Abstract
Blockchain-based federated learning (BCFL) has been regarded as an emerging data sharing paradigm in edge networks of internet-of-things (IoT) because of its advantages, such as decentralization, collaborative model training, and privacy protection. However, there have been few studies focusing on strategic analysis in the BCFL system, which is important for establishing a robust and sustainable BCFL system in an untrustworthy and profit-driven environment. In this paper, we first propose a self-organizing data sharing system supported by BCFL to deeply analyze the data sharing logic. Then, a mathematical model based on evolutionary game theory is established to analyze the interaction between model owners and data providers, aiming at exploring the stability of user strategies under different considerations. According to the strategic analysis, we designed and further discussed a dynamic system control mechanism based on smart contracts to adaptively maintain a robust and sustainable BCFL system. We conducted numerical analysis and experiments to verify our work.
MSC:
93C99
1. Introduction
In recent years, the rapid development of communication and information technology has driven the proliferation of the Internet of Things (IoT) [1,2]. Along with this trend, a vast amount of data are generated and collected at the network edge [3,4]. However, the decentralized deployment of IoT often leads to data islands, which hinder the full exploitation of data values. Therefore, data sharing plays a crucial role in this context [5].
Traditional data sharing models usually adopt a centralized framework, in which all raw data are transmitted and collected in a data center for centralized analysis or training. However, such data sharing solutions have inherent disadvantages, including increased data traffic and high computational and storage costs. More importantly, since data are an individual’s core asset, data privacy [6], security, and ownership [7] are increasingly vital, and data owners are reluctant to share their data. In this situation, a new data sharing model, which not only empowers the autonomy and the willingness of data providers, but also emphasizes individual control over the transfer and utilization of personal data, is an urgent need.
Fortunately, the emerging integration of blockchain and federated learning (also referred to as BCFL) introduces an effective way to address the aforementioned issues, and it has attracted growing attention and research work in many applications [8,9], including IoT data sharing [10,11,12]. BCFL-related works try to offer a fully decentralized, privacy-preserving, and secure data sharing market for the IoT domain. More specifically, FL, introduced in 2016 by Google [13], enables data owners to train their local models based on their private data and share the models instead of the raw data, which transfers the data sharing task into a collaborative model training process and significantly alleviates concerns about data privacy leakage. Furthermore, assisted by blockchain, the central server responsible for global model aggregation and updates can be removed. Models submitted by data owners are verified and aggregated by all the participating miners in the blockchain. In this way, BCFL alleviates the issues of data monopolies and data ownership conflicts in IoT data sharing [14]. Additionally, the blockchain naturally possesses monetary incentive properties, which makes decentralized incentives possible in the data market.
Although BCFL-based approaches are promising, they still face challenges in encouraging participants to contribute to data sharing in a sustainable way. Firstly, BCFL has also introduced more tasks (such as training and mining) while promoting data sharing. However, there is currently a lack of a unified architecture to clarify the task roles of participants, which makes the behavior of participants in data sharing very vague, thereby affecting their enthusiasm for participation. Second, training or mining on the participant’s side incurs operational costs, and participants are willing to join the BCFL only when the reward exceeds the cost. Lastly, since decentralized data sharing can be regarded as a self-organized data trading market involving many economic factors, participants who have bounded rationality will make their decisions based on the profit situation, with the maximization of personal benefits as the strategic goal. We acknowledge that blockchain technology enables the realization of a trustworthy edge data sharing that is not controlled by a central or third party. But in profit-driven data sharing scenarios, participants may still be tempted by economic interests to behave opportunistically at any time. With this motivation in mind, establishing a general BCFL-based IoT data sharing framework, exploring which influencing factors are critical, as well as how they affect the data sharing strategies, and maintaining a robust and sustainable framework are important.
In this study, we explored IoT data sharing behaviors in the BCFL-enabled system by using evolutionary game theory. A BCFL-based IoT data sharing model was first devised to clarify participants’ tasks and behaviors. And mathematical models about BCFL-enabled data sharing utilities were established. Then, toward the point-to-point and dynamic interactions of IoT data sharing, we adopted an evolutionary game approach to obtain the optimal data sharing strategies, which are subject to some parameters. The results are helpful to summarize some corresponding implications for establishing a sustainable blockchain-based IoT data sharing system. We summarize our main contributions as follows.
- We propose a novel data sharing model that is based on a fully decentralized blockchain-based federated learning (BCFL). In this model, we provide a comprehensive explanation of its components and the data sharing process within the BCFL framework. Our aim is to analyze the roles and functions of various entities involved in the data sharing process.
- An evolutionary game method is utilized to analyze the stability of user participation strategies. An optimal data sharing strategy satisfying the stability is also analyzed with the goal of demonstrating how the critical factors affect the evolution process of participation population in the blockchain-based data sharing environment.
- According to the analysis in this article, we provide a corresponding discussion on blockchain-based IoT data sharing research. Two inspirations, that is, a theoretical and methodological paradigm for decentralized data sharing research and a smart-contracts-empowered dynamic control mechanism for systems, guide our applications in this area.
The subsequent sections are organized as follows. Section 2 briefly describes the related work. Section 3 presents a novel blockchain-enabled FL-enabled IoT data sharing model. The proposed evolutionary game model is formulated with a theoretical and numerical analysis in Section 4. Section 5 discusses some inspirations for blockchain-enabled decentralized data sharing research. Finally, Section 6 concludes this article.
2. Related Work
With the large-scale deployment of IoT devices currently, plenty of data sharing operations among different stakeholders are expected to be generated continuously in a decentralized pattern to achieve edge intelligence. Blockchain is considered the most promising technology, as it keeps data sharing records in secure and verifiable distributed ledgers [4]. Xia et al. [15] proposed a medical data sharing system based on blockchain and smart contracts to provide data provenance, auditing, and control for medical data among medical internet of things. Kang et al. [16] proposed a blockchain-based internet of vehicles data sharing process between vehicles and the roadside, which may be the future of autonomous driving. Yang et al. [17] studied IoT data access control for data sharing and proposed a computing outsourcing mechanism to achieve a lightweight blockchain. Bao et al. [18] presented a blockchain-based IoT framework for differential private data publishing, and two protocols were proposed for histogram publishing and anonymized data publishing, respectively. A review of the state-of-the-art blockchain-based data sharing towards 6G networks was also proposed by Shen et al. [4] to comprehensively shape a research picture of blockchain-based mechanisms for collaborative IoT data sharing. However, these works mainly focused on utilizing blockchain and smart contracts to provide a technical guarantee, automatic execution and access control for decentralized IoT data sharing, while ignoring the privacy and security issues in data sharing. In order to improve the security and privacy-protection in data sharing, as well as enhancing the efficiency and intelligence of IoT data sharing, some works have attended to the integration of blockchain and federated learning. A lightweight trusted sharing mechanism based on blockchain and federated learning was proposed in [19] to provide security and trust protection. Zou et al. proposed a blockchain-protected knowledge trading framework with regional federated learning designs in [20] to address data sharing issues with local biased characteristics. Nguyen et al. [21] proposed a new blockchain-based framework with federated GAN algorithm for secure COVID-19 data analytics by decentralizing the learning process with a low-latency mining solution. Although receiving much attention currently, most of the research focuses on the technical and methodological aspects, providing blockchain-based learning-enabled IoT data sharing solutions in terms of technology and algorithms, and few scholars have paid attention to how internal factors affect the stability of data sharing.
Compared with these existing works, our work first pays more attention to describing the contributions of blockchain and various IoT devices, data sharing and service logic, and topological relationships among participants, trying to build a general blockchain-enabled decentralized IoT data sharing framework from both technical and theoretical aspects. An evolutionary game theory is introduced to investigate the stability of participation strategies between data owners and data requesters to explore a robust and sustainable data sharing process.
3. System Model Overview
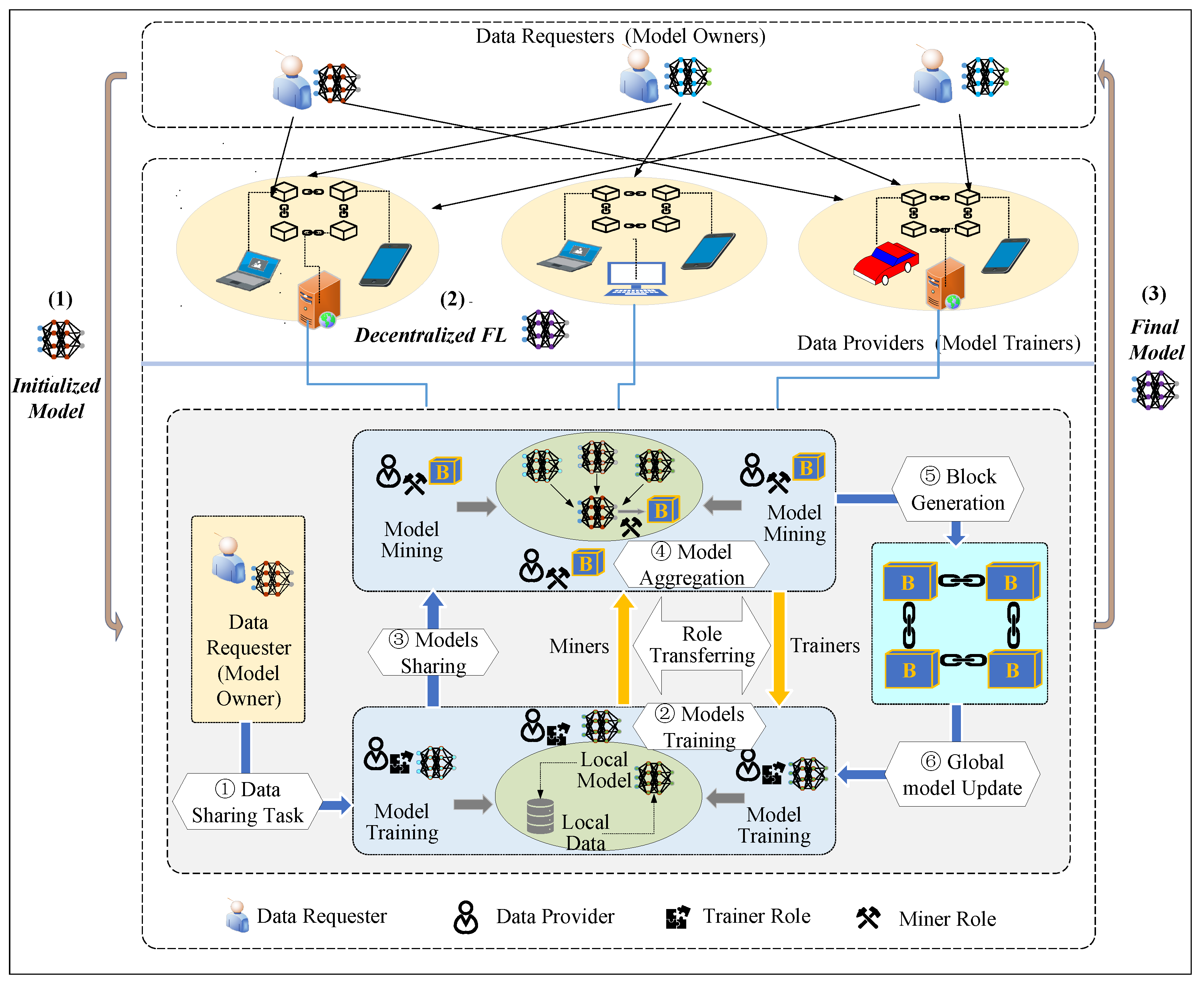
In this section, we consider such a decentralized data sharing system: it is built on top of a blockchain network and incorporates federated learning mechanisms to transform the data sharing process into a collaborative model training process. Importantly, the blockchain is no longer seen as a standalone network for storing data sharing evidence, but is tightly integrated with federated learning to achieve fully decentralized privacy-preserving data sharing. The framework structure and relevant modules of the system are shown in Figure 1, and we provide the following definitions.
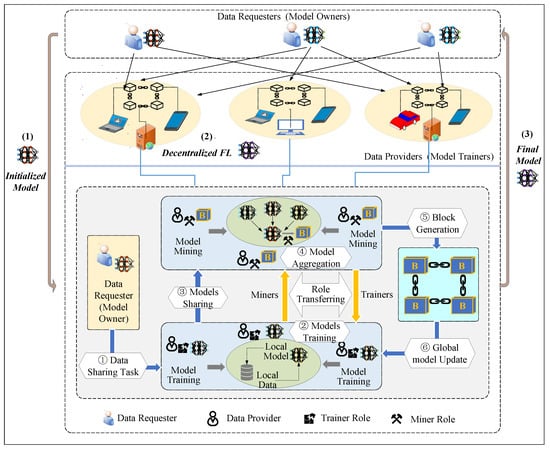
Figure 1.
An overview of federated IoT data sharing based on BCFL.
Definition 1.
Data Requesters. Data Requesters (DRs) refer to IoT end users who need to perform some data services (such as semantic analysis or image recognition) but lack sufficient data and need to publish data requirements through the system platform. They are also commonly referred to as model owners. DRs release data sharing tasks by publishing initialization models and recruit a group of data owners to share data within a limited budget.
Definition 2.
Data Owners. Data Owners (DOs) are a collective of IoT end users who possess data with the same features but different samples and are eager to engage in data sharing tasks. They are commonly known as model trainers, as they facilitate privacy-protected data sharing through collaborative training, replacing data transmission with model transmission. It is important to note that in our system design, DOs are responsible for assuming the roles of both model trainers and blockchain miners, ensuring a fully decentralized data sharing process. For more information, please refer to the detailed workflows outlined in BCFL.
Definition 3.
BCFL Network. The BCFL network is built upon an alliance chain and operates as a decentralized peer-to-peer (P2P) network. It is comprised of authenticated DRs and DOs, offering communication connectivity and horizontal federated learning capabilities. Within the BCFL network, all FL-related activities, such as task publication, learning model broadcasting, and learning result aggregation, are executed, serving as the foundational architecture for the system’s normal operation.
Definition 4.
Smart Contracts (SCs). The key technique that enables programmable IoT data sharing in BCFL is the use of smart contracts. These contracts are triggered by events and are automatically executed by all nodes in the BCFL network. SCs play a crucial role in providing functional interfaces and rules for all participants in BCFL, such as the way tasks or models are published, the rules for aggregating data, and the rules for rewarding participants. This ensures an efficient and fair process for sharing data.
Based on these definitions, as shown in Figure 1, the workflow of the proposed BCFL-enabled data sharing process consists of the following steps.
- Step 1: Task releasing. A DR broadcasts a data sharing task by deploying an SC over the BCFL network, specifying an initialized FL model and budget. Then, they must encapsulate the reward rules into the SC and deposit a reward, ensuring immutable and automatic execution to incentivize data owners to participate.
- Step 2: Model training and sharing. A group of qualified DOs receive the tasks. Each of them performs training locally by using their own data samples and broadcasts their local updates to the BCFL network.
- Step 3: Model aggregation and block generation. Upon receiving the local updates from other participants, each DO updates the global model according to the aggregating rule defined in the SC. After obtaining a new global model, the DO changes roles from trainer to miner and begins mining until they either find the required nonce or receive a generated block from other miners. The obtained global model is stored in the block.
- Step 4: Block propagation. A new block generated by one miner is then broadcast in the network. Other DOs verify the contents of this block (e.g., the nonce, transactions, and new global model). If a block is verified by the majority of miners, this new block defines the latest states of the network and will be added to the blockchain.
- Step 5: Global model download and update. Each training DO obtains the valid aggregated model from the block, proceeding to update their local models and initiating the subsequent round of training.
- Step 6: Reward allocation. The reward rules encapsulated into the SC in Step1 are performed to facilitate the distribution of rewards to DOs.
4. Evolutionary-Game-Based Strategic Analysis for BCFL-Enabled IoT Data Sharing
It is worth noting that the BCFL-enabled IoT data sharing process is essentially a multi-round end-to-end interactive decision-making process in which all rational participants attempt to maximize their individual interests. To analyze the conditions under which DRs and DOs adopt specific strategies in the system and identify a collaborative equilibrium, where a stable proportion of users participates in the system, we have formulated the behaviors of DRs and DOs in the BCFL as a dynamic model based on an evolutionary game.
4.1. Model Hypotheses and Descriptions
In our BCFL evolutionary game model, there are two player types: DRs and DOs, both aiming to maximize their profits. We made certain assumptions in our research. Firstly, we assumed that both Data Requesters (DRs) and Data Owners (DOs) are individuals who make decisions based on irrational but honest reasoning, and we assumed there was no free-riding behavior. The BCFL system operates continuously with the active participation of DRs and DOs. Even if they do not perform data sharing tasks, their involvement is necessary to maintain the operation of the BCFL network. Furthermore, we did not focus on specific algorithms or models employed in BCFL, such as CNN or RNN, in our research. To elucidate the influencing factors in the data sharing process, we initiated an analysis of the potential profits and costs associated with it. We have formulated this analysis as follows, and the notations and descriptions are shown in Table 1.

Table 1.
The notations of the model parameters.
- (1)
- BCFL-enabled data sharing profits:
- Direct Data Value: As a special “commodity”, the same data may have completely different effects on different data requesters. Thus, the proposed data value model consists of a fixed data price and extra profits (such as the improvement in model performance), as follows:in which is the data price determined by data owners, indicates the extra model value determined by data requesters, and is the coefficient.
- Data-Flow Profit: Due to the advantages of blockchain, data owners can obtain benefits from second-hand data transfers operated by data requesters by setting revenue distribution rules in smart contracts. Considering the law of diminishing marginal utility, the logarithmic function is used to express the data flow profit:in which and represent a constant profit of data exchange and the predefined number of data transfers, respectively.
- Mining reward: In blockchain networks, participants who contribute to generate valid blocks can obtain a reward from the blockchain automatically. We define it as , where is a adjustment parameter.
- Extra model services profit: Data sharing would enable data requesters to provide value-added services that are co-created by all data owners. Once users pay for services provided by data requesters, revenue is distributed to all contributors according to predetermined smart contracts. For simplicity, we define the total extra model services profit as , and the proportion allocated to DR is .
- (2)
- BCFL-enabled data sharing costs:
- Data sharing cost: The data sharing cost comprises the computing cost and privacy leakage cost. Computing involves the operations that IoT devices use to generate, sense, or collaboratively train data for data sharing task. Sometimes, privacy computing should also be conducted to protect data privacy. For simplicity, we define the total computing cost as . As for the data privacy leakage cost, it refers to the economic loss caused by sensitive information leakage, which is assumed to be linearly related to the degree of data sharing. Therefore, we introduce a privacy tolerance variable to represent the degree as follows:in which represents the constant cost of data privacy leakage. The smaller the is, the larger the privacy computing resource should be, and the lower the data privacy leakage should be.
- Blockchain maintenance cost: In a blockchain-enabled data sharing system, every data-sharing-related operation is driven by transactions. IoT devices have to consume computation and communication resources to invoke smart contracts to maintain data sharing operations. Thus, these costs are summarized as blockchain maintenance costs, defined as and for DRs and DOs, respectively.
4.2. Problem Formulation and Payoff Matrix
Blockchain-based decentralized IoT data sharing is regarded as a self-organized process. Since data owners and data requesters cannot fully understand each other’s strategies, they tend choose to participate or not to participate in data sharing by analyzing the payoffs based on these data sharing utility and costs. Next, we study the dynamic strategy selection affected by these data sharing parameters to explore a robust and sustainable BCFL-enabled IoT data sharing system.
Players: The set of all participants that subscribe to a data sharing task is denoted as P; i.e., .
Strategy space: With the aim of exploring the stability of the data sharing system, the strategies’ space is modeled as , where represents the participation strategy, and represents a no participation strategy.
Payoff functions: We assume that DOs choose strategy and with probabilities y and , respectively, while DRs choose strategy and with probabilities x and , respectively. The payoffs for participating in data sharing for both DOs and DRs are determined by the difference between the data sharing utility and cost, as illustrated in Table 2. Specifically, if both DOs and DRs choose to participate in the BCFL system for data sharing, DRs can benefit from the Extra Model profit , the Extra Model services profit , the mining reward from the BCFL network , and the Data-Flow profit . The cost for DRs includes the payment (i.e., Direct Data Value) to DOs , as well as the blockchain maintenance cost . Thus, the utility of DRs can be formulated as . Similarly, DOs can benefit from the reward , the Extra Model services profit , the Data-Flow profit , and the mining reward . However, DOs also incur costs from model computing and the risks of privacy leakage , as well as the blockchain maintenance cost . Therefore, the utility of DOs can be formulated as . Furthermore, if one chooses to participate in data sharing while the other does not, the payoff for the participant is the difference between the mining rewards and blockchain maintenance cost, and the payoff for not participating is zero.

Table 2.
Payoff matrix.
4.3. Replicator Dynamics and Evolutionary Equilibrium Analysis
With the aim of providing the dynamical behaviors of IoT users, the replicator dynamics are described in this subsection. According to Table 2, when IoT data requesters choose to participate in the networks, the utility is
And the utility of IoT data requesters with no participation strategy is
Based on (1) and (2), the expected utility function of IoT data requesters is given in (3), which represents the mean payoff of data requesters:
Similarly, the utility functions of IoT data owners with strategies () and () and the expected utility function are as follows, respectively:
Following the definition of the Malthusian dynamic equation [22], the replicator dynamic equations of IoT data requesters and data owners in data sharing networks are, respectively,
With the assistance of the above equations, the optimal strategy choices of the two roles are: , , , , and . Our aim is to find the optimal local evolutionary stable points, which could maintain robust and sustainable data sharing networks. In an evolutionary game, there are evolutionary equilibrium points that can be obtained through analyzing the Jacobian matrix, which is defined as follows:
where
According to the Jacobian matrix and stability theorem, if the following conditions and are met, the studied local equilibrium point can be regarded as evolutionary stable strategy (ESS). Based on (9) and (10), and the condition , we analyzed the value of and under different situations. With the aim of studying a optimal strategy that could encourage more data sharing participants, in this article, we only focus on the case in which points are the ESS. Hence, the only case is presented as follows:
Condition: and .
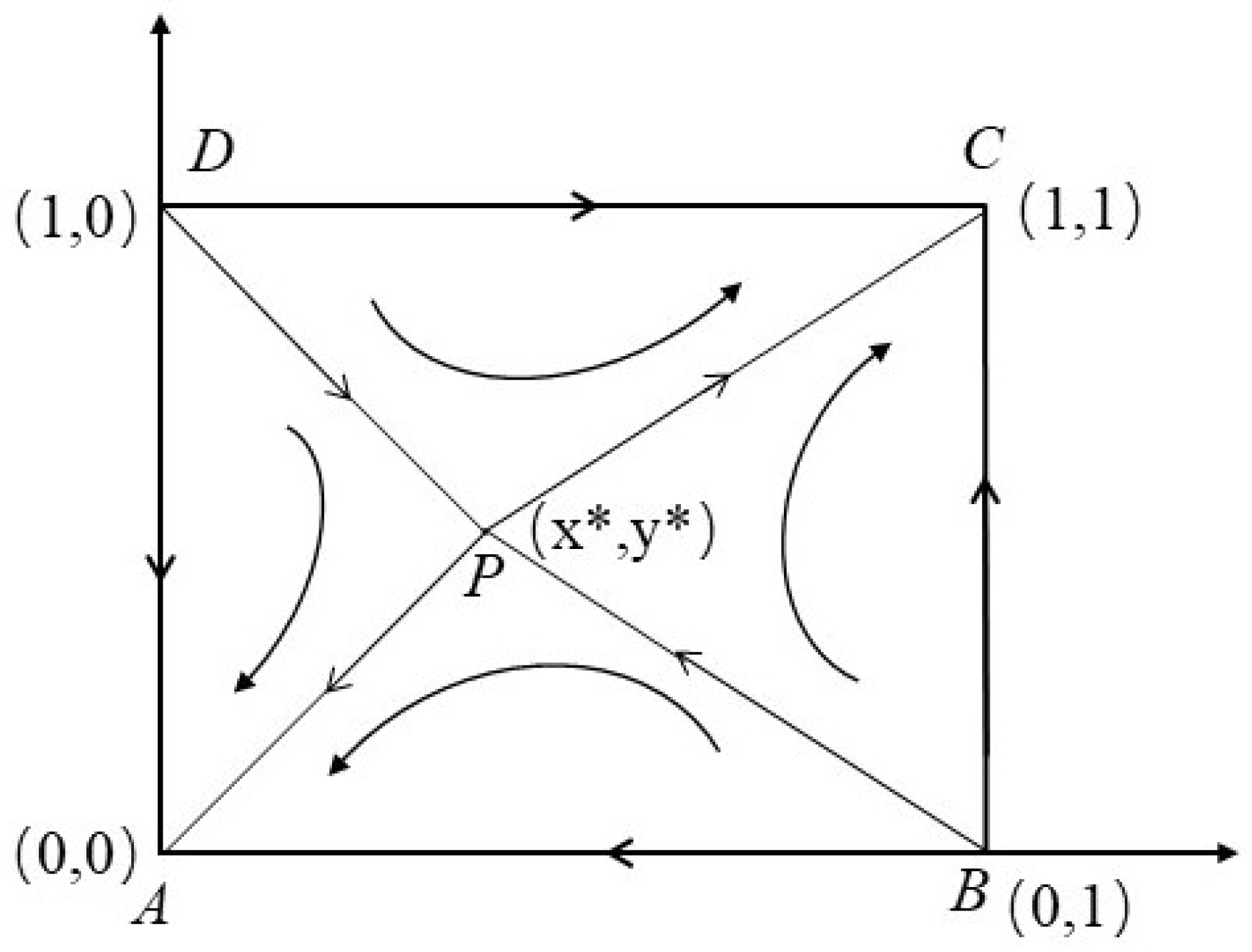
Condition and mean that the blockchain maintenance cost of IoT devices should be greater than the mining reward. The stability of the blockchain-based IoT data sharing system equilibrium points is analyzed in Table 3, and the dynamic phase of evolution between data owners and data requesters is illustrated in Figure 2. The analysis shows that when the value of x (i.e., the proportion of data owners who participate in data sharing) and the value of y (i.e., the proportion of data requesters who participate in data sharing) fall in the area , the evolution of the IoT data sharing game would evolve to a situation where no players participate in data sharing (i.e., ). On the contrary, when x and y fall in the area , the game will eventually lead to stable user participation (i.e., ), where participants are more willing to join the data sharing tasks. As shown in Figure 2, the final evolutionary state depends on the value of saddle points and initial participation proportion.

Table 3.
Analysis of equilibrium points.
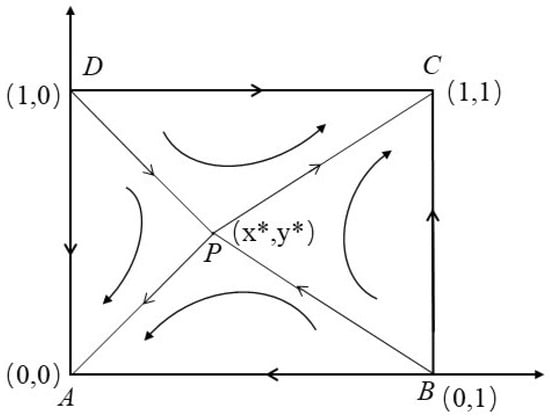
Figure 2.
System dynamic evolution under the ESS strategy.
As mentioned above, the evolutionary game model based on blockchain-enabled decentralized data sharing shows that the long-term equilibrium state of system evolution may be that both parties are willing to participate in sharing data or maybe the other extreme situation. How the system evolves depending on the initial state of the game matrix and its evolution direction. Actually, due to the complexity involved in calculating , , it is very difficult to give a theoretical analysis and solve the proof of the ESS. To this end, we seek to use a numerical simulation method to solve these problems.
4.4. Numerical Analysis and Discussion
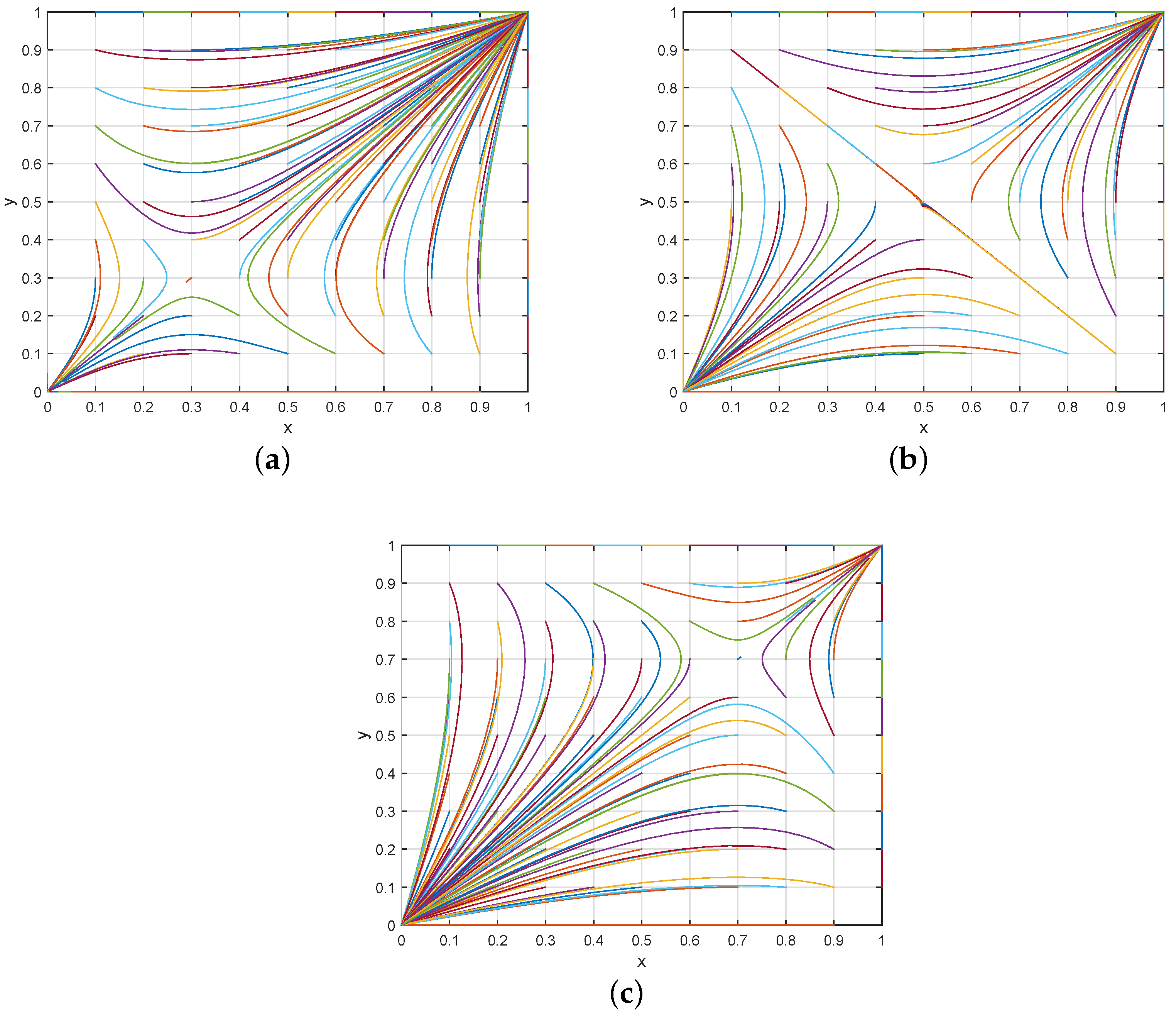
In order to intuitively analyze the impact of different initial states on the results of policy evolution, we utilized Matlab for the numerical simulation of the dynamic evolution process through setting three sets of different model parameters as follows: , , ; , , ; , . According to the three sets of parameters, saddle points were empowered with different initial values; that is, , , and . As illustrated in Figure 3, the results agree with the ESS strategies shown in Table 3 and the dynamic phase of evolution presented in Figure 2. Under the constraint of and , the smaller the saddle point is, the greater the probability of evolving to (i.e., the ESS strategy converges to ()), which provides theoretical support for the research on stable and sustainable user participation in a blockchain-based data sharing environment. Next, we adopted Control Variables to verify the effect of some key parameters on the ESS of the system. In the following cases, the values of the variables are set the same as in .

Figure 3.
Evolution simulation results of the system under different initial state values. (a) ; (b) ; (c) .
- (1)
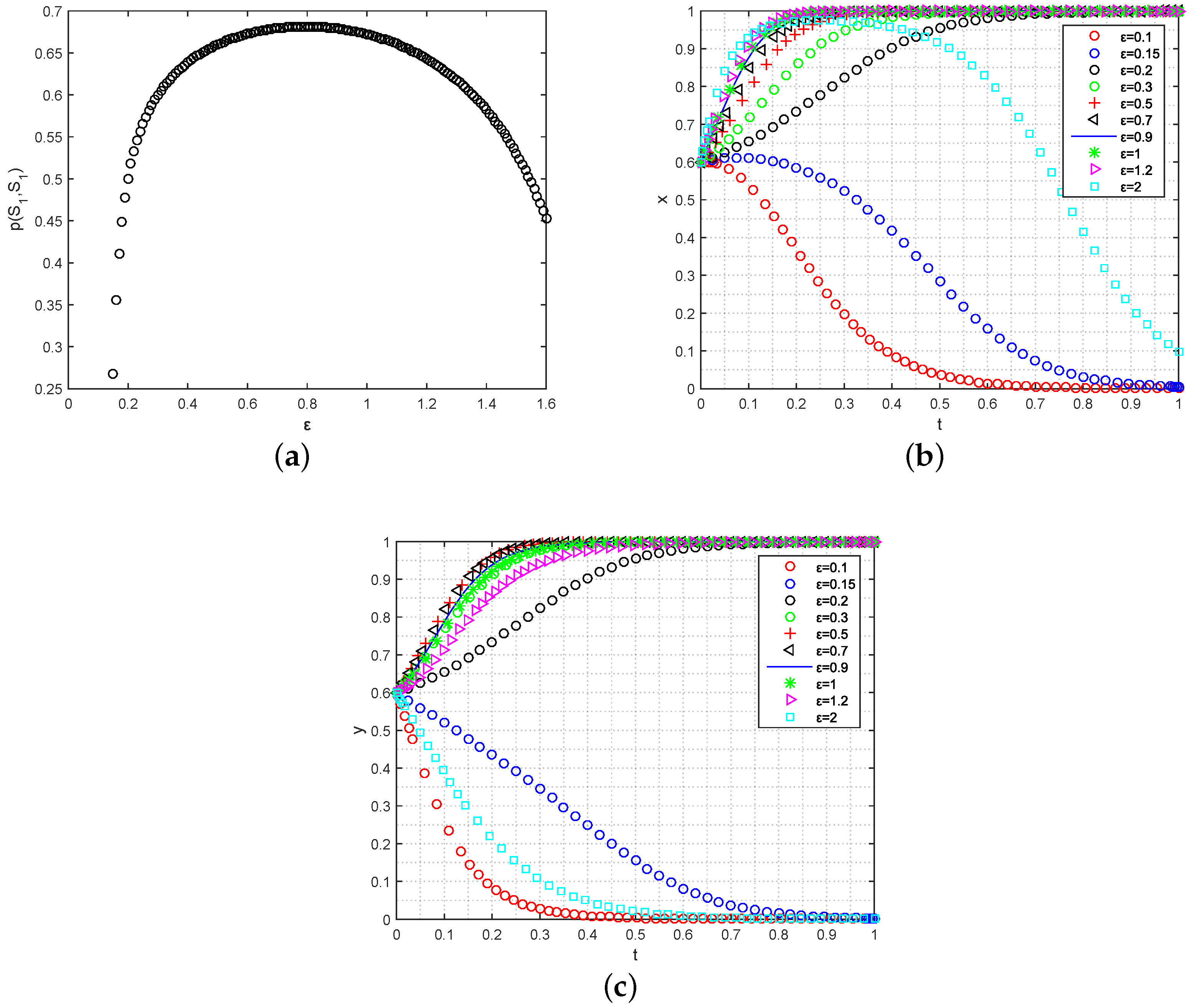
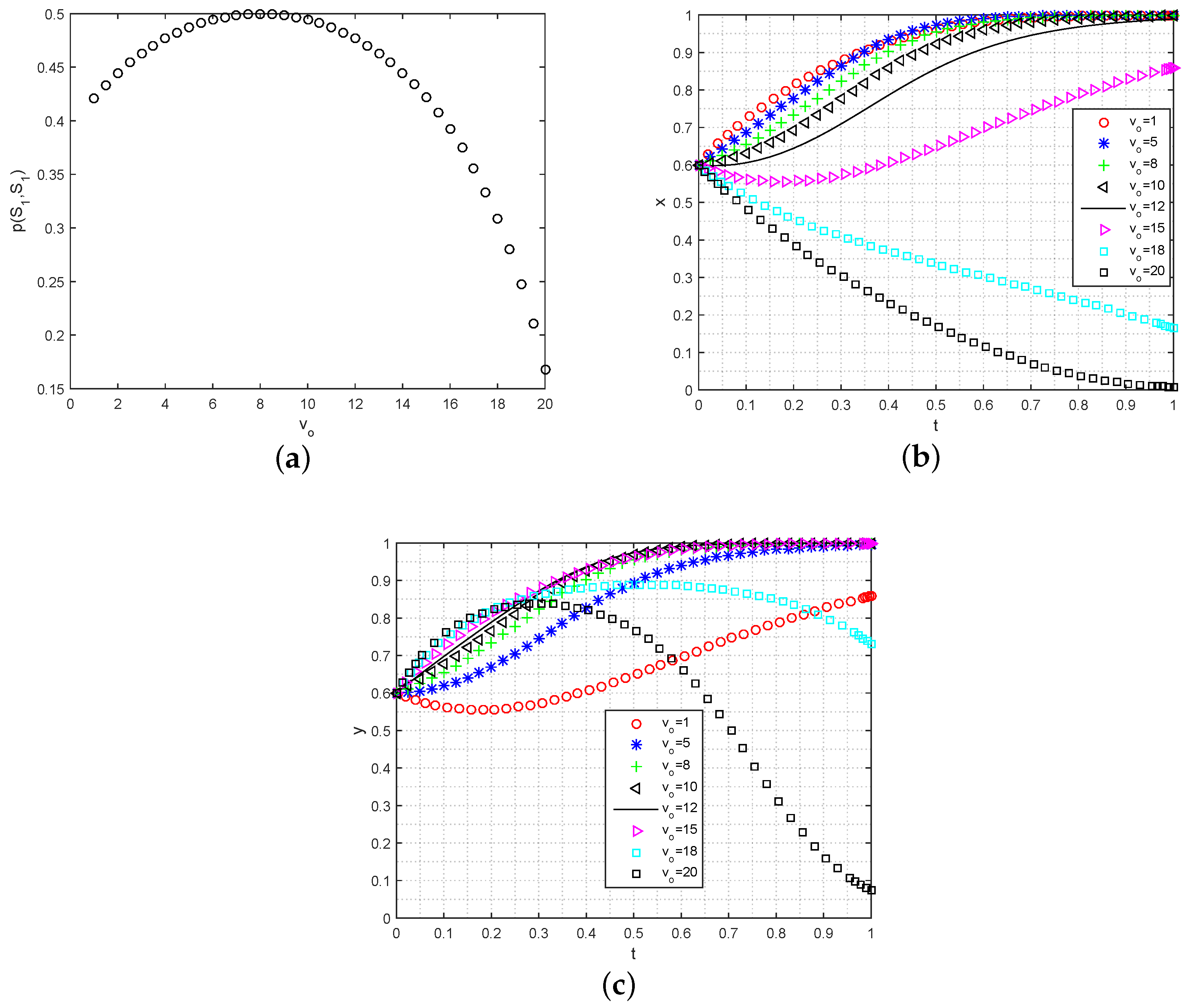
- Analysis of privacy tolerance on ESS: To investigate the influence of privacy requirements on the strategy selection of data owners and data requesters, we conducted simulations by varying the privacy tolerance parameter while considering the ESS constraints. The initial proportion of participating users in the system was set to , as shown in Figure 4. Figure 4a illustrates the impact of on the probability , which represents the likelihood of both data owners and data requesters choosing the participation strategy. As increases, the value of initially experiences a steep rise and then stabilizes when exceeds . Beyond this threshold, the probability starts to rapidly decrease. This observation suggests that there exists an optimal privacy leak tolerance that maximizes the probability of the participation strategy. This finding is further supported by Figure 4b,c. As increases, the likelihood of user participation converging from , to , also increases, and the convergence speed is accelerated. However, excessively large or small values of tend to discourage users from participating in data sharing (i.e., , ). It is worth noting that while the value of has a greater impact on the convergence speed of data requesters, data owners are more sensitive to its value. This implies that there is a need to strike a balance between the privacy requirements of the data requesters and data owners in order to enhance the probability of the participation strategy.
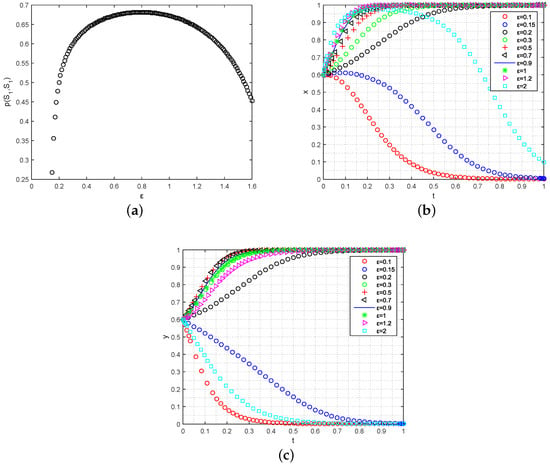 Figure 4. The simulation impact of on data sharing strategies’ evolution. (a) Analysis of on ; (b) analysis of on the strategy evolution for data requesters; (c) analysis of on the strategy evolution for data owners.These insights highlight the importance of considering privacy requirements when designing BCFL data sharing systems. By carefully selecting an appropriate value of , system designers can encourage user participation while still ensuring an acceptable level of privacy protection. Moreover, the results emphasize the need for effective privacy-aware mechanisms and policies that address the concerns of both data owners and data requesters, ultimately fostering a healthy and sustainable data sharing ecosystem.
Figure 4. The simulation impact of on data sharing strategies’ evolution. (a) Analysis of on ; (b) analysis of on the strategy evolution for data requesters; (c) analysis of on the strategy evolution for data owners.These insights highlight the importance of considering privacy requirements when designing BCFL data sharing systems. By carefully selecting an appropriate value of , system designers can encourage user participation while still ensuring an acceptable level of privacy protection. Moreover, the results emphasize the need for effective privacy-aware mechanisms and policies that address the concerns of both data owners and data requesters, ultimately fostering a healthy and sustainable data sharing ecosystem. - (2)
- Analysis of data price on ESS: In order to explore a reasonable and sustainable data sharing process, we analyzed the impact of data price on the system dynamics, as shown in Figure 5a. The behavior of the probability provides valuable insights. As the data price increases, both the data owners and data requesters initially tend to participate in data sharing. However, once the value of surpasses a certain threshold, the population of participating users experiences a sharp decline. For data requesters, the data price has a negative effect on their willingness to participate. As the data price increases, data requesters are less likely to choose the participation strategy. On the other hand, the behavior of data owners is exactly the opposite. This is because the data price directly affects the benefits they receive from data sharing. Higher data prices incentivize data owners to participate and share their data. However, an interesting observation can be made when data requesters adopt a no participation strategy due to a high data price , such as or in Figure 5b. In such cases, data owners also tend to choose the no participation strategy, resulting in a convergence of the participation probability y to 0. This finding suggests that the payoff function in the system is reasonable, as it ensures an equitable data price that provides an incentive for data sharing.
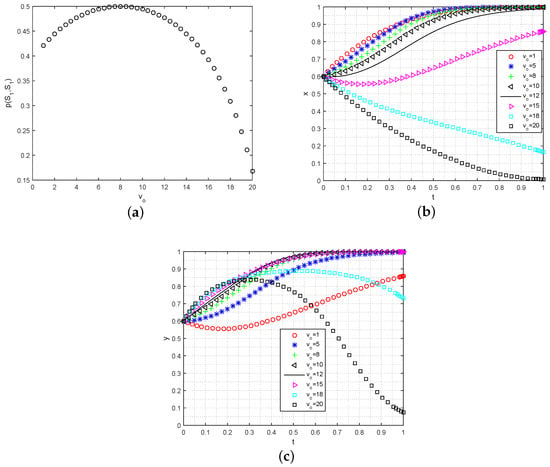 Figure 5. The simulation impact of on data sharing strategies’ evolution. (a) Analysis of on ; (b) analysis of on the strategy evolution for data requesters; (c) analysis of on the strategy evolution for data owners.These findings highlight the importance of carefully determining the data price in a data sharing system. Setting an appropriate data price can strike a balance between incentivizing data owners to participate and ensuring that data requesters find the price acceptable. Moreover, the results emphasize the need for mechanisms and policies that regulate data pricing, taking into account the interests of both data owners and data requesters. By doing so, we can foster an environment that encourages fair and efficient data sharing.
Figure 5. The simulation impact of on data sharing strategies’ evolution. (a) Analysis of on ; (b) analysis of on the strategy evolution for data requesters; (c) analysis of on the strategy evolution for data owners.These findings highlight the importance of carefully determining the data price in a data sharing system. Setting an appropriate data price can strike a balance between incentivizing data owners to participate and ensuring that data requesters find the price acceptable. Moreover, the results emphasize the need for mechanisms and policies that regulate data pricing, taking into account the interests of both data owners and data requesters. By doing so, we can foster an environment that encourages fair and efficient data sharing. - (3)
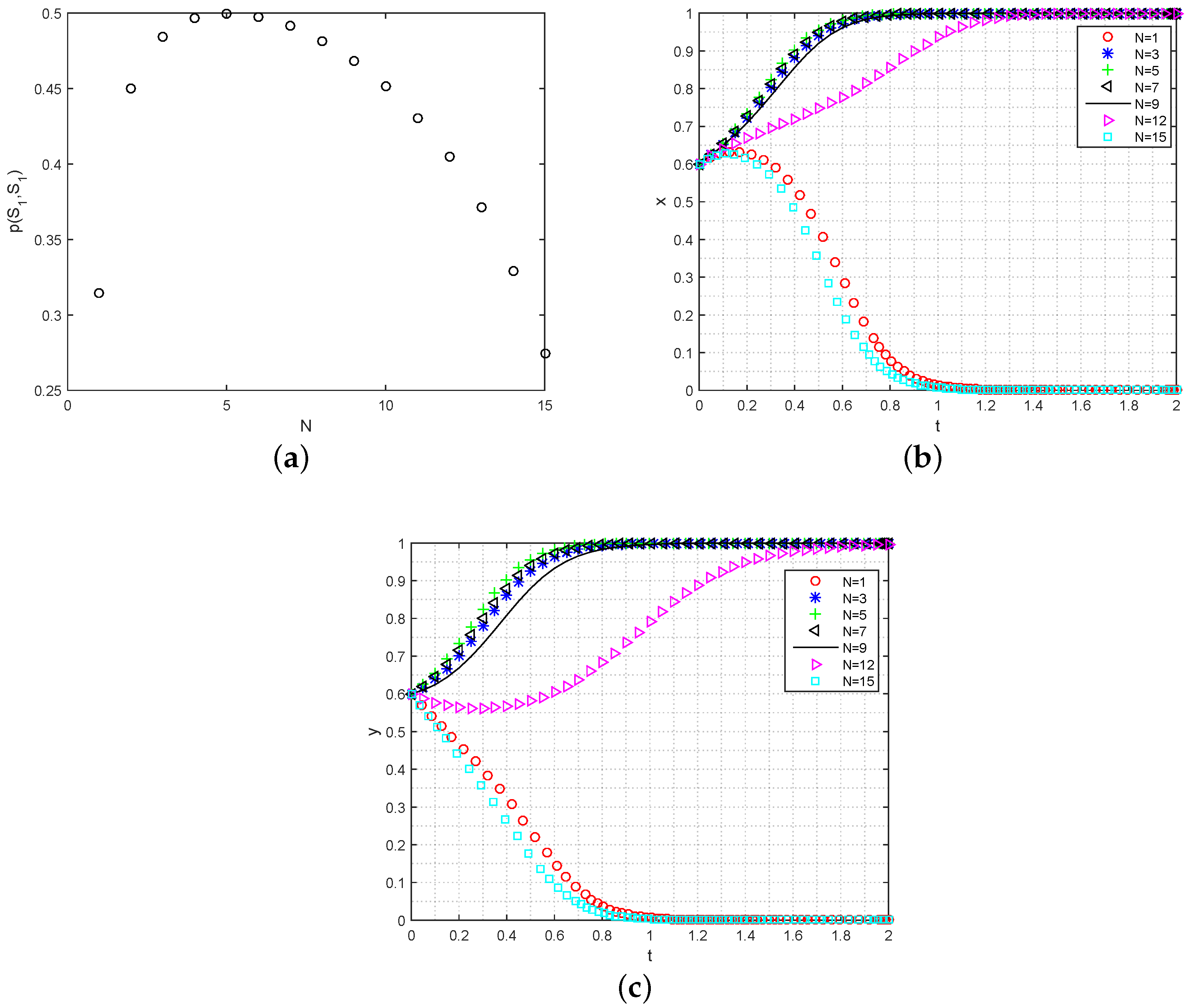
- Analysis of the data exchange numbers on the ESS: The number of times data are allowed to transfer, represented by the parameter , plays a crucial role in determining the level of user engagement in data sharing. Figure 6a illustrates the impact of on the participation probability . As increases, the value of initially shows exponential growth. However, after reaching a maximum value (approximately ), the participation probability starts to decline with further increases in . Moreover, the rate of decrease gradually accelerates, indicating a diminishing marginal value of data as the number of sharing instances increases. To further analyze the evolutionary process for data consumers and data owners under the initial conditions of , , we examine the behavior of data owners. As increases, the proportion of participating data owners converging to also increases, albeit at a slower rate. However, it is worth noting that excessively high values of eventually lead to a convergence of y to 0, as shown in Figure 6b. This can be attributed to concerns about the potential cost of privacy loss for data owners. On the other hand, the increase in has a relatively smaller effect on the convergence rate of data requesters. This implies that users are more likely to choose to participate in data sharing when the value of falls within an appropriate range.
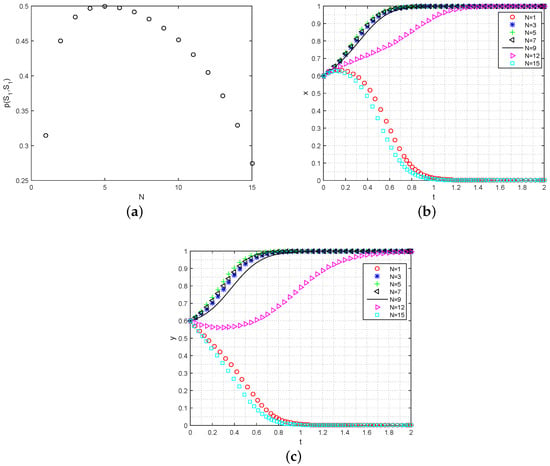 Figure 6. The simulation impact of on data sharing strategies’ evolution. (a) Analysis of on ; (b) analysis of on the strategy evolution for data requesters; (c) analysis of on the strategy evolution for data owners.
Figure 6. The simulation impact of on data sharing strategies’ evolution. (a) Analysis of on ; (b) analysis of on the strategy evolution for data requesters; (c) analysis of on the strategy evolution for data owners. - (4)
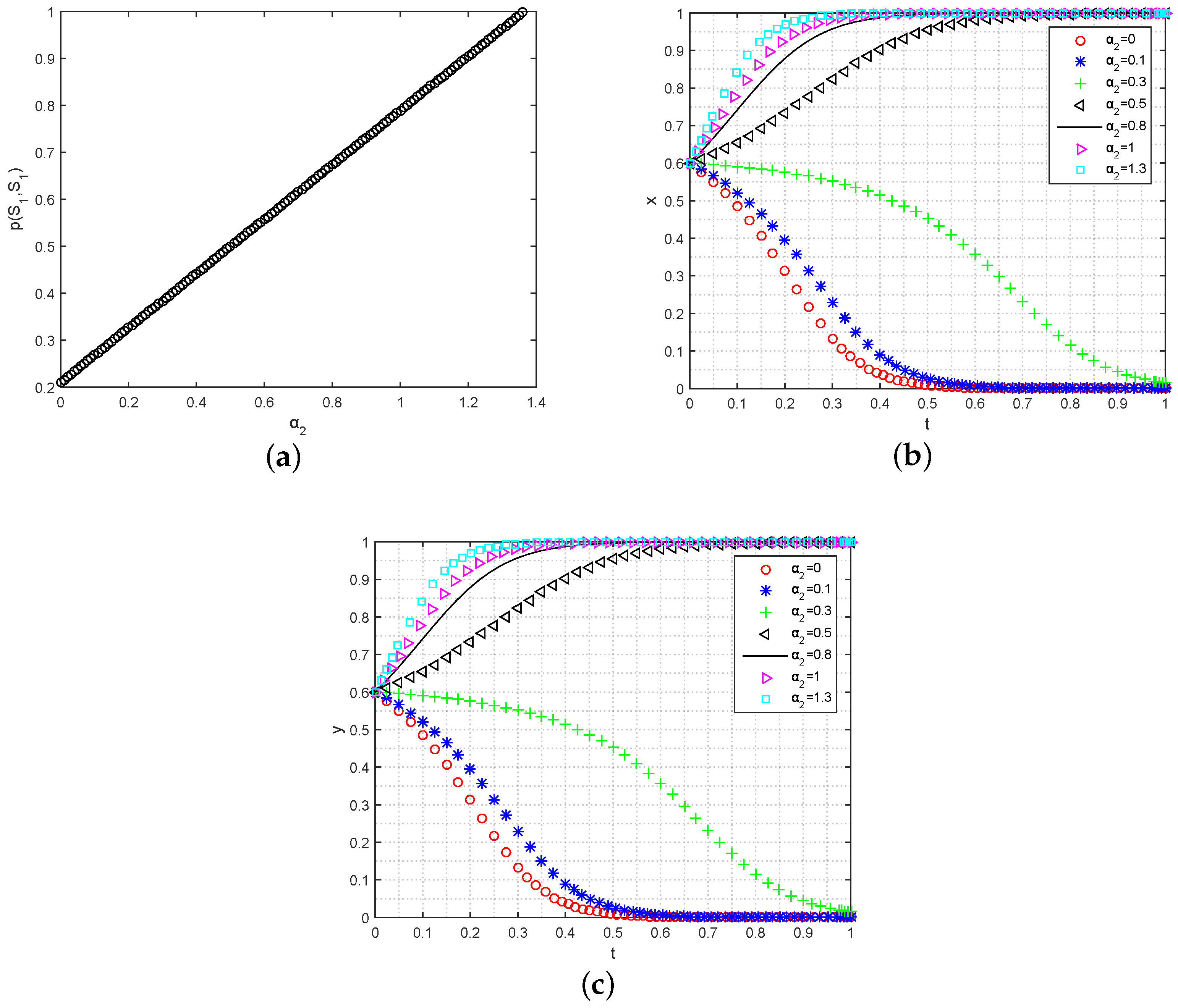
- Analysis of the Mining Reward on the ESS: A mining reward can indeed serve as an effective incentive mechanism to encourage user participation and maintain the stability of a blockchain-enabled data sharing system. To examine the impact of a mining reward on the evolutionary trend of the system, we conducted an analysis by increasing the weight of the mining reward , as shown in Figure 7a. The results indicate that the willingness of both data owners and data requesters to participate in the data sharing system is positively and linearly related to the mining reward . This suggests that the mining reward from the blockchain plays a crucial role in attracting users and ensuring the robustness and sustainability of the data sharing system. Under the conditions that and , the rate of user evolution accelerates as the mining reward increases, as demonstrated in Figure 7b,c. It is important to note that the other variables of the payoff function are determined by the system’s users themselves. Therefore, the mining reward factor can be automatically adjusted by predefined smart contracts in the blockchain, based on different situations. This dynamic control mechanism enables the system to adapt and improve its stability and sustainability in a decentralized manner.
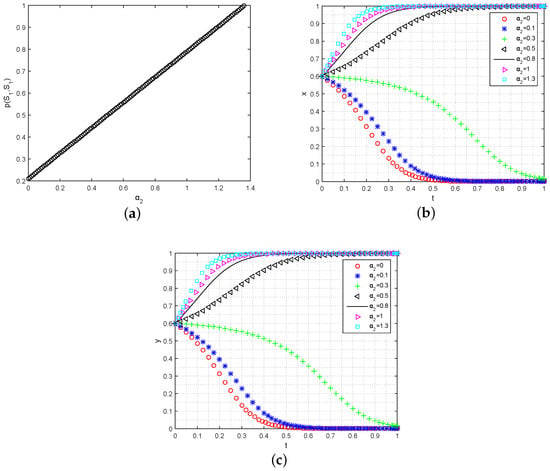 Figure 7. The simulation impact of on data sharing strategies’ evolution. (a) Analysis of on ; (b) analysis of on the strategy evolution for data requesters; (c) analysis of on the strategy evolution for data owners.
Figure 7. The simulation impact of on data sharing strategies’ evolution. (a) Analysis of on ; (b) analysis of on the strategy evolution for data requesters; (c) analysis of on the strategy evolution for data owners.
5. Discussion and Inspiration
Inspired by the evolutionary game analysis for data sharing, we first proposed a general methodological framework for blockchain-based IoT data sharing research as a guideline. Then, we designed a smart-contract-based dynamic system control mechanism according to our analysis in Section 4 to verify the robustness of system and performance of cooperation. A federated learning enabled data sharing experiment was also conducted.
5.1. A Research Framework for Blockchain-Based IoT Data Sharing
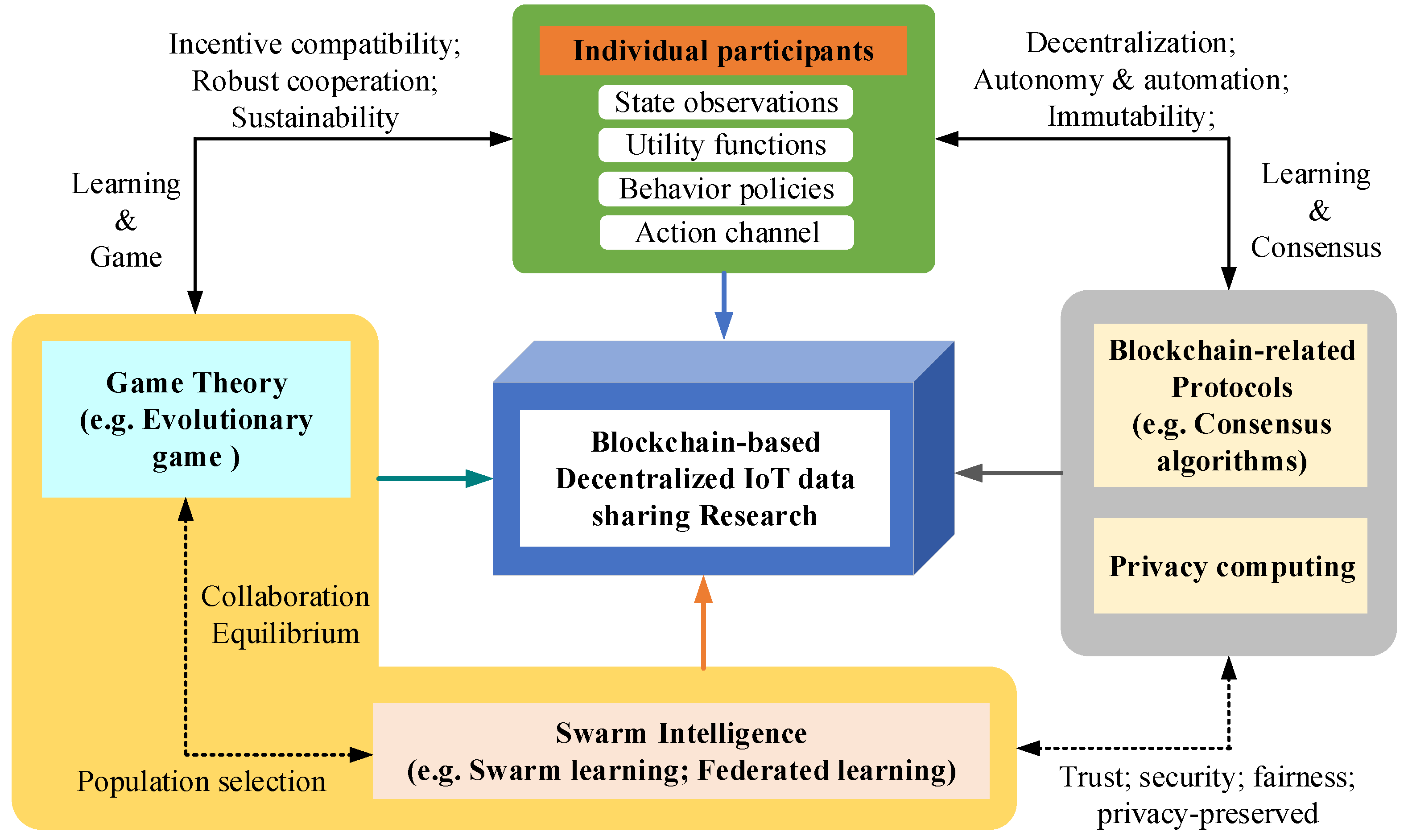
Based on the analysis mentioned above, we established a unified methodological framework for blockchain-based decentralized IoT data sharing research as shown in Figure 8, in which decentralized IoT data sharing can be seen as a multi-agent collaboration with blockchain as the underlying foundation. Compared with pure data content sharing, the data sharing method combined with an AI algorithm has a higher efficiency in mining data value, protecting data privacy, and improving edge intelligence. Therefore, a swarm intelligence module (such as swarm learning [23] or federated learning [24]) can be introduced to transform the data sharing problem into a multiagent collaborative training or learning problem. To guarantee the decentralization characteristics in edge intelligence, some blockchain-related protocols and privacy computing algorithms can be integrated into the framework to design a decentralized and privacy-enhanced swarm intelligent algorithm, so as to promise fair, secure, and trustful edge data sharing. Further, since participants in IoT data sharing scenarios are assumed to have bounded rationality, they can determine their action policies according to state observations and utility functions, and the corresponding decisions they make will vary with individual profit scenarios. In order to maintain a robust and sustainable data sharing environment, game theory (such as evolutionary game theory [22,25,26,27]) can be adopted to adjust the population selection to determine the collaboration equilibrium.
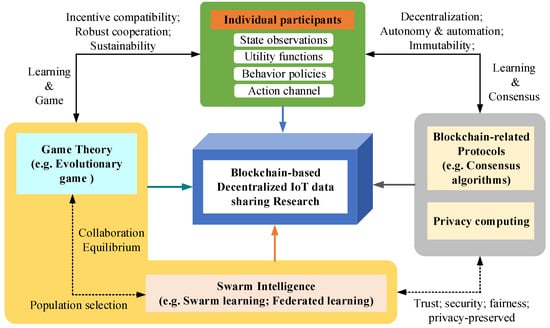
Figure 8.
A methodological framework for blockchain-based decentralized IoT data sharing research.
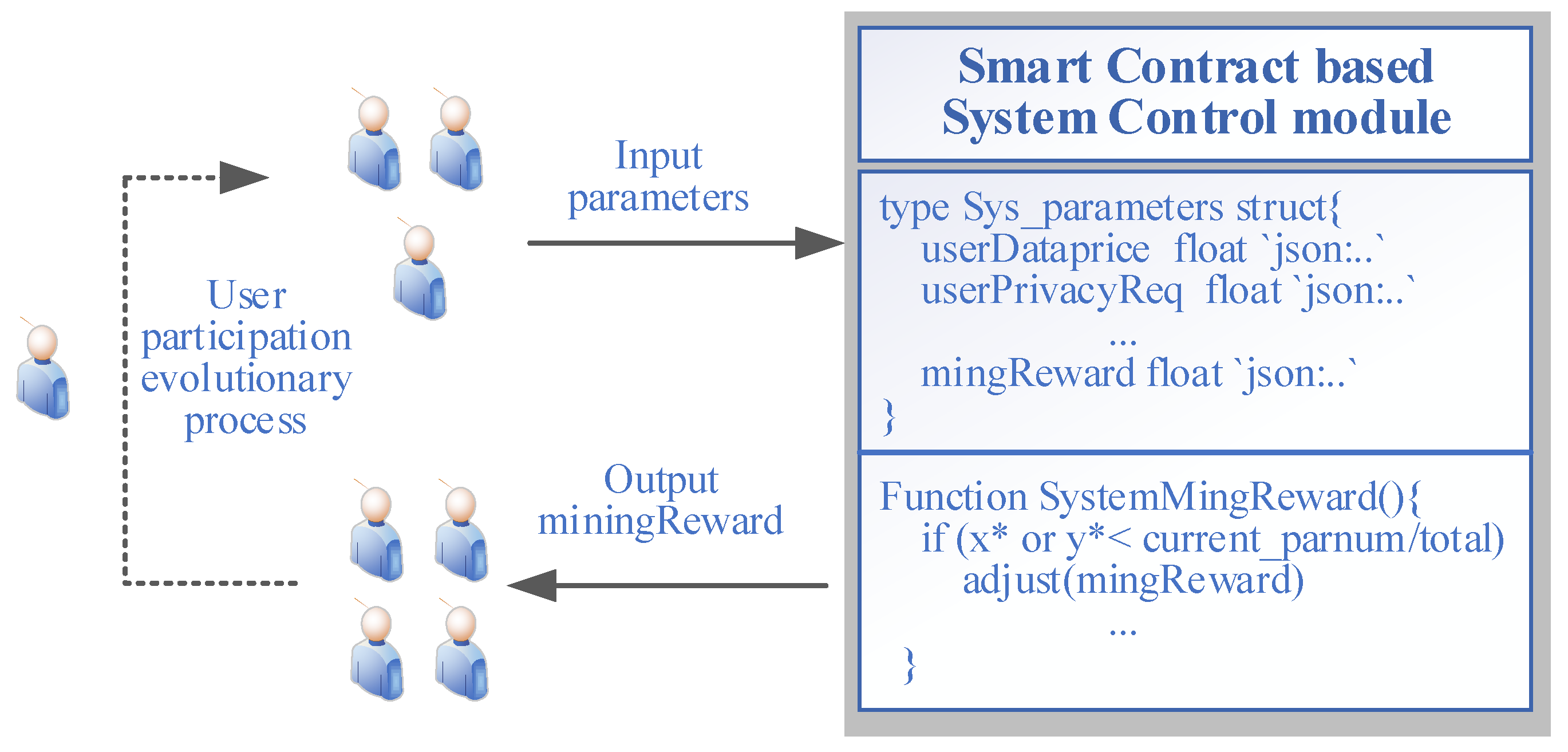
5.2. A Smart-Contract-Based Dynamic System Control Mechanism
The logic of maintaining robustness and sustainability in blockchain-based data sharing is that , in (9) and (10) must be greater than the participation ratio of users in the current system. Constrained by the different privacy protection requirements, degree of data sharing, data prices, limited resources of IoT, etc., there are always fluctuations in the proportion of participants in the system. Therefore, inspired by the analysis of the mining reward on the ESS, a smart-contract-enabled system control mechanism based on (9) and (10) was proposed, as shown in Figure 9. We utilized the Hyperledger-Fabric-channels, incorporating gossip and gRPC protocols, to emulate a BCFL network. Multithreading settings and goroutine channels were utilized for networking, connections, and coordination among 10 simulated FL participants. When IoT participants decide their parameters in a round of data sharing, these parameters can trigger smart contracts, so that the blockchain-based system can adjust the mining reward automatically according to the current participation ratio and change the value of , . For the visualization of the test results, a federated-learning-based data sharing experiment was conducted with a comparison of the collaboratively training accuracy. We used resnet18 as the learning model and Cifar10 as the dataset. Ten participants were initialized, and each contained 5000 training data points. The learning algorithm was written in python, and the smart contract was executed in Go in Hyperledger Fabric. In total, 30 epochs of co-training were performed, and after every three epochs (i.e., a T period includes three epochs), the number of users would change and then trigger smart contracts. The experimental results were as follows.

Figure 9.
The logic of the smart-contract-enabled dynamic system control mechanism.
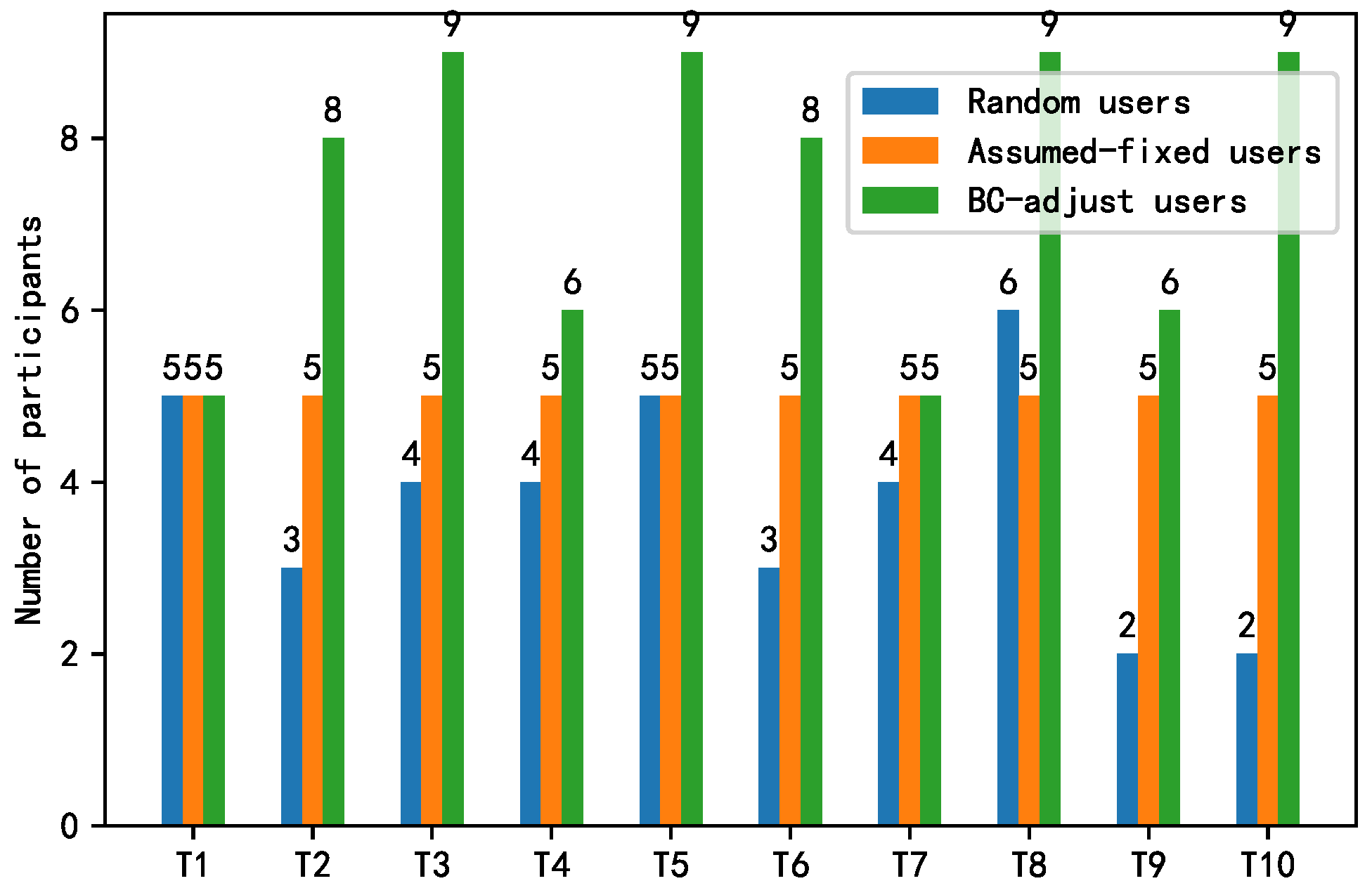
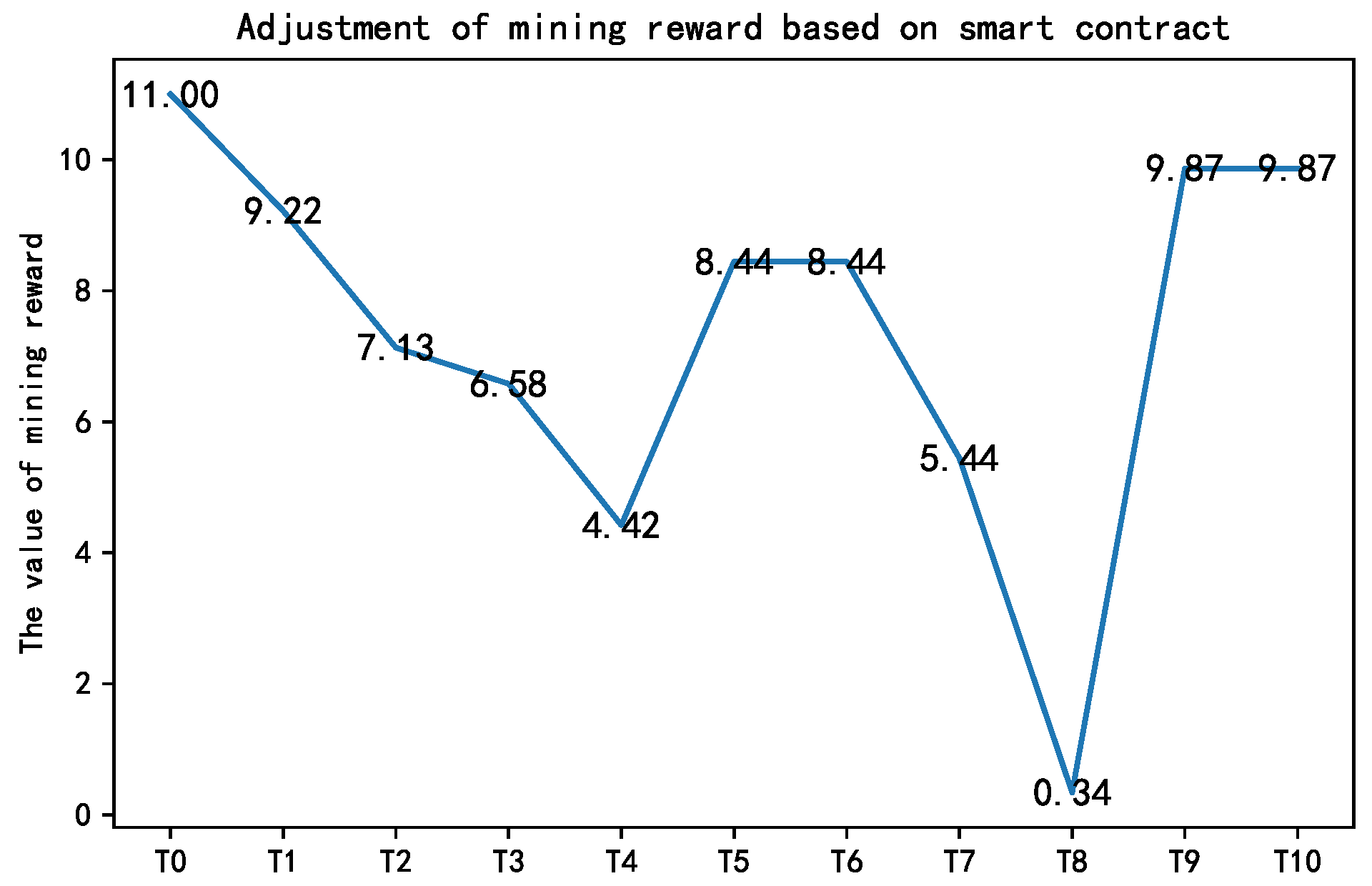
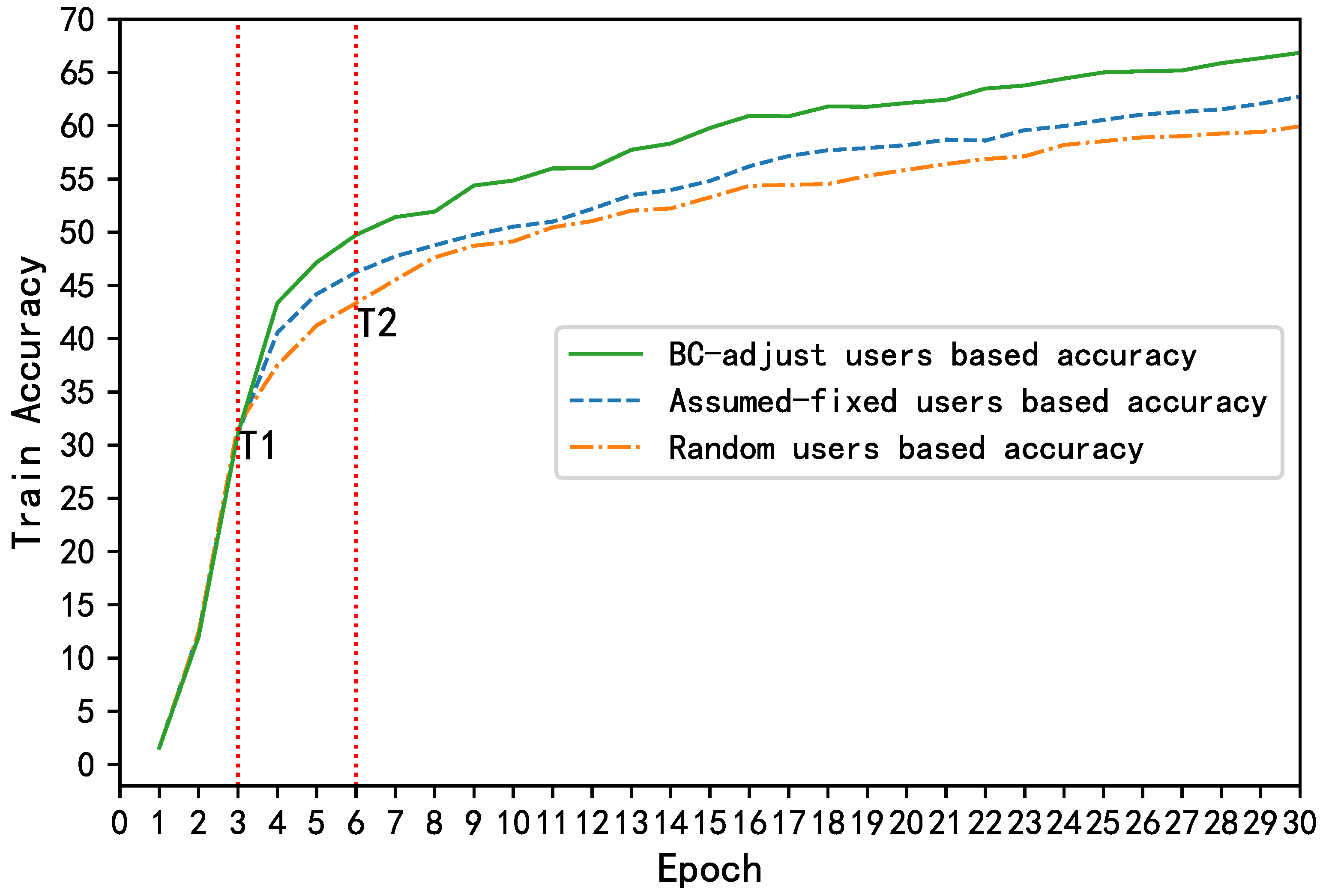
Figure 10 shows the changes in the number of participants during the training process. Random users was set to simulate the fluctuations of IoT devices in participating in federated learning, and BC-adjust users refers to the number of participants after the dynamic regulation based on the smart contract and Random users. As a comparison, an assumed fixed number of users was added to simulate an ideal FL process, where there are always a fixed number of trainers in each epoch. The results show that with the help of the smart-contract-based adjustment in Figure 11, the data owners were always prone to adopt the “participation” strategy to share data. As such, a larger number of co-trainers can be guaranteed to improve the training accuracy, as shown in Figure 12.
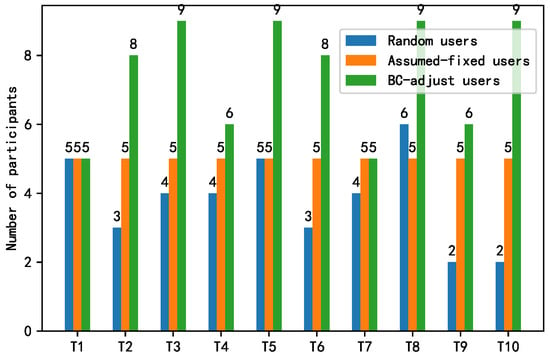
Figure 10.
Changes in the number of participants during the training process.
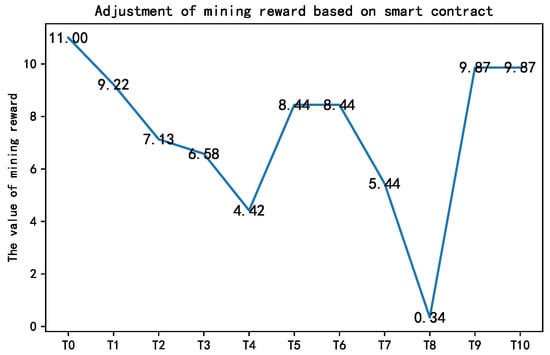
Figure 11.
Dynamic adjustment of the mining reward based on the smart contract.
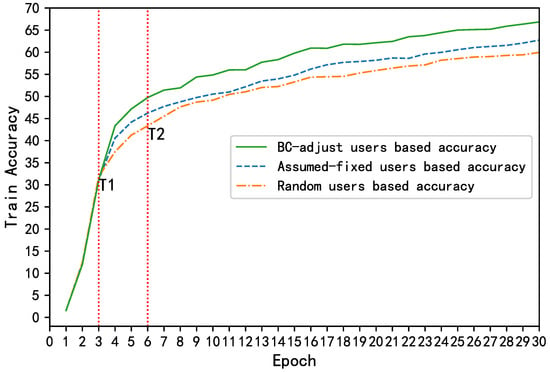
Figure 12.
Training accuracy under different participating strategies.
6. Conclusions
In this article, to fill the gap that few researchers explore the inner IoT data sharing laws and the evolutionary process of user participation in blockchain-enabled networks, our work first designed a blockchain-based IoT data sharing model to analyze the contributions of IoT for blockchain, data sharing logic, and topological relationships among participants. To analyze the stability of our architecture, an evolutionary game method was utilized to stimulate participation strategies according to the data value, data-flow profit, privacy cost, blockchain maintenance cost, and the penalty cost. Numerical analysis shows that an ESS strategy restricted by these elements can maximize the proportion of system users who participate and maintain a robust and sustainable data sharing, and this ESS strategy can also be achieved by a smart-contract-enabled dynamic system control mechanism, which can always incentive a higher participation ratio in decentralized IoT data sharing so as to promise a high quality of edge intelligence.
Our future research endeavors will focus on translating our original conclusions into tangible technical solutions, such as optimizing data value assessment, refining the calculation of data-flow profit, enhancing privacy protection mechanisms, and minimizing blockchain maintenance and penalty costs. By addressing these technical challenges, we can improve the stability of data sharing strategies and ensure a sustainable and efficient BCFL system.
Author Contributions
Conceptualization, Z.C. and Y.L.; methodology, Z.C.; software, Z.C. and B.W.; validation, Z.C. and Y.L.; formal analysis, Z.C. and Y.P. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the Hunan Province Graduate Innovation Project Fund (Grant No. CX20200042) grant number Ziwen Cheng.
Data Availability Statement
The data presented in this study are available on request from the corresponding author.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Nguyen, D.C.; Ding, M.; Pham, Q.V.; Pathirana, P.N.; Le, L.B.; Seneviratne, A.; Li, J.; Niyato, D.; Poor, H.V. Federated Learning Meets Blockchain in Edge Computing: Opportunities and Challenges. IEEE Internet Things J. 2021, 8, 12806–12825. [Google Scholar] [CrossRef]
- Singh, S.K.; Rathore, S.; Park, J.H. BlockIoTIntelligence: A Blockchain-enabled Intelligent IoT Architecture with Artificial Intelligence. Future Gener. Comput. Syst. 2020, 110, 721–743. [Google Scholar] [CrossRef]
- Estopace, E. IDC Forecasts Connected IoT Devices to Generate 79.4ZB of Data in 2025; [EB/OL]. Available online: https://futureiot.tech/ (accessed on 2 March 2022).
- Shen, X.S.; Liu, D.; Huang, C.; Xue, L.; Yin, H.; Zhuang, W.; Sun, R.; Ying, B. Blockchain for Transparent Data Management Toward 6G. Engineering 2022, 8, 74–85. [Google Scholar] [CrossRef]
- Deng, X.; Li, J.; Ma, C.; Wei, K.; Shi, L.; Ding, M.; Chen, W.; Poor, H.V. Blockchain Assisted Federated Learning Over Wireless Channels: Dynamic Resource Allocation and Client Scheduling. IEEE Trans. Wirel. Commun. 2023, 22, 3537–3553. [Google Scholar] [CrossRef]
- Liu, J.; Zhang, G.; Sun, R.; Du, X.; Guizani, M. A Blockchain-based Conditional Privacy-Preserving Traffic Data Sharing in Cloud. In Proceedings of the IEEE International Conference on Communications (ICC), Online, 7–11 June 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Liu, Y.; Du, H.; Niyato, D.; Kang, J.; Xiong, Z.; Miao, C.; Xuemin, S.; Jamalipour, A. Blockchain-Empowered Lifecycle Management for AI-Generated Content (AIGC) Products in Edge Networks. arXiv 2023, arXiv:2303.02836. [Google Scholar]
- AlSobeh, A.M.R.; Magableh, A.A. BlockASP: A Framework for AOP-based Model Checking Blockchain System. IEEE Access 2023, 11, 115062–115075. [Google Scholar] [CrossRef]
- Zarifis, A.; Efthymiou, L.; Cheng, X.; Demetriou, S. Consumer Trust in Digital Currency Enabled Transactions. In Lecture Notes in Business Information Processing, Proceedings of the Business Information Systems Workshops, Berlin, Germany, 18–20 July 2018; Abramowicz, W., Kokkinaki, A., Eds.; Spinger: Berlin/Heidelberg, Germany, 2014; pp. 241–254. [Google Scholar]
- Xiong, Z.; Zhang, Y.; Luong, N.C.; Niyato, D.; Wang, P.; Guizani, N. The Best of Both Worlds: A General Architecture for Data Management in Blockchain-enabled Internet-of-Things. IEEE Netw. 2020, 34, 166–173. [Google Scholar] [CrossRef]
- Lu, Y.; Huang, X.; Zhang, K.; Maharjan, S.; Zhang, Y. Blockchain and Federated Learning for 5G Beyond. IEEE Netw. 2021, 35, 219–225. [Google Scholar] [CrossRef]
- Ali, A.; Al-rimy, B.A.S.; Tin, T.T.; Altamimi, S.N.; Qasem, S.N.; Saeed, F. Empowering Precision Medicine: Unlocking Revolutionary Insights through Blockchain-Enabled Federated Learning and Electronic Medical Records. Sensors 2023, 23, 7476. [Google Scholar] [CrossRef]
- Yang, Q.; Liu, Y.; Chen, T.; Tong, Y. Federated Machine Learning: Concept and Applications. ACM Trans. Intell. Syst. Technol. 2019, 10, 1–19. [Google Scholar] [CrossRef]
- Issa, W.; Moustafa, N.; Turnbull, B.; Sohrabi, N.; Tari, Z. Blockchain-Based Federated Learning for Securing Internet of Things: A Comprehensive Survey. ACM Comput. Surv. 2023, 55, 1–43. [Google Scholar] [CrossRef]
- Xia, Q.; Sifah, E.B.; Asamoah, K.O.; Gao, J.; Du, X.; Guizani, M. MeDShare: Trust-Less Medical Data Sharing Among Cloud Service Providers via Blockchain. IEEE Access 2017, 5, 14757–14767. [Google Scholar] [CrossRef]
- Kang, J.; Yu, R.; Huang, X.; Wu, M.; Maharjan, S.; Xie, S.; Zhang, Y. Blockchain for Secure and Efficient Data Sharing in Vehicular Edge Computing and Networks. IEEE Internet Things J. 2019, 6, 4660–4670. [Google Scholar] [CrossRef]
- Yang, W.; Guan, Z.; Wu, L.; Du, X.; Guizani, M. Secure Data Access Control With Fair Accountability in Smart Grid Data Sharing: An Edge Blockchain Approach. IEEE Internet Things J. 2021, 8, 8632–8643. [Google Scholar] [CrossRef]
- Xu, L.; Bao, T.; Zhu, L. Blockchain Empowered Differentially Private and Auditable Data Publishing in Industrial IoT. IEEE Trans. Ind. Inform. 2021, 17, 7659–7668. [Google Scholar] [CrossRef]
- Liu, C.; Guo, S.; Guo, S.; Yan, Y.; Qiu, X.; Zhang, S. LTSM: Lightweight and Trusted Sharing Mechanism of IoT Data in Smart City. IEEE Internet Things J. 2022, 9, 5080–5093. [Google Scholar] [CrossRef]
- Zou, Y.; Shen, F.; Yan, F.; Lin, J.; Qiu, Y. Reputation-Based Regional Federated Learning for Knowledge Trading in Blockchain-Enhanced IoV. In Proceedings of the 2021 IEEE Wireless Communications and Networking Conference (WCNC), Nanjing, China, 29 March–1 April 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Nguyen, D.C.; Ding, M.; Pathirana, P.N.; Seneviratne, A.; Zomaya, A.Y. Federated Learning for COVID-19 Detection With Generative Adversarial Networks in Edge Cloud Computing. IEEE Internet Things J. 2022, 9, 10257–10271. [Google Scholar] [CrossRef]
- Hu, D.; Chen, J.; Zhou, H.; Yu, K.; Qian, B.; Xu, W. Leveraging Blockchain for Multi-Operator Access Sharing Management in Internet of Vehicles. IEEE Trans. Veh. Technol. 2022, 71, 2774–2787. [Google Scholar] [CrossRef]
- Warnat-Herresthal, S.; Schultze, H.; Shastry, K.L.; Manamohan, S.; Mukherejee, S.; Garg, V.; Sarsevawara, R.; Handler, K.; Pickkers, P.; Aziz, N.A.; et al. Swarm Learning for decentralized and confidential clinical machine learning. Nature 2021, 594, 265–270. [Google Scholar] [CrossRef]
- Peng, Z.; Xu, J.; Chu, X.; Gao, S.; Yao, Y.; Gu, R.; Tang, Y. VFChain: Enabling Verifiable and Auditable Federated Learning via Blockchain Systems. IEEE Trans. Netw. Sci. Eng. 2022, 9, 173–186. [Google Scholar] [CrossRef]
- Cui, S.; Liang, J.; Pan, W.; Chen, K.; Zhang, C.; Wang, F. Collaboration Equilibrium in Federated Learning. arXiv 2022, arXiv:2108.07926. [Google Scholar]
- Kang, J.; Xiong, Z.; Niyato, D.; Xie, S.; Zhang, J. Incentive Mechanism for Reliable Federated Learning: A Joint Optimization Approach to Combining Reputation and Contract Theory. IEEE Internet Things J. 2019, 6, 10700–10714. [Google Scholar] [CrossRef]
- Kang, J.; Xiong, Z.; Niyato, D.; Ye, D.; Kim, D.I.; Zhao, J. Toward Secure Blockchain-Enabled Internet of Vehicles: Optimizing Consensus Management Using Reputation and Contract Theory. IEEE Trans. Veh. Technol. 2019, 68, 2906–2920. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).