ASIC-Resistant Proof of Work Based on Power Analysis of Low-End Microcontrollers
Abstract
:1. Introduction
Research Contributions
- We introduce a novel ASIC-resistant proof of work based on a power analysis: Previous ASIC-resistant PoW methods are based on multi-hash, memory hard, and programmatic approaches. The proposed method presents the first ASIC-resistant PoW based on a power analysis. The power trace during cryptography encryption (e.g., AES) on the microcontroller is utilized for the source of PoW. Since the power trace depends on the target microcontroller, cryptography encryption, and input values, the proposed PoW cannot be emulated by ASIC and FPGA. For this reason, we achieved the ASIC-resistant feature.
- Post-processing for noise elimination: The raw power trace contains noise information. Small noise can significantly alter the result of cryptography operations. In order to filter out the noise from the raw power trace, a Fast Fourier Transform (FFT) is performed. This method efficiently removes the high frequency. After the post-processing, the refined information is used as a source for PoW.
- In-depth analysis of novel PoW based on various block ciphers: The performance was evaluated on a microcontroller. We performed the experiment with various block ciphers. The result shows that the novel PoW works on all block ciphers without difficulty.
2. Related Works
2.1. Proof-of-Work
2.2. ASIC-Resistant PoW
2.2.1. Multi-Hash PoW
2.2.2. Memory-Hard PoW
2.2.3. Memory-Bound PoW
2.2.4. Programmatic PoW
2.3. Power Analysis and Its New Applications
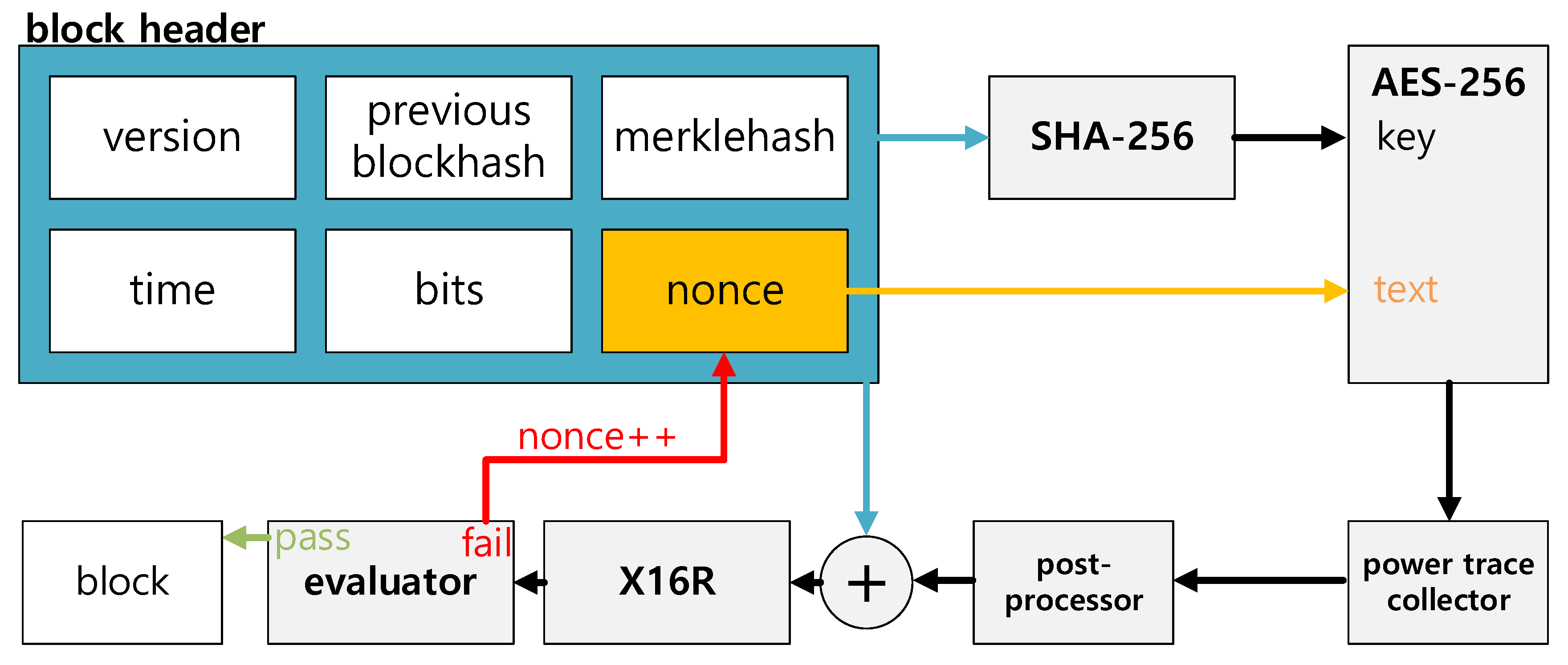
3. Proposed Method
| Algorithm 1 Proposed PoW algorithm |
| Input:, Power Trace. Output:. 1: whiledo 2: 3: 4: 5: 6: 7: 8: 9: end while 10: return |
3.1. Power Trace Based Proof-of-Work
3.1.1. Collection of Power Trace from Microcontrollers
3.1.2. Features of Power Consumption Trace
3.1.3. Post-Processing for Noise Filtering
3.1.4. High Entropy for Input Value
3.1.5. Finding the Target with Hash Function
3.1.6. AI-Resistant Hash Function
3.1.7. Verification with Power Trace
| Algorithm 2 Power Consumption Trace Verification algorithm |
| Input:, , . Output: Verification result. 1: 2: 3: 4: if then 5: return 6: else 7: return 8: end if |
3.2. Advantages of the Proposed Method
3.2.1. PoW Requirements
3.2.2. ASIC Resistance
3.2.3. Operation Time
3.2.4. Flexibility of Encryption Module on Microcontrollers
4. Evaluation
4.1. Experiment Environment
4.2. Uniqueness of Power Consumption
4.3. Lightweight PoW for Low-End Microcontrollers
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 8 August 2020).
- Wood, G. Ethereum: A secure decentralised generalised transaction ledger. Ethereum Proj. Yellow Pap. 2014, 151, 1–32. [Google Scholar]
- Noether, S.; Mackenzie, A. Ring Confidential Transactions. Available online: http://ledger.pitt.edu/ojs/ledger/article/view/34 (accessed on 8 August 2020).
- Dwork, C.; Naor, M. Pricing Via Processing or Combatting Junk Mail. In Annual International Cryptology Conference; Springer: Berlin/Heidelberg, Germany, 1992; pp. 139–147. [Google Scholar]
- Cai, J.Y.; Lipton, R.J.; Sedgewick, R.; Yao, A.C. Towards uncheatable benchmarks. In Proceedings of the Eigth Annual Structure in Complexity Theory Conference, San Diego, CA, USA, 18–21 May 1993; pp. 2–11. [Google Scholar]
- Ar, S.; Cai, J.Y. Reliable Benchmarks Using Numerical Instability. 1994, pp. 34–43. Available online: https://books.google.com.hk/books?hl=zh-TW&lr=&id=SYEy8nTSkMYC&oi=fnd&pg=PA34&dq=Reliable+Benchmarks+Using+Numerical+Instability&ots=5Ujh83NE-k&sig=DRCARrjKZm7LW9KkLtV3PCDRQmY&redir_esc=y&hl=zh-CN&sourceid=cndr#v=onepage&q=ReliableBenchmarksUsingNumericaInstability&f=false (accessed on 8 August 2020).
- Franklin, M.K.; Malkhi, D. Auditable Metering with Lightweight Security. In International Conference on Financial Cryptography; Springer: Berlin/Heidelberg, Germany, 1997; pp. 151–160. [Google Scholar]
- Goldschlag, D.M.; Stubblebine, S.G. Publicly Verifiable Lotteries: Applications of Delaying Functions. In International Conference on Financial Cryptography; Springer: Berlin/Heidelberg, Germany, 1998; pp. 214–226. [Google Scholar]
- Rivest, R.L.; Shamir, A.; Wagner, D.A. Time-Lock Puzzles and Timed-Release Crypto; Massachusetts Institute of Technology, Laboratory for Computer Science: Cambridge, MA, USA, 1996; Available online: http://bitsavers.trailing-edge.com/pdf/mit/lcs/tr/MIT-LCS-TR-684.pdf (accessed on 8 August 2020).
- Back, A. Hashcash-A Denial of Service Counter-Measure. Technical Report. 2002. Available online: ftp://sunsite.icm.edu.pl/site/replay.old/programs/hashcash/hashcash.pdf (accessed on 8 August 2020).
- Bertoni, G.; Daemen, J.; Peeters, M.; Van Assche, G. Keccak. In Annual International Conference on the Theory and Applications of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 2013; pp. 313–314. [Google Scholar]
- Dryja, T. Hashimoto: I/O Bound Proof of Work. Technical Report. 2009. Available online: https://mirrorx.com/files/hashimoto.pdf (accessed on 8 August 2020).
- Buterin, V. Dagger: A Memory-Hard to Compute, Memory-Easy to Verify Scrypt Alternative. Technical Report. 2013. Available online: http://www.hashcash.org/papers/dagger.html (accessed on 8 August 2020).
- Percival, C. Stronger Key Derivation via Sequential Memory-Hard Functions. Technical Report. 2009. Available online: https://pdfs.semanticscholar.org/7c74/956d21f0466c9771bb583e2fdf854c2aedbf.pdf (accessed on 8 August 2020).
- Van Saberhagen, N. CryptoNote v 2.0. Technical Report. 2013. Available online: https://decred.org/research/saberhagen2013.pdf (accessed on 8 August 2020).
- Gencer, A.E.; Basu, S.; Eyal, I.; Van Renesse, R.; Sirer, E.G. Decentralization in Bitcoin and Ethereum Networks. In International Conference on Financial Cryptography and Data Security; Springer: Berlin/Heidelberg, Germany, 2018; pp. 439–457. [Google Scholar]
- Ruoti, S.; Kaiser, B.; Yerukhimovich, A.; Clark, J.; Cunningham, R. SoK: Blockchain technology and its potential use cases. arXiv 2019, arXiv:1909.12454. [Google Scholar]
- De Vries, A. Bitcoin’s growing energy problem. Joule 2018, 2, 801–805. [Google Scholar] [CrossRef] [Green Version]
- Primecoin, K.S. Cryptocurrency with Prime Number Proof-of-Work. Technical Report. 2013. Available online: https://primecoin.io/bin/primecoin-paper.pdf (accessed on 8 August 2020).
- Rivest, R.L.; Shamir, A. PayWord and MicroMint: Two Simple Micropayment Schemes. In International Workshop on Security Protocols; Springer: Berlin/Heidelberg, Germany, 1996; pp. 69–87. [Google Scholar]
- Miller, A.; Juels, A.; Shi, E.; Parno, B.; Katz, J. Permacoin: Repurposing bitcoin work for data preservation. In Proceedings of the 2014 IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 18–21 May 2014; pp. 475–490. [Google Scholar]
- Sompolinsky, Y.; Zohar, A. Secure High-rate Transaction Processing in Bitcoin. In International Conference on Financial Cryptography and Data Security; Springer: Berlin/Heidelberg, Germany, 2015; pp. 507–527. [Google Scholar]
- Jang, J.; Lee, H.N. Profitable double-spending attacks. arXiv 2019, arXiv:1903.01711. [Google Scholar]
- Eyal, I.; Sirer, E.G. Majority is not Enough: Bitcoin Mining is Vulnerable. In International Conference on Financial Cryptography and Data Security; Springer: Berlin/Heidelberg, Germany, 2014; pp. 436–454. [Google Scholar]
- Heilman, E.; Kendler, A.; Zohar, A.; Goldberg, S. Eclipse attacks on bitcoin’s peer-to-peer network. In Proceedings of the 24th USENIX Security Symposium ( USENIX Security 15), Washington, DC, USA, 12–14 August 2015; pp. 129–144. [Google Scholar]
- Daian, P.; Eyal, I.; Juels, A.; Sirer, E.G. (Short paper) Piecework: Generalized Outsourcing Control for Proofs of Work. In International Conference on Financial Cryptography and Data Security; Springer: Berlin/Heidelberg, Germany, 2017; pp. 182–190. [Google Scholar]
- Kroll, J.A.; Davey, I.C.; Felten, E.W. The economics of Bitcoin mining, or Bitcoin in the presence of adversaries. In Proceedings of the WEIS, Washington, DC, USA, 11–12 June 2013; Volume 2013, p. 11. [Google Scholar]
- Abadi, M.; Burrows, M.; Manasse, M.; Wobber, T. Moderately hard, memory-bound functions. Acm Trans. Internet Technol. (Toit) 2005, 5, 299–327. [Google Scholar] [CrossRef]
- Dwork, C.; Goldberg, A.; Naor, M. On Memory-bound Functions for Fighting Spam. In Annual International Cryptology Conference; Springer: Berlin/Heidelberg, Germany, 2003; pp. 426–444. [Google Scholar]
- Dwork, C.; Naor, M.; Wee, H. Pebbling and Proofs of Work. In Annual International Cryptology Conference; Springer: Berlin/Heidelberg, Germany, 2005; pp. 37–54. [Google Scholar]
- Ren, L.; Devadas, S. Bandwidth hard Functions for ASIC Resistance. In Theory of Cryptography Conference; Springer: Berlin/Heidelberg, Germany, 2017; pp. 466–492. [Google Scholar]
- Bradley, W.F. Superconcentration on a Pair of Butterflies. arXiv 2014, arXiv:1401.7263. [Google Scholar]
- Cook, S.A. An observation on time-storage trade off. In Proceedings of the Fifth Annual ACM Symposium on Theory of Computing; Association for Computing Machinery: New York, NY, USA, 1973; pp. 29–33. [Google Scholar] [CrossRef]
- Kocher, P.; Jaffe, J.; Jun, B. Differential Power Analysis. In Annual International Cryptology Conference; Springer: Berlin/Heidelberg, Germany, 1999; pp. 388–397. [Google Scholar]
- Durvaux, F.; Gerard, B.; Kerckhof, S. Intellectual Property Protection for Integrated Systems Using Soft Physical Hash Functions. In International Workshop on Information Security Applications; Springer: Berlin/Heidelberg, Germany, 2012; pp. 208–225. [Google Scholar]
- Samarin, P.; Lemke-Rust, K. Detecting Similar Code Segments through Side Channel Leakage in Microcontrollers. In International Conference on Information Security and Cryptology; Springer: Berlin/Heidelberg, Germany, 2017; pp. 155–174. [Google Scholar]
- Kwon, D.; Kim, J.; Park, S.; Sung, S.H.; Sohn, Y.; Song, J.H.; Yeom, Y.; Yoon, E.J.; Lee, S.; Lee, J.; et al. New Block Cipher: ARIA. In International Conference on Information Security and Cryptology; Springer: Berlin/Heidelberg, Germany, 2003; pp. 432–445. [Google Scholar]
- Hong, D.; Lee, J.K.; Kim, D.C.; Kwon, D.; Ryu, K.H.; Lee, D.G. LEA: A 128-bit Block Cipher for Fast Encryption on Common Processors. In International Workshop on Information Security Applications; Springer: Berlin/Heidelberg, Germany, 2013; pp. 3–27. [Google Scholar]
- Park, J.; Lee, S.; Kim, J.; Lee, J. The SEED Encryption Algorithm; KISA: Seoul, Korea, 2005. [Google Scholar]



| Measurement (Key/Plaintex) | Maximum | Minimum | Mean | First Quartile | Third Quartile |
|---|---|---|---|---|---|
| AES | |||||
| Same key/Different plaintext | 0.99656 | 0.99433 | 0.99549 | 0.99519 | 0.99578 |
| Different key/Same plaintext | 0.99619 | 0.99406 | 0.99516 | 0.99488 | 0.99542 |
| Same key/Same plaintext | 0.99965 | 0.99820 | 0.99884 | 0.99859 | 0.99903 |
| Different key/Different plaintext | 0.99605 | 0.99361 | 0.99493 | 0.99461 | 0.99524 |
| LEA | |||||
| Same key/Different plaintext | 0.99495 | 0.99093 | 0.99288 | 0.99236 | 0.99337 |
| Different key/Same plaintext | 0.99502 | 0.99114 | 0.99283 | 0.99231 | 0.99331 |
| Same key/Same plaintext | 0.99980 | 0.99670 | 0.99809 | 0.99756 | 0.99854 |
| Different key/Different plaintext | 0.99471 | 0.99093 | 0.99271 | 0.99221 | 0.99317 |
| ARIA | |||||
| Same key/Different plaintext | 0.99612 | 0.99417 | 0.99505 | 0.99483 | 0.99526 |
| Different key/Same plaintext | 0.99611 | 0.99409 | 0.99498 | 0.99476 | 0.99518 |
| Same key/Same plaintext | 0.99987 | 0.99872 | 0.99919 | 0.99900 | 0.99937 |
| Different key/Different plaintext | 0.99594 | 0.99401 | 0.99492 | 0.99469 | 0.99514 |
| SEED | |||||
| Same key/Different plaintext | 0.99222 | 0.98817 | 0.99034 | 0.98990 | 0.99080 |
| Different key/Same plaintext | 0.99263 | 0.98849 | 0.99050 | 0.99005 | 0.99097 |
| Same key/Same plaintext | 0.99993 | 0.99834 | 0.99901 | 0.99875 | 0.99927 |
| Different key/Different plaintext | 0.99218 | 0.98801 | 0.99023 | 0.98976 | 0.99068 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kim, H.; Kim, K.; Kwon, H.; Seo, H. ASIC-Resistant Proof of Work Based on Power Analysis of Low-End Microcontrollers. Mathematics 2020, 8, 1343. https://doi.org/10.3390/math8081343
Kim H, Kim K, Kwon H, Seo H. ASIC-Resistant Proof of Work Based on Power Analysis of Low-End Microcontrollers. Mathematics. 2020; 8(8):1343. https://doi.org/10.3390/math8081343
Chicago/Turabian StyleKim, Hyunjun, Kyungho Kim, Hyeokdong Kwon, and Hwajeong Seo. 2020. "ASIC-Resistant Proof of Work Based on Power Analysis of Low-End Microcontrollers" Mathematics 8, no. 8: 1343. https://doi.org/10.3390/math8081343
APA StyleKim, H., Kim, K., Kwon, H., & Seo, H. (2020). ASIC-Resistant Proof of Work Based on Power Analysis of Low-End Microcontrollers. Mathematics, 8(8), 1343. https://doi.org/10.3390/math8081343





