A Memetic Algorithm with a Novel Repair Heuristic for the Multiple-Choice Multidimensional Knapsack Problem
Abstract
:1. Introduction
2. Related Work
3. Design of a Repair Heuristic Algorithm
3.1. Tendency Function and Repair Heuristic Algorithm
| Algorithm 1 The constructive procedure (CP) for finding a feasible solution. |
|
| Algorithm 2 Tendency parameters and tendency utility function. |
|
| Algorithm 3 The procedure for repairing an infeasible solution with the tendency function: RHTF. |
|
3.2. Genetic Approximation of Tendency Function
| Algorithm 4 The pseudo-code of our genetic approximation of the tendency function: GATF. |
|
- Representation: we represent a solution using a six-integer array since the objective of GATF is to find the appropriate values of six tendency parameters. Array cells correspond to , , , , , and , which are the members of tendency parameters in Algorithm 2.
- Crossover: we used a uniform crossover method [50]. Each member of the tendency parameters is completely independent, and hence, the crossover is performed regardless of gene positions.
- Mutation: Two randomly chosen genes among the six genes are swapped.
- Fitness: we determine the fitness of a chromosome by examining the degree of changing infeasible solutions to feasible ones by applying the RHTF using the tendency parameters, which are the values of the given chromosome. For a chromosome, we set its fitness value to the repair success rate .
4. Memetic Algorithm for the MMKP
| Algorithm 5 The pseudo-code of our memetic algorithm for the MMKP: MAMMKP. |
|
4.1. Local Optimization
4.2. Genetic Framework
- Representation: a solution is represented by a length-n integer array. The i-th gene means the index of the i-th class item.
- Crossover: a simple multi-cut circular crossover is adopted.
- Mutation: t genes are randomly changed. The value of t is limited to five or less.
- Repair: we presented a repair heuristic with a tendency function approximated by GATF in Section 3. We repair infeasible solutions using the proposed repair heuristic.
- Fitness: if a given solution is feasible, its fitness value is obtained by computing the objective value of the MMKP. However, if a feasible solution is not obtained from the repair heuristic, the fitness value is set to , where m is the number of constraints, and indicates the weight sum of the selected items on the k-th resource constraint. Unlike the previous method [49], in the case of a violation, we made the fitness value negative. As this method, strategies to give penalty to infeasible solutions have generally been used to deal with infeasible solutions in GAs [52,53,54]. The method makes the fitness value of an infeasible solution always smaller than the fitness value of a feasible one. According to the proposed fitness function, the greater the number of violated constraints is and the greater the degree of violation is, the smaller the fitness value is. This increases the probability of selecting a feasible solution with a positive fitness value and reduces the probability of selecting an infeasible solution with a negative fitness value. By doing this, we can maintain consistency that the solution with a larger fitness value is always superior to that with a smaller fitness value. This method is also useful for dealing with two different kinds of solutions (feasible solutions and infeasible ones) in a population.
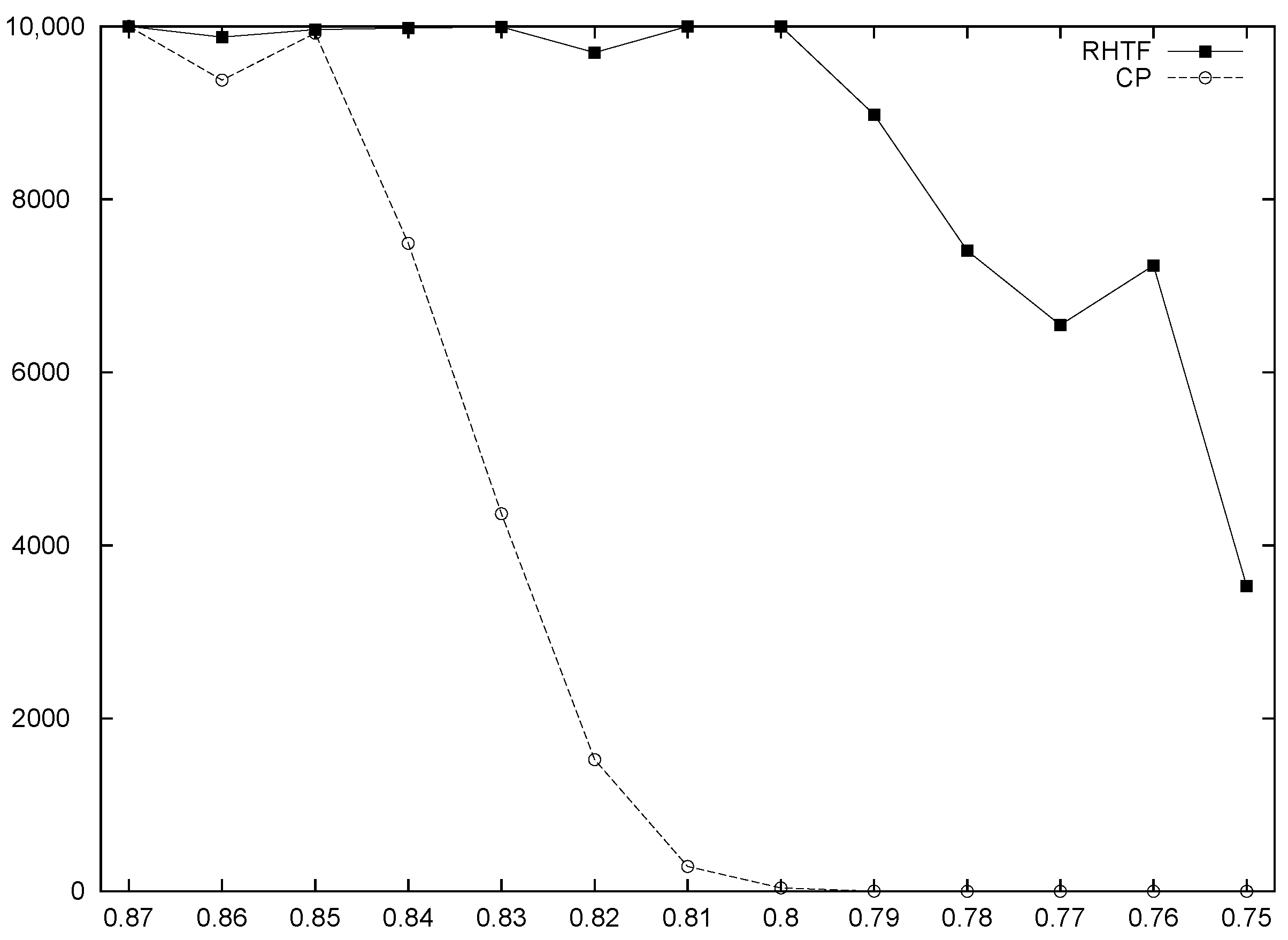
- Replacement: RHTF is most likely to find feasible solutions from infeasible ones even if the density of feasible solutions is very low. However, as shown in Figure 2, the success rate decreases as the density of feasible solutions decreases. When the RHTF fails to repair infeasible solutions, GATF attempts to transform infeasible solutions into feasible ones. Zhou [49] and Htiouech et al. [17] demonstrated that searching both feasible and infeasible solution spaces is necessary for the global optimum. In addition, we do not remove infeasible solutions from the population. Instead of a multi-population, we use the fitness value for a single population that we previously introduced. Therefore, the population is only changed by the fitness values, regardless of the feasibility of the solutions. This is possible because the fitness values of infeasible solutions are always negative. However, if the whole population is filled with feasible solutions, the memetic algorithm may lose the possibility of the performance improvement with the help of infeasible solutions, as we can see in the previous method [49]. To avoid premature convergence, we used a generational GA. The remaining 70% of individuals in the population, except for the top 30%, were replaced with new solutions. By this replacement, the memetic algorithm can avoid falling into local optima.
5. Experiments
5.1. Experimental Settings
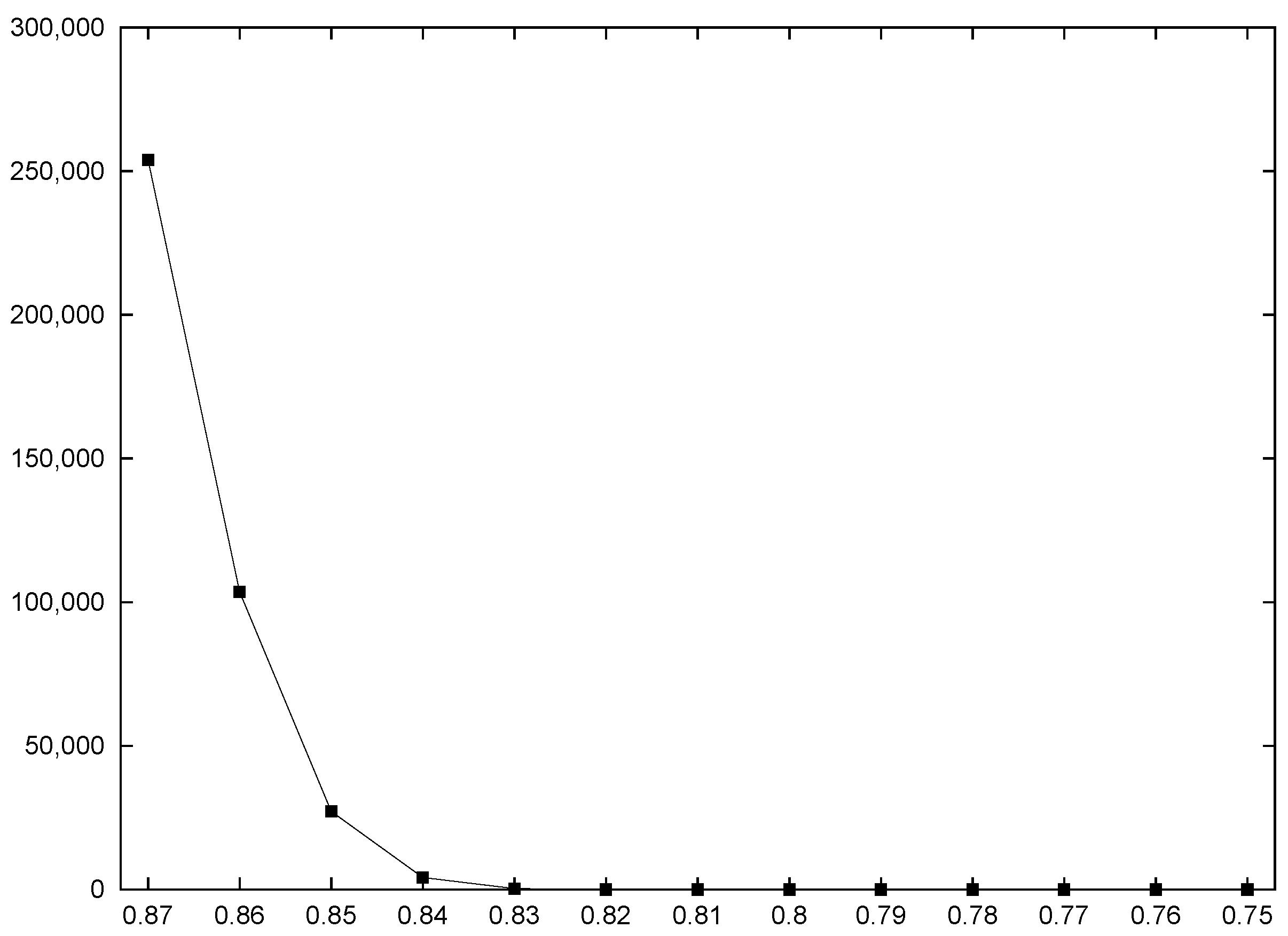
5.2. Performance of the RHTF
5.3. Performance of the MAMMKP
6. Concluding Remarks
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Hifi, M.; Michrafy, M.; Sbihi, A. Heuristic algorithms for the multiple-choice multidimensional knapsack problem. J. Oper. Res. Soc. 2004, 55, 1323–1332. [Google Scholar] [CrossRef]
- Caserta, M.; Voß, S. An exact algorithm for the reliability redundancy allocation problem. Eur. J. Oper. Res. 2015, 244, 110–116. [Google Scholar] [CrossRef]
- Khan, S.; Li, K.F.; Manning, E.; Akbar, M. Solving the knapsack problem for adaptive multimedia systems. Stud. Inform. Univ. 2002, 2, 157–178. [Google Scholar]
- Lee, D.; Siewiorek, D. An Approach for Quality of Service Management. Technical Report. Available online: http://reports-archive.adm.cs.cmu.edu/anon/1998/CMU-CS-98-165R.pdf (accessed on 15 March 2020).
- Shabany, M.; Sousa, E. Joint rate allocation and routing scheme in multihop cellular CDMA networks. In Proceedings of the 9th International Symposium on Computers and Communications, Alexandria, Egypt, 28 June–1 July 2004; Volume 1, pp. 442–447. [Google Scholar]
- Hwang, H.Y.; Lee, H.; Roh, B.; Kim, S. Joint resource allocation, routing and CAC for uplink OFDMA networks with cooperative relaying. Wirel. Netw. 2016, 22, 1493–1503. [Google Scholar] [CrossRef]
- Parra-Hernandez, R.; Dimopoulos, N. A new heuristic for solving the multichoice multidimensional knapsack problem. IEEE Trans. Syst. Man Cybern. Part A Syst. Hum. 2005, 35, 708–717. [Google Scholar] [CrossRef]
- Moser, M.; Jokanovic, D.; Shiratori, N. An algorithm for the multidimensional multiple-choice knapsack problem. IEICE Trans. Fundam. Electron. Commun. Comput. Sci. 1997, 80, 582–589. [Google Scholar]
- Yoon, Y.; Kim, Y.H.; Moon, B.R. A theoretical and empirical investigation on the Lagrangian capacities of the 0-1 multidimensional knapsack problem. Eur. J. Oper. Res. 2012, 218, 366–376. [Google Scholar] [CrossRef]
- Yoon, Y.; Kim, Y.H. A memetic Lagrangian heuristic for the 0-1 multidimensional knapsack problem. Discret. Dyn. Nat. Soc. 2013, 2013, 474852. [Google Scholar] [CrossRef]
- Toyoda, Y. A simplified algorithm for obtaining approximate solutions to zero-one programming problems. Manag. Sci. 1975, 21, 1417–1427. [Google Scholar] [CrossRef]
- Cherfi, N.; Hifi, M. A column generation method for the multiple-choice multi-dimensional knapsack problem. Comput. Optim. Appl. 2010, 46, 51–73. [Google Scholar] [CrossRef]
- Cherfi, N.; Hifi, M. Hybrid algorithms for the multiple-choice multi-dimensional knapsack problem. Int. J. Oper. Res. 2009, 5, 89–109. [Google Scholar] [CrossRef]
- Akbar, M.M.; Sohel Rahman, M.; Kaykobad, M.; Manning, E.; Shoja, G. Solving the multidimensional multiple-choice knapsack problem by constructing convex hulls. Comput. Oper. Res. 2006, 33, 1259–1273. [Google Scholar] [CrossRef] [Green Version]
- Sbihi, A. A best first search exact algorithm for the multiple-choice multidimensional knapsack problem. J. Comb. Optim. 2007, 13, 337–351. [Google Scholar] [CrossRef] [Green Version]
- Crévits, I.; Hanafi, S.; Mansi, R.; Wilbaut, C. Iterative semi-continuous relaxation heuristics for the multiple-choice multidimensional knapsack problem. Comput. Oper. Res. 2012, 39, 32–41. [Google Scholar] [CrossRef]
- Htiouech, S.; Bouamama, S.; Attia, R. Using surrogate information to solve the multidimensional multi-choice knapsack problem. In Proceedings of the IEEE Congress on Evolutionary Computation (CEC), Cancun, Mexico, 20–23 June 2013; pp. 2102–2107. [Google Scholar]
- Xia, Y.; Gao, C.; Li, J. A stochastic local search heuristic for the multidimensional multiple-choice knapsack problem. In Proceedings of the 10th International Conference on Bio-Inspired Computing—Theories and Applications (BIC-TA), Hefei, China, 25–28 September 2015; Communications in Computer and Information Science Book Series (CCIS). Volume 562, pp. 513–522. [Google Scholar]
- Gao, C.; Lu, G.; Yao, X.; Li, J. An iterative pseudo-gap enumeration approach for the multidimensional multiple-choice knapsack problem. Eur. J. Oper. Res. 2017, 260, 1–11. [Google Scholar] [CrossRef]
- Zennaki, M. A new hybrid algorithm for the multiple-choice multi-dimensional knapsack problem. WSEAS Trans. Inf. Sci. Appl. 2013, 10, 219–229. [Google Scholar]
- Ghassemi-Tari, F.; Hendizadeh, H.; Hogg, G.L. Exact solution algorithms for multi-dimensional multiple-choice knapsack problems. Curr. J. Appl. Sci. Technol. 2018, 26, 1–21. [Google Scholar] [CrossRef]
- Hifi, M.; Wu, L. An equivalent model for exactly solving the multiple-choice multidimensional knapsack problem. Int. J. Comb. Optim. Probl. Inform. 2012, 3, 43–58. [Google Scholar]
- Ren, Z.; Feng, Z.; Zhang, A. Fusing ant colony optimization with Lagrangian relaxation for the multiple-choice multidimensional knapsack problem. Inf. Sci. 2012, 182, 15–29. [Google Scholar] [CrossRef]
- Hifi, M.; Wu, L. Lagrangian heuristic-based neighbourhood search for the multiple-choice multi-dimensional knapsack problem. Eng. Optim. 2015, 47, 1619–1636. [Google Scholar] [CrossRef]
- Mansi, R.; Alves, C.; de Carvalho, J.M.V.; Hanafi, S. A hybrid heuristic for the multiple choice multidimensional knapsack problem. Eng. Optim. 2013, 45, 983–1004. [Google Scholar] [CrossRef]
- Chen, Y.; Hao, J.K. A “reduce and solve” approach for the multiple-choice multidimensional knapsack problem. Eur. J. Oper. Res. 2014, 239, 313–322. [Google Scholar] [CrossRef] [Green Version]
- Voß, S.; Lalla-Ruiz, E. A set partitioning reformulation for the multiple-choice multidimensional knapsack problem. Eng. Optim. 2016, 48, 831–850. [Google Scholar] [CrossRef]
- Caserta, M.; Voß, S. The robust multiple-choice multidimensional knapsack problem. Omega 2019, 86, 16–27. [Google Scholar] [CrossRef]
- Shojaei, H.; Basten, T.; Geilen, M.; Davoodi, A. A fast and scalable multidimensional multiple-choice knapsack heuristic. ACM Trans. Des. Autom. Electron. Syst. 2013, 18, 51. [Google Scholar] [CrossRef]
- Ghasemi, T.; Razzazi, M. Development of core to solve the multidimensional multiple-choice knapsack problem. Comput. Ind. Eng. 2011, 60, 349–360. [Google Scholar] [CrossRef]
- Mansini, R.; Zanotti, R. A core-based exact algorithm for the multidimensional multiple choice knapsack problem. INFORMS J. Comput. 2020, 32, 1061–1079. [Google Scholar] [CrossRef]
- Lamanna, L.; Mansini, R.; Zanotti, R. A two-phase kernel search variant for the multidimensional multiple-choice knapsack problem. Eur. J. Oper. Res. 2022, 297, 53–65. [Google Scholar] [CrossRef]
- Syarif, A.; Anggraini, D.; Muludi, K.; Wamiliana, W.; Gen, M. Comparing various genetic algorithm approaches for multiple-choice multi-dimensional knapsack problem (mm-KP). Int. J. Intell. Eng. Syst. 2020, 13, 455–462. [Google Scholar] [CrossRef]
- Rasmy, M.H.; El-Beltagy, M.A.; Tharwat, A.A.; Heikal, A.F. A comparative study on the performance of genetic algorithm, artificial immune system and hybrid intelligent approach to multiple-choice multidimensional knapsack problem. In Proceedings of the 8th International Conference on Informatics and Systems (INFOS), Giza, Egypt, 14–16 May 2012; pp. 20–26. [Google Scholar]
- Zyma, K.; Lu, Y.; Vasko, F.J. Teacher training enhances the teaching-learning-based optimisation metaheuristic when used to solve multiple-choice multidimensional knapsack problems. Int. J. Metaheuristics 2015, 4, 268–293. [Google Scholar] [CrossRef]
- Vasko, F.J.; Lu, Y.; Zyma, K. An empirical study of population-based metaheuristics for the multiple-choice multidimensional knapsack problem. Int. J. Metaheuristics 2016, 5, 193–225. [Google Scholar] [CrossRef]
- Mkaouar, A.; Htiouech, S.; Chabchoub, H. Solving the multiple choice multidimensional knapsack problem with ABC algorithm. In Proceedings of the IEEE Congress on Evolutionary Computation (CEC), Glasgow, UK, 19–24 July 2020; pp. 1–6. [Google Scholar]
- Yang, T.; Zhang, L.; Hong, Z. Distributed estimation algorithm for multi-dimensional multi-choice knapsack problem. J. Syst. Simul. 2017, 29, 3123. [Google Scholar] [CrossRef]
- Shah, S. Simulated Annealing Algorithm for the Multiple Choice Multidimensional Knapsack Problem. OSF Prepr. 2021. [Google Scholar] [CrossRef]
- Hiremath, C.S.; Hill, R.R. First-level tabu search approach for solving the multiple-choice multidimensional knapsack problem. Int. J. Metaheuristics 2013, 2, 174–199. [Google Scholar] [CrossRef]
- Zhang, X.; Luo, W. Evolutionary repair for evolutionary design of combinational logic circuits. In Proceedings of the IEEE Congress on Evolutionary Computation (CEC), Brisbane, Australia, 10–15 June 2012; pp. 1–8. [Google Scholar]
- Xu, P.; Luo, W.; Lin, X.; Qiao, Y. Evolutionary continuous constrained optimization using random direction repair. Inf. Sci. 2021, 566, 80–102. [Google Scholar] [CrossRef]
- Samanipour, F.; Jelovica, J. Adaptive repair method for constraint handling in multi-objective genetic algorithm based on relationship between constraints and variables. Appl. Soft Comput. 2020, 90, 106143. [Google Scholar] [CrossRef]
- Guo, M.; Xin, B.; Chen, J.; Wang, Y. Multi-agent coalition formation by an efficient genetic algorithm with heuristic initialization and repair strategy. Swarm Evol. Comput. 2020, 55, 100686. [Google Scholar] [CrossRef]
- Bidabadi, N. Using a repair genetic algorithm for solving constrained nonlinear optimization problems. J. Inf. Optim. Sci. 2018, 39, 1647–1663. [Google Scholar] [CrossRef]
- Yoon, Y.; Kim, Y.H. Maximizing the coverage of sensor deployments using a memetic algorithm and fast coverage estimation. IEEE Trans. Cybern. 2021. [Google Scholar] [CrossRef]
- Kim, Y.H.; Yoon, Y.; Geem, Z.W. A comparison study of harmony search and genetic algorithm for the max-cut problem. Swarm Evol. Comput. 2019, 44, 130–135. [Google Scholar] [CrossRef]
- Liu, B. Evolutionary Algorithms for the Multiple-Choice Multidimensional 0-1 Knapsack Problem. Undergraduate Thesis, School of Computer Science and Technology, University of Science and Technology of China, Hefei, China, 2008. (In Chinese). [Google Scholar]
- Zhou, Q.; Luo, W. A novel multi-population genetic algorithm for multiple-choice multidimensional knapsack problems. In Proceedings of the International Symposium on Intelligence Computation and Applications, Wuhan, China, 22–24 October 2010; pp. 148–157. [Google Scholar]
- Syswerda, G. Uniform Crossover in Genetic Algorithms. In Proceedings of the 3rd International Conference on Genetic Algorithms, Washington, DC, USA, 4–7 June 1989; pp. 2–9. [Google Scholar]
- Mahi, M.; Baykan, Ö.K.; Kodaz, H. A new hybrid method based on particle swarm optimization, ant colony optimization and 3-Opt algorithms for traveling salesman problem. Appl. Soft Comput. 2015, 30, 484–490. [Google Scholar] [CrossRef]
- Deb, K.; Agrawal, S. A Niched-Penalty Approach for Constraint Handling in Genetic Algorithms. In Proceedings of the International Conference in Artificial Neural Nets and Genetic Algorithms, Portorož, Slovenia, 1999; Springer: Berlin/Heidelberg, Germany, 1999; pp. 235–243. [Google Scholar]
- Yeniay, O. Penalty function methods for constrained optimization with genetic algorithms. Math. Comput. Appl. 2005, 10, 45–56. [Google Scholar] [CrossRef] [Green Version]
- Lin, C.H. A rough penalty genetic algorithm for constrained optimization. Inf. Sci. 2013, 241, 119–137. [Google Scholar] [CrossRef]
- Beasley, J.E. OR-Library: Distributing test problems by electronic mail. J. Oper. Res. Soc. 1990, 41, 1069–1072. [Google Scholar] [CrossRef]
- Yoon, Y.; Kim, Y.H. Gene-similarity normalization in a genetic algorithm for the maximum k-coverage problem. Mathematics 2020, 8, 513. [Google Scholar] [CrossRef] [Green Version]
- Lee, J.; Kim, Y.H. Epistasis-based basis estimation method for simplifying the problem space of an evolutionary search in binary representation. Complexity 2019, 2019, 2095167. [Google Scholar] [CrossRef]
- Kim, Y.H.; Yoon, Y.; Kim, Y.H. Towards a better basis search through a surrogate model-based epistasis minimization for pseudo-Boolean optimization. Mathematics 2020, 8, 1287. [Google Scholar] [CrossRef]
| f | Test Set | HMMKP [7] | LGA [48] | MPGA [49] | MAMMKP | |||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Max | Ave | Min | Max | Ave | Min | Max | Ave | Min | CPU * | |||
| 0.90 | 0 | 17,510 | 18,627 | 18,535.8 | 18,524 | 18,627 | 18,549.1 | 18,524 | 18,627 | 18,627.0 | 18,627 | 8 |
| 1 | 17,948 | 18,081 | 18,077.0 | 17,981 | 18,081 | 18081.0 | 18,081 | 18,081 | 18,081.0 | 18,081 | ||
| 2 | 17,049 | 17,688 | 17,688.0 | 17,688 | 17,688 | 17,688.0 | 17,688 | 17,688 | 17,688.0 | 17,688 | ||
| 3 | 17,833 | 17,935 | 17,935.0 | 17,935 | 17,935 | 17,935.0 | 17,935 | 17,935 | 17,935.0 | 17,935 | ||
| 4 | 17,315 | 18,550 | 18,532.8 | 18,483 | 18,550 | 18,548.7 | 18,483 | 18,550 | 18,550.0 | 18,550 | ||
| 5 | 18,318 | 18,707 | 18,639.3 | 18,608 | 18,707 | 18,705.1 | 18,614 | 18,707 | 18,707.0 | 18,707 | ||
| 6 | 18,045 | 18,141 | 18,135.8 | 18,107 | 18,141 | 18,140.6 | 18,119 | 18,141 | 18,141.0 | 18,141 | ||
| 7 | 17,301 | 18,122 | 18,122.0 | 18,122 | 18,122 | 18,122.0 | 18,122 | 18,122 | 18,122.0 | 18,122 | ||
| 8 | 17,563 | 18,881 | 18,821.9 | 18,799 | 18,881 | 18,869.1 | 18,803 | 18,881 | 18,881.0 | 18,881 | ||
| 9 | 16,691 | 17,286 | 17,263.7 | 17,184 | 17,286 | 17,239.1 | 17,184 | 17,286 | 17,286.0 | 17,286 | ||
| 0.84 | 0 | 15,617 | 17,447 | 17,396.3 | 17,335 | 17,482 | 17,443.1 | 17,351 | 17,482 | 17,478.5 | 17,447 | 27 |
| 1 | 15,951 | 17,025 | 17,008.8 | 16,855 | 17,120 | 17,026.9 | 17,025 | 17,120 | 17,063.0 | 17,025 | ||
| 2 | 14,080 | 16,655 | 16,473.4 | 16,292 | 16,655 | 16,607.8 | 16,421 | 16,655 | 16,655.0 | 16,655 | ||
| 3 | 14,876 | 16,986 | 16913.9 | 16,805 | 17,041 | 16,991.5 | 16,846 | 17,041 | 17,041.0 | 17,041 | ||
| 4 | 15,595 | 17,531 | 17,531.0 | 17,531 | 17,531 | 17,531.0 | 17,531 | 17,531 | 17,531.0 | 17,531 | ||
| 5 | 15,791 | 17,742 | 17,664.0 | 17,546 | 17,742 | 17,671.6 | 17,602 | 17,742 | 17,723.8 | 17,716 | ||
| 6 | 15,484 | 17,408 | 17,323.0 | 17,250 | 17,425 | 17,394.9 | 17,385 | 17,425 | 17,425.0 | 17,425 | ||
| 7 | 14,963 | 16,837 | 16782.5 | 16,692 | 16,985 | 16,855.9 | 16,774 | 16,985 | 16,985.0 | 16,985 | ||
| 8 | 16,160 | 17,763 | 17,751.9 | 17,625 | 17,763 | 17,759.5 | 17,616 | 17,763 | 17,763.0 | 17,763 | ||
| 9 | 13,098 | 16,325 | 16,235.1 | 16,131 | 16,325 | 16,323.6 | 16,289 | 16,325 | 16,316.4 | 16,254 | ||
| 0.80 | 0 | N/A | 15,597 | 15,333.5 | 14,946 | 15,799 | 15,559.6 | 15,404 | 15,799 | 15,680.0 | 15,680 | 61 |
| 1 | 15,816 | 15,599.4 | 15,488 | 15,783 | 15,724.6 | 15,665 | 15,816 | 15,775.2 | 15,735 | |||
| 2 | 15,469 | 14,954.5 | 14,698 | 15,503 | 15,410.3 | 14,951 | 15,503 | 15,496.2 | 15,469 | |||
| 3 | 15,869 | 15,722.6 | 15,381 | 15,869 | 15,822.3 | 15,709 | 16,015 | 16,015.0 | 16,015 | |||
| 4 | 16,300 | 16,211.9 | 15,694 | 16,300 | 16,300.0 | 16,300 | 16,300 | 16,300.0 | 16,300 | |||
| 5 | 16,742 | 16,535.4 | 16,425 | 16,742 | 16,742.0 | 16,742 | 16,742 | 16,742.0 | 16,742 | |||
| 6 | 16,045 | 15,889.7 | 15,700 | 16,401 | 16,088.8 | 15,966 | 16,401 | 16,151.8 | 16,045 | |||
| 7 | 15,029 | 14,883.5 | 14,701 | 15,290 | 15,015.0 | 14,836 | 15,290 | 15,169.2 | 15,029 | |||
| 8 | 16,564 | 16,511.0 | 16,401 | 16,564 | 16,559.9 | 16,541 | 16,564 | 16,564.0 | 16,564 | |||
| 9 | 14,863 | 14,732.8 | 14,567 | 15,033 | 14,862.1 | 14,772 | 15,033 | 14,994.1 | 14,863 | |||
| f | Test Set | HMMKP [7] | LGA [48] | MPGA [49] | MAMMKP | |||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Max | Ave | Min | Max | Ave | Min | Max | Ave | Min | CPU * | |||
| 0.90 | 0 | 45,493 | 45,982 | 45,981.0 | 45,931 | 45,982 | 45,982.0 | 45,982 | 45,982 | 45,982.0 | 45,982 | 27 |
| 1 | 47,130 | 47,291 | 47,278.4 | 47,234 | 47,291 | 47,291.0 | 47,291 | 47,291 | 47,291.0 | 47,291 | ||
| 2 | 45,390 | 45,673 | 45,643.0 | 45,596 | 45,673 | 45,658.6 | 45,616 | 45,673 | 45,673.0 | 45,673 | ||
| 3 | 45,810 | 45,806 | 45,804.2 | 45,804 | 45,810 | 45,808.0 | 45,804 | 45,810 | 45,810.0 | 45,810 | ||
| 4 | 45,270 | 45,361 | 45,334.3 | 45,295 | 45,361 | 45,358.8 | 45,317 | 45,390 | 45,390.0 | 45,390 | ||
| 5 | 46,611 | 46,611 | 46,611.0 | 46,611 | 46,611 | 46,611.0 | 46,611 | 46,611 | 46,611.0 | 46,611 | ||
| 6 | 46,064 | 46,375 | 46,375.0 | 46,375 | 46,375 | 46,375.0 | 46,375 | 46,375 | 46,375.0 | 46,375 | ||
| 7 | 45,450 | 46,491 | 45,472.2 | 45,459 | 45,491 | 45,486.1 | 45,459 | 45,491 | 45,491.0 | 45,491 | ||
| 8 | 47,156 | 47,159 | 47,159.0 | 47,159 | 47,159 | 47,159.0 | 47,159 | 47,159 | 47,159.0 | 47,159 | ||
| 9 | 45,859 | 46,149 | 46,148.6 | 46,139 | 46,149 | 46,148.8 | 46,139 | 46,149 | 46,149.0 | 46,149 | ||
| 0.80 | 0 | 38,523 | 43,230 | 42,980.0 | 42,706 | 43,487 | 43,209.9 | 42,872 | 43,530 | 43,460.2 | 43,394 | 356 |
| 1 | 41,185 | 44,696 | 44,459.9 | 44,261 | 44,843 | 44,629.9 | 44,450 | 44,904 | 44,838.6 | 44,779 | ||
| 2 | 41,259 | 43,237 | 42,938.4 | 42,666 | 43,365 | 43,108.3 | 42,806 | 43,388 | 43,365.1 | 43,290 | ||
| 3 | 40,066 | 42,825 | 42,545.9 | 42,343 | 43,011 | 42,778.7 | 42,513 | 43,114 | 43,001.6 | 42,926 | ||
| 4 | 38,262 | 43,124 | 42,898.3 | 42,688 | 43,308 | 43,040.2 | 42,726 | 43,368 | 43,368.0 | 43,368 | ||
| 5 | 39,670 | 43,277 | 42,949.0 | 42,600 | 43,486 | 43,258.2 | 42,993 | 43,510 | 43,462.5 | 43,298 | ||
| 6 | 38,547 | 43,675 | 43,415.6 | 43,088 | 43,799 | 43,574.6 | 43,330 | 43,823 | 43,798.9 | 43,750 | ||
| 7 | 39,445 | 42,218 | 41,987.7 | 41,603 | 42,520 | 42,225.2 | 41,957 | 42,529 | 42,458.5 | 42,321 | ||
| 8 | 40,954 | 44,485 | 44,173.5 | 43,955 | 44,713 | 44,446.4 | 44,006 | 44,714 | 44,644.0 | 44,603 | ||
| 9 | 39,834 | 43,426 | 43,132.1 | 42,693 | 43,582 | 43,380.2 | 43,062 | 43,618 | 43,535.7 | 43,489 | ||
| 0.75 | 0 | N/A | 38,149 | 37,576.9 | 36,895 | 38,933 | 38,391.6 | 37,519 | 39,171 | 39,160.8 | 38,967 | 1251 |
| 1 | 39,720 | 38,732.8 | 37,572 | 40,105 | 39,704.1 | 38,946 | 40,334 | 40,197.1 | 39,960 | |||
| 2 | 39,000 | 38,208.3 | 37,687 | 39,147 | 38,798.0 | 38,392 | 39,271 | 39,207.4 | 39,204 | |||
| 3 | 38,435 | 37,873.5 | 37,349 | 38,826 | 38,442.9 | 38,013 | 38,905 | 38,754.2 | 38,573 | |||
| 4 | 38,508 | 37,850.3 | 37,059 | 38,508 | 38,728.0 | 38,201 | 39,438 | 39,205.6 | 39,019 | |||
| 5 | 37,444 | 36,264.8 | 35,156 | 37,829 | 37,003.0 | 35,777 | 38,090 | 37,683.9 | 37,254 | |||
| 6 | 37,536 | 36,587.9 | 35,356 | 38,475 | 37,592.2 | 36,747 | 38,706 | 38,339.8 | 38,016 | |||
| 7 | 37,833 | 37,464.8 | 37,054 | 38,322 | 37,925.2 | 37,632 | 38,324 | 38,184.3 | 38,096 | |||
| 8 | 38,910 | 38,009.4 | 36,874 | 39,647 | 38,911.9 | 38,240 | 39,695 | 39,287.4 | 39,014 | |||
| 9 | 36,936 | 36,112.4 | 35,363 | 37,380 | 36,745.5 | 35,689 | 37,632 | 37,215.5 | 36,966 | |||
| f | Test Set | HMMKP [7] | LGA [48] | MPGA [49] | MAMMKP | |||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Max | Ave | Min | Max | Ave | Min | Max | Ave | Min | CPU * | |||
| 0.90 | 0 | 92,021 | 92,025 | 92,025.0 | 92,025 | 92,025 | 92,025.0 | 92,025 | 92,031 | 92,031.0 | 92,031 | 409 |
| 1 | 92,371 | 92,371 | 92,371.0 | 92,371 | 92,371 | 92,371.0 | 92,371 | 92,371 | 92,371.0 | 92,371 | ||
| 2 | 93,396 | 93,396 | 93,391.9 | 93,384 | 93,396 | 93,395.8 | 93,387 | 93,396 | 93,396.0 | 93,396 | ||
| 3 | 91,815 | 91,815 | 91807.4 | 91,798 | 91,816 | 91,813.3 | 91,800 | 91,816 | 91,816.0 | 91,816 | ||
| 4 | 93,317 | 93,317 | 93,317.0 | 93,317 | 93,317 | 93,317.0 | 93,317 | 93,317 | 93,317.0 | 93,317 | ||
| 5 | 91,547 | 91,551 | 91,550.4 | 91,547 | 91,551 | 91,550.4 | 91,549 | 91,553 | 91,553.0 | 91,553 | ||
| 6 | 91,480 | 91,480 | 91,480.0 | 91,480 | 91,480 | 91,480.0 | 91,480 | 91,480 | 91,480.0 | 91,480 | ||
| 7 | 91,672 | 91,681 | 91,657.0 | 91,645 | 91,681 | 91,662.8 | 91,646 | 91,681 | 91,681.0 | 91,681 | ||
| 8 | 93,149 | 93,149 | 93,149.0 | 93,149 | 93,149 | 93,149.0 | 93,149 | 93,149 | 93,149.0 | 93,149 | ||
| 9 | 93,528 | 93,531 | 93,530.0 | 93,507 | 93,531 | 93,531.0 | 93,531 | 93,531 | 93,531.0 | 93,531 | ||
| 0.75 | 0 | 74,927 | 82,742 | 81,578.7 | 80,681 | 83,268 | 82,676.5 | 81,838 | 83,540 | 83,404.4 | 83,261 | 1004 |
| 1 | 73,570 | 80,125 | 78,947.1 | 77,715 | 81,222 | 80,528.5 | 79,791 | 81,646 | 81,263.0 | 81,022 | ||
| 2 | 74,739 | 81,493 | 80,523.3 | 79,458 | 82,815 | 81,928.0 | 80,756 | 83,149 | 82,961.0 | 82,796 | ||
| 3 | 69,813 | 80,288 | 79,201.7 | 77,916 | 81,672 | 80,910.2 | 80,141 | 81,927 | 81,751.4 | 81,571 | ||
| 4 | 74,323 | 82,549 | 81,187.4 | 80,028 | 83,572 | 82,779.4 | 81,719 | 84,121 | 83,703.6 | 83,423 | ||
| 5 | 74,303 | 81,634 | 80,940.3 | 79,892 | 82,815 | 82,049.2 | 81,237 | 83,045 | 82,761.2 | 82,539 | ||
| 6 | 72,018 | 78,658 | 77,265.0 | 75,917 | 79,760 | 78,902.2 | 77,990 | 80,037 | 79,658.3 | 79,372 | ||
| 7 | 73,777 | 79,235 | 78,178.4 | 77,115 | 80,493 | 79,865.2 | 79,055 | 81,052 | 80,700.4 | 80,480 | ||
| 8 | 74,376 | 80,717 | 79,827.0 | 78,840 | 81,970 | 81,262.5 | 80,557 | 82,326 | 82,111.3 | 81,899 | ||
| 9 | 73,496 | 81,877 | 80,893.4 | 79,514 | 83,236 | 82,535.4 | 81,536 | 83,676 | 83,458.8 | 83,154 | ||
| 0.73 | 0 | N/A | 77,443 | 75,357.0 | 73,681 | 78,584 | 77,801.9 | 76,725 | 79,008 | 78,453.0 | 76,241 | 1078 |
| 1 | 73,197 | 71,614.3 | 70,363 | 74,877 | 73,897.2 | 72,803 | 74,968 | 74,156.5 | 73,926 | |||
| 2 | 75,731 | 36,528.3 | 0 | 76,904 | 75,552.8 | 73,675 | 77,082 | 76,109.5 | 72,681 | |||
| 3 | 73,322 | 71,832.4 | 70,024 | 75,335 | 74,259.5 | 72,440 | 75,590 | 75,184.6 | 74,469 | |||
| 4 | 76,382 | 75,142.7 | 74,055 | 78,389 | 77,104.6 | 75,914 | 78,567 | 78,235.8 | 77,888 | |||
| 5 | 76,117 | 74,812.3 | 72,618 | 78,314 | 77,110.2 | 75,709 | 78,516 | 77,980.7 | 77,536 | |||
| 6 | 71,820 | 67,155.3 | 0 | 73,175 | 71,956.2 | 69,992 | 73,523 | 72,753.3 | 69,997 | |||
| 7 | 72,643 | 71,172.7 | 68,969 | 74,434 | 73,268.5 | 71,354 | 74,463 | 73,857.8 | 72,284 | |||
| 8 | 75,431 | 73,764.9 | 72,038 | 76,600 | 75,811.7 | 73,799 | 76,913 | 76,607.3 | 76,337 | |||
| 9 | 74,605 | 59,521.0 | 0 | 77,046 | 75,486.8 | 73,698 | 76,793 | 76,188.0 | 75,583 | |||
| 0.72 | 0 | N/A | N/A | N/A | 73,280 | 72,989.0 | 72,680 | 1094 | ||||
| 1 | 70,017 | 69,841.0 | 69,617 | |||||||||
| 2 | 71,774 | 71,238.0 | 70,434 | |||||||||
| 3 | 69,823 | 69,484.0 | 68,937 | |||||||||
| 4 | 74,896 | 74,682.6 | 74,511 | |||||||||
| 5 | 74,536 | 74,216.2 | 74,040 | |||||||||
| 6 | 68,900 | 68,509.4 | 68,143 | |||||||||
| 7 | 68,738 | 68,467.5 | 68,212 | |||||||||
| 8 | 73,458 | 73,208.2 | 73,016 | |||||||||
| 9 | 72,020 | 70,799.9 | 70,110 | |||||||||
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yang, J.; Kim, Y.-H.; Yoon, Y. A Memetic Algorithm with a Novel Repair Heuristic for the Multiple-Choice Multidimensional Knapsack Problem. Mathematics 2022, 10, 602. https://doi.org/10.3390/math10040602
Yang J, Kim Y-H, Yoon Y. A Memetic Algorithm with a Novel Repair Heuristic for the Multiple-Choice Multidimensional Knapsack Problem. Mathematics. 2022; 10(4):602. https://doi.org/10.3390/math10040602
Chicago/Turabian StyleYang, Jaeyoung, Yong-Hyuk Kim, and Yourim Yoon. 2022. "A Memetic Algorithm with a Novel Repair Heuristic for the Multiple-Choice Multidimensional Knapsack Problem" Mathematics 10, no. 4: 602. https://doi.org/10.3390/math10040602
APA StyleYang, J., Kim, Y.-H., & Yoon, Y. (2022). A Memetic Algorithm with a Novel Repair Heuristic for the Multiple-Choice Multidimensional Knapsack Problem. Mathematics, 10(4), 602. https://doi.org/10.3390/math10040602







