Abstract
This paper investigates the mean square exponential stability (MSES) and performance analysis of discrete networked control systems (NCSs) based on the FlexRay protocol (FRP) when confronted with randomly occurring cyber attacks (ROCAs). In order to deal with network congestion due to the limited bandwidth, the FRP is used to schedule the information exchange. Besides, a comprehensive attack model is built by simultaneously considering false data injection (FDI) attacks and denial-of-service (DoS) attacks. Then, a mode-dependent output feedback controller is designed on this basis. Furthermore, sufficient conditions for the MSES and performance of the considered system are derived under the mode-dependent Lyapunov function and average dwell time (ADT) constraints. Subsequently, the controller gains of two modes are determined by solving the recursive linear matrix inequalities (RLMIs) and the FRP-based MSES algorithm is also presented. The simulation verifies that the proposed algorithm maintains the system stability with good robustness and performance under ROCAs.
Keywords:
H∞ performance; networked control systems (NCSs); randomly occurring cyber attacks (ROCAs); FlexRay protocol (FRP); mean square exponential stability (MSES) MSC:
93B36; 93B70; 93C55; 93D23
1. Introduction
With the advancements in industrial automation and communication control technology, NCSs have gained wide adoption in engineering practice, owing to their advantages such as real-time performance, distributed architecture, scalability, ease of maintenance, and relatively low installation costs. These systems can flexibly adapt to increasingly complex and diverse application scenarios [1,2], achieving remarkable results across a range of fields, including sensor networks [3], power grids [4], autonomous vehicles [5] and geological exploration [6]. NCSs rely on shared communication networks to interconnect their components and enable the exchange of information. However, there are a series of challenges introduced in the network transmission, such as packet dropouts, cyber attacks, signal quantization, and other network-induced phenomena, which puts higher demands on the system stability and thus arouses a wide range of academic concerns about the stability of NCSs [7,8,9,10,11].
Currently, the automotive industry is moving towards autonomous driving and intelligent connected vehicles. Nevertheless, the openness and interconnectivity of NCSs also heighten the risk of cyber attacks, potentially compromising system performance and even disrupting system stability. For example, in 2015, Ukraine experienced large-scale cyber attacks that caused widespread power outages in several regions, affecting thousands of users [12]. While cyber attacks must be condemned, it is also of crucial importance to investigate the stability of NCSs that are exposed to cyber attacks. In recent decades, the modeling and in-depth study of cyber attacks have consistently been a research hotspot, with numerous research results on cyber attack issues being reported [13,14,15,16,17,18]. Cyber attacks can affect one of the CIA (Confidentiality, Integrity and Availability). Specifically, DoS attacks affect availability by flooding the target with a large volume of data, which depletes system resources or causes network congestion, ultimately rendering the system unable to provide normal services [15,16]. FDI attacks compromise data integrity through manipulation of its contents, thereby affecting system decision-making and operation [17,18]. Although data breaches can also impact confidentiality, this study primarily concentrates on the system stability under DoS and FDI attacks. Moreover, in practical network environments, the attacks typically occur randomly. Inspired by the attack model presented in [19,20], Bernoulli distributions are used to model the FDI attacks as well as the DoS attacks.
In addition to cyber security issues, network congestion has emerged as another significant challenge which urgently requires resolution. Network congestion and other network-induced phenomena become inevitable owing to the limited network bandwidth when a substantial quantity of data is accessed simultaneously on the network, posing serious challenges to the system stability. To effectively tackle network congestion problem and alleviate network burden, selecting an appropriate communication protocol has become even more crucial. In the existing literature, a variety of communication protocols have been extensively studied, including the try-once-discard protocol (TODP) [20,21], round-robin protocol (RRP) [22,23], and stochastic communication protocol (SCP) [24,25].
It is worth mentioning that FRP has received widespread attention due to its reliability and flexibility of data transmission in public network channels [26]. The FRP is a hybrid protocol that sends data packets during a predetermined communication cycle, which consists of regularly repeating static and dynamic segments [27]. Compared to other protocols, the FRP combines the advantages of time-triggered protocols (such as RRP) and event-triggered protocols (such as TODP), achieving reliable transmission of periodic data while dynamically adjusting data transmission based on event priority. Especially in the context of cyber attacks, the scheduling strategy may help improve the management of data transmission. Furthermore, the FRP has been proven to have faster, more flexible, and more reliable characteristics [28] and has achieved some preliminary results [26,29,30,31]. However, it is noteworthy that research on the FRP in the existing literature is limited, with the majority of studies focusing on continuous systems [27,28,32]. Despite the aforementioned research, the stability of discrete NCSs with the FRP has not been given enough attention, let alone the study of the effects of ROCAs on the system stability, which provides inspiration for our research.
In recent decades, common control methods primarily include control [33,34,35,36], event-triggered control [37,38], fuzzy control [39,40], and so on. For example, in [33], a static output feedback / fault-tolerant control strategy was proposed for nonlinear NCSs to address hybrid cyber attacks and hybrid-triggered mechanisms. However, these control methods do not fully consider the transmission characteristics and the real-time requirements of FRP, particularly in time-varying systems, and thus cannot be directly applicable to the model discussed in this paper. In contrast, the mode-dependent output feedback controller can flexibly adjust the controller gain based on the system’s current mode, ensuring good robustness in different modes and thus better aligning with the objective of this paper.
Upon reviewing the existing literature, the following significant observations can be drawn: (1) most studies primarily focus on the stability analysis of systems under a single communication protocol when subjected to cyber attacks [41,42], yet it does not delve into the system stability when two protocols, RRP and TODP, are involved in a communication cycle, especially when switching between the static and dynamic segments; and (2) most of the literature on FRP considers only a single fixed attack mode. Compared to a single fixed attack mode [43,44], ROCAs exhibit uncertainty and diversity, and their attack behavior is characterized by randomness and unpredictability in time, which can easily lead to the failure of traditional protection strategies and cause greater impact on the system stability and security [45,46]. Although the literature [47] studies the combination of FRP and hybrid cyber attacks, which primarily focuses on the system filtering problem, this paper specifically addresses the system stability issue, considering a distinct type of system and employing a different modeling approach for DoS attacks. Therefore, the conclusions of existing research are not applicable to the research question of this article. To address this, a more comprehensive and in-depth approach is urgently needed to investigate the stability of NCSs under the simultaneous consideration of the FRP and ROCAs.
In light of this, it is clear that we need to study in depth the transmission characteristics and components of the FRP within a communication cycle, with a particular focus on the stability when switching between static and dynamic segments. Specifically, we need to evaluate the system stability separately in the RRP and TODP modes, especially at the switching points. Therefore, when designing the output feedback controller, we must select an appropriate one based on the current system mode. To this end, a mode-dependent output feedback controller is proposed to make the system achieve MSES and satisfy the performance. Compared with existing methods, the proposed controller design approach is less conservative and more flexible in dealing with system changes, making it of great practical significance.
Inspired by the abovementioned discussions, this article endeavors to present a FRP-based MSES algorithm for NCSs subjected to ROCAs. Below, we discuss the primary challenges encountered in this paper during the study of achieving MSES for the system.
- How to construct a suitable switched system model to take full account for the transmission characteristics of the FRP and the impact of ROCAs?
- How to make sure the system is stable when switching between the static and dynamic segments, especially at the switching point?
- How to design a practical algorithm to calculate the controller gains?
To confront the challenges outlined above, the main contributions of the study are given as follows.
- The closed-loop switched system with a mode-dependent output feedback controller is investigated for the first time within the framework of stability analysis, where the signal is transmitted by the FRP and the system is subjected to ROCAs.
- Sufficient conditions for the MSES and performance of the switched system are developed by utilizing a mode-dependent Lyapunov function in conjunction with the ADT approach. These conditions are employed to determine a set of matrices instead of the conventional yet conservative matrix . This approach serves to diminish conservatism while simultaneously ensuring the system stability when switching between the static and dynamic segments.
- A FRP-based MSES algorithm, which is practical and feasible, is presented to determine the corresponding controller gain of each mode.
The subsequent sections of this paper are organized in the following manner. In Section 2, we construct a mode-dependent output feedback controller and a system model considering the characteristics of the FRP and the effects of ROCAs, and clearly state the primary objective of this paper. Section 3 derives in detail the sufficient conditions for the system stability and performance under ROCAs. Simultaneously, the specific expression for the controller gains are derived computationally. Section 4 demonstrates the effectiveness of the proposed theory and methodology by means of a specific simulation case. Section 5 highlights several possible directions for future research and extensions of this work. Finally, in Section 6, the study is summarized and conclusions are drawn.
Notations denotes the n-dimensional identify matrix. means the mathematical expectation of the random variable . represents the Kronecker delta function, such that if a is equal to 0, and for all other values of a. The notations of key variables and subscripts are summarized in Table 1.

Table 1.
The notations of key variables and subscripts.
2. Problem Formulation
2.1. System Model
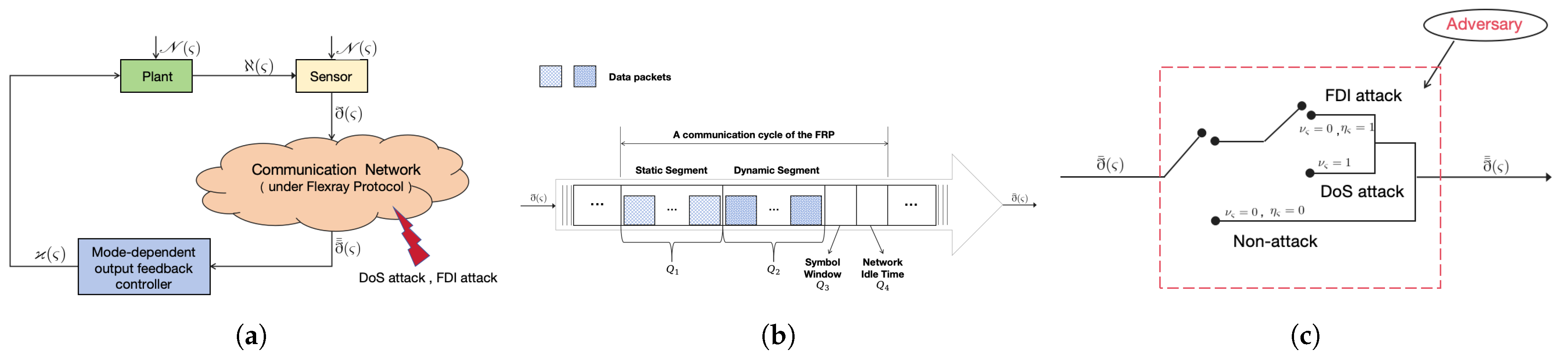
As depicted in Figure 1a, the plant under consideration is as follows:
where is the system state; is the measurement output measured by sensors; is the control input; is the control output; represents the exogenous disturbance satisfying . and are time-varying matrices with appropriate dimensions.

Figure 1.
Main blocks with the FRP and ROCAs.(a) Framework of NCSs with communication network. (b) Schematic diagram of a communication cycle of the FRP. (c) FRP-based communication network under ROCAs.
2.2. FlexRay Protocol
In order to cope with network congestion, this paper adopts the FRP to schedule the data transmission between the sensor and the controller (as shown in Figure 1b, and at each time instant , as used in [26], only one sensor is allowed to transmit the signal. According to [26], transmission time is assumed to have negligible impact, and thus, it is also excluded from the analysis in our paper.
The communication cycle of the FRP with time length , illustrated in Figure 1b, consists of a static segment dedicated to time-triggered scheduling, a dynamic segment dedicated to event-triggered scheduling, a symbol window, and a network idle time (NIT). The corresponding time lengths are set as and , respectively. The lengths of the symbol window and the NIT are considered negligible relative to and . Without loss of generality, they are neglected, i.e., and assume that , in which case . Further details can be found in [29].
It should be noted that owing to the different real-time requirements of each component in the measurement signal, components with high real-time requirements are scheduled with the RRP. Specifically speaking, it is assumed that the first l components of the measurement signal (i.e., ) are scheduled by the RRP, while the rest of the components (i.e., ) are scheduled by the TODP. In the light of the features of the FRP, the RRP is active during the static segments, while the TODP is executed during the dynamic segments.
For ease of expression, we denote
In addition, time intervals of the static and dynamic segments are and , separately. For the sake of simplicity, the static segment interval is abbreviated as , and the dynamic segment interval as . The following will introduce the node selection rules in detail.
- (1)
- :where represents the sensor node granted network access at time . For , through the zero-order holder (ZOH), there holds
- (2)
- :where represents the sensor node granted network access at time and are weighted matrices, which are known positive definite matrices. Let by virtue of the ZOH, can be represented by
Remark 1.
At time instant ς, for RRP (TODP), only the component of is updated, and the rest of the components are updated through the ZOH strategy, called segment-dependent ZOH strategy, which was firstly proposed in the literature [30].
Assumption 1.
The system starts from with and (i.e., zero initial condition), which is in the static segment, and the corresponding sensor node is .
Remark 2.
To ease the process of the following analysis and derivation, suppose that the initial state equals 0. Accordingly, the output , which corresponds to , is also assumed to be zero. In particular, this assumption does not affect the universality of the conclusions, as should be mentioned, and the results of the relevant analysis are equally valid for any initial condition [48,49].
To further enhance resource utilization efficiency and ensure data transmission quality, a switching signal is introduced to enable a smooth transition between the static and dynamic segments, denoted as :
2.3. Randomly Occurring Cyber Attacks
Taking the DoS attack and FDI attack into account on signal transmission, refer to Figure 1c, the actual measurement output is further written as:
where represents the false data injected by the attackers, and are random Bernoulli distributed variables taking values of 0 or 1 with .
Remark 3.
As in the literature [45], suppose that Bernoulli variables and are uncorrelated with and that and are given known parameters.
Next, we will analyze the attack patterns of ROCAs and the corresponding system measurement output. It is noted that model (9) contains three special cases. Specifically, when and the controller receives a normal signal that is not under attack; when the system suffers a DoS attack, the measurement signals cannot be updated, the last moment of transmission is used as the actual measurement output signal; when and , the system suffers a FDI attack, the actual measurement output is .
Assumption 2.
Given a real constant matrix , the following constraint should be satisfied for the occurrence of a FDI attack:
Generally, attackers limit the energy of FDI attacks in order to enhance their stealthiness. Additionally, due to the physical constraints of NCSs and limited network bandwidth, the energy of FDI attacks is also constrained. Hence, it is reasonable to make such an assumption.
2.4. Controller Design
For system (1), we design the following controller:
where represents the actual measurement output after the signal has been subjected to ROCAs during transmission and is the controller gain to be determined. Then, substituting Equations (10) and (12) into (1) gives the closed-loop system state equation:
2.5. System Augmentation
2.6. Switched System
In order to deal with the two modes of the FRP, the switched system theory is used for the study. Based on (8), the piecewise function is a switching rule for switching between the static segment and the dynamic segment in each communication cycle.
Without loss of generality, to simplify the model, one may suppose that there exists an infinite sequence for , such that when , it implies that the measurement signal begins to be transmitted by the TODP. Specifically speaking, the measurement signal is transmitted by the RRP during , while the TODP transmits it during .
In practical NCSs, especially when information transmission depends on the network, delay and data transmission problems may lead to asynchrony between subsystems and controllers, making the system stability analysis more difficult. For the sake of simplifying the analysis, an assumption is made as follows.
Assumption 3
([50]). There is no asynchrony in the switching between a subsystem and its corresponding controller.
To facilitate the presentation and uniformity of the system model and simplify the subsequent analysis, introduce the variables and , where
Inspired by the design of controller gains in [50], the controller gain in this paper is designed as follow:
Based on (12) and (15), the controller becomes
where is the corresponding controller gain of each mode.
Remark 4.
The corresponding closed-loop switched system, based on the controller (16), is represented as:
where
Since (17) contains stochastic parameters, for the convenience of the subsequent analysis, we distinguish between the stochastic and deterministic parameters. To represent this, we define
Before continuing, the following definitions are given in place to assist in the analysis of the paper.
Definition 1
([51]). The closed-loop switched system (18) is MSES if there exist constants and such that for , with and , the inequality is satisfied.
Definition 2
([52]). For switching signal and , let represents the total number of switches of in the interval , if the condition is satisfied for and , we refer to as the ADT, and as the chatter bound.
Remark 5.
To prevent the system instability issues caused by the frequent switching between different subsystems, we introduce the ADT to improve the system stability and performance. To simplify, we choose , as is often the case [53,54].
This paper is dedicated to the construction of a mode-dependent output feedback controller, which aims to satisfy the following requirements (R1) and (R2) simultaneously for the system (18):
(R1) MSES when ;
(R2) Given the scalar and , under Assumption 1, the control output of the system satisfies:
3. Main Results
In the following, considering the simultaneous presence of the FRP and ROCAs, the first two theorems establish analytical frameworks for the MSES with performance index of the system (18), respectively. Then, we give a concrete expression for the design of desired gain for the mode-dependent output feedback controller (16) in the last theorem. The first significant result is outlined below.
Theorem 1.
Let decay rate parameter be given. For the system (18) with the FRP and ROCAs, if there exist positive definite matrices and real-valued matrices satisfying the inequality
where
the system (18) is MSES under the assumption of for any switching signal that satisfies the following ADT constraint
where satisfies
Proof.
Since , there are only two subsystems in the closed-loop switched system (18). To facilitate a more organized stability analysis, we construct the subsequent Lyapunov function:
Case 1: If ,
Noting that , and .
In the light of Assumption 2, there holds
where
Through the application of the Schur complement lemma, it becomes apparent that holds if (20) is true, which implies
On the assumption that the states remain unchanged when switching the system mode. Then, according to (26), one can derive that
Case 2: If , by employing the similar analytical approach, there holds
Then, according to (28), there holds
Thus, it follows from for and for , we have
Furthermore, let , . It is obvious that
Theorem 2.
Proof.
For any , define
We are now considering conducting the performance analysis of the system (18).
Case 1: If ,
where
It can be easily derived that if the condition (33) holds, which implies
Consequently,
With Assumption 1 and in consideration of , we have
that is,
On the other hand, since , it is evident that
Accumulating both sides of (43) from to and changing the order of summation leads to
Case 2: If , similarly, the above inequality can also be derived, from which it follows that the system (18) has the performance index under the framework. □
From the results of the stability analysis above, the next step is the determination of controller gain for the mode-dependent controller (16).
Theorem 3.
Let scalars and be given. For the system (18) with the FRP and ROCAs, if there exist positive definite matrices and real-valued matrices satisfying the inequalities (21), (22) and
where
the system (18) is MSES and the performance condition (19) holds for .
Then, can be calculated by the following specific expression
Proof.
The following algorithm (Algorithm 1) is developed to show the feasibility and reasonableness of Theorems 1–3.
| Algorithm 1 MSES Algorithm. |
|
Remark 6.
The linear matrix inequality (45) can be solved using the YALMIP toolbox in MATLAB R2023b, with Mosek 10.2 employed as the solver. Due to the value of , there are two modes in the system. A common approach in dealing with stability issues is to build a quadratic Lyapunov function and to find a common time-varying Lyapunov matrix. Specifically, in this case, for the Lyapunov function designed in (23), the corresponding matrix has to satisfy . However, this approach is usually more conservative and often faces greater difficulties in solving the matrix. In order to obtain less conservative results, on the basis of the approach in [55], a mode-dependent Lyapunov function is designed, with a Lyapunov matrix existing for each mode. In contrast to [56], the Lyapunov function proposed in this paper provides a more accurate characterization of the system behavior under different modes of the FRP, thereby enlarging the feasible region of the LMIs and effectively reducing the conservatism of the existing approach.
Remark 7.
In Theorem 3, the number of decision variables in the LMI condition is . Therefore, it is not difficult to observe that the computational complexity of MSES Algorithm increases with both the state dimension and sensor nodes. Furthermore, increasing the number of sensor nodes can distribute the computational load, but also introduces greater data processing demands. Additionally, optimizing real-time data transmission speed will be crucial to ensure efficient data handling. These aspects will be further explored in the future work to enhance the algorithm’s performance in practical applications. Moreover, the algorithm may be computationally demanding for real-time implementation, especially in high-dimensional systems. Improving its computational efficiency to enhance real-time applicability will be considered in future research.
4. Simulation Results
Now, we use a numerical simulation to demonstrate the effectiveness of the FRP-based MSES algorithm in the context of our research.
The FDI attack function is given as follows:
On the basis of Assumption 2, the matrix can be obtained. The exogenous disturbance is
We set and . It is assumed that the RRP schedules the first three components of and the TODP schedules the last two components. Correspondingly, the weighted matrices are chosen as .
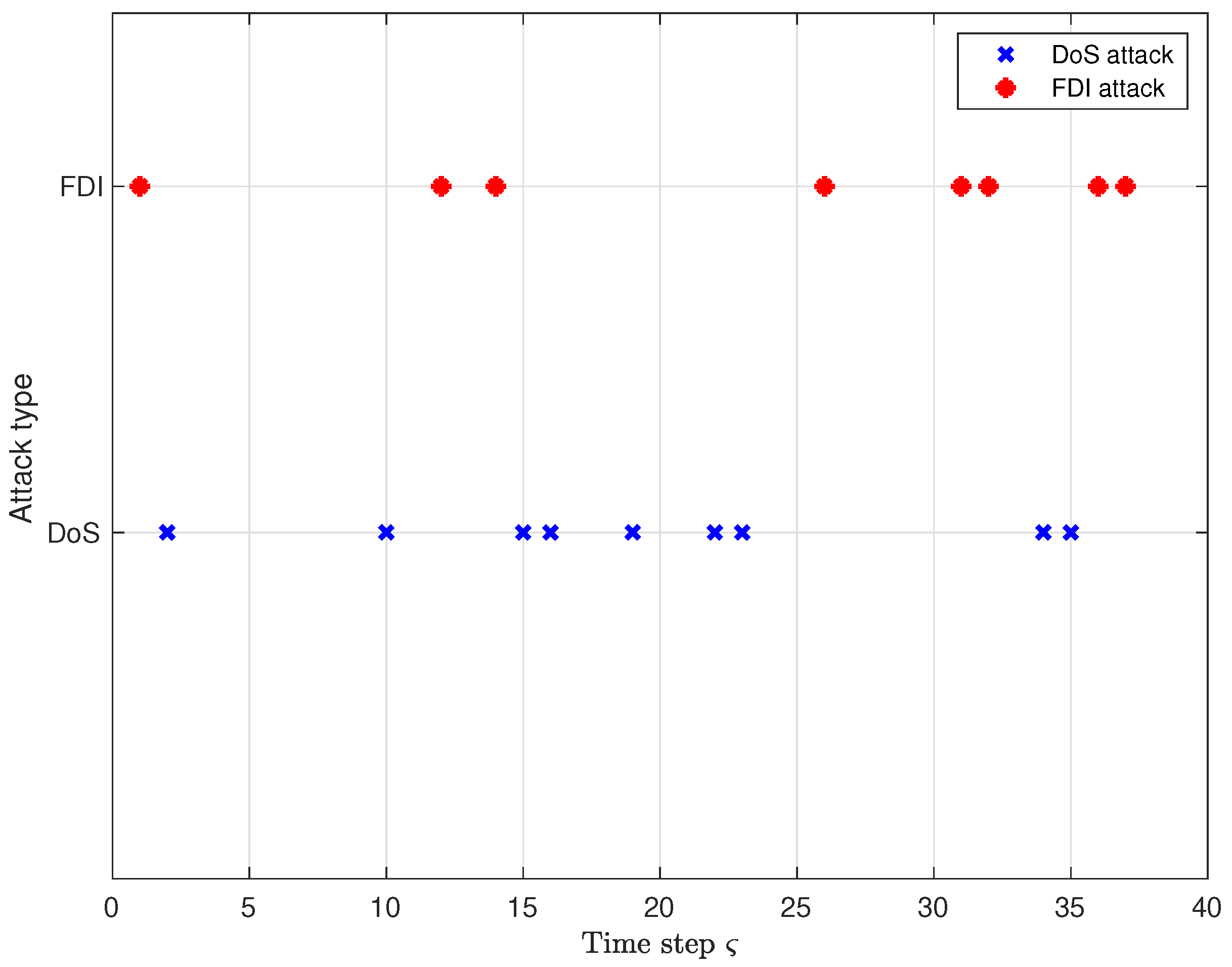
The time instants at which the DoS attack and the FDI attack take place are given in Figure 2, and they occur with probabilities and , respectively.
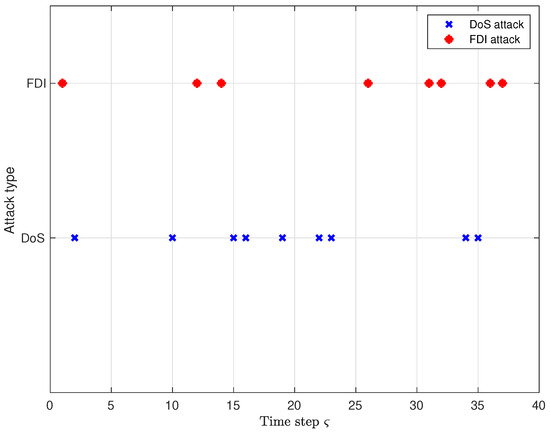
Figure 2.
The occurrence time of the DoS attack and FDI attack.
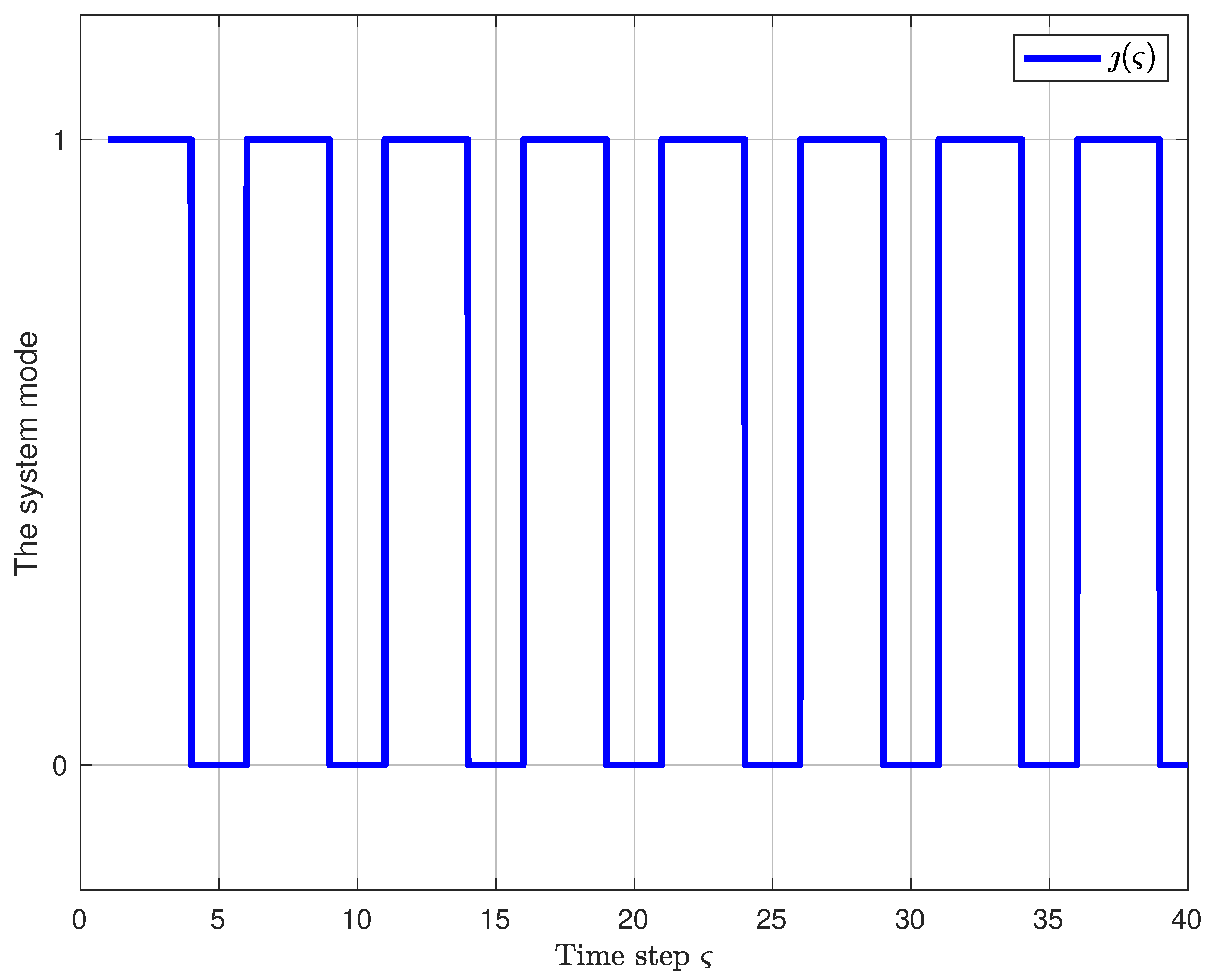
The initial values are and . Choose , . On the basis of Theorem 2, . Therefore, there is . Meanwhile, the switching signal is presented in Figure 3. Furthermore, the controller gains for two modes can be obtained and are presented in Table A1 and Table A2 in Appendix A, where the controller gain for the system in the RRP mode is given in Table A1 and the controller gain for the system in the TODP mode is given in Table A2.

Figure 3.
Switching signal with the ADT of 2.5 (“1” represents the RRP mode and “0” represents the TODP mode).
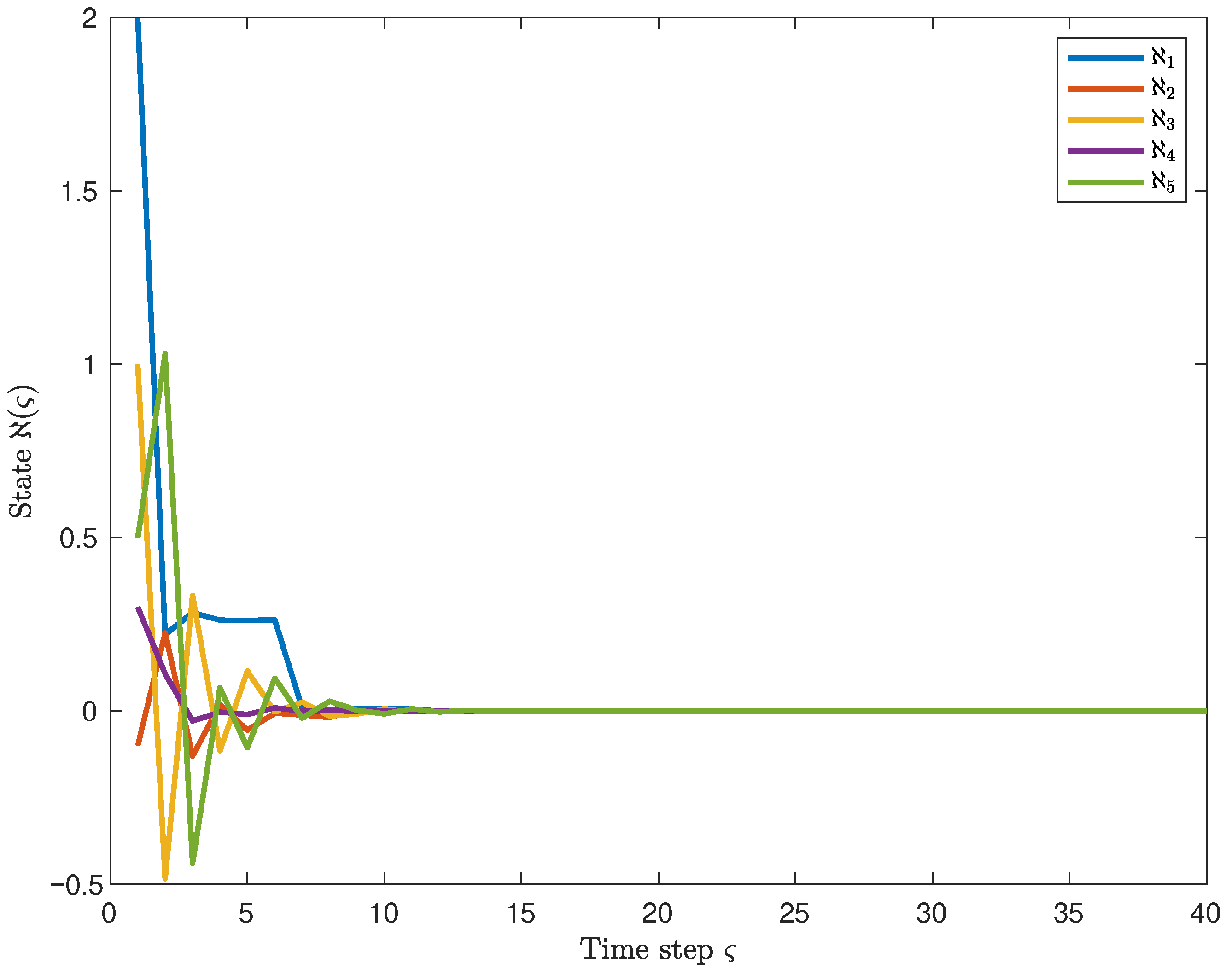
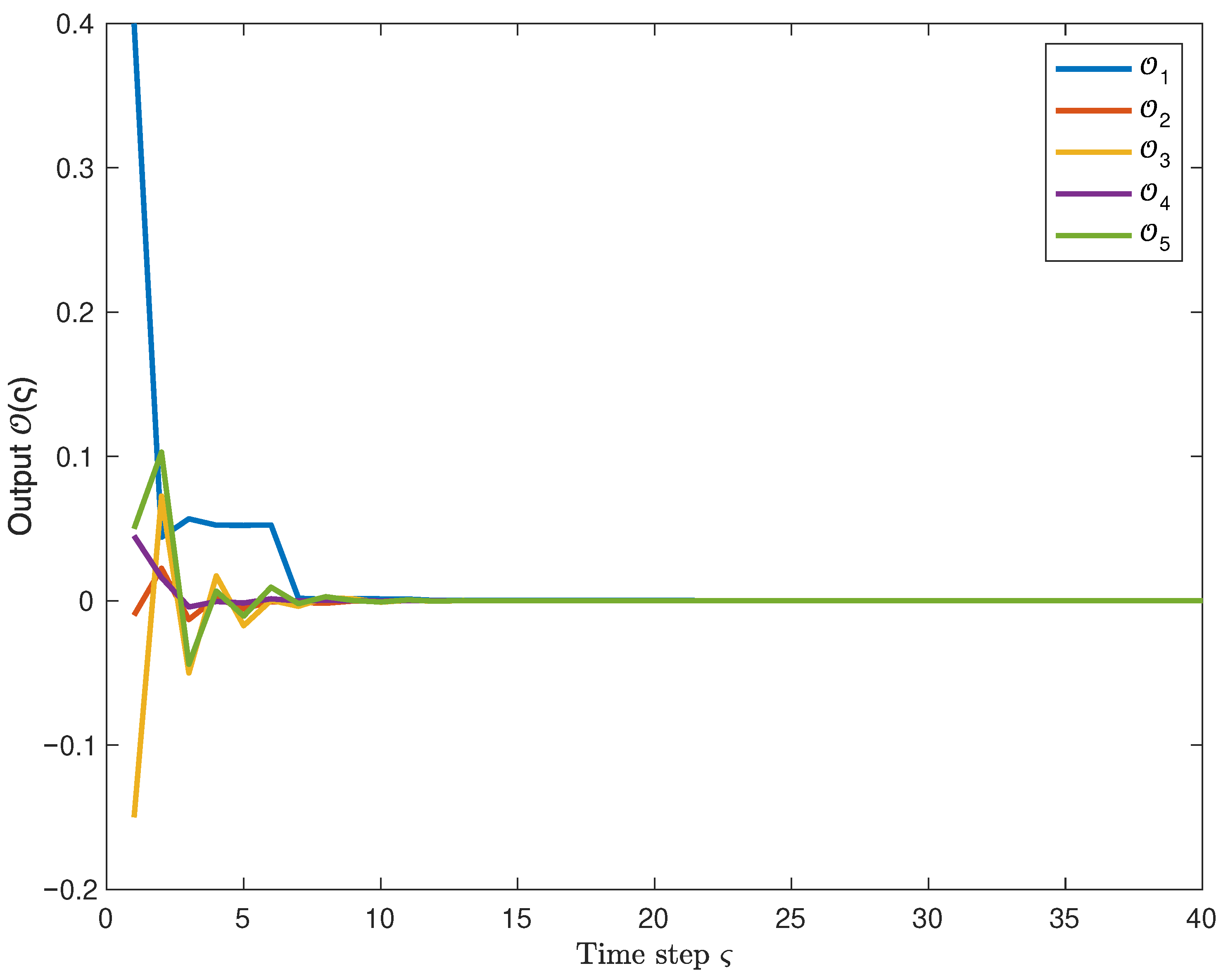
Moreover, Figure 4 shows the state response curves of the system, and one can observe that the state trajectories converge to 0, thereby demonstrating the MSES of the system. Furthermore, the corresponding control output curve is presented in Figure 5. In conjunction with the above, it is apparent that the system output satisfies the given performance index bound. It indicates that the system maintains good robustness under the influence of ROCAs.
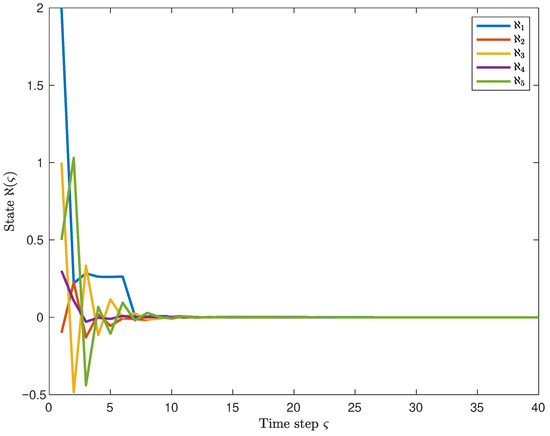
Figure 4.
Response curve of system state with exogenous disturbance (as shown in (47)).
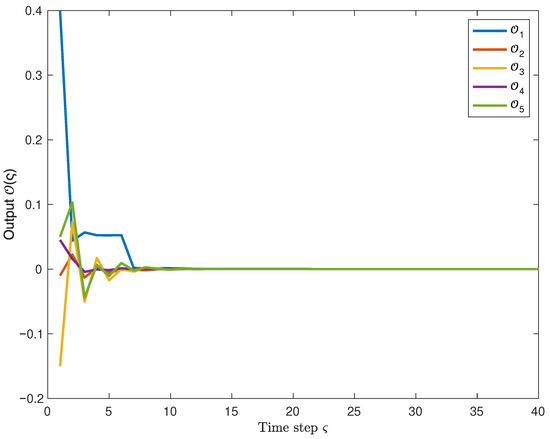
Figure 5.
Response curve of controller output with exogenous disturbance (as shown in (47)).
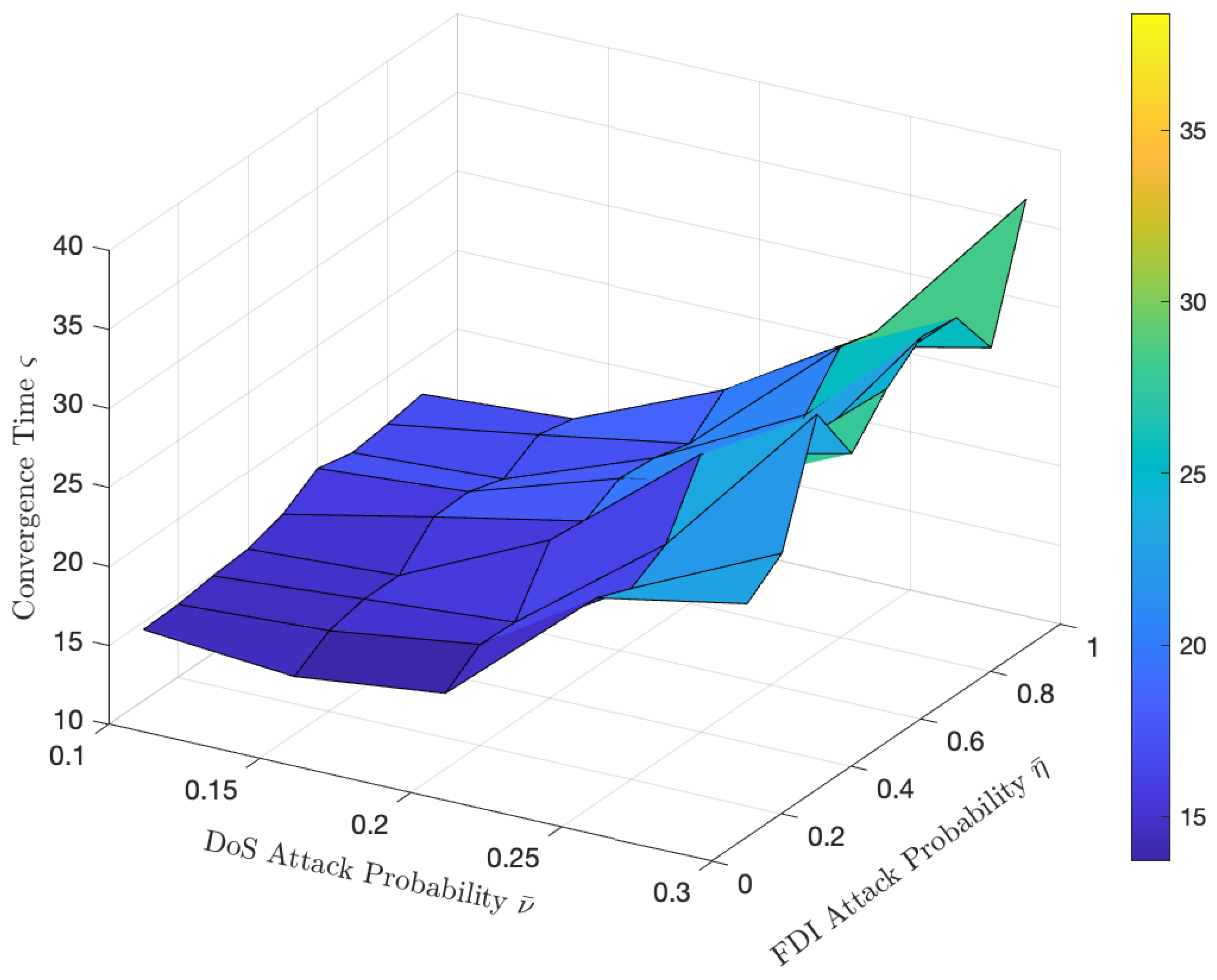
The sensitivity analysis of the probability of DoS and FDI attacks is conducted in Figure 6, of which the convergence time serves as a key performance metric reflecting the stability margin of the system. In the simulation, the convergence time of the system is taken as the average of the experimental results, which is obtained by performing ten trials and calculating the mean. As observed in Figure 6, the system exhibits a significantly higher sensitivity to DoS attacks than to FDI attacks. The convergence time remains short and relatively constant for DoS probabilities between 0 and 0.2, indicating a high stability margin and strong robustness within this range. A critical tipping point is identified at a DoS probability of approximately 0.2. Beyond this threshold, the stability margin decreases rapidly, resulting in a sharp increase in the convergence time. This highlights the critical importance of keeping the DoS attack probability below this value to maintain system resilience.

Figure 6.
Sensitivity analysis.
5. Discussion
Based on the above analysis and results, several possible directions for future research are highlighted and discussed below:
- Due to the possible switching signal detection delays, which may lead to controller mismatches within each switching interval [57], a natural extension of this work is to consider asynchronous switching between subsystems and their corresponding controllers. Such asynchrony commonly arises in practical NCSs, and studying its impact on stability and performance will be an interesting topic for our future research.
- In addition, other network-induced phenomena (such as time delay) and actuator saturation are typical phenomena in NCSs. Several recent studies [49,58] have incorporated performance, time delays, and actuator saturation into the system stability analysis. These factors are not considered in the FRP-based system in our paper. Extending the current results to other systems, such as multi-agent systems [59], and investigating the impact of these factors on the system stability will be important directions for future research.
- Another possible research direction is to consider more complex cyber attack models, such as those with time-varying or uncertain attack probabilities. Some studies, such as [60], have modeled cyber attacks to better capture the randomness and uncertainty of attack occurrences. Although this paper assumes a fixed attack probability, incorporating uncertainty modeling to further evaluate the robustness of the control strategy under different attack conditions could better capture the dynamic attack patterns that may arise in real-world scenarios. This direction will be further explored in our future research.
6. Conclusions
The problem of the stability and performance for the FRP-based NCSs subjected to ROCAs is investigated in this paper. Additionally, a novel mathematical model of the system with the FRP is constructed, taking into account the effects of ROCAs. Moreover, a mode-dependent output feedback controller is designed, as well as sufficient conditions for achieving MSES of the system and satisfying the performance are obtained building on the Lyapunov stability theory, and an algorithm for solving the mode-dependent controller gains is proposed. In the end, a simulation example shows the effectiveness and practicality of the algorithm in addressing the challenges of ROCAs. The system demonstrates good robustness and performance in the presence of ROCAs. Future research directions include: (1) extending our findings from synchronous switching to asynchronous switching; (2) generalizing the proposed algorithm for use in other systems and considering other network-induced phenomena within the framework of stability analysis; (3) adopting more complex modeling frameworks to better characterize the dynamics of cyber attacks.
Author Contributions
Conceptualization, Y.S.; methodology, Y.S.; software, Y.S.; formal analysis, Y.S. and M.H.; investigation, Y.S. and M.H.; writing—original draft, Y.S.; writing—review and editing, Y.S. and M.H. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
The original contributions presented in this study are included in the article. Further inquiries can be directed to the corresponding author.
Conflicts of Interest
The authors declare no conflicts of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| MSES | Mean Square Exponential Stability |
| NCSs | Networked Control Systems |
| FRP | FlexRay Protocol |
| ROCAs | Randomly Occurring Cyber Attacks |
| FDI | False Data Injection |
| DoS | Denial-of-service |
| ADT | Average Dwell Time |
| RLMIs | Recursive Linear Matrix Inequalities |
| TODP | Try-once-discard Protocol |
| RRP | Round-robin Protocol |
| SCP | Stochastic Communication Protocol |
| CIA | Confidentiality, Integrity and Availability |
| NIT | Network Idle Time |
Appendix A. Controller Gain Kȷ(ς)(ς) for Two Modes

Table A1.
Controller gain with .
Table A1.
Controller gain with .
| ⋮ | ⋮ |

Table A2.
Controller gain with .
Table A2.
Controller gain with .
| ⋮ | ⋮ |
References
- Hu, J.; Zhang, H.; Liu, H.; Yu, X. A survey on sliding mode control for networked control systems. Int. J. Syst. Sci. 2021, 52, 1129–1147. [Google Scholar] [CrossRef]
- Zhang, X.M.; Han, Q.L.; Ge, X.; Ding, D.; Ding, L.; Yue, D.; Peng, C. Networked control systems: A survey of trends and techniques. IEEE/CAA J. Autom. Sin. 2020, 7, 1–17. [Google Scholar] [CrossRef]
- Fu, A.; McCann, J.A. Dynamic decentralized periodic event-triggered control for wireless cyber–physical systems. IEEE Trans. Control Syst. Technol. 2021, 29, 1783–1790. [Google Scholar] [CrossRef]
- Aslam, M.S.; Tiwari, P.; Pandey, H.M.; Band, S.S. Observer–based control for a new stochastic maximum power point tracking for photovoltaic systems with networked control system. IEEE Trans. Fuzzy Syst. 2023, 31, 1870–1884. [Google Scholar] [CrossRef]
- Zhang, D.; Han, Q.L.; Zhang, X.M. Network-based modeling and proportional–integral control for direct-drive-wheel systems in wireless network environments. IEEE Trans. Cybern. 2020, 50, 2462–2474. [Google Scholar] [CrossRef]
- Li, X.; Feng, S.; Hou, N.; Wang, R.; Li, H.; Gao, M.; Li, S. Surface microseismic data denoising based on sparse autoencoder and Kalman filter. Syst. Sci. Control Eng. 2022, 10, 616–628. [Google Scholar] [CrossRef]
- Wu, C.; Zhao, X.; Li, C.; Zhao, N. Controller synthesis of asynchronous periodic event-triggered networked control systems subject to quantization effects. IEEE Trans. Signal Inf. Process. Netw. 2022, 8, 907–919. [Google Scholar] [CrossRef]
- Zhang, X.M.; Han, Q.L.; Ge, X. A novel approach to H∞ performance analysis of discrete-time networked systems subject to network-induced delays and malicious packet dropouts. Automatica 2022, 136, 110010. [Google Scholar] [CrossRef]
- Li, C.; Zhao, X.; Chen, M.; Xing, W.; Zhao, N.; Zong, G. Dynamic periodic event-triggered control for networked control systems under packet dropouts. IEEE Trans. Autom. Sci. Eng. 2024, 21, 906–920. [Google Scholar] [CrossRef]
- Liu, J.; Wu, Z.G.; Yue, D.; Park, J.H. Stabilization of networked control systems with hybrid-driven mechanism and probabilistic cyber attacks. IEEE Trans. Syst. Man Cybern. Syst. 2021, 51, 943–953. [Google Scholar] [CrossRef]
- Li, Z.M.; Chang, X.H.; Xiong, J. Event-based fuzzy tracking control for nonlinear networked systems subject to dynamic quantization. IEEE Trans. Fuzzy Syst. 2023, 31, 941–954. [Google Scholar] [CrossRef]
- Liang, G.; Weller, S.R.; Zhao, J.; Luo, F.; Dong, Z.Y. The 2015 Ukraine blackout: Implications for false data injection attacks. IEEE Trans. Power Syst. 2017, 32, 3317–3318. [Google Scholar] [CrossRef]
- Pang, Z.H.; Fan, L.Z.; Guo, H.; Shi, Y.; Chai, R.; Sun, J.; Liu, G.P. Security of networked control systems subject to deception attacks: A survey. Int. J. Syst. Sci. 2022, 53, 3577–3598. [Google Scholar] [CrossRef]
- Li, H.; Yang, Q.; Zhan, X.; Wu, J.; Yan, H. Hybrid-triggered H∞ control for networked control systems with deception attacks. IEEE Trans. Circuits Syst. II Exp. Briefs 2023, 70, 3494–3498. [Google Scholar] [CrossRef]
- Mahmoud, M.S.; Hamdan, M.M.; Baroudi, U.A. Secure control of cyber physical systems subject to stochastic distributed DoS and deception attacks. Int. J. Syst. Sci. 2020, 51, 1653–1668. [Google Scholar] [CrossRef]
- Zhang, L.; Sun, S. Distributed H∞ fusion filtering for multi-sensor networked systems with DoS attacks and sensor saturations. Digit. Signal Process. 2023, 134, 103908. [Google Scholar] [CrossRef]
- Liu, J.; Ke, J.; Liu, J.; Xie, X.; Tian, E. Secure event-triggered control for IT-2 fuzzy networked systems with stochastic communication protocol and FDI attacks. IEEE Trans. Fuzzy Syst. 2024, 32, 1167–1180. [Google Scholar] [CrossRef]
- Pang, Z.H.; Fan, L.Z.; Dong, Z.; Han, Q.L.; Liu, G.P. False data injection attacks against partial sensor measurements of networked control systems. IEEE Trans. Circuits Syst. II Exp. Briefs 2022, 69, 149–153. [Google Scholar] [CrossRef]
- Yan, H.; Wang, J.; Zhang, H.; Shen, H.; Zhan, X. Event-based security control for stochastic networked systems subject to attacks. IEEE Trans. Syst. Man Cybern. Syst. 2020, 50, 4643–4654. [Google Scholar] [CrossRef]
- Liu, J.; Wang, S.; Hu, B.; Liu, J.; Xie, X.; Tian, E. Non-fragile observer-based security control for networked systems via event-triggered WTOD protocol. Int. J. Robust Nonlinear Control 2024, 34, 5852–5872. [Google Scholar] [CrossRef]
- Wang, F.; Liang, J.; Lam, J.; Yang, J.; Zhao, C. Robust filtering for 2-D systems with uncertain-variance noises and weighted try-once-discard protocols. IEEE Trans. Syst. Man Cybern. Syst. 2023, 53, 2914–2924. [Google Scholar] [CrossRef]
- Li, Y.; Song, F.; Liu, J.; Xie, X.; Tian, E.; Fei, S. Round Robin-based synchronization control for discrete-time complex networks with probabilistic coupling delay and deception attacks. IEEE Trans. Syst. Man Cybern Syst. 2024, 54, 4425–4436. [Google Scholar] [CrossRef]
- Shang, H.; Zong, G.; Qi, W. Security control for networked discrete-time semi-Markov jump systems with round-robin protocol. IEEE Trans. Circuits Syst. II Exp. Briefs 2022, 69, 2812–2816. [Google Scholar] [CrossRef]
- Liu, J.; Ke, J.; Liu, J.; Xie, X.; Tian, E. Stochastic communication protocol-based security control for discrete-time networked systems using state observer. IEEE Trans. Syst. Man Cybern Syst. 2024, 54, 5501–5512. [Google Scholar] [CrossRef]
- Cheng, J.; Zhang, Q.; Yan, H.; Zhang, D.; Park, J.H. Observer-based sliding mode control for fuzzy systems under stochastic communication protocol. IEEE Trans. Circuits Syst. II 2024, 71, 3860–3864. [Google Scholar] [CrossRef]
- Liu, S.; Wang, Z.; Wang, L.; Wei, G. Recursive set-membership state estimation over a FlexRay network. IEEE Trans. Syst. Man Cybern. Syst. 2022, 52, 3591–3601. [Google Scholar] [CrossRef]
- Wang, W.; Nešić, D.; Postoyan, R. Emulation-based stabilization of networked control systems implemented on FlexRay. Automatica 2015, 59, 73–83. [Google Scholar] [CrossRef]
- Tang, Y.; Zhang, D.; Ho, D.W.C.; Qian, F. Tracking control of a class of cyber-physical systems via a FlexRay communication network. IEEE Trans. Cybern. 2019, 49, 1186–1199. [Google Scholar] [CrossRef]
- Liu, S.; Wang, Z.; Wang, L.; Wei, G. Finite-horizon H∞ filtering via a high-rate network with the FlexRay protocol. IEEE Trans. Autom. Control 2023, 68, 3596–3603. [Google Scholar] [CrossRef]
- Wang, Y.; Wang, Z.; Zou, L.; Ma, L.; Dong, H. Ultimately bounded PID control for T–S fuzzy systems under FlexRay communication protocol. IEEE Trans. Fuzzy Syst. 2023, 31, 4308–4320. [Google Scholar] [CrossRef]
- Liu, J.; Wang, S.; Liu, J.; Xie, X.; Tian, E. FlexRay protocol-based event-triggered secure filtering for IT-2 fuzzy systems with fading measurements over high-rate communication networks: The finite-horizon case. IEEE Trans. Syst. Man Cybern Syst. 2024, 54, 6055–6067. [Google Scholar] [CrossRef]
- Wang, W.; Nešić, D.; Postoyan, R. Observer design for networked control systems with FlexRay. Automatica 2017, 82, 42–48. [Google Scholar] [CrossRef]
- Zhu, Y.; Tang, X.; Kang, D.; Zhang, L.; She, M.; Tan, C. Static output feedback H2/H∞ fault-tolerant control for nonlinear networked systems under hybrid cyber attacks and hybrid-triggered mechanisms. Int. J. Control Autom. Syst. 2025, 23, 1722–1735. [Google Scholar] [CrossRef]
- Hu, Y.; Kwon, O.M.; Lee, S.H. H∞ control for interval type-2 fuzzy singularly perturbed systems with multi-node round-robin protocol and packet dropouts. Fuzzy Sets Syst. 2025, 500, 109202. [Google Scholar] [CrossRef]
- Wu, Z.; Wang, Y.; Xiong, J.; Xie, M. Switching periodic event-triggered H∞ control for NCSs and its application to UAVs. IEEE Trans. Veh. Technol. 2024, 73, 5078–5088. [Google Scholar] [CrossRef]
- Zhi, Y.; Liu, X.; He, S.; Lin, W.; Chen, W. Adaptively event-triggered H∞ control for networked autonomous aerial vehicles control systems under deception attacks. IEEE Trans. Ind. Inform. 2025, 21, 3458–3465. [Google Scholar] [CrossRef]
- Yue, D.; Tian, E.; Han, Q.L. A delay system method for designing event-triggered controllers of networked control systems. IEEE Trans. Autom. Control 2013, 58, 475–481. [Google Scholar] [CrossRef]
- Tan, Y.; Liu, J.; Xie, X.; Tian, E.; Liu, J. Dynamic-memory event-triggered sliding-mode secure control for nonlinear semi-Markov jump systems with stochastic cyber attacks. IEEE Trans. Autom. Sci. Eng. 2025, 22, 202–214. [Google Scholar] [CrossRef]
- Zhong, Q.; Yang, J.; Shi, K.; Zhong, S. Design of observer-based discrete-type PID control for reconstructed jump model of interconnected power system under hybrid attacks. IEEE Trans. Smart Grid 2023, 14, 1896–1906. [Google Scholar] [CrossRef]
- Cheng, J.; Pang, H.; Yan, H.; Zhang, D. Protocol-based PID control of switched systems with DoS attacks. IEEE Trans. Inf. Forensics Secur. 2025, 20, 8059–8068. [Google Scholar] [CrossRef]
- Gao, X.; Deng, F.; Zeng, P.; Liu, X. Protocol-based stability analysis of stochastic hybrid systems under DoS attacks. IEEE Trans. Syst. Man Cybern. Syst. 2022, 52, 6348–6358. [Google Scholar] [CrossRef]
- Yang, H.; Peng, C.; Cao, Z. Attack-model-independent stabilization of networked control systems under a jump-like TOD scheduling protocol. Automatica 2023, 152, 110982. [Google Scholar] [CrossRef]
- Yu, T.; Xu, H.; He, S. GA-optimized co-design of jump-like FlexRay protocol and dynamic control for NCSs and its applications. IEEE Syst. J. 2025, 19, 670–681. [Google Scholar] [CrossRef]
- Hu, J.; Yang, S.; Caballero-Águila, R.; Dong, H.; Wu, B. Mixed static-dynamic protocol-based Tobit recursive filtering for stochastic nonlinear systems against random false data injection attacks. IEEE Trans. Signal Inf. Process. Netw. 2024, 10, 445–459. [Google Scholar] [CrossRef]
- Liu, S.; Wei, G.; Song, Y.; Liu, Y. Extended Kalman filtering for stochastic nonlinear systems with randomly occurring cyber attacks. Neurocomputing 2016, 207, 708–716. [Google Scholar] [CrossRef]
- Song, H.; Ding, D.; Dong, H.; Yi, X. Distributed filtering based on Cauchy-kernel-based maximum correntropy subject to randomly occurring cyber-attacks. Automatica 2022, 135, 110004. [Google Scholar] [CrossRef]
- Zhang, P.; Zhu, C.; Wang, Z.; Yang, B. Recursive set-membership filtering for two-dimensional shift-varying systems with FlexRay protocol and hybrid cyber attacks. Asian J. Control 2025, 27, 797–816. [Google Scholar] [CrossRef]
- Qu, F.; Tian, E.; Zhao, X. Chance-constrained H∞ state estimation for recursive neural networks under deception attacks and energy constraints: The finite-horizon case. IEEE Trans. Neural Netw. Learn. Syst. 2023, 34, 6492–6503. [Google Scholar] [CrossRef]
- Zhi, Y.L.; Liu, X.; Wang, Y.; Fan, Y. Network-based H∞ control for descriptor systems with time delays under a novel event-triggered strategy. IEEE Trans. Control Netw. Syst. 2025, 12, 943–953. [Google Scholar] [CrossRef]
- Xu, Y.; Mu, X.; Cheng, G. Event-triggered H∞ control for switched systems under multiple attacks. Int. J. Control Autom. Syst. 2023, 21, 1089–1097. [Google Scholar] [CrossRef]
- Qi, W.; Zhang, N.; Ahn, C.K.; Zong, G. Genetic-algorithm-based sliding-mode stabilization for networked switched systems with unreliable channels. IEEE Trans. Control Netw. Syst. 2024, 11, 1778–1789. [Google Scholar] [CrossRef]
- Hespanha, J.P.; Morse, A.S. Stability of switched systems with average dwell-time. In Proceedings of the 38th IEEE Conference on Decision and Control, Phoenix, AZ, USA, 7–10 December 1999. [Google Scholar]
- Deng, Y.; Zhang, H.; Xia, J. H∞ control with convergence rate constraint for time-varying delay switched systems. IEEE Trans. Syst. Man Cybern. Syst. 2023, 53, 7354–7363. [Google Scholar] [CrossRef]
- Zhang, D.; Xu, Z.; Karimi, H.R.; Wang, Q. Distributed filtering for switched linear systems with sensor networks in presence of packet dropouts and quantization. IEEE Trans. Circuits Syst. I Reg. Pap. 2017, 64, 2783–2796. [Google Scholar] [CrossRef]
- Daafouz, J.; Riedinger, P.; Iung, C. Stability analysis and control synthesis for switched systems: A switched Lyapunov function approach. IEEE Trans. Autom. Control 2002, 47, 1883–1887. [Google Scholar] [CrossRef]
- Huang, K.; Pan, F. Finite horizon H-infinity control of nonlinear time-varying systems under WTOD protocol. IEEE Access 2022, 10, 20400–20406. [Google Scholar] [CrossRef]
- Wang, Z.; He, W.; Sun, J.; Wang, G.; Chen, J. Event-triggered control of switched nonlinear time-delay systems with asynchronous switching. IEEE Trans. Cybern. 2024, 54, 4348–4358. [Google Scholar] [CrossRef]
- Huang, X.; Xing, M.; Mo, H.; Hu, S.; Luo, H. Stabilization of uncertain networked control systems with actuator saturation and probabilistic cyberattacks. Asian J. Control 2023, 25, 1407–1419. [Google Scholar] [CrossRef]
- Liu, J.; Yin, T.; Yue, D.; Karimi, H.R.; Cao, J. Event-based secure leader-following consensus control for multiagent systems with multiple cyber attacks. IEEE Trans. Cybern. 2021, 51, 162–173. [Google Scholar] [CrossRef]
- Ma, Y.; Li, Z. Neural network-based secure event-triggered control of uncertain industrial cyber-physical systems against deception attacks. Inf. Sci. 2023, 633, 504–516. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).