Meaningful Secret Image Sharing with Uniform Image Quality
Abstract
:1. Introduction
2. Preliminaries
2.1. Polynomial-Based SIS
2.2. Saliency Detection and LC Algorithm
2.3. MSIS Proposed by Cheng et al.
2.3.1. Identical Bit Allocation Strategy
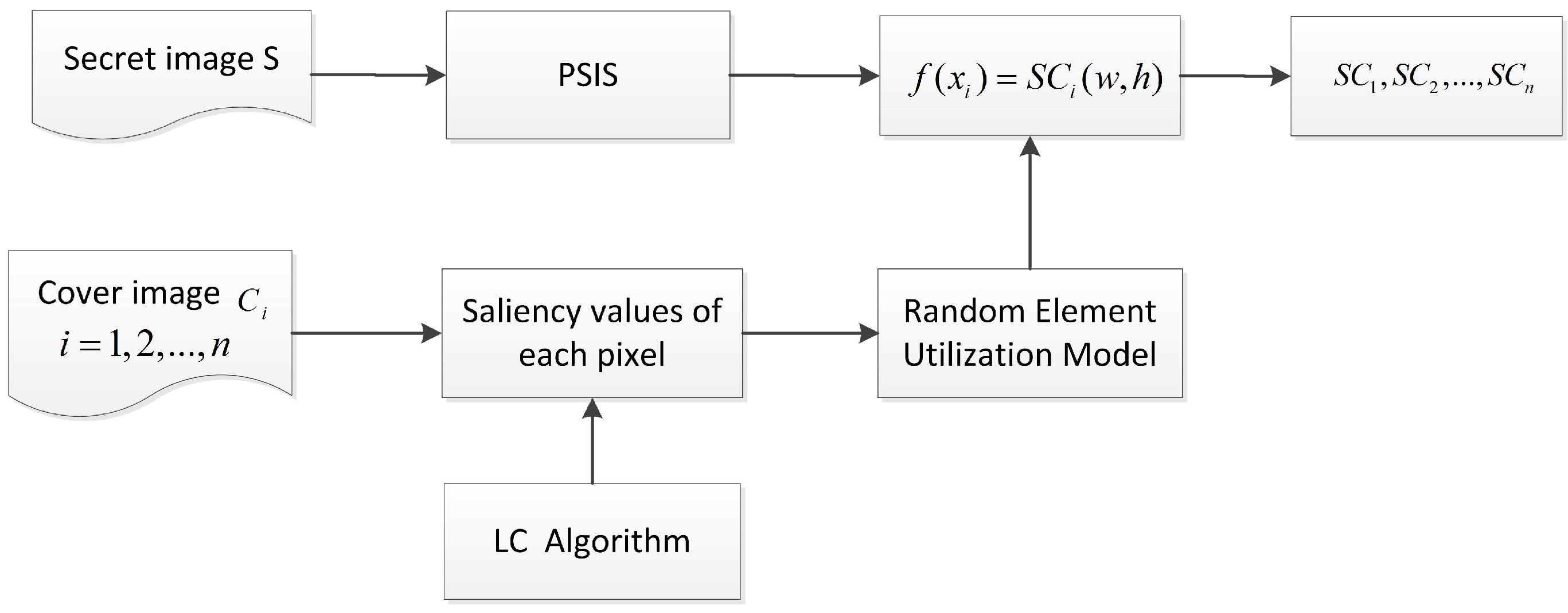
2.3.2. Cheng et al.’s MSIS Scheme
- Step 1. Calculate the saliency value of each pixel of n cover images with the LC algorithm.
- Step 2. Compare the saliency values at the same pixel position among n covers.
- Step 3. Allocate the limited identical bits to n corresponding shadow pixels according to the saliency values.
- Step 4. Take the result of Step 3 as the screening condition in PSIS to screen the generated shadow pixel values.
- Step 5. Repeat Steps 2–4 until all secret pixels are shared.
- Step 6. Output n meaningful shadows.
3. The Proposed Scheme
3.1. The Main Idea
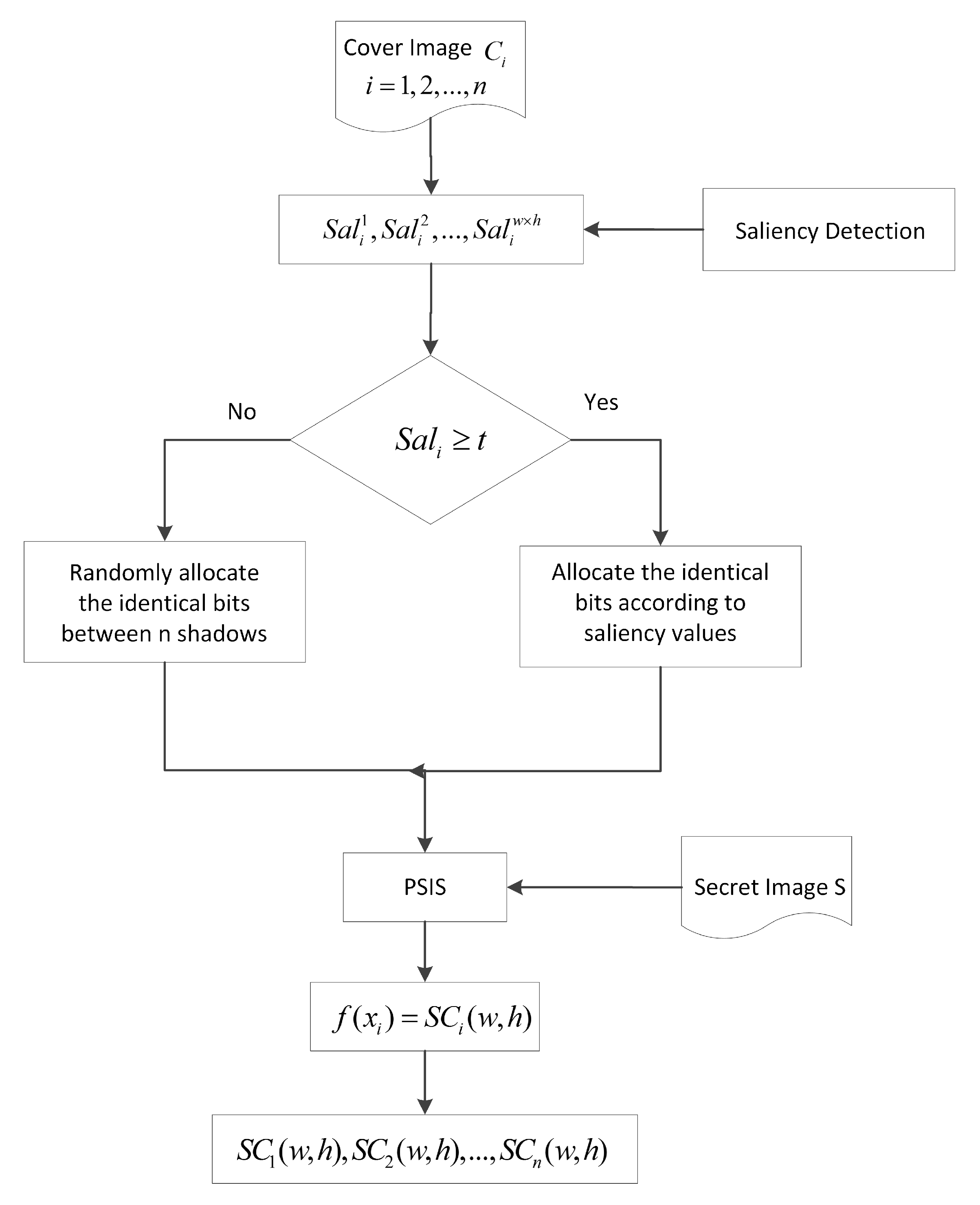
3.2. Our Scheme
| Algorithm 1: The Sharing Phase of Our Proposed Scheme |
|
- The pixel value of a grayscale image is 8 bits, and higher bits have more influence than the lower bits. If the highest bit changes, the variation in pixel value is 128, but if the lowest bit changes, the variation in pixel value is 1. Therefore, the two images are more similar when we keep more higher bits identical between the corresponding pixels in the cover image and the secret image.
- In the sharing phase, the sum of the identical bits for all shadows is fixed [33], and the identical bit allocation strategy between shadows will affect the image quality.
- In Cheng’s scheme, identical bits are allocated only according to the saliency values of cover image pixels. The shadow pixels with larger saliency values obtain more identical bits. If the difference between the saliency values is slight, the identical bit allocation is still based on the saliency values. It may result in the identical bits being allocated to one cover intensively, even though its saliency values are only slightly larger than other covers. If the covers are extreme images with black and white blocks, the identical bits may be centrally allocated to one shadow, which may result in cross-interference between different shadows.
- In our proposed scheme, is calculated to judge whether a pixel is in an absolute saliency region. If , the pixel is regarded as in an absolute saliency region. Pixels in an absolute saliency region are much more important than pixels in other covers. Then, the identical bits are allocated according to the saliency values, and the pixels in absolute regions will obtain better quality.
- If , we consider that the difference between saliency values of different covers is slight, and the identical bits are allocated randomly between n shadows. This random allocation strategy effectively avoids the concentration of the identical bits in one shadow and obtains uniform shadow quality. Furthermore, our scheme eliminates the cross-interference between different shadows that exists in Cheng’s scheme when the covers are extreme images.
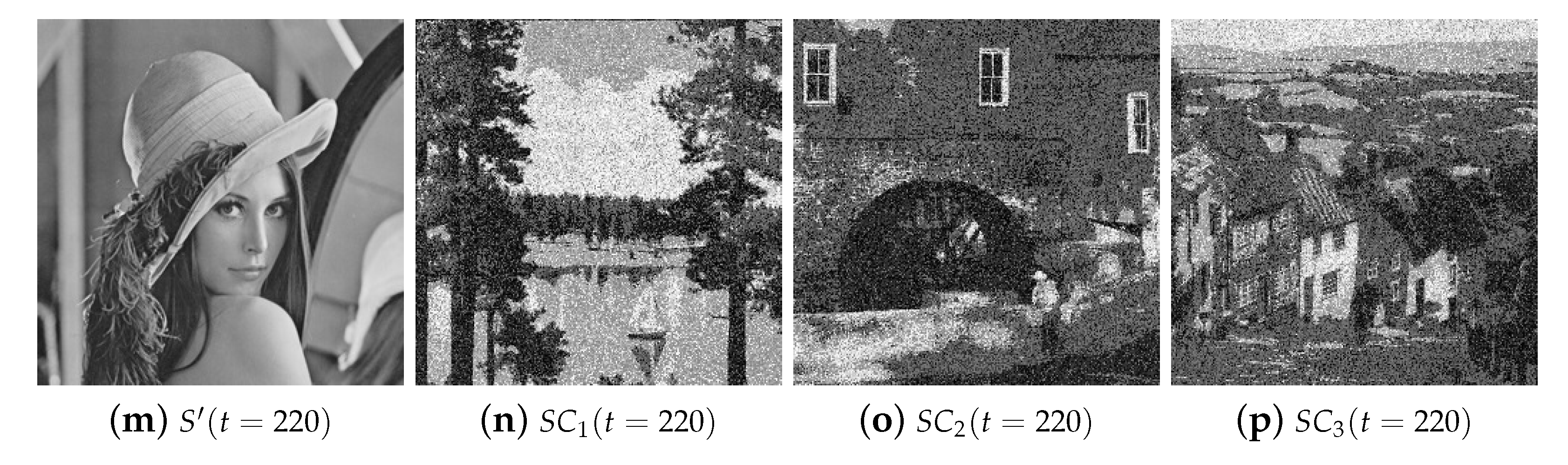
- The threshold t is used to judge whether a pixel is in an absolute saliency region. In our experiment, we demonstrate the influence of different t values on the shadow image quality and the cross-interference between shadows.
- The LC algorithm is also used to calculate the saliency values in our scheme since the LC algorithm is effective for grayscale cover images and performs well in accuracy and running time.
- PSIS is exploited to share the secret image, and the prime number P in our scheme is 257 to achieve lossless recovery. In the recovery phase, Lagrange interpolation is used to recover the secret image.
4. Experiments and Discussion
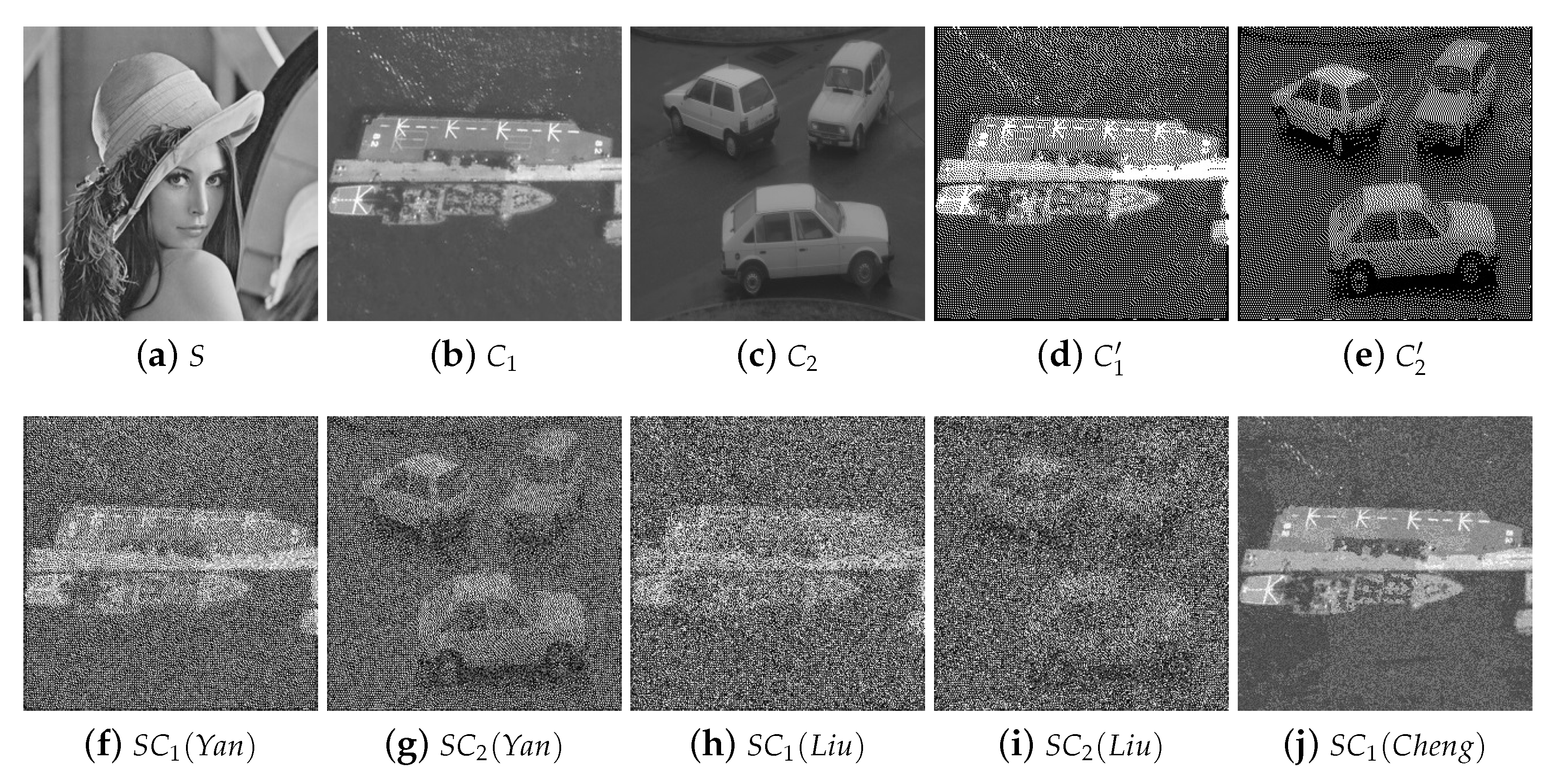
4.1. Image Illustration
4.2. Comparisons with Relative Methods
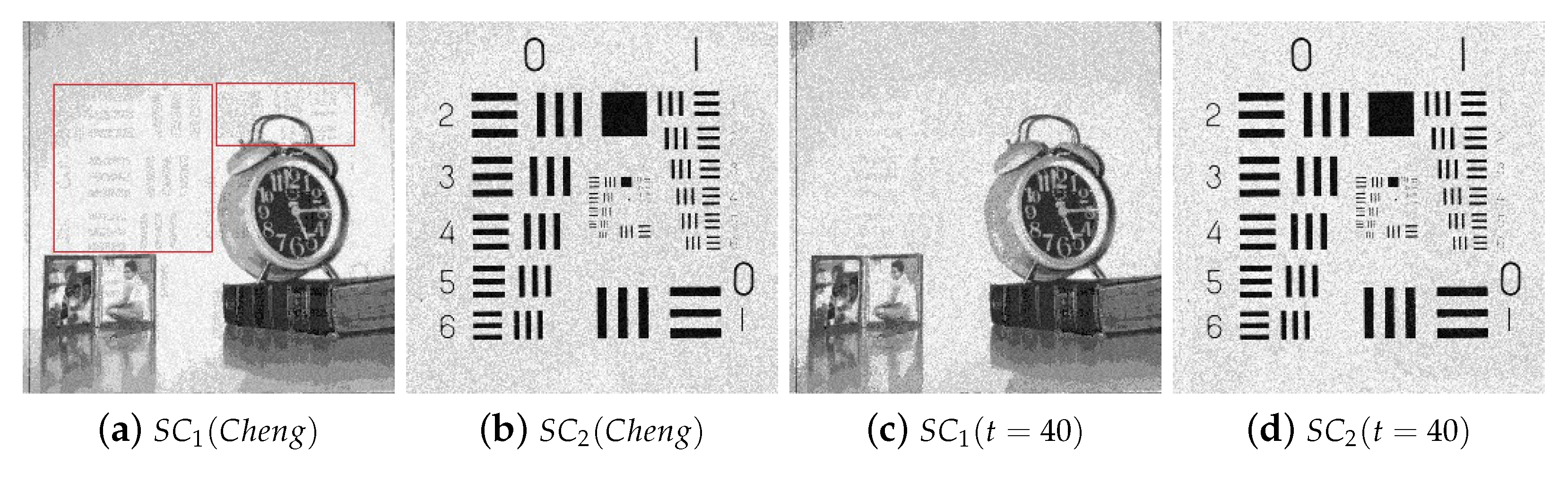
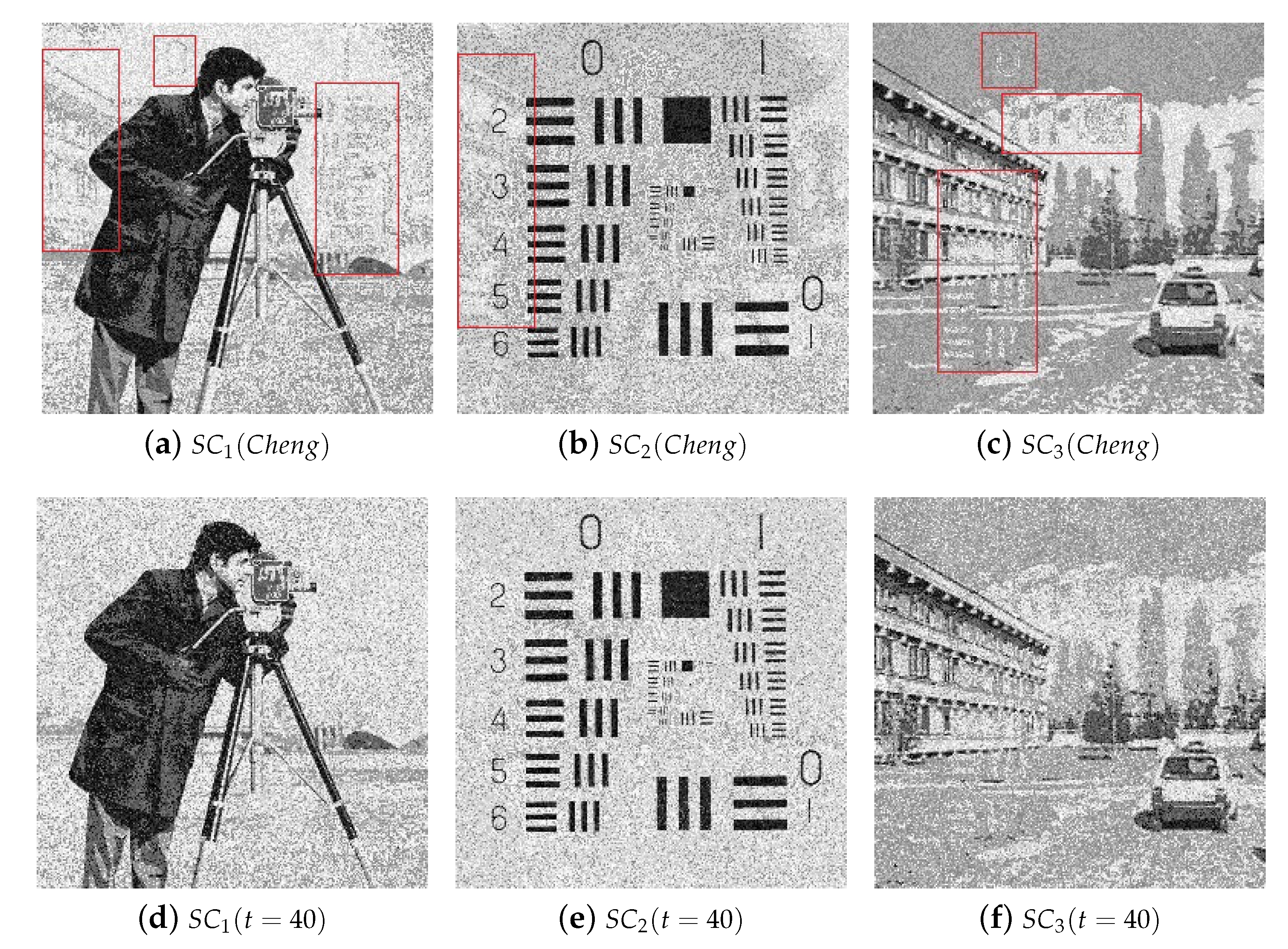
4.2.1. Illustration Comparison
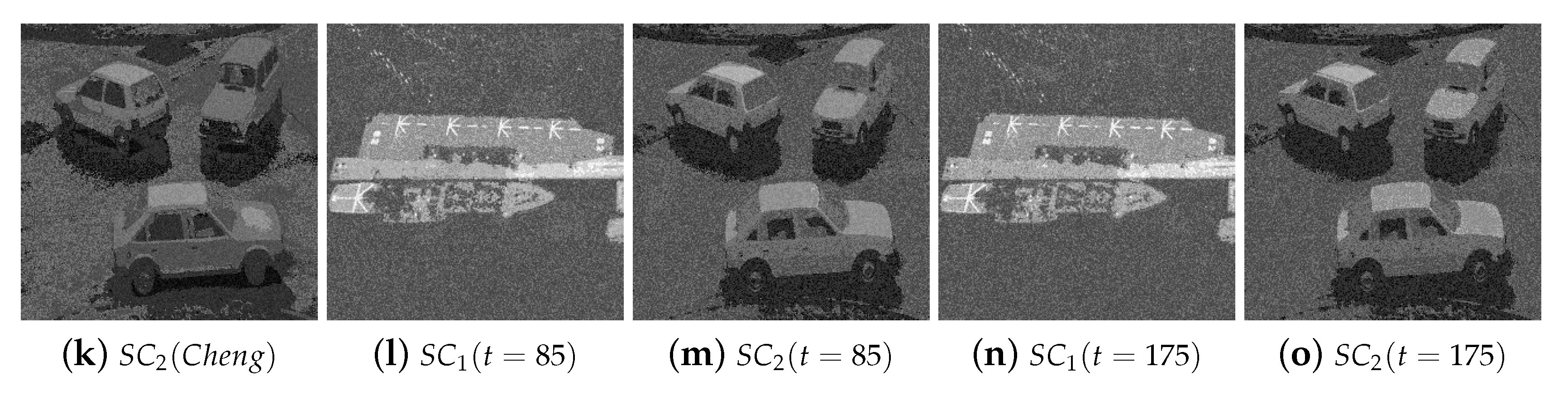
4.2.2. Cross-Interference between Different Shadows
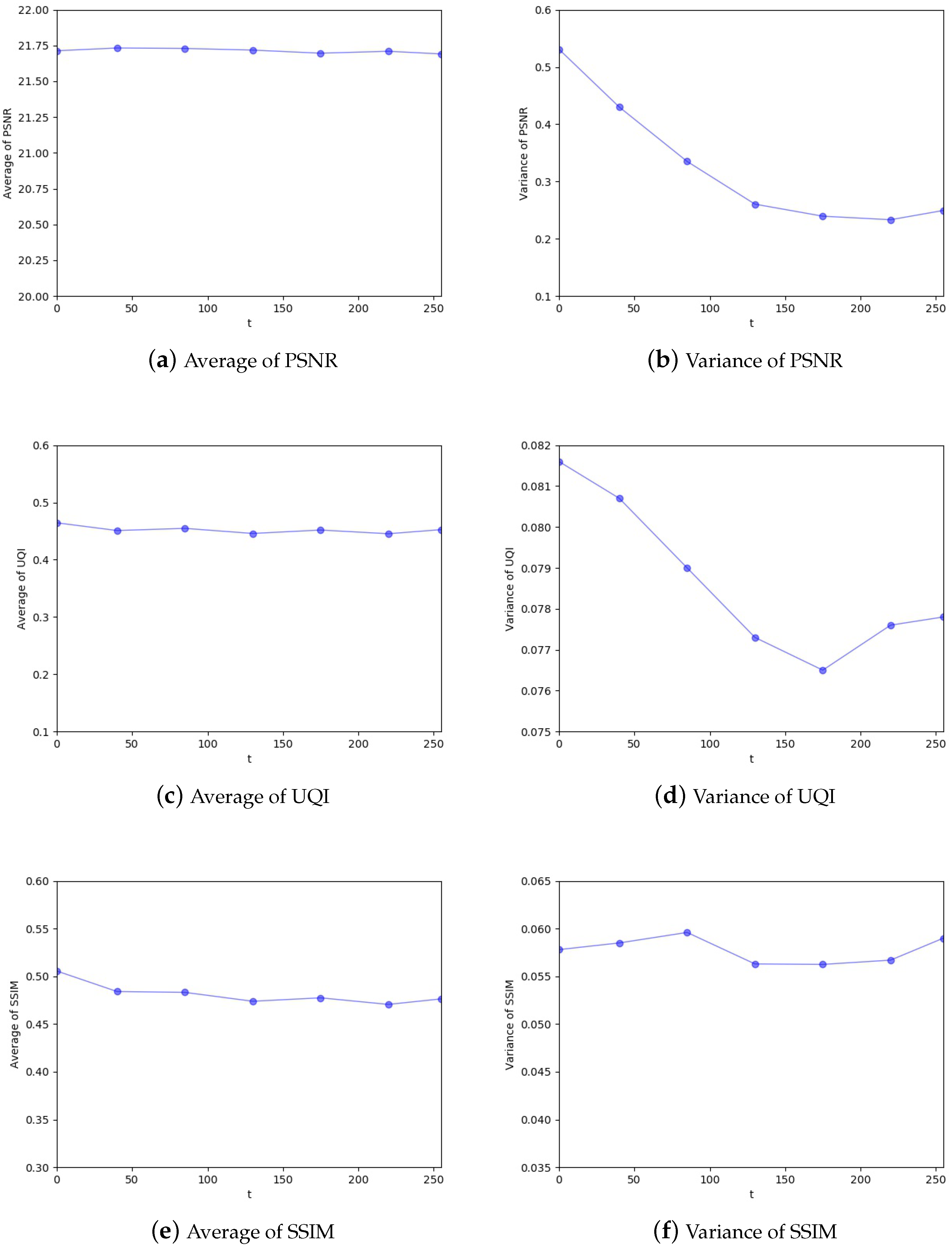
4.3. Analyses and Discussion
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Muhammad, K.; Hamza, R.; Ahmad, J.; Lloret, J.; Wang, H.; Baik, S.W. Secure surveillance framework for IoT systems using probabilistic image encryption. IEEE Trans. Ind. Inform. 2018, 14, 3679–3689. [Google Scholar] [CrossRef]
- Wang, J.; Zhang, L.Y.; Chen, J.; Hua, G.; Zhang, Y.; Xiang, Y. Compressed sensing based selective encryption with data hiding capability. IEEE Trans. Ind. Inform. 2019, 15, 6560–6571. [Google Scholar] [CrossRef]
- Zhou, H.; Chen, K.; Zhang, W.; Yao, Y.; Yu, N. Distortion design for secure adaptive 3-d mesh steganography. IEEE Trans. Multimed. 2018, 21, 1384–1398. [Google Scholar] [CrossRef]
- Shamir, A. How to share a secret. Commun. ACM 1979, 22, 612–613. [Google Scholar] [CrossRef]
- Naor, M.; Shamir, A. Visual cryptography. In Proceedings of the Workshop on the Theory and Application of of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 1994; pp. 1–12. [Google Scholar]
- Ajjipura Basavegowda, R.; Holalu Seenappa, S. Secret Code Authentication Using Enhanced Visual Cryptography. In Proceedings of the Emerging Research in Electronics, Computer Science and Technology; Sridhar, V., Sheshadri, H.S., Padma, M.C., Eds.; Springer: New Delhi, India, 2014; pp. 69–76. [Google Scholar]
- Li, Y.; Guo, L. Robust image fingerprinting via distortion-resistant sparse coding. IEEE Signal Process. Lett. 2017, 25, 140–144. [Google Scholar] [CrossRef]
- Bagherzandi, A.; Jarecki, S.; Saxena, N.; Lu, Y. Password-protected secret sharing. In Proceedings of the ACM Conference on Computer and Communications Security, Chicago, IL, USA, 17–21 October 2011; pp. 433–444. [Google Scholar]
- Jarecki, S.; Kiayias, A.; Krawczyk, H.; Xu, J. Highly-Efficient and Composable Password-Protected Secret Sharing (Or: How to Protect Your Bitcoin Wallet Online). In Proceedings of the 2016 IEEE European Symposium on Security and Privacy (EuroS&P), Saarbruecken, Germany, 21–24 March 2016; pp. 276–291. [Google Scholar] [CrossRef]
- Raman, R.K.; Varshney, L.R. Distributed storage meets secret sharing on the blockchain. In Proceedings of the 2018 Information Theory and Applications Workshop (ITA), San Diego, CA, USA, 11–16 February 2018; pp. 1–6. [Google Scholar]
- Wang, G.; Liu, F.; Yan, W.Q. Basic visual cryptography using braille. Int. J. Digit. Crime Forensics (IJDCF) 2016, 8, 85–93. [Google Scholar] [CrossRef]
- Wang, B.; Wang, W.; Zhao, P. A zero-watermark algorithm for multiple images based on visual cryptography and image fusion. J. Vis. Commun. Image Represent. 2022, 87, 103569. [Google Scholar] [CrossRef]
- Jiao, S.; Feng, J.; Gao, Y.; Lei, T.; Yuan, X. Visual cryptography in single-pixel imaging. Opt. Express 2020, 28, 7301–7313. [Google Scholar] [CrossRef]
- Wu, X.; Yang, C.N. A combination of color-black-and-white visual cryptography and polynomial based secret image sharing. J. Vis. Commun. Image Represent. 2019, 61, 74–84. [Google Scholar] [CrossRef]
- Wang, Y.; Chen, J.; Gong, Q.; Yan, X.; Sun, Y. Weighted polynomial-based secret image sharing scheme with lossless recovery. Secur. Commun. Netw. 2021, 2021, 5597592. [Google Scholar] [CrossRef]
- Xiong, L.; Han, X.; Yang, C.N. CP-PSIS: CRT and polynomial-based progressive secret image sharing. Signal Process. 2021, 185, 108064. [Google Scholar] [CrossRef]
- Jia, X.; Wang, D.; Nie, D.; Luo, X.; Sun, J.Z. A new threshold changeable secret sharing scheme based on the Chinese Remainder Theorem. Inf. Sci. 2019, 473, 13–30. [Google Scholar] [CrossRef]
- Yan, X.; Lu, Y.; Liu, L.; Liu, J.; Yang, G. Chinese remainder theorem-based two-in-one image secret sharing with three decoding options. Digit. Signal Process. 2018, 82, 80–90. [Google Scholar] [CrossRef]
- Yan, X.; Lu, Y.; Liu, L.; Wan, S.; Ding, W.; Liu, H. Chinese remainder theorem-based secret image sharing for (k, n) threshold. In Proceedings of the International Conference on Cloud Computing and Security; Springer: Berlin/Heidelberg, Germany, 2017; pp. 433–440. [Google Scholar]
- Yang, C.N.; Shih, H.W.; Wu, C.C.; Harn, L. k Out of n Region Incrementing Scheme in Visual Cryptography. IEEE Trans. Circuits Syst. Video Technol. 2011, 22, 799–810. [Google Scholar] [CrossRef]
- Gong, Q.; Wang, Y.; Yan, X.; Liu, L. Efficient and lossless polynomial-based secret image sharing for color images. IEEE Access 2019, 7, 113216–113222. [Google Scholar] [CrossRef]
- Tan, L.; Lu, Y.; Yan, X.; Liu, L.; Li, L. Weighted Secret Image Sharing for a (k, n) Threshold Based on the Chinese Remainder Theorem. IEEE Access 2019, 7, 59278–59286. [Google Scholar] [CrossRef]
- Liu, Y.X.; Yang, C.N.; Yeh, P.H. Reducing shadow size in smooth scalable secret image sharing. Secur. Commun. Netw. 2014, 7, 2237–2244. [Google Scholar] [CrossRef]
- Ateniese, G.; Blundo, C.; Santis, A.D.; Stinson, D.R. Extended capabilities for visual cryptography. Theor. Comput. Sci. 2001, 250, 143–161. [Google Scholar] [CrossRef]
- Liu, F.; Wu, C. Embedded extended visual cryptography schemes. IEEE Trans. Inf. Forensics Secur. 2011, 6, 307–322. [Google Scholar] [CrossRef] [Green Version]
- Ou, D.; Sun, W.; Wu, X. Non-expansible XOR-based visual cryptography scheme with meaningful shares. Signal Process. 2015, 108, 604–621. [Google Scholar] [CrossRef]
- Chiu, P.L.; Lee, K.H. Efficient constructions for progressive visual cryptography with meaningful shares. Signal Process. 2019, 165, 233–249. [Google Scholar] [CrossRef]
- Thien, C.C.; Lin, J.C. An image-sharing method with user-friendly shadow images. IEEE Trans. Circuits Syst. Video Technol. 2003, 13, 1161–1169. [Google Scholar] [CrossRef]
- Guo, C.; Wang, Z.H.; Chang, C.C.; Qin, C. A Secret Image Sharing Scheme with High Quality Shadows Based on Exploiting Modification Direction. J. Multimed. 2011, 6, 341–348. [Google Scholar] [CrossRef]
- Wang, Z.H.; Di, Y.F.; Li, J.; Chang, C.C.; Liu, H. Progressive secret image sharing scheme using meaningful shadows. Secur. Commun. Netw. 2016, 9, 4075–4088. [Google Scholar] [CrossRef]
- Ulutas, M.; Ulutas, G.; Nabiyev, V.V. Invertible secret image sharing for gray level and dithered cover images. J. Syst. Softw. 2013, 86, 485–500. [Google Scholar] [CrossRef]
- Wu, X.; Yang, C.N.; Yang, Y.Y. Sharing and hiding a secret image in color palette images with authentication. Multimed. Tools Appl. 2020, 79, 25657–25677. [Google Scholar] [CrossRef]
- Cheng, J.; Yan, X.; Liu, L.; Jiang, Y.; Wang, X. Meaningful Secret Image Sharing with Saliency Detection. Entropy 2022, 24, 340. [Google Scholar] [CrossRef]
- Yan, X.; Lu, Y.; Liu, L.; Song, X. Reversible image secret sharing. IEEE Trans. Inf. Forensics Secur. 2020, 15, 3848–3858. [Google Scholar] [CrossRef]
- Liu, L.; Lu, Y.; Yan, X. Polynomial-based extended secret image sharing scheme with reversible and unexpanded covers. Multimed. Tools Appl. 2019, 78, 1265–1287. [Google Scholar] [CrossRef]
- Zhai, Y.; Shah, M. Visual attention detection in video sequences using spatiotemporal cues. In Proceedings of the 14th ACM International Conference on Multimedia, Santa Barbara, CA, USA, 23–27 October 2006; pp. 815–824. [Google Scholar]
- Duncan, J.; Humphreys, G.W. Visual search and stimulus similarity. Psychol. Rev. 1989, 96, 433. [Google Scholar] [CrossRef]


Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Cheng, J.; Liu, L.; Chen, F.; Jiang, Y. Meaningful Secret Image Sharing with Uniform Image Quality. Mathematics 2022, 10, 3241. https://doi.org/10.3390/math10183241
Cheng J, Liu L, Chen F, Jiang Y. Meaningful Secret Image Sharing with Uniform Image Quality. Mathematics. 2022; 10(18):3241. https://doi.org/10.3390/math10183241
Chicago/Turabian StyleCheng, Jingwen, Lintao Liu, Feng Chen, and Yue Jiang. 2022. "Meaningful Secret Image Sharing with Uniform Image Quality" Mathematics 10, no. 18: 3241. https://doi.org/10.3390/math10183241
APA StyleCheng, J., Liu, L., Chen, F., & Jiang, Y. (2022). Meaningful Secret Image Sharing with Uniform Image Quality. Mathematics, 10(18), 3241. https://doi.org/10.3390/math10183241





