A New ECDLP-Based PoW Model †
Abstract
1. Introduction
2. ECDLP
2.1. The General Case
2.2. Special Cases
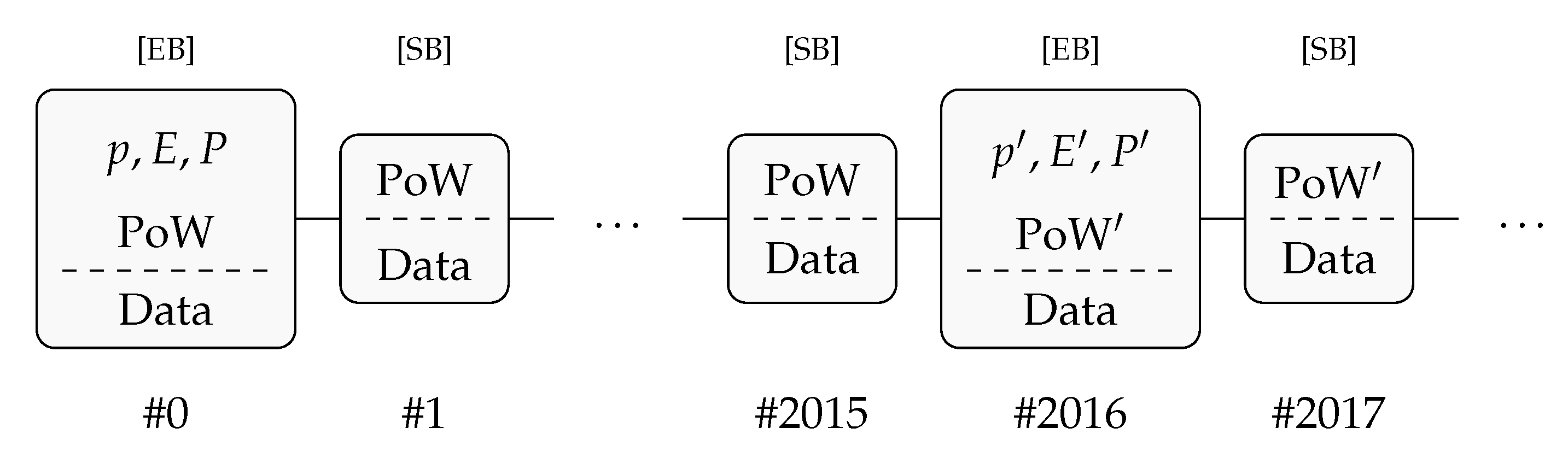
3. A Sample Blockchain Architecture
- [EB]
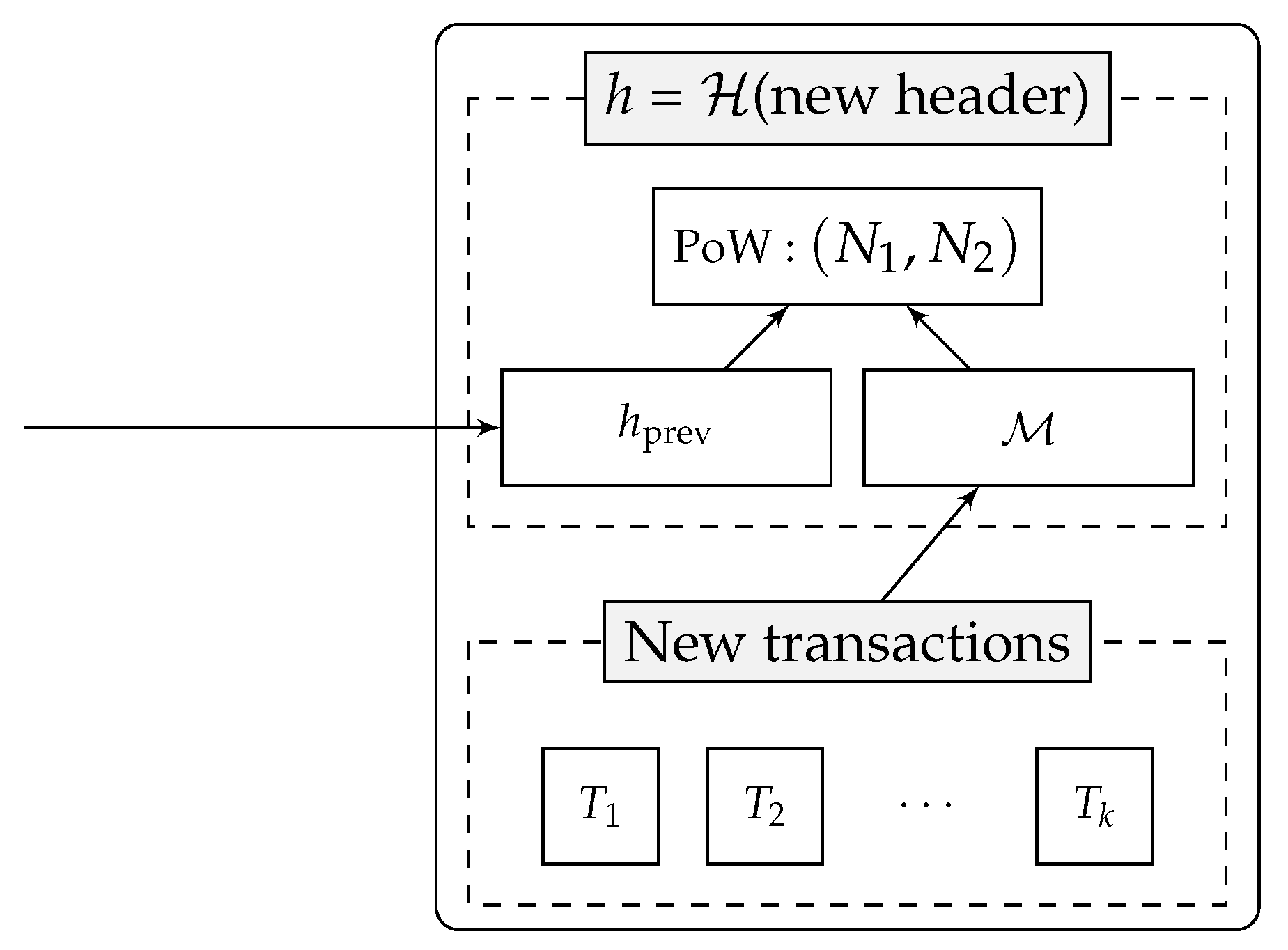
- An Epoch Block contains, aside from the header and a list of transactions, a prime number p, an elliptic curve E defined over , and a base point P of E, all to be determined by the proposing miner via rigid algorithms with a pseudorandom set of input parameters.Moreover, it encloses as PoW a pair of integers to be discovered by the proposing miner, such that are points of E deterministically determined from the block contents and the current chain status.The frequency of the EBs determines the number of changes in the ECDLP-parameters with respect to the network block construction speed. In the current proposal, we arbitrarily set these EBs to occur once every 2016 blocks, emulating the bitcoin difficulty adjustment rate.
- [SB]
- The Standard Blocks are just a light version of the EB blocks; they are constructed in the same way except for p, E, P, which are inherited from the last EB block of the chain.SBs constitute the vast majority of the blocks of the chain, as portrayed in Figure 1.
- function P_Gen (h,E)
- i = 0
- while #{points of E with x-coord = h + i} = 0:
- i = i + 1
- P = (h + i, *) point of E with 0 ≤ * < p/2
- return P
3.1. Standard Blocks
3.2. Epoch Blocks
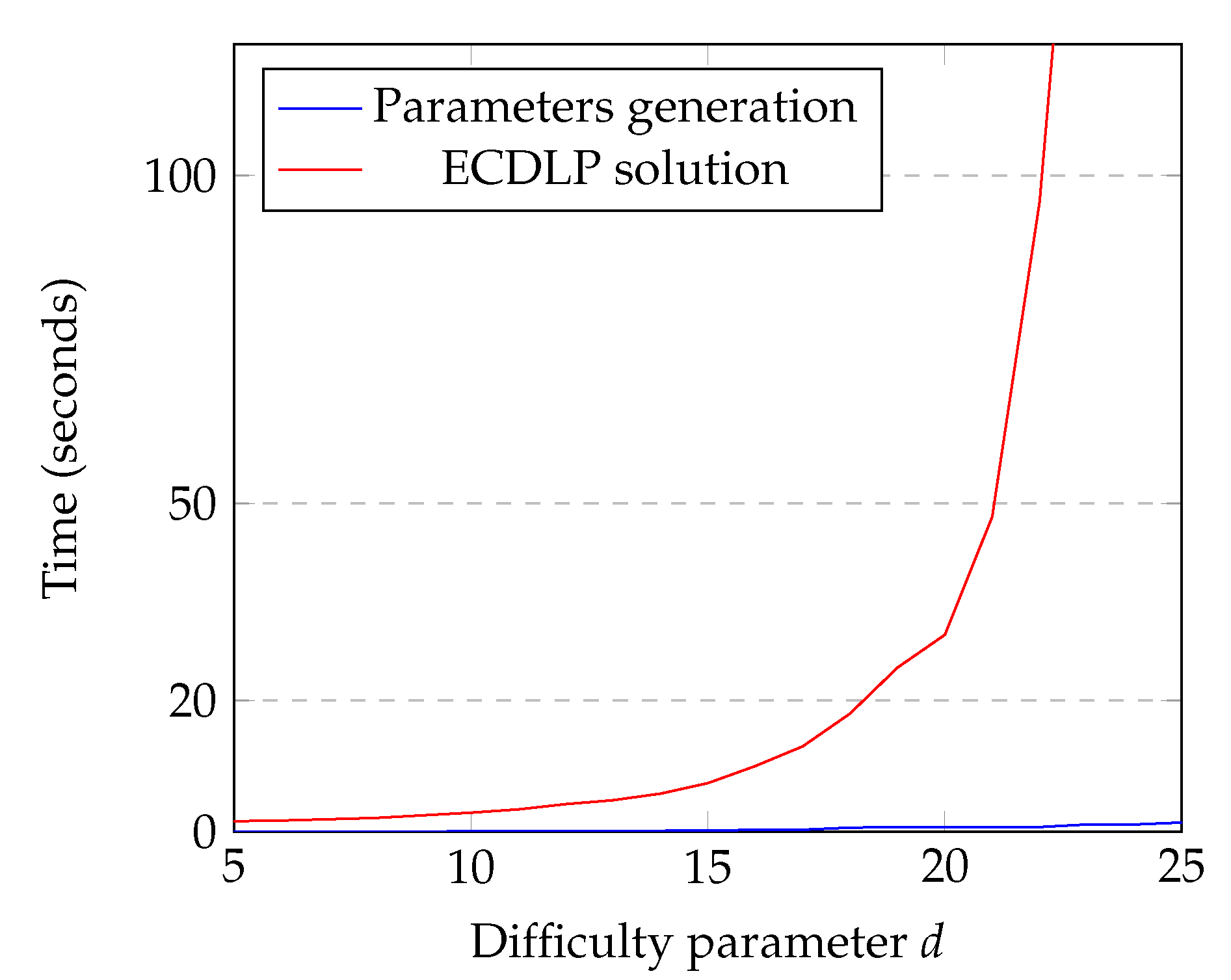
- Generating pThe prime number p is the responsibility of the expected runtime of the PoW. Its size is determined by the difficulty parameter d, whose tuning depends on the block production ratio that a designer wants to obtain. Therefore, we do not discuss the choice of d, but we refer to the BTC implementation [41] or to more structured models such as personalized difficulty adjustments [42]. Our goal is to produce a prime number of the prescribed size and which does not allow fast arithmetic for the known cases, i.e. we pick it satisfying the following properties.Exceptionality properties
- p is not a Crandall prime [43], i.e., not of the from for a relatively small and positive integer c.
Given the difficulty parameter d and the hash of the previous header h, we propose the generation of such a prime number p as follows.- function p_Gen(d, h)
- repeat
- h = (h)
- p = Next, Prime (h mod 22d)
- until p satisfies exceptionality properties
- return p
- Generating EWe aim at generating pseudorandom elliptic curves for which no efficient attacks are currently known, i.e., satisfying the following properties:Security properties
- The number of points of E is prime and different from p.
- The embedding degree B is greater than 20, i.e., for every .
- Let D be the CM field discriminant, defined aswhere t is the trace of E. Then, we require .
Let h be the previous block header; we suggest generating the curve as follows:- function E_Gen (p, h)
- i = 0
- repeat
- i = i + 1
- AE = (h + i)
- BE = (AE)
- E defined by y2 = x3 + AE x + BE over 𝔽p
- until E is an EC satisfying security properties
- return E
- Generating PThe base point we prescribe for an EB and its subsequent epoch iswhere denotes the concatenation of the bit representations of x and y.
4. Method Discussion
- working over prime fields avoids Weil-descent attacks;
- searching for curves of prime order prevents from Pohlig–Hellman attacks;
- since the curves are not anomalous so Smart, Semaev, Satoh–Araki attacks do not apply;
- the embedding degree we suggest is greater than 20 as required by SEC1 [50], which prevents pairing attacks such as Menezes–Okamoto–Vanstone (based on Weil Pairing) and Frey–Rück (based on Tate–Lichtenbaum Pairing);
- attacks to curves with low CM discriminant are prevented by requiring it higher than , as for Brainpool Standard Curves [51].
5. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Meneghetti, A.; Sala, M.; Taufer, D. A Survey on PoW-Based Consensus. AETiC 2020, 4, 1. Available online: http://aetic.theiaer.org/archive/v4/v4n1/p2.html (accessed on 3 January 2020). [CrossRef]
- Jakobsson, M.; Juels, A. Proofs of Work and Bread Pudding Protocols (Extended Abstract). Secure Information Networks. 1999. [CrossRef]
- Ar, S.; Cai, J. Reliable Benchmarks Using Numerical Instability. SODA ’94: Proceedings of the Fifth Annual ACM-SIAM Symposium on Discrete Algorithms. 1994, pp. 34–43. Available online: https://dl.acm.org/citation.cfm?id=314476 (accessed on 3 January 2020).
- Cai, J.; Lipton, R.J.; Sedgewick, R.; Yao, A.C. Towards Uncheatable Benchmarks. In Proceedings of the Eigth Annual Structure in Complexity Theory Conference, San Diego, CA, USA, 18–21 May 1993. [Google Scholar] [CrossRef]
- Dwork, C.; Naor, M. Pricing via Processing or Combatting Junk Mail. In Annual International Cryptology Conference; Springer: Berlin/Heidelberg, Germany, 1992; Volume 740. [Google Scholar] [CrossRef]
- Franklin, M.K.; Malkhi, D. Auditable Metering with Lightweight Security. In International Conference on Financial Cryptography; Springer: Berlin/Heidelberg, Germany, 1997; Volume 1318. [Google Scholar] [CrossRef]
- Goldschlag, D.M.; Stubblebine, S.G. Publicly Verifiable Lotteries: Applications of Delaying Functions. In International Conference on Financial Cryptography; Springer: Berlin/Heidelberg, Germany, 1994; Available online: http://dl.acm.org/citation.cfm?id=647502.728319 (accessed on 5 January 2020).
- Juels, A.; Brainard, J. Client Puzzles: A Cryptographic Countermeasure against Connection Depletion Attacks. NDSS Symposium 1999. Available online: https://www.ndss-symposium.org/ndss1999/cryptographic-defense-against-connection-depletion-attacks (accessed on 5 January 2020).
- Rivest, R.L.; Shamir, A.; Wagner, D.A. Time-Lock Puzzles and Timed-Release Crypto; Massachusetts Institute of Technology: Cambridge, MA, USA, 1996; Available online: https://dl.acm.org/citation.cfm?id=888615 (accessed on 5 January 2020).
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. 2008. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 5 January 2020).
- Back, A. Hashcash. 1997. Available online: http://www.cypherspace.org/hashcash (accessed on 5 January 2020).
- Back, A. Hashcash—A Denial of Service Counter-Measure. 2002. Available online: http://www.hashcash.org/papers/hashcash.pdf (accessed on 5 January 2020).
- CureCoin Team. 2019 Curecoin Model (White Paper Draft). 2019. Available online: https://curecoin.net/white-paper (accessed on 5 January 2020).
- Finney, H. RPOW—Reusable Proofs of Work. 2004. Available online: https://nakamotoinstitute.org/finney/rpow/index.html (accessed on 5 January 2020).
- Miller, A.; Juels, A.; Shi, E.; Katz, J. Permacoin: Repurposing Bitcoin Work for Data Preservation. In Proceedings of the 2014 IEEE Symposium on Security and Privacy, San Jose, CA, USA, 18–21 May 2014; Available online: https://www.microsoft.com/en-us/research/publication/permacoin-repurposing-bitcoin-work-for-data-preservation (accessed on 5 January 2020).
- Shoker, A. Sustainable Blockchain through Proof of Exercise. In Proceedings of the 2017 IEEE 16th International Symposium on Network Computing and Applications (NCA), Cambridge, MA, USA, 30 October–1 November 2017; Available online: https://ieeexplore.ieee.org/stamp/stamp.jsp?tp=&arnumber=8171383 (accessed on 5 January 2020).
- Rivest, R.L.; Shamir, A. PayWord and MicroMint: Two Simple Micropayment Schemes. In International Workshop on Security Protocols; Springer: Berlin/Heidelberg, Germany, 1997; Volume 1189. [Google Scholar] [CrossRef]
- Sunny, K. Primecoin: Cryptocurrency with Prime Number Proof-of-Work. 2013. Available online: http://primecoin.io/bin/primecoin-paper.pdf (accessed on 5 January 2020).
- Ball, M.; Rosen, A.; Sabin, M.; Vasudevan, P.N. Proofs of Useful Work. Cryptology ePrint Archive (IACR). 2017. Available online: https://eprint.iacr.org/2017/203.pdf (accessed on 4 January 2020).
- Meneghetti, A.; Sala, M.; Taufer, D. A Note on an ECDLP-Based PoW Model. In Proceedings of the 3rd Distributed Ledger Technology Workshop (DLT 2020), Ancona, Italy, 4 February 2020; Available online: http://ceur-ws.org/Vol-2580/ (accessed on 6 February 2020).
- Hastings, M.; Heninger, N.; Wustrow, E. The Proof Is in the Pudding: Proofs of Work for Solving Discrete Logarithms. Cryptology ePrint Archive (IACR). 2018. Available online: https://eprint.iacr.org/2018/939.pdf (accessed on 5 January 2020).
- Lochter, M. Blockchain as Cryptanalytic Tool. Cryptology ePrint Archive (IACR). 2018. Available online: https://eprint.iacr.org/2018/893.pdf (accessed on 7 January 2020).
- Bernstein, D.J.; Lange, T.L. Safecurves: Choosing Safe Curves for Elliptic-Curve Cryptography. Available online: https://safecurves.cr.yp.to/ (accessed on 7 January 2020).
- Shanks, D. Class Number, a Theory of Factorization and Genera. In Proceedings of Symposia in Pure Mathematics; American Mathematical Society: Providence, RI, USA, 1969; Volume 20, pp. 415–440. Available online: http://www.ams.org/books/pspum/020/ (accessed on 7 January 2020).
- Pollard, J.M. Monte Carlo Methods for Index Computation (mod p). Math. Comput. 1978, 32, 918–924. [Google Scholar] [CrossRef]
- Semaev, I.A. Summation Polynomials and the Discrete Logarithm Problem on Elliptic Curves. Cryptology ePrint Archive (IACR). 2004. Available online: https://eprint.iacr.org/2004/031.pdf (accessed on 7 January 2020).
- Frey, G.; Rück, H. A Remark Concerning M-Divisibility and the Discrete Logarithm in the Divisor Class Group of Curves. Math. Comput. 1994, 62, 865–874. Available online: https://www.jstor.org/stable/2153546?seq=1 (accessed on 7 January 2020).
- Menezes, A.J.; Okamoto, T.; Vanstone, S.A. Reducing Elliptic Curve Logarithms to Logarithms in a Finite Field. IEEE Trans. Inf. Theory 1993, 39, 5. Available online: https://ieeexplore.ieee.org/stamp/stamp.jsp?arnumber=259647 (accessed on 7 January 2020). [CrossRef]
- Amadori, A.; Pintore, F.; Sala, M. On the Discrete Logarithm Problem for Prime-Field Elliptic Curves. Finite Fields Their Appl. 2018, 51, 168–182. [Google Scholar] [CrossRef]
- McGuire, G.; Mueller, D. A New Index Calculus Algorithm for the Elliptic Curve Discrete Logarithm Problem and Summation Polynomial Evaluation. Cryptology ePrint Archive (IACR). 2017. Available online: https://eprint.iacr.org/2017/1262.pdf (accessed on 7 January 2020).
- Silverman, J.H.; Suzuki, J. Elliptic Curve Discrete Logarithms and the Index Calculus. In International Conference on the Theory and Application of Cryptology and Information Security; Springer: Berlin/Heidelberg, Germany, 1998; pp. 110–125. [Google Scholar] [CrossRef]
- Silverman, J.H. The Xedni Calculus and the Elliptic Curve Discrete Logarithm Problem. Des. Codes Cryptogr. 2000, 20, 5–40. [Google Scholar] [CrossRef]
- Frey, G.; Gangl, H. How to Disguise an Elliptic Curve (Weil Descent). In Talk at ECC ’98; University of Waterloo: Waterloo, ON, Canada, 1998; Available online: http://www.cacr.math.uwaterloo.ca/conferences/1998/ecc98/frey.ps (accessed on 7 January 2020).
- Gaudry, P.; Hess, F.; Smart, N.P. Constructive and Destructive Facets of Weil Descent on Elliptic Curves. J. Cryptol. 2002, 15, 19–46. [Google Scholar] [CrossRef]
- Pohlig, S.; Hellman, M. An Improved Algorithm for Computing Logarithms over GF(p) and Its Cryptographic Significance. IEEE Trans. Inf. Theory 1978, 24, 1. Available online: https://ee.stanford.edu/~hellman/publications/28.pdf (accessed on 7 January 2020). [CrossRef]
- Satoh, T.; Araki, K. Fermat Quotients and the Polynomial Time Discrete Log Algorithm for Anomalous Elliptic Curves. Comm. Math. Univ. Sancti Pauli 1998, 47, 81–92. [Google Scholar]
- Semaev, I.A. Evaluation of Discrete Logarithms in a Group of p-Torsion Points of an Elliptic Curve in Characteristic p. Math. Comput. 1998, 67, 353–356. [Google Scholar] [CrossRef]
- Smart, N. The Discrete Logarithm on Elliptic Curves of Trace One. J. Math. Cryptol. 1999, 12, 193–196. [Google Scholar] [CrossRef]
- Wiener, M.J.; Zuccherato, R.J. Faster Attacks on Elliptic Curve Cryptosystems. In International Workshop on Selected Areas in Cryptography; Springer: Berlin/Heidelberg, Germany, 1998; Available online: https://link.springer.com/chapter/10.1007/3-540-48892-8_15 (accessed on 7 January 2020).
- Bertoni, G.; Daemen, J.; Peeters, M.; van Assche, G.; van Keer, R. Keccak Implementation Overview. 2012. Available online: https://keccak.team/files/Keccak-implementation-3.2.pdf (accessed on 7 January 2020).
- Bitcoin Team. PoW Implementation. The Bitcoin Core Developers. 2018. Available online: https://github.com/bitcoin/bitcoin/blob/master/src/pow.cpp (accessed on 8 January 2020).
- Chou, C.; Lin, Y.; Chen, R.; Chang, H.; Tu, I.; Liao, S. Personalized Difficulty Adjustment for Countering the Double-Spending Attack in Proof-of-Work Consensus Protocols. arXiv 2018, arXiv:1807.02933. Available online: https://arxiv.org/abs/1807.02933 (accessed on 8 January 2020).
- Crandall, R.E. Method and Apparatus for Public Key Exchange in a Cryptographic System. U.S. Patent 5159632A, 27 October 1992. Available online: https://patents.google.com/patent/US5159632A/en (accessed on 8 January 2020).
- Solinas, J.A. Generalized Mersenne Numbers. 1999. Available online: http://www.cacr.math.uwaterloo.ca/techreports/1999/corr99-39.pdf (accessed on 8 January 2020).
- Chung, J.; Hasan, A. More Generalized Mersenne Numbers. 2003. Available online: http://cacr.uwaterloo.ca/techreports/2003/corr2003-17.ps (accessed on 8 January 2020).
- Acar, T.; Shumow, D. Modular Reduction without Pre-Computation for Special Moduli; Microsoft Research: Redmond, WA, USA, 2016; Available online: https://www.microsoft.com/en-us/research/wp-content/uploads/2016/02/modmul_no_precomp.pdf (accessed on 8 January 2020).
- Bos, J.W.; Costello, C.; Hisil, H.; Lauter, K. Fast Cryptography in Genus 2. Cryptology ePrint Archive (IACR). 2012. Available online: https://eprint.iacr.org/2012/670.pdf (accessed on 8 January 2020).
- Hamburg, M. Fast and Compact Elliptic-Curve Cryptography. Cryptology ePrint Archive (IACR). 2012. Available online: https://eprint.iacr.org/2012/309.pdf (accessed on 8 January 2020).
- Meneghetti, A.; Sala, M.; Taufer, D. A survey on Efficient Parallelization of Blockchain-Based Smart Contracts. AETiC 2019, 3, 5. Available online: http://aetic.theiaer.org/archive/v3/v3n5/p2.html (accessed on 8 January 2020). [CrossRef]
- Certicom Research. SEC 1: Elliptic Curve Cryptography; Certicom Research, Information-Technology Promotion Agency: Toronto, ON, Canada, 2000; Available online: https://www.ipa.go.jp/security/enc/CRYPTREC/fy15/doc/1_01sec1.pdf (accessed on 8 January 2020).
- Lochter, M.; Merkle, J. Elliptic Curve Cryptography (ECC) Brainpool Standard Curves and Curve Generation. 2010. Available online: https://tools.ietf.org/html/rfc5639 (accessed on 8 January 2020).
- Bellare, M.; Rogaway, P. Random Oracles Are Practical: A Paradigm for Designing Efficient Protocols. CCS ’93: Proceedings of the 1st ACM Conference on COMPUTER and Communications Security. 1993, pp. 62–73. Available online: http://cseweb.ucsd.edu/~mihir/papers/ro.html (accessed on 8 January 2020).
- Galbraith, S.D.; Mckee, J. The Probability That the Number of Points on an Elliptic Curve over a Finite Field Is Prime. J. Lond. Math. Soc. 2000, 62, 671–684. [Google Scholar] [CrossRef]
- Bosma, W.; Cannon, J.; Playoust, C. The Magma algebra system. I. The user language. J. Symb. Comput. 1997, 24, 235–265. Available online: http://magma.maths.usyd.edu.au/magma (accessed on 8 January 2020). [CrossRef]

| Attack | It Applies on Curves | To Avoid It: Use | Ref. |
|---|---|---|---|
| Weil-descent | over composite fields | prime fields | [33,34] |
| Pohlig–Hellman | of composite orders | prime orders | [35] |
| Semaev, Satoh–Araki, Smart | anomalous | non-anomalous curves | [36,37,38] |
| Menezes–Okamoto–Vanstone | low embedding degree | high embedding degree | [28] |
| Frey–Rück | low embedding degree | high embedding degree | [27] |
| Wiener–Zuccherato | low CM discriminant | high CM discriminant | [39] |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Meneghetti, A.; Sala, M.; Taufer, D. A New ECDLP-Based PoW Model. Mathematics 2020, 8, 1344. https://doi.org/10.3390/math8081344
Meneghetti A, Sala M, Taufer D. A New ECDLP-Based PoW Model. Mathematics. 2020; 8(8):1344. https://doi.org/10.3390/math8081344
Chicago/Turabian StyleMeneghetti, Alessio, Massimiliano Sala, and Daniele Taufer. 2020. "A New ECDLP-Based PoW Model" Mathematics 8, no. 8: 1344. https://doi.org/10.3390/math8081344
APA StyleMeneghetti, A., Sala, M., & Taufer, D. (2020). A New ECDLP-Based PoW Model. Mathematics, 8(8), 1344. https://doi.org/10.3390/math8081344







