Abstract
Reversible Data Hiding (RDH) should be secured as per requirements to protect content in open environments such as the cloud and internet. Integrity and undetectability of steganographic images are amongst the main concerns in any RDH scheme. As steganographic encryption using linear prediction over bit-planes is challenging, so the security and embedding capacity of the existing RDH techniques could not be adequate. Therefore, a new steganographic technique is proposed which provides better security, higher embedding capacity and visual quality to the RDH scheme. In this technique, the cover image is divided into n-bit planes (nBPs) and linear prediction is applied to it. Next, the histogram of the residual nBPs image is taken, and secret data bits are encrypted using the RC4 cryptographic algorithm. To embed the encrypted secret data bits, the histogram shifting process is applied. This is achieved by using peak and zero pairs of residual nBPs images. This scheme provides security to the cover image and hidden data. The proposed RDH scheme is capable of extracting the embedded secret data accurately and recovering the original cover or residual nBPs image.
Keywords:
RDH (Reversible Data Hiding); LSB (least significant bit); histogram shifting; RC4 encryption; bpp (bits per pixel); nBPs (n bit-planes); PSNR (peak to noise ratio); chi-square attack; LPC (linear predictive coding) MSC:
37M99
1. Introduction
Encryption is a significant technique to secure data. Steganography and cryptography are two widely used techniques used to secure data. The steganographic technique is used to conceal the confidential information within data, whereas cryptography obfuscates the secret data to make it unreadable. The basic aim of the steganographic technique is to protect the copyrights, authorization, and ownership of the digital media transmitted over a network. A good stego-image should have high embedding capacity, robustness, imperceptibility, security, and less computational complexity [1].
Steganography has numerous applications in various fields including covert communication, image copyright protection (authentication using watermarking), image captions, extra information such as image integrity (fraud detection), subtitles to videos, smart browsers, automatic copyright of the content, copy control in DVD by media, and broadcasting movies [2]. In medical imaging, patient’s details are concealed within medical images, thus providing a secure scheme, and lowering the cost of transmission. Steganography has vast applications in defense organizations and intelligence agencies for the safe movement of confidential records. In finance, it is used in smart ID cards where personal identifiable information is embedded in the picture itself for the copyright and security of cards. It is also used in online voting systems to provide secure voting and robustness against a variety of fraudulent behaviors [3].
The term “cover image” describes the medium in which secret information is embedded [1]. Modern image data hiding uses two basic principles for concealing data, namely the embedding and extraction algorithms. The essential components of the embedding algorithm are a cover image, secret data, and a secret key. Stego-image is obtained by concealing the secret data into the cover image using the embedding algorithm. The stego-image is then used as an input object to extract the secret data [2]. Multiple formats are used in image data hiding as a cover image, such as PNG, GIF, TIF, JPEG or Bitmap [3]. Image steganography uses image processing techniques for embedding.
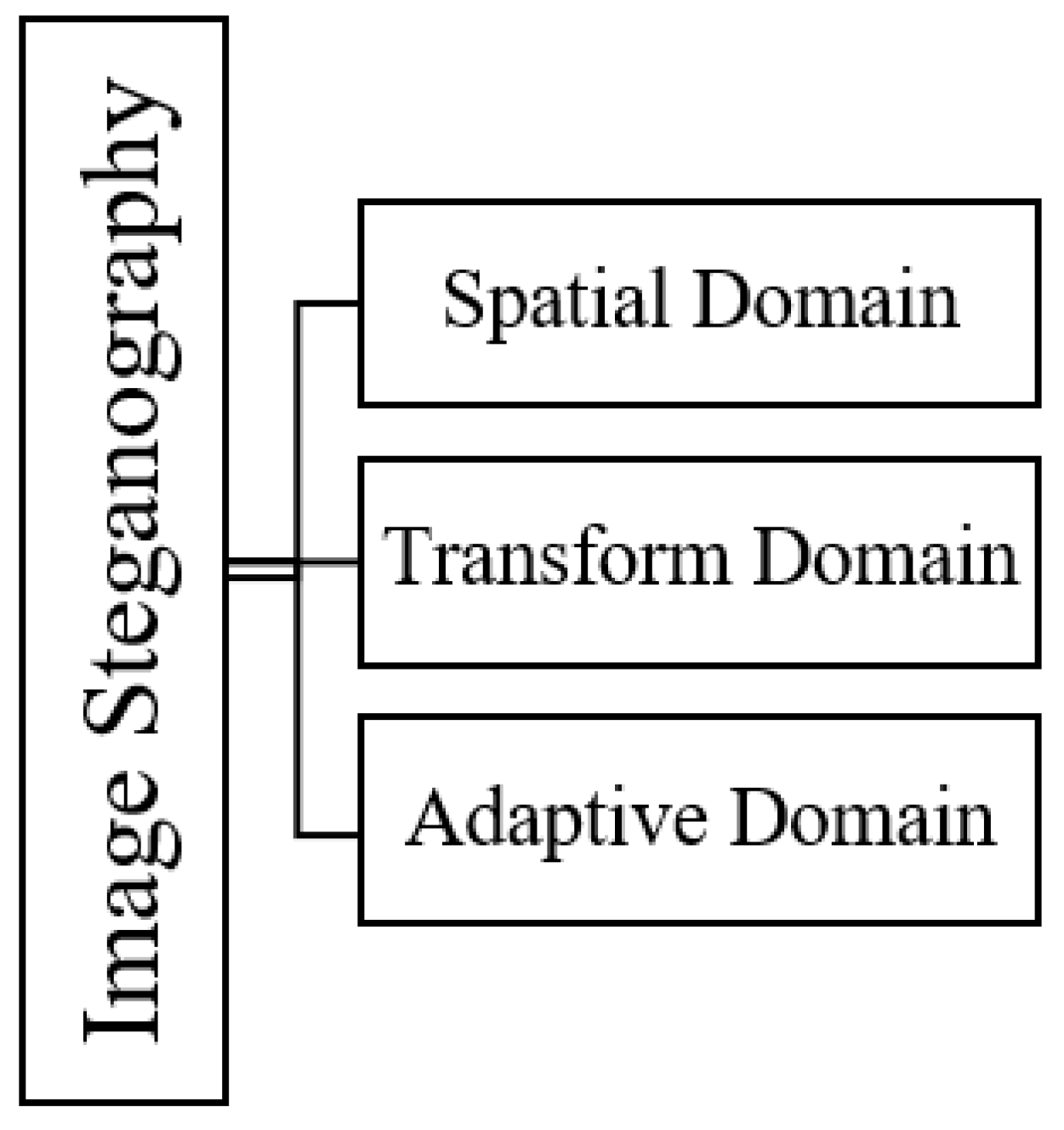
The embedding process in data hiding uses a few basic schemes, as shown in Figure 1, and it plays an important role in any stego-image. The commonly used techniques in steganography are based on the spatial domain [4], in which the secret data is directly embedded into the cover image. The other technique used is the transform domain [5], in which the cover image is first converted to another form, such as signals, and then the secret data is embedded. Thirdly, the adaptive scheme [6] specifically works by utilizing the statistical characteristics of an image before the secret information is concealed into a spatial or transform domain. This approach effectively conceals the alteration in an image [7,8,9].
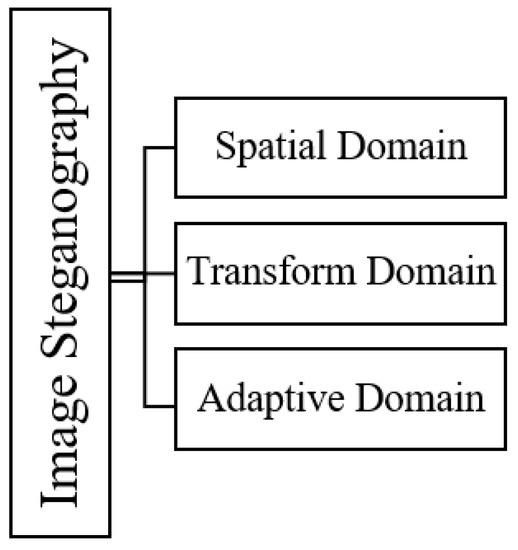
Figure 1.
Categorization of Image Steganography.
The format of the secret data can be either plain or raw, compressed, encrypted, or a combination of both, that can be hidden or concealed within the cover medium [10]. Various cryptographic operations in steganographic schemes have been proposed for the protection of secret data concealed in digital images before transmitting them over a network [11,12]. For example, modulus operations, AES, map-based scramble techniques, XOR, RC4, RSA, etc. These cryptographic methods are combined with digital image processing data hiding techniques [9,13,14,15,16,17,18,19,20]. However, among various methods of cryptography used, RC4 has many advantages, such as higher computational speed, resilience to cryptographic attacks, and providing stability to histogram values [13,14,15]. Steganography based on RDH scheme is generalized into three methods, namely the compression method, histogram shifting and expansion-based methods [21,22,23]. The proposed scheme uses histogram shifting for concealing secret data bits into the cover image.
A combination of bit-plane slicing, linear prediction and RC4 cryptographic algorithm is used in the proposed scheme to provide high embedding capacity and integrity (security) to the steganographic image by enhancing the visual quality. Primarily, the cover image is divided into 8 bit-planes and a new image is reconstructed using the BPs (bit-planes). The linear prediction is applied over the reconstructed bit-plane image blocks to provide an nBPs residual image, and finally, the histogram shifting is applied to the image to conceal the secret information into the bit-planes residual image (nBPs). Specifically, the histogram of the nBPs residual image is scanned and the peak point (highest value) in the histogram is chosen for embedding. Then the encrypted secret data bits are embedded by shifting the histogram towards the zero point. These procedures make a peak point more concentrated for embedding, thus resulting in good embedding capacity, and the occurrence of the zero values of a histogram is enhanced.
As compared to the existing RDH schemes, the proposed scheme has the following contributions:
- Higher security: The existing RDH schemes use cover-image to directly embed the secret data which results in exploitation of the cover-image. The proposed scheme uses the nBPs residual image to embed the information, and this provides security to the cover image. Furthermore, the use of RC4 encryption ensures the safety of the secret data from eavesdropping. RC4 has a higher encrypting speed, therefore, it is more suitable to use with RDH schemes.
- Higher embedding capacity: The existing schemes mostly use bits per pixels which provided less embedding capacity. The proposed scheme uses bit-planes (BPP) with linear prediction providing more peak and zero-point pairs resulting in higher embedding capacity.
- Greater Visual Quality: The proposed scheme provides greater visual quality due to the use of block division of nBPs image and has less distortion of the stego-images making the hidden secret data undetectable.
The rest of this paper is organized as follows. Section 2 provides a brief literature review on the implementation of RDH schemes using image steganography. In Section 3, the proposed scheme is discussed and in Section 4, the experimental results as well as a comparison of the results with previous RDH schemes, are given. Finally, Section 5 concludes this paper.
2. Related Work
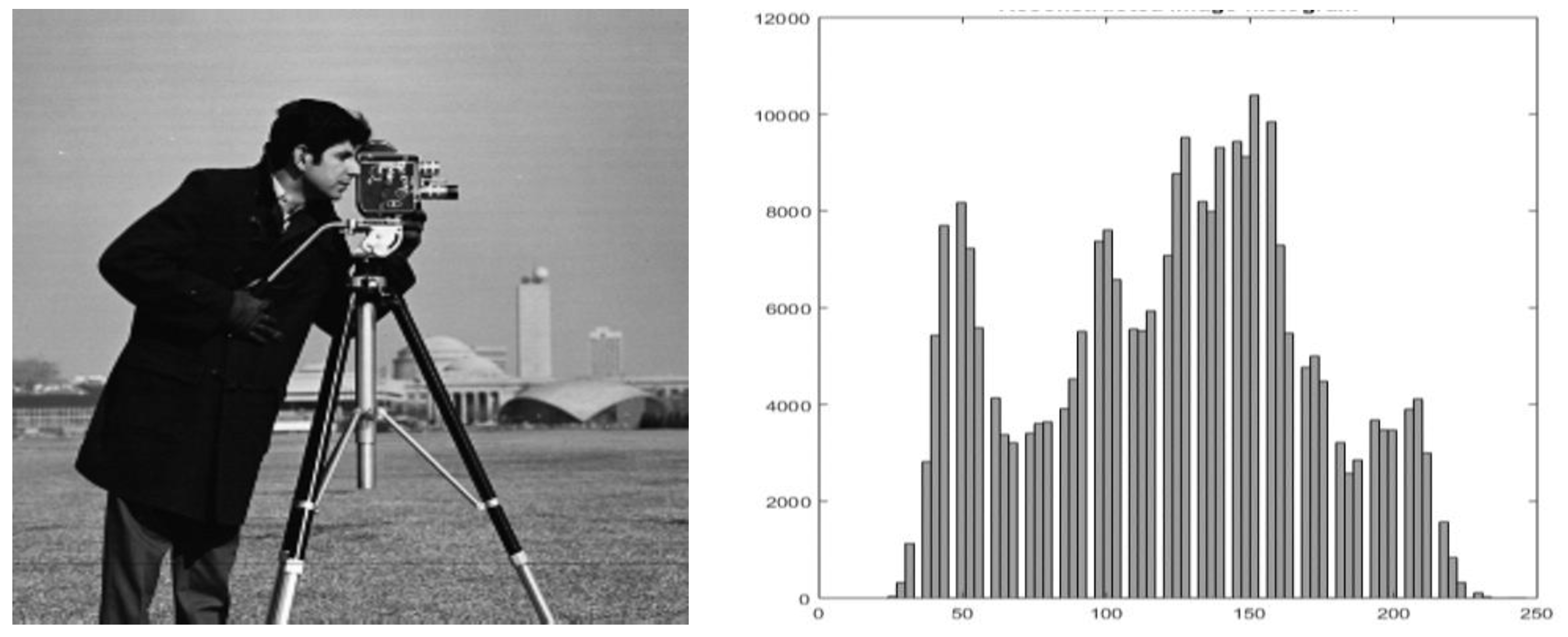
The Reversible Data Hiding (RDH) scheme is initially proposed by M.U.Celik et al. [24] in 2002, which has attracted many researchers due to its vast applications. After extracting the secret data, the cover image is recovered without loss of information. Therefore, this technique is suitable for use in medical and military setups where even a slight image distortion is not tolerable. Ni et al. [9] proposed a novel scheme based on histogram shifting utilizing the RDH scheme. RDH largely operates on four major schemes, including difference expansion, compressive sensing, histogram shifting, and pixel-based methods. The simple illustration of the RDH method is shown in Figure 2. The “Cameraman” image and its histogram are used as an illustration to elucidate the given scheme characteristics [9]. The three steps involved during the embedding process of the scheme are as follows:
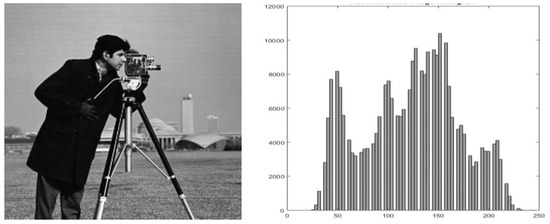
Figure 2.
Cameraman and its histogram.
- Step 1
- First, the peak values and zero values are searched.
- Step 2
- Next, the entire image is scanned in sequential order, such as row-wise and column-wise. The values in the histogram are incremented by “1”, shifting towards the right near the zero point.
- Step 3
- Finally, hiding the secret data in the peak points of the histogram.
The peak points of the histogram, having the highest pixel values, are first searched. If the algorithm encounters “1”, the peak point will be incremented by “1”, and the histogram is shifted towards the right. If the algorithm encounters “0” as secret data, the peak point will remain unchanged. Finally, the stego-image is obtained by applying the embedding process and the stego-image can be transmitted on the internet by applying the RDH basic scheme.
However, the embedding capacity was restricted due to an inadequate number of peak point pixels. Nowadays, the research in RDH has become quite significant and several schemes are proposed. These schemes are divided into two major categories: spatial and transform domain of image steganography.
2.1. Spatial Domain RDH
Zhang et al. [21] proposed a novel technique of RDH in encrypted images. Rashmi et al. [25] used the RDH scheme. They first encrypted the secret text with the AES encryption which is a symmetric key cryptography and embedded the key along with the cipher text. Then the resultant cipher bits are inserted into the cover image using a simple LSB replacement method. The use of encryption has improved security. RDH solely has restricted embedding capacity due to its reversible nature [4]. Lui et al. [26] proposed RDH based histogram shifting. First, the cover image is used to extract nBPs (n number of bit planes) and separated them into BPTI (Bit plane truncation image) to convert them into blocks. The secret data is concealed by using the peak points of each block of the reconstructed bit-planes histogram. Tsai et al. [27] used histogram shifting with predictive coding based on RDH to improve embedding capacity. The authors modified the classic histogram shifting, they applied predictive linear coding on the cover image. This is carried out by finding the difference of basic pixels with all the other pixels of the image. The secret data was concealed into the difference histogram obtained through linear prediction. Kuo et al. [28] proposed the RDH technique using blocks of an image for histogram shifting. In this scheme, the non-overlapping selected cover image is transformed into four blocks. The histogram of each block is taken and shifted, and secret data bits are concealed into a histogram of blocks. The data extraction was used as the inverse for gathering information from the embedding procedure. The embedding capacity was eventually increased but this scheme exploited the cover image. This did not provide enough security to the cover image as the secret data was not encrypted. Xiaoyuan et al. [29] proposed a scheme using bit-planes and encryption. Wengui Su et al. [30] used RDH based on pixel value ordering. In this scheme, the authors divided the cover image into two different regions, and then further divided those two regions into non-overlapping blocks, which are classified using local complexity. The secret data is embedded in these overlapping blocks. Patel et al. [31] proposed an LSB based scheme which used dynamic key cryptography by utilizing random key generation to provide security to stego-image. Xiao et al. [32] used RDH based on bit-plane operation with adaptive embedding. In the proposed method, the authors decomposed the cover image into bit-planes. The bit-plane block difference histogram is taken to add the secret data adaptively using the data hider.
2.2. Transform Domain RDH
Ming li et al. [33] have introduced a compressive sensing based RDH technique that used a small number of coefficients. The cover image is converted into several bit-planes to conceal secret. This conversion is also known as patch-level. It only used the reconstructed image of three-biplanes to hide data. The cover image was directly exploited to hide secret data. Iwendi et al. [34] proposed a scheme which uses Key-Split-Watermark based on blind zero watermarking technique for software code protection. The source code is encrypted using a key. The key and the original watermarked code are registered with the Certification Authority (CA) so that, when the code is altered the key would not match with the CA.
2.3. Miscellaneous RDH Schemes
Srivastava et al. [35] proposed a scheme to secure the medical internet of things for sanitizing the explicit /sensitive terms in unstructured medical datasets. They used three steps for data processing that are, dictionaries, regular expression and re-cognition-tagger for the privacy protection of the patients’ data using HIPAA (Health Insurance Portability and Accountability Act) privacy rules. N. Subramanian et al. [36] proposed a scheme based on deep learning methods that includes Convolutional Neural Network-based method, traditional method, and General Adversarial Network-based method to explore image steganography [37]. Z. Qu. et al. [38] proposed a scheme based on quantum image steganography in which they have used exploiting modification direction (EMD) and one secret bit is concealed using EMD into the corresponding carrier pixel-groups using ary-notational system. Chiung-Chen et al. [39] proposed schemes which showed the use of multiple scanning techniques. Fadhil et al. [40] proposed a scheme that uses RC4 encryption and histogram shifting method for medical image processing. Zhengjun et al. [41] used parameters in gyrator and chaotic map for the encryption of double images. Chen et al. [42] analyzed the automation of machine learning to acquire information about the citations and topics published. Wenqiang et al. [43] showed how fix time can be used to protect images and also analyzed the behavior of the system. Zhengjun et al. [44] uses the fractional Fourier transformation for image encryption. It used iterative procedure to transform unit for concealing images.
3. Proposed Methodology
As shown in the literature review, there are vulnerabilities in the existing techniques such as insecurity and lower embedding capacity of the RDH algorithm. These facts hinder the required achievements such as the inaccessibility and detectability of steganographic images. The security of digital data authorization is also an issue. The cover image and stego-image are prone to steganalysis. To secure steganographic images, the proposed scheme first converts the cover image into 8 bit-planes and then a new image is constructed by combining different bit-planes of the cover image. Afterwards, linear prediction is applied to the reconstructed n-bit-plane image to acquire a residual image. Histogram shifting is applied to the newly obtained nBPs residual image to embed secret encrypted data. The use of bit-planes and linear prediction enable histogram to provide more peak and zero-point pairs. This will result in achieving more embedding space. The embedded data is secured by RC4 encryption which adds an extra layer of security to the proposed scheme. The cover medium (image) secured by using nBPs residual image.
The steps involved in the proposed scheme of the RDH are termed as below:
Input: Let “I” be the cover image of size 512 × 512 and is used to perform RDH technique for data hiding, “S” represents the generated random secret bits.
Output: The stego-image “EI” (Embedded image)
The scheme further consists of two more procedures, such as embedding procedure discussed in Section 3.1, and extraction procedure discussed in Section 3.2.
3.1. The Embedding Procedure
In previous RDH schemes, the peak points did not have high embedding capacity because they either used simple LSB or embed data using bits per pixels. However, in the proposed scheme, the peak points are more concentrated because of using bit-planes and using encryption security is provided to the secret data bits.
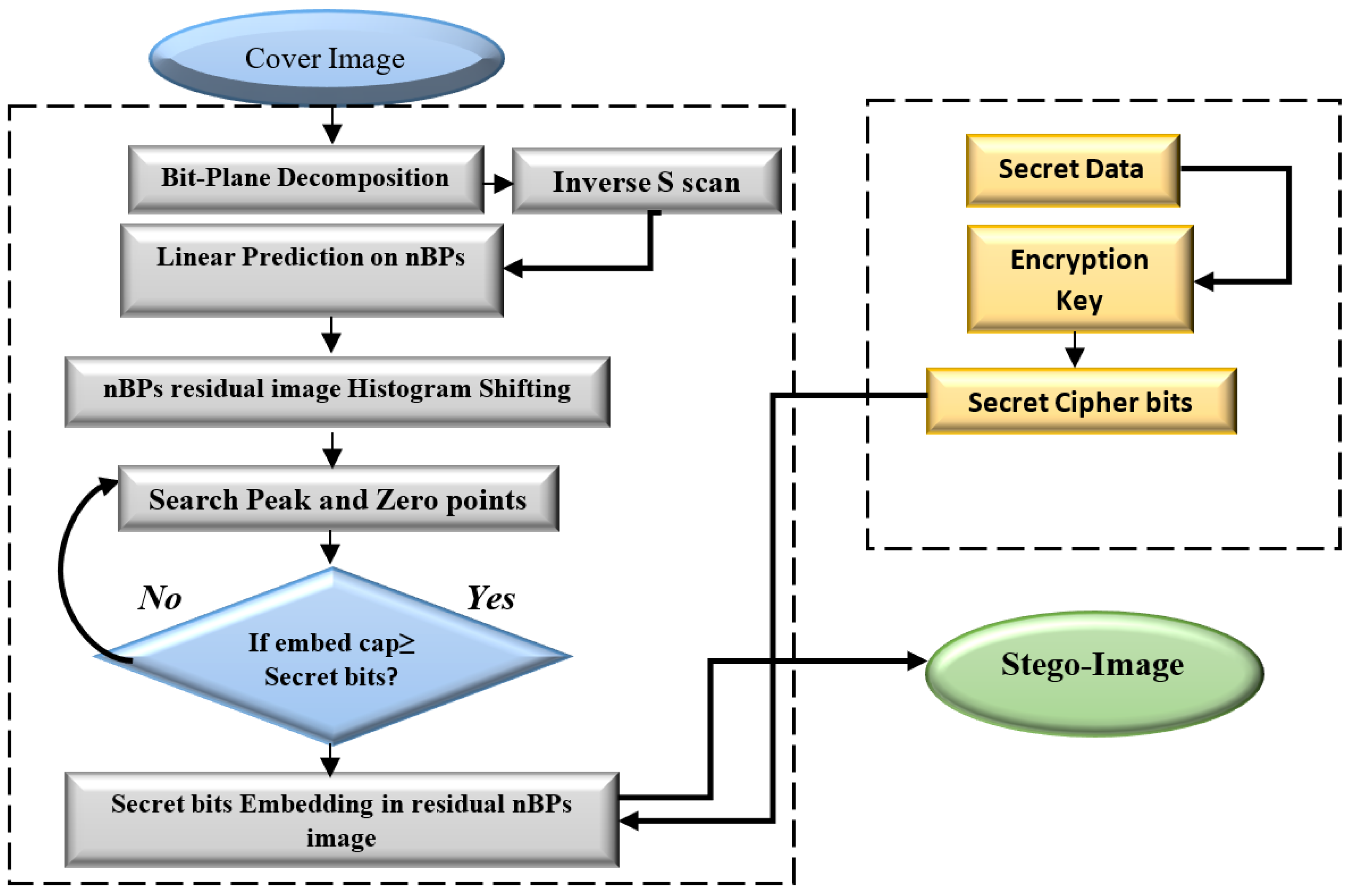
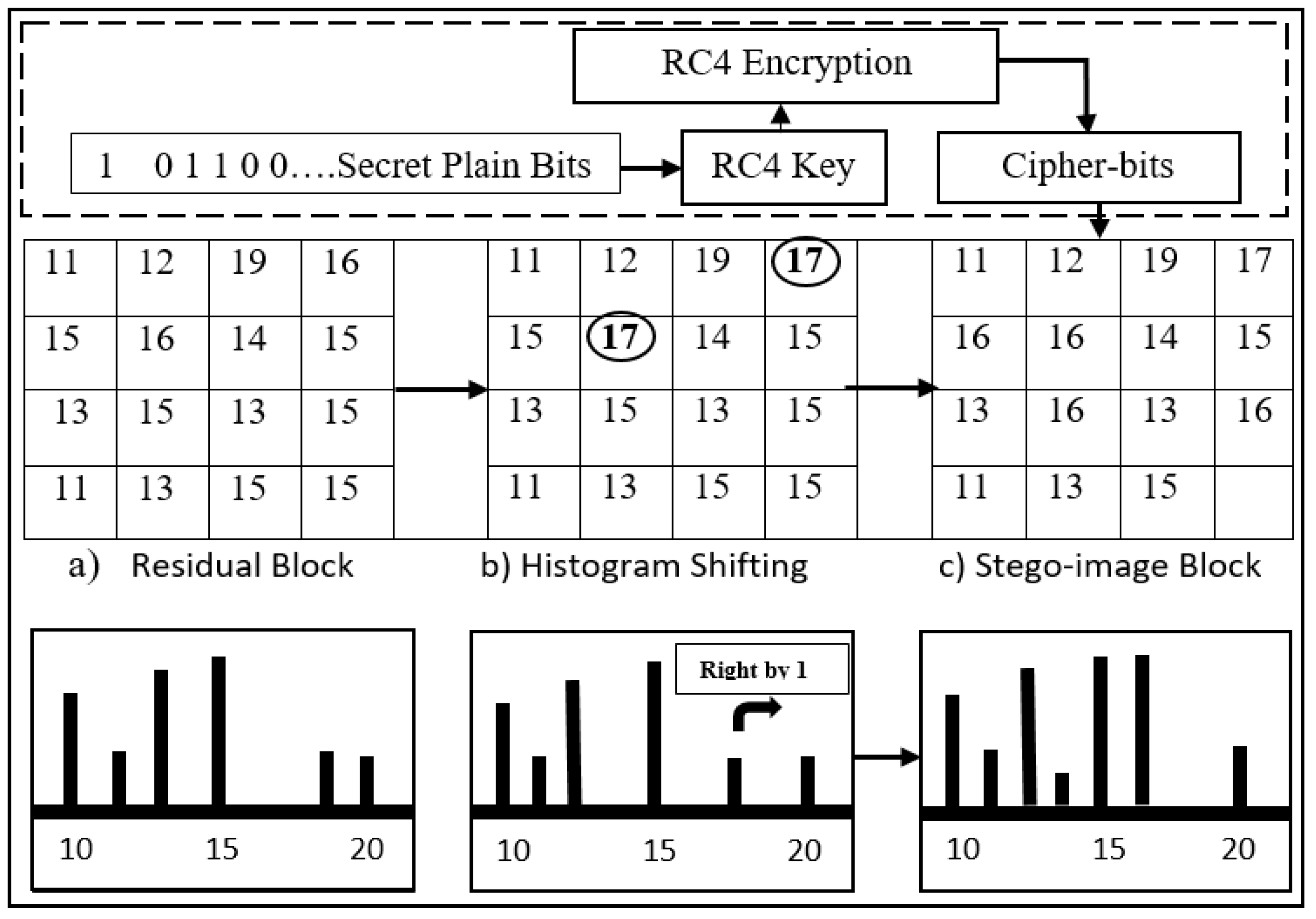
In the embedding procedure, three inputs are required, such as cover image, secret data bits and encryption key. The following steps are involved in the embedding procedure and sequence of operations as shown in Figure 3.
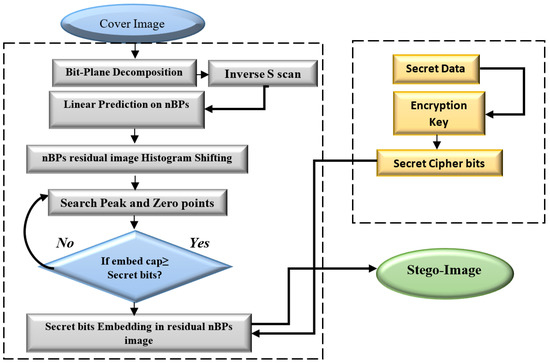
Figure 3.
Flowchart of the Embedding Procedure.
Step-1: Bit-plane conversion
The bit-planes are extracted from the cover image “I” and have 8 individual images where each bit-plane image consists of 512 × 512 bits. The lowest bit-plane does not have any visual features and comprises the least significant bits while the highest bit-plane 7 has the most significant bits and contains the higher visual features of the image.
Step-2: Block division
The nBPs are taken from a cover image. An image is generated by reconstruction using either 4, 3, or 2 bit-planes. The reconstruction using smaller bit-planes is the most suitable as it provides more space to conceal secret information. On the other hand, the most significant bits provide better visual quality, but less embedding capacity as further discussed in Section 4.3.
Step-3: Order of scanning
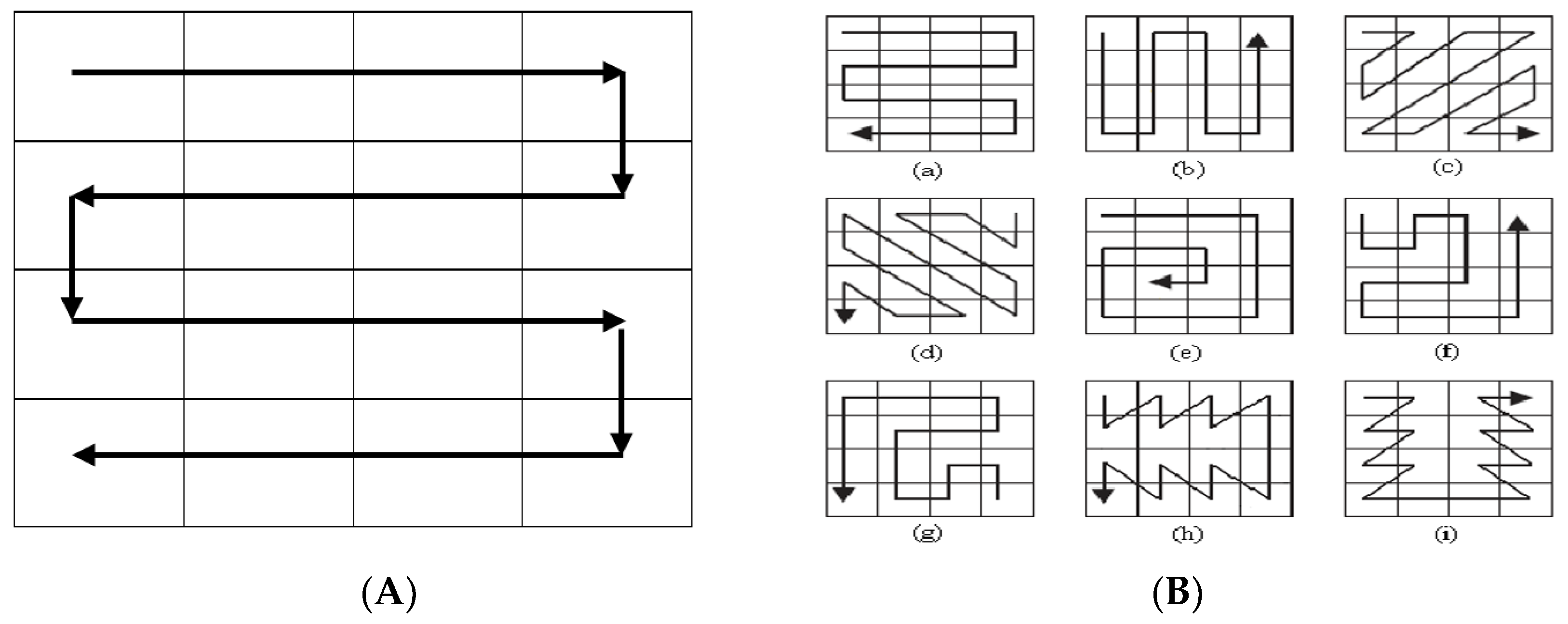
The block of the reconstructed image is scanned in inverse S-order. Commonly, a raster scan is frequently used for pixel scanning order, but it is not suitable for the image scanning as it does not support its characteristic features. It provides better resolution than other scanning patterns. The local pixels are first scanned in inverse S order which is more suitable for the proposed scheme. Figure 4A demonstrates the inverse S-scan [39].
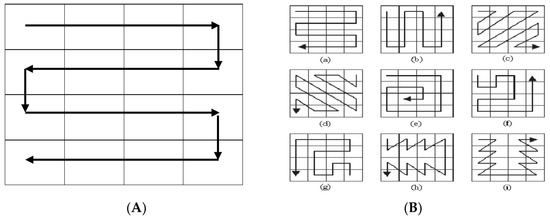
Figure 4.
Scanning and its types, (A) Inverse S scanning, (B) Different types of scans.
Scanning order plays an important role in any RDH scheme. To calculate the adjacent difference of the nBPs image in the proposed scheme, the inverse S scan is chosen as other scans can create underflow conditions by generating negative values of the residual image. Figure 4B shows multiple scanning techniques used in RDH image processing and they are (a) Inverse S scan, (b) Inverse U Scan, (c,d) Diagonal Scan, (e) Spiral in Scan, (f) Continued orthogonal scan, and (f,g) Fractal scans [39].
Step-4: Linear prediction:
The linear prediction is performed on nBPs image block, specifically, the difference among the neighboring pixels is taken. This is known as forward linear prediction. The forward linear prediction is also called causal prediction and it provides a stable inverse. The pixel difference taken by linear prediction is expected to be very close to zero to provide a more concentrated histogram for embedding. The following is the general equation of forward linear prediction:
Observing
Predict
Equation (1) observes the image pixel values of the bit-plane reconstructed image, where i shows the number of pixels, n is the predictor. Here, the image block is scanned after observing the difference between the values of adjacent pixels in an image block. Equation (2) shows the difference values which are calculated using Equation (1). These values are the prediction values, and the resulting image is known as a residual image. The difference between the adjacent pixels is calculated to create an nBPs residual image. Equation (3) is the simplified forward linear prediction: where shows the difference and is calculated using and . These edicts show how the adjacent pixels are subtracted from each other resulting in a new image known as residual image.
Step-5: Encryption
RC4 encryption is applied to the secret data bits S, and plain secret bits will be converted to cipher-bits before concealing them in the nBPs residual image. RC4 has high computational speed and provides a concentrated histogram [40].
Step-6: The secret embedding algorithm
A histogram of the nBPs residual image is taken. The peak and zero-point values of the reconstructed image histogram are searched. The secret data bits S are embedded into the peak and zero-point pairs of the residual image using the embedding algorithm as described in Algorithm 1. Here, P denotes the peak point and Z represents the zero point in the algorithms.
| Algorithm 1: Pseudocode Embedding Algorithm of the Proposed Scheme. | |
| Case 1 | |
| Input: | nBPs Image (I), Secret Data (S) |
| 1.if Secret Data(S1 && P < Z) | |
| 2. then histogram shifts to right by 1; | |
| 3. PeakP; | |
| 4. Select P and P + 1 to embed data | |
| 5. if ()) | |
| 6. | |
| 7. else | |
| 8. do nothing (S) | |
| 9. end | |
| Output: | EI (Embedded Image) |
| Case 2 | |
| Input: | nBPs Image (I), Secret Data (S) |
| 1.if Secret Data(S1 && P>Z) | |
| 2. then histogram shifts to left by 1; | |
| 3. PeakP; | |
| 4. Select P and P−1 to embed data | |
| 5. if ()) | |
| 6. | |
| 7. else | |
| 8. do nothing (S) | |
| 9. end | |
| Output: | EI (Embedded Image) |
The values in the histogram are incremented by “1” shifting towards the right where the zero point is near the peak point. The value of the peak point will become empty for the shifting of the histogram. The peak point values are used to embed the secret information bits and the histogram is shifted. When the algorithm encounters secret data bit S to be “1”, the peak point will be incremented by “1”. If the algorithm encounters “0” as secret data bit S, the peak point remains unchanged. In the embedding algorithm case, where peak value P is “15” and zero value Z is “17”, which shows that P < Z, so the histogram will shift towards the right, and “1” will be added to the peak point. In embedding, the condition in Algorithm 1 shows that if the algorithm encounters P + 1, then secret bit “1” is embedded as cipher-bit as shown in Figure 5.
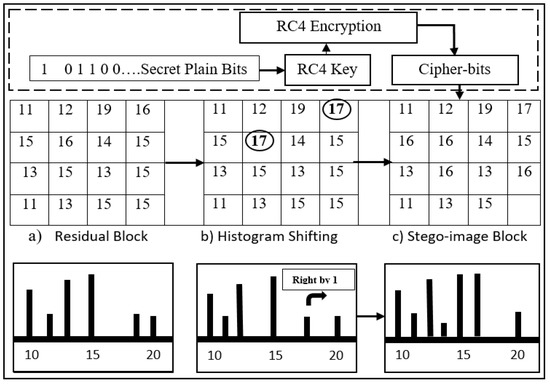
Figure 5.
Histogram shifting illustration.
After concealing the secret bits in the nBPs residual image, the image having secret bits “stego-image” is scanned in inverse order at the receiving end to extract the secret data bits and the nBPs residual image is restored. The embedding capacity can be increased by using numerous peak and zero-point pairs.
3.2. The Extraction Procedure
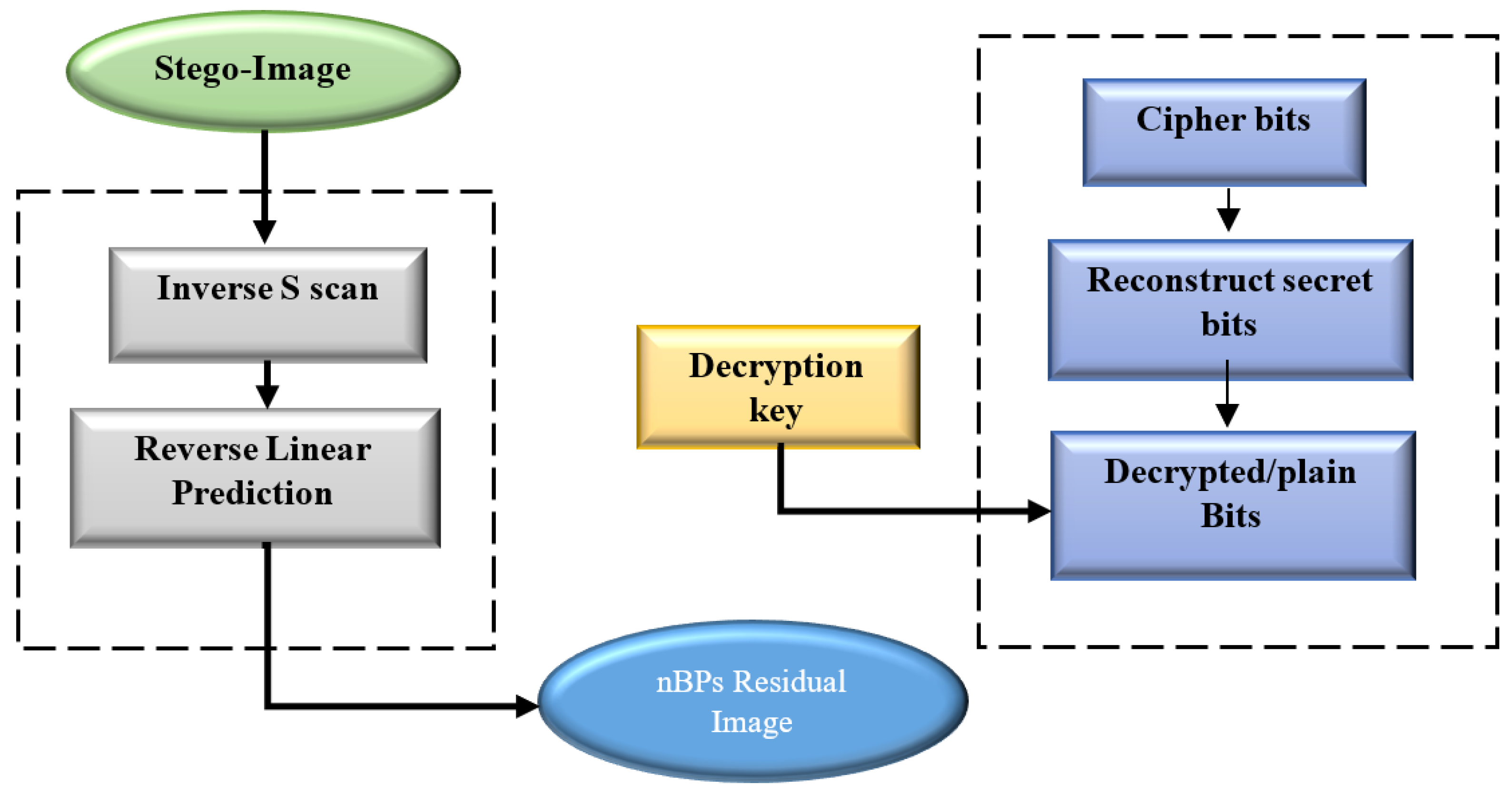
The extraction procedure ensures that the secret data bits are extracted accurately to obtain the exact residual image by applying a reversible data hiding scheme mechanism. The secret data bits are embedded in the nBPs residual image by providing a secure algorithm instead of directly exploiting the cover image. The extraction procedure is the inverse of the embedding technique. The sequence of the extraction procedure is shown in Figure 6.
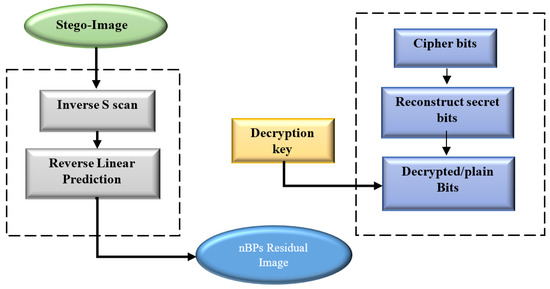
Figure 6.
Flowchart of the Extraction Procedure.
Step-1: Inverse-S scan the stego-image
The stego-image I’ is scanned in inverse S-order. This will ensure the extraction of the secret data bit from the stego-image without losing any data bits.
Step-2: Extracting S bit algorithm
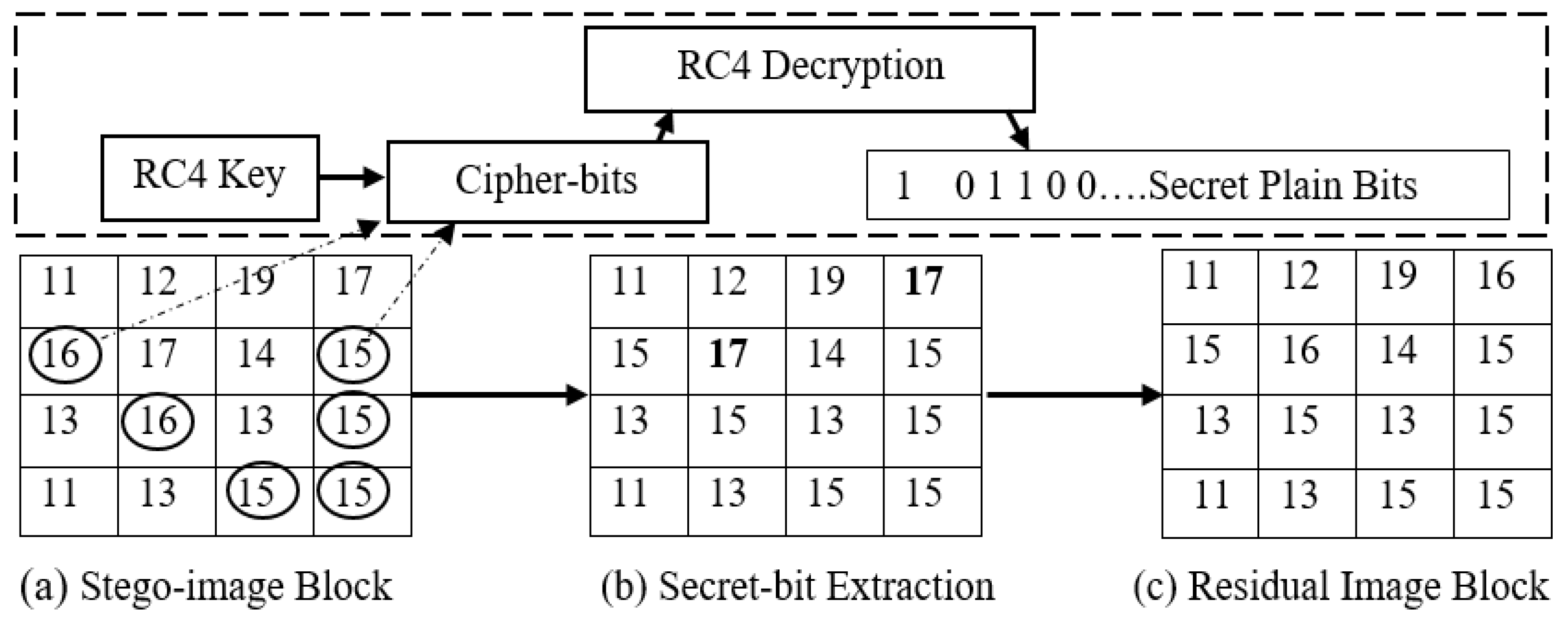
The secret data bits S are concealed into the peak point and zero-point pairs of nBPs residual image histogram to make a stego-image. The stego-image is scanned using inverse-S order, and then the stego-image is decrypted using the same RC4 key that was used for encryption. The cipher-bits are first decrypted using RC4 key and afterwards, the plain secret bits are extracted using the extraction algorithm described in Algorithm 2.
Step-3: Restoring residual image
The restored residual image blocks are used to recover the original nBPs residual image.
Step-4: Recovering original nBPs image
The residual image is used to recover the original cover image by combining the bit-planes.
The extraction process fulfills the reversible data hiding requirements. The illustration in Figure 7 shows how the extraction algorithm works and how the secret data is extracted.
| Algorithm 2: Pseudocode Extraction Algorithm of the Proposed Scheme. | |
| Case 1 | |
| Input: | Cipher Image/EI (Embedded image) |
| 1. | |
| 2. | |
| 3. | |
| 4. | |
| 5. | |
| 6. end | |
| Output: | nBPs Image (I), Secret Data (S) |
| Case 2 | |
| Input: | Cipher Image/EI (Embedded image) |
| 1. Move value of P + 1; | |
| 2. | |
| 3. | |
| 4. | |
| 5. | |
| 6. | |
| 7. | |
| 8. end | |
| Output: | nBPs Image (I), Secret Data (S) |
| Case 3 | |
| Input: | Cipher Image/EI (Embedded image) |
| 1. Move value of Z; | |
| 2. | |
| 3. shifts to right by 1; | |
| 4. end | |
| 5.else do nothing; | |
| 6. end | |
| Output: | nBPs Image (I), Secret Data (S) |
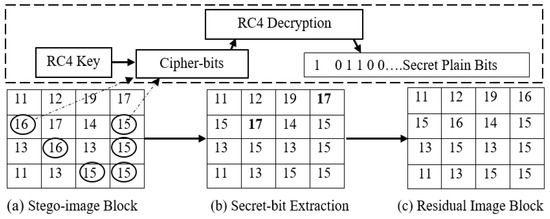
Figure 7.
Illustration of Extraction Procedure.
Where peak point P is 15 (Figure 7) and zero-point Z is 17, which shows that P < Z, so the histogram will shift towards the right and 1 will be added to the peak point. In extraction procedure, the condition in extraction algorithm (Algorithm 2) shows that if the algorithm encounters P + 1, then secret bit 1 is extracted, as illustrated in Figure 7a. The original nBPs residual image block is recovered. The data extraction was used as the inverse for gathering information from the embedding procedure.
4. Experimental Results
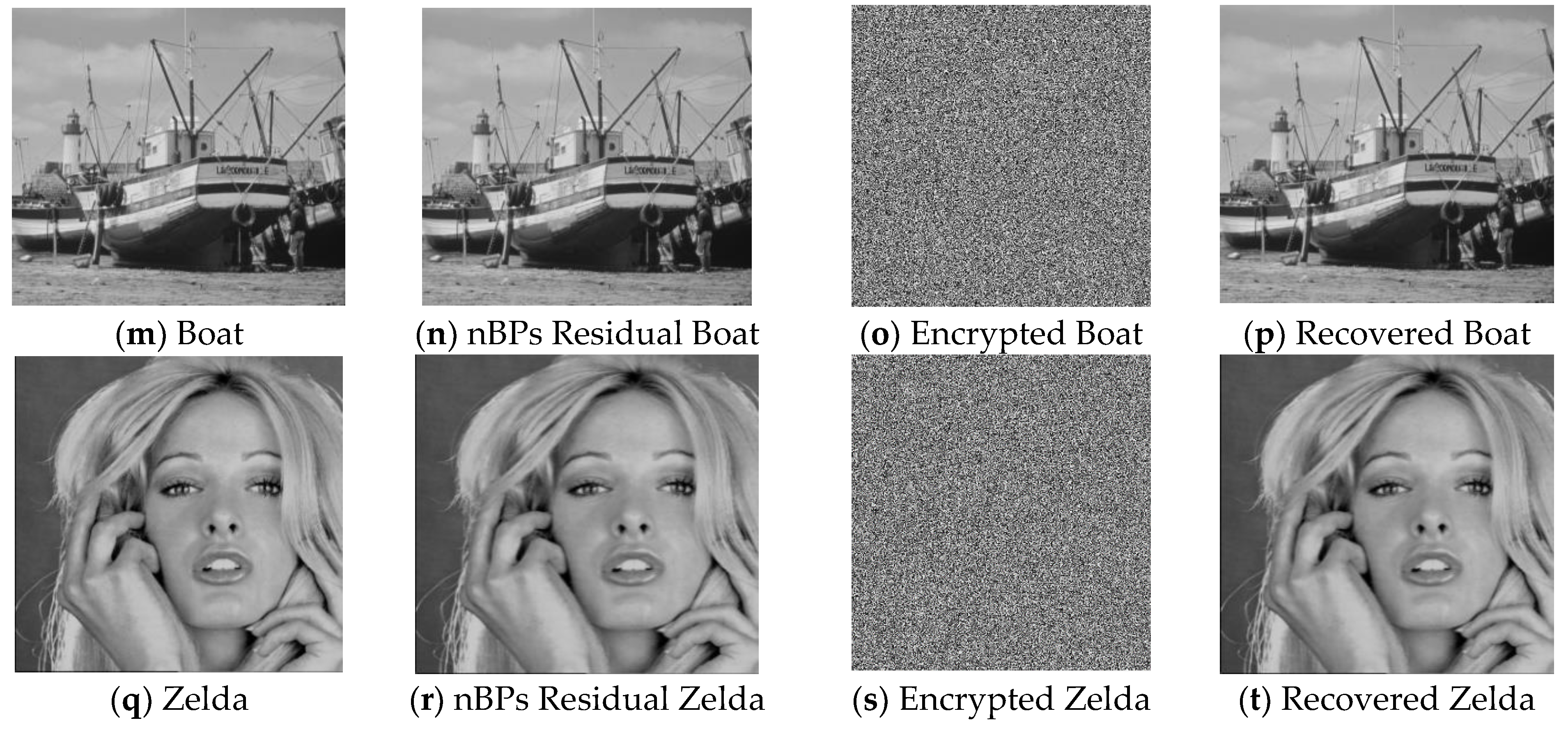
To assess the proposed scheme integrity, embedding, and visual merits, 5 grayscale images of size 512 × 512 are selected for analysis. They are ‘Lena, ‘Baboon’, ‘Airplane’, ‘Boat’ and ‘Zelda’. Figure 8 shows the comparison of the original cover image, nBPs residual image, encrypted image and recovered image, this is shown in the image (a) to image (t).

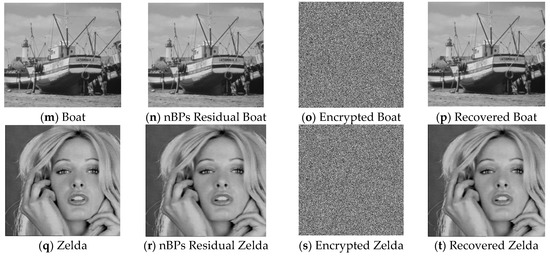
Figure 8.
Cover, nBPs residual stego-image, encrypted image and the recovered/decrypted images of sizes 512 × 512.
4.1. Performance Analysis of the Proposed Method
The performance of the proposed method is analyzed by the Peak Signal to Noise Ratio (PSNR), Structural similarity index (SSIM), embedding capacity and Chi-Square statistical attack on the stego-image to find whether the stego-image is robust and undetectable. To evaluate the visual quality of the cover/nBPs residual image with a stego-image, PSNR is utilized. The following equations show the generalized formula of the PSNR (4)–(6).
The PSNR (dB) is defined as:
The value of is the maximum pixel value in PSNR. Higher PSNR means the quality of the steganographic image having secret data concealed into it is similar to the original residual/cover image. The MAX is the maximum pixel value, and it is normally 255 if the image is represented as an 8-bit image. Where i and j in Equation (7) are rows and columns, respectively. The PSNR and the MSE (mean-squared error) in the proposed scheme is calculated by using the following equation:
where m is the number of rows and n is the number of columns. To evaluate the structural similarity index SSIM is calculated.
where L is the nBPs residual image and M is the stego-image. µ and σ are the co-variants of the residual and stego-images, respectively. Entropy shows the randomness of the encrypted image, and it ranges from 0–8. The value of entropy closer to 8 is considered better [25]. Table 1 shows the ratio, SSIM, and entropy of the proposed scheme.

Table 1.
Proposed RDH Scheme Output Quality measurement.
4.2. Performance Evaluation Using Block Division
The PSNR shows the visual quality of the residual/cover image against stego-image whereas embedding capacity shows the total hiding capacity of the stego-image shown by the name C (bits) where C stands for capacity. The best PSNR values lies between 30–50 db. The proposed scheme provides satisfactory embedding capacity as well as visual quality. Table 2 shows the block division of the Lena image. A pseudo-random number generator is used to generate the secret data bits which are encrypted using the RC4 algorithm. As many researchers for example Ni et al. [9], Li Lui [26] and Kuo et al. [28] showed through their experimental results that the smaller the block size the higher the embedding capacity.

Table 2.
Comparison of embedding capacity using different block sizes of Lena.
The proposed scheme also satisfies the given claims that smaller the block size, the higher is the embedding capacity and larger the block size the higher is the visual quality as larger blocks consist of the Most Significant Bits (MSB) of the images which have the higher visual quality. The proposed scheme also satisfies the given claim that smaller is the block size higher is the embedding capacity, and larger is the block size higher is the visual quality. As larger blocks consist of the Most Significant Bits (MSB) of the images, which have the higher visual quality. Table 2 and Table 3 show the Lena and Airplane image block division which can be seen from the different block sizes selected from 2 × 2, 3 × 3, 4 × 4, 5 × 5, 6 × 6, 7 × 7, 8 × 8, 9 × 9 and 18 × 18. When the block size 18 × 18 is selected the visual quality PSNR is high because it has the MSB pixels of the residual image. More blocks can be generated using the proposed scheme.

Table 3.
Comparison of embedding capacity using different block sizes of Airplane.
4.3. RDH Schemes versus Proposed Scheme
The proposed scheme provides integrity by providing good visual quality as well as embedding capacity. The two elements that affect the performance of the proposed scheme are the number of bit-planes selection and the block division of the residual image.
The performance of the RDH scheme is evaluated further by selecting a different number of bit-planes while keeping the block size fixed, i.e., 18 × 18. The values are compared with the work of Li. et al. [26]. The result shows that when a lower number of bit-planes is selected, the embedding capacity improves but the visual quality is not good. The proposed scheme provides better visual quality by attaining higher PSNR than the scheme [26], which is evident by the results shown in Table 4, Table 5 and Table 6.

Table 4.
Comparison of performance by selecting 4 bit-planes. Bold values shows the best results achieved by the compared schemes.

Table 5.
Comparison of performance by selecting 5 bit-planes. Bold values highlight the highest results.

Table 6.
Comparison of performance by selecting 6 bit-planes. Bold values shows the best result achieved by a scheme.
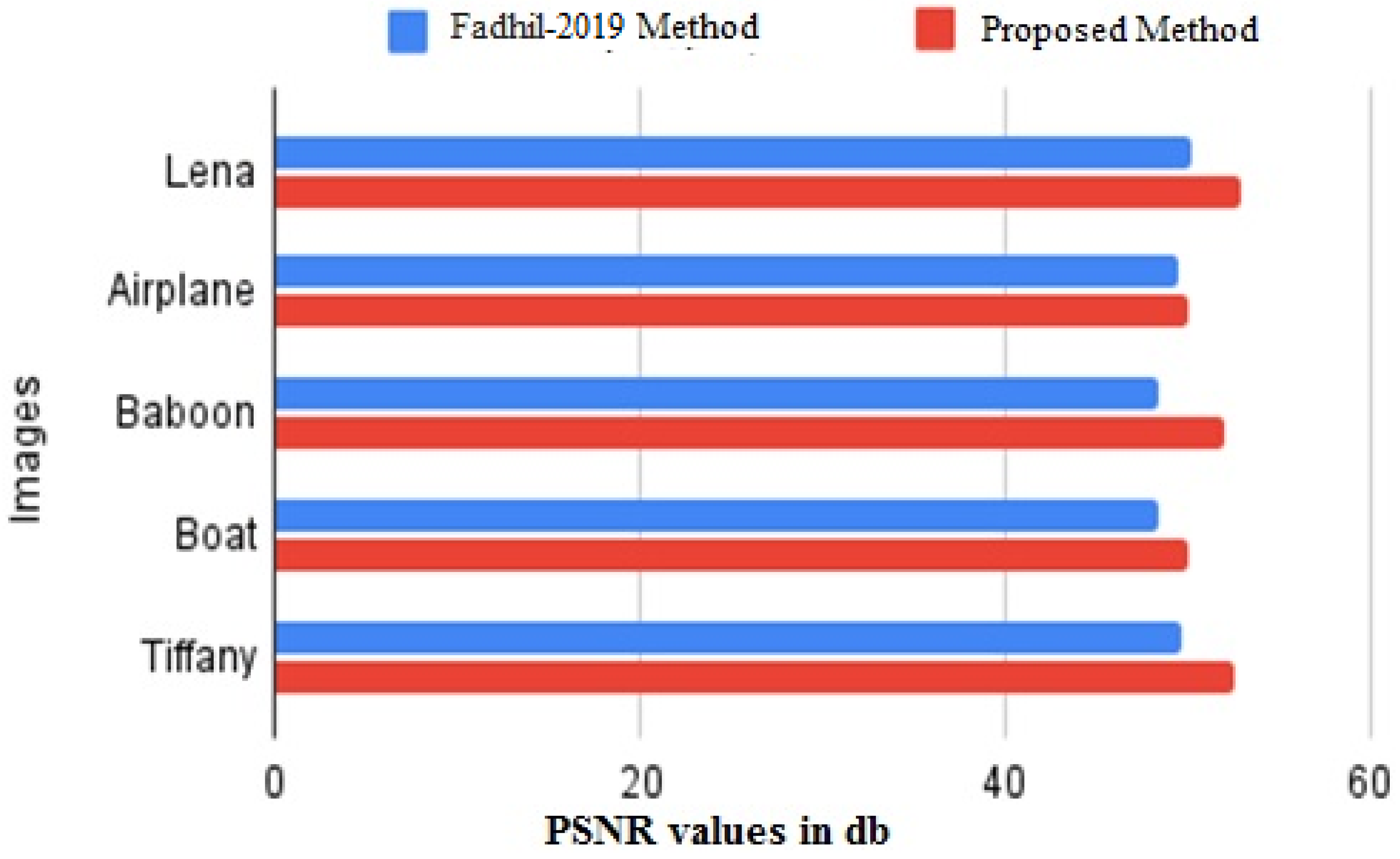
The proposed scheme can also act as a multi-embedding RDH scheme. The residual image and the stego-image can act as a new image in which secret data can be hidden. A comparison of the proposed scheme with other RDH schemes is shown in Table 7. The comparison is carried out with Ni et al. [9], Li et al. [26], Tsai et al. [27] and Kuo et al. [28] scheme. The 3 × 3 block size is selected for the evaluation. The results showed that the proposed scheme achieved higher embedding and visual quality than the preceding histogram based RDH schemes. The experimental results in Table 7 show that the proposed method achieved the highest PSNR value as compared with other methods. Moreover, the PSNR results (values in db) of the proposed method is compared with Fadhil et al. [40] results on selected five grayscale images and shown in Figure 9. The results indicate that the proposed method provides better visual quality. The resulting stego-image using the proposed scheme is visually very similar to the residual image, and thus providing the integrity between the residual image and the stego-image. This also proves that the stego-image is undetectable due to the high PSNR value.

Table 7.
RDH schemes comparison with proposed scheme. Bold shows the best results achieved by a scheme.
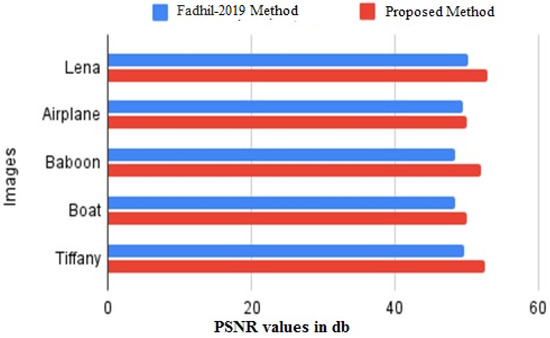
Figure 9.
PSNR values (db) Comparison between Fadhil et al. [40] vs. proposed scheme on five gray-scale images.
4.4. Chi-Square Steganalysis
Chi-square steganalysis is a statistical attack that detects the presence of random/secret data information in the images. The basic equation to find the chi-square test is given below:
where the value of Chi-square is , represents the observed value and is the expected value. The software used for the chi-square value is Guillermito which tests the robustness of plain images and stego-images.
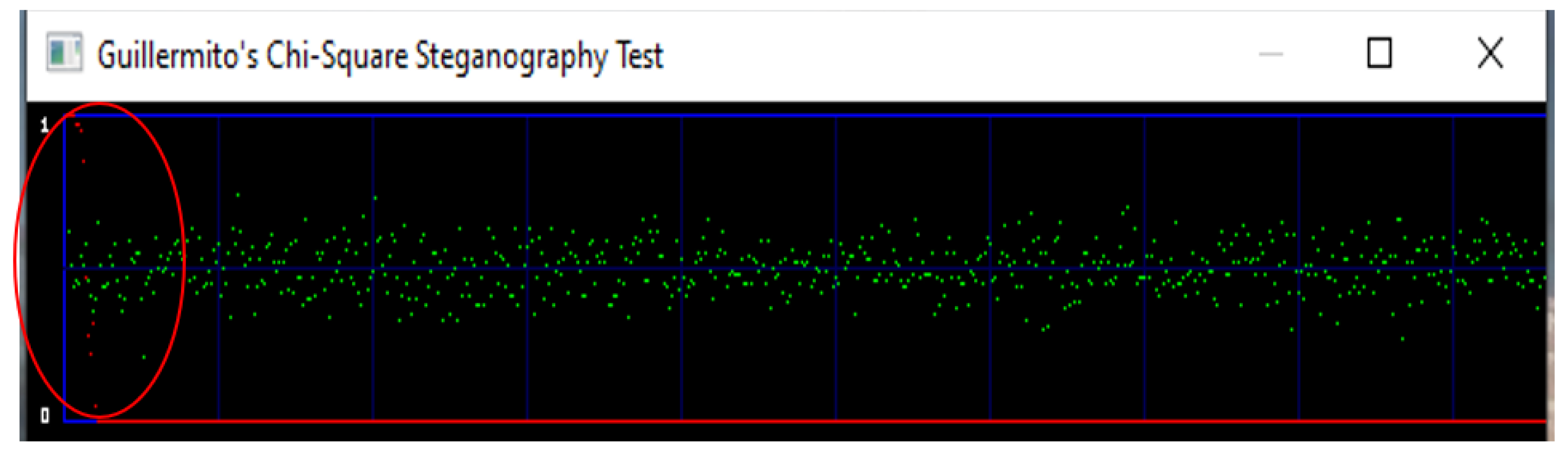
The bottom red line in the Figure 10, Figure 11 and Figure 12, shows the probability, the green dots show the information in the image packed around the blue line. If the top red line drops and moves around 0.5, hidden information is probable in an image. The flat bottom red line shows the probability is at 0 and there is no sign of hidden information. This statistical attack is used to check the randomness in an image. If there is randomness, then there is a chance that the image has been exploited to conceal information. A good steganographic scheme does not reveal if there is any hidden information in it. The first attack is carried out on the Lena cover image. Figure 10 which has no secret data hidden in it. The red circle and red dots show that the probability is near zero which is flat showing no random data hidden in the image.
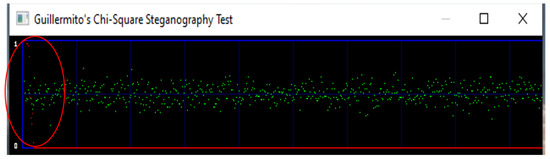
Figure 10.
Chi-square on Lena cover image.
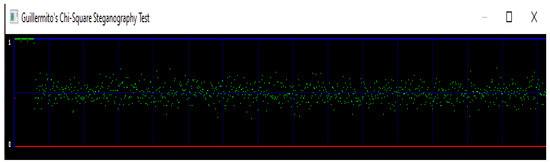
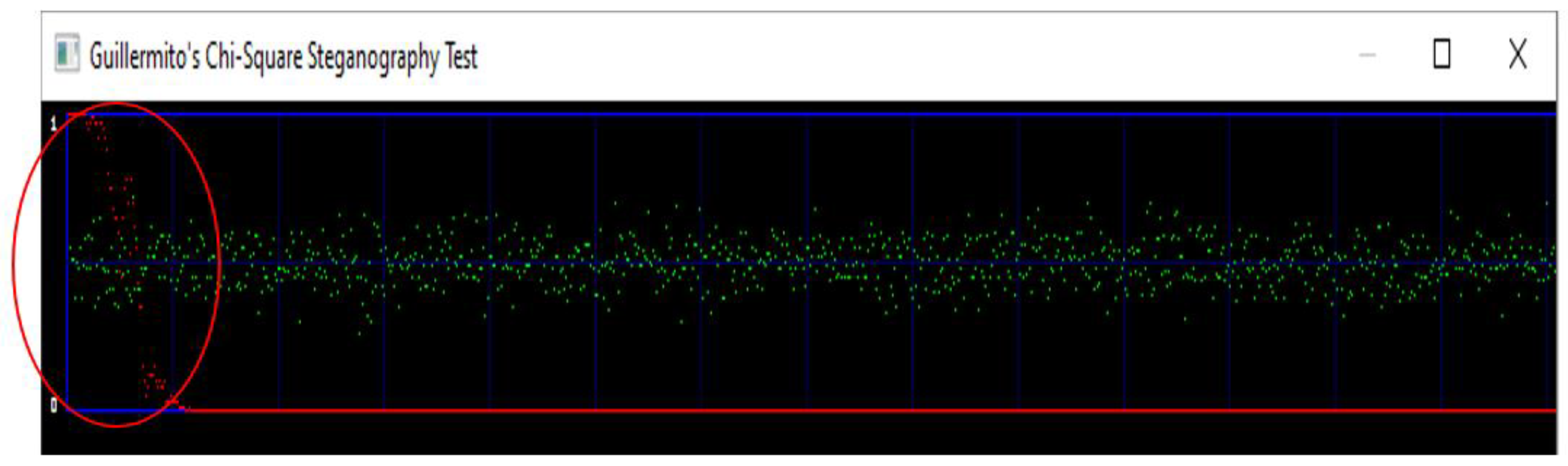
Figure 11.
Chi-Square on Proposed Stego-Lena Image.
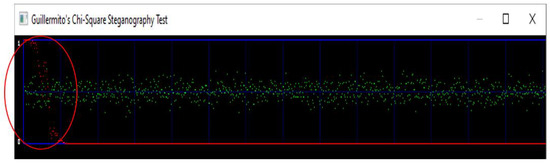
Figure 12.
Chi-square 1-Kb of hidden data detected in a random image.
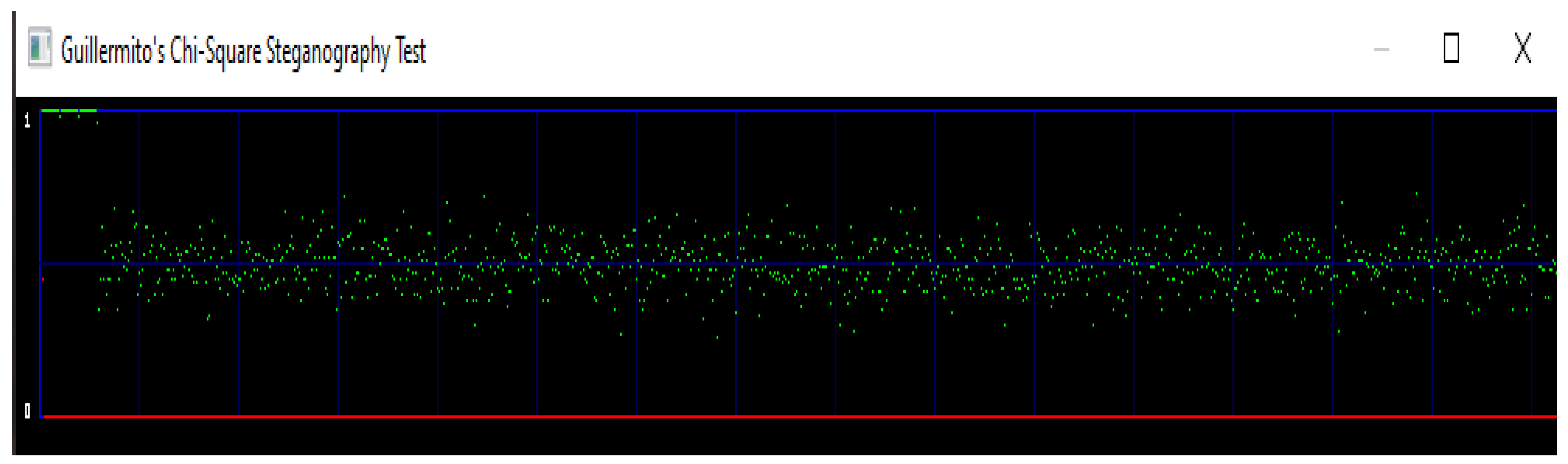
The second attack is carried out on the proposed scheme stego-image of Lena shown in Figure 11. The image is undetectable as the probability is near 0 showing no traces of hidden data.
Figure 12 shows an image having 1 kb random data which is detectable by the chi-square attack. The data is embedded using a simple LSB technique. In Figure 12, the red curve is maximum at the beginning, and eventually, it drops to zero showing the presence of 1kb of hidden data. This shows that there is data embedded in the image, and this one kilo byte of data is packed around 0.5 pointing towards randomness.
The chi-square steganalysis provides evidence that the stego-image generated by the proposed method is robust and undetectable. The Lena image selected for the chi-square attack from the proposed scheme is of size 512 × 512 residual nBPs image with a block size of 18 × 18. This statistical test provides an insight into the stego-image which can’t be seen through naked eyes. The visual attack, on the other hand, provides visual defects in the image having random data hidden either by seeing the distortion or difference in the images.
5. Conclusions
The proposed scheme intends to provide integrity (secure), enhanced embedding capacity, and greater visual quality. In this scheme, first, the extraction of bit-planes of the cover image is carried out and then the linear prediction is applied over reconstructed nBPs image. The reconstructed image (nBPs blocks/image) provides more space for the embedding of secret data in the proposed scheme. The nBPs Residual image’s histogram is used to conceal the secret data bits which provide security to the cover image. Secret bits are encrypted before embedding them into the nBPs image which provides an extra layer of security to the RDH scheme. The use of RC4 encryption provides security to the secret data bits which can be a shield against eavesdropping and man in the middle attack. By using inverse S scan there were no negative values, so this scheme didn’t have any underflow or overflow condition. The chi-square attack provides evidence for the scheme being undetectable. The lowest value of the analysis shows that the decryption was successful with high probability. The visual attack is also carried out which shows no sign of distortion among the cover/residual and stego-image. The performance of the proposed scheme is measured using PSNR, SSIM, embedding capacity and chi-square attacks on five gray-scale images. Our method provides integrity by providing good visual quality, i.e., higher PSNR values as shown in Table 1, as well as higher embedding capacity than the compared schemes. Moreover, the chi-square steganalysis provides evidence that the stego-image generated by the proposed method is robust and undetectable.
Author Contributions
Data curation, N.G.; Formal analysis, M.N., W.J., I.A.K. and S.S.; Funding acquisition, M.E.; Investigation, M.N.; Methodology, W.J., I.A.K. and S.S.; Supervision, W.J., I.A.K., N.G. and S.S.; Validation, M.E.; Writing—review & editing, A.M. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the EIAS Data Science Lab, College of Computer and Information Sciences, Prince Sultan University, Riyadh, Saudi Arabia.
Acknowledgments
This work has been supported by EIAS Data Science Lab, Prince Sultan University, KSA. The authors want to thank EIAS Data Science Lab and Prince Sultan University for their encouragement, support and the facilitation of resources needed to complete the project. Also, this work has been supported by the RUDN University Strategic Academic Leadership Program(recipient Ammar Muthanna).
Conflicts of Interest
The authors have no competing interests to declare that are relevant to the content of this article.
References
- Karakus, S.; Avci, E. A New Image Steganography Method and Optimum Pixel Similarity for Data hiding in Medical Images. Med. Hypotheses 2020, 139, 109691. [Google Scholar] [CrossRef] [PubMed]
- Doshi, R.; Jain, P.; Gupta, L. Steganography and its applications in security. Int. J. Mod. Eng. Res. 2012, 2, 4634–4638. [Google Scholar]
- Subhedar, M.; Mankar, V.H. Current status and key issues in image steganography: A survey. Comput. Sci. Rev. 2014, 13, 95–113. [Google Scholar] [CrossRef]
- Cheddad, A.; Condell, J.; Curran, K.; Mc Kevitt, P. Digital image steganography: Survery and analysis of current methods. Signal Process. 2010, 90, 727–752. [Google Scholar] [CrossRef]
- Liu, J.; Ke, Y.; Zhang, Z.; Lei, Y.; Li, J.; Zhang, M.; Yang, X. Recent Advances of Image Steganography with Generative Adversarial Networks. IEEE Access 2020, 8, 60575–60597. [Google Scholar] [CrossRef]
- Ansari, A.S.; Mohammadi, M.S.; Parvez, M.T. A Multiple-Format Steganography Algorithm for Color Images. IEEE Access 2020, 8, 83926–83939. [Google Scholar] [CrossRef]
- Qui, Y.; Qian, Z.; Zeng, H.; Lin, X.; Zhang, X. Reverisible data hiding in encrypted images using adaptive reversible tranformation. Signal Process. 2019, 167, 107288. [Google Scholar] [CrossRef]
- Hussain, M.; Wahab, A.W.A.; Bin Idris, Y.I.; Ho, A.T.; Jung, K.-H. Image Steganography in spatial domain: A survey. Signal Process. Image Commun. 2018, 65, 46–66. [Google Scholar] [CrossRef]
- Ni, Z.; Shi, Y.; Ansari, N.; Su, W. Reversible data hiding. IEEE Trans. Circuits Syst. Video Technol. 2006, 16, 354–362. [Google Scholar] [CrossRef]
- Wang, J.; Cheng, M.; Wu, P.; Chen, B. A survery on Digital Image Steganography. J. Inf. Hiding Priv. Prot. 2019, 1, 87–93. [Google Scholar]
- Qiu, Y.; Ying, Q.; Lin, X.; Zhang, Y.; Qian, Z. Reversible Data hiding in encrypted images with dual embedding. IEEE Access 2020, 8, 23209–23220. [Google Scholar] [CrossRef]
- Manikandan, V.; Masilamani, V. Reversible Data Hiding Scheme During Encryption Using Machine Learning. Procedia Comput. Sci. 2018, 133, 348–356. [Google Scholar] [CrossRef]
- Kusuma, E.J.; Sari, C.A.; Rachmawanto, E.H.; Moses Setiadi, D.R.I. A combination of inverted LSB, RSA and Arnold transformation to get secure and imperceptible image steganography. J. ICT Res. Appl. 2018, 12, 103. [Google Scholar] [CrossRef]
- Belazi, A.; Abd El-Latif, A.A.; Rhouma, R.; Belghith, S. Selective image encryption scheme based on DWT, AES S-box and chaotic permutation. In Proceedings of the 2015 International Wireless Communications and Mobile Computing Conference (IWCMC), Dubrovnik, Croatia, 24–28 August 2015; pp. 606–610. [Google Scholar]
- Bouslimi, D.; Coatrieux, G.; Cozic, M.; Roux, C. Data hiding in encrypted images based on predefined watermark embedding before encryption process. Signal Process. Image Commun. 2016, 47, 263–270. [Google Scholar] [CrossRef]
- Yan, X.; Wang, S.; Abd El-Latif, A.A.; Niu, X. Visual secret sharing based on random grids with abilities of AND and XOR lossless recovery. Multimed. Tools Appl. 2015, 74, 3231–3252. [Google Scholar] [CrossRef]
- Abd El-Latif, A.A.; Yan, X.; Li, L.; Wang, N.; Peng, J.-L.; Niu, X. A new meaningful secret sharing scheme based on random grids, error diffusion and chaotic encryption. Opt. Laser Technol. 2013, 54, 389–400. [Google Scholar] [CrossRef]
- Amin, M.; Abd El-Latif, A.A. Efficient modified RC5 based on chaos adapted to image encryption. J. Electron. Imaging 2010, 19, 013012. [Google Scholar] [CrossRef]
- Li, L.; Hossain, M.S.; Abd El-Latif, A.A.; Alhamid, M.F. Distortion less secret image sharing scheme for Internet of Things system. Clust. Comput. 2019, 22, 2293–2307. [Google Scholar] [CrossRef]
- Rachmawanto, E.H.; Sari, C.A.; Susanto, A.; Doheir, M. A comparative study of image cryptographic method. In Proceedings of the 2018 5th International Conference on Information Technology, Computer, and Electrical Engineering (ICITACEE), Semarang, Indonesia, 27–28 September 2018; pp. 336–341. [Google Scholar]
- Zhang, X. Reversible Data Hiding in Encrypted Image. IEEE Signal Process. Lett. 2011, 18, 255–258. [Google Scholar] [CrossRef]
- Kumar, S.; Gupta, A.; Walia, G.S. Reversible data hiding: A contemporary survey of state-of-the-art, opportunities and challenges. Appl. Intell. 2021, 52, 7373–7406. [Google Scholar] [CrossRef]
- Tang, Z.; Nie, H.; Pun, C.M.; Yao, H.; Yu, C.; Zhang, X. Color Image Reversible Data Hiding with Double-Layer Embedding. IEEE Access 2020, 8, 6915–6926. [Google Scholar] [CrossRef]
- Celik, M.U.; Sharma, G.; Tekalp, A.M.; Saber, E. Reversible Data Hiding. In Proceedings of the International Conference on Image Processing, Rochester, NY, USA, 22–25 September 2002. [Google Scholar]
- Rashmi, N.; Jyothi, K. An Improved method for reversible data hiding steganography combined with cryptography. In Proceedings of the 2018 2nd International Conference on Inventive Systems and Control (ICISC), Coimbatore, India, 19–20 January 2018; pp. 81–84. [Google Scholar]
- Liu, L.; Chang, C.-C.; Wang, A. Reversible data hiding scheme based on histogram shifting of n-bit planes. Multimed. Tools Appl. 2015, 75, 11311–11326. [Google Scholar] [CrossRef]
- Tsai, P.; Hu, Y.C.; Yeh, H.L. Reversible image hiding scheme using predictive coding and histogram shifting. Signal Process. 2009, 89, 1129–1143. [Google Scholar] [CrossRef]
- Kuo, W.C.; Jiang, D.J.; Huang, Y.C. A Reversible Data Hiding Scheme Based on Block Division. In Proceedings of the 2008 Congress on Image and Signal Processing, Sanya, China, 27–30 May 2008; pp. 365–369. [Google Scholar]
- Di, F.; Huang, F.; Zhang, M.; Liu, J.; Yang, X. Reversible data hiding in encrypted images with high capacity by bitplane operations and adaptive embedding. Multimed. Tools Appl. 2017, 77, 20917–20935. [Google Scholar] [CrossRef]
- Su, W.; Wang, X.; Li, F.; Shen, Y.; Pei, Q. Reversible Data Hiding using the dynamic block-partition strategy and pixel-vlaue-ordering. Multimed. Tools Appl. 2019, 78, 7927–7945. [Google Scholar] [CrossRef]
- Patel, N.; Meena, S. LSB based image steganography using dynamic key cryptography. In Proceedings of the 2016 International Conference on Emerging Trends in Communication Technologies (ETCT), Dehradun, India, 18–19 November 2016; pp. 1–5. [Google Scholar]
- Cao, X.; Du, L.; Wei, X.; Meng, D.; Guo, X. High Capacity Reversible Data Hiding in Encrypted Images by Patch-Level Sparse Representation. IEEE Trans. Cybern. 2015, 46, 1132–1143. [Google Scholar] [CrossRef]
- Li, M.; Fan, H.; Ren, H.; Lu, D.; Xiao, D.; Li, Y. Meaningful Image Encryption Based on Reversible data hiding in compressive sensing domain. Secur. Commun. Netw. 2018. [Google Scholar] [CrossRef]
- Iwendi, C.; Jalil, Z.; Javed, A.R.; Reddy, T.; Kaluri, R.; Srivastava, G.; Jo, O. KeySplitWatermark: Zero Watermarking Algorithm for Software Protection Against Cyber-Attacks. IEEE Access 2020, 8, 72650–72660. [Google Scholar] [CrossRef]
- Iwendi, C.; Moqurrab, S.A.; Anjum, A.; Khan, S.; Mohan, S.; Srivastava, G. N-Sanitization: A semantic privacy-preserving framework for unstructured medical datasets. Comput. Commun. 2020, 161, 160–171. [Google Scholar] [CrossRef]
- Subramanian, N.; Elharrouss, O.; Al-Maadeed, S.; Bouridane, A. Image Steganography: A Review of the Recent Advances. IEEE Access 2021, 9, 23409–23423. [Google Scholar] [CrossRef]
- Panchikkil, S.; Manikandan, V.M.; Zhang, Y.-D. A convolutional neural network model based reversible data hiding scheme in encrypted images with block-wise Arnold transform. Optik 2022, 250, 168137. [Google Scholar] [CrossRef]
- Qu, Z.; Cheng, Z.; Liu, W.; Wang, X. A novel quantum image steganography algorithm based on exploiting modification direction. Multimed. Tools Appl. 2019, 78, 7981–8001. [Google Scholar] [CrossRef]
- Tseng, C.-C.; Chiu, Y.-H.; Chou, Y.-C. A histogram Shifting-Based Reversible Data Hiding Using Multi-pattern Strategy. In Proceedings of the 2015 Intelligent Information Hiding and multimedia Signal Processing (IIH-MSP), Adelaide, Australia, 23–25 September 2015; pp. 125–128. [Google Scholar]
- Fadhil, M.; Rachmawanto, E.H.; Sari, C.A.; Sarker, M.K.; Andono, P.N.; Rizqa, I.; Setyono, A. Secure reversible data hiding in the medical image using histogram shifting and RC4 encryption. In Proceedings of the 2019 International Seminar on Application for Technology of Information and Communication (Isemantic), Semarang, Indonesia, 21–22 September 2019; pp. 1–6. [Google Scholar]
- Liu, Z.; Guo, Q.; Xu, L.; Ahmad, M.A.; Liu, S. Double image encryption by using iterative random binary encoding in gyrator domains. Opt. Express 2010, 18, 12033–12043. [Google Scholar] [CrossRef]
- Chen, Z.; Hu, G.; Zheng, M.; Song, X.; Chen, L. Bibliometrics of machine learning research using homomorphic encryption. Mathematics 2021, 9, 2792. [Google Scholar] [CrossRef]
- Yang, W.; Xiao, L.; Huang, J.; Yang, J. Fixed-time synchronization of neural networks based on quantized intermittent control for image protection. Mathematics 2021, 9, 3086. [Google Scholar] [CrossRef]
- Liu, Z.; Chen, H.; Blondel, W.; Shen, Z.; Liu, S. Image security based on iterative random phase encoding in expanded fractional Fourier transform domains. Opt. Lasers Eng. 2018, 105, 1–5. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).