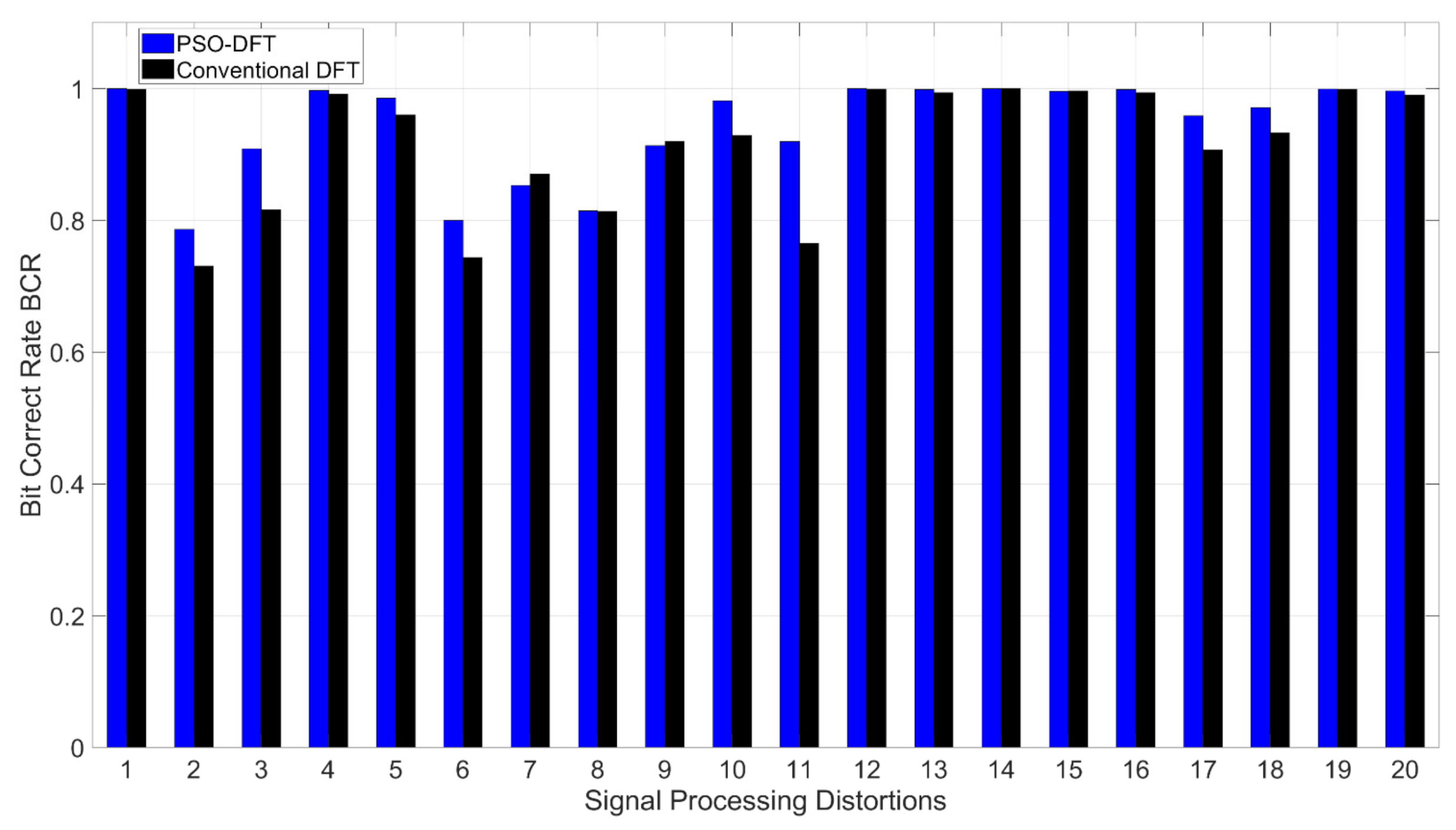
5.2. Watermark Robustness
5.2.1. Signal Processing Distortions
5.2.2. Combined Distortions: JPEG Quality Factor (QF) = 70 + Signal Processing Distortions
5.2.3. Geometric Distortions and Combined Attacks
5.3. Analysis and Discussion
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Cox, I.J.; Miller, M.L.; Bloom, J.A.; Fridrich, J.; Kalker, T. Digital Watermarking and Steganography, 2nd ed.; Morgan Kaufmann Publisher: San Francisco, CA, USA, 2008. [Google Scholar]
- Barni, M.; Bartolini, F. Watermarking Systems Engineering: Enabling Digital Assets Security and Other Applications; Marcel Dekker: New York, NY, USA, 2004. [Google Scholar]
- Jia, L.; Kumar, S. Robust Digital Watermarking Techniques for protecting copyright Applied to Digital Data: A Survey. Turk. J. Comp. Math. Educ. 2021, 12, 3819–3825. [Google Scholar]
- Tao, H.; Chongmin, L.; Mohamad Zain, J.; Abdalla, N. Robust Image Watermarking Theories and Techniques: A Review. J. Appl. Res. Technol. 2014, 12, 122–138. [Google Scholar] [CrossRef] [Green Version]
- Kennedy, J.; Eberhart, R. Particle swarm optimization. In Proceedings of the ICNN’95—International Conference on Neural Networks, Perth, WA, Australia, 27 November 1995; IEEE: Piscataway, NJ, USA, 1995; Volume 4, pp. 1942–1948. [Google Scholar]
- Cedillo-Hernandez, M.; Cedillo-Hernandez, A.; Garcia-Ugalde, F.; Nakano-Miyatake, M.; Perez-Meana, H. Digital color images ownership authentication via efficient and robust watermarking in a hybrid domain. Radioengineering 2017, 26, 536–551. [Google Scholar] [CrossRef]
- Dubendorf, V.A. Wireless Data Technologies; John Wiley & Sons, Ltd.: Hoboken, NJ, USA, 2003. [Google Scholar]
- Solachidis, V.; Pitas, I. Circularly symmetric watermark embedding in 2-D DFT domain. IEEE Trans. Image Process. 2001, 10, 1741–1753. [Google Scholar] [CrossRef] [Green Version]
- Hernandez, M.C.; Miyatake, M.N.; Meana, H.M.P. Analysis of a DFT-based watermarking algorithm. In Proceedings of the 2nd International Conference on Electrical and Electronics Engineering, Mexico City, Mexico, 9 September 2005; IEEE: Piscataway, NJ, USA, 2005; pp. 44–47. [Google Scholar]
- Cedillo-Hernández, M.; García-Ugalde, F.; Nakano-Miyatake, M.; Pérez-Meana, H.M. Robust hybrid color image watermarking method based on DFT domain and 2D histogram modification. Signal Image Video Process. 2014, 8, 49–63. [Google Scholar] [CrossRef]
- Cedillo-Hernández, M.; García-Ugalde, F.; Nakano-Miyatake, M.; Pérez-Meana, H.M. Robust watermarking method in DFT domain for effective management of medical imaging. Signal Image Video Process. 2014, 9, 1163–1178. [Google Scholar] [CrossRef]
- Sun, X.C.; Lu, Z.M.; Wang, Z.; Liu, Y.L. A geometrically robust multi-bit video watermarking algorithm based on 2-D DFT. Multimed. Tools Appl. 2021, 80, 13491–13511. [Google Scholar] [CrossRef]
- Ying, Q.; Lin, J.; Qian, Z.; Xu, H.; Zhang, X. Robust digital watermarking for color images in combined DFT and DT-CWT domains. Math. Biosci. Eng. 2019, 16, 4788–4801. [Google Scholar] [CrossRef] [PubMed]
- Wang, X.Y.; Hou, L.M.; Wu, J. A feature-based robust digital image watermarking against geometric attacks. Image Vision Comput. 2008, 26, 980–989. [Google Scholar] [CrossRef]
- Nuñez-Ramirez, D.; Cedillo-Hernandez, M.; Nakano-Miyatake, M.; Perez-Meana, H. Efficient Management of Ultrasound Images using Digital Watermarking. IEEE Lat. Am. Trans. 2020, 18, 1398–1406. [Google Scholar] [CrossRef]
- Cedillo-Hernandez, M.; Garcia-Ugalde, F.; Nakano-Miyatake, M.; Perez-Meana, H. Robust Object-Based Watermarking Using SURF Feature Matching and DFT Domain. Radioengineering 2013, 22, 1057–1071. [Google Scholar]
- Jung, Y.J.; Kang, H.K.; Ro, Y.M. Novel watermark embedding technique based on human visual system. In Proceedings of the Security and Watermarking of Multimedia Contents III: Proceedings of Spie, San Jose, CA, USA, 22–25 January 2001; Volume 4314, pp. 475–482. [Google Scholar]
- Zhang, L.; Wei, D. Robust and reliable image copyright protection scheme using down sampling and block transform in integer wavelet domain. Digit. Signal Process. 2020, 106, 102805. [Google Scholar] [CrossRef]
- Kang, X.; Chen, Y.; Zhao, F.; Lin, G. Multi-dimensional particle swarm optimization for robust blind image watermarking using intertwining logistic map and hybrid domain. Soft Comput. 2020, 24, 10561–10584. [Google Scholar] [CrossRef]
- Hsu, L.Y.; Hu, H.T. Blind watermarking for color images using EMMQ based on QDFT. Expert Syst. Appl. 2020, 149, 1–16. [Google Scholar] [CrossRef]
- Ahmadi, S.B.B.; Zhang, G.; Wei, S.; Boukela, L. An intelligent and blind image watermarking scheme based on hybrid SVD transforms using human visual system characteristics. Visual Comput. 2021, 37, 385–409. [Google Scholar]
- Zhang, L.; Wei, D. Dual DCT-DWT-SVD digital watermarking algorithm based on particle swarm optimization. Multimed. Tools Appl. 2019, 78, 28003–28023. [Google Scholar] [CrossRef]
- Riadi, S.; Triono, S.; Syahril, S.; Nofriansyah, D. A Novel Security based Image Watermarking using NBP-IWT-DCT-NSVD-GA-PSO Algorithm. Int. J. Eng. Adv. Technol. 2019, 9, 1600–1609. [Google Scholar]
- Thakkar, F.N.; Srivastava, V.K. Performance comparison of recent optimization algorithm Jaya with particle swarm optimization for digital image watermarking in complex wavelet domain. Multidimens. Syst. Signal Process. 2019, 30, 1769–1791. [Google Scholar] [CrossRef]
- Zhou, N.R.; Luo, A.W.; Zou, W.P. Secure and robust watermark scheme based on multiple transforms and particle swarm optimization algorithm. Multimed. Tools Appl. 2019, 78, 2507–2523. [Google Scholar] [CrossRef]
- Takore, T.T.; Kumar, P.R.; Devi, G.L. A New Robust and Imperceptible Image Watermarking Scheme Based on Hybrid Transform and PSO. Int. J. Intell. Syst. Appl. 2018, 11, 50–63. [Google Scholar] [CrossRef]
- Zheng, Z.; Saxena, N.; Mishra, K.; Sangaiah, A.K. Guided dynamic particle swarm optimization for optimizing digital image watermarking in industry applications. Future Gener. Comput. Syst. 2018, 88, 92–106. [Google Scholar] [CrossRef]
- Shih, F.Y.; Zhong, X.; Chang, I.C.; Satoh, S. An adjustable-purpose image watermarking technique by particle swarm optimization. Multimed. Tools Appl. 2018, 77, 1623–1642. [Google Scholar] [CrossRef]
- Sheikh, H.R.; Bovik, A.C. Image information and visual quality. IEEE Trans. Image Process. 2006, 15, 430–444. [Google Scholar] [CrossRef]
- Lin, T.Y.; Maire, M.; Belongie, S.; Hays, J.; Perona, P.; Ramanan, D.; Dollár, P.; Zitnick, C.L. Microsoft COCO: Common objects in context. In Proceedings of the European Conference on Computer Vision; Springer International Publishing: Cham, Switzerland, 2014; pp. 740–755. [Google Scholar]
- Chareyron, G.; Da Rugna, J.; Tremeau, A. Chapter 3: Color in Image Watermarking. In Advanced Techniques in Multimedia Watermarking: Image, Video and Audio Applications; Information Science Reference: Hershey, PA, USA, 2010; pp. 36–56. [Google Scholar]
- Trémeau, A.; Tominaga, S.; Plataniotis, K.N. Color in Image and Video Processing: Most Recent Trends and Future Research Directions. EURASIP J. Image Video Process. 2008, 3, 1–26. [Google Scholar] [CrossRef] [Green Version]
- Tang, C.W.; Hang, H.M. A feature-based robust digital image watermarking scheme. IEEE Trans. Signal Process. 2003, 51, 950–959. [Google Scholar] [CrossRef]
- Cayre, F.; Fontaine, C.; Furon, T. Watermarking security: Theory and practice. IEEE Trans. Signal Process. 2005, 53, 3976–3987. [Google Scholar] [CrossRef] [Green Version]



| Reference | Year | Description |
|---|---|---|
| [18] | 2020 | Robust watermarking to copyright protection based on integer wavelet transform (IWT) and guided dynamic particle swarm optimization (GDPSO). |
| [19] | 2020 | Robust blind image watermarking based on intertwining logistic map, hybrid domain using discrete cosine transform (DCT) domain, discrete wavelet transform (DWT) domain, and singular value decomposition (SVD), in conjunction with multidimensional PSO. |
| [20] | 2020 | Blind watermarking for color images based on extreme pixel adjustment (EPA), multi-bit partly sign-altered mean modulation (MP-SAM), mixed modulation (MM), quaternion discrete Fourier transform (QDFT), and PSO. |
| [21] | 2021 | Image watermarking scheme based on DWT and SVD using human visual system (HVS) and PSO. |
| [22] | 2019 | Digital watermarking algorithm with dual embedding in DCT-DWT-SVD domains, using PSO. |
| [23] | 2019 | Image watermarking using normalized block processing (NBP), normalized singular value decomposition (NSVD), IWT, DCT, a genetic algorithm (GA) and PSO. |
| [24] | 2019 | Digital image watermarking based on SVD in complex wavelet transform (CWT) domain, employing PSO and Jaya algorithm. |
| [25] | 2019 | Robust image watermarking performed in multiple transforms Lifting wavelet transform (LWT), DCT, discrete fractional angular transform (DFAT), SVD, and PSO. |
| [26] | 2018 | Robust image watermarking based on hybrid domain composed by LWT-DCT-SVD and using PSO. |
| [27] | 2018 | Digital image watermarking for industry applications in DWT-SVD domain and employing GDPSO algorithm. |
| [28] | 2018 | Image watermarking with criteria of region of interest (ROI) and region of non-interest (RONI), based on DWT-DCT-SVD domain and using PSO algorithm. |
| Distortion | Tolerance |
|---|---|
| Centered cropping | 100 × 100 for images with spatial resolution of 640 × 480 |
| Box filter | Kernel of 5 × 5 |
| Downsizing | Scaling factor of 0.6 |
| JPEG compression | Quality factor 30 |
| Gaussian noise | µ = 0, σ2 = 0.01 |
| Maximum Number of Iterations | Population Size N | Cognitive and Social Factors C1, C2 | Inertia Coefficient ω |
|---|---|---|---|
| 100 | 10 | 2.0 | 1.0–0.99 |
| Image | PSO-DFT | Conventional DFT | ||||||||
|---|---|---|---|---|---|---|---|---|---|---|
| r1 | r2 | α | PSNR (dB) | VIF | r1 | r2 | α | PSNR (dB) | VIF | |
 | 86 | 110 | 2.62 | 43.17 | 0.90 | 50 | 150 | 1.5 | 42.14 | 0.87 |
 | 61 | 143 | 0.65 | 44.96 | 0.94 | 42.33 | 0.81 | |||
 | 71 | 105 | 1.97 | 43.82 | 0.92 | 42.21 | 0.87 | |||
 | 56 | 153 | 0.67 | 44.70 | 0.93 | 42.26 | 0.83 | |||
 | 76 | 108 | 1.51 | 44.30 | 0.95 | 42.24 | 0.88 | |||
| ID: Signal Processing Distortion | |
|---|---|
| 1: Without distortion | 11: Box filter 5 × 5 |
| 2: JPEG lossy compression QF = 20 | 12: Histogram equalization |
| 3: JPEG lossy compression QF = 30 | 13: Gaussian filter 7 × 7 |
| 4: JPEG lossy compression QF = 50 | 14: Sharpening |
| 5: Gaussian noise µ = 0 and σ2 = 0.01 | 15: Brightness increase |
| 6: Gaussian noise µ = 0 and σ2 = 0.05 | 16: Brightness reduction |
| 7: Impulsive noise density = 0.09 | 17: Median filter 3 × 3 |
| 8: Speckle noise µ = 0 and σ2 = 0.2 | 18: Motion filter 5 × 5 |
| 9: Speckle noise µ = 0 and σ2 = 0.09 | 19: Gamma correction γ = 2 |
| 10: Box Filter 3 × 3 | 20: Gamma correction γ = 0.5 |
| Signal Processing Distortion | Average BCR PSO-DFT | Average BCR Conventional DFT |
|---|---|---|
| JPEG lossy compression QF = 20 | 0.79 | 0.73 |
| JPEG lossy compression QF = 30 | 0.90 | 0.81 |
| Gaussian noise µ = 0 and σ2 = 0.05 | 0.80 | 0.74 |
| Box Filter 3 × 3 | 0.98 | 0.92 |
| Box filter 5 × 5 | 0.92 | 0.76 |
| Median filter 3 × 3 | 0.96 | 0.90 |
| Motion filter 5 × 5 | 0.97 | 0.93 |
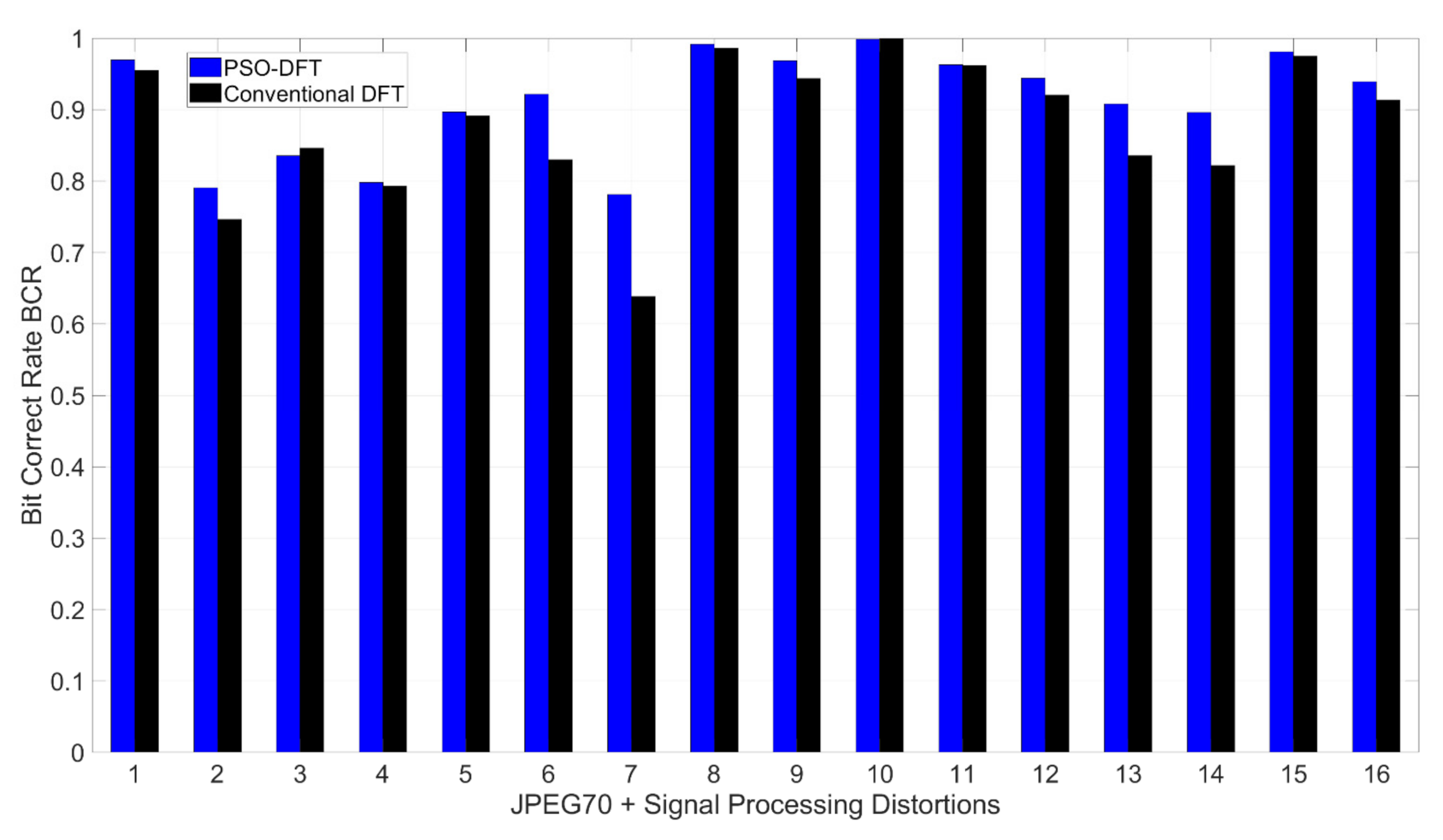
| ID: JPEG70 + Signal Processing Distortion | |
|---|---|
| 1: Gaussian noise µ = 0 and σ2 = 0.01 | 9: Gaussian filter 7 × 7 |
| 2: Gaussian noise µ = 0 and σ2 = 0.05 | 10: Sharpening |
| 3: Impulsive noise density = 0.09 | 11: Brightness increase |
| 4: Speckle noise µ = 0 and σ2 = 0.2 | 12: Brightness reduction |
| 5: Speckle noise µ = 0 and σ2 = 0.09 | 13: Median filter 3 × 3 |
| 6: Box Filter 3 × 3 | 14: Motion filter 5 × 5 |
| 7: Box filter 5 × 5 | 15: Gamma correction γ = 2 |
| 8: Histogram equalization | 16: Gamma correction γ = 0.5 |
| JPEG QF = 70+ | Average BCR PSO-DFT | Average BCR Conventional DFT |
|---|---|---|
| Gaussian noise µ = 0 and σ2 = 0.05 | 0.79 | 0.74 |
| Box Filter 3 × 3 | 0.92 | 0.82 |
| Box Filter 5 × 5 | 0.79 | 0.63 |
| Median filter 3 × 3 | 0.90 | 0.83 |
| Motion filter 5 × 5 | 0.89 | 0.82 |
| Distortion | Average BCR PSO-DFT | Average BCR Conventional DFT |
|---|---|---|
| Rotation by 45° with auto-crop | 0.98 | 0.96 |
| Rotation by 135° with auto-crop | 0.97 | 0.92 |
| Resizing, scaling factor = 0.6 | 0.96 | 0.77 |
| Resizing, scaling factor = 2 | 0.99 | 0.99 |
| Central cropping 120 × 120 | 0.98 | 0.97 |
| Translation x = 100, y = 100 | 0.96 | 0.96 |
| Affine [0.9,0.2,0;0.1,1.2,0;0,0,1] | 0.99 | 0.98 |
| Shearing (0, 20%) | 0.99 | 0.99 |
| Aspect Ratio (1.0, 1.2) | 0.99 | 0.97 |
| Aspect Ratio (0.8, 1.0) | 0.99 | 0.98 |
| JPEG70 + Rotation by 55° with auto-crop | 0.90 | 0.87 |
| JPEG70 + Rotation by 115° with auto-crop | 0.89 | 0.85 |
| JPEG70 + Resizing, scaling factor = 0.6 | 0.92 | 0.76 |
| JPEG70 + Resizing, scaling factor = 2 | 0.95 | 0.93 |
| JPEG70 + cropping 35% with re-scaling | 0.81 | 0.76 |
| JPEG70 + Translation x = 100, y = 100 | 0.87 | 0.85 |
| JPEG70 + Affine [0.9,0.2,0;0.1,1.2,0;0,0,1] | 0.97 | 0.96 |
| JPEG70 + Shearing (20%, 0) | 0.96 | 0.96 |
| JPEG70 + Aspect Ratio (1.0, 1.2) | 0.97 | 0.95 |
| JPEG70 + Aspect Ratio (0.8, 1.0) | 0.98 | 0.98 |
| Method | JPEG Compression | Watermark Payload | Imperceptibility Metric Used in PSO Fitness Function | Detection Metric Used in PSO Fitness Function | Maximum Number of Iterations in PSO | Number of Images in Trials/Bit Depth | Geometric Attacks | Types of Noises |
|---|---|---|---|---|---|---|---|---|
| [19] | 10–100 | 1024 bits | PSNR | BER | 30 | 8 images in grayscale with 8 bit/pixel in depth | Resizing. Cropping | Gaussian, Salt and pepper, Speckle |
| [20] | 20–100 | 4096 bits | PSNR-Mean SSIM | BER | 30 | 64 images in color with 24 bit/pixel in depth | Cropping | Gaussian, Salt and pepper, Speckle |
| [21] | 30–100 | 1024 bits | PSNR | Normalized (NC) and Cross (CC) Correlations | 10 | 10 images in grayscale with 8 bit/pixel in depth | Cropping | Gaussian, Salt and pepper |
| [22] | 10–100 | 16,384 bits | PSNR | NC | 100 | 8 images in grayscale with 8 bit/pixel in depth | Rotation, Resizing, Cropping | Gaussian, Salt and pepper |
| [24] | 10–100 | 16384 bits | - | 2D Correlation Coefficient | 10 | 1 image in grayscale with 8 bit/pixel in depth | Rotation, Scaling | Gaussian |
| [25] | 75–100 | 1024 bits | PSNR | NC | - | 2 images in grayscale with 8 bit/pixel in depth | Cropping | Gaussian, Salt and pepper, Speckle |
| [26] | 70–100 | 1024 bits | PSNR | NC | 100 | 4 images in grayscale with 8 bit/pixel in depth | Rotation, Cropping | Gaussian, Salt and pepper, Speckle |
| Proposed Method | 20–100 | 32 bits | VIF | BCR | 100 | 1000 images in color with 24 bit/pixel in depth | Rotation, Resizing, Cropping, Affine transformation Translation, Shearing, Aspect ratio changes | Gaussian, Salt and pepper, Speckle |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Cedillo-Hernandez, M.; Cedillo-Hernandez, A.; Garcia-Ugalde, F.J. Improving DFT-Based Image Watermarking Using Particle Swarm Optimization Algorithm. Mathematics 2021, 9, 1795. https://doi.org/10.3390/math9151795
Cedillo-Hernandez M, Cedillo-Hernandez A, Garcia-Ugalde FJ. Improving DFT-Based Image Watermarking Using Particle Swarm Optimization Algorithm. Mathematics. 2021; 9(15):1795. https://doi.org/10.3390/math9151795
Chicago/Turabian StyleCedillo-Hernandez, Manuel, Antonio Cedillo-Hernandez, and Francisco J. Garcia-Ugalde. 2021. "Improving DFT-Based Image Watermarking Using Particle Swarm Optimization Algorithm" Mathematics 9, no. 15: 1795. https://doi.org/10.3390/math9151795
APA StyleCedillo-Hernandez, M., Cedillo-Hernandez, A., & Garcia-Ugalde, F. J. (2021). Improving DFT-Based Image Watermarking Using Particle Swarm Optimization Algorithm. Mathematics, 9(15), 1795. https://doi.org/10.3390/math9151795






