Efficient Graph Network Using Total Magic Labeling and Its Applications
Abstract
1. Introduction
2. Preliminaries
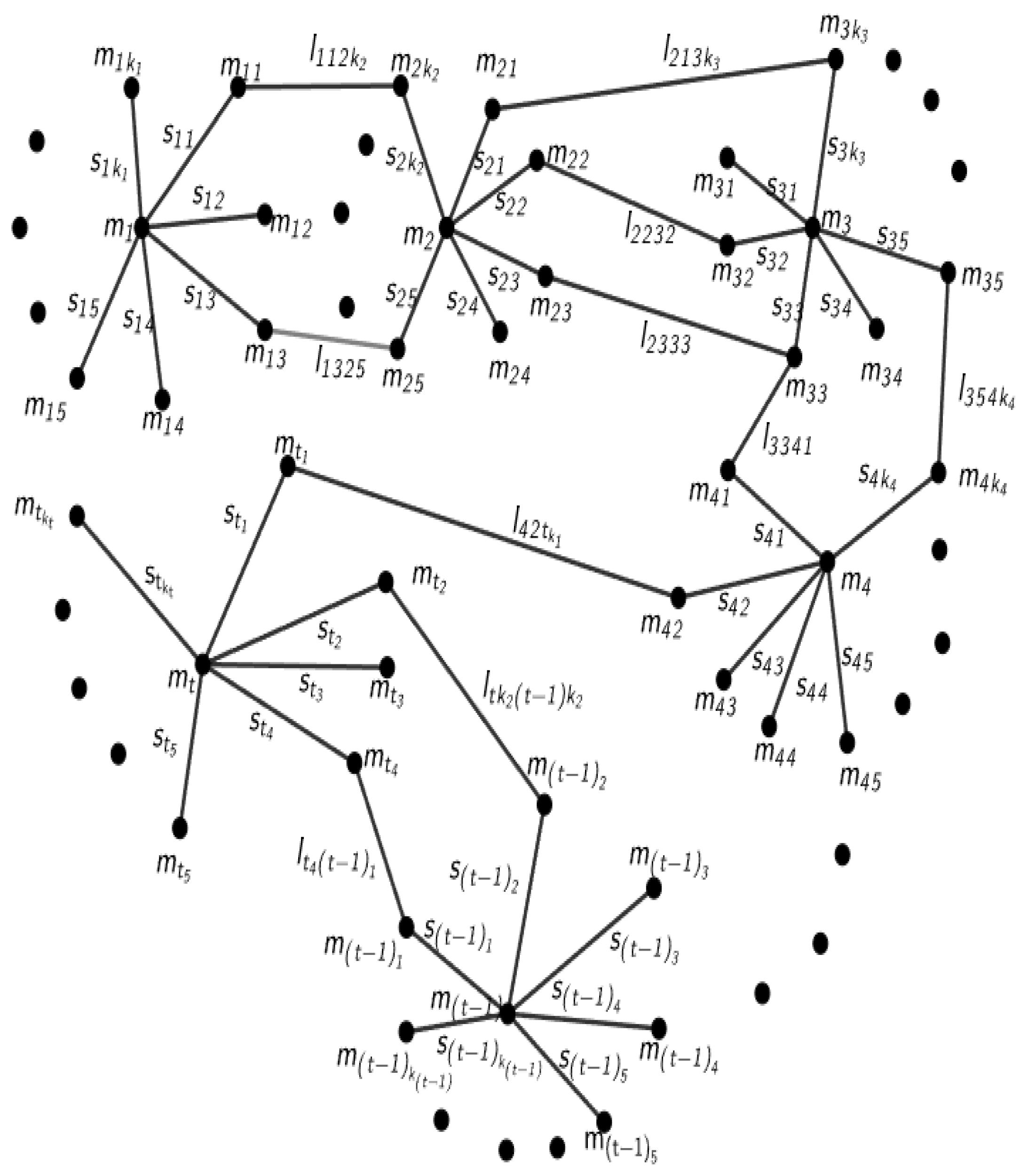
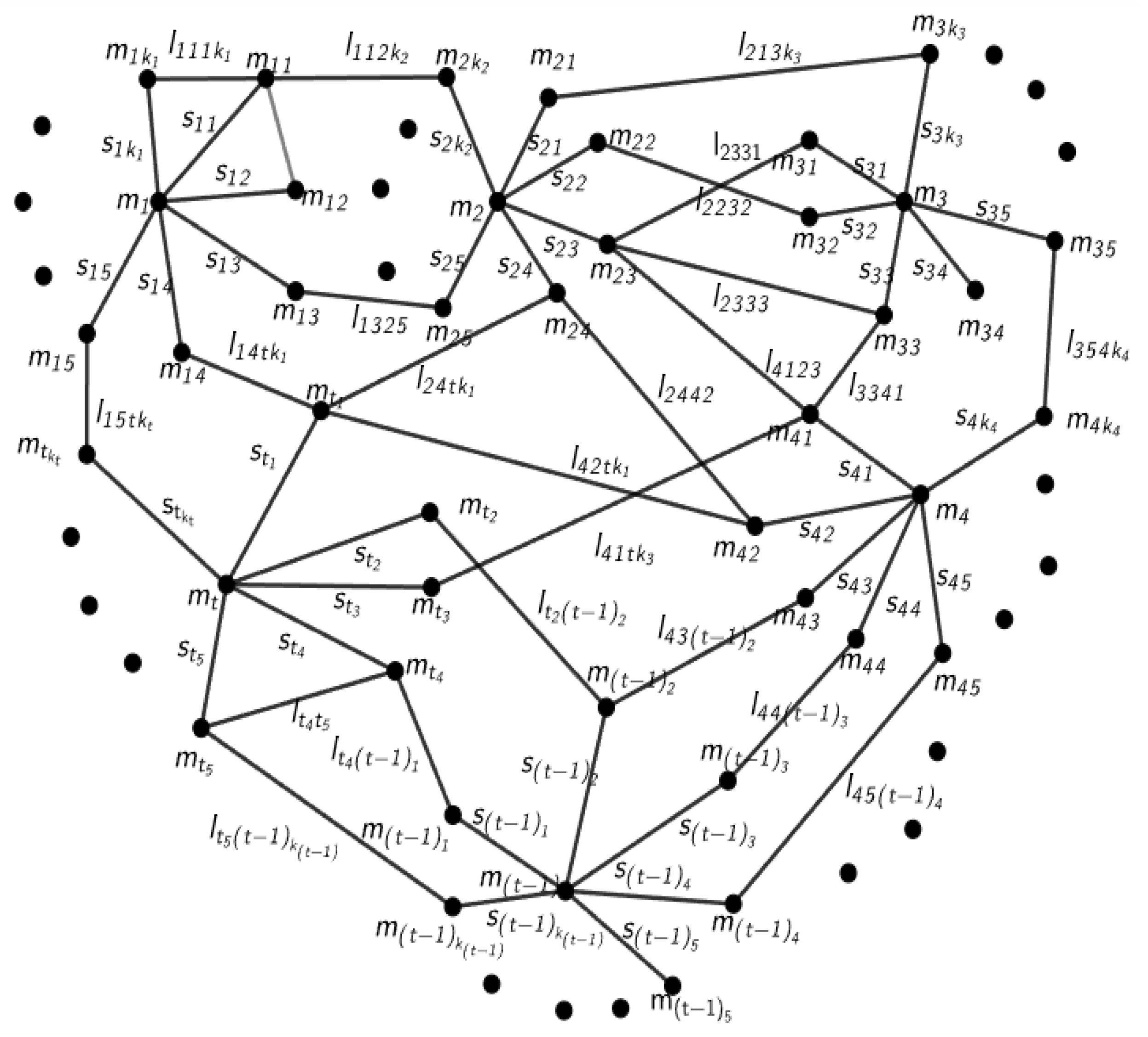
3. Graph Network Construction
4. Encryption System of Graph Network
4.1. Plain Text
4.2. Encryption Algorithm: LSN ≡ asn (mod t), Where asn = 0
4.3. Secret Key
4.4. Cypher Text
5. Decryption System of Graph Network
Decryption Algorithm
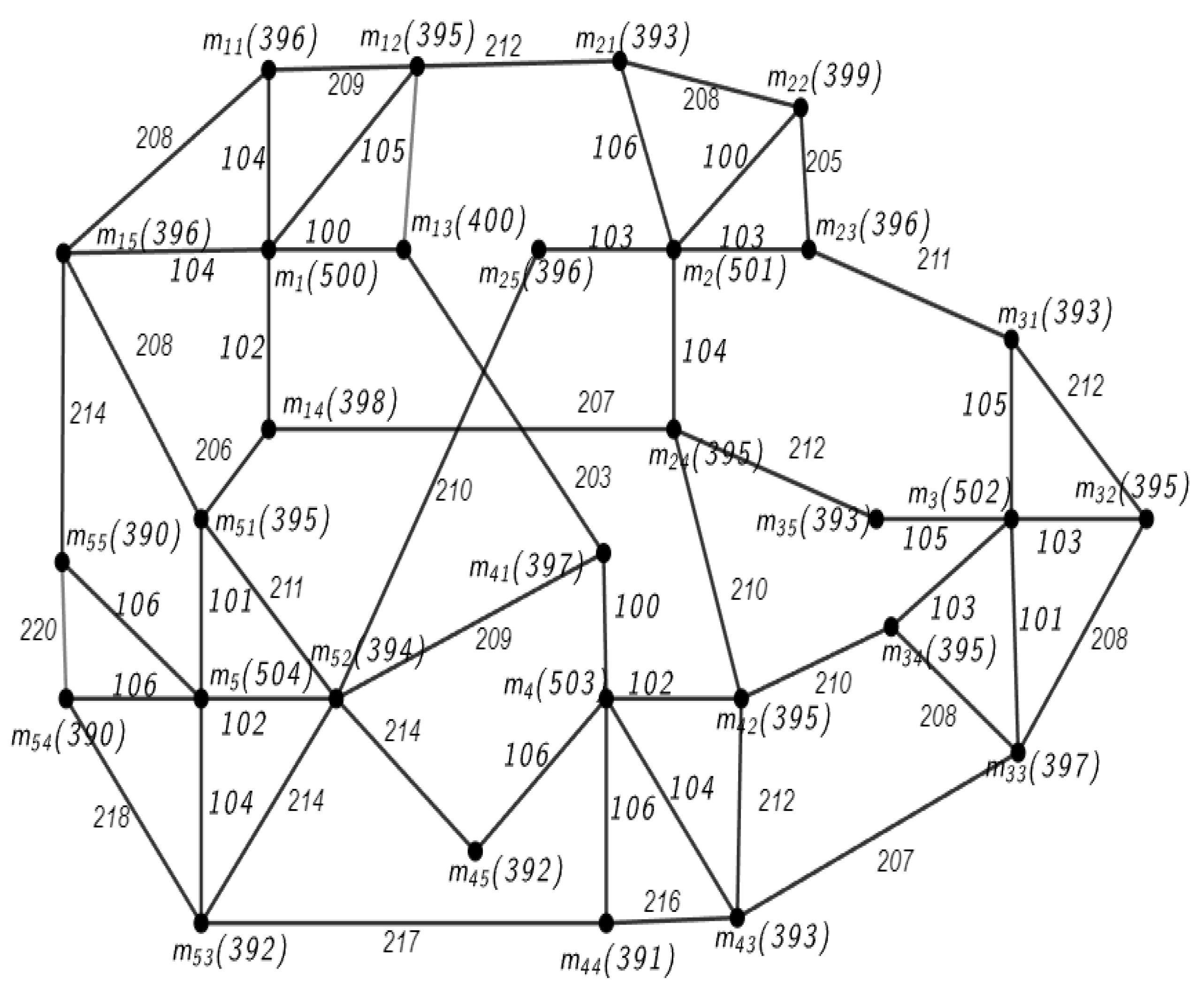
6. Illustration: Secret Number LSN ≡ asn (mod t), Where asn = 0 and t = 5
6.1. Graph Network for LSN ≡ asn (mod t), Where asn = 0 and t = 5
6.2. Encryption Algorithm
6.3. Decryption Algorithm
6.4. Secret Number LSN = 12,935 (mod t), Where = 0 and t = 5
6.4.1. Encrypting LSN, 12,935
6.4.2. DECRYPTING LSN, 12,935
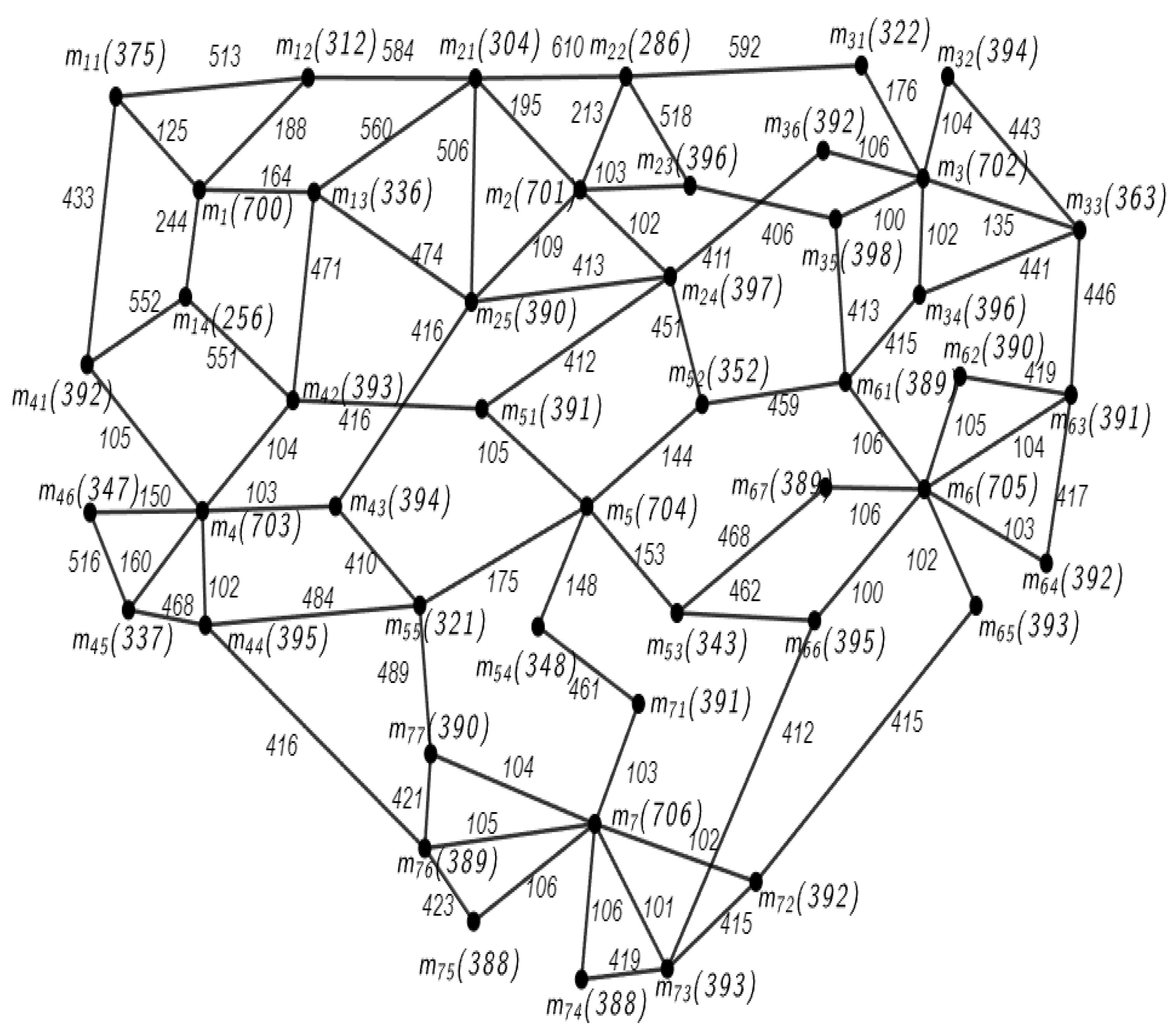
7. Illustration: Secret Number LSN ≡ asn (mod t), Where asn = 0 and t = 7
7.1. Graph Network Construction LSN ≡ asn (mod t), Where asn = 0 and t = 7
7.2. Encryption Algorithm
7.3. Decryption Algorithm
7.4. ILLUSTRATION: Secret Number LSN = 35497 ≡ asn (mod t), Where asn = 0 and t = 7
7.4.1. Graph Network Construction for LSN ≡ asn (mod t), Where asn = 0 and t = 7
7.4.2. ENCRYPTING LSN, 35,497
7.4.3. DECRYPTING LSN, 12,935
8. Adversary Model
9. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Ore, O. Theory of Graphs; American Mathematical Society Colloquium Publications: Providence, RI, USA, 1962. [Google Scholar]
- Bondy Murthy, J.A. Graph Theory with Applications; Elsevier Science Publishing Co., Inc.: New York, NY, USA, 1976. [Google Scholar]
- Haynes, T.W.; Hedetniemi, S.T.; Slater, P.J. Fundamentals of Domination in Graphs; Marcel Decker: New York, NY, USA, 1998. [Google Scholar]
- Cockayne, E.J.; Dawes, R.M.; Hedetniemi, S.T. Total domination in graphs. Networks 1980, 10, 211–219. [Google Scholar] [CrossRef]
- Bujtás, C. Domination number of graphs with minimum degree five. Discuss. Math. Graph Theory 2021, 41, 763–777. [Google Scholar] [CrossRef]
- Favaron, O.; Kabanov, V.; Puech, J. The ratio of three domination parameters in some classes of claw-free graphs. J. Comb. Math. Comb. Comput. 1999, 31, 151–160. [Google Scholar]
- Harary, F.; Haynes, T.W. Double domination in Graphs. Ars Comb. 2000, 55, 201–213. [Google Scholar]
- Gorzkowska, A.; Henning, M.A.; Kleszcz, E. Monika Pilśniak, Paired Domination in Trees. Graphs Comb. 2022, 38, 129. [Google Scholar] [CrossRef]
- Henning, M.A.; Pilśniak, M.; Tumidajewicz, E. Bounds on the paired domination number of graphs with minimum degree at least three. Appl. Math. Comput. 2022, 417, 12782. [Google Scholar] [CrossRef]
- Chellali, M.; Haynes, T.W. Total and paired domination numbers of a tree. AKCE Int. J. Graphs Comb. 2004, 1, 69–75. [Google Scholar]
- Edwards, M. Critically Concepts for Paired Domination in Graphs. Master’s Thesis, University of Victoria, Victoria, BC, Canada, 2006. [Google Scholar]
- Brigham, R.C.; Chinn, P.Z.; Dutton, R.D. Vertex domination-critical graphs. Networks 1988, 18, 173–179. [Google Scholar] [CrossRef]
- Hou, X.; Edwards, M. Paired Domination Vertex Critical Graphs. Graphs Comb. 2008, 24, 453–459. [Google Scholar] [CrossRef]
- Dunbar, J.E.; Haynes, T.W. Domination in inflated graphs. Congr. Numer. 1996, 118, 143–154. [Google Scholar]
- Favaron, O. Irredundance in inflated graphs. J. Graph Theory 1998, 28, 97–104. [Google Scholar] [CrossRef]
- Puech, J. The lower irredundance and domination parameters are equal for inflated trees. J. Comb. Math. Comb. Comput. 2000, 33, 117–127. [Google Scholar]
- Puech, J. Lower Domination Parameters in Inflated Trees; Research Report 97-57; Mathematical Department, UniversitNe Paris-Sud: Paris, France, 1997. [Google Scholar]
- Henning, M.A.; Kazemi, A.P. Total domination in inflated graphs. Discret. Appl. Math. 2012, 160, 164–169. [Google Scholar] [CrossRef][Green Version]
- Swaminathan, V.; Dharmalingam, K.M. Degree equitable domination on graphs. Kragujev. J. Math. 2011, 35, 191–197. [Google Scholar]
- Meenakshi, A. Equitable domination of complement of inflated graph. AIP Conf. Proc. 2019, 2112, 020079–1–6. [Google Scholar]
- Kumaran, N.; Meenakshi, A.; Mahdal, M.; Prakash, J.U.; Guras, R. Application of Fuzzy Network Using Efficient Domination. Mathematics 2023, 11, 2258. [Google Scholar] [CrossRef]
- Rosa, A. On Certain Valuations of the Vertices of a Graph, Theory of Graphs; Internat. Symposium: Rome, Italy, 1967. [Google Scholar]
- Hung, C.; Kotzig, A.; Rosa, A. Furter results on tree labellings. Util. Math. 1982, 21, 31–48. [Google Scholar]
- Grannell, M.J.; Griggs, T.S.; Holroyd, F.C. Modular gracious labellings of trees. Discret. Math. 2001, 231, 199–219. [Google Scholar] [CrossRef]
- Slater, P.J. On k-graceful graphs. In Proceedings of the 13th Southeastern Conference on Combinatorics, Graph Theory, and Computing, Boca Raton, FL, USA, 15–18 February 1982; Volume 53, p. 57. [Google Scholar]
- Lo, S.P. On edge-graceful labelings of graphs. Congr. Numer. 1985, 50, 231–241. [Google Scholar]
- MacDougall, J.A.; Miller, M.; Wallis, W.D. Vertex-magic total labelings of graphs. Util. Math. 2002, 61, 3–21. [Google Scholar]
- Tout, A.; Dabboucy, A.N.; Howalla, K. Prime labeling of graphs. Nat. Acad. Sci. Lett. 1982, 11, 365–368. [Google Scholar]
- Jeyanthi, P.; Maheswari, A. Some results on vertex equitable labeling. Open J. Discret. Math. 2012, 2012, 18867. [Google Scholar] [CrossRef][Green Version]
- Zhang, X.; Ye, C.; Zhang, S.; Yao, B. Graph Colorings and Labelings Having Multiple Restrictive Conditions in Topological Coding. Mathematics 2022, 10, 1592. [Google Scholar] [CrossRef]
- Zhang, X.; Ibrahim, M.; Bokhary, S.A.U.H.; Siddiqui, M.K. Edge irregular reflexive labeling for the disjoint union of gear graphs and prism graphs. Mathematics 2018, 6, 142. [Google Scholar] [CrossRef]
- Hao, J.; Gong, Y.; Sun, J.; Tan, L. Use the K-Neighborhood Subgraphs to Compute Canonical Labelings of Graphs. Mathematics 2019, 7, 690. [Google Scholar] [CrossRef]
- Allan, R.B.; Laskar, R.; Hedetniemi, S. A note on total domination. Discret. Math. 1984, 49, 7–13. [Google Scholar] [CrossRef]
- Liu, X.; Shi, T.; Zhou, G.; Liu, M.; Yin, Z.; Yin, L.; Zheng, W. Emotion classification for short texts: An improved multi-label method. Humanit. Soc. Sci. Commun. 2023, 10, 306. [Google Scholar] [CrossRef]
- Liu, X.; Zhou, G.; Kong, M.; Yin, Z.; Li, X.; Yin, L.; Zheng, W. Developing Multi-Labelled Corpus of Twitter Short Texts: A Semi-Automatic Method. Systems 2023, 11, 390. [Google Scholar] [CrossRef]
- Meenakshi, A.; Mythreyi, O.; Bramila, M.; Kannan, A.; Senbagamalar, J. Application of neutrosophic optimal network using operations. J. Intell. Fuzzy Syst. 2023, 45, 421–433. [Google Scholar] [CrossRef]
- Cheng, B.; Zhu, D.; Zhao, S.; Chen, J. Situation-Aware IoT Service Coordination Using the Event-Driven SOA Paradigm. IEEE Trans. Netw. Serv. Manag. 2016, 13, 349–361. [Google Scholar] [CrossRef]
- Li, B.; Zhou, X.; Ning, Z.; Guan, X.; Yiu, K.C. Dynamic event-triggered security control for networked control systems with cyber-attacks: A model predictive control approach. Inf. Sci. 2022, 612, 384–398. [Google Scholar] [CrossRef]
- Zhuang, Y.; Jiang, N.; Xu, Y.; Xiangjie, K.; Kong, X. Progressive Distributed and Parallel Similarity Retrieval of Large CT Image Sequences in Mobile Telemedicine Networks. Wirel. Commun. Mob. Comput. 2022, 2022, 1–13. [Google Scholar] [CrossRef]
- Idrees, M.S.; Roudier, Y.; Apvrille, L. Model the system from adversary viewpoint: Threats identification and modeling. Adv. Intrusion Prev. Workshop 2014, 165, 45–58. [Google Scholar]
- Zhang, J.; Peng, S.; Gao, Y.; Zhang, Z.; Hong, Q. APMSA: Adversarial Perturbation Against Model Stealing Attacks. IEEE Trans. Inf. Forensics Secur. 2023, 18, 1667–1679. [Google Scholar] [CrossRef]
- Jin, H.; Wang, Z.; Wu, L. Global dynamics of a three-species spatial food chain model. J. Differ. Equ. 2022, 333, 144–183. [Google Scholar] [CrossRef]
- Liu, P.; Shi, J.; Wang, Z.-A. Pattern formation of the attraction-repulsion Keller-Segel system. Discret. Contin. Dyn. Syst.-Ser. B 2013, 18, 2597–2625. [Google Scholar] [CrossRef]
- Jin, H.Y.; Wang, Z.A. Global stabilization of the full attraction-repulsion Keller-Segel system. Discret. Contin. Dyn. Syst.-Ser. A 2020, 40, 3509–3527. [Google Scholar] [CrossRef]
- Wang, F.; Wang, H.; Zhou, X.; Fu, R. A Driving Fatigue Feature Detection Method Based on Multifractal Theory. IEEE Sens. J. 2022, 22, 19046–19059. [Google Scholar] [CrossRef]
- Yang, S.; Li, Q.; Li, W.; Li, X.; Liu, A. Dual-Level Representation Enhancement on Characteristic and Context for Image-Text Retrieval. IEEE Trans. Circuits Syst. Video Technol. 2022, 32, 8037–8050. [Google Scholar] [CrossRef]
- Liu, A.-A.; Zhai, Y.; Xu, N.; Nie, W.; Li, W.; Zhang, Y. Region-Aware Image Captioning via Interaction Learning. IEEE Trans. Circuits Syst. Video Technol. 2022, 32, 3685–3696. [Google Scholar] [CrossRef]
- Qiao, F.; Li, Z.; Kong, Y. A Privacy-Aware and Incremental Defense Method Against GAN-Based Poisoning Attack. IEEE Trans. Comput. Soc. Syst. 2023. [Google Scholar] [CrossRef]
- Jiang, H.; Wang, M.; Zhao, P.; Xiao, Z.; Dustdar, S. A Utility-Aware General Framework with Quantifiable Privacy Preservation for Destination Prediction in LBSs. IEEE/ACM Trans. Netw. 2021, 29, 2228–2241. [Google Scholar] [CrossRef]
- Ma, J.; Hu, J. Safe consensus control of cooperative-competitive multi-agent systems via differential privacy. Kybernetika 2022, 58, 426–439. [Google Scholar] [CrossRef]
- Tan, J.; Jin, H.; Hu, H.; Hu, R.; Zhang, H.; Zhang, H. WF-MTD: Evolutionary Decision Method for Moving Target Defense Based on Wright-Fisher Process. IEEE Trans. Dependable Secur. Comput. 2022. [Google Scholar] [CrossRef]
- Lu, S.; Liu, M.; Yin, L.; Yin, Z.; Liu, X.; Zheng, W. The multi-modal fusion in visual question answering: A review of attention mechanisms. PeerJ Comput. Sci. 2023, 9, e1400. [Google Scholar] [CrossRef]
- Lu, S.; Ding, Y.; Liu, M.; Yin, Z.; Yin, L.; Zheng, W. Multiscale Feature Extraction and Fusion of Image and Text in VQA. Int. J. Comput. Intell. Syst. 2023, 16, 54. [Google Scholar] [CrossRef]

Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Meenakshi, A.; Kannan, A.; Cep, R.; Elangovan, M. Efficient Graph Network Using Total Magic Labeling and Its Applications. Mathematics 2023, 11, 4132. https://doi.org/10.3390/math11194132
Meenakshi A, Kannan A, Cep R, Elangovan M. Efficient Graph Network Using Total Magic Labeling and Its Applications. Mathematics. 2023; 11(19):4132. https://doi.org/10.3390/math11194132
Chicago/Turabian StyleMeenakshi, Annamalai, Adhimoolam Kannan, Robert Cep, and Muniyandy Elangovan. 2023. "Efficient Graph Network Using Total Magic Labeling and Its Applications" Mathematics 11, no. 19: 4132. https://doi.org/10.3390/math11194132
APA StyleMeenakshi, A., Kannan, A., Cep, R., & Elangovan, M. (2023). Efficient Graph Network Using Total Magic Labeling and Its Applications. Mathematics, 11(19), 4132. https://doi.org/10.3390/math11194132








