1. Introduction
Video streaming (on-demand and real-time) has revolutionized our communication culture in all aspects of our lives (social, healthcare, entertainment, business, education, etc.), accounting for 65% of total Internet traffic [
1], and it is projected to increase to 82% during 2025 [
2]. Among video streaming applications, live or real-time streaming is one of the most popular media transmitted over the Internet (27% more views per video compared to video on demand [
3]), allowing for virtual interactions among geographically separated individuals. This increasing demand in video communications has consequently driven the need for users’ right to privacy and consequently propelled the development of highly secure and computationally efficient encryption schemes.
Although the security of current encryption standards is paramount, good performance and low power consumption are equally important aspects that chaos-based encryption schemes can offer [
4,
5,
6]. Previous studies [
7,
8] have shown that chaos-based block ciphers can consume 150% less energy and be 200% faster than current implementations of the Advanced Encryption Standard (AES) [
9] on various platforms, such as desktops, laptops, and smartphones. These promising results open up new possibilities for the development of competitive chaotic encryption schemes on very different platforms, ranging from high-end workstations to mobile devices, including low-performance Internet of Things (IoT) technologies.
However, Chaos-Based Cryptography (CBC) still faces some major challenges, including security, computational complexity, and floating-point precision. The security of CBC schemes depends on the appropriate choice of the underlying chaotic dynamical systems. These systems must have good dynamical properties, such as long cycles, high sensitivity to initial conditions, and an appropriate (uniform) probability distribution. The computational complexity of CBC schemes must be efficient in meeting the demands of modern multimedia applications, especially on power and energy-constrained mobile devices. Lastly, most CBC schemes require floating-point precision calculations, which can introduce rounding errors and affect the probability distribution of generated trajectories, introducing vulnerabilities to the system [
10,
11]. Despite these challenges, various techniques have been proposed to improve the security and efficiency of CBC schemes, focusing on extending the cycle length at the expense of increasing their computational complexity. Among the most important techniques for this work are multiple maps and perturbation schemes [
7,
12,
13,
14,
15,
16,
17], High-Dimensional Chaotic Systems (HDCSs) [
18,
19,
20,
21], and LookUp Table (LUT) approaches [
22,
23]. In particular, the use of LUTs, initially controversial [
24,
25], is now an excellent solution for robust chaos-based cryptography, as described in
Section 2.
The idea behind multiple chaotic maps is to increase both the cycle length and the robustness of the overall system. In this way, an attacker must face the task of breaking a network of chaotic maps rather than a single map. When combined with periodic perturbations, the level of security increases considerably. We are convinced that both the cryptographic strategy itself and the use of multiple low-dimensional chaotic maps should work together to ensure the security of the system. Moreover, the vulnerabilities of chaotic maps should be independent of the overall scheme itself. That is, the scheme should have the ability to overcome these vulnerabilities when they arise.
In [
26], a simple Coupled Map Lattice (CML) is proposed for color image encryption, consisting of interacting elements (chaotic maps) through a coupling parameter. Every trajectory produced by the CML is influenced by all maps, providing greater security than single map schemes. A similar but more complex and robust image encryption scheme is proposed in [
27]. The authors mixed different chaotic maps (Logistic, Sine and Tent maps) into the CML and applied a Z-scrambling method at a bit level to increase the security of the encryption scheme. A CML variant is presented in [
7], in which the
N interacting maps are iterated into smaller subgroups rather than collectively. A moving window of size
is defined, and only the maps falling within
w are sequentially iterated a random number of times. The window moves periodically along the CML, grouping different maps in such a way that, in the end, all maps are equally iterated. A three-level perturbation scheme is also proposed [
7], which modifies the map’s variables, parameters, and the initial key to increase the cycle length of the CML.
Although HDCS offer greater complexity, this often results in a significant decrease in performance [
28,
29], resulting in slower schemes. Excess complexity is the main cause of speed limitations in many chaos-based schemes [
28,
30,
31]. In [
32], the authors propose a multi-channel image encryption algorithm that makes use of pixel reorganization and hyperchaotic maps. Their algorithm employs two hyperchaotic maps to jointly generate chaotic sequences to obtain better randomness. Then, two rounds of scrambling and diffusion operations are applied and coupled with one round of substitution operations to the high 4-bit components of the image. For the 4-bit low components, one round of substitution and diffusion operations is conducted. In [
33], an encryption algorithm is proposed, using a new Pseudo-Random Number Generator (PRNG) based on mixing three-dimensional variables of a cat chaotic map. A uniformly distributed chaotic sequence by a logistic map is also used during a pixel mixing step. The core of the algorithm is to use the sequence generated by the PRNG to achieve the disruption and diffusion of the image pixels and produce an effect of obfuscation and encryption of the image content. Hyperchaos and biological systems such as DNA sequence merging have been proposed for robust image encryption [
23,
34,
35,
36,
37]. The authors in [
34] transform the input image into a binary matrix, then carry out DNA encoding, and they perform the DNA sequence complement operation using two logistic maps. olor image encryption based on the DNA and double chaos system is proposed [
35]. After the input image is scrambled, three sets of chaotic sequences are generated using Lorenz chaotic mapping and fourth-order Rossler hyperchaotic to transform the chaotic component images and chaotic sequences into DNA sequences. They applied the DNA coding rules and three DNA operation rules for the final image encryption.
The use of chaotic maps along with dynamic LUT models has been shown to generate fast and secure encryption systems with an excellent avalanche effect (ciphertexts from slightly different plaintexts differ significantly), as described in [
38]. An LUT can be seen as a transformation function in which the input value produces an index to be used in the encryption process. The beginning of LUT models can be traced back to Baptista (1998) [
39], who proposed an iterative chaotic encryption scheme where the phase space is divided into
M equal-sized subintervals corresponding to the number of elements in the plaintext alphabet. Each plaintext alphabet is assigned to one subinterval and encrypted as the number of iterations on the logistic map needed to visit the corresponding subinterval departing from a private initial condition. Baptista´s scheme and variants stayed in the eye of the hurricane for more than 10 years due to security flaws and low speed performance [
40]. A different and improved LUT approach is proposed in [
38], in which the
M subintervals are represented by indices pointing to chaotic trajectories stored (initially) in sequential order. Since the indices are randomly chosen, the encryption process is performed using non-sequential trajectories that may be far apart (in time) from each other, increasing the security and speed of the system.
Our goal is to develop a system that is not only secure but also highly efficient and adaptable to the needs of modern real-time multimedia applications. In contrast to previously mentioned approaches that use high-dimensional or multiple chaotic maps sequentially iterated, in this research, we propose a simpler and more efficient structure based on the concept of a random graph of chaotic maps (representing the vertices), wherein maps are randomly selected via a spin-wheel-like procedure. This random selection, combined with a new two-dimensional lookup table of trajectories and random perturbations, allows for a higher degree of diffusion and confusion in the ciphertext, increasing resistance to cryptanalysis attacks. Finally, a fast and robust scheme is incorporated after the encryption process to establish the integrity of the encrypted plaintext at the recipient’s end [
41]. The overall goal of this research is to develop an encryption scheme that provides an optimal balance between security and performance, focusing on applications that require a high level of confidentiality and low latency.
2. Proposed Scheme
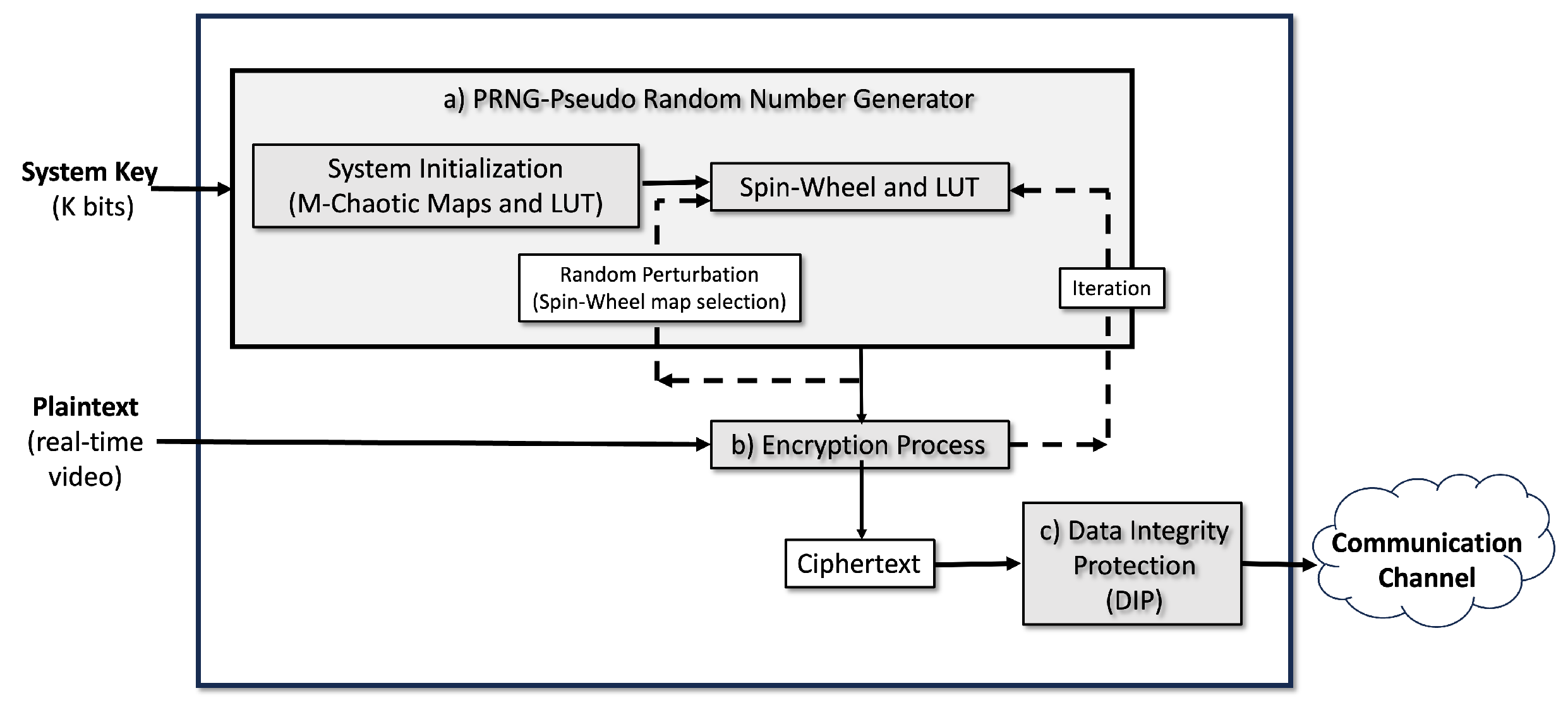
Our proposed encryption algorithm can be applied to any type of multimedia data, including text, audio, images, and video, in a compressed or uncompressed domain. It is independent of the compression method and can be applied as full or selective encryption [
4,
37,
42,
43,
44], depending on the level of security required by the application. Broadly speaking, our encryption system consists of three main modules (see
Figure 1): (a) A Pseudo-Random Number Generator (PRNG), the core algorithm in the encryption process; (b) Encryption Process; and (c) Data Integrity Protection (DIP), a mechanism for detecting ciphertext manipulation or attacks during the communication process. Each module is described in detail in the following subsections.
2.1. Pseudo-Random Number Generator (PRNG)
Our PRGN is based on the concept of a random graph or random network of M chaotic maps and a 2-Dimensional LUT (2D-LUT) of size that stores N trajectories per map. Each map and corresponding trajectories are randomly selected on the basis of the Spin-Wheel Picker (SWP) game. The SWP generates two random indices, one for the selection of the chaotic map and the other for the corresponding map trajectory within the 2D-LUT. In this way, every system iteration generates random trajectories from different maps without a predefined temporal order (older trajectories may be randomly used before newer ones within the selected map), which increases the robustness of the system against various attacks such as brute-force, plaintext, ciphertext, etc. Each requested trajectory is replaced by a new one coming from the sequential iterative process of the corresponding selected map. Each component of the PRNG is described in detail in the following sub-sections.
2.1.1. Chaotic Map: Digitized Renyi Map
An important decision that must be made in any chaos-based encryption is the choice of the chaotic map (i.e., the core function of the system). Since our interest lies in developing a fast and highly secure encryption system, we choose a digitized version of the Renyi map [
45], defined as follows:
where
is the Renyi map function,
k is the iteration index,
and
are control parameters,
is the CPU bit-precision (32 or 64 bits), and
is the initial condition.
is defined over the integer domain and generates trajectories with much higher speed than the corresponding chaotic maps with floating-point arithmetic. However, as a digitized chaotic map, it presents degraded dynamic properties caused by the limited precision of computers (see [
15]). In consequence, its statistical properties and cycle length are severely degraded compared to their analog representation, resulting in trajectories with poor random behavior. Furthermore, the trajectories of the Renyi map follow a linear process (see Equation (
1)), increasing until they exceed the computer precision and the wrap-around occurs. Having consecutive trajectories of this map significantly reduces the number of possible parameters, making it partially predictable to an attacker. Ideal chaotic behavior has been shown not to be necessary from the chosen map, as long as the proposed scheme provides the mechanisms or strategies to improve randomness, mitigate cycles, overcome fixed points, and generate a uniform distribution [
38]. Our proposed scheme is intended to provide all the necessary protection to avoid exposing the identity of chaotic maps.
2.1.2. PRNG Initialization
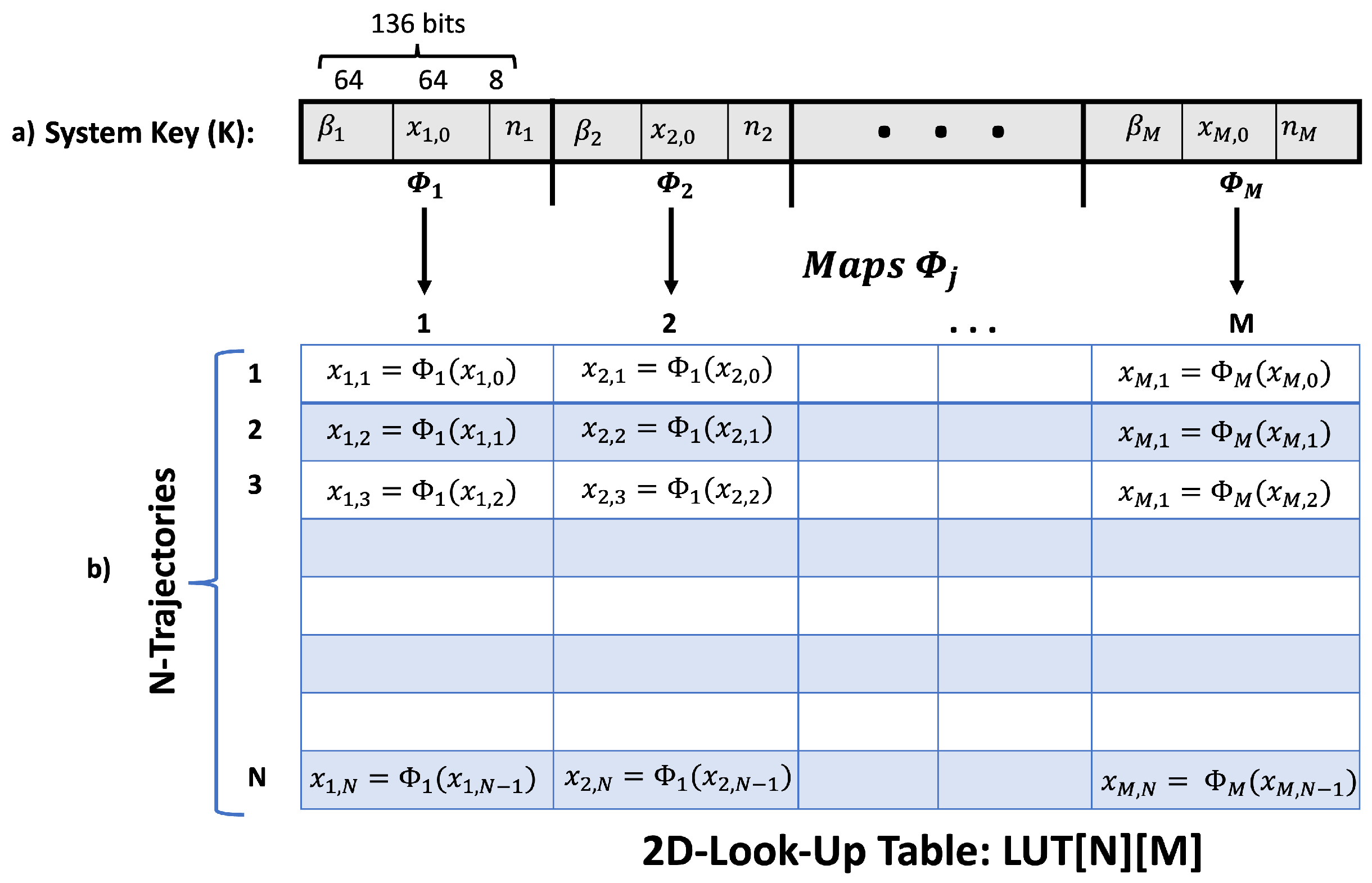
The initialization process (Algorithm 1) begins by assigning random values to each map parameter and initial variable, according to a predefined seed or system key
K, as shown in
Figure 2a.
and
are represented by
bits (see
Table 1), while
n is represented by 8 bits; therefore, 136 bits are taken from the cipher key
to initialize each map in sequential order (from 1 to
M). The longer the encryption key, the greater the number of chaotic maps involved in the system. For
M maps, a key length of 136 ×
M bits is required; however, if
K is shorter, a bit overlap strategy of at most
bits can be used to initialize each map to avoid the same or similar control parameters. The
M maps are represented as follows:
where
is the current map index and
is the total number of maps as a function of
bits (without map overlapping). For every cipher session, different system’s seeds are employed; that is,
K is a random variable in both value and length (and thus
M). An associated matrix (2D-LUT) is then built and fed with
N sequential trajectories from each map to form an
initial matrix (
Figure 2b). It is worth mentioning that this is the only step in which the trajectories for each map (or column) are inserted in order in the 2D-LUT; during plaintext encryption, the trajectories are inserted randomly for additional security (as explained later in
Section 2.1.1).
| Algorithm 1 Initialization |
- 1:
Parameters, X_initials = PRNG_SEED - 2:
H = 0 // Perturbation Term - 3:
Maps = [ Map(Parameter,X) for Parameter,X in Parameters, X_initials ] - 4:
for i in 0…N do // Fill the the trajectories 2D-LUT - 5:
for j in 0…M do - 6:
2D-LUT[i][j] = Maps[i].next() // this also updates Maps[i].X - 7:
end for - 8:
end for - 9:
= 2D-LUT[i][j] // Sets the last value entered into the 2D-LUT - 10:
iteration = 0 - 11:
for m in 0…M do - 12:
H = H ⨁ Matrix[N][M] - 13:
end for
|
Once the look-up table has been populated, a system perturbation variable (to be used during ciphering) is initialized as follows:
where
i represents the system iteration index, and
represents the XOR (⨁) operation of the last inserted trajectories in the 2D-LUT per map; that is, all map trajectories along the
row (
Figure 2b).
is updated on an iteration basis using the most recently inserted trajectory. The main function of
during the encryption process is to randomly perturb individual maps with contributions from all maps (as explained in the following subsection), modifying in this way the future behavior and dynamics of the encryption system. Finally,
is the last trajectory inserted in the lookup-table and used by the SWP for the selection of a map (
varies on an iteration basis).
2.1.3. Spin-Wheel and Crossover Process
The goal of our proposed PRNG is to create complex and mutual interactions between maps to lengthen the encryption system cycle. Our strategy is to avoid using consecutive trajectories of the same map or a predefined sequence of maps; otherwise, chaotic parameters could be inferred and used to predict future values of the sequence. Our PRNG consists of two schemes (
Figure 3):
Spin-Wheel Picker (SWP): The first step in the PRNG is the random selection of the map and corresponding trajectory within the 2D-LUT employing the SWP strategy (
Figure 3a). The SWP generates two random indices, one for the selection of the map (column index) and another for the selection of its corresponding trajectory (row index) in the 2D-LUT. In the first case (map index), the SWP is simulated by putting together the
M maps in a circular array and using the module operation as follows:
where
is the selected map index in the 2D-LUT at global or system iteration
i, and
is the Least Significant Byte (LSB) of
. The corresponding trajectory or row index (
) is obtained in a similar way as in Equation (
4), except that we now use the Most Significant Byte (MSB) of
, named
:
The corresponding random trajectory
becomes the seed for generating the final trajectories to be used in the ciphering process (described in
Section 2.2).
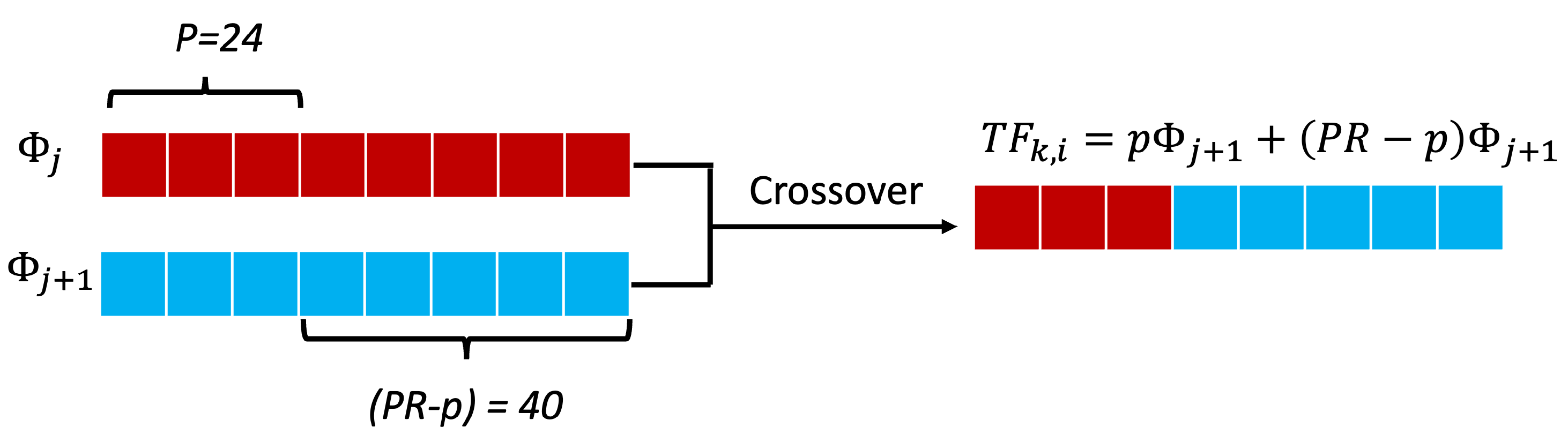
Crossover Strategy: In our second step, three additional trajectories are generated through a
p-point crossover operation between the selected trajectories
and its adjacent trajectory
(
Figure 3b). During crossover, a random bit position
is calculated so that the first
bits of
and the
bits of
are combined to generate the first final trajectory (out of three) of the
iteration
, as shown in
Figure 4. After this process, the bits used in
and
are replaced by the next trajectory of the selected chaotic map. The
map is first perturbed with the following expression:
where (
) is the perturbation mechanism and
is an arbitrary 3-bit value obtained from the crossover variable
. The new perturbed trajectory
is now inserted in
. Henceforth, the 2D-LUT holds original and perturbed trajectories in the same column (or map) in a nonsequential order, and both are available to be randomly picked for future iterations.
is simply replaced by the next iterated trajectory
, which is also involved in the new values of
and
.
Similarly, to compute the second final trajectory, new indices
and
are calculated from the SWP (Equations (
4) and (
5)) based on the least and most significant bytes of the new
, respectively. The new adjacent and randomly selected trajectories
and
are retrieved from the 2D-LUT to go through the
p-point crossover operation to obtain
. In a similar fashion as in
,
and
are replaced by new trajectories from their corresponding maps, and
and
are updated, respectively. The same operation is performed to obtain
. As can be seen, only those trajectories selected by the SWP are perturbed; the corresponding adjacent trajectories (which become the actual
) are used as pointers to the new indices for the next trajectory.
It is worth noting that the described approach ensures that it is not possible to know which trajectory corresponds to each map at a given time. As a result, even if an attacker obtains consecutive trajectories used in the ciphering processing, he cannot easily determine the parameters of an individual map because the trajectories are masked (crossover process) and do not necessarily belong to the same map consecutively. The random selection of maps and trajectories breaks the continuity of the entire system.
The process used to generate a single random number is explained in Algorithm 2.
| Algorithm 2 Random Number Generation |
- 1:
// SWP random selection of the map and trajectory indices - 2:
M - 3:
- 4:
selected_trajectory = 2D-LUT[,] - 5:
selected_trajectory_secondary = 2D-LUT[, + 1 mod M] - 6:
// Crossover Strategy - 7:
p = ( mod (PR − 15)) + 8 - 8:
TF = crossover(selected_trajectory, selected_trajectory_secondary, p) - 9:
// before returning the random number we have to replace the random bits used - 10:
// & H adds the perturbation term - 11:
= Maps[].next() + & H - 12:
H = H ⨁ - 13:
// —————————– - 14:
// this will replace only the bits used to generate the random number - 15:
selected_trajectory = crossover(, selected_trajectory, p) - 16:
selected_trajectory_secondary = crossover(selected_trajectory_secondary, , p) - 17:
// —————————– - 18:
return TF
|
2.2. Ciphertext and Data Integrity
A resistant encryption scheme along with a simple mechanism to verify and detect data integrity at the receiver’s end is proposed. For each cipher block
i, three final trajectories (
(
)) are generated by the PRNG (
Section 2.1) and combined in a block-cipher as follows:
is the plaintext of length PR bits,
is the corresponding ciphertext, and
is a new Renyi map with parameters
and
.
is independent of the PRNG and only participates in the cipher as a feedback transformation function between previous ciphertext (
) and the actual final trajectory
. It creates ciphertext dependencies in each iteration, making the system more sensitive to changes in the plaintext and corresponding key. As described in
Section 3 (Performance Analysis), due to feedback transformation, it is difficult to determine the individual values of
,
,
,
, and
parameters (
and
n). Moreover, it is practically impossible to determine the original trajectories and corresponding parameters of the
Renyi maps for the following reasons: (a) trajectories may have gone through multiple perturbations; and (b) trajectories in the LUT are taken randomly.
A severe disadvantage of adding feedback to the cipher is that a single bit error in the received bitstream impedes deciphering of all remaining data. To solve this, packets (transmitted over the Internet) are ciphered independently; that is, feedback is reset on a packet basis, eliminating all dependencies among them (the dependency is only intra-packet). If a packet is lost, the rest of the information can still be deciphered. In the case of an attack, such as Man-in-the-Middle, the intruder positions himself between two-party communication and may divert and/or alter original messages, taking control of the communication. The mechanism for verifying data integrity is simple and lightweight; it does not have an impact on the encryption/decryption speed or the information transfer time. The scheme is based on a predefined SHA-256 key, known by both the sender and receiver. Each byte of the SHA-256 key (32 bytes long), represented by
, is transformed according to the ciphertext content of each packet as follows:
The resulting byte is appended to the corresponding cipher-packet as an identifier of data integrity. (where p is the packet number) is obtained by adding all bytes in the last plaintext of the processing packet () and XORed with the byte of , and the result is transformed by .
The decryption process consists of performing the inverse operations; therefore, the inverse transformation is expressed as follows:
where Equation (
8) remains unmodified. The operations performed are practically the same as during encryption, so in contrast to other encryption algorithms such as AES, the encryption and decryption speeds should be the same.
After processing the ciphertext, the last deciphered text should coincide with the original plaintext , which is then used to compute a candidate byte . The computed candidate byte is compared with the real ; if they coincide, then the package is considered legitimate; otherwise, the packet has been tampered with.
4. Conclusions
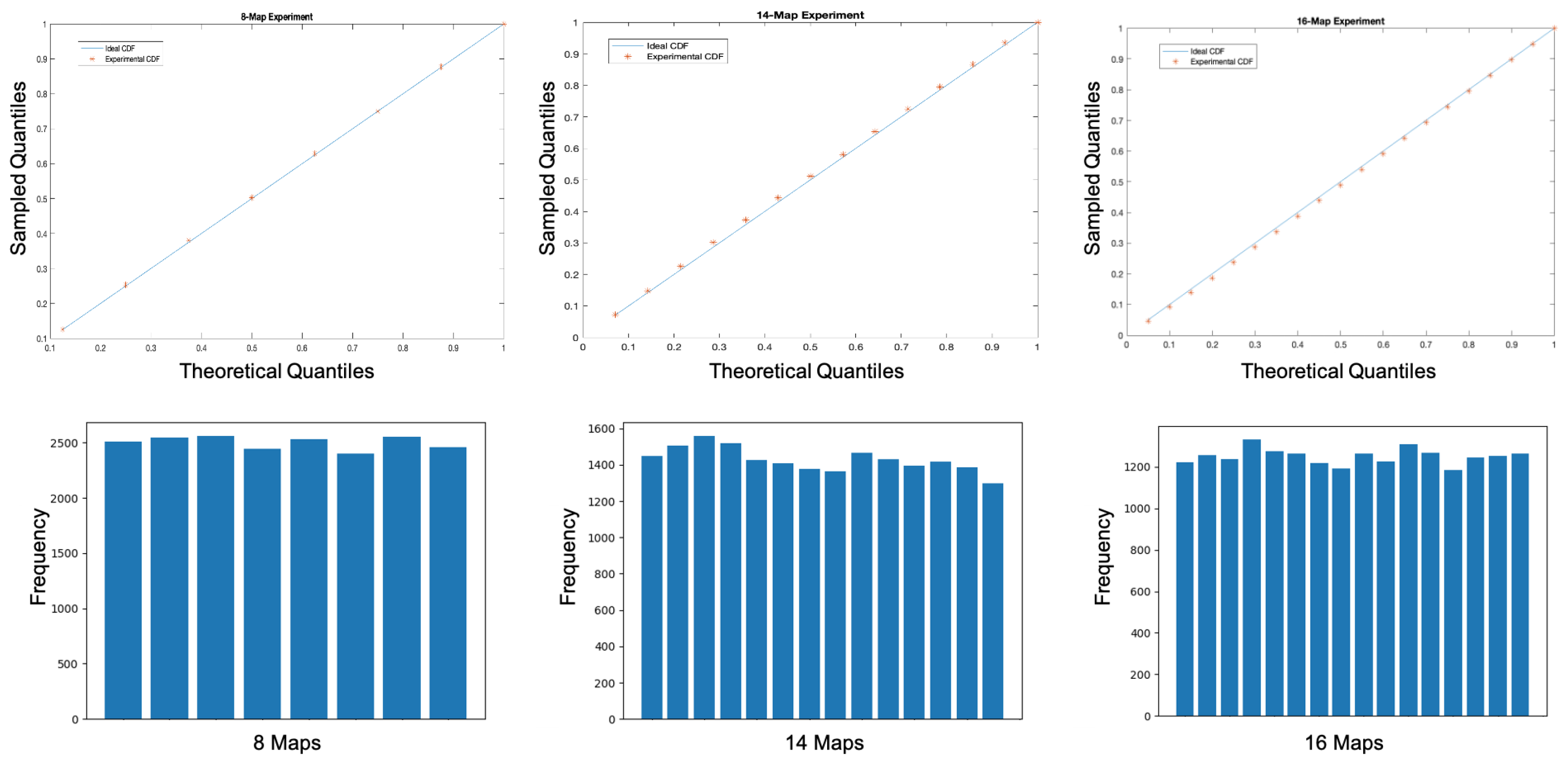
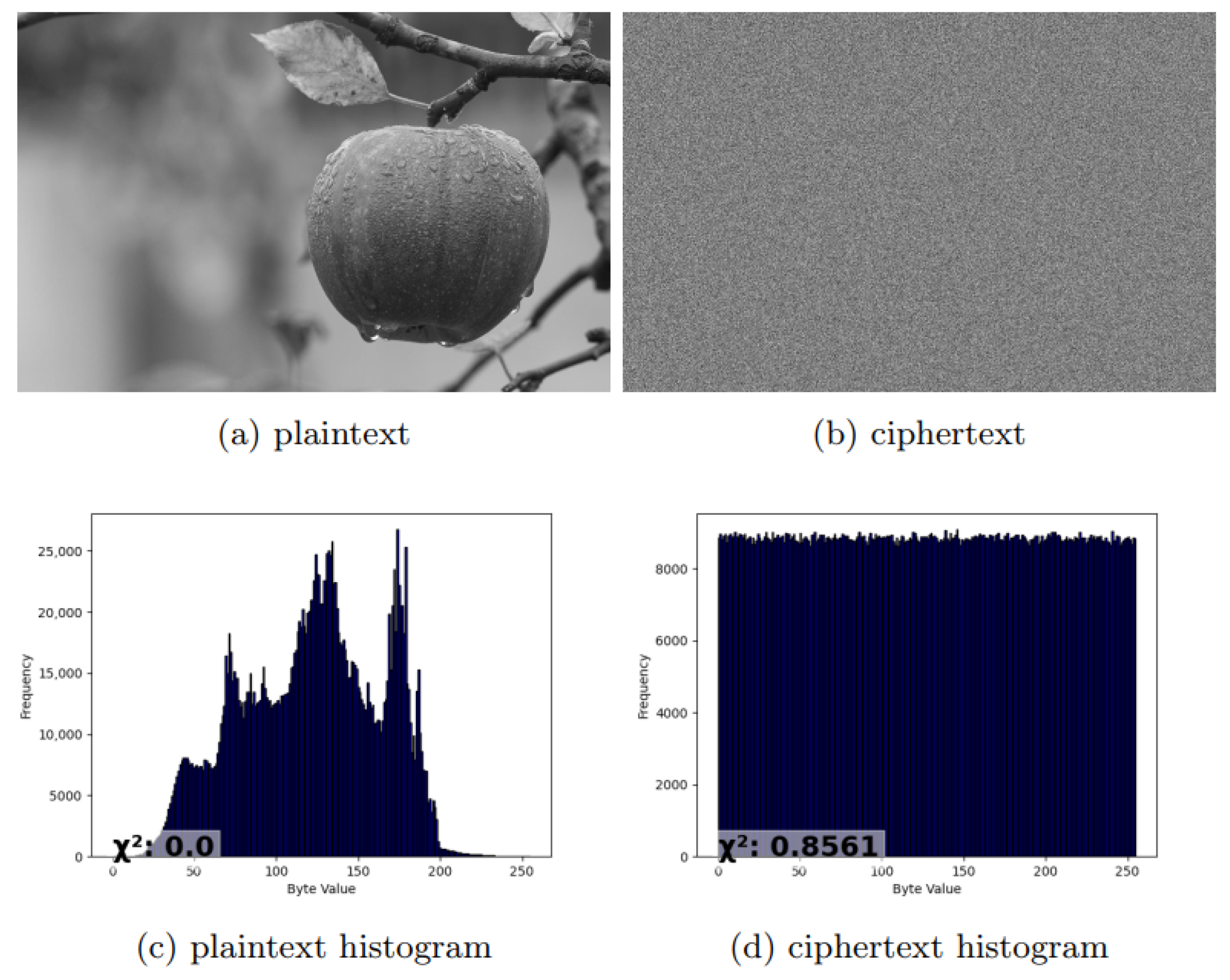
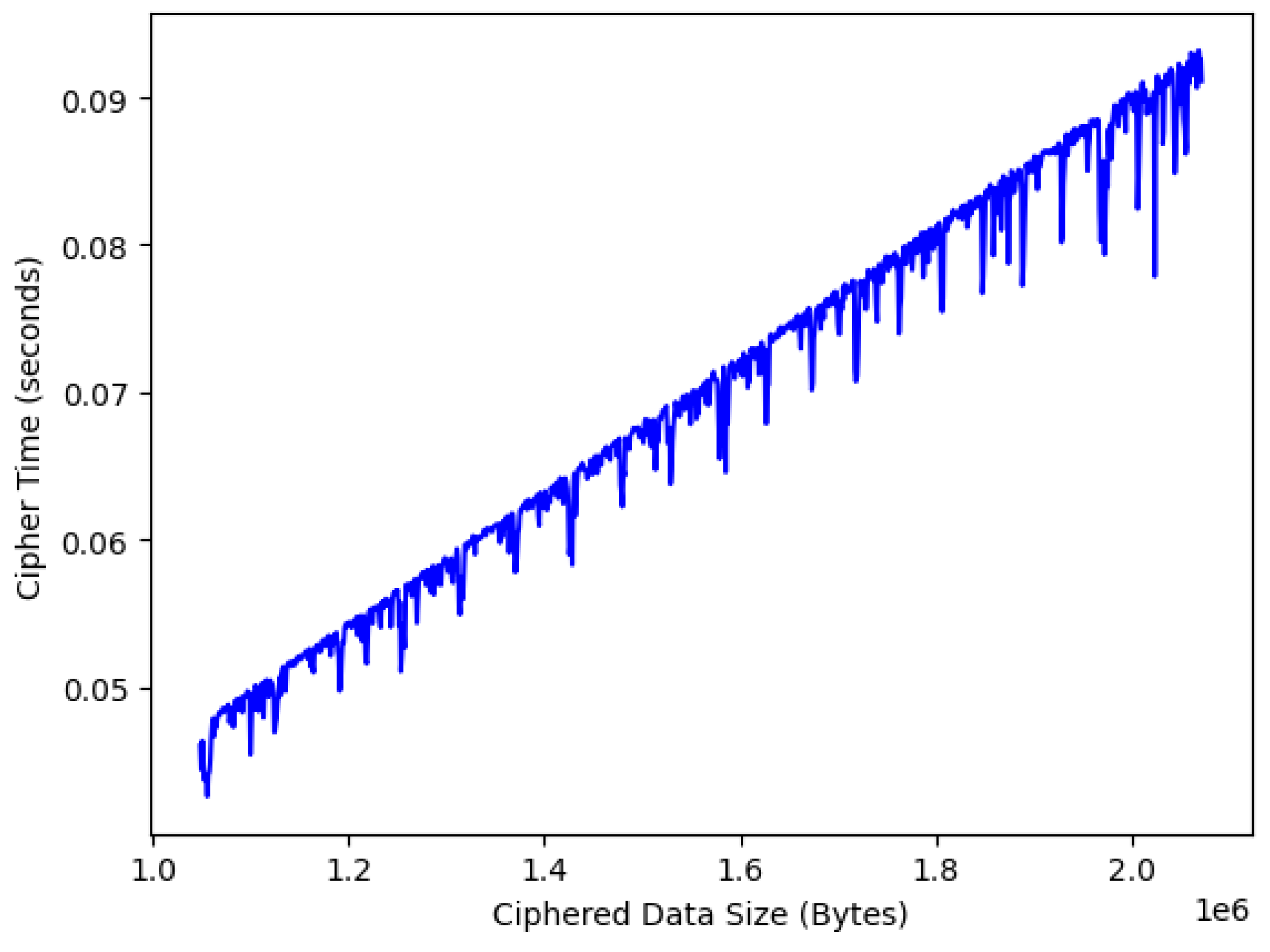
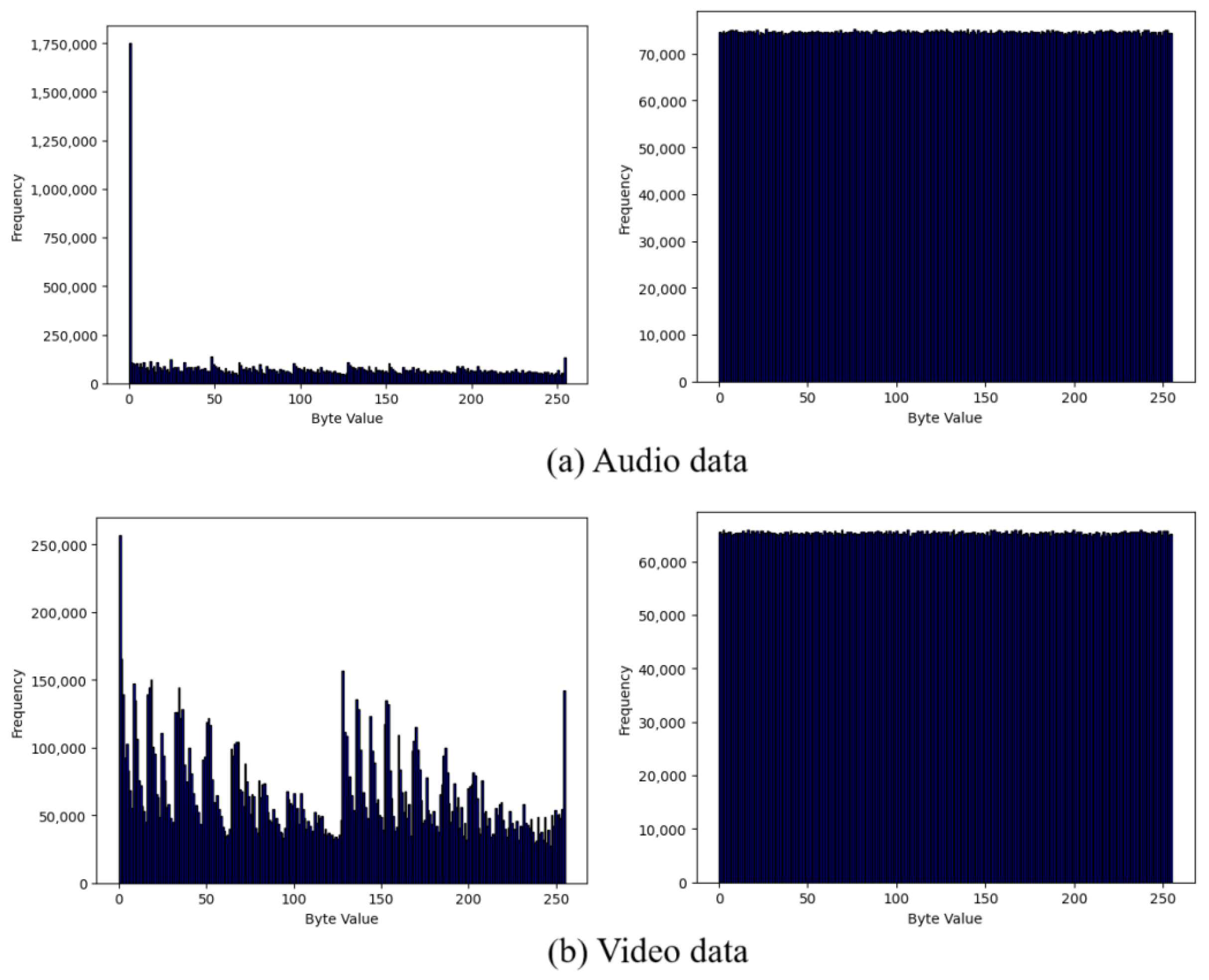
The proposed scheme is based on a random roulette method for selecting and iterating through a graph composed of M chaotic maps and an lookup table, with N precalculated trajectories initially ordered in temporal order for each map M. Three random values are involved in the encryption process: (1) selection of the map through the random roulette; (2) selection of the trajectory of the map map in the lookup table; and (3) random selection of the variable , which indicates the position of the byte within the selected map trajectory from which the trajectory will start for the encryption process (each trajectory consists of 8 bytes). Point (2) indicates that the trajectories of each map are not used sequentially or in temporal order, while point (3) indicates that the final trajectory selected within the lookup table may come from up to two contiguous maps and , containing the first bytes of and the last of , which significantly increases the security of the system in case of attacks. Experimental analysis demonstrates that the developed scheme is completely random in terms of trajectory generation and selection of maps or nodes in the chaotic map graph, showing a uniform distribution in both cases. There is an equal probability of visiting any map within the graph, offering high security against both system and brute-force attacks. According to the reported encryption speeds, the proposed scheme is theoretically capable of serving hundreds of real-time video communications without affecting performance. Based on our state-of-the-art literature review, we can confirm that our proposed encryption scheme is the fastest reported in the literature.
Since our proposed scheme exhibits a very high performance, the main target applications are real-time multimedia communications (audio, image, and video). In the context of video conferencing, the implementation of this scheme would enable higher concurrent participants without perceptible degradation in the stream quality. This capability holds significant implications for applications which require secure communication for sensitive domains, including governmental and corporate sectors, remote medical consultations, or financial exchanges.