Efficient Multi-Biometric Secure-Storage Scheme Based on Deep Learning and Crypto-Mapping Techniques
Abstract
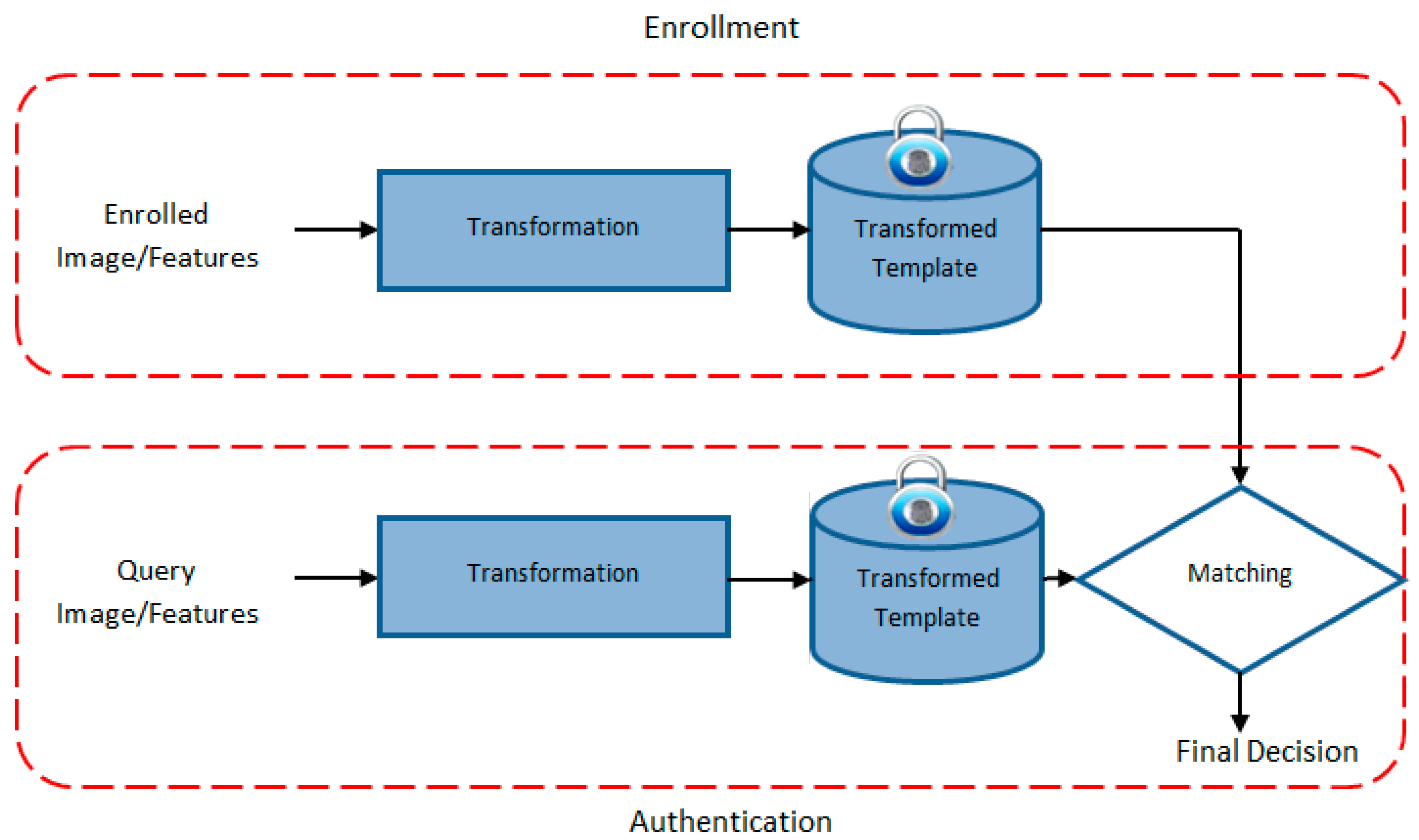
1. Introduction
- Unlinkability: Secure biometric patterns can be produced in dissimilar versions based on the biometric information (renewability), but secure patterns should not enable cross-matching (diversity) [12,13,14]. Cancelable biometrics is a promising trend in the direction of more secure biometric systems [15,16,17].
- Fusion of the input human biometrics including face, fingerprint, iris, and palm images based on deep learning.
- Generation of random kernels based on chaotic maps.
- Convolution of the generated kernels with the fused images to generate the cancelable biometrics.
- Introduction of an extensive comparative study among the proposed methods in each phase of the proposed system.
- Evaluation of the proposed system and selection of the optimal modalities based on performance metrics.
- Comparison of the proposed system with state-of-the-art works.
2. Related Work
3. Preliminaries
3.1. Integer Wavelet Transform (IWT)
3.2. Discrete Wavelet Transform (DWT)
3.3. Random Kernel Generation
3.3.1. Baker Map
- The N × N square image is split into k rectangles, each having a width ni and N components.
- In the permuted version, the elements of each rectangle are remapped into a row.
- These rectangles are dragged from left to right, starting with the top rectangles and finishing with the bottom rectangles.
- The scan begins at the lowest-left corner and progresses upward in each rectangle.
3.3.2. The Modified Logistic Map
- Analysis of Modified Logistic Map
- Bifurcations
- Lyapunov exponents
- When r [0, 5.2], the points are focused on various values that cannot be used in the image cryptosystem.
4. Proposed Cancelable Biometric Recognition Framework
Deep Fusion Process
5. Simulation Results
5.1. The Proposed Recognition System in the Absence of Noise
5.1.1. The Proposed Recognition System Using Baker Map
5.1.2. The Proposed Recognition System Using Modified Logistic Map
5.2. The Proposed Recognition System in the Existence of Noise
5.2.1. The Proposed Recognition System Using the Baker Map in the Existence of Noise
5.2.2. The Proposed Recognition System Using a Modified Logistic Map in the Existence of Noise
6. Conclusions and Future Work
- Studying the realization of the proposed systems.
- Investigation of other non-invertible transforms for cancelable template generation.
- Extension of the suggested systems in this paper for other biometrics.
- Exploitation of deep learning concepts for cancelable biometric systems.
- Utilization of fusion techniques for multi-biometric security.
- Investigation of the presented techniques for remote-access systems.
Author Contributions
Funding
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| Abbreviation | Full form |
| IWT | Integer Wavelet Transform |
| DWT | Discrete Wavelet Transform |
| IAFIS | Integrated Automatic Fingerprint Identification Service |
| FVC | Fingerprint Verification Competition |
| EER | Equal Error Rate |
| AUC-ROC | Area Under Curve–Receiver Operating Characteristic Curve |
| PFD | Probability of False Distribution |
| PTD | Probability of True Distribution |
| PIN | Personal Identification |
| FAR | False Acceptance Rate |
| MVD | Minutiae Vicinity Decomposition |
| RGHE | Randomized Graph-based Hamming Embedding |
| DFT | Discrete Fourier Transformation |
| MCC | Minutiae Cylinder Code |
| GAR | Genuine Accept Rate |
| RP | Random Projection |
| PR-NNLS | Permutated Randomized Non-Negative Least Square |
References
- Sinha, G.R.; Oo, P.S. Introduction to Biometrics and Special Emphasis on Myanmar Sign Language Recognition. In Advances in Biometrics; Springer: Cham, Switzerland, 2019; pp. 1–23. [Google Scholar]
- Li, Y.; Zhao, H.; Cao, Z.; Liu, E.; Pang, L. Compact and Cancelable Fingerprint Binary Codes Generation via One Permutation Hashing. IEEE Signal Process. Lett. 2021, 28, 738–742. [Google Scholar] [CrossRef]
- Shen, W.; Tan, T. Based on Personal Identification-Automated Biometrics. Sci. J. Biome. Biost. 2018, 1, 001–002. [Google Scholar] [CrossRef]
- Guesmi, R.; Farah, M.A.; Kachouri, A.; Samet, M. A novel chaos-based image encryption using DNA sequence operation and Secure Hash Algorithm SHA-2. Nonlinear Dyn. 2016, 83, 1123–1136. [Google Scholar] [CrossRef]
- Pagnin, E.; Mitrokotsa, A. Privacy-preserving biometric authentication: Challenges and directions. Secur. Commun. Netw. 2017, 2017, 1–9. [Google Scholar] [CrossRef]
- Jayapal, R.; Govindan, P. Biometric encryption system for increased security. In Proceedings of the 2016 IEEE International Carnahan Conference on Security Technology (ICCST), Orlando, FL, USA, 24–27 October 2016; pp. 1–3. [Google Scholar]
- Nandakumar, K.; Jain, A.K. Biometric template protection: Bridging the performance gap between theory and practice. IEEE Signal Process. Mag. 2015, 32, 88–100. [Google Scholar] [CrossRef]
- Dwivedi, R.; Dey, S.; Singh, R.; Prasad, A. A privacy-preserving cancelable iris template generation scheme using decimal encoding and look-up table mapping. Comput. Secur. 2017, 65, 373–386. [Google Scholar] [CrossRef]
- Gomez-Barrero, M.; Galbally, J.; Rathgeb, C.; Busch, C. General framework to evaluate unlinkability in biometric template protection systems. IEEE Trans. Inf. Secur. 2017, 13, 1406–1420. [Google Scholar] [CrossRef]
- Boujnah, S.; Jaballah, S.; Khalifa, A.B.; Ammari, M.L. Person’s Identification with Partial Fingerprint Based on a Redefinition of Minutiae Features. In Proceedings of the 2018 IEEE/ACS 15th International Conference on Computer Systems and Applications (AICCSA), Aqaba, Jordan, 28 October–1 November 2018; pp. 1–5. [Google Scholar]
- Bashir, A.; Tabassum, M.; Naeem, N. Biometric Image Enhancement, Feature Extraction, and Recognition Comprising FFT and Gabor Filtering. In Science and Information Conference; Springer: Cham, Switzerland, 2018; pp. 581–591. [Google Scholar]
- Patel, V.M.; Ratha, N.K.; Chellappa, R. Cancelable biometrics: A review. IEEE Signal Process. Mag. 2015, 32, 54–65. [Google Scholar] [CrossRef]
- Kaur, H.; Khanna, P. Non-invertible Biometric Encryption to Generate Cancelable Biometric Templates. In Proceedings of the World Congress on Engineering and Computer Science, San Francisco, CA, USA, 25–27 October 2017; Volume 1, pp. 1–4. [Google Scholar]
- Wang, H.; Dong, X.; Jin, Z.; Teoh, A.B.; Tistarelli, M. Interpretable security analysis of cancellable biometrics using constrained-optimized similarity-based attack. In Proceedings of the IEEE/CVF Winter Conference on Applications of Computer Vision WACV (Workshops), Waikoloa, HI, USA, 4–8 January 2022; pp. 70–77. [Google Scholar]
- Hashad, F.G.; Zahran, O.; El-Rabaie, E.S.; Elashry, I.F.; Abd El-Samie, F.E. Fusion-based encryption scheme for cancelable fingerprint recognition. Multimed. Tools Appl. 2019, 78, 27351–27381. [Google Scholar] [CrossRef]
- Priesnitz, J.; Rathgeb, C.; Buchmann, N.; Busch, C.; Margraf, M. An overview of touchless 2D fingerprints recognition. EURASIP J. Image Video Process. 2021, 2021, 1–28. [Google Scholar] [CrossRef]
- Asthana, R.; Walia, G.S.; Gupta, A. Random area-perimeter method for generation of unimodal and multimodal cancelable biometric templates. Appl. Intell. 2021, 4, 7281–7297. [Google Scholar] [CrossRef]
- Ouda, O.; Tsumura, N.; Nakaguchi, T. On the security of bioencoding based cancelable biometrics. IEICE TRANSACTIONS Inf. Syst. 2011, 94, 1768–1777. [Google Scholar] [CrossRef]
- Ross, A.; Othman, A. Visual cryptography for biometric privacy. IEEE Trans. Inf. Secur. 2010, 6, 70–81. [Google Scholar] [CrossRef]
- Algarni, A.D.; El Banby, G.; Ismail, S.; El-Shafai, W.; El-Samie, F.E.; FSoliman, N. Discrete Transforms and Matrix Rotation Based Cancelable Face and Fingerprint Recognition for Biometric Security Applications. Entropy 2020, 22, 1361. [Google Scholar] [CrossRef]
- Wang, S.; Hu, J. A blind system identification approach to cancelable fingerprint templates. Pattern Recognit. 2016, 54, 14–22. [Google Scholar] [CrossRef]
- Wei-Chao, L.; Hong-Tao, G. Occluded fingerprint recognition algorithm based on multi association features match. J. Multimed. 2014, 9, 910. [Google Scholar]
- Wang, S.; Deng, G.; Hu, J. A partial Hadamard transform approach to the design of cancelable fingerprint templates containing binary biometric representations. Pattern Recognit. 2017, 61, 447–458. [Google Scholar] [CrossRef]
- Yang, W.; Hu, J.; Wang, S.; Wu, Q. Biometrics based privacy-preserving authentication and mobile template protection. Wirel. Commun. Mob. Comput. 2018, 2018, 7107295. [Google Scholar] [CrossRef]
- Jin, Z.; Lim, M.H.; Teoh, A.B.; Goi, B.M. A non-invertible randomized graph-based hamming embedding for generating cancelable fingerprint template. Pattern Recognit. Lett. 2014, 42, 137–147. [Google Scholar] [CrossRef]
- Wang, S.; Yang, W.; Hu, J. Design of alignment-free cancelable fingerprint templates with zoned minutia pairs. Pattern Recognit. 2017, 66, 295–301. [Google Scholar] [CrossRef]
- Das, P.; Karthik, K.; Garai, B.C. A robust alignment-free fingerprint hashing algorithm based on minimum distance graphs. Pattern Recognit. 2012, 45, 3373–3388. [Google Scholar] [CrossRef]
- Yang, W.; Wang, S.; Hu, J.; Zheng, G.; Valli, C. A fingerprint and finger-vein-based cancelable multi-biometric system. Pattern Recognit. 2018, 78, 242–251. [Google Scholar] [CrossRef]
- Lacharme, P.; Plateaux, A. PIN-based cancelable biometrics. Int. J. Autom. Identif. Technol. (IJAIT) 2011, 3, 75–79. [Google Scholar]
- Liu, E.; Zhao, Q. Encrypted domain matching of fingerprint minutia cylinder-code (MCC) with l1 minimization. Neurocomputing 2017, 259, 3–13. [Google Scholar] [CrossRef]
- Karthi, G.; Azhilarasan, M. Hybrid Multimodal Template Protection Technique Using Fuzzy Extractor and Random Projection. IJRCCT 2013, 2, 381–386. [Google Scholar]
- Kaur, H.; Khanna, P. Random distance method for generating unimodal and multimodal cancelable biometric features. IEEE Trans. Inf. Secur. 2018, 14, 709–719. [Google Scholar] [CrossRef]
- Kho, J.B.; Kim, J.; Kim, I.J.; Teoh, A.B. Cancelable fingerprint template design with randomized non-negative least squares. Pattern Recognit. 2019, 91, 245–260. [Google Scholar] [CrossRef]
- Trivedi, A.K.; Thounaojam, D.M.; Pal, S. Non-Invertible cancellable fingerprint template for fingerprint biometric. Comput. Secur. 2020, 90, 101690. [Google Scholar] [CrossRef]
- Shahzad, M.; Wang, S.; Deng, G.; Yang, W. Alignment-free cancelable fingerprint templates with dual protection. Pattern Recognit. 2021, 111, 107735. [Google Scholar] [CrossRef]
- Xiong, L.; Xu, Z.; Shi, Y.Q. An integer wavelet transform-based scheme for reversible data hiding in encrypted images. Multidimens. Syst. Signal Process. 2018, 29, 1191–1202. [Google Scholar] [CrossRef]
- Li, Y.; Wang, C.; Chen, H. A hyper-chaos-based image encryption algorithm using pixel-level permutation and bit-level permutation. Opt. Lasers Eng. 2017, 90, 238–246. [Google Scholar] [CrossRef]
- Bhairannawar, S.S.; Sarkar, S.; Raja, K.B.; Venugopal, K.R. Implementation of fingerprint-based biometric system using optimized 5/3 DWT architecture and modified CORDIC-based FFT. Circuits Syst. Signal Process. 2018, 37, 342–366. [Google Scholar] [CrossRef]
- Wang, Y.; Liu, Z.; Ma, J.; He, H. A pseudorandom number generator based on a piecewise logistic map. Nonlinear Dyn. 2016, 83, 2373–2391. [Google Scholar] [CrossRef]
- Han, C. An image encryption algorithm based on a modified logistic chaotic map. Optik 2019, 181, 779–785. [Google Scholar] [CrossRef]
- Abd Al Rahim, M.; El-Shafai, W.; El-Rabaie, E.S.; Zahran, O.; El-Samie, A.; Fathi, E. Comb Filter Approach for Cancelable Face and Fingerprints Recognition. Menoufia J. Electron. Eng. Res. 2019, 28, 89–94. [Google Scholar] [CrossRef]
- Srinivasan, A.; Battacharjee, P.; Sanyal, G. Brain MR image analysis using discrete wavelet transform with fractal feature analysis. In Proceedings of the 2018 Second International Conference on Electronics, Communication and Aerospace Technology (ICECA), Coimbatore, India, 29–31 March 2018; pp. 1660–1664. [Google Scholar]
- Liu, W.; Sun, K.; Zhu, C. A fast image encryption algorithm based on chaotic map. Opt. Lasers Eng. 2016, 84, 26–36. [Google Scholar] [CrossRef]
- Awudong, B.; Li, G. Research on image encryption technology based on the multi chaotic mapping. In Proceedings of the 2017 international conference on smart city and systems engineering (ICSCSE), Changsha, China, 11–12 November 2017; pp. 127–131. [Google Scholar]
- Gawande, U.; Hajari, K.O.; Golhar, Y.G. Novel Cryptographic Algorithm Based Fusion of Multimodal Biometrics Authentication System. In Proceedings of the International Conference on Computing and Communication Technologies, IEEE, Hyderabad, India, 11–13 December 2014; pp. 1–6. [Google Scholar]
- Ibrahim, S.; Egila, M.G.; Shawky, H.; Elsaid, M.K.; El-Shafai, W.; Abd El-Samie, F.E. Cancelable face and fingerprint recognition based on the 3D jigsaw transform and optical encryption. Multimed. Tools Appl. 2020, 79, 14053–14078. [Google Scholar]
- Al-Qassas, R.S.; Qasaimeh, M.; Al-Nouri, H. A fingerprint featured data encryption algorithm. In Proceedings of the 2016 7th International Conference on Information and Communication Systems (ICICS), Irbid, Jordan, 5–7 April 2016; pp. 227–232. [Google Scholar]



























| Authors–Year | Methodology | Performance |
|---|---|---|
| Wei-Chao et al. (2014) | This technique uses a Fourier-like transform for all minutiae within the same local zone, and segments the fingerprint pattern into localized zones. | EER ranges from 0.19% to 9%. |
| Wang et al. (2017) | In this system, the Hadamard transform is used to apply the binary design of the fingerprint minutiae in the system. | Various databases have been used and EERs ranging from 1% up to 5% have been obtained. |
| Jin et al. (2014) | In this approach, RGHE has been combined with a minutiae classifier called MVD to construct a collection of arbitrary projections in addition to the arbitrary geometrical invariant features. | Tests have been performed on the FVC2002DB1 and DB2 datasets, achieving EERs of 4.36% and 1.77%. On FVC2004 DB1 and DB2 datasets, EER values of 24.71% and 21.825% have been achieved, respectively. |
| Wang et al. (2017) | A constrained form of circular convolution has been used. To begin, single points are selected to capture fingerprint patterns. Then, by multiplying the DFT of two series, truncated convolution is applied. | The experiments were performed on the FVC2002 DB1, DB2, and DB3 databases achieving EERs of 2%, 3%, and 6.12%, respectively. |
| Das et al. (2012) | As a feature set, an alignment-free fingerprint hashing approach was created based on a minimum distance graph of the inter-minutiae minimum distance vectors. | The experiments were performed on the FVC2002-DB1a and DB2a datasets achieving an EER of 2.27%. |
| Yang et al. (2018) | Two arrangements have been realized, namely local arrangement and distant arrangement at the characteristic level. | Binary-valued characteristics have been produced. They are subsequently protected by an arbitrary-projection-based cancelable biometric recognition system. |
| Lacharme and Plateaux (2011) | A PIN-based cancelable biometric system for fingerprint patterns has been presented. A biometric authentication system has been realized. It uses a secret PIN code or a variety of passwords that are only known by the user. The minutiae are extracted using Gabor filters. | In the simulation tests, the FAR is not null and is sometimes high and EER is around 20%. |
| Liu and Zhao (2017) | L1-minimization was utilized to secure and save fingerprint templates in encrypted form. The user is authenticated, when the query fingerprint matches a stored fingerprint pattern. The MCC has been utilized. | The system achieved 91.4%, 84.0% and 65.6% Genuine Accept Rate (GAR) with FAR = 0 on FVC2002DB1 and DB2 and FVC2004 DB1, respectively. |
| Karthi and Azhilarasan (2013) | Both the FE technique for key generation and the salting technique for feature transformation have been used. | Instead of keeping the key, a user-specific key is produced from the person’s biometric characteristics during the authentication procedure. As a result, this improves the privacy of users. |
| Kaur and Khanna (2018) | The system is based on blind cancelable fingerprint recognition. | The results were obtained on FVC2002 DB1, DB2, and DB3 databases, achieving acceptable results. |
| Kho et al. (2019) | A designed algorithm employing randomized non-negative least squares has been presented. The authors created a unique PR-NNLS descriptor for non-invertible transformations, but instead of using it on the minutiae descriptor, it has been used on the PLS descriptor dictionary | The descriptor has been implemented on the PLS descriptor dictionary to keep the accuracy high. |
| Trivedi et al. (2020) | A non-invertible technique based on the data from the Delaunay triangulation of minutiae points has been introduced. | The scheme has only been tested on a single dataset, which is insufficient for testing the accuracy. |
| Shahzad et al. (2021) | Alignment-free cancelable fingerprint templates have been created with dual protection using the partial DWT and the window-shift-XOR model. | The EER of this scheme is 0% for both FVC2002 DB1 and DB2, 1.63% for FVC2002 DB3, 7.35% for FVC2004 DB1 and 4.69% for FVC2004 DB2. |
| Dataset Name | Sensor Type | Image Size | Resolution (dpi) |
|---|---|---|---|
| FVC2002DB1 | Optical sensor | 388 × 374 | 500 |
| FVC2002DB2 | Capacitive sensor | 296 × 560 | 569 |
| FVC2002DB3 | Capacitive sensor | 300 × 300 | 500 |
| FVC2002DB4 | Synthetic | 288 × 384 | 500 |
| FVC2004DB1 | Optical | 640 × 480 | 500 |
| FVC2004DB2 | Optical sensor | 328 × 364 | 500 |
| FVC2004DB3 | Thermal sweeping sensor | 300 × 480 | 512 |
| FVC2004DB4 | SFinGe v3.0 | 288 × 384 | 500 |
| FVC2006DB1 | Electric Field sensor | 96 × 96 | 250 |
| FVC2006DB2 | Optical Sensor | 400 × 560 | 569 |
| FVC2006DB3 | Thermal sweeping Sensor | 400 × 500 | 500 |
| FVC2006DB4 | SFinGe v3.0 | 88 × 384 | 500 |
| Domain | Mean of | EER | Error Probability | Correct Detection Probability | Authentication Time (Sec) | |
|---|---|---|---|---|---|---|
| Imposter Patterns | Genuine Patterns | |||||
| Spatial domain | 0.102 | 0.864 | 0.002 | 2 % | 98% | 0.282 |
| IWT domain | 0.229 | 0.988 | 0.020 | 2.2% | 97.8% | 0.554 |
| IWT domain with different keys | 0.2280 | 0.989 | 0.026 | 1.8% | 98.2% | 0.477 |
| DWT domain | 0.230 | 0.989 | 0.002 | 1% | 99% | 0.279 |
| DWT domain with different keys | 0.128 | 0.989 | 0.001 | 0.8% | 99.2% | 0.264 |
| Domain | Mean of | EER | Error Probability | Probability of Correct Detection | Authentication Time (Sec) | |
|---|---|---|---|---|---|---|
| Imposter Patterns | Genuine Patterns | |||||
| Spatial domain | 0.102 | 0.864 | 0.012 | 1.8 % | 98.2% | 0.273 |
| IWT domain | 0.229 | 0.988 | 0.014 | 1.7% | 98.4% | 0.351 |
| IWT domain with different keys | 0.228 | 0.989 | 0.026 | 1.6% | 98.4% | 0.462 |
| DWT domain | 0.230 | 0.989 | 0.004 | 1% | 99% | 0.276 |
| DWT domain with different keys | 0.128 | 0.989 | 0.011 | 0.7% | 99.3% | 0.285 |
| Encryption Domain | Evaluation Metric | Noise Variance | |
|---|---|---|---|
| 0.01 | 0.02 | ||
| Spatial domain | EER | - | 0.011 |
| AROC | - | 0.968 | |
| IWT domain | EER | 0.455 | 0.354 |
| AROC | 0.982 | 0.869 | |
| IWT domain with different keys | EER | 0.455 | 0.354 |
| AROC | 0.977 | 0.868 | |
| DWT domain | EER | 0.455 | 0.344 |
| AROC | 0.977 | 0.869 | |
| DWT domain with different keys | EER | 0.454 | 0.354 |
| AROC | 0.977 | 0.877 | |
| Encryption Domain | Evaluation Metric | Noise Variance | |
|---|---|---|---|
| 0.01 | 0.02 | ||
| Spatial domain | EER | - | 0.054 |
| AROC | - | 0.767 | |
| IWT domain | EER | 0.345 | 0.354 |
| AROC | 0.883 | 0.773 | |
| IWT domain with different keys | EER | 0.355 | 0.366 |
| AROC | 0.988 | 0.8284 | |
| DWT domain | EER | 0.303 | 0.365 |
| AROC | 0.928 | 0.869 | |
| DWT domain with different keys | EER | 0.201 | 0.387 |
| AROC | 0.987 | 0.986 | |
| System | EER (%) | |||||||||
|---|---|---|---|---|---|---|---|---|---|---|
| FVC2002 | FVC2004 | FVC2006 | ||||||||
| DB1 | DB2 | DB3 | DB4 | DB1 | DB2 | DB3 | DB4 | DB1 | DB2 | |
| Wang et al., 2017 | 1 | 2 | 5.2 | - | - | - | - | - | - | - |
| Jin et al., 2014 | 4.36 | 1.77 | - | - | 24.71 | 21.82 | - | - | - | - |
| Wang et al., 2017 | 2 | 3 | 6.12 | - | - | - | - | - | - | - |
| Das et al., 2012 | 2.27 | 3.97 | - | - | - | - | - | - | - | - |
| Kaur et al., 2018 | - | 1.6 | - | - | - | 12.7 | - | - | - | - |
| Shahzad et al., 2021 | 0 | 0 | 1.63 | - | 7.35 | 4.69 | - | - | - | - |
| Proposed system using Baker map | 0.001 | 0.4 | 1 | 0.6 | 1 | 0.8 | 0 | 0.4 | 0.34 | 0.47 |
| Proposed system using modified logistic map | 0.004 | 0.36 | 1.38 | 0.45 | 1 | 0.8 | 0.3 | 0.2 | 0.34 | 0.77 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sedik, A.; El-Latif, A.A.A.; Wani, M.A.; El-Samie, F.E.A.; Bauomy, N.A.-S.; Hashad, F.G. Efficient Multi-Biometric Secure-Storage Scheme Based on Deep Learning and Crypto-Mapping Techniques. Mathematics 2023, 11, 703. https://doi.org/10.3390/math11030703
Sedik A, El-Latif AAA, Wani MA, El-Samie FEA, Bauomy NA-S, Hashad FG. Efficient Multi-Biometric Secure-Storage Scheme Based on Deep Learning and Crypto-Mapping Techniques. Mathematics. 2023; 11(3):703. https://doi.org/10.3390/math11030703
Chicago/Turabian StyleSedik, Ahmed, Ahmed A. Abd El-Latif, Mudasir Ahmad Wani, Fathi E. Abd El-Samie, Nariman Abdel-Salam Bauomy, and Fatma G. Hashad. 2023. "Efficient Multi-Biometric Secure-Storage Scheme Based on Deep Learning and Crypto-Mapping Techniques" Mathematics 11, no. 3: 703. https://doi.org/10.3390/math11030703
APA StyleSedik, A., El-Latif, A. A. A., Wani, M. A., El-Samie, F. E. A., Bauomy, N. A.-S., & Hashad, F. G. (2023). Efficient Multi-Biometric Secure-Storage Scheme Based on Deep Learning and Crypto-Mapping Techniques. Mathematics, 11(3), 703. https://doi.org/10.3390/math11030703







