Security Threats and Cryptographic Protocols for Medical Wearables
Abstract
:1. Introduction
- Remote health monitoring systems (RHMS) are devices situated far from the system receiving the collected data.
- Mobile health monitoring systems (MHMS) are mobile devices such as mobile phones, computers, pocket laptops, etc., that monitor health parameters.
- Portable health monitoring systems or wearables include WHMS, RHMS and/or MHMS. These devices can be carried by patients in such a way that the sensors are integrated into clothing or accessory. These are called wearables. Thus, these give rise to smart fabrics, smart-textiles, or e-textiles.
2. Security in Medical Devices
- Firmware vulnerabilities: an inadequate development process of the software or the lack of authentication protocols in firmware updates facilitate the introduction of an altered, malicious firmware by an attacker. This vector is usually exploited by conducting inverse engineering to the original firmware, concretely in the cases in which there are no protection techniques as code obfuscating/packing [35]. Some authors defend that this attack vector is the most powerful, as it scales better than the others, and proportionates more benefits to the adversary, only requiring one interaction with the wearable [36].
- Communication protocols: most of the current WHMS transfer data to a database server or other electronic devices is done via BLE, Wi-Fi, and RF. These channels have been demonstrated in several studies to be vulnerable and leak the information of the patients [37,38]. Especially harmful is the scenario in which the transmitted data are not encrypted and can be directly interpreted [39].
- Applications and sensors: excessive privileged apps and sensors might be used by attackers to attack WHMS. This scenario can be conducted by substituting the original app by a malicious one, specifically designed by the adversary to perform concrete actions. Likewise, leaks of sensors readings can be used to infer the activity the patient was executing at a certain time [39].
- Eavesdropping: this attack takes advantage of poor communication protocols to secretly stole the transmitted data [38]. By doing this, the attacker can not only obtain critical health-related information of the patient, but also know the activities he has performed, the places he has visited and the format in which the WHMS stores the data [41].
- Replay attack: the attacker can go one step further from eavesdropping, introducing previous, eavesdropped data to compromise WHMS readings or gain illegitimate access to the patient’s devices. For example, if a wearable device has the permission to unlock the patient’s smartphone, the adversary might be able to unlock it by replaying information that has previously eavesdropped [29].
- Data tampering/modification: this attack occurs when the attacker modifies the measured data without having the proper authorization. To do this, the attacker must know the format in which the WHMS reads and transmits information, therefore this type of attack starts with an eavesdropping attack [34].
- Denial of service (DoS): the purpose of this attack is to alter the correct functioning of the WHMS by collapsing it with continuous orders. In this way, the battery of the device will run out very rapidly, or the patient will be unable to use it. A distributed DoS (DDoS) attack performed by botnets could lead many nodes to be involved in the attack [38,42].
- Side-channel attack: in this type of attack, the adversary uses information from the implementation of a WHMS to gather critical details of the patient. For example, an electromagnetic analysis can be conducted to derive the power consumption of a WHMS and, hence, extract the activities it is executing [43]. Likewise, it has been shown that information acquired from motion sensors of wearable devices can be used to profile the patient [39].
2.1. Firmware Vulnerabilities
2.2. Communication Protocols
2.3. Applications and Sensors
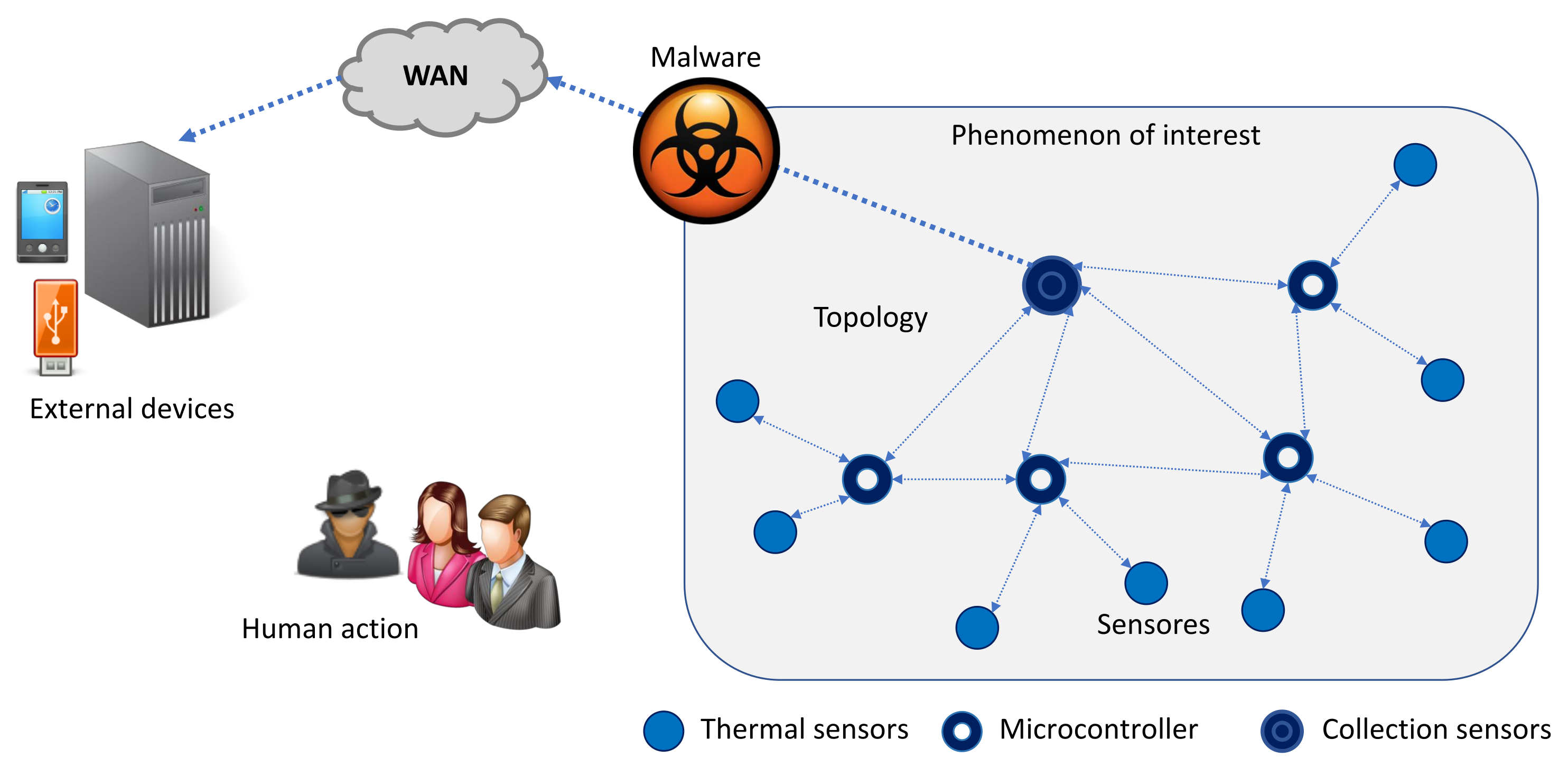
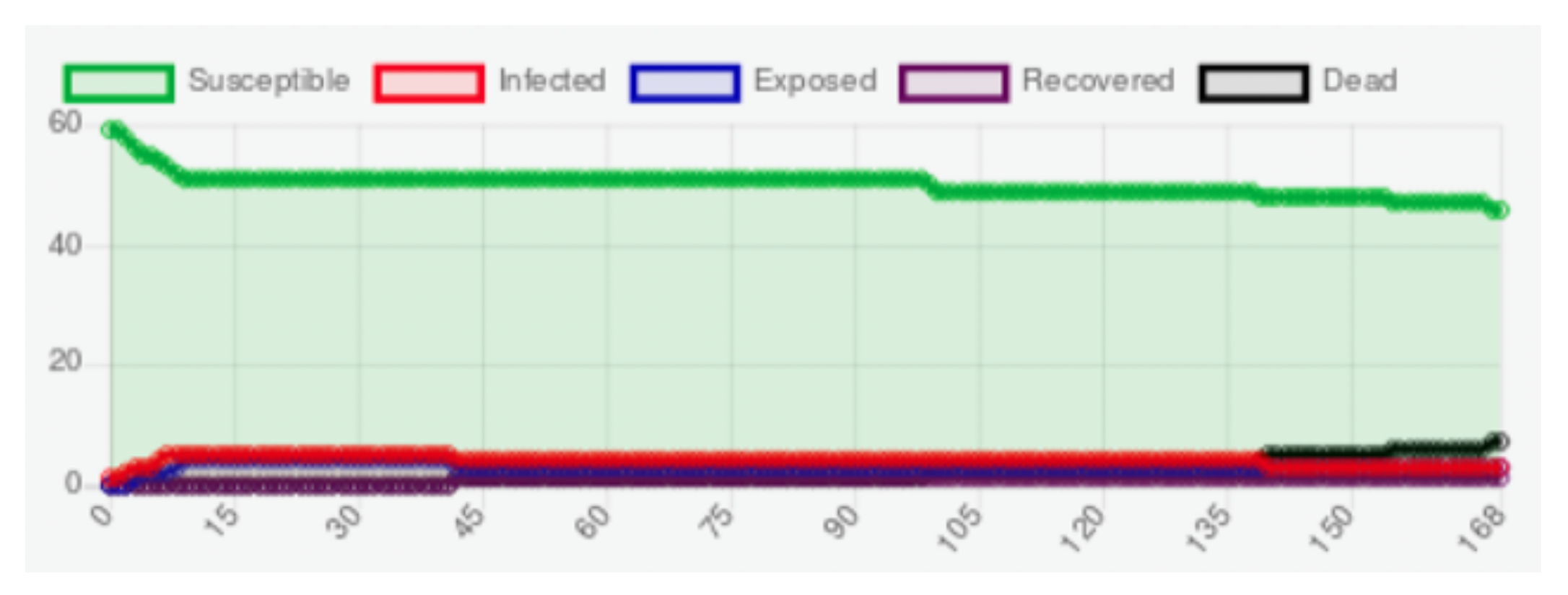
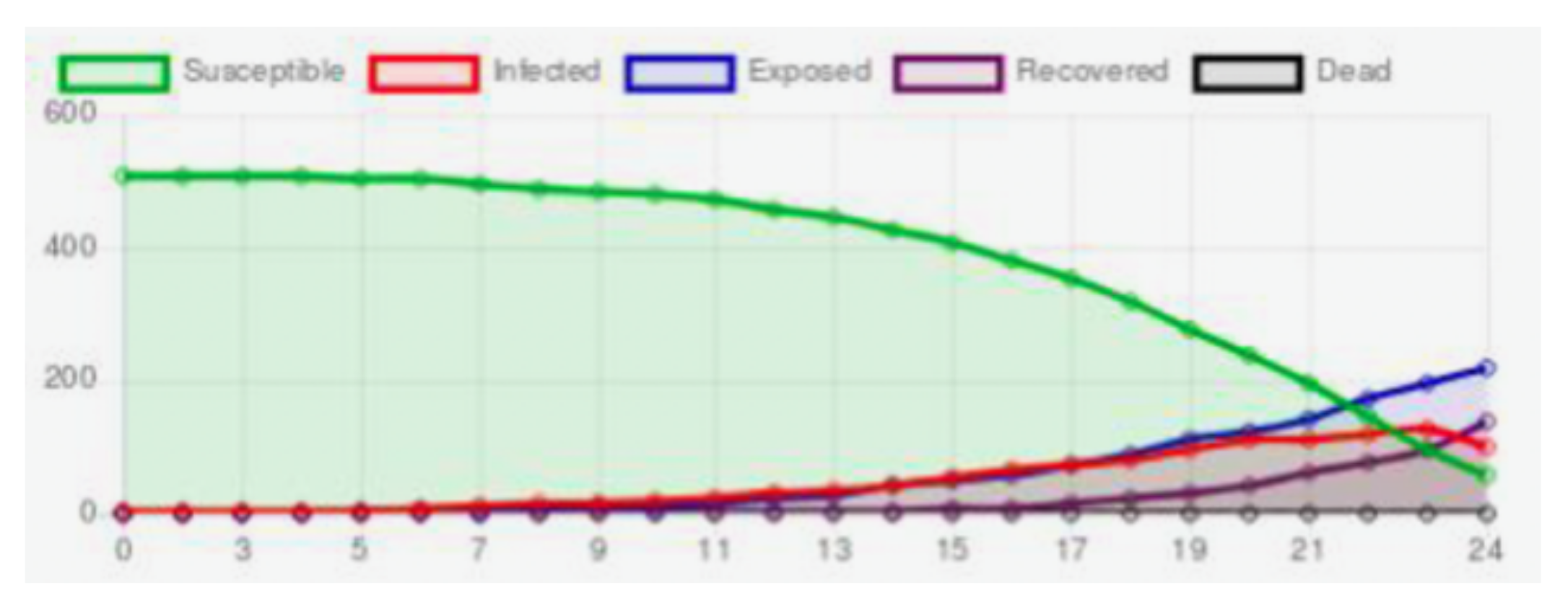
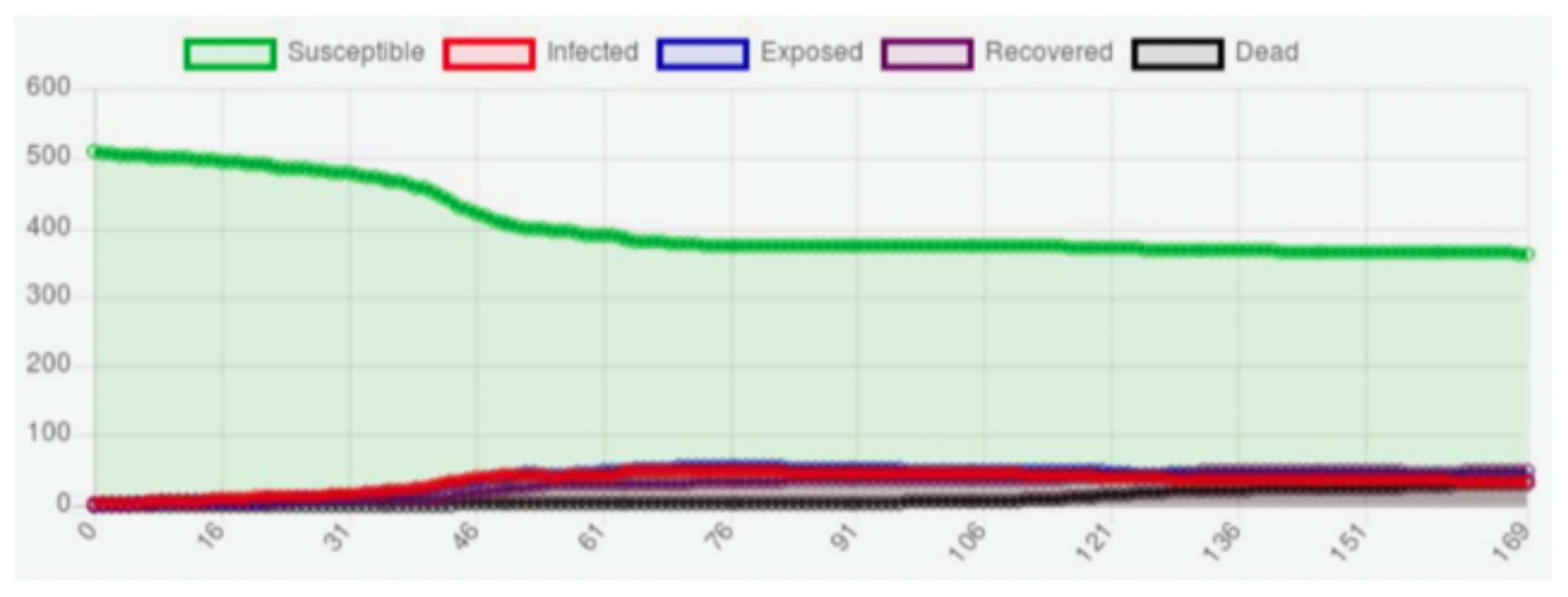
3. Simulation of a Malware Attack against Medical Devices
- Susceptible: the sensor has the characteristics for been infected by malware.
- Exposed: the malware has attacked the sensor, but the sensor cannot be transmitted to the sensors neighbors.
- Infected: the computational characteristics of the sensor allows it to be infected by malware and a sensor is capable of transmitting malware to its neighbors and the gateway.
- Recovered: the malware has been removed from the sensor, either by updating or fixing.
- Dead: the sensor battery life may be exhausted faster because of the infection of malware, and the sensor is no longer useful.
- WHMS sensors: are responsible for measuring various vital signs of a person, such as foot temperature.
- –
- Type of sensors: can be sensor, sink, and cluster-head nodes. Each one performs a particular function within the device.
- –
- Computational capacity: each WHMS can have computational capabilities, such as a microprocessor, memory, and storage, which allow performing different measurements.
- –
- Energy consumption: depends on the number and the frequency of measurements.
- –
- The capacity of transmission and reception of information: is related to the computational capacity; for example, a device with higher computational capacity will process more data and, in turn, transmit that information to its neighbours.
- –
- Security level: is critical, as the health data handled by these sensors are sensitive.
- –
- Data collection method: refers to the technique and periodicity in which a sensor performs measurements.
- –
- Duty cycle: when the sensor is not taking measurements, it may be in a inactive state, while its state is active when it is taking measurements.
- Malware: are those malicious codes that seek to perform unauthorized actions on the devices.
- –
- Type of malware: WMHS sensors may be affected by IoT-based malware.
- –
- Spreading mechanism: malware can use self-replication, exploit, or user interaction to perform malicious actions.
- –
- Target: the most common attacks for WHMS are DoS/DDoS or botnet attacks.
- Network topology: represents the form of communication of the sensors.
- –
- Type of topology: WHMS is based on a body area network.
- –
- Routing or communication protocols: depending on the tier, the communication is established through different protocols.
- The phenomenon of interest: the environment where these devices are located is outside hospitals to monitor patients during their daily activities.
- –
- Risk of malware attack: can range from low to high according to exposure to unsafe networks.
- Human action refers to human intervention in the device functioning.
- –
- Human action level on the network: may vary according to the required patient interaction with the device or sensors.
- External devices: connections to external devices for manual data download may expose the sensors to malware.
- –
- Risk of devices infected with malware: those external devices that can connect to unsecured networks are at higher risk of exposure to malware, and therefore, if a WHMS connects to this external device, it may have a high probability of malware infection.
4. Cryptographic Protocols to Secure Medical Devices
- Initialization: The algorithm starts with the key, K, the nonce, N, the rate, r, and the round numbers a and b as 8-bit integers. During this phase, a rounds of the round transformation are applied to the initial state.
- Processing associated data: during this state the data A is processed in r-bits blocks.
- Processing plaintext/ciphertext: the plain text, P and the ciphertext, C, are processed in blocks of r bits.
- Finalization: The encryption algorithm output consist on the tag, T, and the ciphertext blocks, , and the decryption one returns the plaintext blocks, (if T matches the calculated tag from the secret key).
5. Discussion
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| WHMS | Wearable health–monitoring systems |
| ECG | Electrocardiogram |
| RHMS | Remote health monitoring systems |
| MHMS | Mobile health monitoring systems |
| ROI | regions of interest |
| BAN | Body area network |
| BLE | Bluetooth Low Energy |
| RF | RadioFrequency |
| MITM | Man-in-the-middle |
| TLS | Transport Layer Security |
| DoS | Denial-of-service |
| AI | Artificial Intelligence |
| LWC | Lightweight cryptography |
| ABM | Agent-based model |
| AEAD | Authenticated encryption with associated data |
| CAESAR | Competition for Authenticated Encryption: Security, Applicability, and Robustness |
References
- Sacală, I.Ş.; Moisescu, M.A. The Development of Enterprise Systems based on Cyber-Physical Systems Principles. Rom. Stat. Rev. 2014, 4, 29–39. [Google Scholar]
- Robson, K.; Pitt, L.; Kietzmann, J.; Halvorson, W.; Wallstrom, A. Wearable Technology: Trends and Opportunities for Organizations. In Celebrating America’s Pastimes: Baseball, Hot Dogs, Apple Pie and Marketing? Springer: Berlin/Heidelberg, Germany, 2016; p. 801. [Google Scholar]
- Islam, S.R.; Kwak, D.; Kabir, M.H.; Hossain, M.; Kwak, K.S. The internet of things for health care: A comprehensive survey. IEEE Access 2015, 3, 678–708. [Google Scholar] [CrossRef]
- European Union. Regulation (EU) 2017/745 of the European Parliament and of the Council of 5 April 2017 on medical devices, amending Directive 2001/83/EC, Regulation (EC) No 178/2002 and Regulation (EC) No 1223/2009 and repealing Council Directives 90/385/EEC and 93/42/EEC. Off. J. Eur. Union 2017, 117, 1–175. [Google Scholar]
- Anliker, U.; Ward, J.A.; Lukowicz, P.; Troster, G.; Dolveck, F.; Baer, M.; Keita, F.; Schenker, E.B.; Catarsi, F.; Coluccini, L.; et al. AMON: A wearable multiparameter medical monitoring and alert system. IEEE Trans. Inf. Technol. Biomed. 2004, 8, 415–427. [Google Scholar] [CrossRef] [Green Version]
- Mundt, C.W.; Montgomery, K.N.; Udoh, U.E.; Barker, V.N.; Thonier, G.C.; Tellier, A.M.; Ricks, R.D.; Darling, R.B.; Cagle, Y.D.; Cabrol, N.A.; et al. A multiparameter wearable physiologic monitoring system for space and terrestrial applications. IEEE Trans. Inf. Technol. Biomed. 2005, 9, 382–391. [Google Scholar] [CrossRef] [PubMed]
- Gopalsamy, C.; Park, S.; Rajamanickam, R.; Jayaraman, S. The wearable motherboardTM: The first generation of adaptive and responsive textile structures (arts) for medical applications. Virtual Real. 1999, 4, 152–168. [Google Scholar] [CrossRef]
- Park, S.; Jayaraman, S. Enhancing the quality of life through wearable technology. IEEE Eng. Med. Biol. Mag. 2003, 22, 41–48. [Google Scholar] [CrossRef] [PubMed]
- Di Rienzo, M.; Rizzo, F.; Parati, G.; Brambilla, G.; Ferratini, M.; Castiglioni, P. MagIC system: A new textile-based wearable device for biological signal monitoring. Applicability in daily life and clinical setting. In Proceedings of the 2005 IEEE Engineering in Medicine and Biology 27th Annual Conference, Shanghai, China, 17–18 January 2005; pp. 7167–7169. [Google Scholar]
- Kandris, D.; Nakas, C.; Vomvas, D.; Koulouras, G. Applications of wireless sensor networks: An up-to-date survey. Appl. Syst. Innov. 2020, 3, 14. [Google Scholar] [CrossRef] [Green Version]
- Qiao, L.; Benzigar, M.R.; Subramony, J.A.; Lovell, N.H.; Liu, G. Advances in sweat wearables: Sample extraction, real-time biosensing, and flexible platforms. ACS Appl. Mater. Interfaces 2020, 12, 34337–34361. [Google Scholar] [CrossRef]
- Wang, B.; Facchetti, A. Mechanically flexible conductors for stretchable and wearable e-skin and e-textile devices. Adv. Mater. 2019, 31, 1901408. [Google Scholar] [CrossRef]
- Lou, Z.; Wang, L.; Jiang, K.; Wei, Z.; Shen, G. Reviews of wearable healthcare systems: Materials, devices and system integration. Mater. Sci. Eng. R Rep. 2020, 140, 100523. [Google Scholar] [CrossRef]
- Kang, S.K.; Murphy, R.K.; Hwang, S.W.; Lee, S.M.; Harburg, D.V.; Krueger, N.A.; Shin, J.; Gamble, P.; Cheng, H.; Yu, S.; et al. Bioresorbable silicon electronic sensors for the brain. Nature 2016, 530, 71–76. [Google Scholar] [CrossRef] [PubMed]
- Baig, M.M.; Gholamhosseini, H. Smart health monitoring systems: An overview of design and modeling. J. Med. Syst. 2013, 37, 1–14. [Google Scholar] [CrossRef] [PubMed]
- DeFronzo, R.A.; Ferrannini, E.; Zimmet, P.; Alberti, G. International Textbook of Diabetes Mellitus; John Wiley & Sons: Hoboken, NJ, USA, 2015. [Google Scholar]
- Macdonald, A.; Petrova, N.; Ainarkar, S.; Allen, J.; Plassmann, P.; Whittam, A.; Bevans, J.; Ring, F.; Kluwe, B.; Simpson, R.; et al. Thermal symmetry of healthy feet: A precursor to a thermal study of diabetic feet prior to skin breakdown. Physiol. Meas. 2016, 38, 33. [Google Scholar] [CrossRef]
- Torreblanca González, J.; Gómez-Martín, B.; Hernández Encinas, A.; Martín-Vaquero, J.; Queiruga-Dios, A.; Martínez-Nova, A. The Use of Infrared Thermography to Develop and Assess a Wearable Sock and Monitor Foot Temperature in Diabetic Subjects. Sensors 2021, 21, 1821. [Google Scholar] [CrossRef]
- Venkatasubramanian, K.K.; Banerjee, A.; Gupta, S.K.S. PSKA: Usable and secure key agreement scheme for body area networks. IEEE Trans. Inf. Technol. Biomed. 2010, 14, 60–68. [Google Scholar] [CrossRef]
- Jamil, F.; Iqbal, M.A.; Amin, R.; Kim, D. Adaptive thermal-aware routing protocol for wireless body area network. Electronics 2019, 8, 47. [Google Scholar] [CrossRef] [Green Version]
- Bhangwar, A.R.; Ahmed, A.; Khan, U.A.; Saba, T.; Almustafa, K.; Haseeb, K.; Islam, N. WETRP: Weight based energy & temperature aware routing protocol for wireless body sensor networks. IEEE Access 2019, 7, 87987–87995. [Google Scholar]
- Bhanumathi, V.; Sangeetha, C. A guide for the selection of routing protocols in WBAN for healthcare applications. Hum.-Centric Comput. Inf. Sci. 2017, 7, 1–19. [Google Scholar] [CrossRef]
- José Bulllón Pérez, J. Smart System to Monitor Temperature in Diabetic Foot. Ph.D. Thesis, Universidad de Salamanca, Salamanca, Spain, 2015. [Google Scholar]
- Al Ameen, M.; Liu, J.; Kwak, K. Security and Privacy Issues in Wireless Sensor Networks for Healthcare Applications. J. Med. Syst. 2012, 36, 93–101. [Google Scholar] [CrossRef] [Green Version]
- Siponen, M.T.; Oinas-Kukkonen, H. A review of information security issues and respective research contributions. ACM Sigmis Database 2007, 38, 60–80. [Google Scholar] [CrossRef]
- Dhanda, S.S.; Singh, B.; Jindal, P. Lightweight cryptography: A solution to secure IoT. Wirel. Pers. Commun. 2020, 112, 1947–1980. [Google Scholar] [CrossRef]
- Fotovvat, A.; Rahman, G.M.; Vedaei, S.S.; Wahid, K.A. Comparative Performance Analysis of Lightweight Cryptography Algorithms for IoT Sensor Nodes. IEEE Internet Things J. 2020, 8, 8279–8290. [Google Scholar] [CrossRef]
- Singh, S.; Sharma, P.K.; Moon, S.Y.; Park, J.H. Advanced lightweight encryption algorithms for IoT devices: Survey, challenges and solutions. J. Ambient. Intell. Humaniz. Comput. 2017, 1–18. [Google Scholar] [CrossRef]
- Alsubaei, F.; Abuhussein, A.; Shiva, S. Security and Privacy in the Internet of Medical Things: Taxonomy and Risk Assessment. In Proceedings of the 2017 IEEE 42nd Conference on Local Computer Networks Workshops (LCN Workshops), Singapore, 9–12 October 2017. [Google Scholar]
- Jain, A.; Nandakumar, K.; Nagar, A. Biometric Template Security. EURASIP J. Adv. Signal Process. 2008, 2008, 1–17. [Google Scholar] [CrossRef]
- Hernández Álvarez, F. Biometric Authentication for Users through Iris by Using Key Binding and Similarity Preserving Hash Functions. Ph.D. Thesis, Universidad Politécnica de Madrid, Madrid, Spain, 2015. [Google Scholar]
- Mills, A.J.; Watson, R.T.; Pitt, L.; Kietzmann, J. Wearing safe: Physical and informational security in the age of the wearable device. Bus. Horizons 2016, 59, 615–622. [Google Scholar] [CrossRef]
- Kim, D.; Park, S.; Choi, K.; Kim, Y. BurnFit: Analyzing and Exploiting Wearable Devices. In Proceedings of the WISA 2015: Information Security Applications, Jeju Island, Korea, 20–22 August 2015; Springer: Cham, Switzerland, 2016; pp. 227–239. [Google Scholar]
- Yaqoob, T.; Abbas, H.; Atiquzzaman, M. Security Vulnerabilities, Attacks, Countermeasures, and Regulations of Networked Medical Devices—A Review. IEEE Commun. Surv. Tutor. 2019, 21, 3723–3768. [Google Scholar] [CrossRef]
- Clausing, E.; Schiefer, M.; Lösche, U. Internet of Things Security Evaluation of nine Fitness Trackers Dipl; Independent IT-Security Institue AV TEST: Magdeburg, Germany, 2015; pp. 1–19. [Google Scholar]
- Rieck, J. Attacks on Fitness Trackers Revisited: A Case-Study of Unfit Firmware Security. arXiv 2016, arXiv:1604.03313. [Google Scholar]
- Kassem Fawaz, K.H.K.; Shin, K.G. Protecting Privacy of BLE Device Users. In Proceedings of the 25th USENIX Security Symposium (USENIX Security 16), Austin, TX, USA, 10–12 August 2016. [Google Scholar]
- Zhang, Q.; Liang, Z. Security analysis of bluetooth low energy based smart wristbands. In Proceedings of the 2017 2nd International Conference on Frontiers of Sensors Technologies (ICFST), Shenzhen, China, 14–16 April 2017; pp. 421–425. [Google Scholar]
- Hernández-Álvarez, L.; de Fuentes, J.M.; González-Manzano, L.; Encinas, L.H. SmartCAMPP—Smartphone-based continuous authentication leveraging motion sensors with privacy preservation. Pattern Recognit. Lett. 2021, 147, 189–196. [Google Scholar] [CrossRef]
- Fouad, M.; El-Bendary, N.; Ramadan, R.; Hassanien, A.E. Wireless Sensor Networks, A Medical Perspective; CRC Press: Boca Raton, FL, USA, 2013. [Google Scholar]
- Hernández-Álvarez, L.; De Fuentes, J.M.; González-Manzano, L.; Hernandez Encinas, L. Privacy-Preserving Sensor-Based Continuous Authentication and User Profiling: A Review. Sensors 2020, 21, 92. [Google Scholar] [CrossRef]
- Harbi, Y.; Aliouat, Z.; Refoufi, A.; Harous, S. Recent Security Trends in Internet of Things: A Comprehensive Survey. IEEE Access 2021, 9, 113292–113314. [Google Scholar] [CrossRef]
- Kim, Y.; Lee, W.S.; Raghunathan, A.; Raghunathan, V.; Jha, N. Reliability and security of implantable and wearable medical devices. In Implantable Biomedical Microsystems; William Andrew Publishing: Norwich, NY, USA, 2015; pp. 167–199. [Google Scholar]
- Arias, O.; Wurm, J.; Hoang, K.; Jin, Y. Privacy and Security in Internet of Things and Wearable Devices. IEEE Trans. Multi-Scale Comput. Syst. 2015, 1, 99–109. [Google Scholar] [CrossRef]
- Ly, K.; Jin, Y. Security Studies on Wereable Fitness Trackers. In Proceedings of the 38th Annual International Conference IEEE Engineering Mediocal Biological Society (EMBC), Orlando, FL, USA, 16–20 August 2016; p. 1. [Google Scholar]
- Shim, J.; Lim, K.; Jeong, J.; Cho, S.J.; Park, M.; Han, S. A Case Study on Vulnerability Analysis and Firmware Modification Attack for Wearable Fitness Tracker. IT Converg. Pract. 2017, 2, 1–24. [Google Scholar]
- Classen, J.; Wegemer, D.; Patras, P.; Spink, T.; Hollick, M. Anatomy of a Vulnerable Fitness Tracking System: Dissecting the Fitbit Cloud, App, and Firmware. Proc. ACM Interact. Mob. Wearable Ubiquitous Technol. 2018, 2, 1–24. [Google Scholar] [CrossRef] [Green Version]
- Li, C.; Raghunathan, A.; Jha, N.K. Hijacking an insulin pump: Security attacks and defenses for a diabetes therapy system. In Proceedings of the 2011 IEEE 13th International Conference on e-Health Networking, Applications and Services, Columbia, MO, USA, 13–15 June 2011; pp. 150–156. [Google Scholar]
- Li, C.; Zhang, M.; Raghunathan, A.; Jha, N.K. Attacking and defending a diabetes therapy system. In Security and Privacy for Implantable Medical Devices; Springer: New York, NY, USA, 2014. [Google Scholar]
- Mahmudur Rahman, B.C.; Banik, M. Fit and Vulnerable: Attacks and Defenses for a Health Monitoring Device. arXiv 2013, arXiv:1304.5672. [Google Scholar]
- Ching, K.; Mahinderjit Singh, M.M. Wearable Technology Devices Security and Privacy Vulnerability Analysis. Int. J. Netw. Secur. Its Appl. 2016, 8, 19–30. [Google Scholar] [CrossRef]
- Lotfy, K.; Hale, M.L. Assessing Pairing and Data Exchange Mechanism Security in the Wearable Internet of Things. In Proceedings of the 2016 IEEE International Conference on Mobile Services (MS), San Francisco, CA, USA, 27 June–2 July 2016. [Google Scholar]
- Goyal, R.; Dragoni, N.; Spognardi, A. Mind the Tracker You Wear: A Security Analysis of Wearable Health Trackers. In Proceedings of the 31st Annual ACM Symposium on Applied Computing, Pisa, Italy, 4–8 April 2016. [Google Scholar]
- Cusack, B.; Antony, B.; Ward, G.; Mody, S. Assessment of security vulnerabilities in wearable devices. In Proceedings of the 15th Australian Information Security Management Conference, Edith Cowan University, Perth, Australia, 5–6 December 2017; pp. 42–48. [Google Scholar]
- Wood, D.; Apthorpe, N.; Feamster, N. Cleartext Data Transmissions in Consumer IoT Medical Devices. In Proceedings of the 2017 Workshop on Internet of Things Security and Privacy, Dallas, TX, USA, 3 November 2017; Association for Computing Machinery: New York, NY, USA, 2017; pp. 7–12. [Google Scholar]
- Aliasgari, M.; Black, M.; Yadav, N. Security Vulnerabilities in Mobile Health Applications. In Proceedings of the 2018 IEEE Conference on Application, Information and Network Security (AINS), Langkawi, Malaysia, 21–22 November 2018; pp. 21–26. [Google Scholar]
- Almenárez-Mendoza, F.; Alonso, L.; Marín-López, A.; Cabarcos, P. Assessment of Fitness Tracker Security: A Case of Study. Proceedings 2018, 2, 1235. [Google Scholar] [CrossRef] [Green Version]
- Sethuraman, S.C.; Vijayakumar, V.; Walczak, S. Cyber Attacks on Healthcare Devices Using Unmanned Aerial Vehicles. J. Med. Syst. 2019, 44, 1–10. [Google Scholar] [CrossRef]
- Newaz, A.I.; Sikder, A.K.; Babun, L.; Uluagac, A.S. HEKA: A Novel Intrusion Detection System for Attacks to Personal Medical Devices. In Proceedings of the 2020 IEEE Conference on Communications and Network Security (CNS), Avignon, France, 29 June–1 July 2020; pp. 1–9. [Google Scholar]
- Thamilarasu, G.; Odesile, A.; Hoang, A. An Intrusion Detection System for Internet of Medical Things. IEEE Access 2020, 8, 181560–181576. [Google Scholar] [CrossRef]
- Chauhan, J.; Seneviratne, S.; Kaafar, M.A.; Mahanti, A.; Seneviratne, A. Characterization of early smartwatch apps. In Proceedings of the 2016 IEEE International Conference on Pervasive Computing and Communication Workshops (PerCom Workshops), Sydney, Australia, 14–18 March 2016; pp. 1–6. [Google Scholar]
- Maiti, A.; Jadliwala, M.; He, J.; Bilogrevic, I. (Smart)Watch Your Taps: Side-Channel Keystroke Inference Attacks Using Smartwatches. In Proceedings of the 2015 ACM International Symposium on Wearable Computers, Osaka Japan, 7–11 September 2015; pp. 27–30. [Google Scholar]
- Liu, X.; Zhou, Z.; Diao, W.; Li, Z.; Zhang, K. When Good Becomes Evil: Keystroke Inference with Smartwatch. In Proceedings of the 22nd ACM SIGSAC Conference on Computer and Communications Security, Denver, CO, USA, 12–16 October 2015. [Google Scholar]
- Wang, C.; Guo, X.; Wang, Y.; Chen, Y.; Liu, B. Friend or Foe? Your Wearable Devices Reveal Your Personal PIN. In Proceedings of the 11th ACM on Asia Conference on Computer and Communications Security, Xi’an, China, 30 May–3 June 2016. [Google Scholar]
- Khan, M.N.; Rao, A.; Camtepe, S. Lightweight cryptographic protocols for IoT-constrained devices: A survey. IEEE Internet Things J. 2020, 8, 4132–4156. [Google Scholar] [CrossRef]
- Batista, F.K.; Martin del Rey, A.; Queiruga-Dios, A. A new individual-based model to simulate malware propagation in wireless sensor networks. Mathematics 2020, 8, 410. [Google Scholar] [CrossRef] [Green Version]
- Masad, D.; Kazil, J. MESA: An agent-based modeling framework. In Proceedings of the 14th PYTHON in Science Conference, Austin, TX, USA, 6–12 July 2015; Volume 2015, pp. 53–60. [Google Scholar]
- NIST. Lightweight Cryptography. On-Line Publication. 2015. Available online: https://csrc.nist.gov/projects/lightweight-cryptography (accessed on 15 February 2022).
- Turan, M.S.; McKay, K.A.; Çalik, Ç.; Chang, D.; Bassham, L. Status Report on the First Round of the NIST Lightweight Cryptography Standardization Process; NIST Interagency/Internal Rep. (NISTIR); National Institute of Standards and Technology: Gaithersburg, MD, USA, 2019. [Google Scholar]
- NIST. Lightweight Cryptography, Finalists. On-Line Publication. 2021. Available online: https://csrc.nist.gov/Projects/lightweight-cryptography/finalists (accessed on 15 February 2022).
- Turan, M.S.; McKay, K.; Chang, D.; Calik, C.; Bassham, L.; Kang, J.; Kelsey, J. Status Report on the Second Round of the NIST Lightweight Cryptography Standardization Process; Technical Report; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2021. [Google Scholar] [CrossRef]
- Bovy, E.; Daemen, J.; Mennink, B. Comparison of the Second Round Candidates of the NIST Lightweight Cryptography Competition. Bachelor’s Thesis, Radboud University, Nijmegen, The Netherlands, 2020. [Google Scholar]
- Thakor, V.A.; Razzaque, M.A.; Khandaker, M.R. Lightweight cryptography algorithms for resource-constrained IoT devices: A review, comparison and research opportunities. IEEE Access 2021, 9, 28177–28193. [Google Scholar] [CrossRef]
- Aagaard, M.D.; Zidaric, N. Asic benchmarking of round 2 candidates in the NIST lightweight cryptography standardization process. Cryptol. ePrint Arch. 2021. Available online: https://eprint.iacr.org/2021/049.pdf (accessed on 15 February 2022).
- Jadhav, S.P. Towards light weight cryptography schemes for resource constraint devices in IoT. J. Mob. Multimed. 2019, 91–110. [Google Scholar] [CrossRef]
- Shor, P.W. Polynomial-time algorithms for prime factorization and discrete logarithms on a quantum computer. SIAM Rev. 1999, 41, 303–332. [Google Scholar] [CrossRef]
- Díaz, R.D.; Hernández-Álvarez, L.; Encinas, L.H.; Queiruga-Dios, A. Chor-Rivest Knapsack Cryptosystem in a Post-quantum World. In Advances in Security, Networks, and Internet of Things; Springer: Berlin/Heidelberg, Germany, 2021; pp. 67–83. [Google Scholar]
- NIST. Post-Quantum Cryptography. On-Line Publication. 2016. Available online: https://csrc.nist.gov/projects/post-quantum-cryptography (accessed on 15 February 2022).
- Zhang, P. Permutation-Based Lightweight Authenticated Cipher with Beyond Conventional Security. Secur. Commun. Netw. 2021, 2021, 1468007. [Google Scholar] [CrossRef]
- Hallman, R.; Bryan, J.; Palavicini, G.; Divita, J.; Romero-Mariona, J. IoDDoS-the internet of distributed denial of sevice attacks. In Proceedings of the 2nd International Conference on Internet of Things, Big Data and Security, SCITEPRESS, Porto, Portugal, 24–26 April 2017; pp. 47–58. [Google Scholar]
- Marzano, A.; Alexander, D.; Fonseca, O.; Fazzion, E.; Hoepers, C.; Steding-Jessen, K.; Chaves, M.H.; Cunha, Í.; Guedes, D.; Meira, W. The evolution of bashlite and mirai iot botnets. In Proceedings of the 2018 IEEE Symposium on Computers and Communications (ISCC), Natal, Brazil, 25–28 June 2018; pp. 00813–00818. [Google Scholar]
- Hayajneh, T.; Mohd, B.J.; Imran, M.; Almashaqbeh, G.; Vasilakos, A.V. Secure authentication for remote patient monitoring with wireless medical sensor networks. Sensors 2016, 16, 424. [Google Scholar] [CrossRef] [Green Version]
- Khan, S.; Lee, W.K.; Hwang, S.O. Scalable and efficient hardware architectures for authenticated encryption in IoT applications. IEEE Internet Things J. 2021, 8, 11260–11275. [Google Scholar] [CrossRef]
- Bertoni, G.; Daemen, J.; Peeters, M.; Van Assche, G. Permutation-based encryption, authentication and authenticated encryption. In Proceedings of the Workshop Records of Dir. Authenticated Ciphers (DIAC), Stockholm, Sweden, 5–6 July 2012; pp. 159–170. [Google Scholar]
- Bertoni, G.; Daemen, J.; Peeters, M.; Van Assche, G. Duplexing the sponge: Single-pass authenticated encryption and other applications. In Proceedings of the International Workshop on Selected Areas in Cryptography, Toronto, ON, Canada, 11–12 August 2011; pp. 320–337. [Google Scholar]
- Dobraunig, C.; Eichlseder, M.; Mendel, F.; Schläffer, M. Ascon v1. 2. CAESAR Competition. On-Line Publication. 2016. Available online: https://competitions.cr.yp.to/round3/asconv12.pdf (accessed on 15 February 2022).


| Type of Agents | Characteristics |
|---|---|
| WHMS sensors | Type: Sensor or sink nodes |
| Computational capacity: Low | |
| Energy consumption: Low or medium | |
| Capacity of transmission and reception of information: Low | |
| Security level for nodes: Low or medium | |
| Data collection method: Periodical or requested | |
| Duty cycle: Active or inactive | |
| Malware | Type: IoT based malware |
| Spreading mechanisms: Self-replication, exploit, or user interaction | |
| Target: DoS/DDoS or botnet attack, or information exfiltration | |
| Network topology | Type: BAN |
| Routing protocols: ATAR/WETRP, BLE/Wi-Fi/RF or Internet | |
| Phenomenon of interest | Risk of malware attack: medium or high |
| Human action | Level: medium or high |
| External devices | Risk of devices infected with malware: Low, medium or high |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Hernández-Álvarez, L.; Bullón Pérez, J.J.; Batista, F.K.; Queiruga-Dios, A. Security Threats and Cryptographic Protocols for Medical Wearables. Mathematics 2022, 10, 886. https://doi.org/10.3390/math10060886
Hernández-Álvarez L, Bullón Pérez JJ, Batista FK, Queiruga-Dios A. Security Threats and Cryptographic Protocols for Medical Wearables. Mathematics. 2022; 10(6):886. https://doi.org/10.3390/math10060886
Chicago/Turabian StyleHernández-Álvarez, Luis, Juan José Bullón Pérez, Farrah Kristel Batista, and Araceli Queiruga-Dios. 2022. "Security Threats and Cryptographic Protocols for Medical Wearables" Mathematics 10, no. 6: 886. https://doi.org/10.3390/math10060886
APA StyleHernández-Álvarez, L., Bullón Pérez, J. J., Batista, F. K., & Queiruga-Dios, A. (2022). Security Threats and Cryptographic Protocols for Medical Wearables. Mathematics, 10(6), 886. https://doi.org/10.3390/math10060886







