A New Construction and Convergence Analysis of Non-Monotonic Iterative Methods for Solving ρ-Demicontractive Fixed Point Problems and Variational Inequalities Involving Pseudomonotone Mapping
Abstract
:1. Introduction
Is it possible to introduce strongly convergent inertial extragradient methods for solving variational inequalities and fixed point problems with a self-adaptive step size rule without requiring Mann and Viscosity-type methods?
2. Preliminaries
- (1)
- (2)
- (3)
- (1)
- (2)
- (1)
- L-Lipschitz continuous if there exists a constant such that
- (2)
- pseudomonotone if
- (3)
- sequentially weakly continuous if a sequence weakly convergent to for any sequence that is weakly convergent to
- (4)
- ρ-demicontractive if there exists a constant such thator equivalently
- (ℑ 1)
- The solution set
- (ℑ 2)
- The mapping ℑ is pseudomonotone, Lipschitz continuous and sequentially weakly continuous;
- (ℑ 3)
- The is -demicontractive and is demiclosed at zero.
3. Main Results
| Algorithm 1 Inertial Subgradient Extragradient Method with Non-Monotone Step Size Rule. |
Step 0: Take Moreover, select a non-negative real sequence such that and satisfies the following conditions:
Step 1: Compute
while taken as follows:
Moreover, a positive sequence such that Step 2: Compute
If , then STOP. Else, move to Step 3. Step 3: First, construct a half-space and compute
Step 4: Compute Step 5: Compute
Set and go back to Step 1. |
| Algorithm 2 Inertial Tseng’s Extragradient Method with Non-Monotone Step Size Rule. |
Step 0: Take Moreover, select a non-negative real sequence such that and satisfies the following conditions:
Step 1: Compute
while taken as follows:
Moreover, a positive sequence such that Step 2: Compute
If , then STOP. Otherwise, go to Step 3. Step 3: Compute
Step 4: Compute
Step 5: Compute
Set and move back to Step 1. |
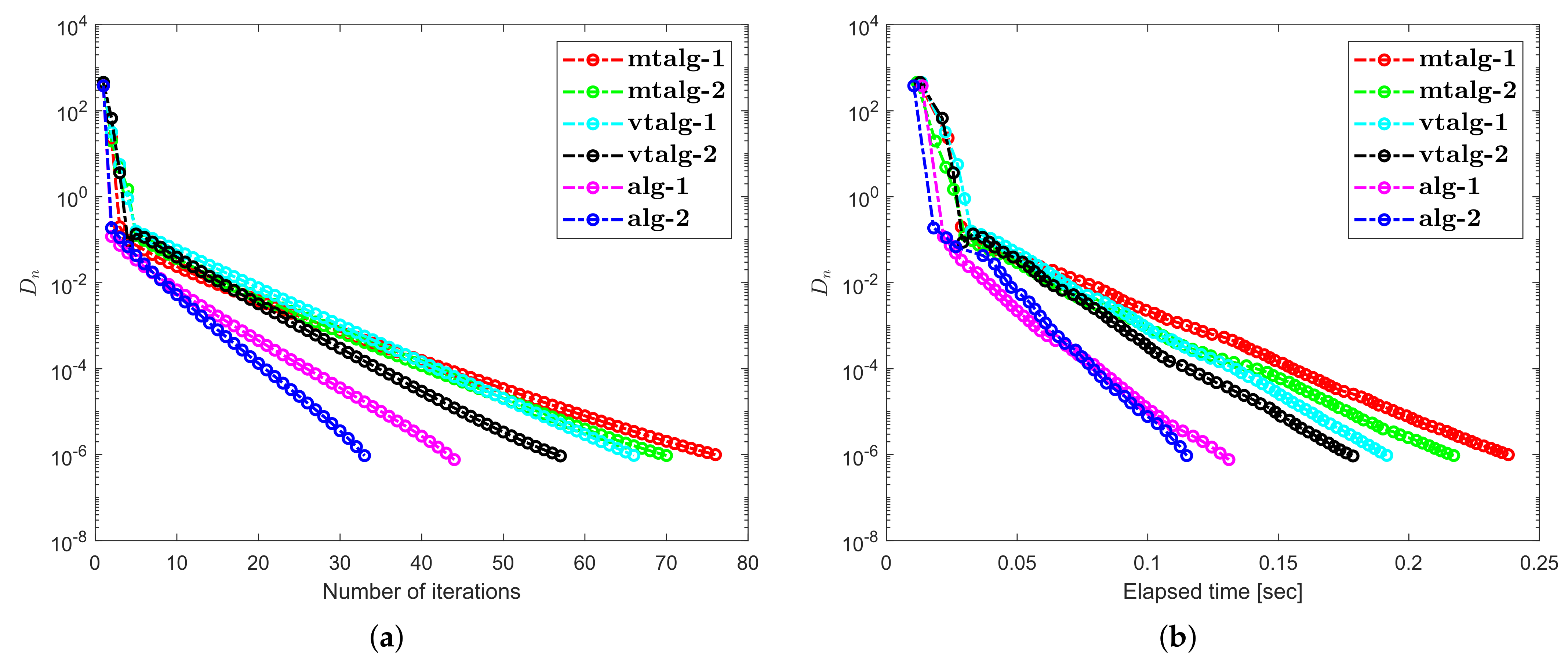
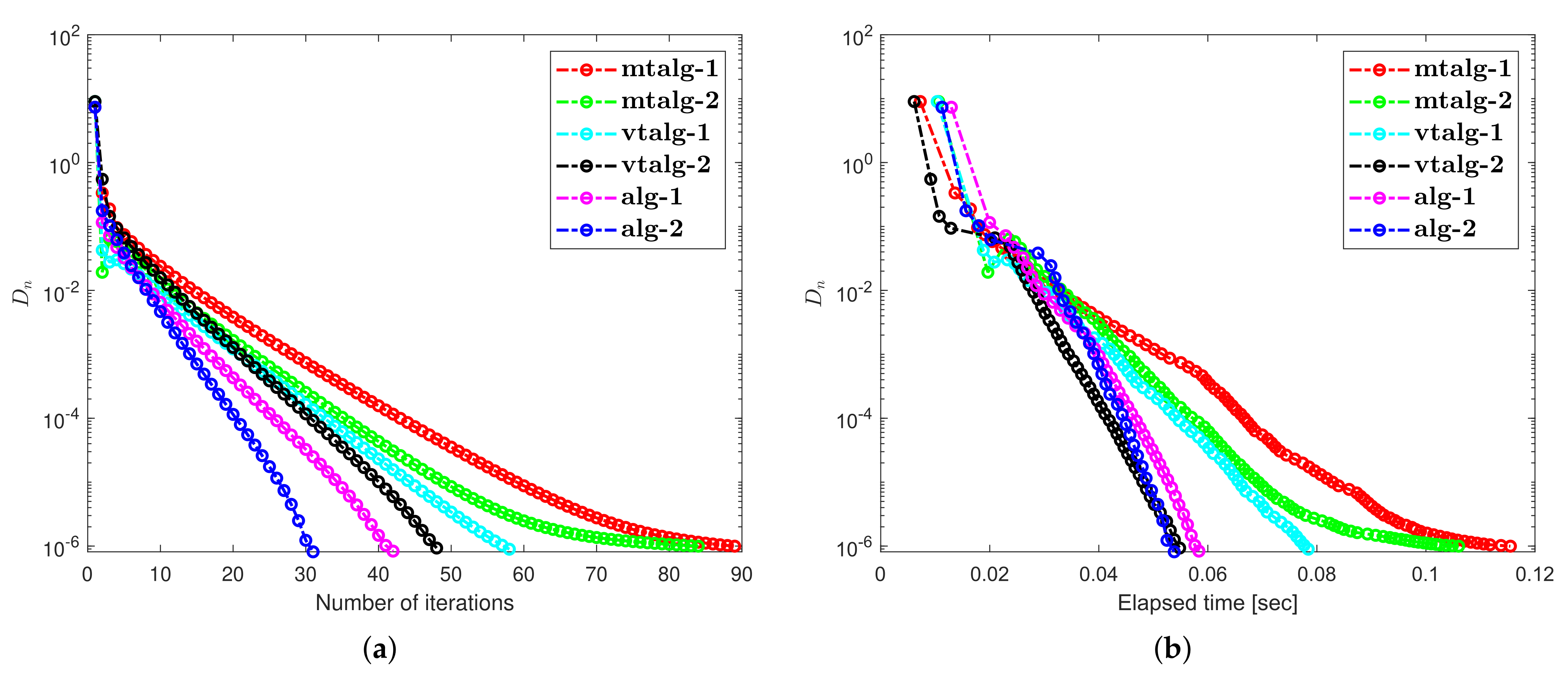
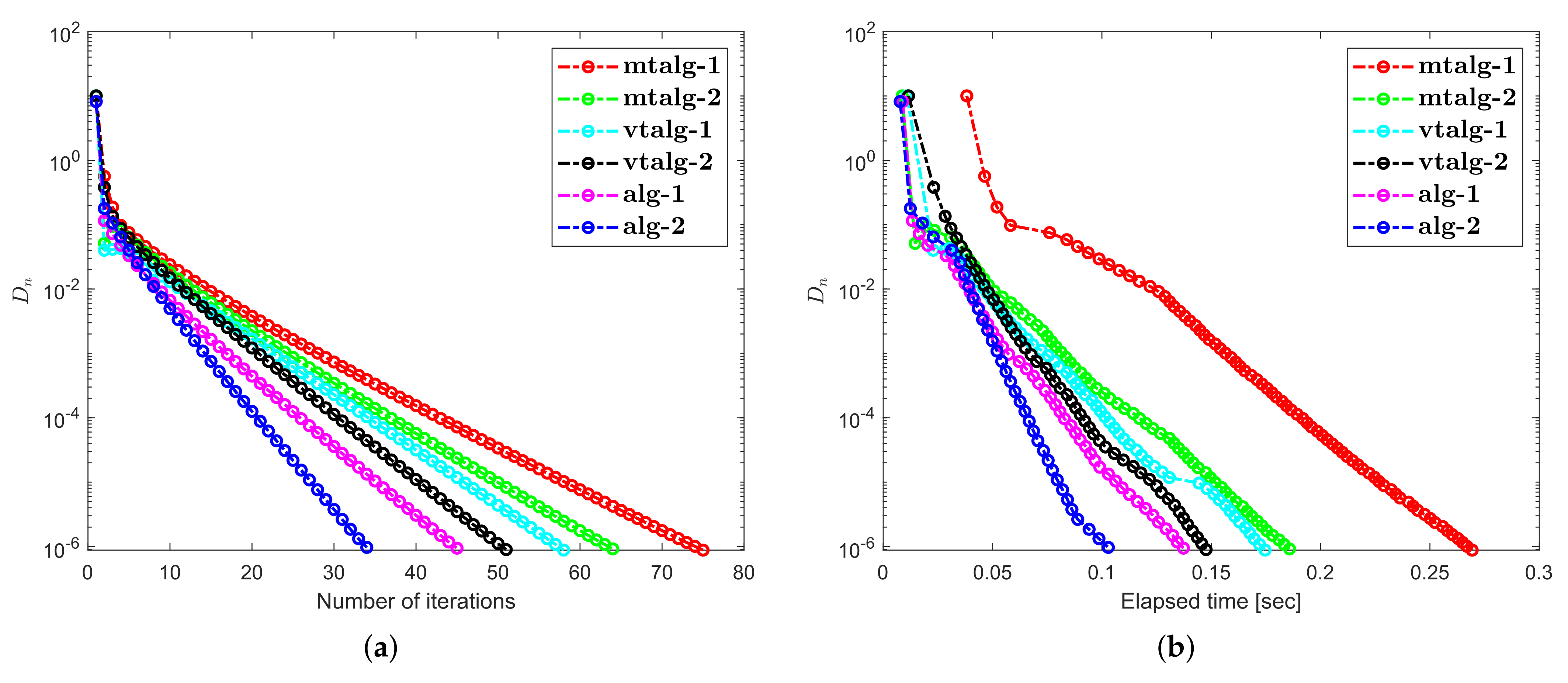
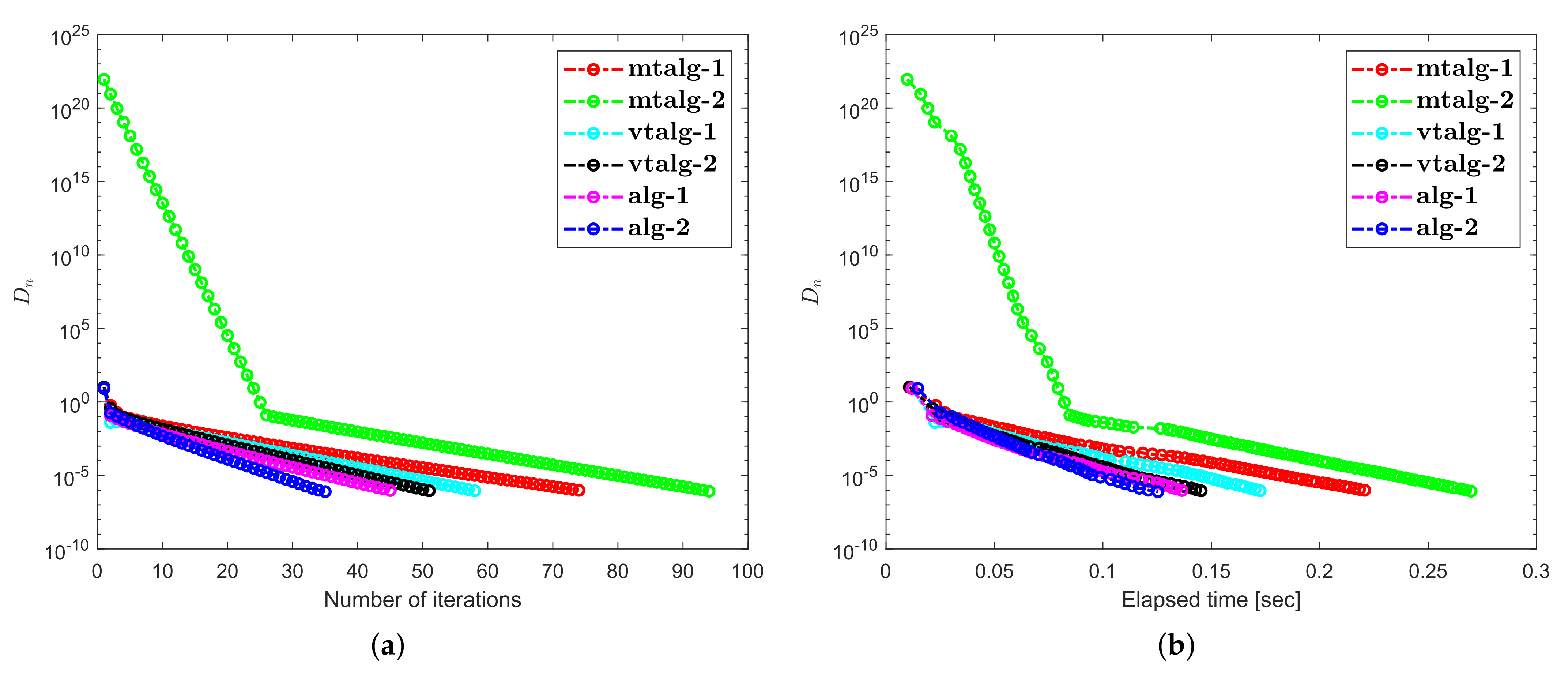
4. Numerical Illustrations
5. Discussion about Numerical Illustrations
- (1)
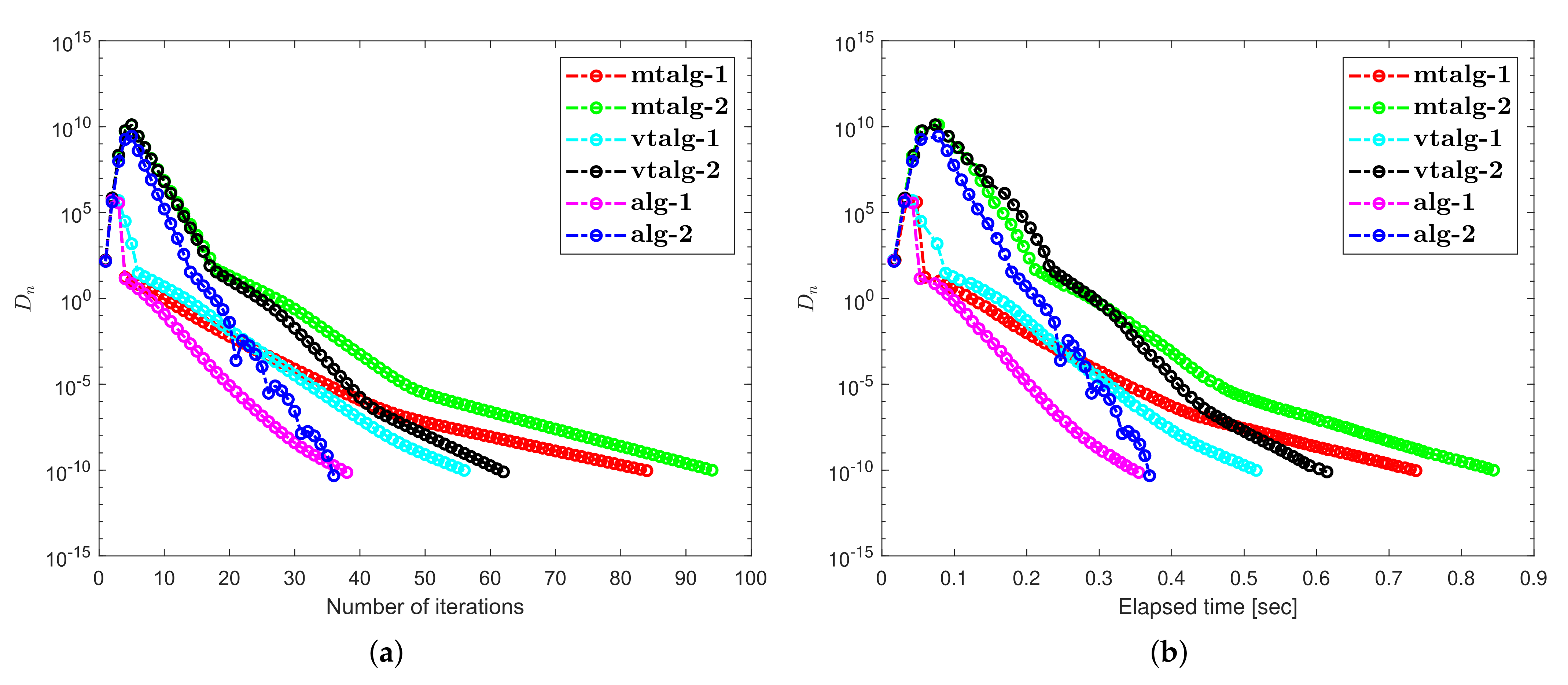
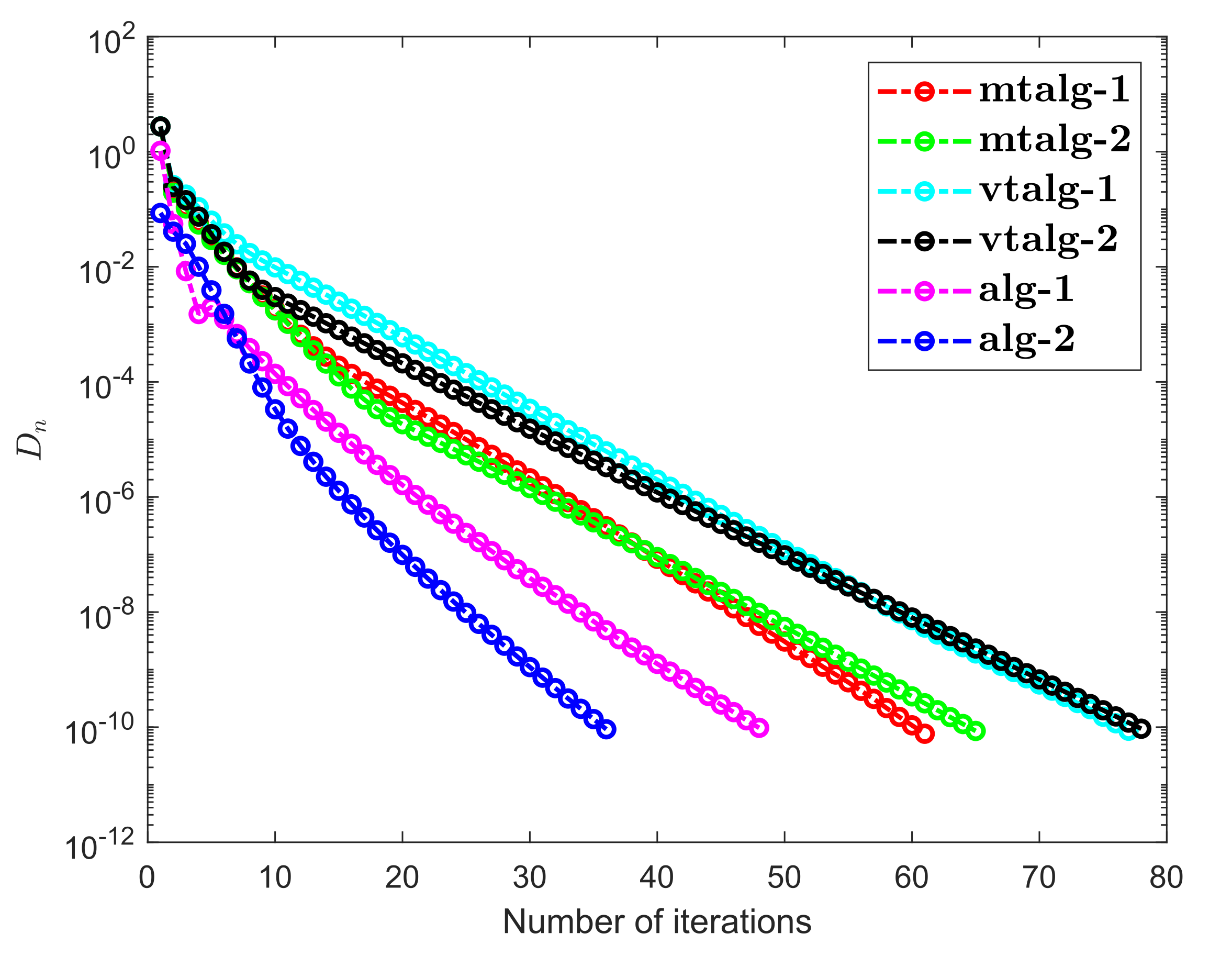
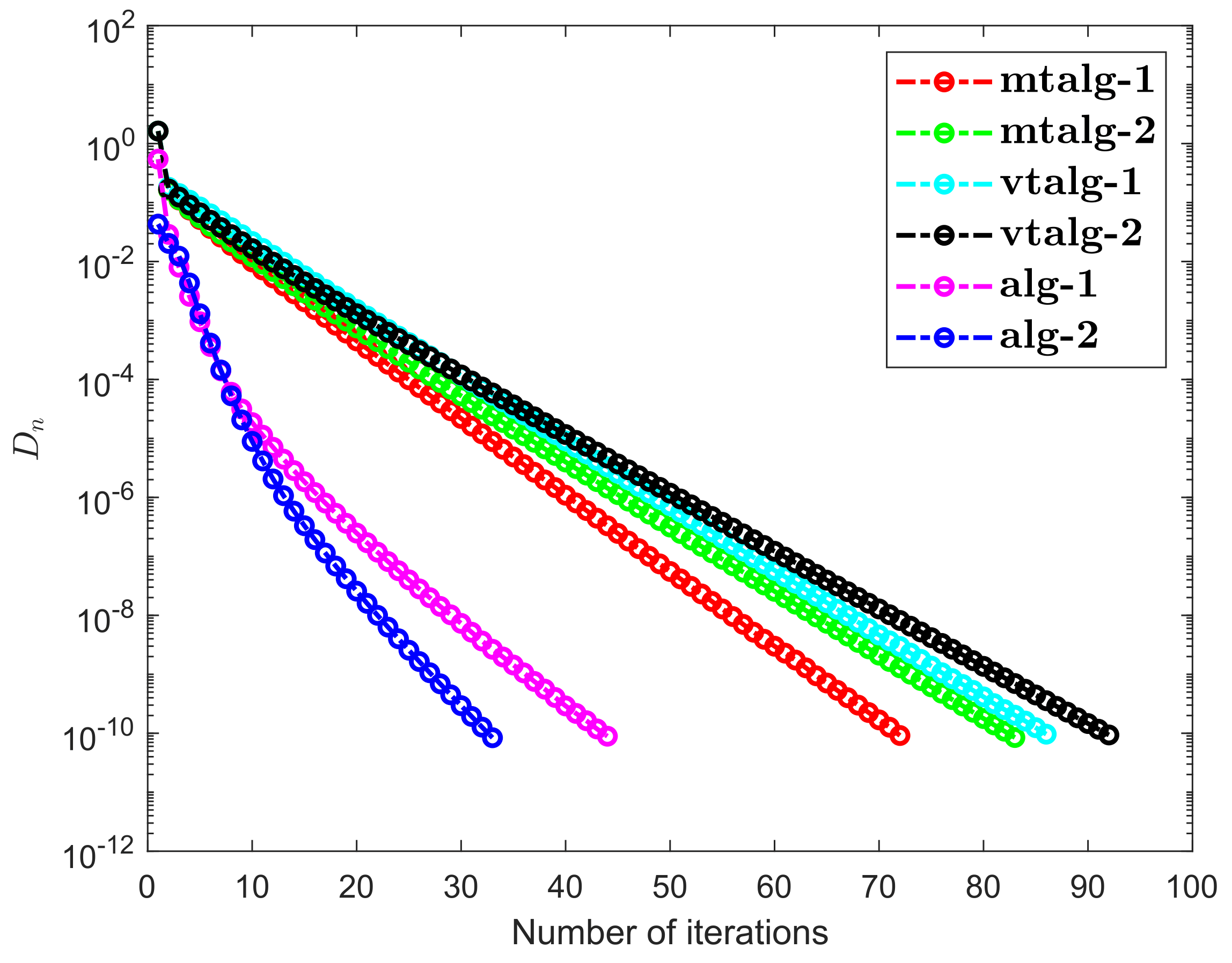
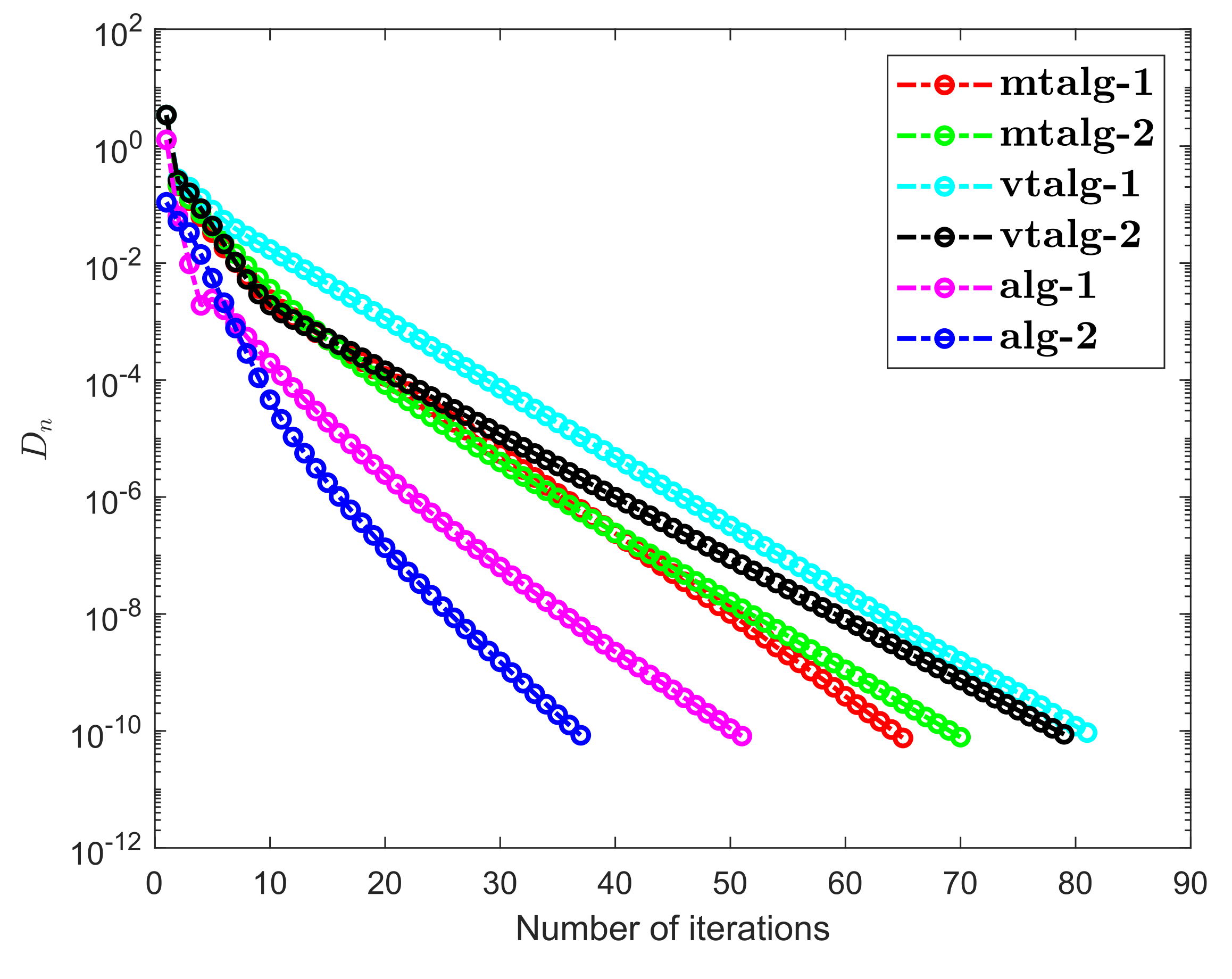
- Examples 1–3 reported results for several algorithms in both finite and infinite-dimensional spaces. It is clear to see that the provided algorithms outperformed in terms of number of iterations and elapsed time in almost all situations. All experiments show that the proposed algorithms perform better the previously existing algorithms.
- (2)
- The appearance of unsuitable variable step size causes a hump in the graph of algorithms in Example 2. It does not really effect the overall performance of the algorithms.
- (3)
- Examples 1–3 reported results for different algorithms for both finite and infinite-dimensional spaces. In most cases, we can see that the algorithm’s performance is determined by the nature of the problem and the tolerance value employed.
- (4)
- For large-dimensional problems, all approaches typically took longer and showed significant variation in execution time. The number of iterations, on the other hand, changes slightly less.
- (5)
- It is also observed that a specific formula for stepsize evaluation enhances the algorithm’s efficiency and the pace of convergence. In other words, rather than the fixed stepsize, the appropriate variable stepsize improves the performance of algorithms.
- (6)
- In Examples 2 and 3, it can also be shown that the initial point choice and the complexity of the operators have an influence on the performance of algorithms in terms of the number of iterations and time of execution in seconds.
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Maingé, P.E. A Hybrid Extragradient-Viscosity Method for Monotone Operators and Fixed Point Problems. SIAM J. Control. Optim. 2008, 47, 1499–1515. [Google Scholar] [CrossRef]
- Maingé, P.E.; Moudafi, A. Coupling viscosity methods with the extragradient algorithm for solving equilibrium problems. J. Nonlinear Convex Anal. 2008, 9, 283–294. [Google Scholar]
- Iiduka, H.; Yamada, I. A subgradient-type method for the equilibrium problem over the fixed point set and its applications. Optimization 2009, 58, 251–261. [Google Scholar] [CrossRef]
- Qin, X.; An, N.T. Smoothing algorithms for computing the projection onto a Minkowski sum of convex sets. Comput. Optim. Appl. 2019, 74, 821–850. [Google Scholar] [CrossRef] [Green Version]
- An, N.T.; Nam, N.M.; Qin, X. Solving k-center problems involving sets based on optimization techniques. J. Glob. Optim. 2019, 76, 189–209. [Google Scholar] [CrossRef]
- Stampacchia, G. Formes bilinéaires coercitives sur les ensembles convexes. Comptes Rendus Hebd. Des Seances Acad. Des Sci. 1964, 258, 4413. [Google Scholar]
- Konnov, I.V. On systems of variational inequalities. Russ. Math. C/C -Izv.-Vyss. Uchebnye Zaved. Mat. 1997, 41, 77–86. [Google Scholar]
- Kassay, G.; Kolumbán, J.; Páles, Z. On Nash stationary points. Publ. Math. 1999, 54, 267–279. [Google Scholar]
- Kassay, G.; Kolumbán, J.; Páles, Z. Factorization of Minty and Stampacchia variational inequality systems. Eur. J. Oper. Res. 2002, 143, 377–389. [Google Scholar] [CrossRef]
- Kinderlehrer, D.; Stampacchia, G. An Introduction to Variational Inequalities and Their Applications; Society for Industrial and Applied Mathematics: Philadelphia, PA, USA, 2000. [Google Scholar] [CrossRef]
- Konnov, I. Equilibrium Models and Variational Inequalities; Elsevier: Amsterdam, The Netherlands, 2007; Volume 210. [Google Scholar]
- Elliott, C.M. Variational and Quasivariational Inequalities Applications to Free—Boundary ProbLems. (Claudio Baiocchi Furthermore, António Capelo). SIAM Rev. 1987, 29, 314–315. [Google Scholar] [CrossRef]
- Nagurney, A. Network Economics: A Variational Inequality Approach; Kluwer Academic Publishers Group: Dordrecht, The Netherlands, 1999. [Google Scholar] [CrossRef]
- Takahashi, W. Introduction to Nonlinear and Convex Analysis; Yokohama Publishers: Yokohama, Japan, 2009. [Google Scholar]
- Korpelevich, G. The extragradient method for finding saddle points and other problems. Matecon 1976, 12, 747–756. [Google Scholar]
- Noor, M.A. Some iterative methods for nonconvex variational inequalities. Comput. Math. Model. 2010, 21, 97–108. [Google Scholar] [CrossRef]
- Censor, Y.; Gibali, A.; Reich, S. The subgradient extragradient method for solving variational inequalities in Hilbert space. J. Optim. Theory Appl. 2010, 148, 318–335. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Censor, Y.; Gibali, A.; Reich, S. Extensions of Korpelevich extragradient method for the variational inequality problem in Euclidean space. Optimization 2012, 61, 1119–1132. [Google Scholar] [CrossRef]
- Tseng, P. A Modified Forward-Backward Splitting Method for Maximal Monotone Mappings. SIAM J. Control. Optim. 2000, 38, 431–446. [Google Scholar] [CrossRef]
- Moudafi, A. Viscosity Approximation Methods for Fixed-Points Problems. J. Math. Anal. Appl. 2000, 241, 46–55. [Google Scholar] [CrossRef] [Green Version]
- Zhang, L.; Fang, C.; Chen, S. An inertial subgradient-type method for solving single-valued variational inequalities and fixed point problems. Numer. Algorithms 2018, 79, 941–956. [Google Scholar] [CrossRef]
- Iusem, A.N.; Svaiter, B.F. A variant of korpelevich’s method for variational inequalities with a new search strategy. Optimization 1997, 42, 309–321. [Google Scholar] [CrossRef]
- Thong, D.V.; Hieu, D.V. Modified subgradient extragradient method for variational inequality problems. Numer. Algorithms 2017, 79, 597–610. [Google Scholar] [CrossRef]
- Thong, D.V.; Hieu, D.V. Weak and strong convergence theorems for variational inequality problems. Numer. Algorithms 2017, 78, 1045–1060. [Google Scholar] [CrossRef]
- Rehman, H.; Kumam, P.; Shutaywi, M.; Alreshidi, N.A.; Kumam, W. Inertial optimization based two-step methods for solving equilibrium problems with applications in variational inequality problems and growth control equilibrium models. Energies 2020, 13, 3292. [Google Scholar] [CrossRef]
- Hammad, H.A.; Rehman, H.; la Sen, M.D. Advanced algorithms and common solutions to variational inequalities. Symmetry 2020, 12, 1198. [Google Scholar] [CrossRef]
- Yordsorn, P.; Kumam, P.; Rehman, H.; Ibrahim, A.H. A weak convergence self-adaptive method for solving pseudomonotone equilibrium problems in a real Hilbert space. Mathematics 2020, 8, 1165. [Google Scholar] [CrossRef]
- Rehman, H.; Gibali, A.; Kumam, P.; Sitthithakerngkiet, K. Two new extragradient methods for solving equilibrium problems. Rev. Real Acad. Cienc. Exactas Fis. Nat. Ser. Mat. 2021, 115. [Google Scholar] [CrossRef]
- Rehman, H.; Kumam, P.; Gibali, A.; Kumam, W. Convergence analysis of a general inertial projection-type method for solving pseudomonotone equilibrium problems with applications. J. Inequalities Appl. 2021, 2021. [Google Scholar] [CrossRef]
- Rehman, H.; Alreshidi, N.A.; Muangchoo, K. A New Modified Subgradient Extragradient Algorithm Extended for Equilibrium Problems with Application in Fixed Point Problems. J. Nonlinear Convex Anal. 2021, 22, 421–439. [Google Scholar]
- Muangchoo, K.; Rehman, H.; Kumam, P. Weak convergence and strong convergence of nonmonotonic explicit iterative methods for solving equilibrium problems. J. Nonlinear Convex Anal. 2021, 22, 663–681. [Google Scholar]
- Rehman, H.; Kumam, P.; Özdemir, M.; Karahan, I. Two generalized non-monotone explicit strongly convergent extragradient methods for solving pseudomonotone equilibrium problems and applications. Math. Comput. Simul. 2021. [Google Scholar] [CrossRef]
- Antipin, A.S. On a method for convex programs using a symmetrical modification of the Lagrange function. Ekon. Mat. Metod. 1976, 12, 1164–1173. [Google Scholar]
- Yamada, I.; Ogura, N. Hybrid Steepest Descent Method for Variational Inequality Problem over the Fixed Point Set of Certain Quasi-nonexpansive Mappings. Numer. Funct. Anal. Optim. 2005, 25, 619–655. [Google Scholar] [CrossRef]
- Tan, B.; Zhou, Z.; Li, S. Viscosity-type inertial extragradient algorithms for solving variational inequality problems and fixed point problems. J. Appl. Math. Comput. 2021. [Google Scholar] [CrossRef]
- Tan, B.; Fan, J.; Qin, X. Inertial extragradient algorithms with non-monotonic step sizes for solving variational inequalities and fixed point problems. Adv. Oper. Theory 2021, 6. [Google Scholar] [CrossRef]
- Mann, W.R. Mean value methods in iteration. Proc. Am. Math. Soc. 1953, 4, 506. [Google Scholar] [CrossRef]
- Zhou, H.; Qin, X. Fixed Points of Nonlinear Operators; De Gruyter: Berlin, Germany, 2020. [Google Scholar]
- Saejung, S.; Yotkaew, P. Approximation of zeros of inverse strongly monotone operators in Banach spaces. Nonlinear Anal. Theory Methods Appl. 2012, 75, 742–750. [Google Scholar] [CrossRef]
- Hicks, T.L.; Kubicek, J.D. On the Mann iteration process in a Hilbert space. J. Math. Anal. Appl. 1977, 59, 498–504. [Google Scholar] [CrossRef] [Green Version]
- Karamardian, S. Complementarity problems over cones with monotone and pseudomonotone maps. J. Optim. Theory Appl. 1976, 18, 445–454. [Google Scholar] [CrossRef]
- Harker, P.T.; Pang, J.S. A damped-Newton method for the linear complementarity problem. Comput. Solut. Nonlinear Syst. Equ. 1990, 26, 265. [Google Scholar]
- Solodov, M.V.; Svaiter, B.F. A New Projection Method for Variational Inequality Problems. SIAM J. Control. Optim. 1999, 37, 765–776. [Google Scholar] [CrossRef]
- Van Hieu, D.; Anh, P.K.; Muu, L.D. Modified hybrid projection methods for finding common solutions to variational inequality problems. Comput. Optim. Appl. 2016, 66, 75–96. [Google Scholar] [CrossRef]
- Dong, Q.L.; Cho, Y.J.; Zhong, L.L.; Rassias, T.M. Inertial projection and contraction algorithms for variational inequalities. J. Glob. Optim. 2017, 70, 687–704. [Google Scholar] [CrossRef]




| Total Number of Iterations | ||||||
|---|---|---|---|---|---|---|
| alg-1 | alg-2 | mtalg-1 | mtalg-2 | vtalg-1 | vtalg-2 | |
| 5 | 36 | 19 | 94 | 78 | 60 | 49 |
| 10 | 46 | 24 | 102 | 80 | 62 | 51 |
| 20 | 42 | 25 | 93 | 85 | 59 | 53 |
| 50 | 38 | 25 | 86 | 87 | 57 | 55 |
| 100 | 37 | 32 | 84 | 88 | 56 | 56 |
| 200 | 38 | 36 | 84 | 94 | 56 | 62 |
| Required CPU Time | ||||||
|---|---|---|---|---|---|---|
| alg-1 | alg-2 | mtalg-1 | mtalg-2 | vtalg-1 | vtalg-2 | |
| 5 | 0.246841 | 0.1317703 | 0.5865135 | 0.4009539 | 0.360533465 | 0.3001653 |
| 10 | 0.284076 | 0.1523123 | 0.5159276 | 0.4722816 | 0.375091336 | 0.3097725 |
| 20 | 0.2602246 | 0.1633652 | 0.4246998 | 0.4630932 | 0.393142367 | 0.3358743 |
| 50 | 0.293302 | 0.1854808 | 0.4320612 | 0.5335381 | 0.331728156 | 0.3663686 |
| 100 | 0.2566573 | 0.2301228 | 0.4752024 | 0.5067862 | 0.358997537 | 0.3936471 |
| 200 | 0.3544296 | 0.3695034 | 0.7371152 | 0.8441844 | 0.516623963 | 0.6142675 |
| Total Number of Iterations | ||||||
|---|---|---|---|---|---|---|
| alg-1 | alg-2 | mtalg-1 | mtalg-2 | vtalg-1 | vtalg-2 | |
| 49 | 35 | 68 | 75 | 82 | 85 | |
| 48 | 36 | 61 | 65 | 77 | 78 | |
| 44 | 33 | 72 | 83 | 86 | 92 | |
| 51 | 37 | 65 | 70 | 81 | 79 | |
| Required CPU Time | ||||||
|---|---|---|---|---|---|---|
| alg-1 | alg-2 | mtalg-1 | mtalg-2 | vtalg-1 | vtalg-2 | |
| 0.2284193 | 0.1631707 | 0.2969821 | 0.3224385 | 0.3469049 | 0.3625844 | |
| 0.2297859 | 0.1757931 | 0.3720656 | 0.3078242 | 0.3847476 | 0.4105755 | |
| 0.1986126 | 0.1512495 | 0.3220028 | 0.3729462 | 0.3787876 | 0.4068135 | |
| 0.2380988 | 0.1703252 | 0.2690971 | 0.3069672 | 0.3448697 | 0.3428332 | |
| Total Number of Iterations | ||||||
|---|---|---|---|---|---|---|
| alg-1 | alg-2 | mtalg-1 | mtalg-2 | vtalg-1 | vtalg-2 | |
| 1 | 44 | 33 | 76 | 70 | 66 | 57 |
| t | 42 | 31 | 89 | 84 | 58 | 48 |
| 45 | 34 | 75 | 64 | 58 | 51 | |
| 47 | 35 | 74 | 94 | 58 | 51 | |
| Required CPU Time | ||||||
|---|---|---|---|---|---|---|
| alg-1 | alg-2 | mtalg-1 | mtalg-2 | vtalg-1 | vtalg-2 | |
| 1 | 0.1310831 | 0.1149104 | 0.2380825 | 0.2171721 | 0.1915358 | 0.178602 |
| t | 0.0583617 | 0.0538350 | 0.1154974 | 0.1059993 | 0.0784157 | 0.0548289 |
| 0.1372786 | 0.1029274 | 0.2692971 | 0.185825 | 0.1745996 | 0.1476468 | |
| 0.1364229 | 0.1253482 | 0.2207376 | 0.2697567 | 0.172504 | 0.1452834 | |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Khunpanuk, C.; Panyanak, B.; Pakkaranang, N. A New Construction and Convergence Analysis of Non-Monotonic Iterative Methods for Solving ρ-Demicontractive Fixed Point Problems and Variational Inequalities Involving Pseudomonotone Mapping. Mathematics 2022, 10, 623. https://doi.org/10.3390/math10040623
Khunpanuk C, Panyanak B, Pakkaranang N. A New Construction and Convergence Analysis of Non-Monotonic Iterative Methods for Solving ρ-Demicontractive Fixed Point Problems and Variational Inequalities Involving Pseudomonotone Mapping. Mathematics. 2022; 10(4):623. https://doi.org/10.3390/math10040623
Chicago/Turabian StyleKhunpanuk, Chainarong, Bancha Panyanak, and Nuttapol Pakkaranang. 2022. "A New Construction and Convergence Analysis of Non-Monotonic Iterative Methods for Solving ρ-Demicontractive Fixed Point Problems and Variational Inequalities Involving Pseudomonotone Mapping" Mathematics 10, no. 4: 623. https://doi.org/10.3390/math10040623
APA StyleKhunpanuk, C., Panyanak, B., & Pakkaranang, N. (2022). A New Construction and Convergence Analysis of Non-Monotonic Iterative Methods for Solving ρ-Demicontractive Fixed Point Problems and Variational Inequalities Involving Pseudomonotone Mapping. Mathematics, 10(4), 623. https://doi.org/10.3390/math10040623







