1. Introduction
Zero-Trust (ZT) mechanisms [
1,
2,
3] have led to a new paradigm of cybersecurity, which is the new concept of “never trust, always verify” [
1]. Zero-Trust does not implicitly trust any entity, inside or outside the network. Continuous authentication, fine-grained access control, and real-time monitoring are used in system security against increasing numbers of threats [
4,
5,
6]. Today, this approach is especially important in environments of decentralized architecture, dynamic user behavior, and multiple access points [
7,
8,
9,
10]. Within the realm of next-generation networks, particularly 6G, the adoption of Zero-Trust can be a solution to the challenges brought on by highly complex distributed computing systems [
11,
12,
13,
14,
15].
Integrating distributed edge and fog computing plays a crucial role in the architecture of 6G networks, as it brings the data processing closer to its source so that it can minimize latency and further optimize resource utilization [
16]. When compared to edge computing, fog computing goes one step further, as it comprises additional layers between the edge devices and the cloud, as its name suggests [
17,
18,
19,
20]. To be able to support latency-sensitive applications such as autonomous vehicles, industrial IoT, and all of the smart city applications mentioned in [
21,
22,
23,
24], these paradigms are indispensable. However, the cybersecurity vulnerability of edge and fog computing environments, due to their distributed and decentralized nature, is significantly higher when compared to traditional computing environments [
25,
26,
27,
28,
29]. Nonetheless, traditional security mechanisms are usually poor at dealing with these challenges, as they do not scale to the peculiar demands of these environments [
30,
31,
32].
In the context of 6G networks, their ultra-low latency, high reliability, and connectivity of a massive number of devices are key, and, hence, robust security mechanisms are needed. They can be integrated into 6G networks with distributed edge and fog computing environments, where these challenges can be solved by using the scalable, adaptive solution of Zero-Trust principles [
33,
34,
35,
36]. Zero-Trust can be enabled with the usage of cutting-edge technologies like AI-powered anomaly detection, identity management on a blockchain, and dynamic access control policies to verify all the network entities continually. We introduce ZTF-6G, a Zero-Trust-based solution that can be used to deploy Zero-Trust and security to the distributed edge and fog computing in 6G networks; it is also capable of addressing their limitations and aligning with the next-generation system requirements [
37,
38,
39,
40].
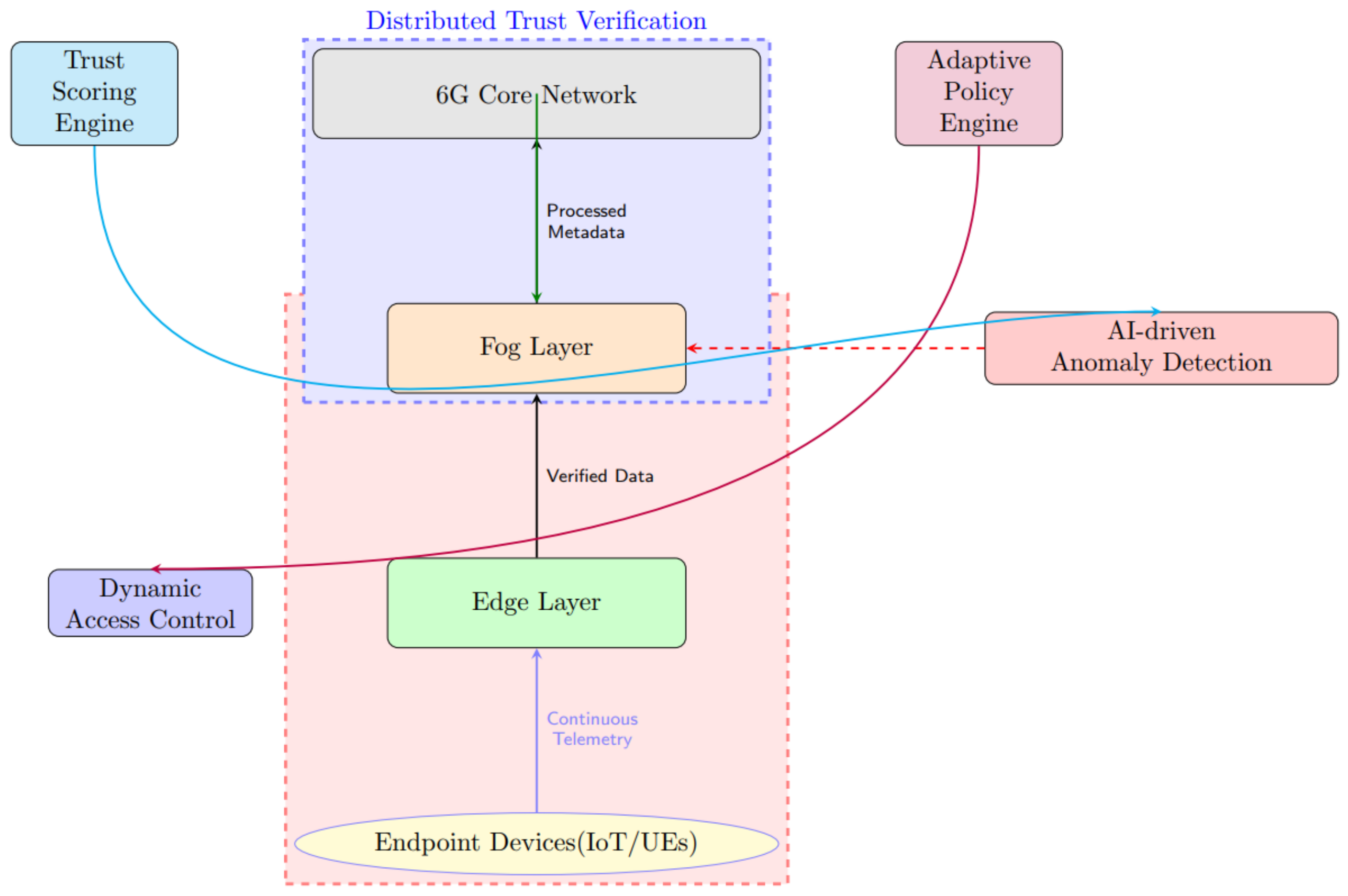
Figure 1 illustrates the proposed trust evaluation techniques in 6G Zero-Trust networks. The framework includes real-time anomaly detection, dynamic access control, and blockchain-based authentication to ensure security at the edge and fog layers.
Implementing Zero-Trust in 6G networks presents several challenges due to ultra-low latency requirements, a massively distributed architsaecture, and an expanding attack surface. Security mechanisms must operate within a sub-millisecond latency to support critical applications, such as autonomous vehicles and industrial IoT, without introducing delays [
41,
42,
43,
44]. The highly decentralized nature of 6G networks, with thousands of edge and fog nodes, makes centralized security models ineffective [
45,
46,
47,
48]. Additionally, multi-node authentication across edge, fog, and cloud layers remains complex and prone to performance bottlenecks [
49,
50]. Zero-Trust principles—such as ‘never trust, always verify’—face significant challenges when applied to 6G networks. Sixth-generation networks are anticipated to be highly distributed, low-latency, and massively connected with billions of devices. This introduces several obstacles for traditional Zero-Trust models:
- (a)
Decentralized Security Infrastructure: 6G networks require security mechanisms that scale across a highly decentralized and heterogeneous environment consisting of edge, fog, and cloud nodes. Traditional Zero-Trust frameworks, often designed for centralized environments, are ill suited for such vast and distributed systems.
- (b)
Ultra-Low Latency: For applications such as autonomous vehicles and industrial IoT, the Zero-Trust mechanisms must not only be secure but also efficient to minimize latency. Blockchain-based consensus and AI-driven anomaly detection can introduce delays that are not acceptable in latency-sensitive applications.
- (c)
Massive Device Connectivity: With billions of devices connected, dynamic trust evaluations and continuous authentication must be handled efficiently without overwhelming network resources.
- (d)
AI and Blockchain Integration: Implementing AI-based anomaly detection and blockchain for decentralized identity management in real time requires heavy computation and resource usage, which may not be feasible for all 6G-enabled edge devices.
The rapid growth of IoT and untrusted devices further expands the attack surface, increasing risks such as insider threats, unauthorized access, and AI-driven cyberattacks. Traditional Zero-Trust frameworks, designed for centralized cloud environments, struggle to scale efficiently for billions of 6G transactions. Moreover, resource-constrained edge devices lack the computational power to handle frequent re-authentication and heavy cryptographic processing, rendering traditional security approaches impractical.
To address these challenges, we propose ZTF-6G (Zero-Trust Framework for 6G Networks), which integrates AI-driven anomaly detection and blockchain-based authentication for real-time security enforcement. The framework dynamically adjusts trust scores based on user behavior and network anomalies, ensuring continuous verification without impacting performance. Blockchain-based identity management eliminates reliance on centralized trust authorities, providing tamper-proof authentication while reducing security risks. The use of lightweight cryptographic verification optimizes security for resource-constrained devices. Additionally, scalable and adaptive security policies ensure efficient multi-layer authentication, maintaining low latency while securing network interactions.
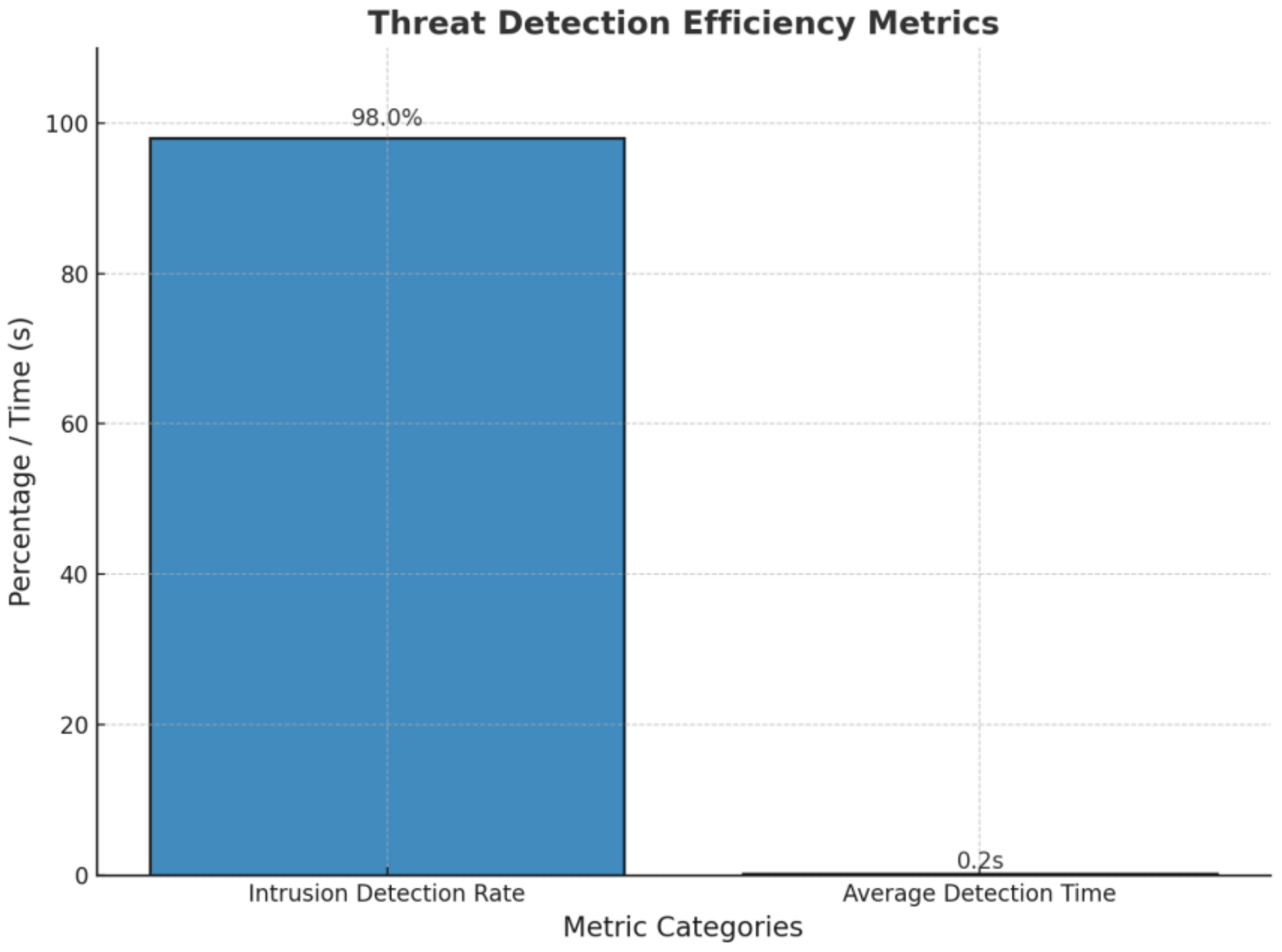
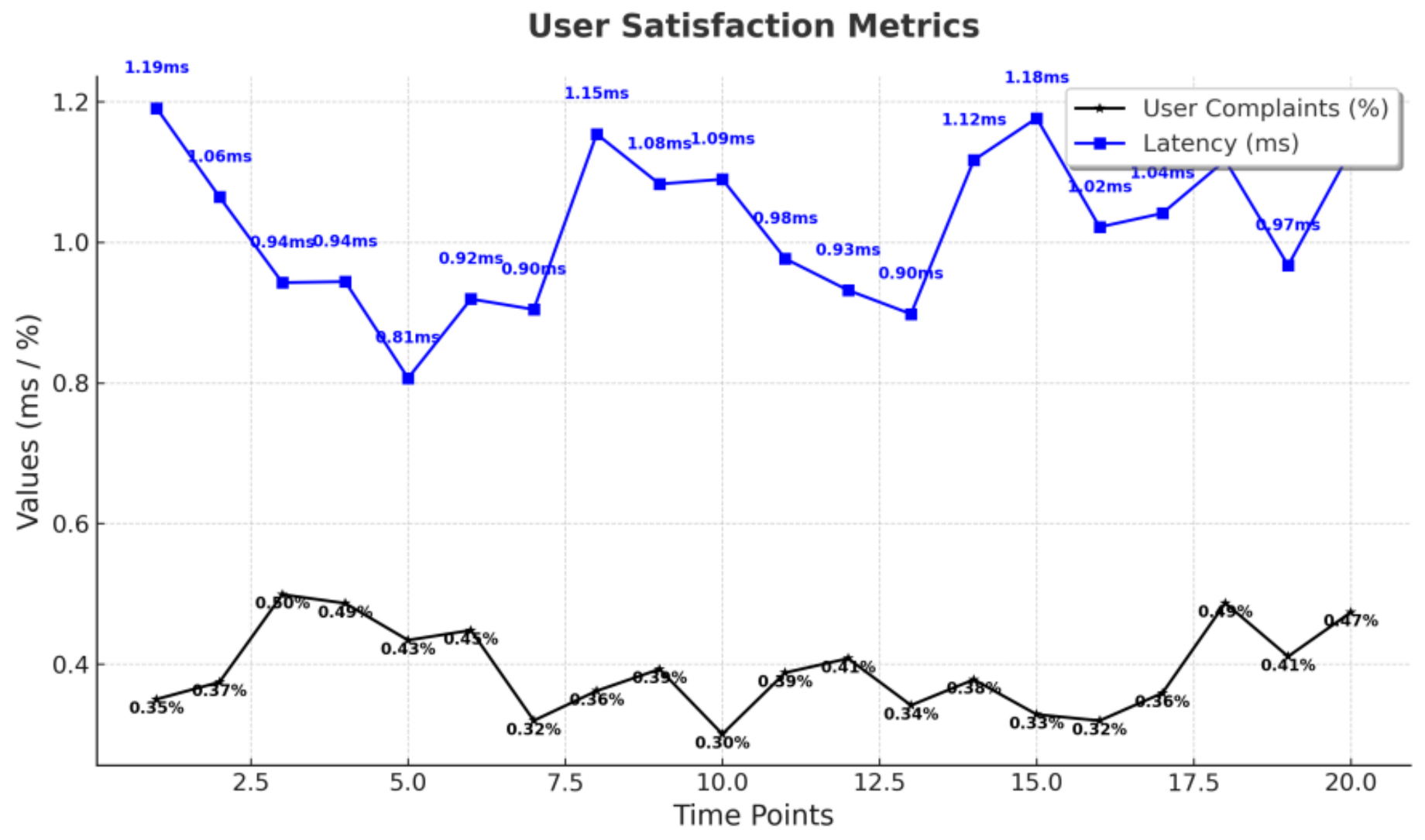
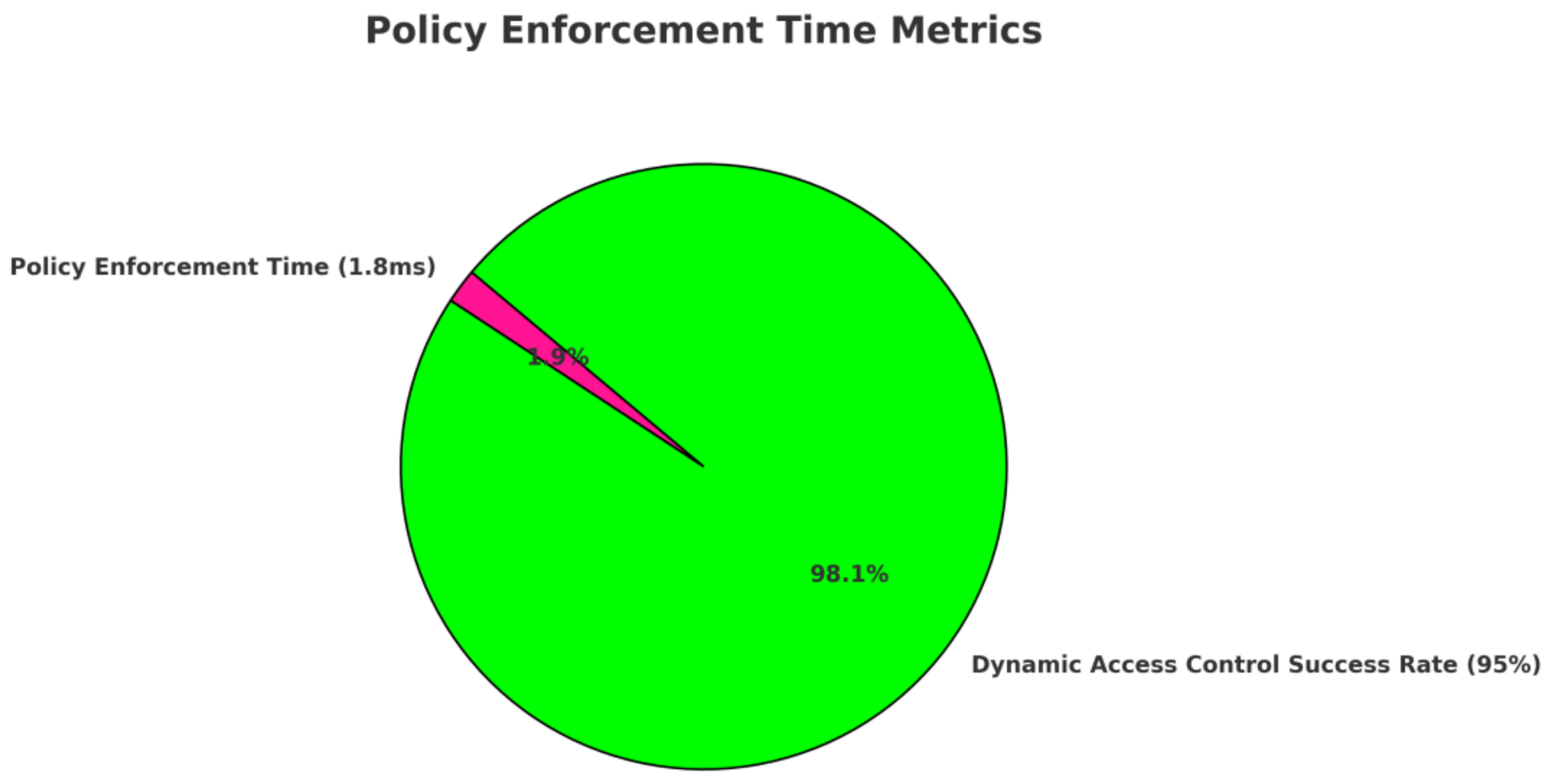
By mitigating security risks within 1.8 ms, ZTF-6G effectively blocks insider threats, unauthorized access, and AI-driven attacks, making it a highly scalable and efficient Zero-Trust solution for 6G networks.
1.1. Justification of Novelty and Improvement
The proposed ZTF-6G framework introduces a novel integration of Zero-Trust security mechanisms, specifically tailored for the 6G network environment. It addresses the growing security challenges associated with distributed edge and fog computing. Unlike traditional security models, which rely on static perimeter-based defenses and predefined access controls, ZTF-6G adopts a dynamic and AI-driven security approach that continuously evaluates trust scores derived from real-time network interactions. By leveraging machine learning-based anomaly detection, the framework can proactively identify and mitigate emerging threats, thereby reducing the risk of unauthorized access, data breaches, and insider threats. Additionally, ZTF-6G integrates blockchain-based identity verification, providing a decentralized, tamper-proof authentication system. This eliminates reliance on centralized trust authorities and enhances the integrity of access control mechanisms. The framework further employs adaptive anomaly detection algorithms that adjust network security policies based on contextual factors such as device behavior, historical interactions, and emerging threats. Unlike conventional approaches that compromise performance for security, ZTF-6G is designed to maintain ultra-low latency and high computational efficiency essential for 6G-enabled distributed computing environments. The combination of AI-driven security analytics, blockchain-backed authentication, and real-time access control makes ZTF-6G a highly scalable, resilient, and future-proof Zero-Trust solution for next-generation networks. It ensures that security mechanisms evolve alongside the rapid advancements in 6G technologies.
1.2. Securing Distributed Edge and Fog Nodes with Zero-Trust Mechanisms
In 6G networks, it is necessary to employ a robust mechanism that continuously authenticates and authorizes network entities while maintaining low latency and minimal resource overhead on the distributed edge and fog nodes. The key challenge is to design a Zero-Trust-based model in which interactions are dynamically monitored, and fine-grained access controls are enforced to prevent unauthorized access and insider threats.
The problem formulations are clearly defined, with corresponding symbols and descriptions outlined in
Table 1.
Here, represents the total risk score of the network, which needs to be minimized. The term denotes the adjacency matrix representing the connection between nodes and , while is the computed trust score between them. The cost function captures the security cost of interactions. The objective is to minimize risk by penalizing connections with lower trust scores, effectively reducing the likelihood of communication between potentially compromised nodes.
Subject to the following: This approach periodically computes trust scores for each node to ensure that communication only occurs when the trust thresholds are met. The network topology is represented using an adjacency matrix, and the objective function aims to minimize the aggregated risk score by considering both trust scores and communication costs. Resource usage is constrained within predefined limits, and communication is permitted only under specified access control constraints.
1.3. Dynamic Resource Allocation for Secure Edge and Fog Computing
Resource allocation in distributed edge and fog computing for 6G networks under Zero-Trust security constraints remains a critical optimization challenge. The goal is to balance resource utilization, maintain low latency, and implement dynamic access policies to ensure secure and efficient operations.
represents the allocated bandwidth for node , while denotes power consumption. The coefficients and control the trade-off between latency and energy efficiency.
A risk-aware bandwidth allocation strategy can be incorporated by introducing a risk factor , which accounts for node reliability, past performance, and authentication frequency. Higher values indicate potentially compromised nodes, prompting stricter bandwidth restrictions and additional security verifications.
Subject to the following: The focus of this formulation is to minimize latency and energy efficiency in the resource allocation problem for secure edge and fog operations. The trade-off between latency and energy consumption is balanced as part of the objective function, and the total bandwidth and power consumption are constrained to system limits. Just like Zero-Trust, trust scores are established to ensure that resource access is secure.
The integrity and security of 6G-enabled distributed systems are threatened by unique and evolving security risks. This research introduces a novel framework that combines Zero-Trust principles with cutting-edge technologies to provide a robust, scalable, and adaptive security solution to the 6G-enabled distributed systems.
Proposed a novel Zero-Trust Framework (ZTF-6G): It is designed for securing dynamic and decentralized edge and fog computing environments in 6G networks.
Developed AI-driven anomaly detection modules: It guarantees the real-time identification and solving of security threats.
Implemented blockchain-based identity management: It provides decentralized, tamper-proof authentication and fine-grained access control.
Validated the framework through simulations: The system demonstrated significant improvements in security, scalability, and overall performance when compared to traditional approaches.
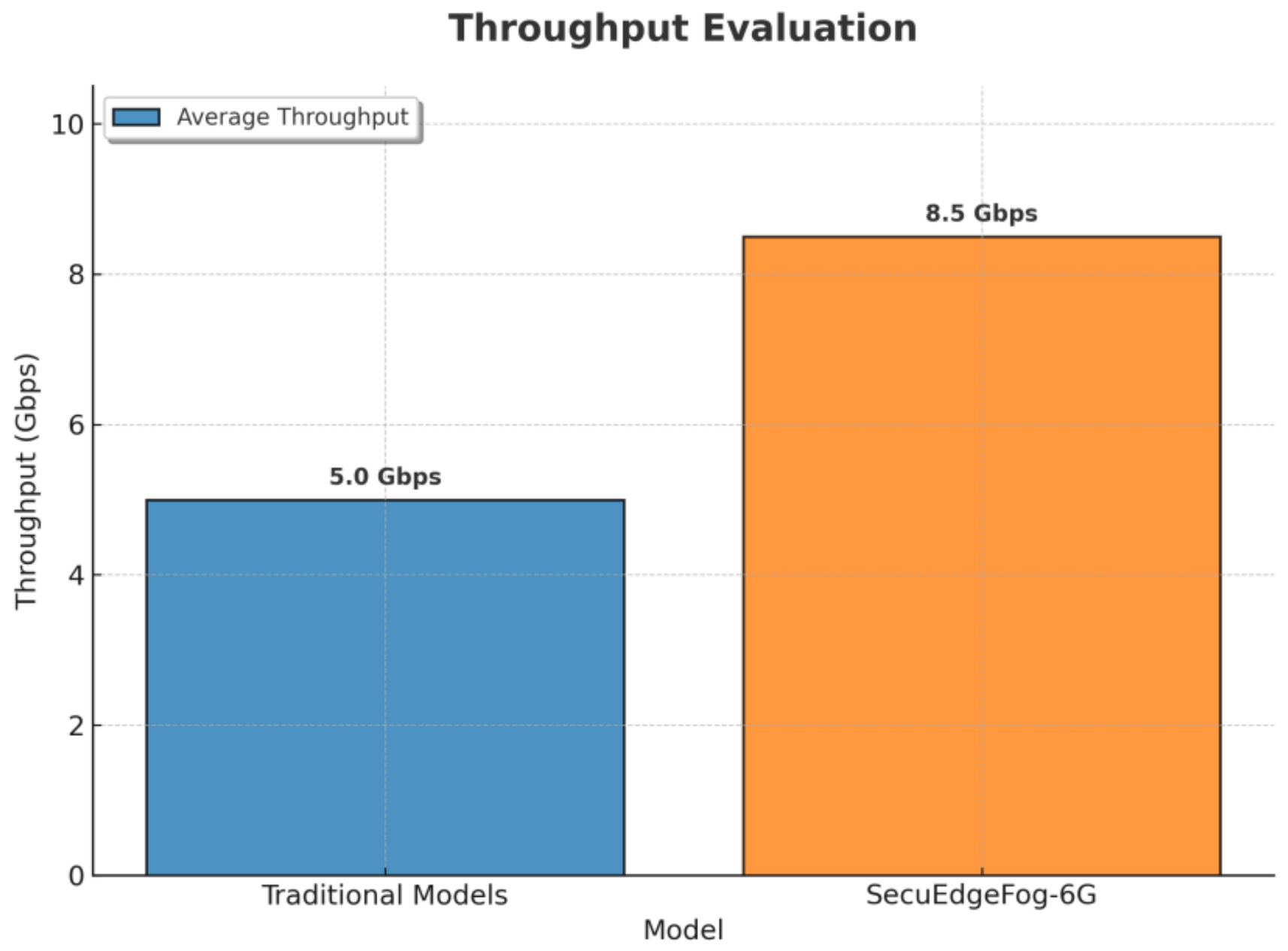
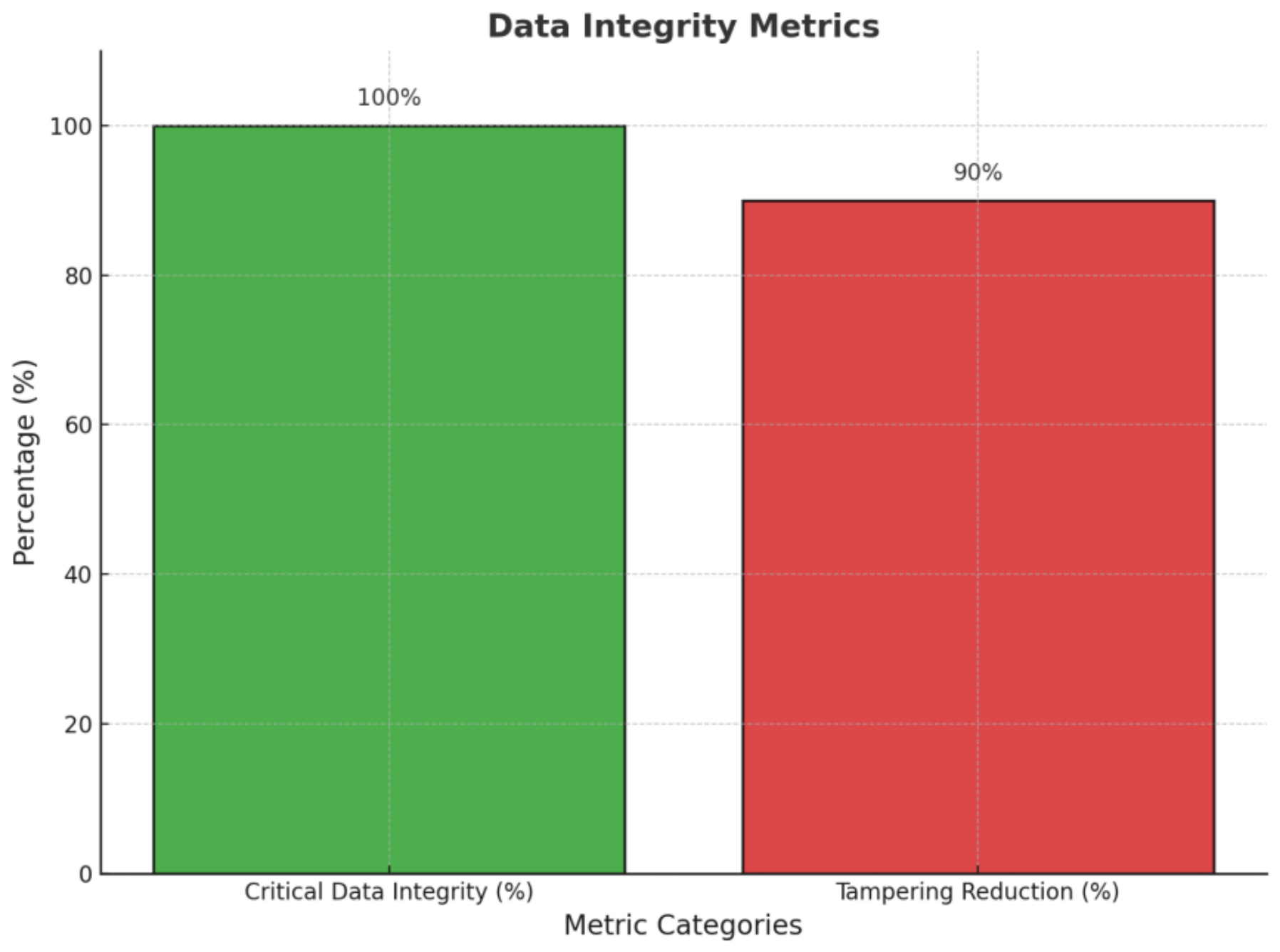
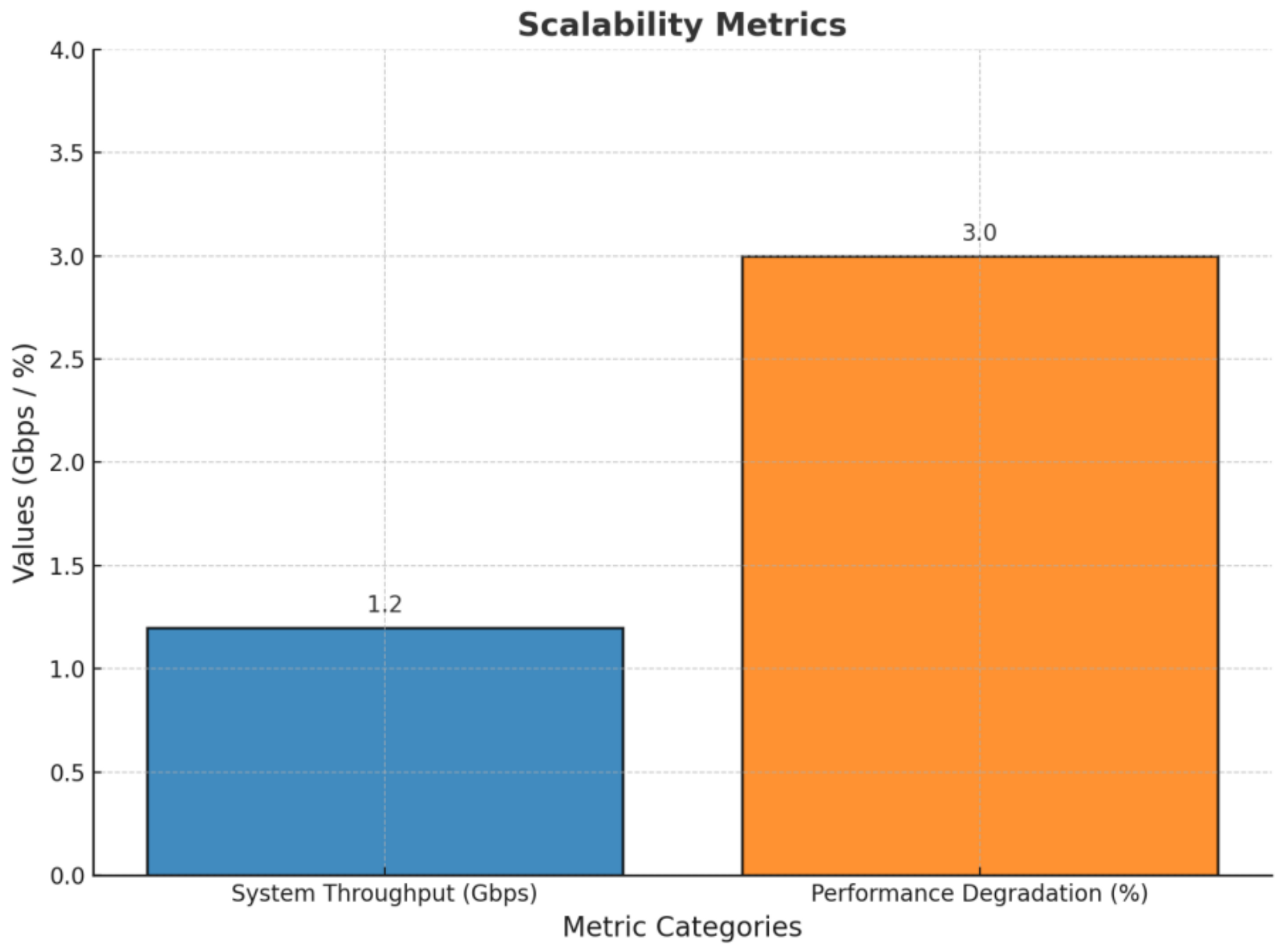
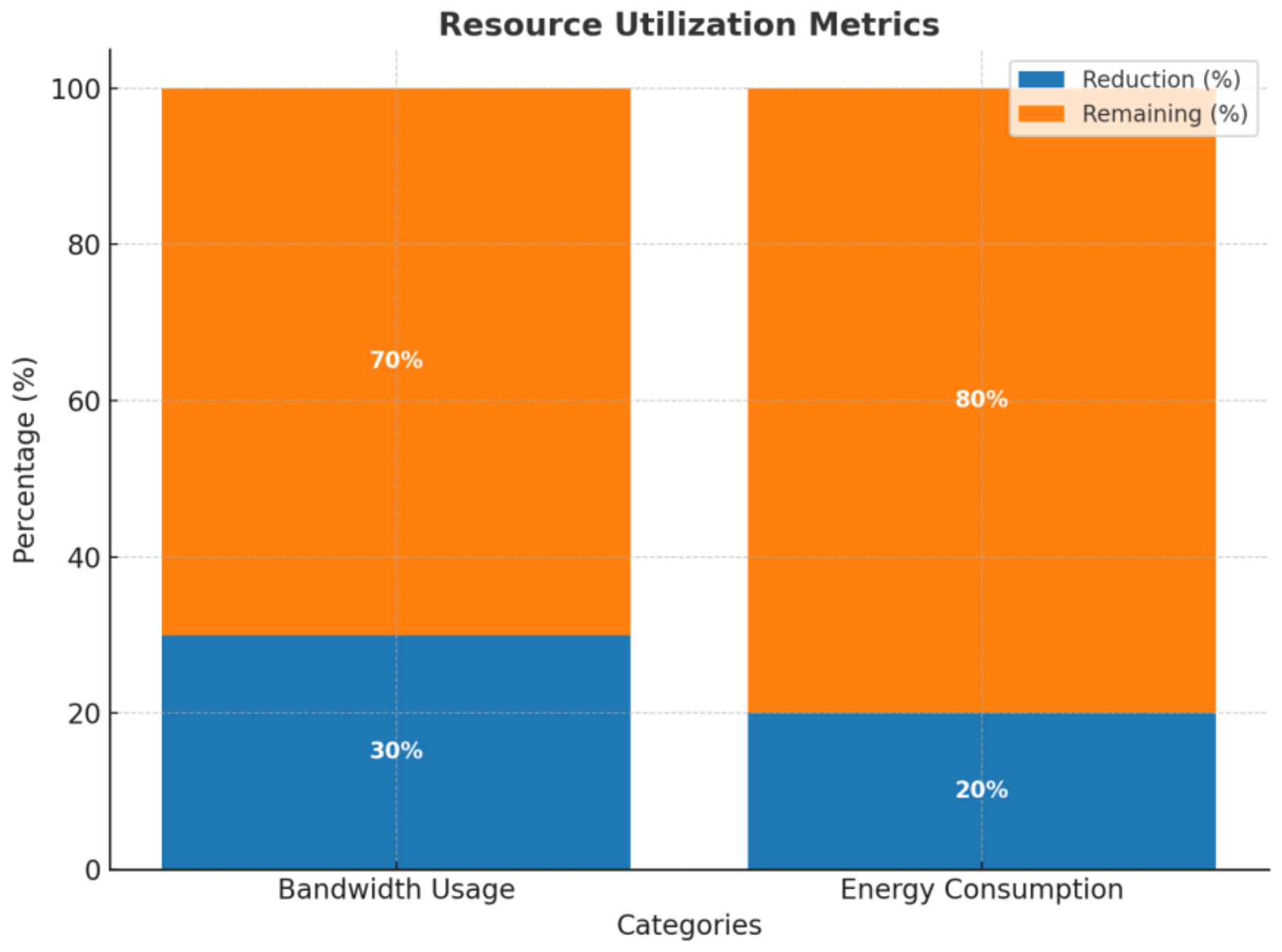
Optimized Resource Allocation and Performance: Achieves 77.6% lower latency, 70% higher throughput, and 41.5% better resource utilization compared to traditional models.
The paper is organized into four main sections, as described below: The research begins by presenting the problem that requires Zero-Trust principles for 6G network security.
Section 2 details the related works and literature studies.
Section 3 details the proposed ZTF-6G framework, including its architecture, key components, and methodology, outlining the design, implementation, and simulation setup.
Section 4 discusses the results and evaluations, comparing the performance of ZTF-6G with the existing methods.
Section 5 concludes the paper by summarizing the key findings and suggesting future research directions.
2. Related Work
Zero-Trust frameworks have emerged as crucial security paradigms for 6G networks, addressing diverse security challenges such as risk mitigation, access control, authentication, and anomaly detection. Several existing models have been proposed to enhance the security of distributed computing in 6G, leveraging AI, blockchain, and decentralized trust mechanisms.
Security experts recognize the growing need to implement Zero-Trust mechanisms for 6G networks, as they address specific security demands of distributed edge and fog computing platforms [
1,
2,
3].
According to researchers [
4,
5,
6,
7,
8],
Zero-Trust analytics offer solutions for modernized authentication, enhanced access control, and threat detection in dynamic, decentralized 6G environments.The 6G network architecture relies on edge and fog computing, which places data processing resources close to their sources, thereby enabling low-latency processing [
10,
11,
12,
13,
14]. This method reduces data analysis time, making it suitable for applications such as autonomous vehicles, smart healthcare systems, and real-time analytics. Although these paradigms are inherently decentralized, the attack surface, so to say, is significantly expanded, making the network vulnerable to a variety of security threats, such as unauthorized access, data breaches, and distributed denial of service (DDoS) attacks [
8]. In order to address these concerns, Ali et al. [
4] proposed a maturity framework for Zero-Trust security in multi-access edge computing. On the basis of fine-grained access control mechanisms and continuous monitoring, their framework puts an emphasis on risk mitigation and robust defense mechanisms. Kaur et al. [
16] also studied the application of Zero-Trust principles in securing fog computing in the healthcare domain. Their blockchain-integrated Zero-Trust framework ensures secure data exchange and tamper-proof authentication, addressing the sector’s high standards for privacy and data integrity [
15,
16,
17,
18,
19,
20]. These studies collectively underscore the flexibility of Zero-Trust principles in adapting to dynamic and distributed environments such as edge and fog computing [
9,
21,
22,
23,
24]. However, practical implementations of these solutions continue to face challenges, including the scalability of security mechanisms to accommodate the growing number of connected devices and the resource efficiency required to operate within constrained environments [
25,
26,
27,
30].
The adoption of Zero-Trust mechanisms in 6G networks has gained substantial momentum due to the stringent security requirements of ultra-low latency, high reliability, and mission-critical applications such as remote surgery, industrial automation, and autonomous systems [
28,
29,
32,
33,
37]. Given their massive device connectivity and reliance on real-time data exchange, 6G networks require advanced security solutions. To address these needs, Chen et al. [
7] proposed a software-defined Zero-Trust model, integrating AI-driven security policies for dynamic trust evaluation in 6G networks. This model employs behavior-based anomaly detection, continuously adapting access control policies based on network conditions. However, its heavy dependency on AI inference accuracy may result in false positives or negatives, potentially compromising overall security reliability. To overcome the limitations of centralized authentication, Sedjelmaci et al. [
34] developed a decentralized Zero-Trust framework for 6G Radio Access Networks (RANs). Their model introduces hierarchical trust scoring, decentralized access control, and lightweight encryption techniques to enable low-latency authentication. Despite its advantages, the computational overhead of trust management could negatively impact real-time network performance. Enright et al. [
10] applied artificial intelligence to integrate Zero-Trust frameworks, utilizing machine learning algorithms for intelligent threat detection and automated response mechanisms. In addition, this integration not only accelerates threat management, but also provides a proactive view of potential vulnerabilities before they are exploited. Collectively, these contributions highlight Zero-Trust as a foundational security paradigm for 6G networks. However, challenges remain in terms of operational complexity and seamless integration with the existing infrastructure—both of which are active areas of research.
With the rise in intelligent decision-making and data-handling techniques, emerging fields such as artificial intelligence (AI) and blockchain have enhanced the capabilities of Zero-Trust frameworks. Ramezanpour et al. [
26] designed a Zero-Trust model that combines AI and blockchain for 6G security, enhancing proactive threat mitigation and decentralized identity management. By integrating biometric authentication, the framework ensures robust security. However, its computational intensity makes it less suitable for resource-constrained edge devices. Blika et al. [
6] proposed a Federated Learning-based Zero-Trust model, which enhances security in distributed nodes while preserving user privacy. By applying adaptive risk assessment policies, the model strengthens authentication mechanisms. Nevertheless, federated learning introduces communication overhead, which may affect network efficiency in high-load environments. Similarly to the work of Yiliang et al. [
40], the Zero-Trust-based mobile network security architecture proposed for decentralized identities uses a blockchain to manage decentralized identities. The inherent immutability and transparency of blockchain make its authentication processes tamper-proof and verifiable, thereby mitigating risks such as identity spoofing and unauthorized access. The integration of AI and blockchain not only enhances security mechanisms but also addresses key challenges such as scalability, decentralized control, and system interoperability. This is especially relevant in distributed environments such as edge and fog computing, where traditional centralized security models face significant limitations. These technologies enable dynamic, distributed control and promote robust, efficient, and adaptive implementation of Zero-Trust in next-generation networks.
Several comprehensive surveys have synthesized the growing body of research on Zero-Trust architecture, examining its applications, benefits, and outstanding challenges. According to Nahar et al. [
22], Zero-Trust plays a central role in 6G networks, addressing issues such as system heterogeneity, interoperability, bandwidth and computational limitations, and the dynamic enforcement of policies in evolving network contexts. Their findings emphasize the need for adaptable and resource-efficient frameworks capable of supporting the diverse requirements of 6G applications. In the context of 6G smart networks, Liyanage et al. [
19] investigated the convergence of Zero-Trust with technologies such as IoT and artificial intelligence. The primary objective of their review is to understand how these technologies can improve Zero-Trust with the help of intelligent automation, real-time analytics, and secure device-to-device communication. Across these studies, researchers emphasize the urgent need for Zero-Trust frameworks that not only secure systems but also maintain performance and usability in complex, distributed environments. Given the increasing heterogeneity and connectivity of modern networks, Zero-Trust principles and emerging technologies must jointly address challenges such as horizontal scaling, latency, and dynamic resource allocation.
Beyond general use cases, Zero-Trust framework implementations are rapidly expanding across sectors, as organizations recognize the need for tailored security solutions that address their specific industry requirements. Safak et al. [
31] studied security and privacy mechanisms in 6G-enabled Internet of Everything (IoE) networks within the banking domain, where institutions face advanced cyber threats such as financial fraud, data breaches, and ransomware attacks. The study demonstrated how Zero-Trust principles—such as continuous monitoring, granular access control, and secure identity verification—can collectively mitigate these risks by ensuring only authorized users and devices access sensitive financial data. Similarly, Son et al. [
38] proposed a Zero-Trust authentication scheme for IoT environments in 6G networks, incorporating secure and context-aware access control for interconnected devices. This approach evaluates not only user credentials, but also contextual factors such as device behavior and location, providing an additional layer of protection against unauthorized access. These studies emphasize the flexibility of Zero-Trust frameworks in addressing diverse and sector-specific security requirements, from industrial IoT to financial systems. With Zero-Trust, the security mechanisms are themselves set as flexible and adaptive, which makes it a foundational paradigm to support strict sector-specific use cases.
The rapid advancement in 6G wireless networks necessitates robust security frameworks to tackle evolving cyber threats and network vulnerabilities. Yang et al. [
42] explored cross-layer automated security solutions for 6G, emphasizing the importance of Zero-Trust networks that incorporate AI-driven anomaly detection and self-adaptive security mechanisms. While they proposed Zero-Trust security automation, their model lacked decentralized trust mechanisms, making it vulnerable to identity spoofing. Although their approach enhances automation, the absence of decentralized trust management renders it vulnerable to insider attacks. In contrast, Singh et al. introduced WIND, a Wireless Intelligent Network Digital Twin, leveraging federated learning and multi-layer optimization to enhance privacy-preserving security mechanisms in decentralized networks [
43]. However, federated learning—though effective in distributed environments—introduces computational overhead that can hinder real-time Zero-Trust enforcement. Additionally, Hamroun et al. provided an extensive survey on intrusion detection in 5G and Wi-Fi networks, identifying critical limitations in current intrusion detection methods, particularly in multi-access edge computing (MEC) scenarios [
44]. Their work highlights the need for adaptive, AI-driven security frameworks capable of mitigating novel attack vectors in heterogeneous 6G environments. Building upon these studies, the proposed ZTF-6G framework integrates blockchain-based authentication, real-time AI-driven anomaly detection, and Zero-Trust adaptive access control, addressing the limitations of the existing models and enhancing security, scalability, and efficiency in distributed 6G edge and fog computing networks.
The convergence of Zero-Trust principles with emerging technologies, such as AI and IoT, within the 6G framework has been extensively studied, upon which new opportunities for securing distributed systems in real time have been found. IoT environments are being scrutinized by Singh et al. [
36], who examined the part that Zero-Trust architecture plays within these environments to help resolve its critical problems, including ensuring that data are authentic, preventing the use of unauthorized devices, and protecting the massive quantities of data generated by IoT devices. This reaffirms Zero-Trust’s importance for secure device-to-device communication and data integrity in environments where traditional security methods fail to meet the complexity and scale requirements. Another significant contribution comes from Partala and Agrawal [
25], who explored Secure Edge Intelligence in 6G networks, integrating Zero-Trust principles with AI-driven security policies. Their framework supports secure data offloading and distributed decision-making, ensuring robust authentication and threat mitigation. However, the model prioritizes computational efficiency over advanced security enforcement, which may create vulnerabilities in mission-critical applications.
Recent advancements in Zero-Trust security for 6G networks focus on decentralized authentication and proactive enforcement to address evolving cyber threats. Traditional models struggle with scalability and resource constraints in distributed edge and fog computing. Bai et al. [
41] proposed a blockchain-based caching strategy for mobile edge computing but lacked adaptive trust mechanisms. Chen et al. [
7] introduced an AI-driven Zero-Trust model for 6G but faced high computational overhead. To overcome these limitations, we propose ZTF-6G, integrating AI-driven anomaly detection and blockchain-based authentication for real-time trust scoring and tamper-proof identity verification. Unlike previous models, ZTF-6G ensures high security, minimal latency, and efficient resource utilization, making it an optimal Zero-Trust solution for 6G networks.
Ali et al. [
4] introduced a Zero-Trust framework for multi-access edge computing (MEC), focusing on risk mitigation through continuous monitoring and fine-grained access control. This framework enforces real-time authentication and adaptive security policies, ensuring that only verified entities can access critical resources. However, it lacks blockchain-based identity verification, which could further enhance the integrity of authentication mechanisms. In contrast, Kaur et al. [
16] developed a blockchain-powered Zero-Trust framework tailored for fog computing in healthcare. Their model ensures tamper-proof authentication and secure data exchange among medical IoT (MIoT) devices by utilizing smart contracts. While effective for healthcare applications, the model’s scalability remains a challenge when applied to broader 6G environments.
While each of these frameworks contributes valuable security enhancements, they exhibit limitations such as lack of scalability, high computational requirements, or inefficiencies in anomaly detection. Our proposed ZTF-6G framework addresses these gaps by integrating AI-driven anomaly detection, blockchain-based identity management, and adaptive trust scoring into a unified security architecture. Unlike prior models, ZTF-6G ensures a multi-layered security approach by incorporating lightweight AI models to reduce computational overhead and optimize real-time authentication. Additionally, it supports scalable security solutions applicable across diverse 6G domains, including smart cities, autonomous vehicles, and industrial IoT. By leveraging blockchain’s decentralized authentication and AI-driven trust scoring, ZTF-6G overcomes the weaknesses of the existing frameworks and offers a robust, scalable, and adaptive Zero-Trust solution for next-generation 6G networks.
Table 2 presents a comparative analysis of studies focusing on Zero-Trust mechanisms. Furthermore, it highlighted what they looked at, what technologies they used, and what they wrote that is relevant to peers working for distributed edge and 6G networks. A Zero-Trust-based framework (ZTF-6G) for edge-to-fog distributed computing in a 6G network is proposed to meet the following requirements of securing the network, including real-time threat detection, adaptive access control, and enhancing the data integrity with low latency and scalability. ZTF-6G provides a novel integration of Zero-Trust principles specifically designed to address the unique challenges posed by 6G networks. Key innovations include the following:
AI-driven Anomaly Detection: The real-time detection of security threats through machine learning models enables continuous authentication and behavior analysis for dynamic trust scoring.
Blockchain-Based Authentication: A decentralized approach to identity management ensures tamper-proof authentication and eliminates reliance on centralized trust authorities, thereby reducing the risk of insider threats and unauthorized access.
Adaptive Access Control: The trust evaluation mechanism in ZTF-6G continuously adjusts security policies based on the current network environment, device behavior, and previous interactions, ensuring granular control over access rights.
3. Methodology
This section outlines the systematic methodology used to design, develop, and evaluate the proposed framework. It covers the collection of datasets, preprocessing, experimental setup, implementation, and performance evaluation.
3.1. Dataset Collection
To ensure the adequacy of the data collected for this study, data from publicly available datasets and custom-generated sources were used. The datasets included features such as latency, throughput, and network events under varying network conditions. To address specific research requirements, publicly available data were augmented with simulated data to fill gaps in the existing resources. This hybrid approach combined the strengths of scenario-based modeling and realist methodology, ensuring the dataset was representative of real-world conditions while maintaining diversity and scalability. The dataset used in this research is a hybrid of publicly available intrusion detection data (e.g., UNSW-NB15) and synthetic data generated using NS-(3) and OMNeT++ (6.0) simulators. These simulators model 6G-specific attack vectors such as AI-driven cyberattacks and insider threats, which are critical in the context of 6G network security.
3.2. Dataset Description
The dataset used in this study consists of 50,000 instances, combining both real-world network logs (30%) and synthetically generated data (70%) to ensure comprehensive coverage of 6G-specific security scenarios. The real-world data are sourced from open-source intrusion detection systems, capturing diverse network activity, authentication requests, access control logs, and previously recorded cyber threats. This ensures the dataset reflects actual network behavior and security challenges faced in distributed edge and fog computing environments. Synthetic data were generated using NS-3 and OMNeT++ simulators, modeling advanced 6G attack vectors such as AI-driven cyberattacks, adversarial machine learning intrusions, dynamic insider threats, and trust manipulation attacks—scenarios that are underrepresented in publicly available datasets. The dataset includes key performance metrics such as latency, throughput, trust scores, anomaly detection logs, authentication attempts, and attack instance details, ensuring a diverse and realistic representation of security conditions in 6G networks. By integrating real and synthetic data, this dataset effectively captures scalability challenges, Zero-Trust authentication complexities, and real-time threat detection requirements necessary for evaluating the ZTF-6G framework.
While the dataset contains 50,000 instances, the majority are synthetically generated. The risk of sample bias from this overrepresentation is acknowledged. To mitigate this, future work will involve real-world testing using a 6G test platform to ensure that the synthetic data accurately reflects real-world 6G scenarios. Algorithm 1 below outlines the ZTF-6G security enforcement and trust evaluation process.
| Algorithm 1: ZTF-6G Security Enforcement and Trust Evaluation. |
Input: → Data from edge devices → Number of network nodes → Initial trust score for each node → AI-detected anomalies → Blockchain verification module
Output: Steps:
Initialize Security → Set network size, edge-fog nodes, and trust scores. Deploy AI-driven anomaly detection and blockchain authentication. Monitor Activity → Detect anomalies, unauthorized access, or threats. Update trust scores dynamically. Evaluate Trust threshold, grant access; else, trigger re-authentication. Blockchain Verification → If re-authentication is needed, verify identity via blockchain and log records securely. Adaptive Access Control → Restrict or restore access based on trust score variations. Optimize Performance → Measure latency, throughput, and security overhead. Minimize processing delays. Simulate & Compare → Test attack models, trust variations, and security strategies. Log and compare results with baseline models.
End Algorithm |
3.3. Simulation Parameters and Dataset Details
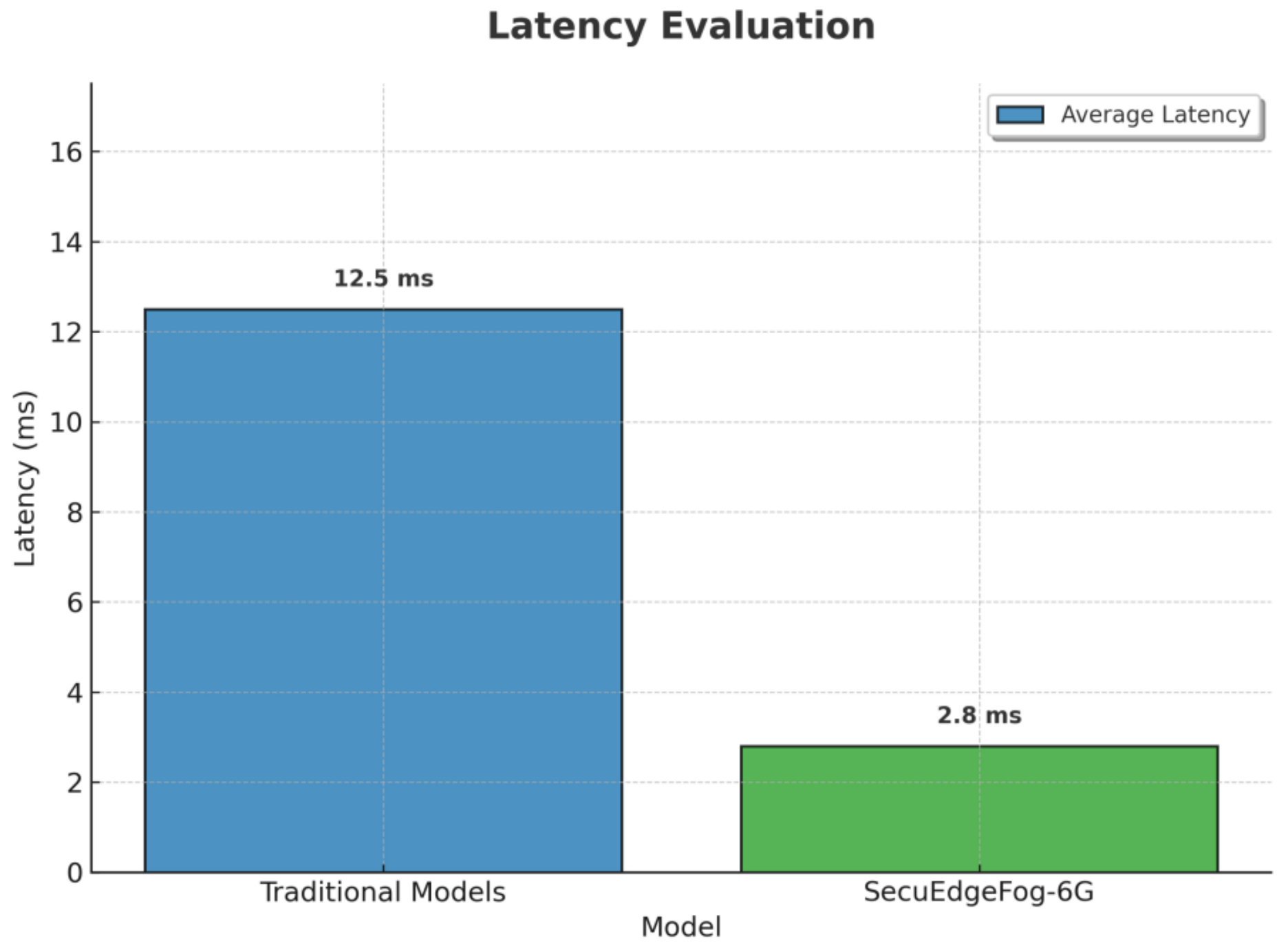
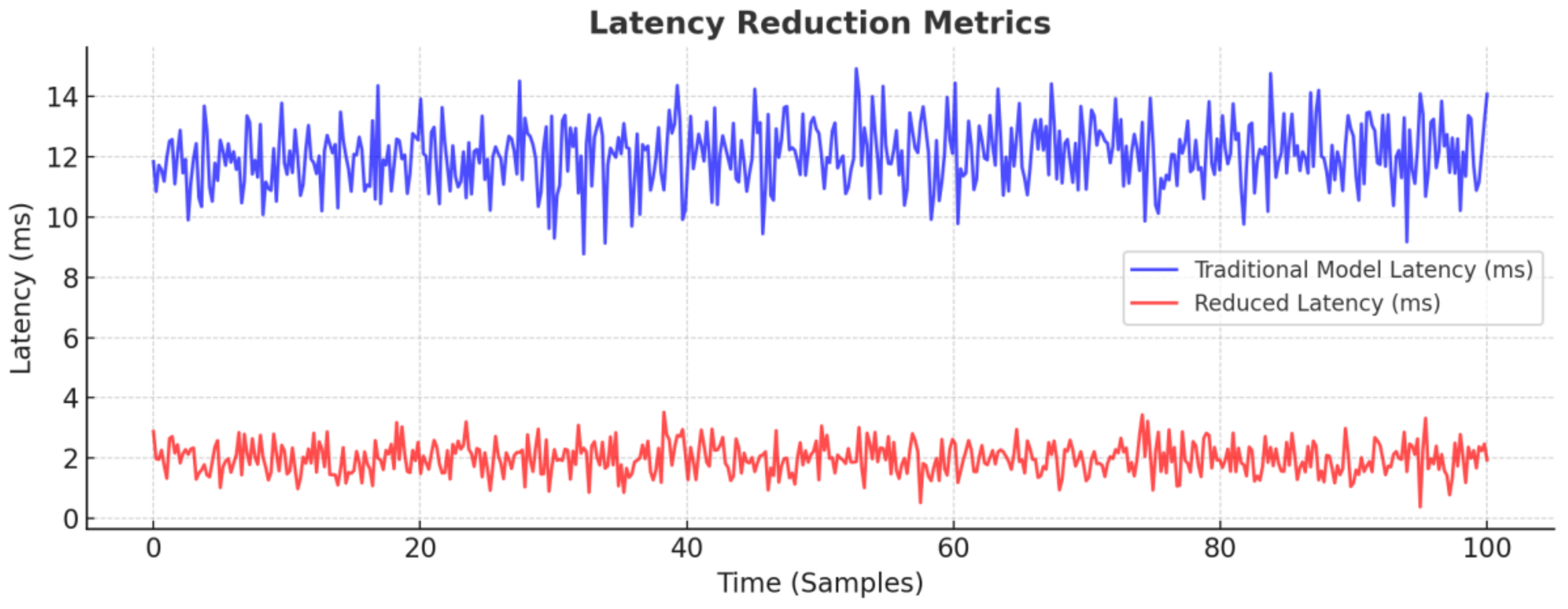
The simulations were conducted using OMNeT++ and NS-3, incorporating a dataset of 50,000 instances to evaluate the performance of ZTF-6G. The dataset comprises 30% real-world network logs sourced from open-source intrusion detection systems and 70% synthetically generated attack scenarios designed using network simulation tools to replicate 6G-specific security threats. The simulated network environment includes 10,000 connected devices, ensuring scalability and real-world applicability. Performance evaluation was based on key simulation parameters, including a latency benchmark of 12.5 ms for traditional security models. In comparison, ZTF-6G achieved a significantly lower latency of 2.8 ms. The system processed 1000 authentication requests per second, demonstrating its ability to handle high-security verification loads efficiently. Blockchain transaction latency was measured at 0.7 ms, ensuring secure decentralized authentication without compromising performance. Additionally, an AI-based anomaly detection system with a 12-layer deep learning architecture was deployed to identify and mitigate threats in real time, further improving security enforcement. These parameters provide a realistic, scalable, and computationally efficient environment to validate ZTF-6G’s superiority over traditional Zero-Trust models in 6G networks. The dataset composition is summarized in
Table 3 below.
3.4. Proposed Model: SecuEdgeFog-6G
To meet the stringent requirements of 6G networks, we propose SecuEdgeFog-6G—a model based on edge and fog computing paradigms—integrating Zero-Trust principles. The model employs a hierarchical architecture designed to achieve ultra-low latency, high scalability, robust security, and efficient resource utilization. In this section, we provide a detailed description of the architecture, the underlying mathematical model, and the implementation algorithm.
3.5. Model Architecture
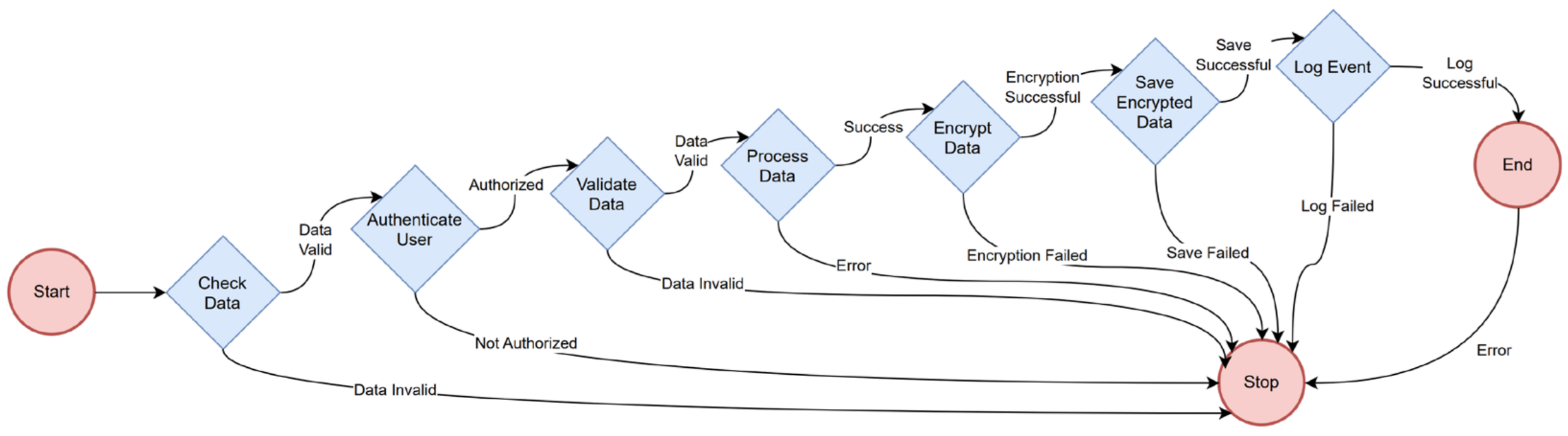
The structured process of secure data handling—starting with an initial data validation—is illustrated in the flowchart shown in
Figure 2. User authentication is carried out if the data are valid. Subsequent data processing occurs only after successful authentication and validation by the system. The next step is data encryption; upon success, the encrypted data are securely stored. Once the encrypted data are stored, system integrity is maintained by logging the event. If an error occurs at any stage—such as invalid data, unauthorized access, encryption failure, or logging failure—the process is terminated to ensure security and prevent inconsistencies. The UML flowchart below clearly outlines the decision points and possible outcomes, providing a comprehensive model for the secure and systematic handling of data.
3.6. Edge Layer
The edge layer comprises IoT devices, mobile phones, and sensors that gather and preprocess data close to the source. This layer handles latency-sensitive tasks that require immediate responses. Lightweight Zero-Trust mechanisms are employed to perform authentication and prevent unauthorized access.
3.7. Fog Layer
The fog layer acts as an intermediate computational tier between edge devices and the core network, handling advanced processing tasks offloaded from the edge. Security and efficiency are maintained using AI-driven Zero-Trust mechanisms based on real-time anomaly detection. Decentralized authentication is guaranteed through blockchain-based identity management.
3.8. Core Network Layer
The core network handles centralized storage, global analytics, and deep learning model training. It serves as a storage and security monitoring platform with long-term storage of data and provides seamless communication with edge and fog layers.
3.9. Mathematical Model
The SecuEdgeFog-6G framework is mathematically formulated to ensure security and operational efficiency across all three architectural layers. This section defines the key components as follows:
3.9.1. Latency Minimization
Latency
in the system can be modeled as follows:
where
is the total number of tasks;
is the data size of task ;
is the bandwidth allocated to task .
To minimize latency, we optimize bandwidth allocation using the following:
The optimal allocation of bandwidth
can be expressed as follows:
where
is the total available bandwidth.
3.9.2. Resource Utilization
The total resource utilization
is defined as follows:
where
The objective is to optimize resource utilization:
To balance computational load across nodes, the resource allocation for each task
can be modeled as follows:
where
represents the weight assigned to task
based on its priority.
3.9.3. Zero-Trust Mechanism
Zero-Trust security involves continuous verification of entities using trust scores
:
where
is the authentication score of entity ;
is the historical behavior score of entity ;
and are weights such that .
To dynamically adjust
based on network conditions, we define the following:
where
is the base trust score and
represents the frequency of anomalies detected for entity
.
3.9.4. Energy Efficiency
The total energy consumption
can be minimized as follows:
where
is the Total Energy Consumption;
is the Energy Consumption of Network Operations;
is the Energy Consumption Due to Blockchain Operations.
The objective is to minimize while satisfying task constraints.
3.9.5. Explanation of ZTF-6G Workflow
We show below Algorithm 2 for SecEdgeFog-6G workflow.
| Algorithm 2: SecuEdgeFog-6G Workflow. |
Input: Data from edge devices D, available resources R, trust scores . Output: Processed results . Initialize edge, fog, and core layers. For each task i in D, do If (i.e., if is latency-sensitive), then Process at the edge layer. Else Offload to the fog layer. If resources at the fog layer are insufficient, then Forward to the core network. Else Reject task iii due to an insufficient trust score. Return processed results .
|
The security enforcement and trust evaluation process begins by setting up the network size and initializing the trust scores for all the devices based on their previous trust history and device type. This initial configuration ensures that each device’s security posture is accounted for from the start. Once the network is initialized, the system uses AI models to continuously monitor real-time network activity and detect any anomalies. These anomalies may include unauthorized access attempts or unusual behaviors that deviate from normal network activity. If an anomaly is detected, the system flags the corresponding device for further verification to prevent potential security breaches. Next, the system evaluates each node’s trust score based on current interactions and historical behavior. If the calculated trust score is below a predefined threshold (total < T threshold), access is denied, or the system may request re-authentication to ensure that only trusted devices remain within the network. If re-authentication is required, the system utilizes blockchain consensus mechanisms to verify the identity of the device and securely log the transaction. This decentralized approach eliminates single points of failure, strengthening the authentication process. Finally, once the trust score is updated, the access control policy is dynamically adjusted. Based on the updated trust score, the access control mechanism either grants or revokes access to the network, ensuring that only devices with a verified and trustworthy status can interact with the system. This dynamic approach maintains high security while minimizing potential vulnerabilities.
This article proposes the SecuEdgeFog-6G model—based on a hierarchical edge–fog–core architecture and incorporating state-of-the-art Zero-Trust mechanisms. At the mathematical level, the model optimizes latency, resource utilization, and security. The proposed algorithm supports automatic task management through systematic workflows. The model is particularly well suited for 6G-enabled applications such as autonomous vehicles, smart cities, and industrial IoT, as it delivers robust, scalable, and secure performance.
3.10. Evaluation Matrix
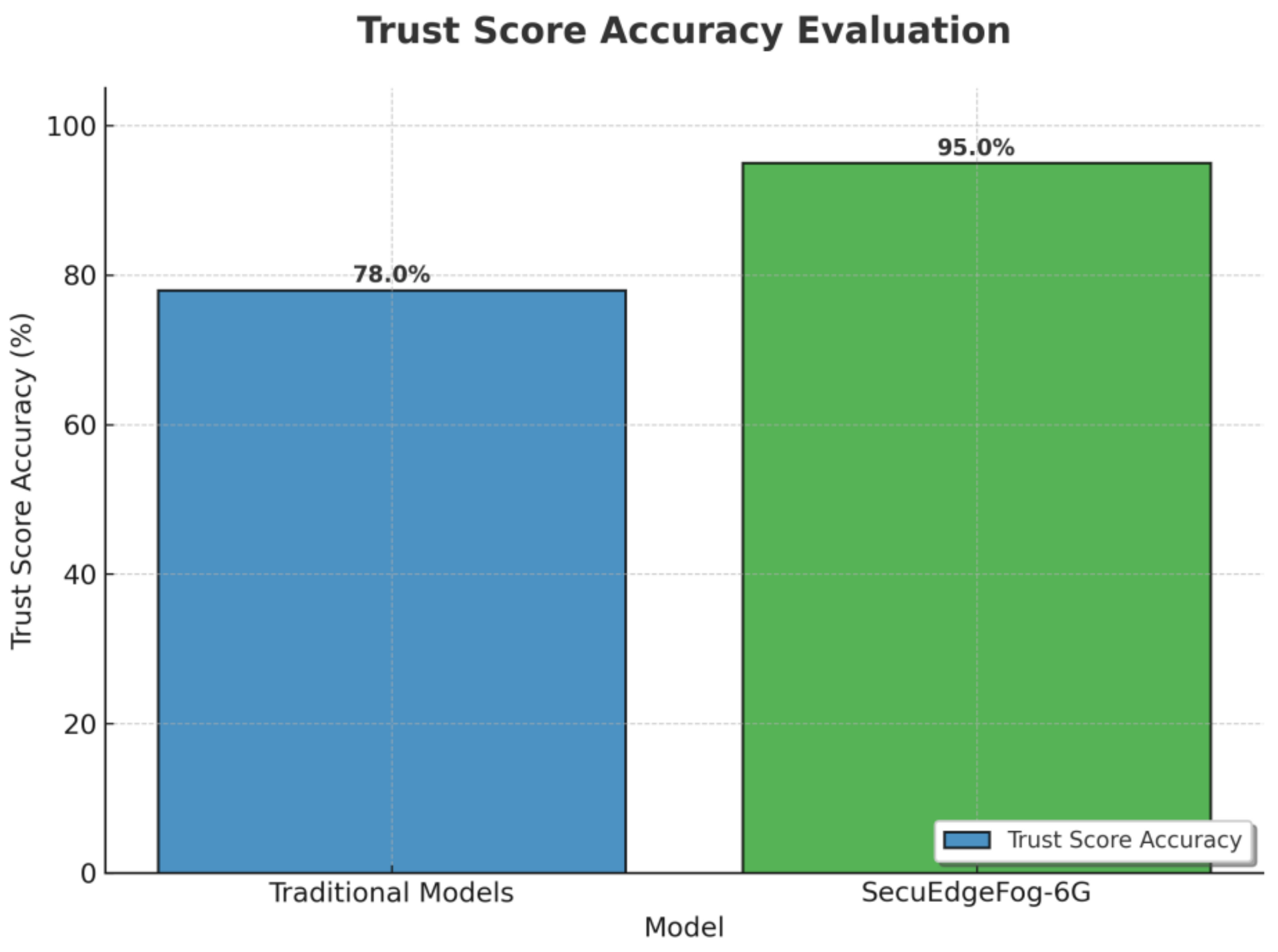
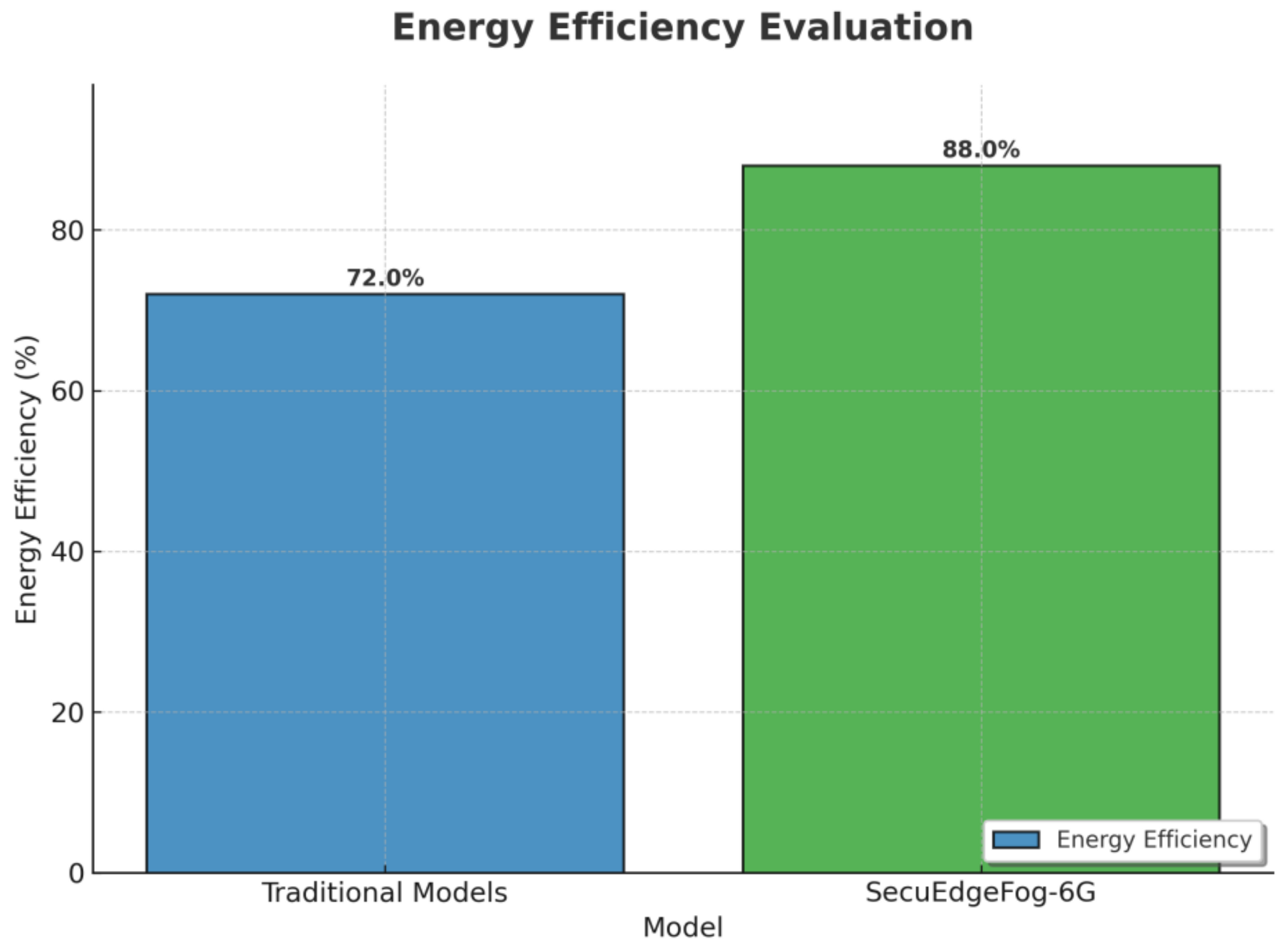
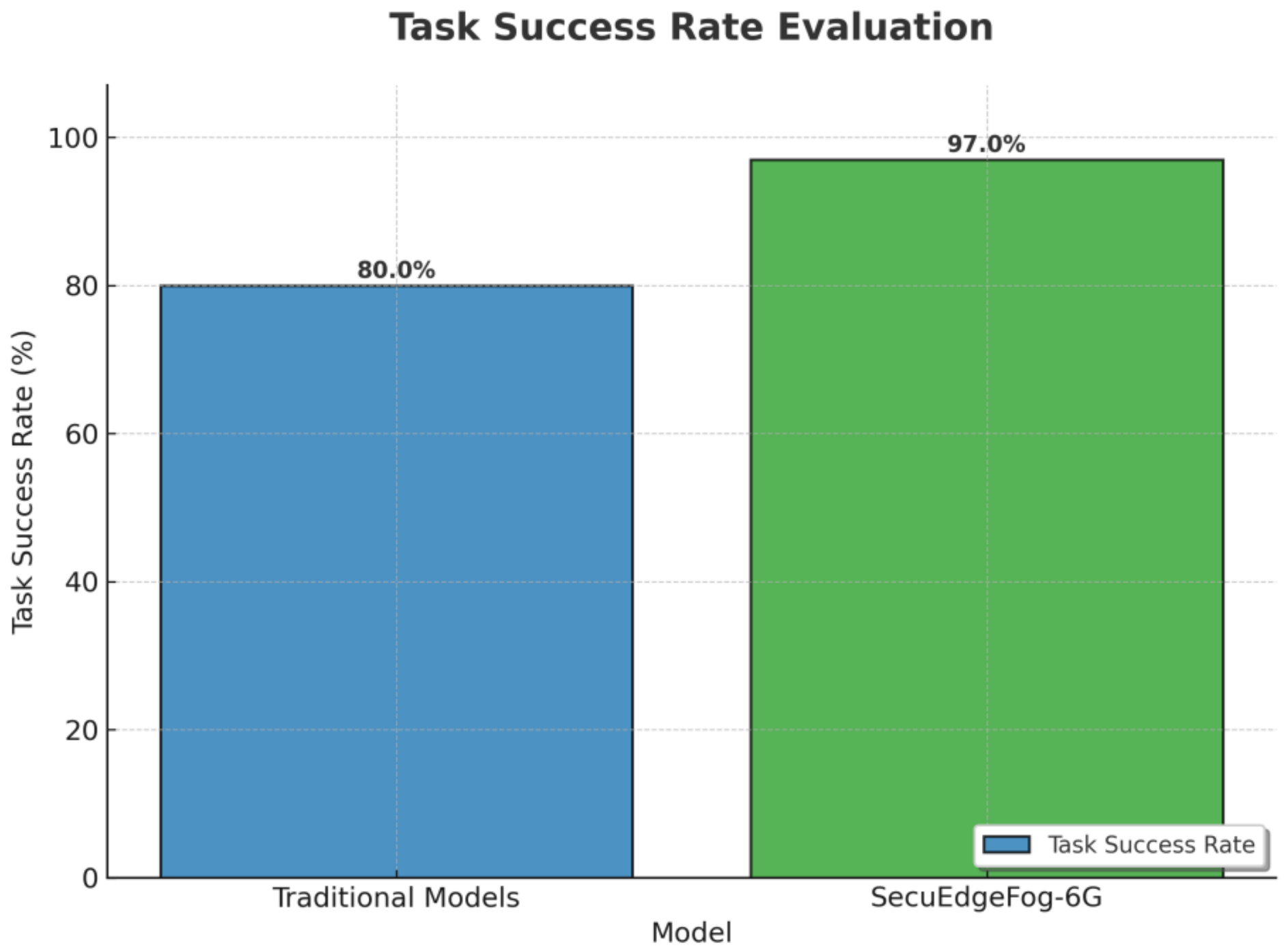
Metrics shown in
Table 4 are used to evaluate the performance of the
SecuEdgeFog-6G model. These metrics provide a comprehensive insight into the system’s effectiveness, efficiency, and security.