1. Introduction
With the advent of the digital era and the rapid evolution of emerging technologies such as artificial intelligence (AI), cloud computing, and big data, digital images have found increasingly widespread use across diverse industries. Constantly, a vast number of digital images are generated, originating from a multitude of sensors, smartphones, and other terminal devices. These images are then distributed and stored through various channels, including intranets and the Internet [
1]. During their transmission and storage, digital images face a growing spectrum of security threats, encompassing data breaches and unauthorized access. These threats not only jeopardize personal privacy but also pose significant risks to the information security of diverse industries. As a result, the challenge of ensuring the efficient and secure safeguarding of image data has risen to the forefront as a critical issue requiring immediate attention [
2].
As an effective means of safeguarding image data, image encryption technology is gaining increasing favor. This technology transforms digital images into unrecognizable, quasi-noise images, rendering it impossible for unauthorized parties to obtain meaningful information, thereby effectively ensuring the security of image data [
3]. Notably, digital images are characterized by strong pixel correlation, significant data redundancy, and vast data volume. This renders text-oriented traditional algorithms, such as advanced encryption standard (AES), inappropriate for encrypting image data [
4]. Thus, to achieve higher encryption efficiency and security, researchers are continually exploring various techniques and methodologies to devise image encryption algorithms. Among these are chaotic systems [
5,
6,
7,
8,
9,
10], quantum computing [
11,
12,
13], deoxyribonucleic acid (DNA) sequence operations [
14,
15,
16], compressed sensing [
17,
18,
19], neural networks [
20,
21,
22,
23,
24,
25], optical transformations [
26,
27], and numerous others [
28,
29,
30,
31]. Additionally, a notable trend in the field of image encryption is that chaotic systems are increasingly adopted [
2,
32].
In fact, this trend is by no means accidental. Chaotic systems are highly regarded because of their remarkable characteristics, which are extremely suitable for developing cryptographic systems. Specifically, chaotic systems have the characteristics of ergodicity, unpredictability, randomness, and extreme sensitivity to initial conditions. In recent years, the academic community has continued to deepen and advance the research on chaos-based image encryption. There is a large number of image encryption algorithms that have been proposed in the past few years [
5,
6,
7,
8,
9,
33,
34,
35,
36,
37]. However, many recently reported encryption algorithms still exhibit certain weaknesses in terms of practicality or security [
38,
39,
40].
With a 2D hyperchaotic map formed by coupling multiple seed maps, Nan et al. [
33] presented an encryption algorithm based on compressed sensing and S-box. The algorithm exhibits commendable encryption results due to the inherent randomness of chaotic sequences. Nevertheless, the complex structure of their map leads to poor encryption efficiency. Furthermore, their algorithm brings data loss, rendering it impractical for encrypting images with intricate details.
Wang et al. [
34] devised an encryption algorithm based on a 1D chaotic map, which employs a common permutation and diffusion framework. To bolster the algorithm’s ability to resist plaintext attacks, they utilized the image’s hash value directly to obtain the initial inputs of the adopted chaotic map. Such a design poses practical challenges in terms of key management. Furthermore, given that the chaotic map employed features just a single control parameter, the algorithm’s effective key space is actually small.
Employing a 2D combined hyperchaotic map, Etoundi et al. [
35] built an efficient encryption algorithm. This algorithm achieves the encryption of the input image by conducting substitution and scrambling operations. Since no diffusion mechanism is introduced, it is actually unable to effectively resist various differential attacks.
In [
36], Liu et al. introduced an encryption algorithm that leverages a spatiotemporal chaotic system and DNA sequence operations. Due to its dual-bit encryption approach, the algorithm’s encryption efficiency fails to satisfy the demands of practical applications. In addition, the algorithm exploits hash values to generate the initial inputs of the chaotic system, which also leads to the dilemma of key management.
To address the deficiencies in existing algorithms and achieve higher encryption efficiency and security, we propose a novel multi-channel image encryption algorithm that leverages hyperchaotic maps and pixel reorganization (MIEA-PRHM). Distinct from numerous encryption algorithms reported in recent years [
3,
4,
5,
7,
8,
9,
14,
15,
16,
17,
23,
29,
31,
33,
34,
35,
41,
42,
43,
44,
45,
46,
47,
48,
49,
50,
51,
52,
53,
54], our MIEA-PRHM incorporates several novel designs aimed at enhancing encryption efficiency and bolstering security.
Firstly, we adopt two recently reported robust hyperchaotic maps, the 2D sinusoidally constrained polynomial hyperchaotic map (2D-SCPM) [
46] and the 2D enhanced logistic modular map (2D-ELMM) [
47]. These two hyperchaotic maps are used to jointly generate chaotic sequences. This not only expands the key space but also helps to enhance the non-periodicity and randomness of the generated chaotic sequences.
Secondly, we optimize the utilization of hash values. In our MIEA-PRHM algorithm, rather than being employed as secret keys, hash values are utilized solely to bolster the dynamism of the encryption process. This optimization not only enhances the sensitivity to plaintext, but also addresses the practical issues related to key management.
Thirdly, we apply pixel reorganization to encrypt the high 4-bit and low 4-bit components of image pixels with varying intensities. By leveraging pixel fusion and differentiated encryption, this design can reduce the computational overhead of subsequent encryption operations by roughly three-quarters.
Lastly, the encryption process of MIEA-PRHM encompasses multiple rounds of vector-level scrambling, diffusion, and substitution operations, which are not only computationally efficient but also exhibit dynamic characteristics.
In summary, our research contributes in the following aspects:
Utilizing two robust hyperchaotic maps, 2D-SCPM and 2D-ELMM, we propose a novel multi-channel image encryption algorithm called MIEA-PRHM.
Our proposed MIEA-PRHM algorithm utilizes 2D-SCPM and 2D-ELMM to jointly generate chaotic sequences, which can not only expand the key space but also enhance the randomness of chaotic sequences.
Pixel reorganization achieves differentiated encryption by splitting and fusing image pixels. This can significantly reduce the computational amount in the entire encryption process and thus improve encryption efficiency.
Dynamic vector-level encryption operations guarantee that MIEA-PRHM delivers exceptional security and encryption efficiency. Experimental results and performance analyses demonstrate that MIEA-PRHM possesses notable advantages in various aspects, particularly in terms of encryption efficiency.
We organize the remainder of this paper as follows:
Section 2 briefly describes the two hyperchaotic maps and the SHA-256 hash function.
Section 3 provides a detailed introduction to the entire encryption process of MIEA-PRHM.
Section 4 evaluates and analyzes the performance of MIEA-PRHM through a series of experiments and comparisons. In the final section, we conclude the paper.
3. Proposed MIEA-PRHM
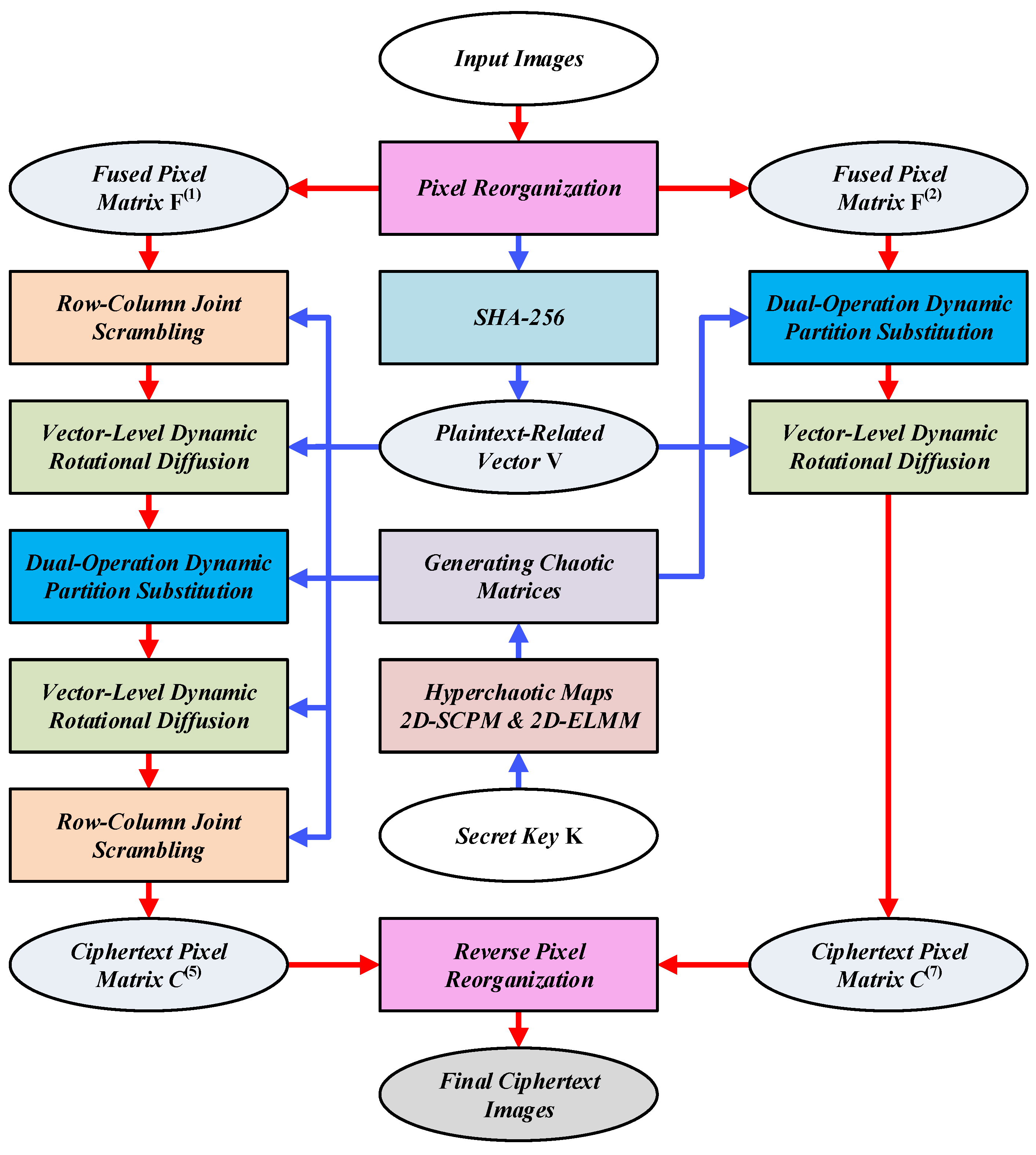
This section introduces the encryption steps and the complete encryption process of our proposed MIEA-PRHM algorithm. In this novel chaotic image encryption algorithm, there are five distinct encryption steps, which are pixel reorganization, generating chaotic sequences, row–column joint scrambling, vector-level dynamic rotational diffusion, and dual-operation dynamic partition substitution. As shown in
Figure 2, some of these encryption steps are performed once, while others are performed twice or three times. Next, we introduce these encryption steps in detail one by one.
3.1. Pixel Reorganization
In this encryption step, we split the image pixels that require encryption into high 4-bit and low 4-bit components. Subsequently, separate pixel fusion operations are conducted on these components. The purpose of pixel splitting is to facilitate the application of different encryption intensities to the high 4-bit and low 4-bit components in subsequent encryption steps. Meanwhile, pixel fusion aims to more fully exploit the computational capabilities of the processor. Consequently, both approaches contribute to improving the encryption efficiency of MIEA-PRHM. Specifically, pixel reorganization encompasses the following steps:
Step 1: For one or multiple input images that require encryption, aggregate them into a 3D pixel matrix with dimensions of . Here signifies the channel dimensions of these images, and N signifies the total number of channels across these input images. In this context, a grayscale image is deemed a single channel image, whereas a color image is considered a three channel image, comprising the red (R), green (G), and blue (B) channels.
Step 2: Reshape into a 3D pixel matrix with dimensions of , where and . If or is not an integer, is filled with zero-value pixels to ensure that or becomes the smallest integer greater than itself.
Step 3: Mathematically split
into a high 4-bit component
, and a low 4-bit component
:
where
yields the largest integer that does not exceed its operand.
Step 4: Sequentially superimpose each of the eight planes within
to obtain a fused 2D pixel matrix
with dimensions
:
Step 5: Analogously, each plane of size
within
is accumulated to yield another fused 2D pixel matrix
.
3.2. Generating Chaotic Matrices
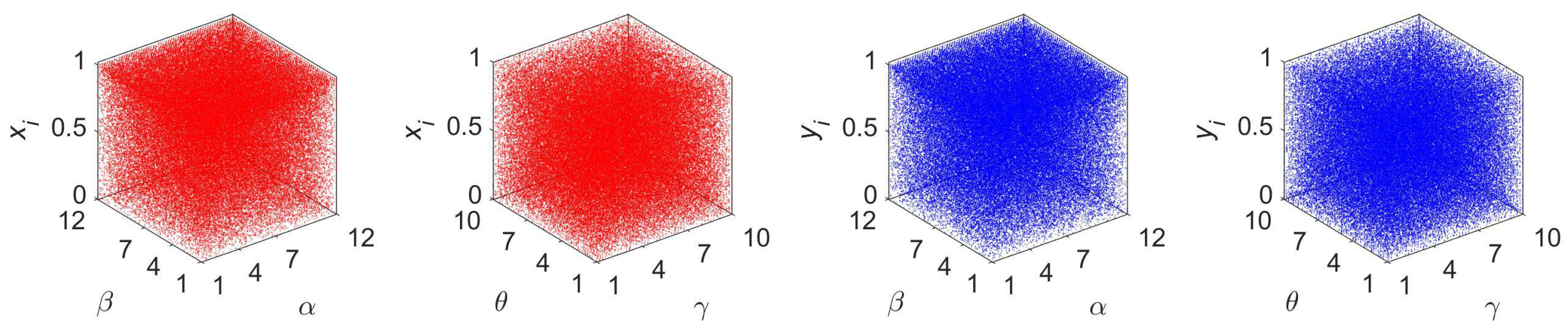
In our proposed MIEA-PRHM, the secret key comprises eight components, denoted as . Among these eight components, the first four serve as inputs for 2D-SCPM, while the latter four are utilized as inputs for 2D-ELMM. In our proposed MIEA-PRHM, the chaotic sequences and generated by these two hyperchaotic maps are first superimposed to ensure that the resultant chaotic sequence exhibits enhanced aperiodicity and randomness. Subsequently, is further partitioned and transformed into four chaotic matrices , , , and , which are utilized in the subsequent encryption steps. Specifically, the generation processes of , , , and are as follows:
Step 1: Input , , , and into 2D-SCPM and subsequently perform iterations on it. The two chaotic state values obtained in each iteration are sequentially appended to , continuing this process until the length of reaches . Here, H and W are the height and width, respectively, of the two fused pixel matrices and .
Step 2: Input , , , and into 2D-ELMM and perform iterations on it. The two chaotic state values obtained in each iteration are sequentially appended to , continuing this process until the length of reaches .
Step 3: Conduct a mathematical superposition on
and
to derive
:
Step 4: Conduct the following partitioning and transformation operations on
to obtain the required four chaotic matrices:
where
.
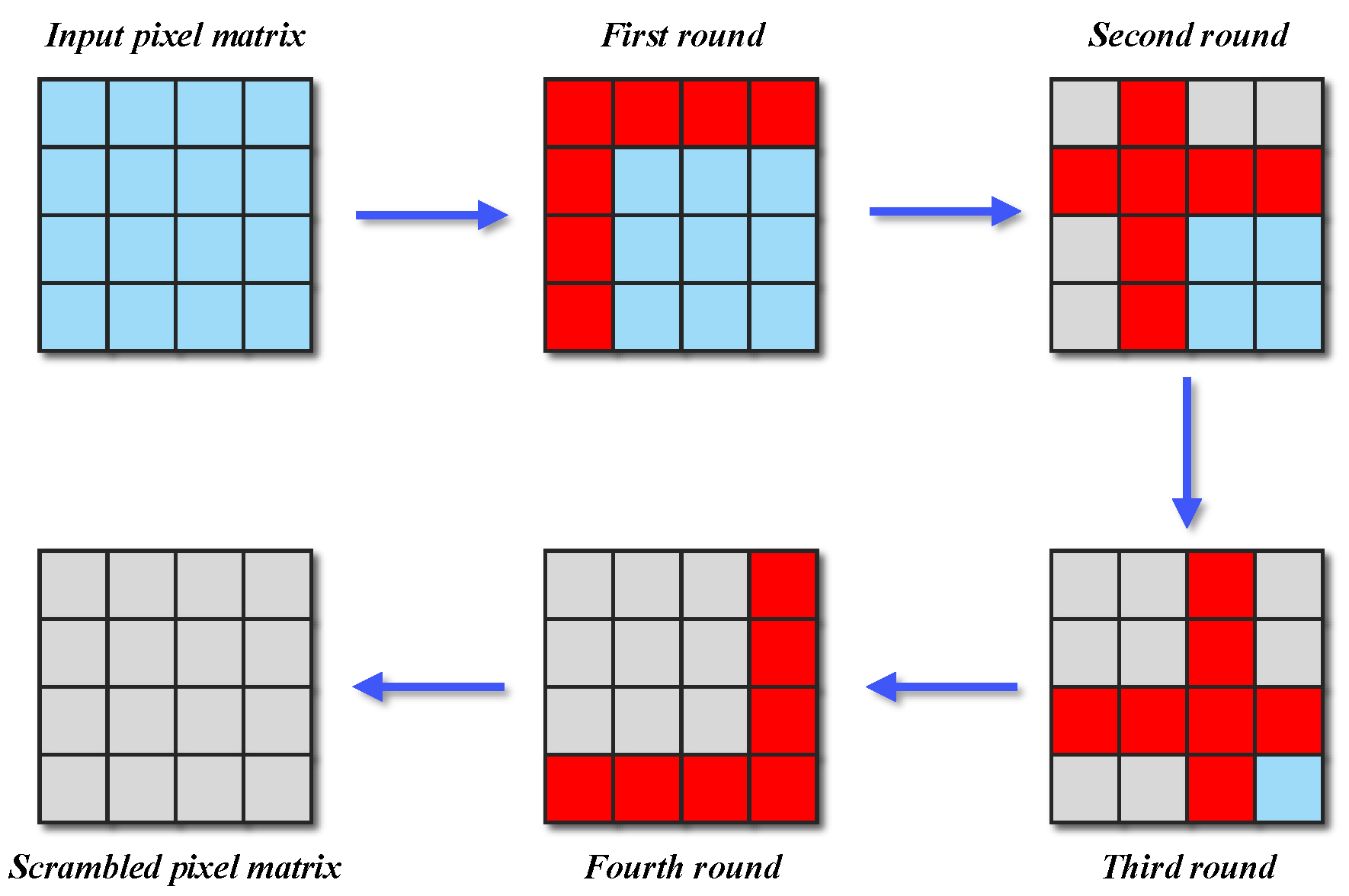
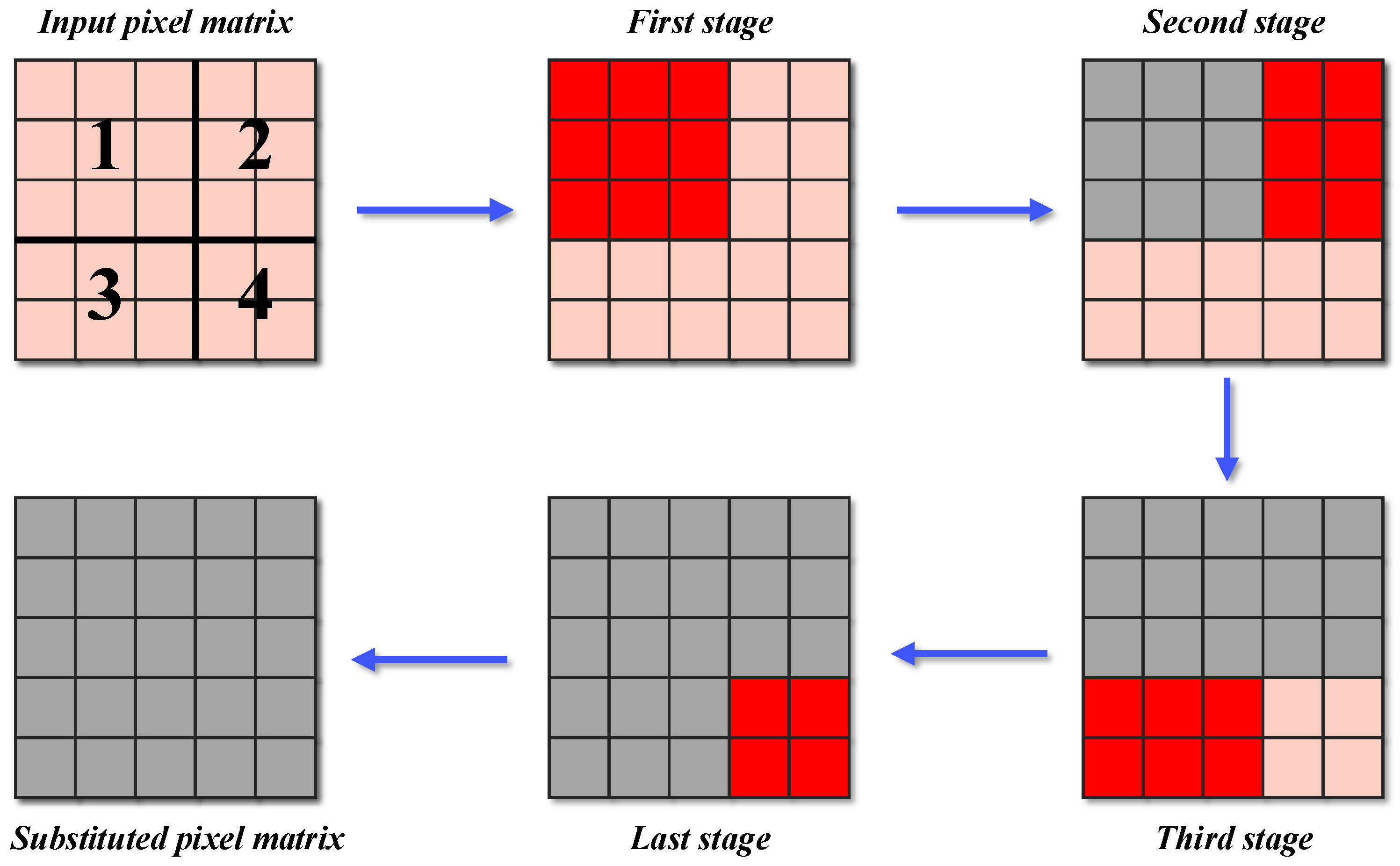
3.3. Row–Column Joint Scrambling
Scrambling or permutation operations constitute a pivotal component in modern cryptographic systems. In the context of image encryption algorithms, scrambling not only aids in reducing the correlation between adjacent pixels but also obscures the relationship between plaintext and ciphertext pixels, thereby enhancing the key sensitivity of image encryption algorithms [
49]. Consequently, within our proposed MIEA-PRHM, we have devised an encryption step termed row–column joint scrambling. Below, we introduce this novel scrambling operation with a simple illustrative example as depicted in
Figure 3.
This example demonstrates the row–column joint scrambling process for a
input pixel matrix. It can be observed that the scrambling process consists of a total of four rounds. Initially, the pixels in the first row and first column are scrambled together. These seven pixels undergo permutation collectively. Subsequently, the seven pixels in the second row and second column are scrambled. Immediately thereafter, the pixels in the third row and third column are scrambled as well. Finally, the pixels in the fourth row and fourth column undergo scrambling. As shown in
Figure 2, our proposed MIEA-PRHM performs row–column joint scrambling twice during the encryption process. Apart from the difference in input, there are no actual distinctions between these two scrambling steps. Therefore, we only provide the pseudocode for the first scrambling here as presented in Algorithm 1.
| Algorithm 1 Row–column joint scrambling of MIEA-PRHM. |
- Input:
The fused pixel matrix of size and the chaotic matrix of size . - 1:
; - 2:
for to do - 3:
; - 4:
; - 5:
; - 6:
; - 7:
; - 8:
; - 9:
; - 10:
; - 11:
; - 12:
end for - 13:
; - Output:
The scrambled pixel matrix .
|
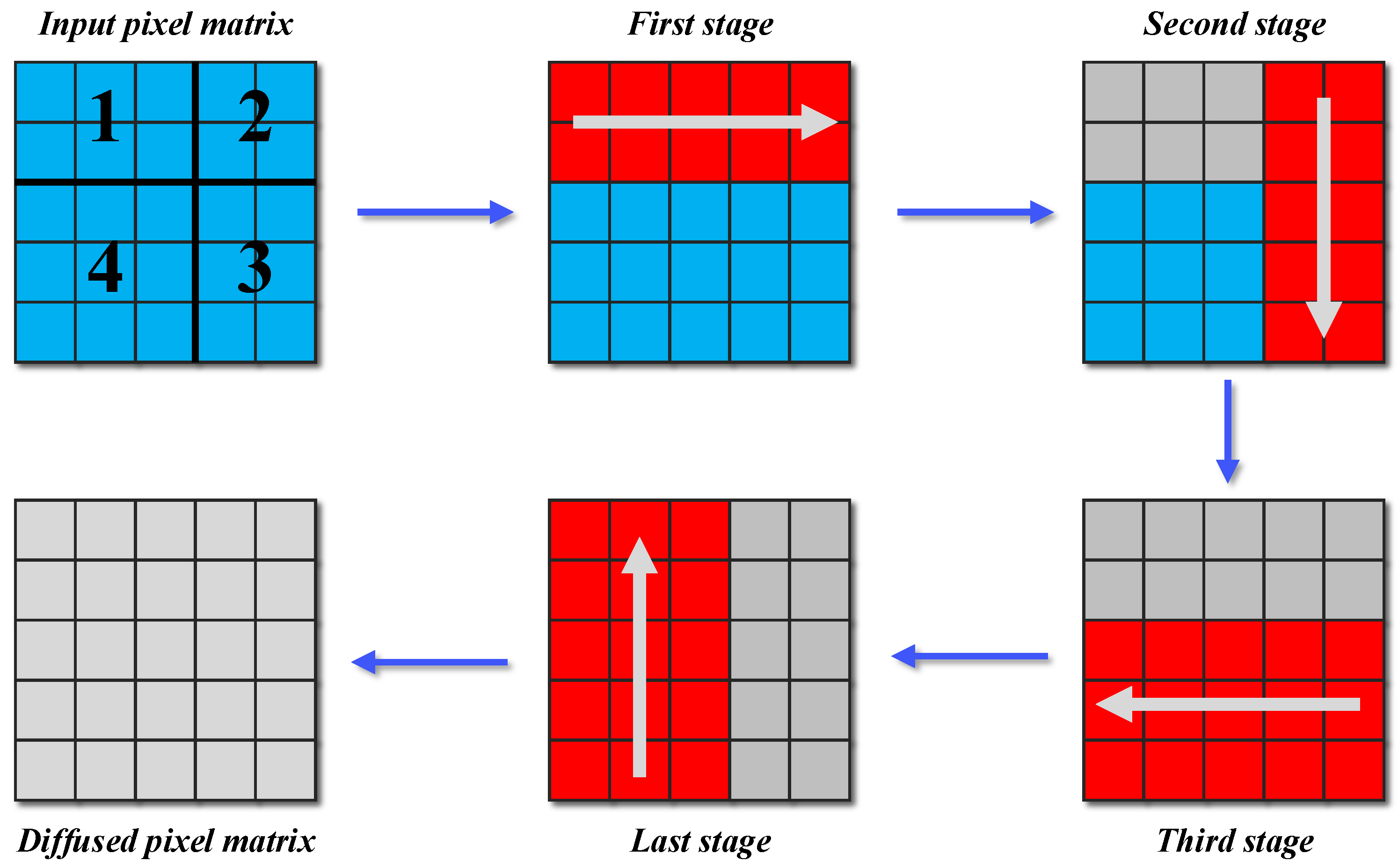
3.4. Vector-Level Dynamic Rotational Diffusion
Similarly to confusion, diffusion is one of the two fundamental principles advocated by Shannon for the design of cryptographic systems. Consequently, diffusion operations are indispensable in the design of image encryption algorithms. A well-designed diffusion operation will enhance the plaintext sensitivity and key sensitivity of the image encryption algorithm [
49]. In light of this, we have devised an encryption step named vector-level dynamic rotational diffusion within our MIEA-PRHM. In comparison to the diffusion operations employed in some recent image encryption algorithms, our diffusion operation has several notable advantages. Firstly, it operates at the vector level, facilitating a more efficient pixel diffusion process, thereby enhancing encryption efficiency. Secondly, the dynamism of it, which is contingent upon image sizes, plaintext-related parameters, and chaotic sequence values, significantly increases the difficulty for attackers to launch successful differential attacks. Lastly, during the rotational diffusion of pixels, the mathematical operations employed vary depending on the diffusion directions. This design fosters a more complex nonlinear relationship between ciphertext and plaintext pixels, which similarly facilitates the thwarting of various differential attacks, including plaintext attacks.
In
Figure 4, we provide a straightforward example to demonstrate the proposed vector-level dynamic rotational diffusion. Before initiating the diffusion process, we first determine a partitioning coordinate based on the input pixel matrix’s size, plaintext-related parameters, and chaotic sequence values. Specifically, in this example, the partitioning coordinate is
. Consequently, the input pixel matrix can be logically partitioned into four sub-blocks, named for convenience as logical sub-block 1, logical sub-block 2, logical sub-block 3, and logical sub-block 4. Subsequently, the diffusion of all pixels proceeds in four phases. In the first phase, the pixels within logical sub-blocks 1 and 2 are initially diffused. These pixels undergo horizontal diffusion from left to right in the form of column vectors. During the second phase, diffusion occurs in the regions occupied by logical sub-blocks 2 and 3, where pixels are vertically diffused from top to bottom in the form of row vectors. In the third phase, the pixels in logical sub-blocks 3 and 4 undergo diffusion in a manner similar to the first phase but with the opposite direction. During the final stage, the pixels within logical sub-blocks 1 and 4 are diffused in a bottom-to-top manner. As shown in
Figure 2, our proposed MIEA-PRHM algorithm performs row–column joint scrambling third times during the encryption process.
As can be seen in
Figure 2, our MIEA-PRHM algorithm incorporates three identical vector-level dynamic rotational diffusion steps in the encryption process, differing only in their input. Hence, we provide only the pseudocode for the initial diffusion step here, which is presented in Algorithm 2.
| Algorithm 2 Vector-level dynamic rotational diffusion of MIEA-PRHM. |
- Input:
The scrambled pixel matrix of size , the chaotic matrix of size , and the plaintext-related vector of size . - 1:
Perform XOR operations on all elements of and save the result to ; - 2:
= ; - 3:
; - 4:
; - 5:
; - 6:
; - 7:
for to W do - 8:
; - 9:
end for - 10:
; - 11:
for to H do - 12:
; - 13:
end for - 14:
; - 15:
; - 16:
for to 1 do - 17:
; - 18:
end for - 19:
; - 20:
for to 1 do - 21:
; - 22:
end for - Output:
The diffused pixel matrix .
|
3.5. Dual-Operation Dynamic Partition Substitution
Like permutation and diffusion operations, substitution operations play a crucial role in the construction of modern cryptographic systems. They significantly contribute to enhancing the nonlinearity of the encryption process [
49]. In numerous image encryption algorithms that rely on chaotic systems, substitution operations are typically carried out using single fixed mathematical operations. According to current cryptanalysis studies, such designs are vulnerable to plaintext attacks launched by attackers. Therefore, to further bolster the nonlinearity and security of the encryption process, we introduce an encryption step named dual-operation dynamic partition substitution in our MIEA-PRHM. Unlike some existing substitution operations, this encryption step possesses dynamic behavior that depends on both the plaintext and chaotic sequences. Additionally, it operates on partitioned sub-blocks while incorporating two mathematical operations. These features collectively reinforce the security of MIEA-PRHM, effectively safeguarding it against various potential attacks, especially the most threatening plaintext attacks.
Similarly, we illustrate our dual-operation dynamic partition substitution with a simple example as depicted in
Figure 5. First, we determine a partitioning coordinate based on the input chaotic sequence values and plaintext parameters. Utilizing this coordinate, the input pixel matrix is logically divided into four sub-blocks. Subsequently, these four sub-blocks will undergo substitution in distinct phases and manners. In our proposed MIEA-PRHM, we perform a total of two dual-operation dynamic partition substitutions as demonstrated in
Figure 2. Since the only distinction between these two substitution operations is the input parameters, we only provide the pseudocode for the substitution operation on
in Algorithm 3.
| Algorithm 3 Dual-operation dynamic partition substitution of MIEA-PRHM. |
- Input:
The diffused pixel matrix of size , the chaotic matrix of size , and the plaintext-related vector of size . - 1:
; - 2:
= ; - 3:
; - 4:
; - 5:
; - 6:
; - 7:
; - 8:
; - Output:
The substituted pixel matrix .
|
3.6. Entire Encryption and Decryption Process of MIEA-PRHM
Below, we provide a concise description of the entire encryption and decryption process, aiming to clearly illustrate the execution sequence for all encryption steps, along with their corresponding input and output. Let us consider a scenario where Alice (the sender) and Bob (the receiver) wish to transmit a batch of images over an insecure communication channel. The secret key that they have mutually agreed upon is . Initially, Alice proceeds with the encryption of the images as follows:
Step 1: Perform pixel reorganization on the input images to obtain two fused 2D pixel matrices
and
. For more information about pixel reorganization, please refer to
Section 3.1.
Step 2: Input the fused pixel matrices
and
into the SHA-256 algorithm to generate a 256-bit hash value
. Then, convert the hash value
into a plaintext-related vector
. More details on generating the plaintext-related vector
can be found in
Section 2.4.
Step 3: Utilize the secret key
to generate the four chaotic matrices
,
,
, and
. For more information about generating chaotic matrices, please refer to
Section 3.2.
Step 4: Employ the chaotic matrix
to perform row–column joint scrambling on the fused pixel matrix
to obtain the scrambled pixel matrix
. More details on row–column joint scrambling can be found in
Section 3.3.
Step 5: Utilize the plaintext-related vector
and the chaotic matrix
to perform vector-level dynamic rotational diffusion on the scrambled pixel matrix
. The output obtained is the diffused pixel matrix
. For more information about vector-level dynamic rotational diffusion, please refer to
Section 3.4.
Step 6: Employ the plaintext-related vector
and the chaotic matrix
to perform dual-operation dynamic partition substitution on the diffused pixel matrix
. The output obtained is the substituted pixel matrix
. More details on perform dual-operation dynamic partition substitution can be found in
Section 3.5.
Step 7: Utilize the plaintext-related vector and the chaotic matrix to perform vector-level dynamic rotational diffusion on the substituted pixel matrix . The output obtained is the diffused pixel matrix .
Step 8: Employ the chaotic matrix to perform row–column joint scrambling on the diffused pixel matrix to obtain the scrambled pixel matrix .
Step 9: Utilize the plaintext-related vector and the chaotic matrix to perform dual-operation dynamic partition substitution on the fused pixel matrix . The output obtained is the substituted pixel matrix .
Step 10: Employ the plaintext-related vector and the chaotic matrix to perform vector-level dynamic rotational diffusion on the substituted pixel matrix . The output obtained is the diffused pixel matrix .
Step 11: Perform inverse pixel reorganization on the two ciphertext pixel matrices and to obtain the final ciphertext images.
Subsequently, Alice sends the final ciphertext images, along with the hash value
, to Bob via the insecure communication channel. Upon receiving them, Bob proceeds to decrypt the ciphertext images according to the decryption process depicted in
Figure 6, ultimately acquiring the necessary decrypted images. By examining
Figure 6, one can clearly see that the decryption process of MIEA-PRHM is the mirror image of its encryption process. Each decryption step corresponds directly to an encryption step, and is essentially the reverse of its counterpart. Since there are no significant differences, we will, for brevity’s sake, omit the redundant description of these decryption steps here.
5. Conclusions
To address the security concerns, efficiency issues, and practical limitations identified in some recently reported encryption algorithms, we have meticulously designed a novel multi-channel image encryption algorithm called MIEA-PRHM. This encryption algorithm utilizes two robust hyperchaotic maps, 2D-SCPM and 2D-ELMM, to jointly generate chaotic sequences. This design enables MIEA-PRHM to possess a larger key space and better output randomness. Subsequently, a series of dynamic vector-level encryption steps, including row–column joint scrambling, vector-level dynamic rotational diffusion, and dual-operation dynamic partition substitution, further transform these matrices into indistinguishable noise-like ciphertext images.
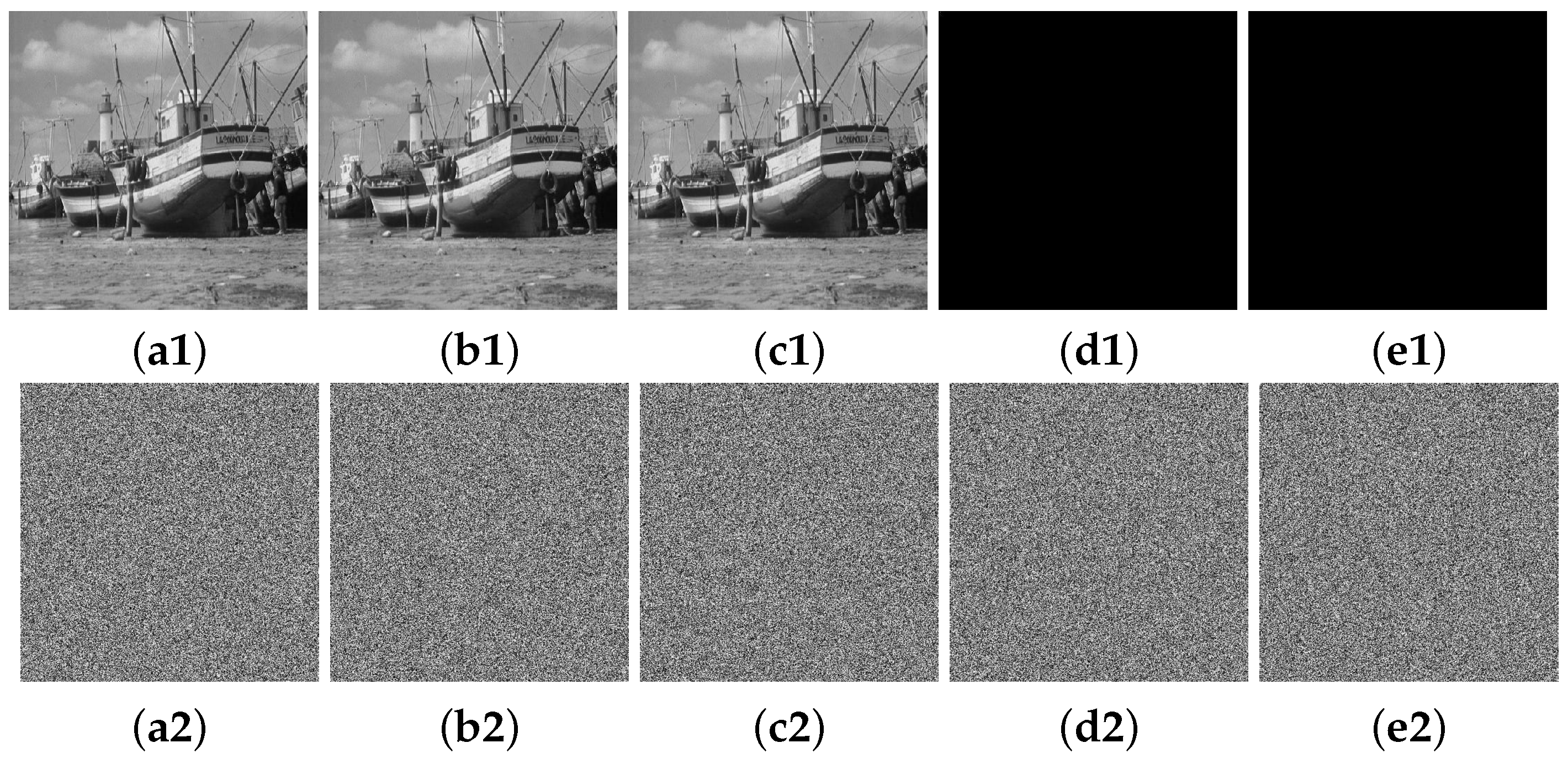
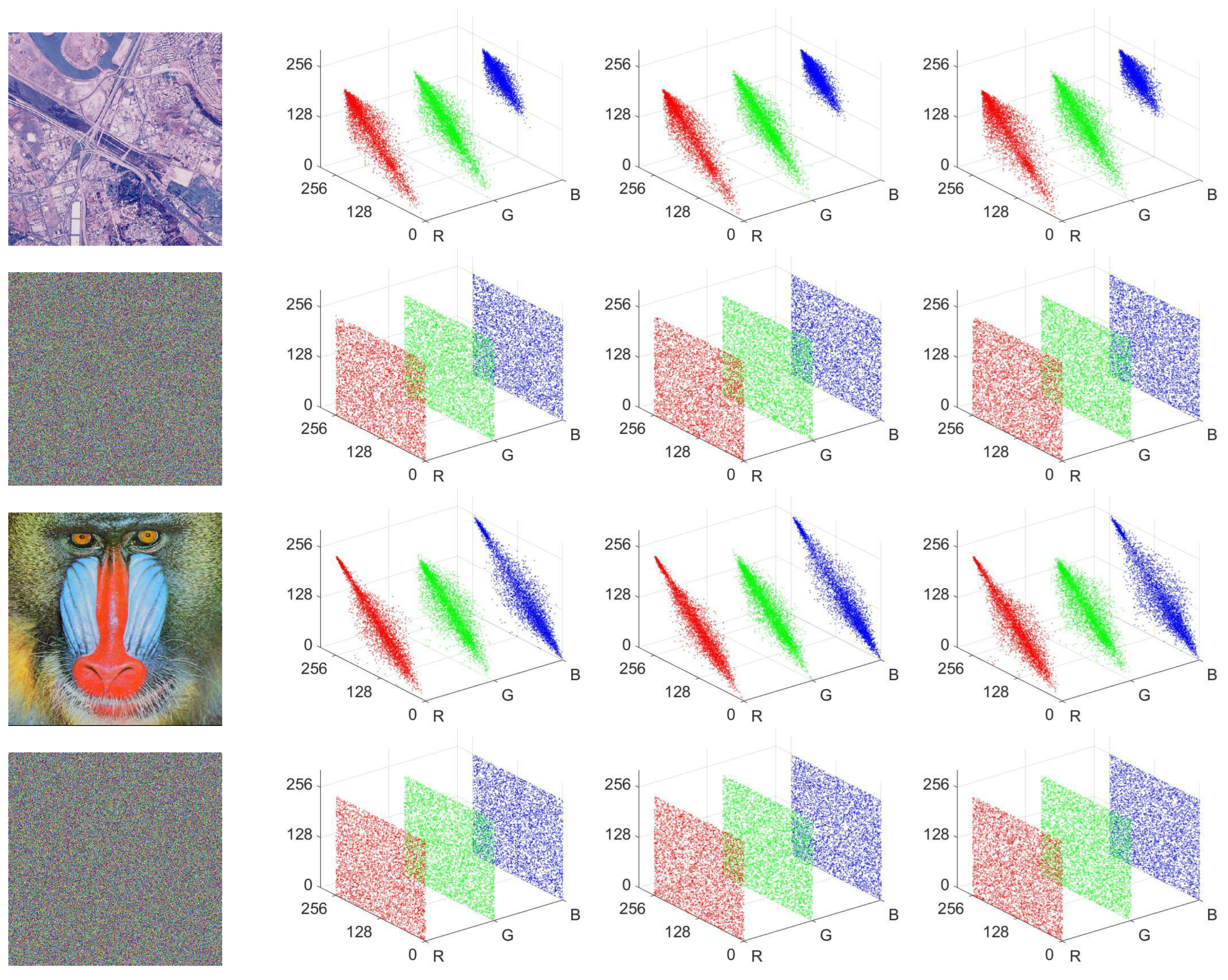
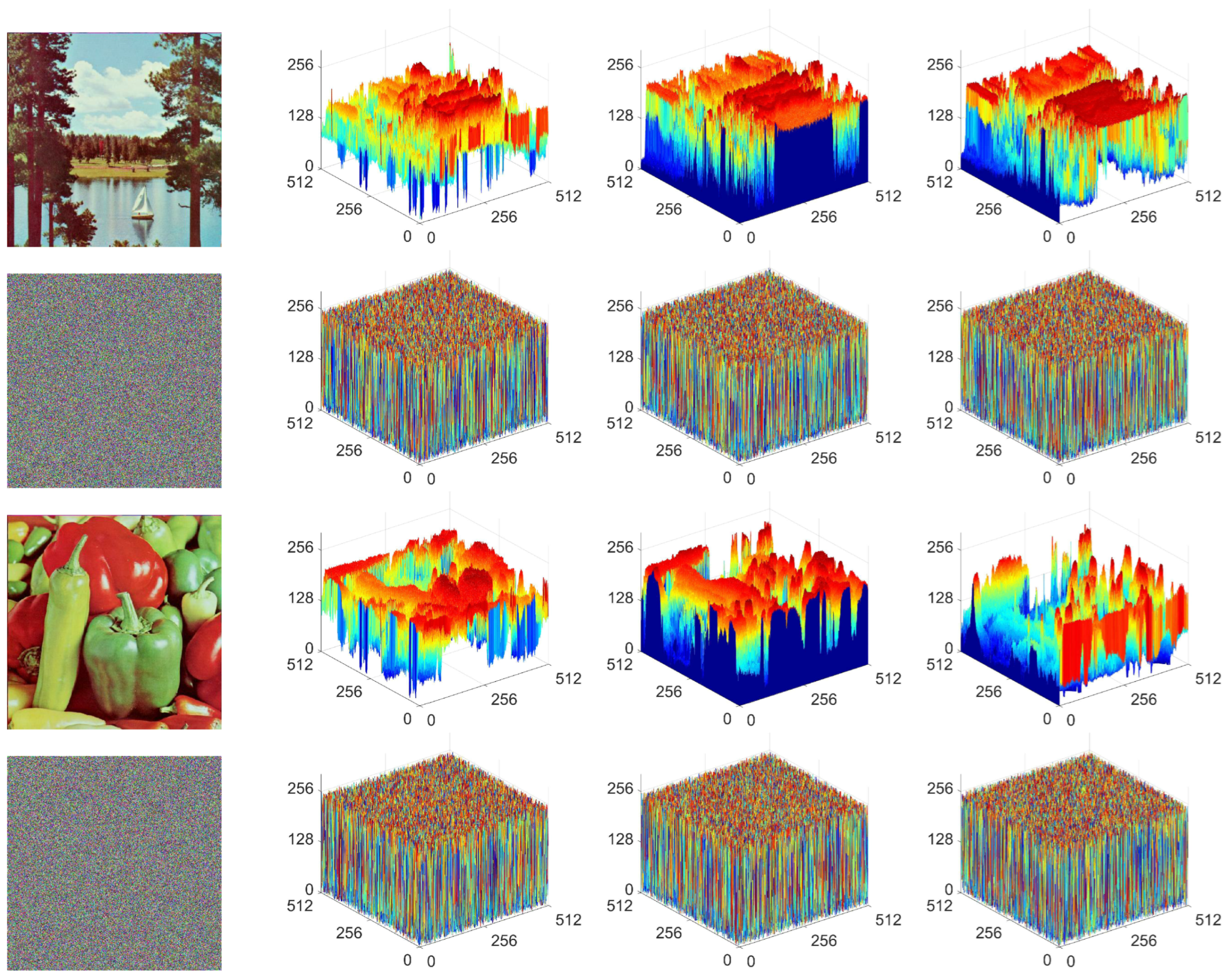
We have conducted extensive experiments and analyses to evaluate the encryption performance of MIEA-PRHM. Our proposed MIEA-PRHM exhibits outstanding performance across a range of performance evaluation metrics, including key space (), plaintext sensitivity (99.6096% and 33.4641%), pixel correlation (<0.002), information entropy (>7.999), pixel distribution (<293.2478), and encryption efficiency (60.9447 Mbps). Numerous experimental results and comparative analyses demonstrate that MIEA-PRHM outperforms many recently reported encryption algorithms, offering higher security and excellent encryption efficiency.
In the future, we will continue to optimize MIEA-PRHM and introduce more new techniques and methodologies to make it more secure and efficient. Furthermore, we will also endeavor to apply MIEA-PRHM to other multimedia data requiring protection, such as audio and video.