1. Introduction
Currently, with the rapid development of the internet and the wide application of intelligent devices, people are increasingly fond of sharing their lives on social media and networks [
1]. There is no doubt that images are the main way to show the state of a person’s life and their understanding of the real world [
2]. According to statistics, 136,000 photos are uploaded to Facebook every minute, which is equivalent to 195 million images per day, while this number was only 2.7 million in 2010 [
3,
4]. Photos uploaded to social platforms are only part of the volume of images taken. In June 2021, Rise Above Research, a consulting firm that provides market research for the digital imaging industry, estimated the number of global images was 1.12 trillion in 2020 and predicts that the number of global images will grow to 1.4 trillion images in 2021 [
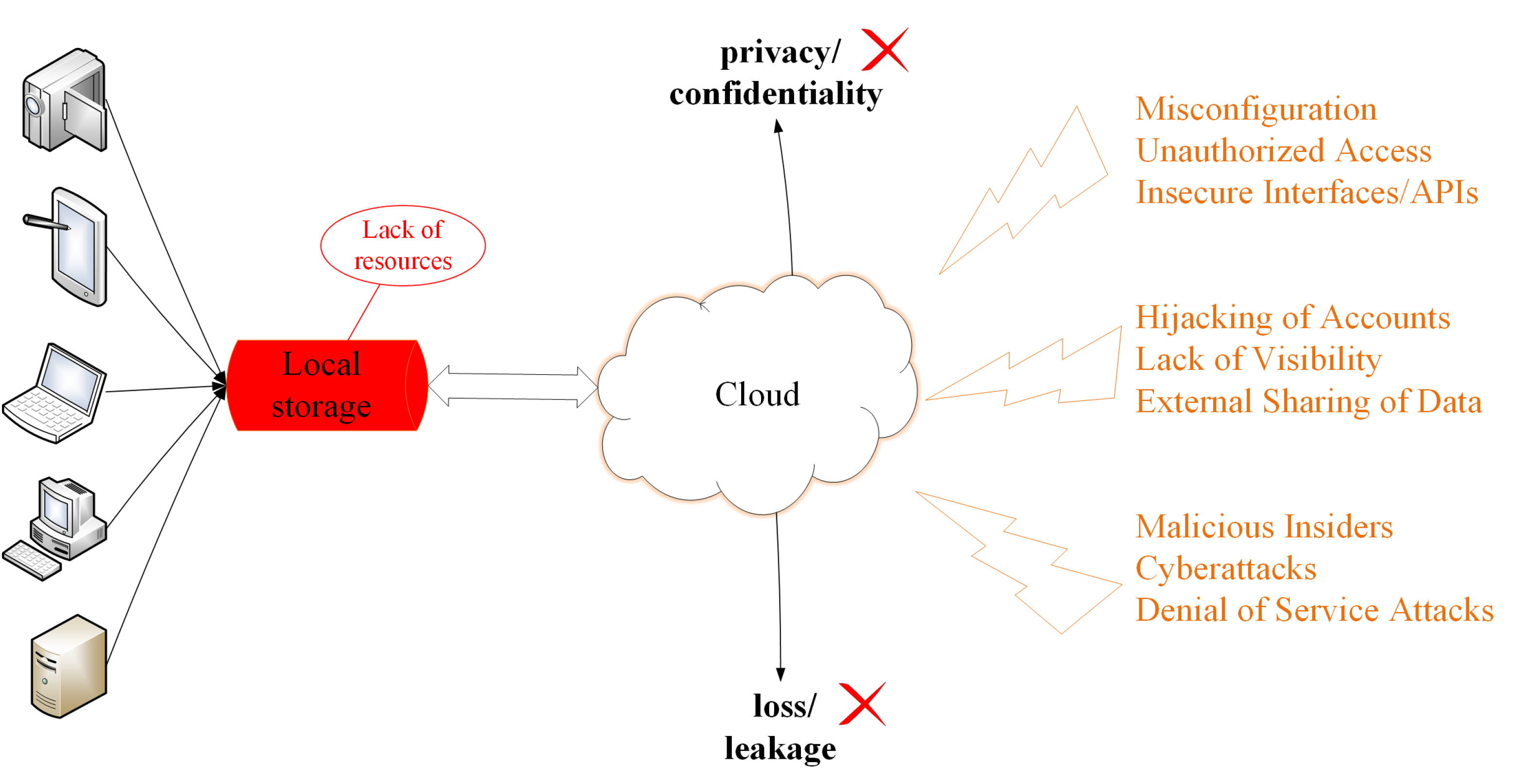
5]. Faced with such a large and growing amount of images, local storage in the traditional sense will become difficult to deal with. If these images are all stored in a local storage device, it will take up a great deal of resources and space from the user and cause inconvenience in management.
Uploading images to the cloud space for storage and management has overturned the traditional image storage and management methods and has become the current development trend [
6,
7]. Many internet companies and major mobile phone manufacturers now provide general cloud storage services, such as Dropbox, OneDrive, Google Drive, and iCloud. The development and popularity of cloud storage services make cloud storage space larger and cheaper. Therefore, more users will be attracted to use cloud storage services, and increasing numbers of images will be uploaded to the cloud space. Among the massive images, there are some high-value images containing personal privacy and trade secret information that need to be protected, which are called secret images. The large increase of secret images has forced them to be uploaded to the cloud space to alleviate the lack of local resources [
8,
9]. However, in the 2020 Cloud Security Report from Check Point [
10], nine main cloud security issues and threats were listed in 2021: misconfiguration, unauthorized access, insecure interfaces/APIs, hijacking of accounts, lack of visibility, external sharing of data, malicious insiders, cyberattacks, and denial of service attacks. Although many users have no choice but to decide to upload sensitive data and secret images to the cloud space, these threats have caused great concerns among users [
11,
12]. These concerns mainly include data loss/leakage and data privacy/confidentiality. The status of cloud storage is shown in
Figure 1.
1.1. Related Work
To protect secret images stored in cloud space, a series of works have been proposed. Information security is often assessed by CIA (confidentiality, integrity, availability) [
13,
14], which are three elements of information security. For the security of secret images, secret images cannot be uploaded directly to the cloud space but must be processed. Currently, the most common way is to encrypt [
15,
16,
17] the secret image and upload cipher images to the cloud space. Traditional image encryption algorithms with a confusion and diffusion structure are commonly used to encrypt secret images. Although these schemes can protect the confidentiality of secret images, there are still many problems after uploading encrypted images to the cloud. For example, users cannot directly browse cipher images through the cloud, so they are prohibited from organizing and managing images through visual content [
18,
19,
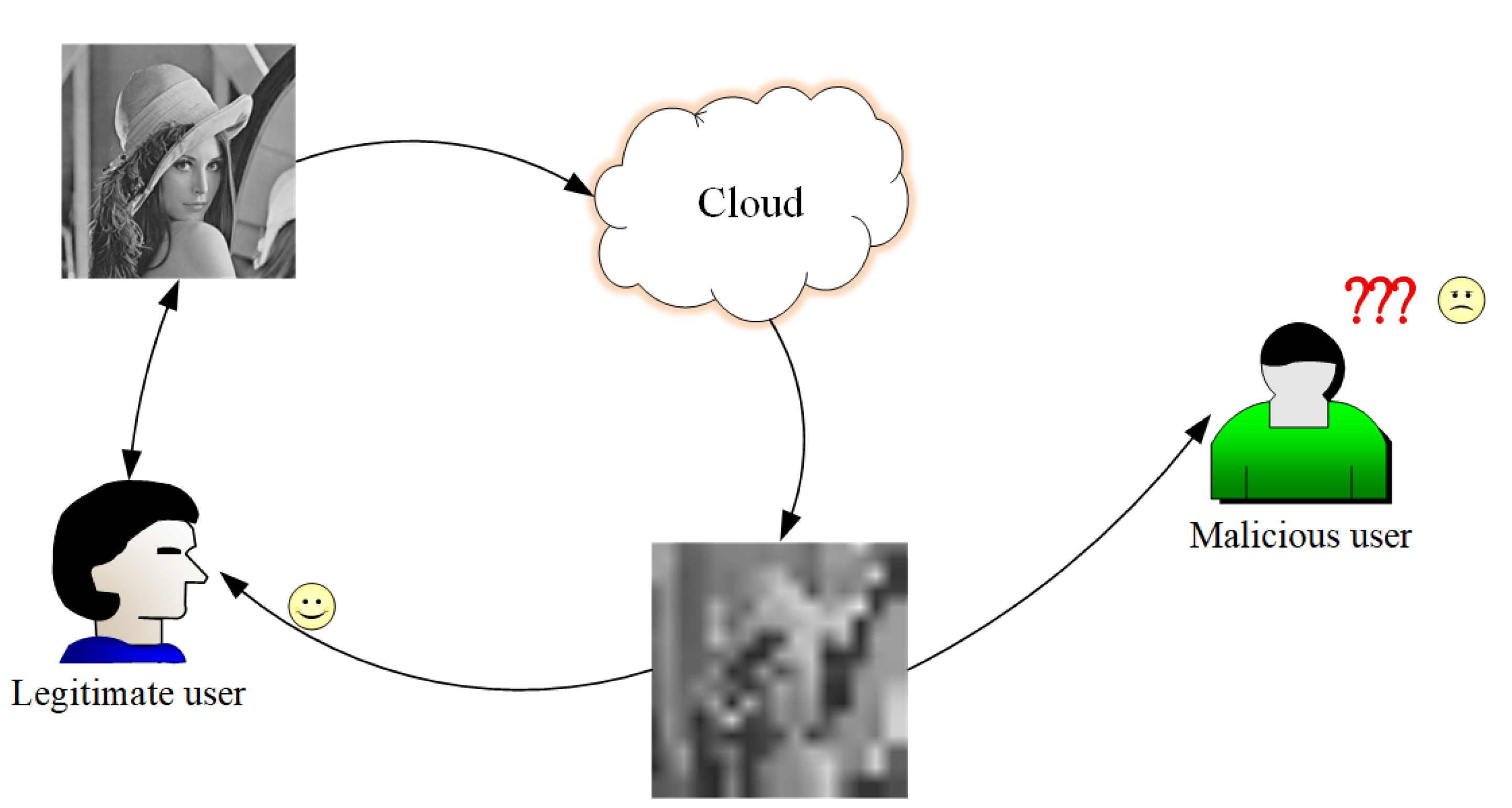
20]. Users can only understand the content of the image after downloading and decrypting the cipher image, which violates the principle of availability in cloud space. Regarding the problem of cipher images management, some scholars have combined the research results of visual memory in visual psychology to propose a concept of image encryption based on prior knowledge, that is, thumbnail-preserving encryption (TPE) [
21,
22,
23]. The basic idea of TPE is that the cipher image retains the thumbnail of the original image. Legal users with prior knowledge can combine the visual information of the cipher image with prior knowledge to infer the specific content of the image, while illegal users without prior knowledge cannot infer from the rough visual information of the cipher image, as shown in
Figure 2.
The first TPE scheme was designed by Wright et al. [
21], and then many scholars made improvements to further the recognition and organization of cipher images [
24,
25,
26]. Zhao et al. [
27] improved the original scheme [
25,
26] and further optimized the practicability and efficiency of TPE, but their scheme still did not solve the problem of image integrity. Therefore, we carried out further design and optimization.
1.2. Discussion
Organizations and individuals use the cloud to store their data and applications and trust it to be safe and reliable. However, the cloud is not perfect, and even the most reliable cloud provider will suffer data loss, which is inevitable. Cyberattacks or equipment failures are important reasons for data loss. Similarly, human error, such as simply an incorrect instruction, may lead to data loss. However, none of the above schemes can deal with data loss well, which is the main concern of users.
The traditional encryption scheme protects the privacy of secret images, but it brings about the problems of the difficult management of cipher images and data loss, leading to data unavailability. Although TPE solves the management problem of cipher images, it cannot prevent data loss and data damage, which seriously affects the integrity of data. In order to further improve the security of cloud storage and increase users’ trust in cloud storage, we adopt the idea of SS to perform encryption. The image is encrypted into multiple cipher images by secret image sharing (SIS) [
28,
29,
30] and then stored in different cloud spaces by distributed storage. SIS has the property of loss tolerance, so it can prevent data loss and data damage [
29,
31]. The traditional SIS cipher image and encrypted image are noise images [
32].
The current work cannot meet the security and management needs of images in the cloud, so we use the knowledge of secret sharing (SS) [
33,
34] and thumbnails to realize the perfect protection and convenient management of images. Proposed scheme mainly uses approximate thumbnails and control sharing models. Approximate thumbnails are mainly used to solve the usability problem of encrypted images. Controlling secret sharing is performed to ensure the integrity of the secret and change the situation that the original shared cipher image is noise, which is based on approximate thumbnail sharing. We specifically describe the contributions of the proposed scheme in the CIA of information security below.
Confidentiality: This paper uses the method of SS to encrypt the secret image to realize the protection of image privacy.
Integrity: Compared with previous schemes, our scheme has the characteristics of loss tolerance, which is critical for the complete recovery and utilization of secrets, greatly improving the security of cloud storage.
Availability: The cipher image generated by the proposed scheme is visually identifiable and achieves the management of the cipher image. Compared with meaningful SIS, our scheme greatly improves the efficiency of sharing.
The rest of the paper is organized as follows.
Section 2 introduces the basic concepts and related knowledge needed in this paper. The proposed scheme is introduced in
Section 3, including the general overview of the scheme, the design of the scheme and algorithm, and the security analysis.
Section 4 gives the experimental result and data. Finally,
Section 5 concludes this paper.
2. Preliminary
In this section, we introduced the basic definitions and preliminaries used in this paper, including secret sharing, polynomial-based SIS, and thumbnail-preserving.
2.1. Secret Sharing
SS [
33,
34] encrypts the secret information into several shares and secretly distributes them to a number of participants. At the same time, it requires that the authorized subset of participants can be combined to recover the secret information by using the shares held. Other unauthorized subsets cannot recover secret information by shares.
An SS scheme can be described as a six-tuple , where
is the finite set of secret sharing participants, and , where n is the number of participants, namely ;
is an access structure, which is composed of participant authorization subsets;
is a finite set of possible secret values, and the number of elements in the secret value space is defined as ;
is a finite set of possible shared values. Since each shared value may have a different value space, let ;
The sharing function is a probabilistic algorithm, denoted as . Among them, the secret value ; the output is n shared values, and ;
The recovery function is a deterministic algorithm, denoted as . Assuming that e participates in recovery, is the set of shared values participating in secret recovery, , and .
SS has the advantages of unconditional security, loss tolerance, and access control. Considering that SS has many advantages, the technology is widely used in the field of security, such as key management, password sharing, electronic voting, group signature authentication, and secure multi-party calculation, etc.
2.2. Polynomial-Based SIS
In 1979, Shamir proposed the polynomial-based SS. The sharing algorithm of the scheme is shown in Algorithm 1, and its recovery algorithm can be realized by Lagrangian interpolation. The core of polynomial-based SIS is
order sharing polynomial
, where the value space is a finite field
, the modulus
p is a prime power, the secret value
, and the random factors
. Since the sharing and recovery algorithms are simple and efficient and there are few public parameters, the polynomial-based SIS is widely used and is often used as the basic algorithm for security protocol design [
35,
36,
37].
| Algorithm 1 The polynomial-based SS |
Input: Output: n cipher images Step 1: Select n different non-zero elements in the finite field , denoted as , and p is a prime number). can be made public. Step 2: Randomly and independently select elements in the finite space , denoted as . Step 3: Calculate respectively, where . Step 4: The shared value is secretly sent to the corresponding participant , . |
Thien and Lin [
38] introduced SS into the image field in 2002. The difference between SIS and SS is as follows:
is the pixel value of each group in each SS process.
p is selected as 251, and the pixels above 250 are treated as 250.
Thien–Lin’s scheme shares a cipher image whose size is only of the original image, but in some cases, the cipher image will leak information about the original secret image. In order to avoid the security problem of Thien–Lin’s scheme, our paper uses the original polynomial-based SIS scheme, that is, only is embedded with a pixel. In order to avoid the loss and distortion of secret pixels, this paper chooses . However, the maximum storage pixel of an image is 256, which means that if occurs, it must be re-shared in the same way. The encryption scheme of SIS can effectively protect the privacy of secret images and can also protect against the loss of secrets. However, the cipher images generated by SIS are noise images, which is not convenient for management and use, and the efficiency is also very low. These are the factors that this article needs to improve and upgrade.
2.3. Thumbnail-Preserving Encryption
Wright et al. [
21] proposed the concept of thumbnail-preserving encryption, that is, the cipher image presents the same visual content as the low-resolution version of the original image. The algorithm is shown in Algorithm 2.
| Algorithm 2 Thumbnail-preserving encryption |
Input: Secret image of size . Output: Cipher image. Step 1: Use the passphrase to derive a secret symmetric key K using a password based key derivation function. Step 2: Color space transformation. Step 3: Divide the secret image into blocks of pixels and encrypt the pixels in each block by first permuting the order in which they appear. |
The goal of TPE is to encrypt each block such that the cipher image reveals the average pixel value in the block but nothing more. This allows an untrusted third party who does not possess the key to reconstruct an accurate
pixel thumbnail, where each block in the cipher image corresponds to a single pixel in the thumbnail. The legal owner of the image has prior knowledge of the original image’s visual characteristics, so the image owner can accurately identify and preview the image based on these low-resolution encrypted images [
39,
40].
TPE can not only protect the privacy of cloud-stored images but also can easily use today’s cloud services to achieve a satisfactory balance between image privacy and usability. It is worth noting that the existing TPE scheme cannot resist information loss, which is worth promoting.
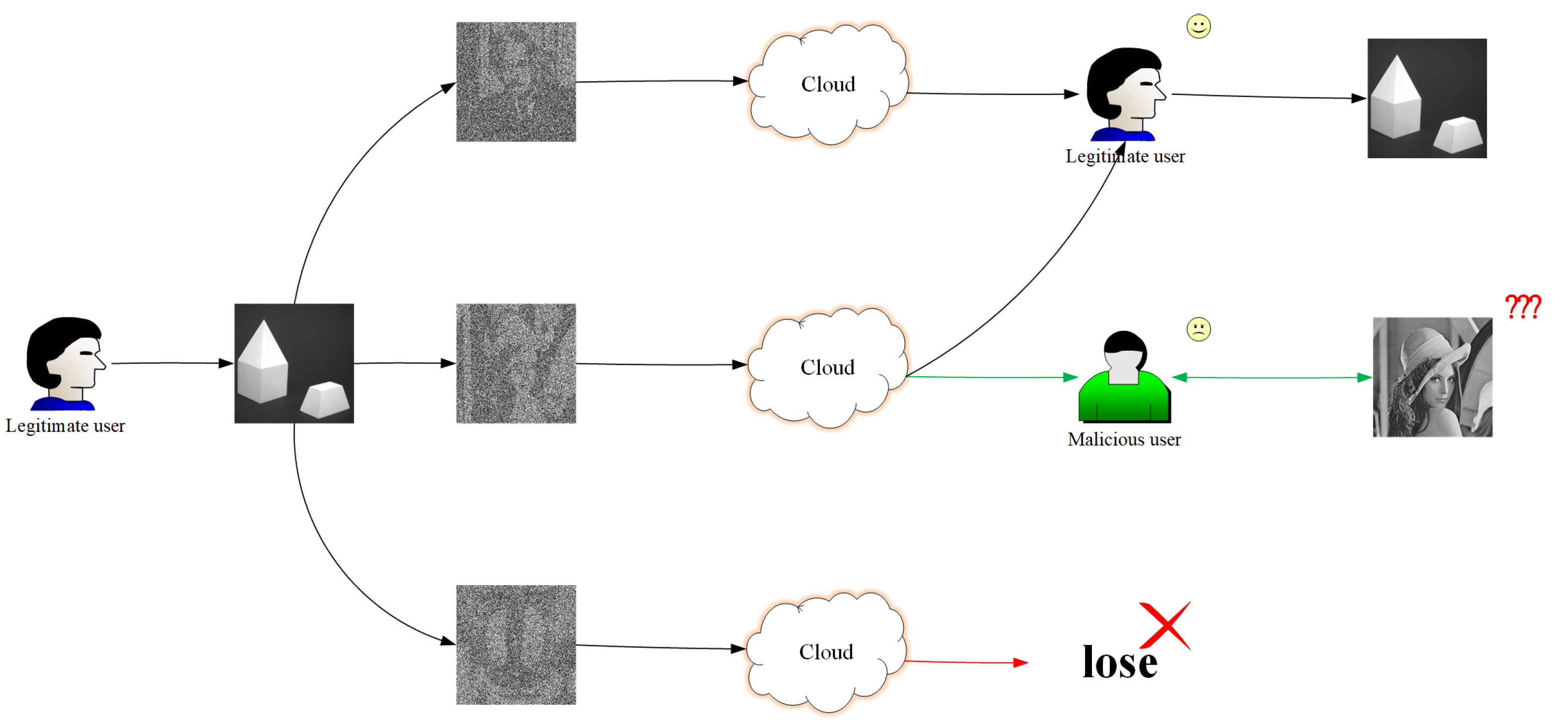
3. The Proposed Scheme
Our scheme fully considers the three elements of information security and realizes the full protection of secret images. Legitimate users can use our scheme to encrypt the secret image into meaningful cipher images. These cipher images have the characteristics of loss tolerance, which means that the loss of
cipher images will not affect the recovery of the secret image, and fully protect the availability of the secret image. Even if a malicious user obtains up to
cipher images, the malicious user does not obtain any information of the secret image through visual information or computation and does not have any impact on the confidentiality of the secret image. The legitimate user can easily manage cipher images through visual features, and when at least
k cipher images are obtained, the legitimate user can restore the secret image losslessly, ensuring the integrity of the secret. The detailed process can be referred to
Figure 3 and
Figure 4.
Our scheme is suitable for most high-value digital images, such as gray-scale images and color images. These images are composed of one or more channels, and each channel is a two-dimensional matrix array. Since the structure and value range of channels are the same, this paper mainly focuses on the single-channel image, that is, a gray-scale image. The range of gray image pixels is 0–255, that is, eight bits (one byte), which means that any data that can be represented by the binary stream are converted into a gray image. Therefore, through simple coding, any valuable binary data stream can be shared using the scheme presented in this paper.
The symbol description of the proposed scheme is shown in
Table 1.
3.1. Description of the Proposed Scheme
The scheme proposed in this paper mainly uses the knowledge of SS and thumbnails to realize the highly secure storage of secrets, which means that the confidentiality and integrity protection of secret images can be realized. Our proposed scheme mainly uses approximate thumbnails and control sharing models. Approximate thumbnails are mainly used to solve the usability problem of encrypted images. Unlike previous TPEs, the accuracy of our TPE images can be controlled on the premise that legitimate users with prior knowledge can be identified, and the overall pixel quality of the TPE image is lower than that of the original thumbnail. Controlling secret sharing is performed to solve the integrity of the secret and change the situation that the original shared cipher image is noise, which is based on approximate thumbnail sharing.
3.2. Approximate Thumbnails
Approximate thumbnails and thumbnails are visually similar, but the pixel accuracy is less than that of the original image.
In order to accurately describe the quality of approximate thumbnails, we introduce the following definitions.
Definition 1. Thumbnail ratio: The thumbnail ratio ℜ refers to the ratio of the length (width) of the secret image to the length (width) of the original image. General thumbnails do not change the aspect ratio (the ratio of length to width) of the original image, so the usual thumbnail ratio is .
Definition 2. Identification points: The identification point [] is the position of the pixel in the encrypted or shared cipher image that is similar to the meaningful image. The identification points can be calculated by Formula (1). Corresponding to the identification points are the unidentification points (). Through the definition and formula, it can be concluded that the identification point is only a part of the cipher image, and the cipher image is composed of identification points and unidentification points. That is, .
Definition 3. High-level same bit number: The high-level same bit number is the maximum equal bit number of two integers from high to low in the binary representation of the same bit number, and its calculation formula is denoted as .
Definition 4. Accuracy: Precision is the numerical similarity between the cipher image and the carrier image. The higher the precision is, the clearer the cipher image is, and vice versa. Precision only represents the numerical accuracy of the cipher image and the meaningful image, which can reflect the visual characteristics to a certain extent and can be obtained by Formula (2). The algorithm for approximate thumbnails is shown in Algorithm 3:
| Algorithm 3 Approximate thumbnails |
Input: Output: Approximate thumbnails R. Step 1: Determine the identifiable point A according to and Formula ( 1). Step 2: Read the pixels value of the carrier image according to the identifiable point. Step 3: According to , determine the range . The binary representation of is . The lower limit of is Formula ( 3),
and the upper limit of is Formula ( 4)
Step 4: The range of pixel values of non-identifiable point is . Step 5:R is obtained according to and , shown as Formula ( 5).
|
3.3. Control Sharing Models
There are a large number of available random numbers in the multiple sharing of SS. Using these variable random numbers can make the range of sharing pixel values meet the expected requirements, which is often used in SIS with meaningful shadows.
Different from the SIS with meaningful shadows [
41,
42], controlling secret sharing only needs to control the value range of location pixels, and the sharing of non-location pixels can be uncontrolled. This controllable secret sharing is more operable and flexible than the original SIS.
The specific steps of controlling the sharing model are shown in Algorithm 4.
3.4. Security Analysis
SS has the perfect security feature of one secret at a time. When the number of shadows is less than
k, no one can recover the secret, which has been proved in many works [
43,
44]. The main point of this scheme is the security equivalence of SS. However, the meaningful screening of pixels may have a certain impact on the security of the solution. Therefore, we conduct security analysis from the following two aspects.
| Algorithm 4 Control sharing models |
Input: , Secret image, Approximate thumbnail Output: n identifiable cipher images. Step 1: Share each pixel in the secret image P. Step 2: Judge whether is the identifiable point. Step 3: If is a identifiable point, randomly adjust the value of until the value range of is C; if it is not a identifiable point, just generate it directly. And its basic principle is Formula ( 6).
Step 4: Repeat 1, 2, 3 until all pixels of the secret image are encrypted. |
3.4.1. Security of Single Pixel
Suppose participants try to recover the master secret value . According to the security conditions of threshold secret sharing, since there are only shared values, participants cannot obtain any secret value-related information. If the participant tries to guess the value of the shared value , has a total of values, and the sharing sequence composed of known shared values corresponds to possible secret values, that is, the recovered secret value obeys uniformity on a distribution.
3.4.2. Security of Cipher Image
Due to the strong correlation between adjacent or close pixels of the secret image, even if the secret value is difficult to recover accurately, the special probability distribution characteristics of the shared sequence may leak visual information, such as texture features and contour information, posing certain security risks.
Theorem 1. The hidden danger of visual information leakage increases with the increase of accuracy.
Proof. Accuracy is determined by the high-level same bit number and the thumbnail ratio. The greater the high-level same bit number, the smaller the space that meets the conditions. The larger the thumbnail ratio, the more positioning points, and the corresponding conditions to be met also increase, which means that the matching space is reduced. When the value space of becomes smaller, we believe that there is a security risk in a certain sense. □
In fact, without k shadows in the recovery stage, it is also impossible to recover the secret image. In this paper, by selecting the identifiable point, the correlation between the adjacent pixels of the secret image is destroyed to a certain extent, and the definition is further reduced. Compared with the original meaningful secret sharing, the proposed scheme has higher security.
3.5. Efficiency Analysis
Our scheme only needs to control the sharing process of
pixels. Therefore, compared with the SIS with meaningful shadows, our scheme can effectively improve the efficiency of sharing. Assuming that the time for sharing a meaningful pixel is
, the total time for traditional meaningful sharing is shown in Formula (
7), and
T refers to the time used by other modules.
The time required for our scheme is shown in Formula (
8).
The time efficiency of improvement is shown in Formula (
9). When
T is negligible relative to
, ≈ holds. In fact, this is the case in most cases.
This is a comparison of theoretical efficiency, and we also give a comparison of the actual time efficiency in the experiment.
4. Experiments
In this section, the experimental data and results prove that the proposed scheme can achieve the expected effect and realize the effective protection of secret images. The experiment part includes four parts—thumbnail secret sharing, parametric analysis, efficiency comparison, and the thumbnail secret sharing of color images—that prove our scheme from different angles. As a single-channel image, a gray-scale image is the basis of the image and has strong scalability. Therefore, our experiment includes most gray-scale images and a few color images. For the impact of parameters, we also give the relevant data and analysis. In order to compare with the original meaningful secret sharing, we carried out the experimental comparison on the basis of theoretical analysis.
The relevant images used in this paper are shown in
Figure 5a–g.
Our implementation is written in Python, and we use the NumPy library for both 64 bit integer and float-point computations. We conduct our experiments on a desktop computer equipped with a 16-core Intel i7-10 CPU and 16 Gb RAM.
4.1. Thumbnail Secret Sharing
In order to verify the universality of the scheme, we select two groups of thumbnail sharing experimental results with different thresholds, high-level same bit number, and image size.
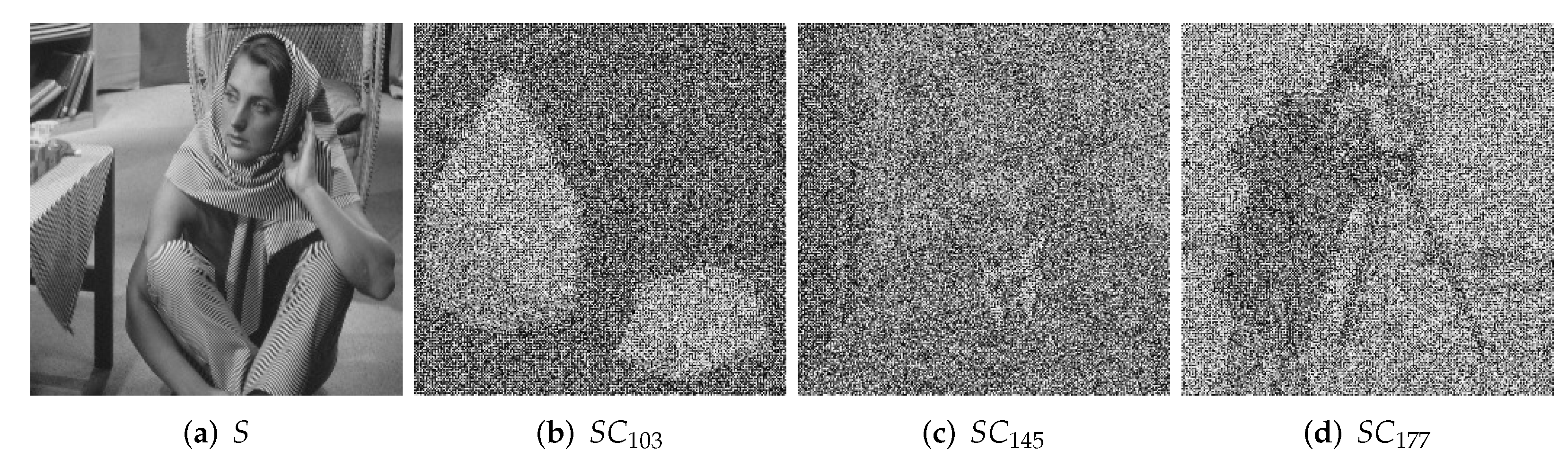
The secret image is
Figure 6a, the size is
, the thumbnail ratio
ℜ is 0.5, the high-level same bit number
is 2, the sharing threshold is
, the value of the serial number is
, and the shared cipher images are shown in
Figure 6b–d.
The secret image is
Figure 7a, the size is
, the thumbnail ratio
ℜ is 0.5, the high-level same bit number
is 1, the sharing threshold is
, the value of the serial number is
, and the shared cipher images are shown in
Figure 7b–e. Any three of the cipher images can be selected to restore the secret image in
Figure 7a.
The secret image is
Figure 8a, the size is
, the thumbnail ratio
ℜ is 0.5, the high-level same bit number
is 3, the sharing threshold is
, the value of the serial number is
, and the shared cipher images are shown in
Figure 8b–d. All cipher images can restore the secret image in
Figure 8a.
We adjust the thumbnail ratio ℜ and high-level same bit number through the algorithm so that the accuracy of the cipher image is . It is very easy for legitimate users with prior knowledge to identify the cipher images by adjusting the accuracy.
Experiments show that the visual characteristics of the cipher images can quickly identify the thumbnails corresponding to different serial numbers, and at the same time, the secret can be recovered when one of them is lost, which realizes the management of the cipher images and loss tolerance.
4.2. Thumbnail Secret Sharing of Color Images
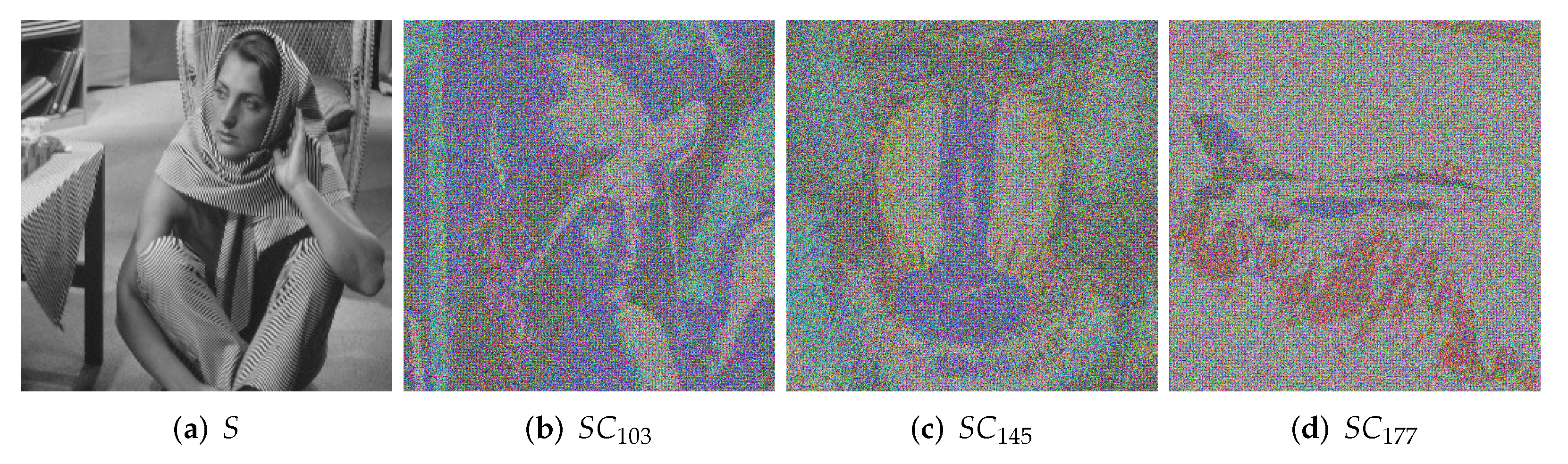
To verify the availability of the scheme for color images (multi-channel images), we performed this experiment. The experimental results are similar to those of a single channel, which proves that our scheme can be applied to most digital images. The secret image is
Figure 9a, the size is
, the thumbnail ratio
ℜ is 0.5, the high-level same bit number
is 1, the sharing threshold is
, the value of the serial number is
, and the shared cipher images are shown in
Figure 9b–d.
The color image is composed of RGB three channels, and its basic principle is similar to that of a single channel image. Therefore, our scheme is suitable for the protection of most digital images, which is well proved in this experiment.
4.3. Parametric Analysis
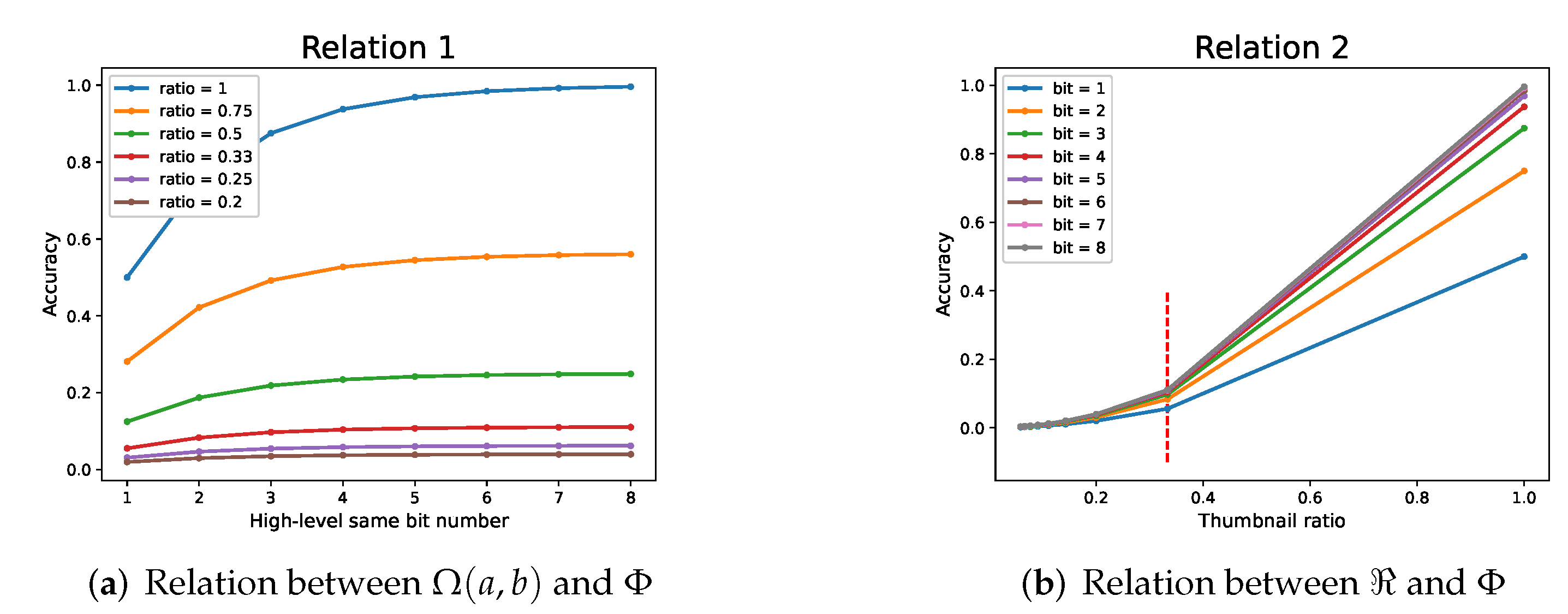
According to Formula (
2), we draw the relationship between the high-level same bit number and accuracy in
Figure 10a, with the relationship between compression rate and accuracy in
Figure 10b. By analyzing the visual quality of relation graphs and cipher images, we obtain the following conclusions and suggestions. Compared with the high-level same bit number, the thumbnail rate has a greater impact on accuracy and visual quality. When the thumbnail ratio is greater than
, the accuracy will decrease rapidly as the compression ratio decreases, and the recognition rate will drop rapidly.
We obtain the following parameter relationship:
When the thumbnail rate is greater than , the high-level same bit number can be appropriately reduced.
When the thumbnail rate is below , the high-level same bit number should be appropriately increased.
We analyze the relationship among the high-level same bit number, thumbnail ratio, and accuracy and obtain the regular characteristics between them. According to our conclusion, users can choose parameters flexibly according to their needs.
4.4. Comparison
4.4.1. Efficiency Comparison
The theoretical efficiency is analyzed in our paper. In this section, through the comparison of the time used in the listed experiments, it can be proved that our scheme can effectively improve efficiency. We select the classic SIS with meaningful shadows for comparison, which are used in multiple schemes [
41,
42]. We compare several dimensions, including threshold, compression ratio
ℜ, and the highest bit number
, and obtain the running time (
) and efficiency comparison (
). It can be seen from
Table 2 that the efficiency comparison(
) of our scheme is better than that of the SIS with meaningful shadows, and the efficiency improvement of some experimental results is very obvious, which fully shows the efficiency of the proposed scheme.
4.4.2. Functional Comparison
Our scheme has the complete functions and the fastest efficiency among all the current schemes. The comparison of specific functions is shown in
Table 3.
Confidentiality refers to the encryption of the image, which is the basic requirement of image security. In addition to uploading directly, other schemes are encrypted. Management is performed to manage images in the cloud through uploaded images. Directly encryption and SIS are noise images that cannot be directly managed; while uploaded directly, TPE and SIS with meaningful shadows and our scheme are all visually distinguishable images, showing that the management of images is possible. Loss tolerance refers to the ability to restore the secret image without loss after the uploaded image is lost. Uploading directly, direct encryption, and TPE have only one uploaded image, and the secret image cannot be restored after the file is lost. Only the functions of our scheme and SIS with meaningful shadows are the most comprehensive. In combination with the efficiency comparison in
Table 2, we find that our scheme is the best at present.
5. Conclusions
Aiming at resolving the problem of secret image management and loss in cloud space, this paper proposes a thumbnail secret sharing scheme based on thumbnail encryption and secret sharing, which mainly includes approximate thumbnails and control sharing models. The cipher image of the proposed scheme has the characteristics of visual recognition and loss tolerance. Visual recognition solves the management problem of cipher images and improves the availability of cipher images. Loss tolerance ensures the integrity and availability of important confidential images. The security and efficiency of the proposed scheme are analyzed and discussed. In addition, experiments and comparisons show that the proposed scheme has good visual characteristics and loss tolerance, and the efficiency of the scheme is significantly improved, which greatly improves the secret availability and security. In the future, reducing data redundancy and communication overheads are problems that need to be solved.
Author Contributions
Conceptualization, Y.Y. and X.Y.; methodology, Y.Y.; validation, S.W., X.W. and H.L.; formal analysis, S.W.; investigation, X.W.; data curation, H.L.; writing—original draft preparation, Y.Y.; writing—review and editing, S.W., X.W. and H.L.; supervision, X.Y.; funding acquisition, X.Y. All authors have read and agreed to the published version of the manuscript.
Funding
This research is funded by the National Natural Science Foundation of China (Grant Number: 61602491).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Dong, Y.; Ding, Z.; Chiclana, F.; Herrera-Viedma, E. Dynamics of Public Opinions in an Online and Offline Social Network. IEEE Trans. Big Data 2021, 7, 610–618. [Google Scholar] [CrossRef]
- Banerjee, S.; Jenamani, M.; Pratihar, D.K. A survey on influence maximization in a social network. Knowl. Inf. Syst. 2020, 62, 3417–3455. [Google Scholar] [CrossRef]
- Osman, M. Wild and Interesting Facebook Statistics and Facts (2021). Available online: https://kinsta.com/blog/facebook-statistics/ (accessed on 3 January 2021).
- Aslam, S. Facebook by the Numbers: Stats, Demographics & Fun Facts. Available online: https://www.omnicoreagency.com/facebook-statistics/ (accessed on 22 February 2022).
- Pantic, N. How Many Photos Will Be Taken in 2021? 2021. Available online: https://blog.mylio.com/how-many-photos-will-be-taken-in-2021-stats/ (accessed on 18 July 2022).
- Li, J.; Yan, H.; Zhang, Y. Certificateless Public Integrity Checking of Group Shared Data on Cloud Storage. IEEE Trans. Serv. Comput. 2021, 14, 71–81. [Google Scholar] [CrossRef]
- Zhang, Y.; Xu, C.; Lin, X.; Shen, X. Blockchain-Based Public Integrity Verification for Cloud Storage against Procrastinating Auditors. IEEE Trans. Cloud Comput. 2021, 9, 923–937. [Google Scholar] [CrossRef]
- Zhang, Y.; Yu, J.; Hao, R.; Wang, C.; Ren, K. Enabling Efficient User Revocation in Identity-Based Cloud Storage Auditing for Shared Big Data. IEEE Trans. Dependable Secur. Comput. 2020, 17, 608–619. [Google Scholar] [CrossRef]
- Shen, W.; Qin, J.; Yu, J.; Hao, R.; Hu, J. Enabling Identity-Based Integrity Auditing and Data Sharing With Sensitive Information Hiding for Secure Cloud Storage. IEEE Trans. Inf. Forensics Secur. 2019, 14, 331–346. [Google Scholar] [CrossRef]
- Aslam, S. Main Cloud Security Issues and Threats in 2021. 2021. Available online: https://www.checkpoint.com/cyber-hub/cloud-security/what-is-cloud-security/top-cloud-security-issues-threats-and-concerns/ (accessed on 18 July 2022).
- Esposito, C.; De Santis, A.; Tortora, G.; Chang, H.; Choo, K.K.R. Blockchain: A Panacea for Healthcare Cloud-Based Data Security and Privacy? IEEE Cloud Comput. 2018, 5, 31–37. [Google Scholar] [CrossRef]
- Lakshmi, V.S.; Deepthi, S.; Deepthi, P.P. Collusion resistant secret sharing scheme for secure data storage and processing over cloud. J. Inf. Secur. Appl. 2021, 60, 102869. [Google Scholar] [CrossRef]
- Meng, S.; Huang, W.; Yin, X.; Khosravi, M.R.; Li, Q.; Wan, S.; Qi, L. Security-Aware Dynamic Scheduling for Real-Time Optimization in Cloud-Based Industrial Applications. IEEE Trans. Ind. Inform. 2021, 17, 4219–4228. [Google Scholar] [CrossRef]
- Mishra, P.; Varadharajan, V.; Pilli, E.S.; Tupakula, U. VMGuard: A VMI-Based Security Architecture for Intrusion Detection in Cloud Environment. IEEE Trans. Cloud Comput. 2020, 8, 957–971. [Google Scholar] [CrossRef]
- Masood, F.; Driss, M.; Boulila, W.; Ahmad, J.; Jan, S.U.; Qayyum, A.; Buchanan, W. A Lightweight Chaos-Based Medical Image Encryption Scheme Using Random Shuffling and XOR Operations. Wirel. Pers. Commun. 2021. [Google Scholar] [CrossRef]
- Guo, S.; Xiang, T.; Li, X.; Yang, Y. PEID: A Perceptually Encrypted Image Database for Visual Security Evaluation. IEEE Trans. Inf. Forensics Secur. 2020, 15, 1151–1163. [Google Scholar] [CrossRef]
- Hua, Z.; Zhu, Z.; Chen, Y.; Yuanman, L. Color image encryption using orthogonal Latin squares and a new 2D chaotic system. Nonlinear Dyn. 2021, 104, 1–18. [Google Scholar] [CrossRef]
- Hua, Z.; Zhang, K.; Li, Y.; Zhou, Y. Visually secure image encryption using adaptive-thresholding sparsification and parallel compressive sensing. Signal Process. 2021, 183, 107998. [Google Scholar] [CrossRef]
- Yang, C.N.; Lin, Y.C.; Li, P. Cheating immune k-out-of-n block-based progressive visual cryptography. J. Inf. Secur. Appl. 2020, 55, 102660. [Google Scholar] [CrossRef]
- Yan, X.; Liu, X.; Yang, C.N. An enhanced threshold visual secret sharing based on random grids. J. Real-Time Image Process. 2018, 14, 61–73. [Google Scholar] [CrossRef]
- Wright, C.V.; Feng, W.C.; Liu, F. Thumbnail-Preserving Encryption for JPEG. In Proceedings of the 3rd ACM Workshop on Information Hiding and Multimedia Security, Portland, OR, USA, 17–19 June 2015; IH&MMSec ’15. Association for Computing Machinery: New York, NY, USA, 2015; pp. 141–146. [Google Scholar] [CrossRef]
- Marohn, B.; Wright, C.V.; Feng, W.C.; Rosulek, M.; Bobba, R.B. Approximate Thumbnail Preserving Encryption. In Proceedings of the 2017 on Multimedia Privacy and Security, Dallas, TX, USA, 30 October 2017; MPS ’17. Association for Computing Machinery: New York, NY, USA, 2017; pp. 33–43. [Google Scholar] [CrossRef]
- Chai, X.; Wang, Y.; Chen, X.; Gan, Z.; Zhang, Y. TPE-GAN: Thumbnail Preserving Encryption Based on GAN With Key. IEEE Signal Process. Lett. 2022, 29, 972–976. [Google Scholar] [CrossRef]
- Bellare, M.; Ristenpart, T.; Rogaway, P.; Stegers, T. Format-Preserving Encryption. In Selected Areas in Cryptography; Jacobson, M.J., Rijmen, V., Safavi-Naini, R., Eds.; Springer: Berlin/Heidelberg, Germany, 2009; pp. 295–312. [Google Scholar]
- Tajik, K.; Gunasekaran, A.; Dutta, R.; Ellis, B.; Bobba, R.; Rosulek, M.; Wright, C.; Feng, W.C. Balancing Image Privacy and Usability with Thumbnail-Preserving Encryption. In Proceedings of the Network and Distributed System Security Symposium, San Diego, CA, USA, 24–27 February 2019. [Google Scholar] [CrossRef]
- Zhang, Y.; Zhao, R.; Xiao, X.; Lan, R.; Liu, Z.; Zhang, X. HF-TPE: High-Fidelity Thumbnail- Preserving Encryption. IEEE Trans. Circuits Syst. Video Technol. 2022, 32, 947–961. [Google Scholar] [CrossRef]
- Zhao, R.; Zhang, Y.; Xiao, X.; Ye, X.; Lan, R. TPE2: Three-Pixel Exact Thumbnail-Preserving Image Encryption. Signal Process. 2021, 183, 108019. [Google Scholar] [CrossRef]
- Houmani, H.; Mejri, M. Secrecy by interpretation functions. Knowl.-Based Syst. 2007, 20, 617–635. [Google Scholar] [CrossRef]
- Yan, X.; Lu, Y.; Yang, C.N.; Zhang, X.; Wang, S. A Common Method of Share Authentication in Image Secret Sharing. IEEE Trans. Circuits Syst. Video Technol. 2021, 31, 2896–2908. [Google Scholar] [CrossRef]
- Li, P.; Ma, J.; Ma, Q. (t, k, n) XOR-based visual cryptography scheme with essential shadows. J. Vis. Commun. Image Represent. 2020, 72, 102911. [Google Scholar] [CrossRef]
- Yan, X.; Li, J.; Pan, Z.; Zhong, X.; Yang, G. Multiparty verification in image secret sharing. Inf. Sci. 2021, 562, 475–490. [Google Scholar] [CrossRef]
- Wu, X.; Yang, C.N.; Li, J.M. Secure image secret sharing over distributed cloud network. Signal Process. 2021, 178, 107768. [Google Scholar] [CrossRef]
- Shamir, A. How to Share a Secret. Commun. ACM 1979, 22, 612–613. [Google Scholar] [CrossRef]
- Blakley, G.R. Safeguarding cryptographic keys. In Proceedings of the 1979 International Workshop on Managing Requirements Knowledge (MARK), New York, NY, USA, 4–7 June 1979; pp. 313–318. [Google Scholar] [CrossRef]
- Yan, X.; Lu, Y.; Liu, L.; Song, X. Reversible Image Secret Sharing. IEEE Trans. Inf. Forensics Secur. 2020, 15, 3848–3858. [Google Scholar] [CrossRef]
- Li, L.; Hossain, M.S.; El-Latif, A.A.A.; Alhamid, M.F. Distortion Less Secret Image Sharing Scheme for Internet of Things System. Clust. Comput. 2019, 22, 2293–2307. [Google Scholar] [CrossRef]
- Yan, X.; Liu, L.; Li, L.; Lu, Y. Robust Secret Image Sharing Resistant to Noise in Shares. ACM Trans. Multimedia Comput. Commun. Appl. 2021, 17, 1–22. [Google Scholar] [CrossRef]
- Thien, C.C.; Lin, J.C. Secret image sharing. Comput. Graph. 2002, 26, 765–770. [Google Scholar] [CrossRef]
- Jiang, D.; Liu, L.; Zhu, L.; Wang, X.; Rong, X.; Chai, H. Adaptive embedding: A novel meaningful image encryption scheme based on parallel compressive sensing and slant transform. Signal Process. 2021, 188, 108220. [Google Scholar] [CrossRef]
- Yang, C.N.; Tsai, P.Y.; Liu, Y. A (k, n) secret document sharing with meaningful shares. J. Inf. Secur. Appl. 2021, 62, 102973. [Google Scholar] [CrossRef]
- Ateniese, G.; Blundo, C.; Santis, A.D.; Stinson, D.R. Extended capabilities for visual cryptography. Theor. Comput. Sci. 2001, 250, 143–161. [Google Scholar] [CrossRef]
- Cheng, J.; Yan, X.; Liu, L.; Jiang, Y.; Wang, X. Meaningful Secret Image Sharing with Saliency Detection. Entropy 2022, 24, 340. [Google Scholar] [CrossRef] [PubMed]
- Pedersen, T.P. Non-Interactive and Information-Theoretic Secure Verifiable Secret Sharing. In Proceedings of the Advances in Cryptology—CRYPTO’91, 11th Annual International Cryptology Conference, Santa Barbara, CA, USA, 11–15 August 1991; Feigenbaum, J., Ed.; Lecture Notes in Computer Science. Springer: Berlin/Heidelberg, Germany, 1991; Volume 576, pp. 129–140. [Google Scholar] [CrossRef] [Green Version]
- Cramer, R.; Damgård, I.; Nielsen, J.B. Secure Multiparty Computation and Secret Sharing; Cambridge University Press: Cambridge, UK, 2015. [Google Scholar]
| Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).