An Efficient Fractional Chebyshev Chaotic Map-Based Three-Factor Session Initiation Protocol for the Human-Centered IoT Architecture
Abstract
1. Introduction
1.1. Research Contributions
- ▪
- An efficient and secure remote authentication scheme for a SIP is proposed using extended FCCM, a smart card (SC), and user biometrics simultaneously in the HC-IoT environment.
- ▪
- An informal security analysis of the projected protocol is demonstrated, and the results show that it is provably secure in the ROR model.
- ▪
- A comparison of the projected protocol with related authentication protocols is conducted and it is found that it is cost-efficient and requires fewer computational resources. This is because the presented approach uses FCCM, which eliminates computationally intensive elliptic curve point multiplication.
1.2. Organization of Manuscript
2. Related Work
3. Background and Material
3.1. Hash Function
3.2. Chebyshev Chaotic Maps
- Chaotic map-based discrete logarithm problem (CMDLP): For any given x and y, it is not computationally feasible to calculate the integer n such that
- Chaotic map-based computational Diffie–Hellman problem (CMDHP): It is not computationally feasible to compute , for three elements and .
3.3. Fractal Chaotic Maps (FCM)
3.4. Possessions of Fractal Chaotic Maps with Extension
3.5. Biometrics and Fuzzy Extractor
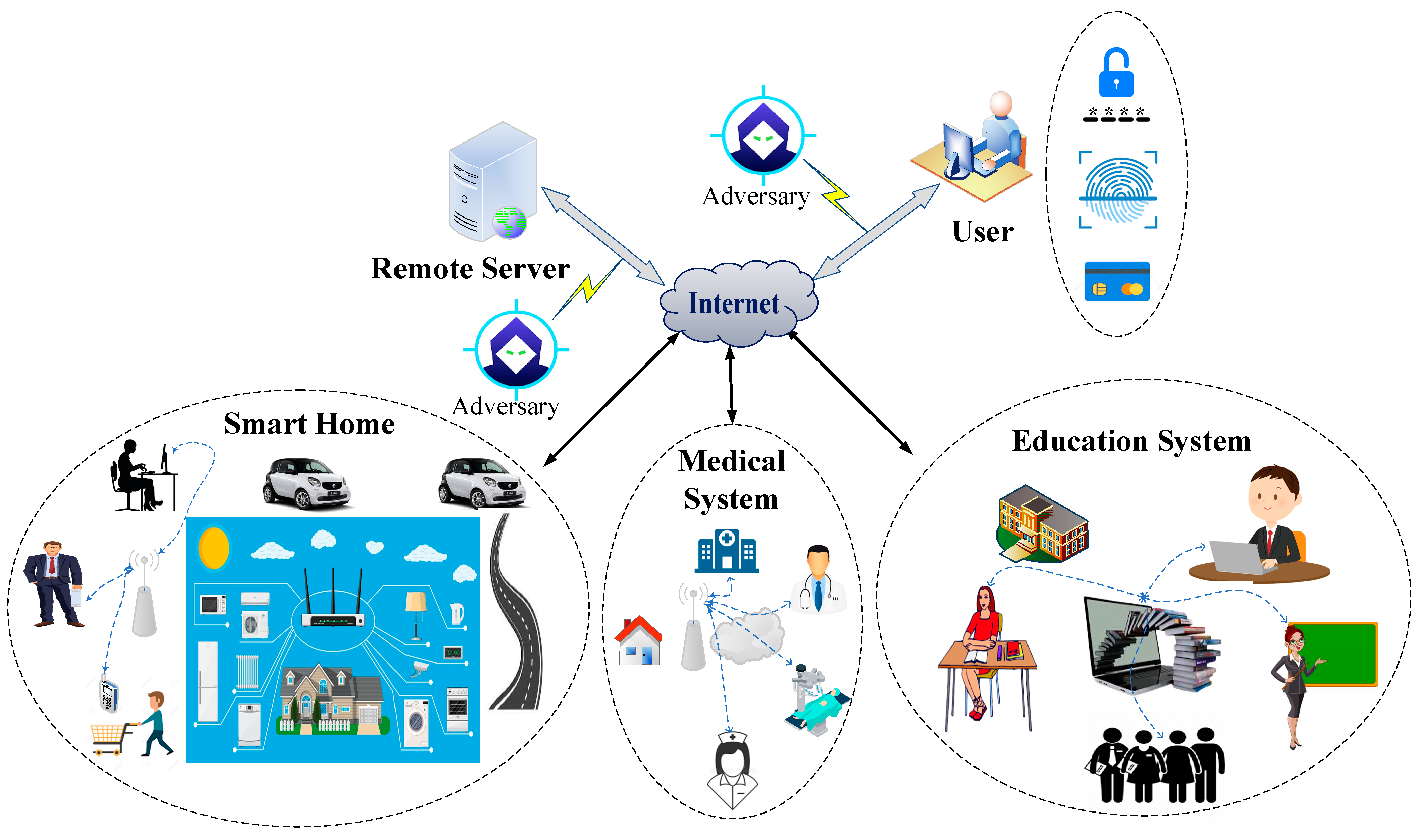
4. The Proposed Three-Factor SIP Scheme Based on FCCM under the HCIoT Environment
4.1. Setup Stage
- Step 1.
- The picks as its secret key.
- Step 2.
- and a secure hash function are computed by the using a random number and rational number
- Step 3.
- The makes the constraints available to all legal users.
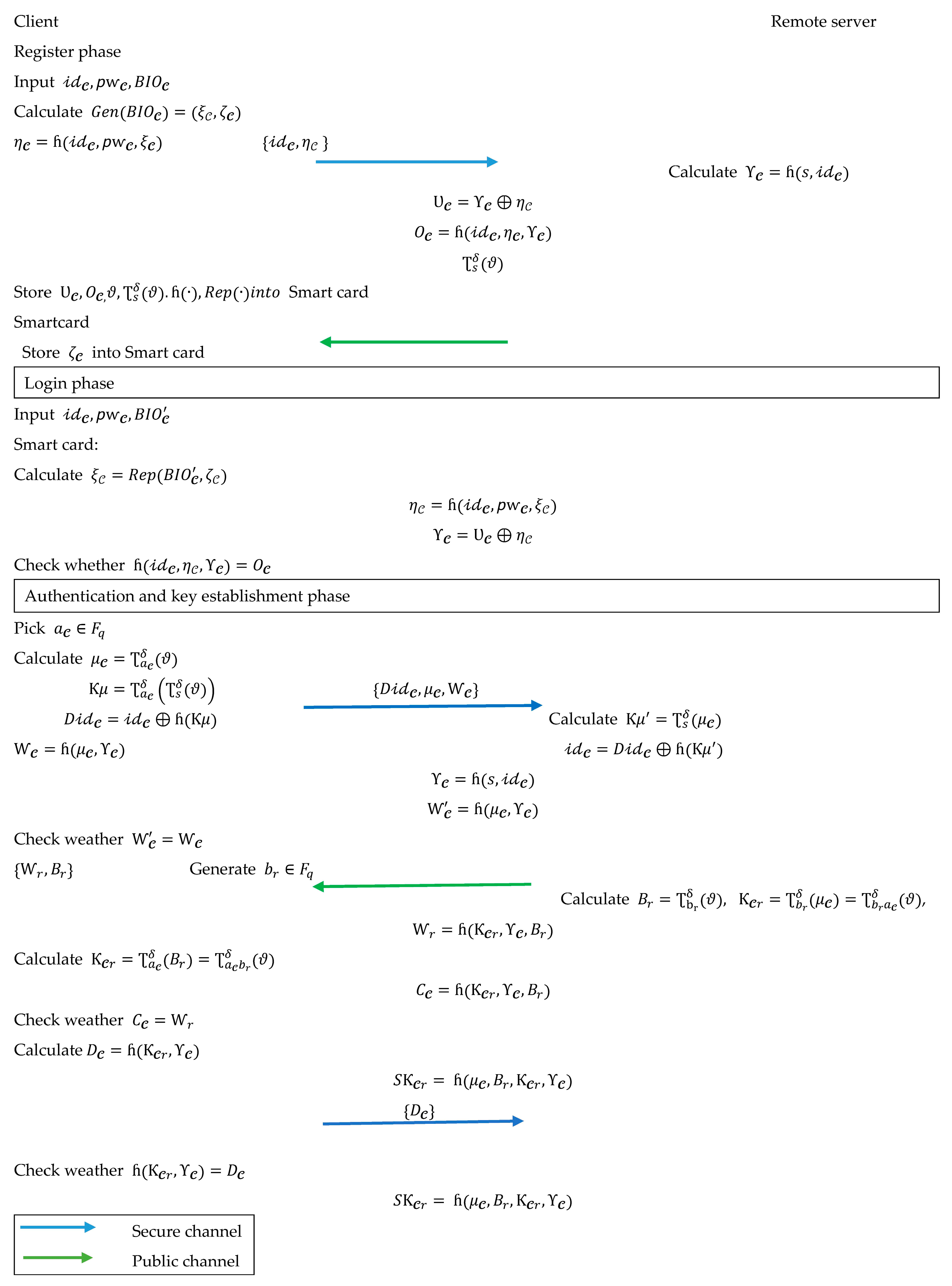
4.2. Registration Stage
- Step 1.
- The scans her/his biometrics using a biometric scanner gadget. The picks an , as well as a password . Then, he/she computes and , and sends , through a secure channel to the .
- Step 2.
- When the registration message is received, the usages its private key s and to calculate , , and . Then, the stores into a and transmits it to the over a protected channel.
- Step 3.
- When the receives the , he/she writes on it.
4.3. Login Stage
- Step 1.
- The enters his/her and into the terminal contraption before allowing a scan to obtain his/her biometrics . In addition, the must use the terminal card reader to input his/her .
- Step 2.
- The calculates , , , and . If , the exits this stage, and the ’s login request is rejected. Otherwise, the next phase is carried out by both the and the .
4.4. Authentication and Key Formation Stage
- Step 1.
- The ’s picks an arbitrary number and computes and . The uses a public channel to send a request message to the .
- Step 2.
- The computes , , and after receiving the request message . If is equal to the computed value . If the verification fails, the immediately rejects this stage. Otherwise, the selects an arbitrary number and computes , and . Over a public channel, the sends to the .
- Step 3.
- When the receives , it computes and . The validates the correctness of by comparing to . If , the aborts the session; otherwise, it calculates and transmits the answer message to the through a public channel. Then, calculates the .
- Step 4.
- When the gets from the ’s smart card, it computes and compares to the calculated value. If , the calculates the . Figure 3 depicts the registration, login, authentication, and key establishment processes.
4.5. Password and Biometrics Change Stage
- Step 1.
- The inserts the into the card reader and enters the credentials and . Then, the uses a biometric scanner gadget to scan her/his biometrics .
- Step 2.
- The smart card calculates , and . Then, the smart card checks to see if the calculated is similar to . If the conditions are met, the can change the existing and . Otherwise, the request can be denied.
- Step 3.
- The updates the smart card with a new password and biometrics . Then, the smart card computes , as well as , , and . The smart card replaces the tuple with the new tuple .
5. Security Examination of the Proposed Protocol
5.1. The ROR Model for Session Key Security
- Participants
- b.
- Partnering
- c.
- Adversary
- : is obtained by via the query.
- : The query allows to obtain data from ’s Smart card.
- : Through the query, obtains ’s biometrics .
- d.
- Semantic Security
5.2. The Proof of Security
- Case 1:
- Assume sends a query to corrupt to guess the real password. The probability is because there are chances to send inquiries and passwords.
- Case 2:
- Assume inquiries corrupt to crack . There are two subcases to consider:
- (a)
- Within , guesses Send queries. is the probability.
- (b)
- tries the event of “false positive” with send inquiries using her/his biometrics. is the probability.
5.3. Informal Security Examination and Discussion
5.3.1. User Anonymity
5.3.2. User Untraceability
5.3.3. Impersonation Attack
5.3.4. Offline Password Guessing Attack
5.3.5. Known Key Secrecy
5.3.6. Temporary Information Attack on Known Sessions
5.3.7. Privileged-Insider Attack
5.3.8. Password and Biometrics Change Attack
5.3.9. Efficient Password and Biometrics Change
5.3.10. Three-Factor Confidentiality
- If the user’s smart card and biometrics are revealed, the adversary attempts to crack the password. On the one hand, the parameters and are obtained by the , where and . The , on the other hand, is unable to reveal because , where is known only to the and is known only to the user.
- If the user’s smart card and password are revealed, on the one hand, the obtains the parameters , and , where and . The , on the other hand, is unable to deduce from and because it must simultaneously guess correct , and .
- The tries to crack the smart card’s specifications if the biometrics and password are disclosed. Because is unavailable, retrieving the critical factor is impossible.
5.3.11. Clock Synchronization Issue
6. Performance Evaluation
6.1. Computation Cost Analysis
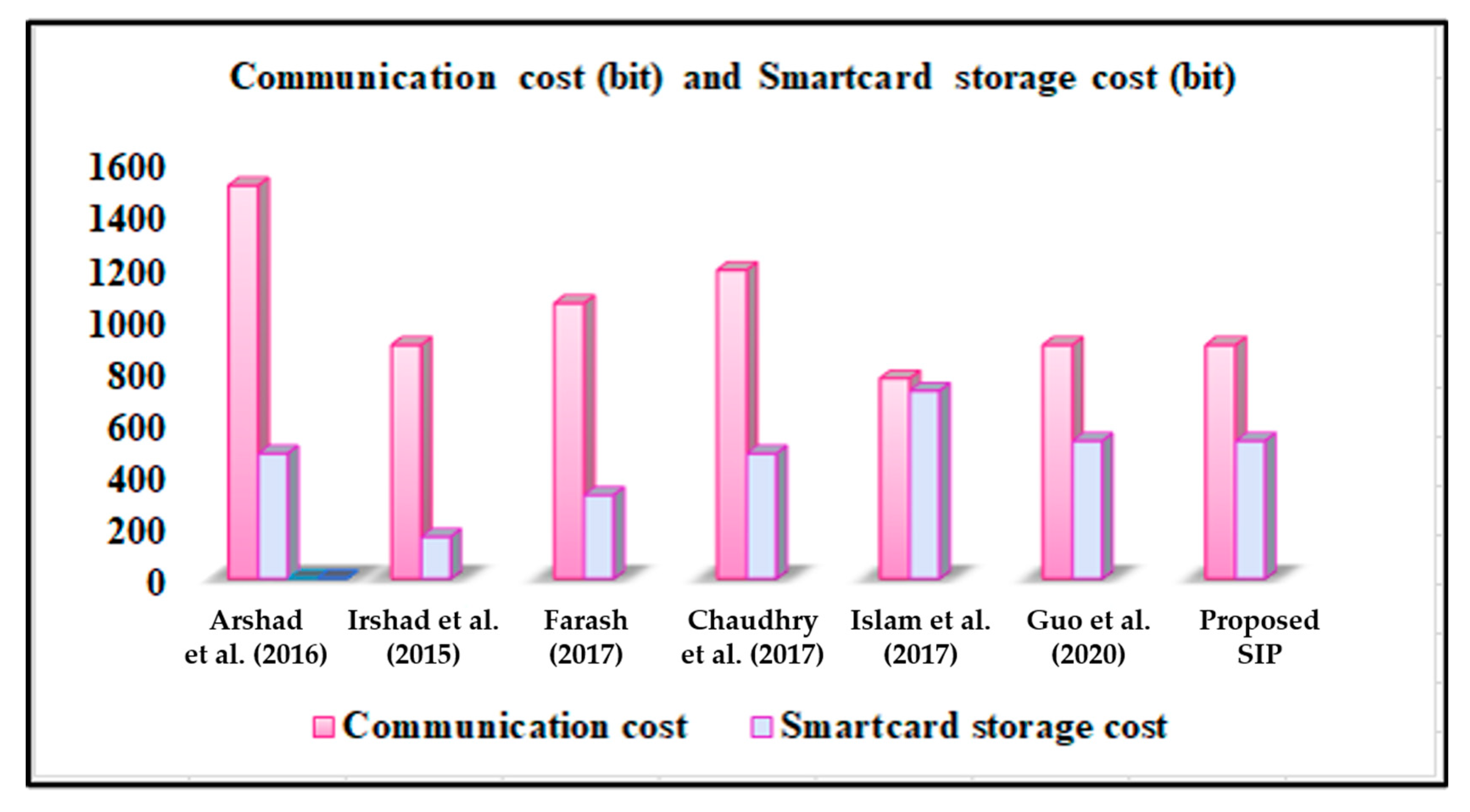
6.2. Communication Cost and Smart Card Storage Assessment
6.3. Analysis of Security and Functionality
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Yeh, H.-L.; Chen, T.-H.; Shih, W.-K. Robust smart card secured authentication scheme on SIP using elliptic curve cryptography. Comput. Stand. Interfaces 2014, 36, 397–402. [Google Scholar] [CrossRef]
- He, D.; Chen, J.; Chen, Y. A secure mutual authentication scheme for session initiation protocol using elliptic curve cryptography. Secur. Commun. Netw. 2012, 5, 1423–1429. [Google Scholar] [CrossRef]
- Guo, X.Y.; Sun, D.Z.; Yang, Y. An Improved Three-Factor Session Initiation Protocol Using Chebyshev Chaotic Map. IEEE Access 2020, 8, 111265–111277. [Google Scholar] [CrossRef]
- Yoon, E.-J.; Shin, Y.-N.; Jeon, I.-S.; Yoo, K.-Y. Robust mutual authentication with a key agreement scheme for the session initiation protocol. IETE Tech. Rev. 2010, 27, 203–213. [Google Scholar] [CrossRef]
- Kilinc, H.H.; Yanik, T. A survey of SIP authentication and key agreement schemes. IEEE Commun. Surv. Tutor. 2013, 16, 1005–1023. [Google Scholar] [CrossRef]
- Arshad, H.; Nikooghadam, M. An efficient and secure authentication and key agreement scheme for session initiation protocol using ECC. Multimed. Tools Appl. 2016, 75, 181–197. [Google Scholar] [CrossRef]
- Febro, A.; Xiao, H.; Spring, J.; Christianson, B. Edge security for SIP-enabled IoT devices with P4. Comput. Netw. 2022, 203, 108698. [Google Scholar] [CrossRef]
- Xie, Q.; Tang, Z. Biometrics based authentication scheme for session initiation protocol. Springerplus 2016, 5, 1–14. [Google Scholar] [CrossRef]
- Arshad, R.; Ikram, N. Elliptic curve cryptography based mutual authentication scheme for session initiation protocol. Multimed. Tools Appl. 2013, 66, 165–178. [Google Scholar] [CrossRef]
- Tang, H.; Liu, X. Cryptanalysis of Arshad et al.’s ECC-based mutual authentication scheme for session initiation protocol. Multimed. Tools Appl. 2013, 65, 321–333. [Google Scholar] [CrossRef]
- Irshad, A.; Sher, M.; Faisal, M.S.; Ghani, A.; Ul Hassan, M.; Ashraf, C.S. A secure authentication scheme for session initiation protocol by using ECC on the basis of the Tang and Liu scheme. Secur. Commun. Netw. 2014, 7, 1210–1218. [Google Scholar] [CrossRef]
- Zhang, L.; Tang, S.; Cai, Z. Efficient and flexible password authenticated key agreement for voice over internet protocol session initiation protocol using smart card. Int. J. Commun. Syst. 2014, 27, 2691–2702. [Google Scholar] [CrossRef]
- Irshad, A.; Sher, M.; Rehman, E.; Ch, S.A.; Hassan, M.U.; Ghani, A. A single round-trip sip authentication scheme for voice over internet protocol using smart card. Multimed. Tools Appl. 2015, 74, 3967–3984. [Google Scholar] [CrossRef]
- Kumari, S.; Chaudhry, S.A.; Wu, F.; Li, X.; Farash, M.S.; Khan, M.K. An improved smart card based authentication scheme for session initiation protocol. Peer-to-Peer Netw. Appl. 2017, 10, 92–105. [Google Scholar] [CrossRef]
- Farash, M.S. Security analysis and enhancements of an improved authentication for session initiation protocol with provable security. Peer-to-Peer Netw. Appl. 2016, 9, 82–91. [Google Scholar] [CrossRef]
- Naqvi, H.; Chaudhry, S.A.; Mahmood, K. An improved authentication protocol for SIP-based VoIP. In Proceedings of the International Conference on Recent Advances in Computer Systems (RACS 2015), Hail, Saudi Arabia, 30 November–1 December 2015; pp. 7–12. [Google Scholar]
- Mishra, D.; Das, A.K.; Mukhopadhyay, S. A secure and efficient ECC-based user anonymity-preserving session initiation authentication protocol using smart card. Peer-to-Peer Netw. Appl. 2016, 9, 171–192. [Google Scholar] [CrossRef]
- Farash, M.S. An improved password-based authentication scheme for session initiation protocol using smart cards without verification table. Int. J. Commun. Syst. 2017, 30, e2879. [Google Scholar] [CrossRef]
- Chaudhry, S.A.; Naqvi, H.; Sher, M.; Farash, M.S.; Hassan, M.U. An improved and provably secure privacy preserving authentication protocol for SIP. Peer-to-Peer Netw. Appl. 2017, 10, 1–15. [Google Scholar] [CrossRef]
- Islam, S.K.H.; Rajeev, V.; Amin, R. A robust and efficient three-factor authentication and session key agreement mechanism for SIP. In Proceedings of the 2017 Second International Conference on Recent Trends and Challenges in Computational Models (ICRTCCM), IEEE, Tindivanam, India, 3–4 February 2017; pp. 286–291. [Google Scholar]
- Reddy, A.G.; Yoon, E.-J.; Das, A.K.; Yoo, K.-Y. An enhanced anonymous two-factor mutual authentication with key-agreement scheme for session initiation protocol. In Proceedings of the 9th International Conference on Security of Information and Networks, Newark, NJ, USA, 20–22 July 2016; pp. 145–149. [Google Scholar]
- Lu, Y.; Li, L.; Peng, H.; Yang, Y. An anonymous two-factor authenticated key agreement scheme for session initiation protocol using elliptic curve cryptography. Multimed. Tools Appl. 2017, 76, 1801–1815. [Google Scholar] [CrossRef]
- Meshram, C.; Imoize, A.L.; Aljaedi, A.; Alharbi, A.R.; Jamal, S.S.; Barve, S.K. A Provably Secure IBE Transformation Model for PKC Using Conformable Chebyshev Chaotic Maps under Human-Centered IoT Environments. Sensors 2021, 21, 7227. [Google Scholar] [CrossRef]
- Meshram, C.; Obaidat, M.S.; Tembhurne, J.V.; Shende, S.W.; Kalare, K.W.; Meshram, S.G. A Lightweight Provably Secure Digital Short-Signature Technique Using Extended Chaotic Maps for Human-Centered IoT Systems. IEEE Syst. J. 2020, 15, 5507–5515. [Google Scholar] [CrossRef]
- Meshram, C.; Imoize, A.L.; Jamal, S.S.; Alharbi, A.R.; Meshram, S.G.; Hussain, I. CGST: Provably Secure Lightweight Certificateless Group Signcryption Technique Based on Fractional Chaotic Maps. IEEE Access 2022, 10, 39853–39863. [Google Scholar] [CrossRef]
- Dharminder, D.; Kumar, U.; Gupta, P. A construction of a conformal Chebyshev chaotic map based authentication protocol for healthcare telemedicine services. Complex Intell. Syst. 2021, 7, 2531–2542. [Google Scholar] [CrossRef]
- Dhillon, P.K.; Kalra, S. Secure and efficient ECC based SIP authentication scheme for VoIP communications in internet of things. Multimed. Tools Appl. 2019, 78, 22199–22222. [Google Scholar] [CrossRef]
- Farash, M.S.; Kumari, S.; Bakhtiari, M. Cryptanalysis and improvement of a robust smart card secured authentication scheme on SIP using elliptic curve cryptography. Multimed. Tools Appl. 2016, 75, 4485–4504. [Google Scholar] [CrossRef]
- Azrour, M.; Ouanan, M.; Farhaoui, Y. A new secure SIP authentication scheme based on elliptic curve cryptography. In Proceedings of the International Conference on Information Technology and Communication Systems, Churibka, Morocco, 28–29 March 2017; Springer: Berlin/Heidelberg, Germany, 2017; pp. 155–170. [Google Scholar]
- Sureshkumar, V.; Amin, R.; Anitha, R. A robust mutual authentication scheme for session initiation protocol with key establishment. Peer-to-Peer Netw. Appl. 2018, 11, 900–916. [Google Scholar] [CrossRef]
- Nikooghadam, M.; Amintoosi, H. A secure and robust elliptic curve cryptography-based mutual authentication scheme for session initiation protocol. Secur. Priv. 2020, 3, e92. [Google Scholar] [CrossRef]
- Lin, H.; Wen, F.; Du, C. An anonymous and secure authentication and key agreement scheme for session initiation protocol. Multimed. Tools Appl. 2017, 76, 2315–2329. [Google Scholar] [CrossRef]
- Wu, L.; Zhang, Y.; Wang, F. A new provably secure authentication and key agreement protocol for SIP using ECC. Comput. Stand. Interfaces 2009, 31, 286–291. [Google Scholar] [CrossRef]
- Chen, C.-M.; Xiang, B.; Wang, K.-H.; Yeh, K.-H.; Wu, T.-Y. A robust mutual authentication with a key agreement scheme for session initiation protocol. Appl. Sci. 2018, 8, 1789. [Google Scholar] [CrossRef]
- Islam, S.K.H.; Vijayakumar, P.; Bhuiyan, M.Z.A.; Amin, R.; Balusamy, B. A provably secure three-factor session initiation protocol for multimedia big data communications. IEEE Internet Things J. 2017, 5, 3408–3418. [Google Scholar] [CrossRef]
- Zhang, L.; Tang, S.; Zhu, S. A lightweight privacy preserving authenticated key agreement protocol for SIP-based VoIP. Peer-to-Peer Netw. Appl. 2016, 9, 108–126. [Google Scholar] [CrossRef]
- Tu, H.; Kumar, N.; Chilamkurti, N.; Rho, S. An improved authentication protocol for session initiation protocol using smart card. Peer-to-Peer Netw. Appl. 2015, 8, 903–910. [Google Scholar] [CrossRef]
- Wang, D.; He, D.; Wang, P.; Chu, C.-H. Anonymous two-factor authentication in distributed systems: Certain goals are beyond attainment. IEEE Trans. Dependable Secur. Comput. 2014, 12, 428–442. [Google Scholar] [CrossRef]
- Maitra, T.; Giri, D.; Mohapatra, R.N. SAS-SIP: A secure authentication scheme based on ECC and a fuzzy extractor for session initiation protocol. Cryptologia 2019, 43, 212–232. [Google Scholar] [CrossRef]
- Hassan, M.U.; Chaudhry, S.A.; Irshad, A. An Improved SIP Authenticated Key Agreement Based on Dongqing et al. Wirel. Pers. Commun. 2020, 110, 2087–2107. [Google Scholar] [CrossRef]
- Meshram, C.; Ibrahim, R.W.; Obaidat, M.S.; Sadoun, B.; Meshram, S.G.; Tembhurne, J. V An effective mobile-healthcare emerging emergency medical system using conformable chaotic maps. Soft Comput. 2021, 25, 8905–8920. [Google Scholar] [CrossRef]
- Tiwari, D.; Gangadharan, G.R. SecAuth-SaaS: A hierarchical certificateless aggregate signature for secure collaborative SaaS authentication in cloud computing. J. Ambient Intell. Humaniz. Comput. 2021, 12, 10539–10563. [Google Scholar] [CrossRef]
- Mandal, S.; Bera, B.; Sutrala, A.K.; Das, A.K.; Choo, K.K.R.; Park, Y.H. Certificateless-Signcryption-Based Three-Factor User Access Control Scheme for IoT Environment. IEEE Internet Things J. 2020, 7, 3184–3197. [Google Scholar] [CrossRef]
- Gaikwad, V.P.; Tembhurne, J.V.; Meshram, C.; Lee, C.-C. Provably secure lightweight client authentication scheme with anonymity for TMIS using chaotic hash function. J. Supercomput. 2021, 77, 8281–8304. [Google Scholar] [CrossRef]
- Meshram, C.; Imoize, A.L.; Aljaedi, A.; Alharbi, A.R.; Jamal, S.S.; Barve, S.K. An Efficient Electronic Cash System Based on Certificateless Group Signcryption Scheme Using Conformable Chaotic Maps. Sensors 2021, 21, 7039. [Google Scholar] [CrossRef] [PubMed]
- Meshram, C.; Ibrahim, R.W.; Obaid, A.J.; Meshram, S.G.; Meshram, A.; Abd El-Latif, A.M. Fractional chaotic maps based short signature scheme under human-centered IoT environments. J. Adv. Res. 2021, 32, 139–148. [Google Scholar] [CrossRef]
- Meshram, C.; Obaidat, M.S.; Lee, C.-C.; Meshram, S.G. An Efficient, Robust, and Lightweight Subtree-Based Three-Factor Authentication Procedure for Large-Scale DWSN in Random Oracle. IEEE Syst. J. 2021, 15, 4927–4938. [Google Scholar] [CrossRef]
- Yang, X.-J.; Baleanu, D.; Srivastava, H.M. Local Fractional Integral Transforms and Their Applications; Academic Press: Cambridge, MA, USA, 2015; ISBN 0128040327. [Google Scholar]
- Han, S.; Chang, E. Chaotic map based key agreement with/out clock synchronization. Chaos Solitons Fractals 2009, 39, 1283–1289. [Google Scholar] [CrossRef]
- Abdalla, M.; Fouque, P.-A.; Pointcheval, D. Password-based authenticated key exchange in the three-party setting. IEE Proc. Inf. Secur. 2006, 153, 27–39. [Google Scholar] [CrossRef]
- Dua, A.; Kumar, N.; Das, A.K.; Susilo, W. Secure message communication protocol among vehicles in smart city. IEEE Trans. Veh. Technol. 2017, 67, 4359–4373. [Google Scholar] [CrossRef]
- Das, A.K.; Wazid, M.; Kumar, N.; Khan, M.K.; Choo, K.-K.R.; Park, Y. Design of secure and lightweight authentication protocol for wearable devices environment. IEEE J. Biomed. Health Inform. 2017, 22, 1310–1322. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Odelu, V.; Kumar, N.; Susilo, W. Secure remote user authenticated key establishment protocol for smart home environment. IEEE Trans. Dependable Secur. Comput. 2017, 17, 391–406. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Odelu, V.; Kumar, N.; Conti, M.; Jo, M. Design of Secure User Authenticated Key Management Protocol for Generic IoT Networks. IEEE Internet Things J. 2018, 5, 269–282. [Google Scholar] [CrossRef]
- Srinivas, J.; Das, A.K.; Kumar, N.; Rodrigues, J.J.P.C. Cloud centric authentication for wearable healthcare monitoring system. IEEE Trans. Dependable Secur. Comput. 2018, 17, 942–956. [Google Scholar] [CrossRef]
- Chang, C.-C.; Le, H.-D. A provably secure, efficient, and flexible authentication scheme for ad hoc wireless sensor networks. IEEE Trans. Wirel. Commun. 2015, 15, 357–366. [Google Scholar] [CrossRef]
- Chattaraj, D.; Sarma, M.; Das, A.K. A new two-server authentication and key agreement protocol for accessing secure cloud services. Comput. Netw. 2018, 131, 144–164. [Google Scholar] [CrossRef]
- Bellare, M.; Pointcheval, D.; Rogaway, P. Authenticated key exchange secure against dictionary attacks. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Bruges, Belgium, 14–18 May 2000; Springer: Berlin/Heidelberg, Germany, 2000; pp. 139–155. [Google Scholar]
- Shoup, V. Sequences of games: A tool for taming complexity in security proofs. IACR Cryptol. ePrint Arch. 2004, 2004, 332. [Google Scholar]
| Notation | Explanation |
|---|---|
| Client | |
| Remote server | |
| Identity of | |
| Adversary | |
| Password of | |
| Biometrics of | |
| Smart cards identity | |
| ’s secret key | |
| Random number | |
| Session key | |
| Random rational number from [0, 1] | |
| A finite field, where is a huge prime | |
| A th degree Chebyshev polynomial | |
| A th fractional Chebyshev polynomial | |
| Cryptographic one-way hash function | |
| XOR operation | |
| Concatenation operation |
| Syntaxes | Description |
|---|---|
| The execution time of the hash function | |
| The execution time of symmetric key decryption/encryption | |
| The execution time of ellipse curve point multiplication | |
| The execution time of the Chebyshev map operation | |
| The execution time of fractional Chebyshev map operation | |
| The execution time of fuzzy extractor operation |
| Protocols | Computational Cost | Running Time (In Milliseconds) |
|---|---|---|
| [6] | 445.6 | |
| [13] | 256.4 | |
| [18] | 383.5 | |
| [19] | 446.6 | |
| [35] | 337.8 | |
| [3] | 193.7 | |
| Proposed SIP | 126.5 |
| Security Features | [6] | [13] | [18] | [19] | [35] | [3] | Proposed SIP |
|---|---|---|---|---|---|---|---|
| ⊠ | ⊠ | ☑ | ☑ | ☑ | ☑ | ☑ | |
| ☑ | ☑ | ☑ | ☑ | ⊠ | ☑ | ☑ | |
| ☑ | ⊠ | ⊠ | ⊠ | ☑ | ☑ | ☑ | |
| ☑ | ☑ | ☑ | ☑ | ☑ | ☑ | ☑ | |
| ⊠ | ☑ | ☑ | ☑ | ⊠ | ☑ | ☑ | |
| ⊠ | ⊠ | ⊠ | ☑ | ⊠ | ☑ | ☑ | |
| ☑ | ☑ | ☑ | ⊠ | ☑ | ☑ | ☑ | |
| ☑ | ☑ | ⊠ | ⊠ | ☑ | ☑ | ☑ | |
| ⊠ | ⊠ | ⊠ | ☑ | ☑ | ☑ | ☑ | |
| ⊠ | ⊠ | ☑ | ☑ | ☑ | ☑ | ☑ | |
| ⊠ | ⊠ | ⊠ | ⊠ | ⊠ | ⊠ | ☑ |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Meshram, C.; Lee, C.-C.; Bahkali, I.; Imoize, A.L. An Efficient Fractional Chebyshev Chaotic Map-Based Three-Factor Session Initiation Protocol for the Human-Centered IoT Architecture. Mathematics 2023, 11, 2085. https://doi.org/10.3390/math11092085
Meshram C, Lee C-C, Bahkali I, Imoize AL. An Efficient Fractional Chebyshev Chaotic Map-Based Three-Factor Session Initiation Protocol for the Human-Centered IoT Architecture. Mathematics. 2023; 11(9):2085. https://doi.org/10.3390/math11092085
Chicago/Turabian StyleMeshram, Chandrashekhar, Cheng-Chi Lee, Ismail Bahkali, and Agbotiname Lucky Imoize. 2023. "An Efficient Fractional Chebyshev Chaotic Map-Based Three-Factor Session Initiation Protocol for the Human-Centered IoT Architecture" Mathematics 11, no. 9: 2085. https://doi.org/10.3390/math11092085
APA StyleMeshram, C., Lee, C.-C., Bahkali, I., & Imoize, A. L. (2023). An Efficient Fractional Chebyshev Chaotic Map-Based Three-Factor Session Initiation Protocol for the Human-Centered IoT Architecture. Mathematics, 11(9), 2085. https://doi.org/10.3390/math11092085









