H∞ Performance of FlexRay Protocol-Based Networked Control Systems Subjected to Randomly Occurring Cyber Attacks
Abstract
1. Introduction
- How to construct a suitable switched system model to take full account for the transmission characteristics of the FRP and the impact of ROCAs?
- How to make sure the system is stable when switching between the static and dynamic segments, especially at the switching point?
- How to design a practical algorithm to calculate the controller gains?
- The closed-loop switched system with a mode-dependent output feedback controller is investigated for the first time within the framework of stability analysis, where the signal is transmitted by the FRP and the system is subjected to ROCAs.
- Sufficient conditions for the MSES and performance of the switched system are developed by utilizing a mode-dependent Lyapunov function in conjunction with the ADT approach. These conditions are employed to determine a set of matrices instead of the conventional yet conservative matrix . This approach serves to diminish conservatism while simultaneously ensuring the system stability when switching between the static and dynamic segments.
- A FRP-based MSES algorithm, which is practical and feasible, is presented to determine the corresponding controller gain of each mode.
2. Problem Formulation
2.1. System Model
2.2. FlexRay Protocol
- (1)
- :where represents the sensor node granted network access at time . For , through the zero-order holder (ZOH), there holds
- (2)
- :where represents the sensor node granted network access at time and are weighted matrices, which are known positive definite matrices. Let by virtue of the ZOH, can be represented by
2.3. Randomly Occurring Cyber Attacks
2.4. Controller Design
2.5. System Augmentation
2.6. Switched System
3. Main Results
| Algorithm 1 MSES Algorithm. |
|
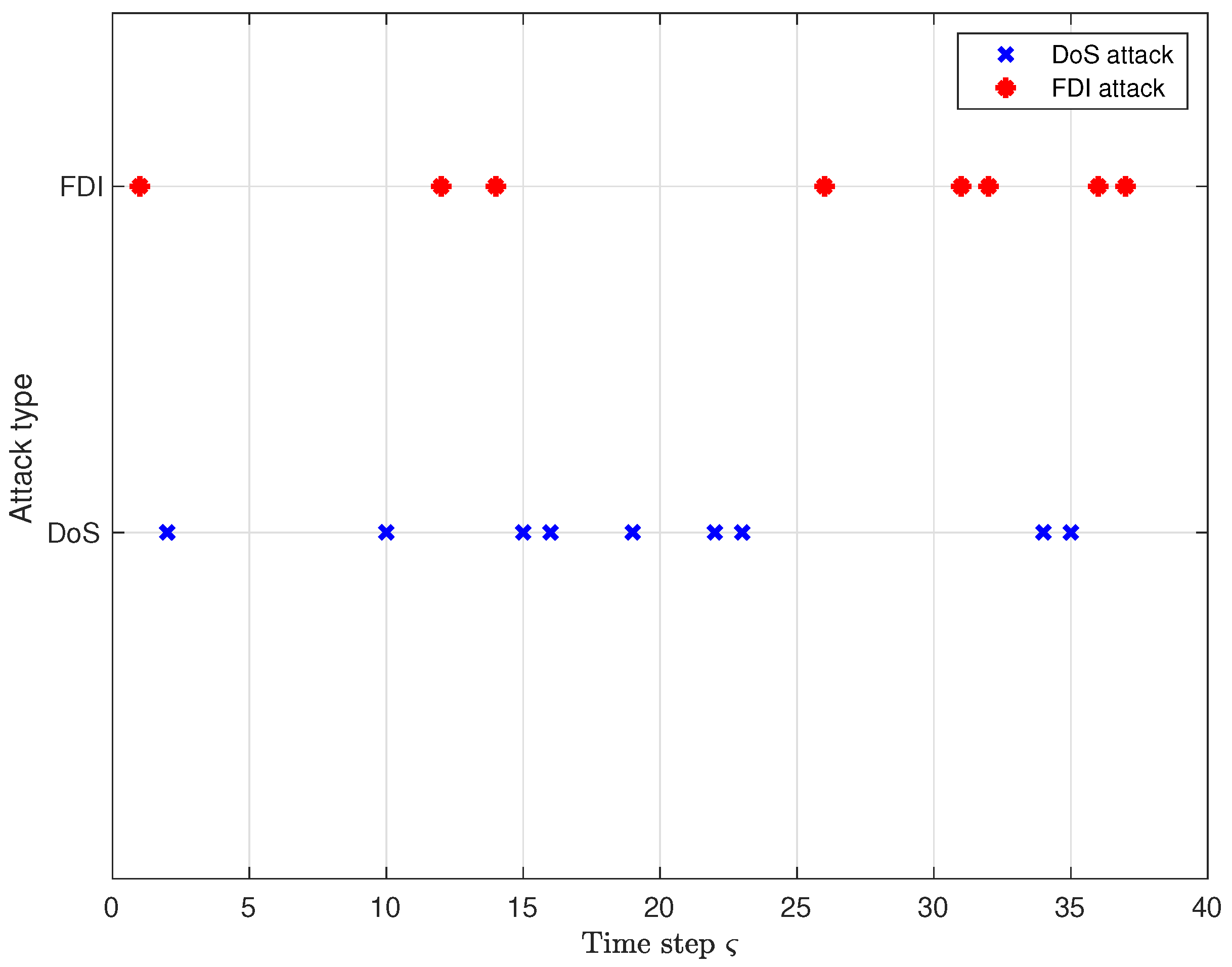
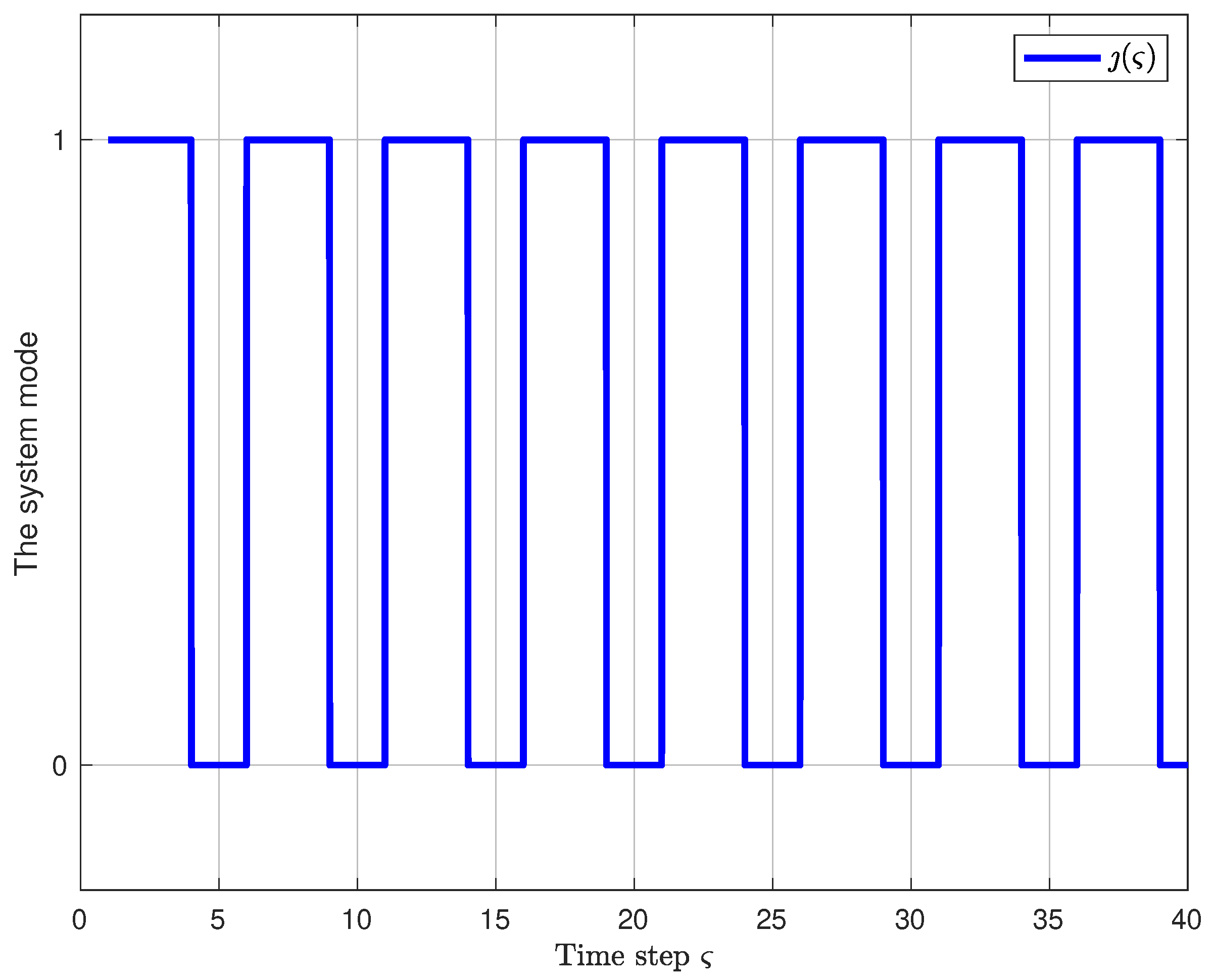
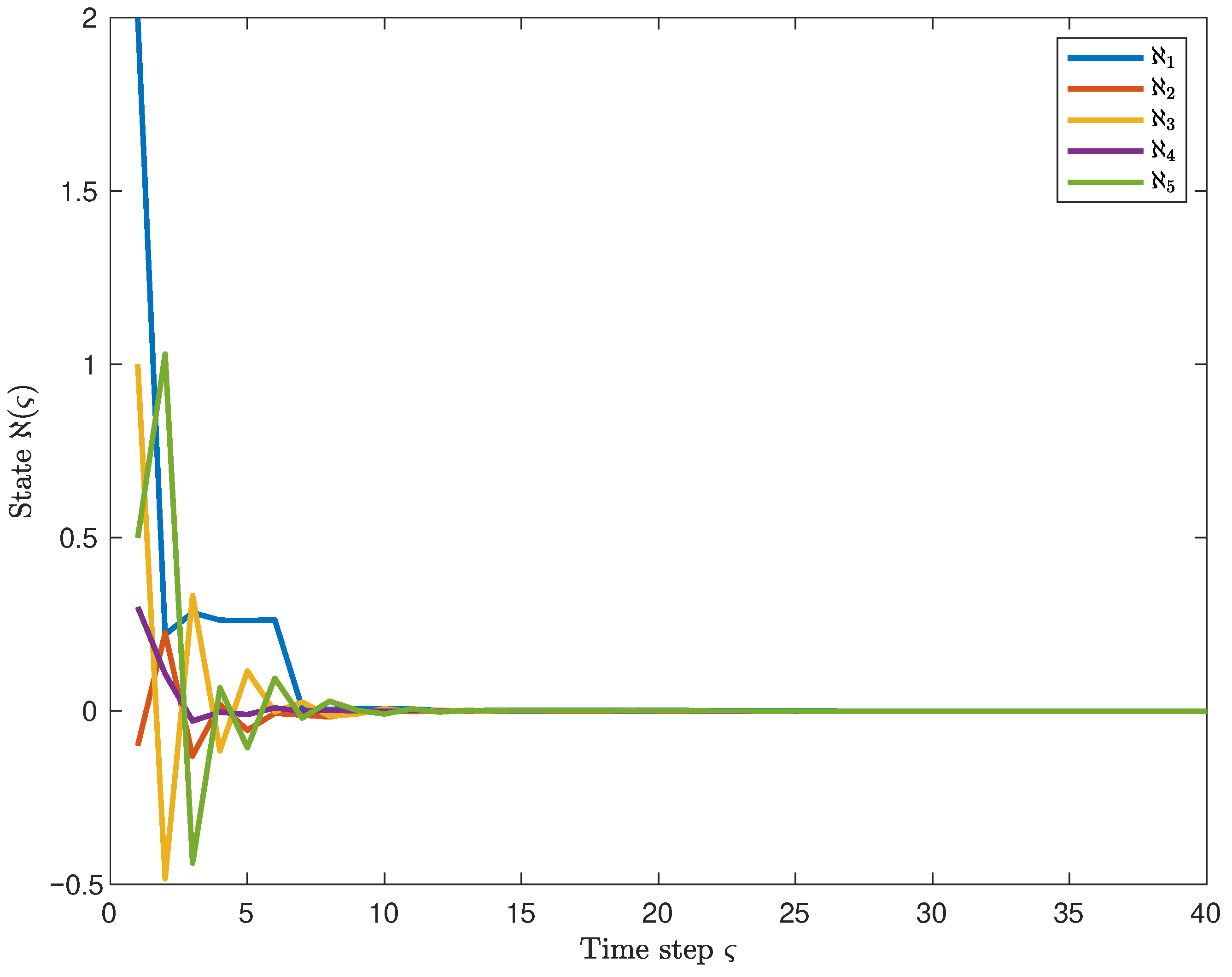
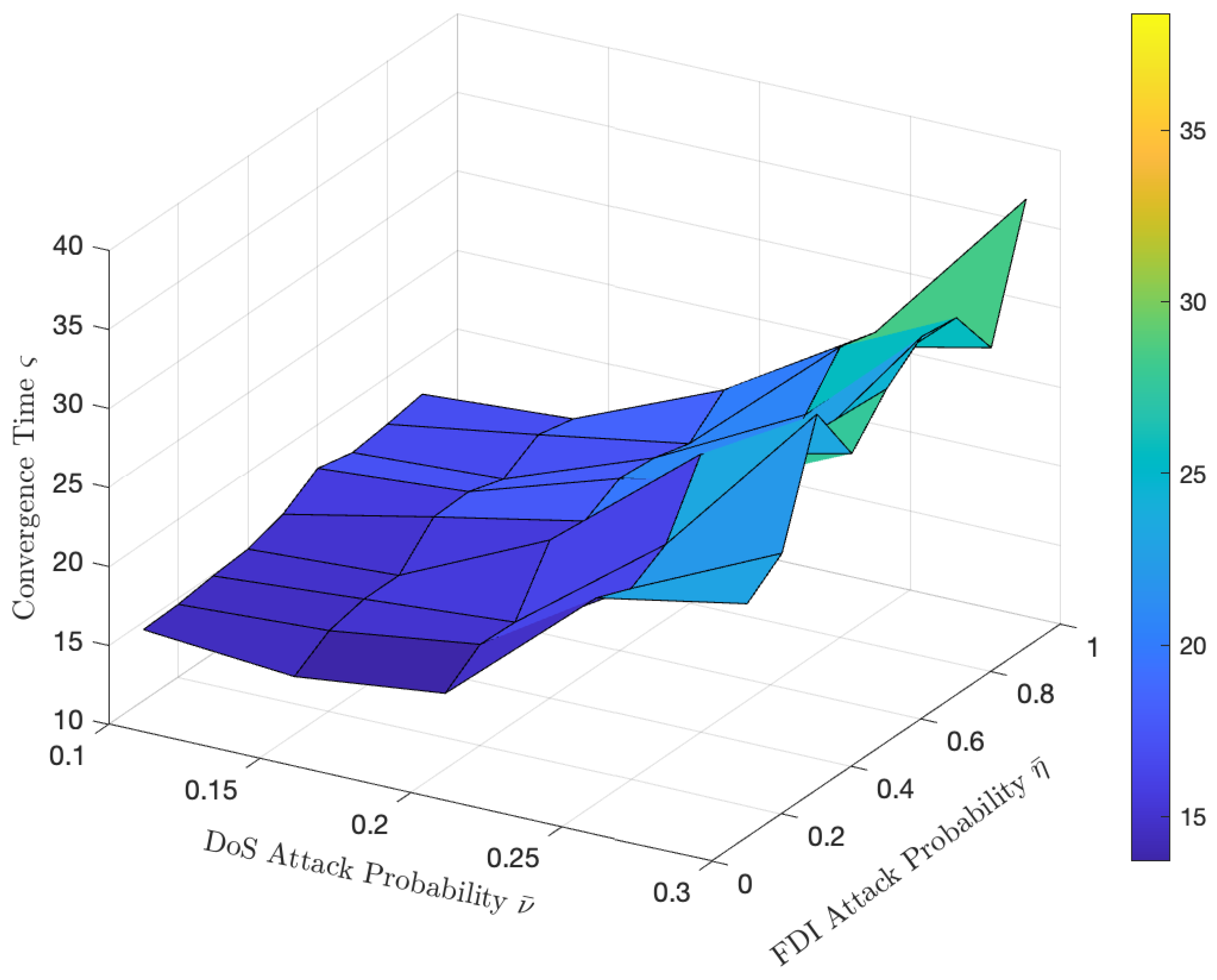
4. Simulation Results
5. Discussion
- Due to the possible switching signal detection delays, which may lead to controller mismatches within each switching interval [57], a natural extension of this work is to consider asynchronous switching between subsystems and their corresponding controllers. Such asynchrony commonly arises in practical NCSs, and studying its impact on stability and performance will be an interesting topic for our future research.
- In addition, other network-induced phenomena (such as time delay) and actuator saturation are typical phenomena in NCSs. Several recent studies [49,58] have incorporated performance, time delays, and actuator saturation into the system stability analysis. These factors are not considered in the FRP-based system in our paper. Extending the current results to other systems, such as multi-agent systems [59], and investigating the impact of these factors on the system stability will be important directions for future research.
- Another possible research direction is to consider more complex cyber attack models, such as those with time-varying or uncertain attack probabilities. Some studies, such as [60], have modeled cyber attacks to better capture the randomness and uncertainty of attack occurrences. Although this paper assumes a fixed attack probability, incorporating uncertainty modeling to further evaluate the robustness of the control strategy under different attack conditions could better capture the dynamic attack patterns that may arise in real-world scenarios. This direction will be further explored in our future research.
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| MSES | Mean Square Exponential Stability |
| NCSs | Networked Control Systems |
| FRP | FlexRay Protocol |
| ROCAs | Randomly Occurring Cyber Attacks |
| FDI | False Data Injection |
| DoS | Denial-of-service |
| ADT | Average Dwell Time |
| RLMIs | Recursive Linear Matrix Inequalities |
| TODP | Try-once-discard Protocol |
| RRP | Round-robin Protocol |
| SCP | Stochastic Communication Protocol |
| CIA | Confidentiality, Integrity and Availability |
| NIT | Network Idle Time |
Appendix A. Controller Gain Kȷ(ς)(ς) for Two Modes
| ⋮ | ⋮ |
| ⋮ | ⋮ |
References
- Hu, J.; Zhang, H.; Liu, H.; Yu, X. A survey on sliding mode control for networked control systems. Int. J. Syst. Sci. 2021, 52, 1129–1147. [Google Scholar] [CrossRef]
- Zhang, X.M.; Han, Q.L.; Ge, X.; Ding, D.; Ding, L.; Yue, D.; Peng, C. Networked control systems: A survey of trends and techniques. IEEE/CAA J. Autom. Sin. 2020, 7, 1–17. [Google Scholar] [CrossRef]
- Fu, A.; McCann, J.A. Dynamic decentralized periodic event-triggered control for wireless cyber–physical systems. IEEE Trans. Control Syst. Technol. 2021, 29, 1783–1790. [Google Scholar] [CrossRef]
- Aslam, M.S.; Tiwari, P.; Pandey, H.M.; Band, S.S. Observer–based control for a new stochastic maximum power point tracking for photovoltaic systems with networked control system. IEEE Trans. Fuzzy Syst. 2023, 31, 1870–1884. [Google Scholar] [CrossRef]
- Zhang, D.; Han, Q.L.; Zhang, X.M. Network-based modeling and proportional–integral control for direct-drive-wheel systems in wireless network environments. IEEE Trans. Cybern. 2020, 50, 2462–2474. [Google Scholar] [CrossRef]
- Li, X.; Feng, S.; Hou, N.; Wang, R.; Li, H.; Gao, M.; Li, S. Surface microseismic data denoising based on sparse autoencoder and Kalman filter. Syst. Sci. Control Eng. 2022, 10, 616–628. [Google Scholar] [CrossRef]
- Wu, C.; Zhao, X.; Li, C.; Zhao, N. Controller synthesis of asynchronous periodic event-triggered networked control systems subject to quantization effects. IEEE Trans. Signal Inf. Process. Netw. 2022, 8, 907–919. [Google Scholar] [CrossRef]
- Zhang, X.M.; Han, Q.L.; Ge, X. A novel approach to H∞ performance analysis of discrete-time networked systems subject to network-induced delays and malicious packet dropouts. Automatica 2022, 136, 110010. [Google Scholar] [CrossRef]
- Li, C.; Zhao, X.; Chen, M.; Xing, W.; Zhao, N.; Zong, G. Dynamic periodic event-triggered control for networked control systems under packet dropouts. IEEE Trans. Autom. Sci. Eng. 2024, 21, 906–920. [Google Scholar] [CrossRef]
- Liu, J.; Wu, Z.G.; Yue, D.; Park, J.H. Stabilization of networked control systems with hybrid-driven mechanism and probabilistic cyber attacks. IEEE Trans. Syst. Man Cybern. Syst. 2021, 51, 943–953. [Google Scholar] [CrossRef]
- Li, Z.M.; Chang, X.H.; Xiong, J. Event-based fuzzy tracking control for nonlinear networked systems subject to dynamic quantization. IEEE Trans. Fuzzy Syst. 2023, 31, 941–954. [Google Scholar] [CrossRef]
- Liang, G.; Weller, S.R.; Zhao, J.; Luo, F.; Dong, Z.Y. The 2015 Ukraine blackout: Implications for false data injection attacks. IEEE Trans. Power Syst. 2017, 32, 3317–3318. [Google Scholar] [CrossRef]
- Pang, Z.H.; Fan, L.Z.; Guo, H.; Shi, Y.; Chai, R.; Sun, J.; Liu, G.P. Security of networked control systems subject to deception attacks: A survey. Int. J. Syst. Sci. 2022, 53, 3577–3598. [Google Scholar] [CrossRef]
- Li, H.; Yang, Q.; Zhan, X.; Wu, J.; Yan, H. Hybrid-triggered H∞ control for networked control systems with deception attacks. IEEE Trans. Circuits Syst. II Exp. Briefs 2023, 70, 3494–3498. [Google Scholar] [CrossRef]
- Mahmoud, M.S.; Hamdan, M.M.; Baroudi, U.A. Secure control of cyber physical systems subject to stochastic distributed DoS and deception attacks. Int. J. Syst. Sci. 2020, 51, 1653–1668. [Google Scholar] [CrossRef]
- Zhang, L.; Sun, S. Distributed H∞ fusion filtering for multi-sensor networked systems with DoS attacks and sensor saturations. Digit. Signal Process. 2023, 134, 103908. [Google Scholar] [CrossRef]
- Liu, J.; Ke, J.; Liu, J.; Xie, X.; Tian, E. Secure event-triggered control for IT-2 fuzzy networked systems with stochastic communication protocol and FDI attacks. IEEE Trans. Fuzzy Syst. 2024, 32, 1167–1180. [Google Scholar] [CrossRef]
- Pang, Z.H.; Fan, L.Z.; Dong, Z.; Han, Q.L.; Liu, G.P. False data injection attacks against partial sensor measurements of networked control systems. IEEE Trans. Circuits Syst. II Exp. Briefs 2022, 69, 149–153. [Google Scholar] [CrossRef]
- Yan, H.; Wang, J.; Zhang, H.; Shen, H.; Zhan, X. Event-based security control for stochastic networked systems subject to attacks. IEEE Trans. Syst. Man Cybern. Syst. 2020, 50, 4643–4654. [Google Scholar] [CrossRef]
- Liu, J.; Wang, S.; Hu, B.; Liu, J.; Xie, X.; Tian, E. Non-fragile observer-based security control for networked systems via event-triggered WTOD protocol. Int. J. Robust Nonlinear Control 2024, 34, 5852–5872. [Google Scholar] [CrossRef]
- Wang, F.; Liang, J.; Lam, J.; Yang, J.; Zhao, C. Robust filtering for 2-D systems with uncertain-variance noises and weighted try-once-discard protocols. IEEE Trans. Syst. Man Cybern. Syst. 2023, 53, 2914–2924. [Google Scholar] [CrossRef]
- Li, Y.; Song, F.; Liu, J.; Xie, X.; Tian, E.; Fei, S. Round Robin-based synchronization control for discrete-time complex networks with probabilistic coupling delay and deception attacks. IEEE Trans. Syst. Man Cybern Syst. 2024, 54, 4425–4436. [Google Scholar] [CrossRef]
- Shang, H.; Zong, G.; Qi, W. Security control for networked discrete-time semi-Markov jump systems with round-robin protocol. IEEE Trans. Circuits Syst. II Exp. Briefs 2022, 69, 2812–2816. [Google Scholar] [CrossRef]
- Liu, J.; Ke, J.; Liu, J.; Xie, X.; Tian, E. Stochastic communication protocol-based security control for discrete-time networked systems using state observer. IEEE Trans. Syst. Man Cybern Syst. 2024, 54, 5501–5512. [Google Scholar] [CrossRef]
- Cheng, J.; Zhang, Q.; Yan, H.; Zhang, D.; Park, J.H. Observer-based sliding mode control for fuzzy systems under stochastic communication protocol. IEEE Trans. Circuits Syst. II 2024, 71, 3860–3864. [Google Scholar] [CrossRef]
- Liu, S.; Wang, Z.; Wang, L.; Wei, G. Recursive set-membership state estimation over a FlexRay network. IEEE Trans. Syst. Man Cybern. Syst. 2022, 52, 3591–3601. [Google Scholar] [CrossRef]
- Wang, W.; Nešić, D.; Postoyan, R. Emulation-based stabilization of networked control systems implemented on FlexRay. Automatica 2015, 59, 73–83. [Google Scholar] [CrossRef]
- Tang, Y.; Zhang, D.; Ho, D.W.C.; Qian, F. Tracking control of a class of cyber-physical systems via a FlexRay communication network. IEEE Trans. Cybern. 2019, 49, 1186–1199. [Google Scholar] [CrossRef]
- Liu, S.; Wang, Z.; Wang, L.; Wei, G. Finite-horizon H∞ filtering via a high-rate network with the FlexRay protocol. IEEE Trans. Autom. Control 2023, 68, 3596–3603. [Google Scholar] [CrossRef]
- Wang, Y.; Wang, Z.; Zou, L.; Ma, L.; Dong, H. Ultimately bounded PID control for T–S fuzzy systems under FlexRay communication protocol. IEEE Trans. Fuzzy Syst. 2023, 31, 4308–4320. [Google Scholar] [CrossRef]
- Liu, J.; Wang, S.; Liu, J.; Xie, X.; Tian, E. FlexRay protocol-based event-triggered secure filtering for IT-2 fuzzy systems with fading measurements over high-rate communication networks: The finite-horizon case. IEEE Trans. Syst. Man Cybern Syst. 2024, 54, 6055–6067. [Google Scholar] [CrossRef]
- Wang, W.; Nešić, D.; Postoyan, R. Observer design for networked control systems with FlexRay. Automatica 2017, 82, 42–48. [Google Scholar] [CrossRef]
- Zhu, Y.; Tang, X.; Kang, D.; Zhang, L.; She, M.; Tan, C. Static output feedback H2/H∞ fault-tolerant control for nonlinear networked systems under hybrid cyber attacks and hybrid-triggered mechanisms. Int. J. Control Autom. Syst. 2025, 23, 1722–1735. [Google Scholar] [CrossRef]
- Hu, Y.; Kwon, O.M.; Lee, S.H. H∞ control for interval type-2 fuzzy singularly perturbed systems with multi-node round-robin protocol and packet dropouts. Fuzzy Sets Syst. 2025, 500, 109202. [Google Scholar] [CrossRef]
- Wu, Z.; Wang, Y.; Xiong, J.; Xie, M. Switching periodic event-triggered H∞ control for NCSs and its application to UAVs. IEEE Trans. Veh. Technol. 2024, 73, 5078–5088. [Google Scholar] [CrossRef]
- Zhi, Y.; Liu, X.; He, S.; Lin, W.; Chen, W. Adaptively event-triggered H∞ control for networked autonomous aerial vehicles control systems under deception attacks. IEEE Trans. Ind. Inform. 2025, 21, 3458–3465. [Google Scholar] [CrossRef]
- Yue, D.; Tian, E.; Han, Q.L. A delay system method for designing event-triggered controllers of networked control systems. IEEE Trans. Autom. Control 2013, 58, 475–481. [Google Scholar] [CrossRef]
- Tan, Y.; Liu, J.; Xie, X.; Tian, E.; Liu, J. Dynamic-memory event-triggered sliding-mode secure control for nonlinear semi-Markov jump systems with stochastic cyber attacks. IEEE Trans. Autom. Sci. Eng. 2025, 22, 202–214. [Google Scholar] [CrossRef]
- Zhong, Q.; Yang, J.; Shi, K.; Zhong, S. Design of observer-based discrete-type PID control for reconstructed jump model of interconnected power system under hybrid attacks. IEEE Trans. Smart Grid 2023, 14, 1896–1906. [Google Scholar] [CrossRef]
- Cheng, J.; Pang, H.; Yan, H.; Zhang, D. Protocol-based PID control of switched systems with DoS attacks. IEEE Trans. Inf. Forensics Secur. 2025, 20, 8059–8068. [Google Scholar] [CrossRef]
- Gao, X.; Deng, F.; Zeng, P.; Liu, X. Protocol-based stability analysis of stochastic hybrid systems under DoS attacks. IEEE Trans. Syst. Man Cybern. Syst. 2022, 52, 6348–6358. [Google Scholar] [CrossRef]
- Yang, H.; Peng, C.; Cao, Z. Attack-model-independent stabilization of networked control systems under a jump-like TOD scheduling protocol. Automatica 2023, 152, 110982. [Google Scholar] [CrossRef]
- Yu, T.; Xu, H.; He, S. GA-optimized co-design of jump-like FlexRay protocol and dynamic control for NCSs and its applications. IEEE Syst. J. 2025, 19, 670–681. [Google Scholar] [CrossRef]
- Hu, J.; Yang, S.; Caballero-Águila, R.; Dong, H.; Wu, B. Mixed static-dynamic protocol-based Tobit recursive filtering for stochastic nonlinear systems against random false data injection attacks. IEEE Trans. Signal Inf. Process. Netw. 2024, 10, 445–459. [Google Scholar] [CrossRef]
- Liu, S.; Wei, G.; Song, Y.; Liu, Y. Extended Kalman filtering for stochastic nonlinear systems with randomly occurring cyber attacks. Neurocomputing 2016, 207, 708–716. [Google Scholar] [CrossRef]
- Song, H.; Ding, D.; Dong, H.; Yi, X. Distributed filtering based on Cauchy-kernel-based maximum correntropy subject to randomly occurring cyber-attacks. Automatica 2022, 135, 110004. [Google Scholar] [CrossRef]
- Zhang, P.; Zhu, C.; Wang, Z.; Yang, B. Recursive set-membership filtering for two-dimensional shift-varying systems with FlexRay protocol and hybrid cyber attacks. Asian J. Control 2025, 27, 797–816. [Google Scholar] [CrossRef]
- Qu, F.; Tian, E.; Zhao, X. Chance-constrained H∞ state estimation for recursive neural networks under deception attacks and energy constraints: The finite-horizon case. IEEE Trans. Neural Netw. Learn. Syst. 2023, 34, 6492–6503. [Google Scholar] [CrossRef]
- Zhi, Y.L.; Liu, X.; Wang, Y.; Fan, Y. Network-based H∞ control for descriptor systems with time delays under a novel event-triggered strategy. IEEE Trans. Control Netw. Syst. 2025, 12, 943–953. [Google Scholar] [CrossRef]
- Xu, Y.; Mu, X.; Cheng, G. Event-triggered H∞ control for switched systems under multiple attacks. Int. J. Control Autom. Syst. 2023, 21, 1089–1097. [Google Scholar] [CrossRef]
- Qi, W.; Zhang, N.; Ahn, C.K.; Zong, G. Genetic-algorithm-based sliding-mode stabilization for networked switched systems with unreliable channels. IEEE Trans. Control Netw. Syst. 2024, 11, 1778–1789. [Google Scholar] [CrossRef]
- Hespanha, J.P.; Morse, A.S. Stability of switched systems with average dwell-time. In Proceedings of the 38th IEEE Conference on Decision and Control, Phoenix, AZ, USA, 7–10 December 1999. [Google Scholar]
- Deng, Y.; Zhang, H.; Xia, J. H∞ control with convergence rate constraint for time-varying delay switched systems. IEEE Trans. Syst. Man Cybern. Syst. 2023, 53, 7354–7363. [Google Scholar] [CrossRef]
- Zhang, D.; Xu, Z.; Karimi, H.R.; Wang, Q. Distributed filtering for switched linear systems with sensor networks in presence of packet dropouts and quantization. IEEE Trans. Circuits Syst. I Reg. Pap. 2017, 64, 2783–2796. [Google Scholar] [CrossRef]
- Daafouz, J.; Riedinger, P.; Iung, C. Stability analysis and control synthesis for switched systems: A switched Lyapunov function approach. IEEE Trans. Autom. Control 2002, 47, 1883–1887. [Google Scholar] [CrossRef]
- Huang, K.; Pan, F. Finite horizon H-infinity control of nonlinear time-varying systems under WTOD protocol. IEEE Access 2022, 10, 20400–20406. [Google Scholar] [CrossRef]
- Wang, Z.; He, W.; Sun, J.; Wang, G.; Chen, J. Event-triggered control of switched nonlinear time-delay systems with asynchronous switching. IEEE Trans. Cybern. 2024, 54, 4348–4358. [Google Scholar] [CrossRef]
- Huang, X.; Xing, M.; Mo, H.; Hu, S.; Luo, H. Stabilization of uncertain networked control systems with actuator saturation and probabilistic cyberattacks. Asian J. Control 2023, 25, 1407–1419. [Google Scholar] [CrossRef]
- Liu, J.; Yin, T.; Yue, D.; Karimi, H.R.; Cao, J. Event-based secure leader-following consensus control for multiagent systems with multiple cyber attacks. IEEE Trans. Cybern. 2021, 51, 162–173. [Google Scholar] [CrossRef]
- Ma, Y.; Li, Z. Neural network-based secure event-triggered control of uncertain industrial cyber-physical systems against deception attacks. Inf. Sci. 2023, 633, 504–516. [Google Scholar] [CrossRef]


| Symbol | Implication |
|---|---|
| time instant | |
| a switching signal between the static segment and the dynamic segment | |
| the sensor node granted network access at time instnat under RRP | |
| the sensor node granted network access at time instnat under TODP | |
| a Bernoulli variable that denotes whether a DoS attack occurs | |
| a Bernoulli variable that denotes whether a FDI attack occurs | |
| an auxiliary matrix in RRP | |
| an auxiliary matrix in TODP | |
| a mode-dependent variable with respect to auxiliary matrices | |
| a mode-dependent variable with respect to identify matrices | |
| a time-varying matrix with appropriate dimensions in the corresponding subsystem |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Shen, Y.; Hu, M. H∞ Performance of FlexRay Protocol-Based Networked Control Systems Subjected to Randomly Occurring Cyber Attacks. Mathematics 2025, 13, 3515. https://doi.org/10.3390/math13213515
Shen Y, Hu M. H∞ Performance of FlexRay Protocol-Based Networked Control Systems Subjected to Randomly Occurring Cyber Attacks. Mathematics. 2025; 13(21):3515. https://doi.org/10.3390/math13213515
Chicago/Turabian StyleShen, Yuwen, and Manfeng Hu. 2025. "H∞ Performance of FlexRay Protocol-Based Networked Control Systems Subjected to Randomly Occurring Cyber Attacks" Mathematics 13, no. 21: 3515. https://doi.org/10.3390/math13213515
APA StyleShen, Y., & Hu, M. (2025). H∞ Performance of FlexRay Protocol-Based Networked Control Systems Subjected to Randomly Occurring Cyber Attacks. Mathematics, 13(21), 3515. https://doi.org/10.3390/math13213515






