Abstract
Data security represents an essential task in the present day, in which chaotic models have an excellent role in designing modern cryptosystems. Here, a novel oscillator with chaotic dynamics is presented and its dynamical properties are investigated. Various properties of the oscillator, like equilibria, bifurcations, and Lyapunov exponents (LEs), are discussed. The designed system has a center point equilibrium and an interesting chaotic attractor. The existence of chaotic dynamics is proved by calculating Lyapunov exponents. The region of attraction for the chaotic attractor is investigated by plotting the basin of attraction. The oscillator has a chaotic attractor in which its basin is entangled with the center point. The complexity of the chaotic dynamic and its entangled basin of attraction make it a proper choice for image encryption. Using the effective properties of the chaotic oscillator, a method to construct pseudo-random numbers (PRNGs) is proposed, then utilizing the generated PRNG sequence for designing secure substitution boxes (S-boxes). Finally, a new image cryptosystem is presented using the proposed PRNG mechanism and the suggested S-box approach. The effectiveness of the suggested mechanisms is evaluated using several assessments, in which the outcomes show the characteristics of the presented mechanisms for reliable cryptographic applications.
Keywords:
chaotic dynamical oscillator; chaos-based PRNG; chaos-based S-box; chaos-based image cryptosystem; security purposes MSC:
65P20; 34C28; 68P25
1. Introduction
Information security plays a significant role in our daily lives [,]. Information can be protected via performing one of the data security methods like information hiding []. The main objective of data encryption is to convert the data style from an intelligible style into an unintelligible pattern. Chaotic models are considered as a backbone of designing modern data encryption algorithms [,]. In [], an encryption method based on a hyperchaotic oscillator was proposed to use the ciphertext in the pseudo-random sequences, and also the encryption method has a closed-loop form.
Chaos is one of the most mysterious dynamics that catches the attention of many researchers []. A critical question in this area is the generation of chaotic attractors. Previously, there was a hypothesis that chaotic attractors are linked to saddle points [,]. After that, two systems were presented to show chaotic oscillations without saddle point [,]. Thus, two groups of dynamics were investigated: self-excited and hidden. The basin of attraction of a self-excited attractor is around an unstable equilibrium, while in hidden attractors, there is not such an association []. It was a turning point in the study of chaotic flows. Then, investigations have been focused on various features of chaotic flows such as multistability and multi-scroll attractors. Dynamical properties of of a novel oscillator with extreme multistability was studied in []. A memristive oscillator with multiwing dynamics was discussed in []. In [], an image encryption method based on a multi-scroll memristive system was designed. The analog implementation of Hindmarsh–Rose neuron model was discussed in []. Various dynamics of a fractional-order chaotic oscillator were investigated in []. The oscillator has three types of offset-boosting. The synchronization of flows is interesting. The synchronization of chaotic neural network with impulsive control was studied in []. Sliding mode and passivity method was used to investigate the synchronization of chaotic flows with perturbations [].
Various tools can be used to investigate the properties of dynamical oscillators [,,]. Plotting a bifurcation diagram is one of the most noticeable methods [,,]. It shows the variations of the oscillator’s attractors by varying a parameter. Another tool is a Lyapunov exponent that reveals the chaotic behaviors []. Plotting the basin of attraction helps to investigate various oscillator dynamics by changing initial conditions []. The basin of attraction is often a two-dimensional plot that shows the attraction’s area of various attractors. Multistability is an interesting behavior of dynamical oscillators [,,]. Multistability is a condition in which the system has two or more attractors in a constant set of parameters and just by changing initial conditions. Extreme multistability is a particular case of multistability [,]. It is a case with coexisting uncountable infinite attractors. Here, a novel chaotic flow is proposed. Dynamical behavior of the system reveals its noticeable behavior.
PRNG and S-box mechanisms are considered as the backbone of designing modern data encryption algorithms and draw in much attention from cryptographers and specialists [], in which chaotic models are commonly used for generating PRNG sequences and constructing S-boxes due to their complex dynamics []. Using the effective properties of the new chaotic flow, a method to construct PRNGs is presented and then utilizes the generated PRNG sequence for designing secure S-boxes. Finally, a new image cryptosystem is proposed using the suggested PRNG method and the suggested S-box approach. The effectiveness of the suggested mechanisms is evaluated using several assessments, in which the outcomes show the vital characteristics of the presented mechanisms for reliable cryptographic applications.
We can recap the principal contributions of this work as given below:
- Presenting a novel oscillator with chaotic dynamics and investigating its dynamical properties;
- Constructing a novel PRNG method using the effective properties of the new chaotic flow;
- Utilizing the PRNG method for designing secure S-boxes;
- Due to the importance of data security in the present day, a new image cryptosystem is presented as a cryptographic application of the presented chaotic oscillator.
In the following, the chaotic oscillator system is proposed, and its features are investigated in Section 2. In Section 3, the suggested PRNG scheme is introduced including its performance analyses, while the suggested chaos-based S-box and its performance analyses are provided in Section 4. The image cryptosystem is proposed including its analyses in Section 5. Section 6 gives the concluding points and future works.
2. Chaotic Oscillator
A novel chaotic oscillator is designed and its equations are presented in Equation (1). It is a jerk system that shows chaotic dynamics in , and initial values . Figure 1 gives the attractor of the oscillator. The oscillator is solved by runtime 800. Half of the signals are removed as the transient time:
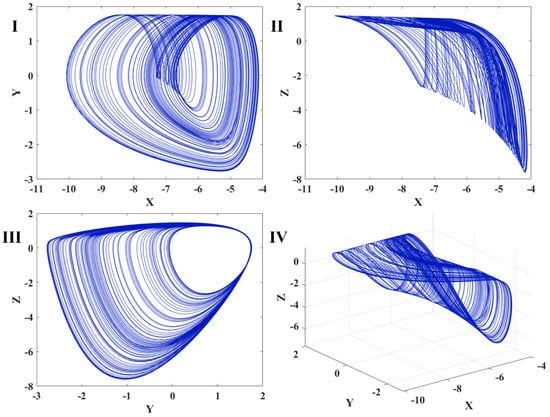
Figure 1.
Chaotic behavior of the oscillator in various projections; (I) plane; (II) plane; (III) plane; (IV) space.
To investigate the dynamics of the oscillator, its equilibrium point is calculated as . The characteristic equation of the oscillator at is . Therefore, the eigenvalues are . Thus, the type of the origin cannot be revealed by the eigenvalues. Numerical examinations show that the equilibrium point is a center point. The dynamics of the oscillator around the equilibrium point are a cycle in which its amplitude changes by changing initial conditions. In this situation, which is proved by running the system for many initial conditions, the equilibrium point is called a center point. Investigation of equilibrium points and their stability is very important in the study of chaotic systems. In [], various chaotic flows with different equilibrium points were reviewed. Chaotic flows with specific analytical solutions were discussed in [].
Different dynamics of the oscillator can be investigated using a bifurcation diagram (BD). The BD of a continuous oscillator is schemed using a Poincare section (PS) of the attractors in each parameter by varying the bifurcation parameter gradually. Usually, the PS is selected as the peak values of the variables. Lyapunov exponent (LE) is another mechanism to investigate various dynamics of a flow. The Wolf method with runtime 20,000 is used to calculate Lyapunov exponents []. It is a well-known method and is very popular in the literature [,]. Here, the BDs of the oscillator are studied by varying three parameters, a, b and c. A period-doubling route to chaos is shown in all of the figures. The first row of Figure 2 presents a BD for changing . It presents the peaks of x. By increasing a, the oscillator’s dynamics become more orderly. Part II of Figure 2 displays the LEs of the oscillator by varying parameters a. It shows that the oscillator has chaotic dynamics in since it has one positive LE. Then, in the interval , the largest LE is zero, which means the dynamics are limit cycles. The first row of Figure 3 presents the bifurcations by changing . The oscillator shows a period-doubling until it reaches the chaotic attractors. Part II of Figure 3 displays the LEs of the oscillator by varying parameters b. The results show that the oscillator has periodic dynamics in . In that interval, the largest LE of the oscillator is zero. Then, by increasing the parameter b, the oscillator’s dynamics become chaotic with one positive LE. Figure 4 shows the BD by varying c. The bifurcation has a wider chaotic region than bifurcation by changing a and b. Its LEs by changing c represents the chaotic regions (part II of Figure 4).
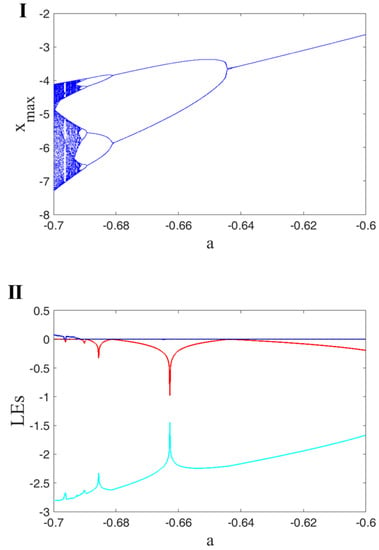
Figure 2.
BD of Oscillator (1) by constant initial conditions ; (I) peaks of x by varying the parameter a; (II) three different Lyapunov exponents of the oscillator shown by different colors calculated using constant initial values and by changing a.
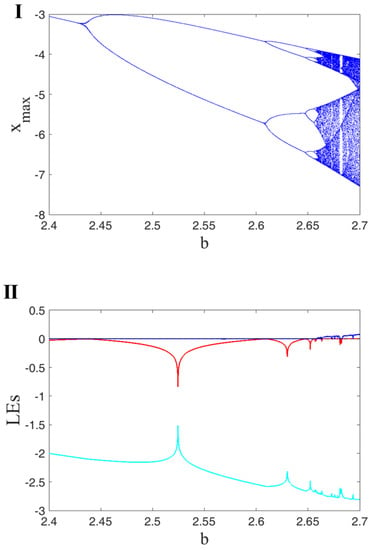
Figure 3.
BD of Oscillator (1) by constant initial conditions ; (I) peaks of x by varying the parameter b; (II) three different Lyapunov exponents of the oscillator shown by different colors calculated using constant initial values and by changing b.
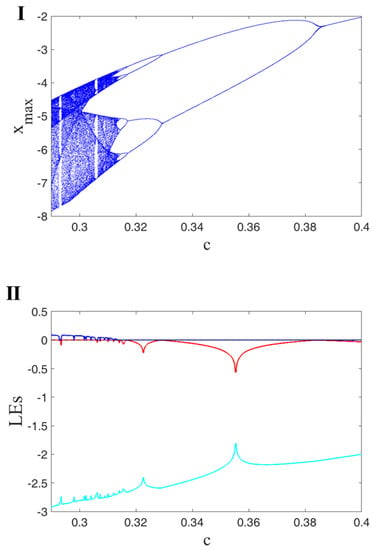
Figure 4.
BD of Oscillator (1) by constant initial conditions ; (I) peaks of x by varying the parameter c; (II) three different Lyapunov exponents of the oscillator shown by different colors calculated using constant initial values and by changing c.
The basin of attraction of the oscillator is shown in Figure 5. The yellow region in this plot shows unbounded solutions, the cyan color is attracted to the chaotic attractors, and the red color remains around the equilibrium point. The result shows that the chaotic dynamics have a large basin of attraction entangled with center point dynamics.
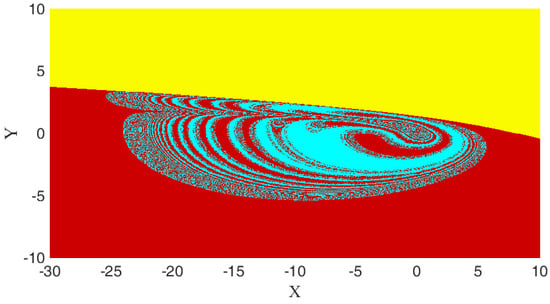
Figure 5.
Basin of attraction of Oscillator (1); The yellow region in this plot shows unbounded solutions, the cyan color is attracted to the chaotic attractors, and the red color remains around the equilibrium point.
The chaotic dynamic of the oscillator shows a complex signal which can be used in encryption applications. In addition, it has a range of parameters to present chaotic dynamics, making finding the exact system hard for attackers. However, initial conditions are an essential matter if they know the exact system. In the following, the proposed oscillator is used in designing various cryptographic applications.
3. Proposed PRNG Mechanism and Its Performance
PRNG plays a vital task in designing robust cryptographic primitives []. It guarantees that the attackers cannot prophesy the data. In this part, the proposed PRNG mechanism and its performance analyses are presented.
3.1. PRNG Mechanism
The PRNG scheme is proposed using the presented chaotic oscillator. The itemized actions of the presented PRNG are provided in the following:
- Solve the chaotic oscillator (Equation (1)) with initial values (,,) and control parameters to obtain the signals X, Y, and Z;
- Transform signals X, Y, and Z into integer numbers in the interval ;where fix function rounds each number to the closest integer toward zero (i.e., fix(5.483) = 5) and mod function represents the modulo operation (i.e., 7.5 mod 3 = 1.5) [].
3.2. PRNG Performance Analyses
To guarantee the effectiveness of the presented PRNG mechanism, security analyses are carried out for the generated PRNG sequences in terms of correlation, randomness tests, histograms, key sensitivity, and entropy.
3.2.1. Correlation Performance
The correlation coefficient measures the relation between two pseudo-random sequences. The correlation coefficient of two sequences can be defined by
where and are the ith pair of adjacent numbers, and M is the entire number of neighborhood numbers. The average outcome of correlation is 0.0001288, which refers to the absence of correlation between the two generated sequences.
3.2.2. Randomness Test
To measure the randomness of the signal, NIST SP 800-22 is employed. Its role is to highlight any non-randomness in a PRNG signal. It consists of 15 tests that are executed on different 1000 PRNG signals each of bits []. The outcomes are shown in Table 1, in which the successful proportion is greater than 98%. Therefore, the PRNG signal is purely random.

Table 1.
NIST SP800-22 outcomes of 1000 PRNG signals each of bits.
3.2.3. Key Sensitivity (KS)
The KS is a vital feature of any secure PRNG method. Any tiny modifications in the key lead to different results. To assess the KS of the PRNG, some tests are done: byte change rate and bit change rate. For two sequences with tiny modifications in the secret key, the byte change rate is 99.62745% and the bit change rate is 50.01032%, which is near the ideal bit change rate of 50%. The stated results for both byte and bit change rates proved that the PRNG mechanism is susceptible to slight modifications in the secret key.
3.2.4. Histograms
A good PRNG scheme should ensure the uniformity of histograms for distinct PRNG sequences. Figure 6 presents the histograms of four different PRNG sequences, in which the histograms are uniform.
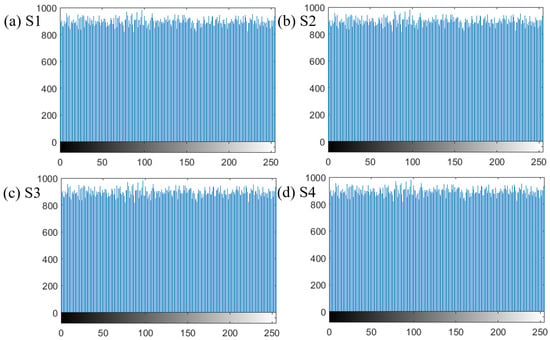
Figure 6.
Histograms of four different PRNG sequences, in which the histograms are uniform. (a) Histogram of sequence S1; (b) Histogram of sequence S2; (c) Histogram of sequence S3; (d) Histogram of sequence S4.
3.2.5. Information Entropy
Information entropy is intended for computing the randomness of a specific message as Equation (5) []:
where signifies the probability of . Optimal entropy value for a number with 8-bit is equal to 8. To estimate the effectiveness of the presented PRNG scheme, the information entropy test is performed on the generated PRNG sequence. The outcome value of entropy is 7.9992, which is close to 8. Therefore, the presented PRNG mechanism is reliable for various cryptographic applications.
4. Proposed S-Box Mechanism and Its Performance
S-boxes is important in designing robust cryptographic applications. Here, the S-box mechanism and its performance are provided.
4.1. S-Box Mechanism
The S-box approach is based on the presented PRNG approach. The itemized actions of the presented S-box are provided in the following steps:
- Obtain a PRNG sequence using the presented PRNG algorithm (see Section 3.1);
- Collect the first 256 dissimilar element from the PRNG sequence to construct an 8 × 8 S-box.
4.2. S-Box Performance Analyses
To guarantee the effectiveness of the presented S-box mechanism, performance analyses are carried out for the generated S-box [,]. The primary states and control parameters that are used to create an S-box (An S-box has an different elements) are given as = −0.2851, = 0.7692, = 0.6170, a = −0.7, b = 2.7, and c = 0.3. The created S-box is provided in Table 2, while Table 3 presented a comparison of the performance for the proposed S-box besides relevant S-boxes as reported in [,,,] in terms of nonlinearity, strict avalanche criterion (SAC), bit independence (BIC), linear approximation probability (LP), and differential probability (DP), in which the stated S-box approach has good SAC, BIC, and nonlinearity properties.

Table 2.
An S-box created via the proposed approach.

Table 3.
Comparison of the performance for the S-box besides relevant S-boxes.
5. Proposed Image Encryption Algorithm and Its Performance
Data security is important due to the rapid growth of internet technologies. Digital images are usually utilized for representing information [,]. Digital images can be protected via image encryption algorithms. Image encryption aims to convert the image from an intelligible style into an unintelligible pattern. Chaotic models are usually utilized for designing reliable image cryptosystems [,]. Using the effective properties of the chaotic flow, an image cryptosystem is presented. Therefore, this part is devoted to the proposed image cryptosystem and its performance analyses.
5.1. Encryption Algorithm
The proposed image cryptosystem is based on the PRNG algorithm and the suggested S-box approach. At first, the plain image is substituted using the generated PRNG sequence, then some information about the substituted image is acquired, and this information is utilized to update the initial conditions of the chaotic oscillator. Using the updated initial conditions, solve the chaotic oscillator system to generate three sequences, and utilize the first and the third sequences to construct a permutation box for shuffling the rows of the substituted image and utilize the second and the third sequences to construct a permutation box for shuffling the columns of the substituted image. Finally, construct an S-box for substituting the permutated image to generate the cipher image. The procedure of the proposed image encryption algorithm is outlined in Figure 7 and its details in Algorithm 1.
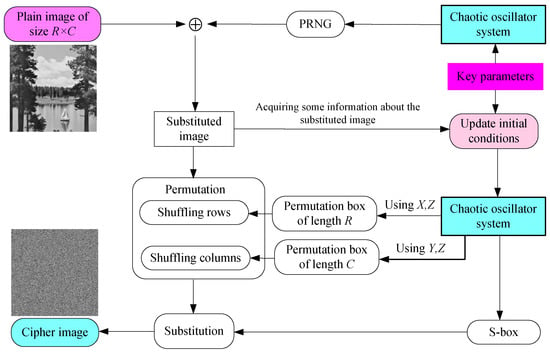
Figure 7.
Outline of the image encryption algorithm for the proposed cryptosystem.
5.2. Decryption Algorithm
The decryption algorithm of the proposed cryptosystem is the inverse of the encryption algorithm. Prior to the encryption process, the key parameters utilized in the encryption process are shared between the sender and the receiver via a closed environment or by utilizing one of the appropriate asymmetric cryptography algorithms for distributing keys (i.e., 5 RSA, ECC). After the encryption process, the value of is shared between the sender and the receiver by utilizing one of the asymmetric cryptography algorithms, to perform the decryption algorithm on the receiver’s device. The procedure of the proposed decryption algorithm is outlined in Figure 8 and its details in Algorithm 2.
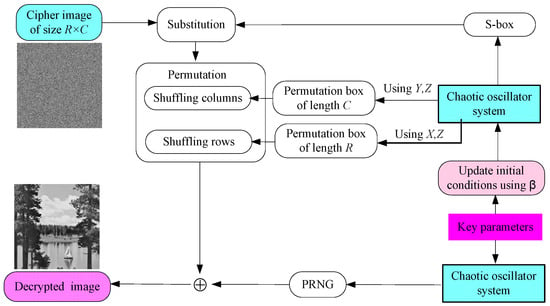
Figure 8.
Outline of the decryption algorithm for the proposed cryptosystem.
5.3. Image Cryptosystem Performance Analyses
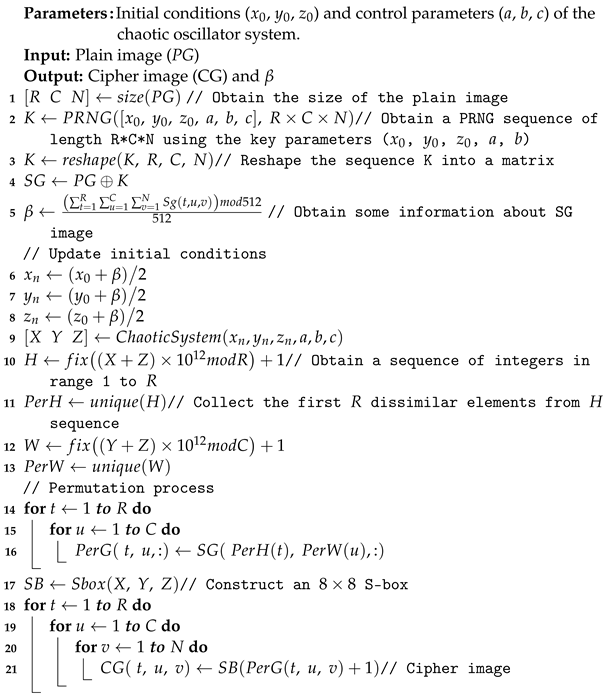
To guarantee the effectiveness of the presented image cryptosystem, performance analyses are carried out on a PC with Intel 2 Duo of CPU 3.00 GHz, 4.00 GB of RAM, and preinstalled with MATLAB 2016b. The dataset of used images consists of four standard grayscale images with dimension 512 × 512 and labeled as Lake, WalkBridge, Mandrill, and JetPlane (see Figure 9). The primary key parameters are given as = −0.2851, = 0.7692, = 0.6170, a = −0.7, b = 2.7, and c = 0.3.
| Algorithm 1: Image encryption algorithm |
 |
| Algorithm 2: Image decryption algorithm |
 |
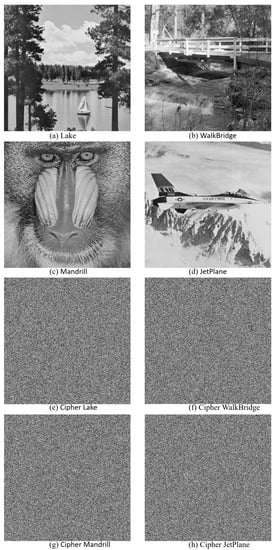
Figure 9.
Experimental dataset of images, in which the top two rows represent the plain version of images and the bottom two rows indicate the cipher version of images.
The efficiency of any image encryption algorithm relies on two factors; the first one is based on encryption time, while the second factor is based on the ability to resistant manifold attacks: such as brute force, statistical cryptanalysis, differential cryptanalysis, etc. These factors are discussed in the following subsections to illustrate the efficiency of the presented image encryption algorithm.
5.3.1. Encryption Time
Encryption time is the time elapsed to encrypt one image. Table 4 provides the encryption speed in Mbits/second, in which the presented cryptosystem has good encryption time besides other related algorithms.

Table 4.
Comparison of encryption speed (in Mbits/second) for the proposed cryptosystem with other corresponding methods, as stated in [,,].
5.3.2. Correlation Performance
Each pixel value in a plain image is extremely correlated with its adjacent pixels and its correlation coefficients are close to 1 in all directions, while correlation coefficients for cipher images are very close to 0. For calculating the correlation coefficients for plain and their cipher images, we randomly picked 10,000 neighboring pixels in each direction. Table 5 stated the correlation coefficients for the plain images and their analogous cipher versions, in which the correlation coefficients of cipher images are very close to 0. In addition, the correlation distribution for the plain and cipher Lake image are plotted in Figure 10. From the declared outcomes, we can deduce that the proposed cryptosystem withstands correlation analysis.

Table 5.
Correlation coefficients for the plain images and their analogous cipher versions, in which the correlation coefficients of cipher images are very close to 0.
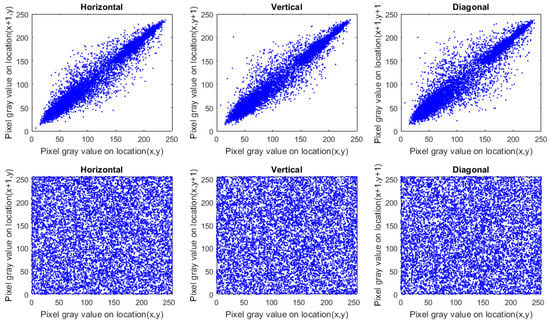
Figure 10.
Correlation distribution for plain and cipher Lake image, in which the top row refers to the correlation distribution of the plain image, while the bottom row refers to the correlation distribution of the ciphered image.
5.3.3. Differential Analyses
Plain image sensitivity is a vital feature of any secure image cryptosystem, in which any tiny modifications in the plain image lead to significant different in the cipher image. To assess the plain image sensitivity of the proposed cryptosystem, some tests are done: NPCR (Number of Pixels Change Rate) and UACI (Unified Average Changing Intensity). They can be defined as follows []:
where , are two generated cipher images for one plain image with tiny modifications in one of its bits; N denotes the entire pixels for the image. The results are stated in Table 6, in which the stated data proved that the proposed cryptosystem is sensitive to slight modifications in the plain image.

Table 6.
NPCR and UACI values for investigated images when changing one bit in one pixel in the image.
5.3.4. Histogram Test
A good image cryptosystem scheme should ensure the uniformity of histograms for distinct cipher images. Figure 11 presents the histograms of the plain images and their analogous cipher versions, in which the histograms of plain images are distinct from each other’s while the histograms of their analogous cipher images are uniform with each other. To ensure the similarity of histograms for the ciphered images, we used a quantity test like variance (Var) [], which can be defined as provided in Equation (8):
where is the sequence of the histogram values, and and are the pixel numbers whose grey values are equal to p and q, respectively. Table 7 provides the outcomes of histogram variance for the tested images previous and after the encryption process, in which the low values denote the high uniformity of histograms.
Figure 11.
Histograms of images, in which the top two rows represent the histograms of plain images and the bottom two rows indicate the histograms of cipher images.

Table 7.
Outcomes of histogram variance, in which low values of histogram variance denote the high uniformity of histograms.
5.3.5. Information Entropy
Information entropy is intended to compute the randomness of a specific message []. The optimal entropy value for a grayscale image is equal to 8. To estimate the effectiveness of the presented image cryptosystem, the information entropy test is performed on the plain and its analog cipher images. The outcomes of entropy are provided in Table 8, in which the entropy values for cipher images are near 8. From the stated data, we can deduce that the proposed cryptosystem withstands entropy analysis.

Table 8.
Outcomes of entropy, in which the entropy values for cipher images are very close to 8.
5.3.6. Key Space and Key Sensitivity
The key space refers to the diverse keys that can be used in brute force attacks which should be extensive sufficiently to resist those attacks. In the presented encryption algorithm, we utilize the primary key parameters (, , , a, and b) to solve the chaotic oscillator (Equation (1)) in the encryption and decryption procedures. By assuming that the precision computation of digital devices is , the key space for the presented cryptosystem is , which is enough for any cryptographic method.
Key sensitivity is a vital feature of any secure cryptosystem. Any tiny modifications in the key lead to different results. To assess the key sensitivity of the proposed image cryptosystem, we attempt to decrypt the cipher image of Lake several times utilizing tiny modifications in key parameters. The decryption effects are provided in Figure 12, in which the original image is not retrieved when making tiny changes in the key parameters. Furthermore, to test the key sensitivity in quantity terms, we execute an NPCR test on the decrypted Lake image with the actual key and other decrypted images with slight changes in the initial keys as stated in Figure 12, the outcomes are displayed in Table 9. From the outcomes given in Figure 12 and Table 9, the presented image encryption algorithm has high key sensitivity, in which any slight modifications in initial keys lead to significant modifications in the results.

Figure 12.
Decryption effects of cipher Lake image when making tiny changes in the key parameters.

Table 9.
NPCR values for the decrypted Lake image with the actual key and other decrypted images with slight changes in the initial keys as stated in Figure 12.
5.3.7. Data Loss Attack
During data transmission across a communication channel, the cipher data may have vulnerability to data loss attacks. Therefore, any image cryptosystem must be invincible against data loss attacks. To value the proposed image cryptosystem for withstanding data loss attacks, we cut out some blocks of the cipher image and then attempt to retrieve the secret data from the defective cipher image through the decryption algorithm. Figure 13 presents the outcomes of data loss attacks, in which the plain image is retrieved effectively from the defective cipher image.
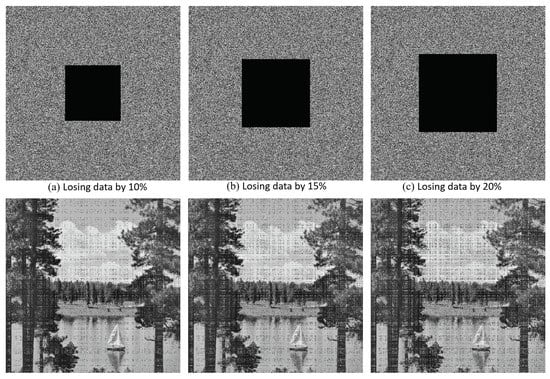
Figure 13.
Results of data loss attacks, in which the Lake image is retrieved effectively from the defective cipher image.
To assess in quantity terms the visual quality of the retrieved images from defected cipher images, we utilized peak signal-to-noise ratio (PSNR) which can be formulated mathematically as stated in Equation (9) []:
where is dimensional of the plain image P, and D indicates the retrieved image from the defective image. The outcomes of PSNR test for the plain Lake image (Figure 9a) and the retrieved images (the second row of Figure 13) are displayed in Table 10. From the outcomes given in Figure 13 and Table 10, it is seen that, when the defective image losses more data, the retrieved image has lost more of its visual quality.
5.3.8. Comparative Analysis
To prove the effectiveness of the presented image cryptosystem alongside other similar image cryptosystems, Table 11 presents a comparison of the average values of information entropy, NPCR, UACI, and correlation coefficients of our encryption system with their average values reported in [,,,,]. From the stated data, we can deduce the efficiency of the proposed image cryptosystem compared to other related approaches.

Table 11.
Comparison of the average values of information entropy, NPCR, UACI, and correlation coefficients of our encryption system with their average values reported in [,,,,].
We can recap the principal advantages of the proposed encryption algorithm as given below:
- According to the data stated in Table 4, the presented cryptosystem has good encryption time besides other related algorithms.
- According to the data stated in Table 5, the correlation coefficients of cipher images are very close to 0, and the proposed cryptosystem has the ability to withstand correlation analysis.
- According to the data stated in Table 6, the proposed cryptosystem is sensitive to slight modifications in the plain image.
- According to the plots stated in Figure 11, the histograms of cipher images are uniform with each other.
- According to the data stated in Table 7, the cipher images have high uniformity of histograms.
- According to the data stated in Table 8, the entropy values for cipher images are near 8, and the proposed cryptosystem has the ability to withstand entropy analysis.
6. Conclusions
Here, a novel chaotic oscillator was proposed, and its dynamical properties were investigated.The chaotic attractor of the system was shown. The oscillator was discussed using bifurcation diagram and Lyapunov exponents. The oscillator has fascinating bifurcations by changing three parameters, a, b and c. Lyapunov exponents of the oscillator were wholly matched with the bifurcation diagrams and present their types of dynamics. In addition, this study introduced various cryptographic applications using the effectiveness of the chaotic flow. A method is presented to construct PRNGs, and the generated PRNG algorithm is utilized for constructing secure S-boxes. Finally, a new image cryptosystem is presented using the proposed PRNG method and the suggested S-box approach. The effectiveness of the suggested mechanisms was evaluated using several assessments, in which the outcomes showed the vital characteristics of the presented mechanisms that are valuable for reliable security purposes. In the future, we aim to study applying the generated sequences from the proposed PRNG algorithm to the auxiliary classifier generative adversarial nets [].
Author Contributions
Conceptualization, A.A.A.E.-L. and J.R.; methodology, B.A.-E.-A. and J.R.; validation, B.A.-E.-A. and F.N.; investigation, A.A.A.E.-L. and H.S.K.; writing—original draft preparation, A.A.A.E.-L., J.R. and B.A.-E.-A.; writing—review and editing, H.S.K., B.A.-E.-A. and F.N.; supervision, H.S.K. and F.N. All authors have read and agreed to the published version of the manuscript.
Funding
This work is supported by the EIAS Data Science Lab, College of Computer and Information Sciences, Prince Sultan University, Riyadh, Saudi Arabia. This work also is funded by the Center for Nonlinear Systems, Chennai Institute of Technology, India, vide funding number CIT/CNS/2022/RP-006.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Data generated during the current study will be made available at reasonable request.
Conflicts of Interest
The authors declare that they have no conflict of interest.
References
- Logrippo, L. Multi-level models for data security in networks and in the Internet of things. J. Inf. Secur. Appl. 2021, 58, 102778. [Google Scholar] [CrossRef]
- Mousavi, S.K.; Ghaffari, A. Data cryptography in the Internet of Things using the artificial bee colony algorithm in a smart irrigation system. J. Inf. Secur. Appl. 2021, 61, 102945. [Google Scholar] [CrossRef]
- Chen, Y.Q.; Sun, W.J.; Li, L.Y.; Chang, C.C.; Wang, X. An efficient general data hiding scheme based on image interpolation. J. Inf. Secur. Appl. 2020, 54, 102584. [Google Scholar] [CrossRef]
- Tsafack, N.; Iliyasu, A.M.; De Dieu, N.J.; Zeric, N.T.; Kengne, J.; Abd-El-Atty, B.; Belazi, A.; Abd EL-Latif, A.A. A memristive RLC oscillator dynamics applied to image encryption. J. Inf. Secur. Appl. 2021, 61, 102944. [Google Scholar] [CrossRef]
- Lin, H.; Wang, C.; Yu, F.; Xu, C.; Hong, Q.; Yao, W.; Sun, Y. An Extremely Simple Multiwing Chaotic System: Dynamics Analysis, Encryption Application, and Hardware Implementation. IEEE Trans. Ind. Electron. 2021, 68, 12708–12719. [Google Scholar] [CrossRef]
- Deng, J.; Zhou, M.; Wang, C.; Wang, S.; Xu, C. Image segmentation encryption algorithm with chaotic sequence generation participated by cipher and multi-feedback loops. Multimed. Tools Appl. 2021, 80, 13821–13840. [Google Scholar] [CrossRef]
- Zhang, X.; Li, C.; Min, F.; Iu, H.H.C.; Gao, H. Broken Symmetry in a Memristive Chaotic Oscillator. IEEE Access 2020, 8, 69222–69229. [Google Scholar] [CrossRef]
- Lorenz, E.N. Deterministic Nonperiodic Flow. J. Atmos. Sci. 1963, 20, 130–141. [Google Scholar] [CrossRef] [Green Version]
- Chen, G.; Ueta, T. Yet Another Chaotic Attractor. Int. J. Bifurc. Chaos 1999, 9, 1465–1466. [Google Scholar] [CrossRef]
- Wei, Z. Dynamical behaviors of a chaotic system with no equilibria. Phys. Lett. A 2011, 376, 102–108. [Google Scholar] [CrossRef]
- Wang, X.; Chen, G. A chaotic system with only one stable equilibrium. Commun. Nonlinear Sci. Numer. Simul. 2012, 17, 1264–1272. [Google Scholar] [CrossRef] [Green Version]
- Danca, M.F.; Kuznetsov, N. Hidden strange nonchaotic attractors. Mathematics 2021, 9, 652. [Google Scholar] [CrossRef]
- Jin, Q.; Min, F.; Li, C. Infinitely many coexisting attractors of a dual memristive Shinriki oscillator and its FPGA digital implementation. Chin. J. Phys. 2019, 62, 342–357. [Google Scholar] [CrossRef]
- Zhou, L.; Wang, C.; Zhou, L. A novel no-equilibrium hyperchaotic multi-wing system via introducing memristor. Int. J. Circuit Theory Appl. 2018, 46, 84–98. [Google Scholar] [CrossRef]
- Zhang, S.; Zheng, J.; Wang, X.; Zeng, Z. Multi-scroll hidden attractor in memristive HR neuron model under electromagnetic radiation and its applications. Chaos 2021, 31, 011101. [Google Scholar] [CrossRef]
- Cai, J.; Bao, H.; Xu, Q.; Hua, Z.; Bao, B. Smooth nonlinear fitting scheme for analog multiplierless implementation of Hindmarsh—Rose neuron model. Nonlinear Dyn. 2021, 104, 4379–4389. [Google Scholar] [CrossRef]
- Gu, S.; He, S.; Wang, H.; Du, B. Analysis of three types of initial offset-boosting behavior for a new fractional-order dynamical system. Chaos Solitons Fractals 2021, 143, 110613. [Google Scholar] [CrossRef]
- Zhang, X.; Lv, X.; Li, X. Sampled-data-based lag synchronization of chaotic delayed neural networks with impulsive control. Nonlinear Dyn. 2017, 90, 2199–2207. [Google Scholar] [CrossRef]
- Takhi, H.; Kemih, K.; Moysis, L.; Volos, C. Passivity based sliding mode control and synchronization of a perturbed uncertain unified chaotic system. Math. Comput. Simul. 2021, 181, 150–169. [Google Scholar] [CrossRef]
- Gholamin, P.; Sheikhani, A.R. A new three-dimensional chaotic system: Dynamical properties and simulation. Chin. J. Phys. 2017, 55, 1300–1309. [Google Scholar] [CrossRef]
- He, S.; Sun, K.; Banerjee, S. Dynamical properties and complexity in fractional-order diffusionless Lorenz system. Eur. Phys. J. Plus 2016, 131. [Google Scholar] [CrossRef]
- Ghosh, D.; Chowdhury, A.R.; Saha, P. Multiple delay Rossler system-Bifurcation and chaos control. Chaos Solitons Fractals 2008, 35, 472–485. [Google Scholar] [CrossRef]
- Rajagopal, K.; Nazarimehr, F.; Guessas, L.; Karthikeyan, A.; Srinivasan, A.; Jafari, S. Analysis, Control and FPGA Implementation of a Fractional-Order Modified Shinriki Circuit. J. Circuits, Syst. Comput. 2019, 28, 1950232. [Google Scholar] [CrossRef]
- Rajagopal, K.; Kingni, S.T.; Khalaf, A.J.M.; Shekofteh, Y.; Nazarimehr, F. Coexistence of attractors in a simple chaotic oscillator with fractional-order-memristor component: Analysis, FPGA implementation, chaos control and synchronization. Eur. Phys. J. Spec. Top. 2019, 228, 2035–2051. [Google Scholar] [CrossRef]
- Ghosh, D.; Chowdhury, A.R.; Saha, P. Bifurcation continuation, chaos and chaos control in nonlinear Bloch system. Commun. Nonlinear Sci. Numer. Simul. 2008, 13, 1461–1471. [Google Scholar] [CrossRef]
- Ahmad, W.M.; Sprott, J. Chaos in fractional-order autonomous nonlinear systems. Chaos Solitons Fractals 2003, 16, 339–351. [Google Scholar] [CrossRef] [Green Version]
- Prakash, P.; Rajagopal, K.; Singh, J.; Roy, B. Megastability in a quasi-periodically forced system exhibiting multistability, quasi-periodic behaviour, and its analogue circuit simulation. AEU-Int. J. Electron. Commun. 2018, 92, 111–115. [Google Scholar] [CrossRef]
- Ray, A.; Ghosh, D.; Chowdhury, A.R. Topological study of multiple coexisting attractors in a nonlinear system. J. Phys. Math. Theor. 2009, 42, 385102. [Google Scholar] [CrossRef]
- Li, C.; Lu, T.; Chen, G.; Xing, H. Doubling the coexisting attractors. Chaos 2019, 29, 051102. [Google Scholar] [CrossRef]
- Chen, M.; Feng, Y.; Bao, H.; Bao, B.; Wu, H.; Xu, Q. Hybrid State Variable Incremental Integral for Reconstructing Extreme Multistability in Memristive Jerk System with Cubic Nonlinearity. Complexity 2019, 2019, 8549472. [Google Scholar] [CrossRef] [Green Version]
- Chen, M.; Sun, M.; Bao, H.; Hu, Y.; Bao, B. Flux Charge Analysis of Two-Memristor-Based Chuas Circuit: Dimensionality Decreasing Model for Detecting Extreme Multistability. IEEE Trans. Ind. Electron. 2020, 67, 2197–2206. [Google Scholar] [CrossRef]
- Bao, H.; Chen, M.; Wu, H.; Bao, B. Memristor initial-boosted coexisting plane bifurcations and its extreme multi-stability reconstitution in two-memristor-based dynamical system. Sci. China Technol. Sci. 2019, 63, 603–613. [Google Scholar] [CrossRef]
- El-Latif, A.A.A.; Abd-El-Atty, B.; Amin, M.; Iliyasu, A.M. Quantum-inspired cascaded discrete-time quantum walks with induced chaotic dynamics and cryptographic applications. Sci. Rep. 2020, 10, 1930. [Google Scholar] [CrossRef] [PubMed]
- Tsafack, N.; Kengne, J.; Abd-El-Atty, B.; Iliyasu, A.M.; Hirota, K.; EL-Latif, A.A.A. Design and implementation of a simple dynamical 4-D chaotic circuit with applications in image encryption. Inf. Sci. 2020, 515, 191–217. [Google Scholar] [CrossRef]
- Nazarimehr, F.; Jafari, S.; Chen, G.; Kapitaniak, T.; Kuznetsov, N.V.; Leonov, G.A.; Li, C.; Wei, Z. A tribute to JC Sprott. Int. J. Bifurc. Chaos 2017, 27, 1750221. [Google Scholar] [CrossRef]
- Faghani, Z.; Nazarimehr, F.; Jafari, S.; Sprott, J.C. Simple chaotic systems with specific analytical solutions. Int. J. Bifurc. Chaos 2019, 29, 1950116. [Google Scholar] [CrossRef]
- Wolf, A.; Swift, J.B.; Swinney, H.L.; Vastano, J.A. Determining Lyapunov exponents from a time series. Phys. Nonlinear Phenom. 1985, 16, 285–317. [Google Scholar] [CrossRef] [Green Version]
- Farhan, A.K.; Al-Saidi, N.M.; Maolood, A.T.; Nazarimehr, F.; Hussain, I. Entropy analysis and image encryption application based on a new chaotic system crossing a cylinder. Entropy 2019, 21, 958. [Google Scholar] [CrossRef] [Green Version]
- Rajagopal, K.; Akgul, A.; Pham, V.T.; Alsaadi, F.E.; Nazarimehr, F.; Alsaadi, F.E.; Jafari, S. Multistability and coexisting attractors in a new circulant chaotic system. Int. J. Bifurc. Chaos 2019, 29, 1950174. [Google Scholar] [CrossRef]
- EL-Latif, A.A.A.; Abd-El-Atty, B.; Venegas-Andraca, S.E. Controlled alternate quantum walk-based pseudo-random number generator and its application to quantum color image encryption. Phys. Stat. Mech. Its Appl. 2020, 547, 123869. [Google Scholar] [CrossRef]
- Wu, X.; Wang, K.; Wang, X.; Kan, H.; Kurths, J. Color image DNA encryption using NCA map-based CML and one-time keys. Signal Process. 2018, 148, 272–287. [Google Scholar] [CrossRef]
- Meranza-Castillón, M.; Murillo-Escobar, M.; López-Gutiérrez, R.; Cruz-Hernández, C. Pseudorandom number generator based on enhanced Hénon map and its implementation. AEU-Int. J. Electron. Commun. 2019, 107, 239–251. [Google Scholar] [CrossRef]
- Zhao, Y.; Gao, C.; Liu, J.; Dong, S. A self-perturbed pseudo-random sequence generator based on hyperchaos. Chaos Solitons Fractals X 2019, 4, 100023. [Google Scholar] [CrossRef]
- El-Latif, A.A.A.; Abd-El-Atty, B.; Belazi, A.; Iliyasu, A.M. Efficient Chaos-Based Substitution-Box and Its Application to Image Encryption. Electronics 2021, 10, 1392. [Google Scholar] [CrossRef]
- Belazi, A.; Abd El-Latif, A.A.; Diaconu, A.V.; Rhouma, R.; Belghith, S. Chaos-based partial image encryption scheme based on linear fractional and lifting wavelet transforms. Opt. Lasers Eng. 2017, 88, 37–50. [Google Scholar] [CrossRef]
- Khan, M.; Asghar, Z. A novel construction of substitution box for image encryption applications with Gingerbreadman chaotic map and S 8 permutation. Neural Comput. Appl. 2018, 29, 993–999. [Google Scholar] [CrossRef]
- Belazi, A.; Khan, M.; Abd El-Latif, A.A.; Belghith, S. Efficient cryptosystem approaches: S-boxes and permutation-substitution-based encryption. Nonlinear Dyn. 2017, 87, 337–361. [Google Scholar] [CrossRef]
- Li, L.; Abd El-Latif, A.A.; Jafari, S.; Rajagopal, K.; Nazarimehr, F.; Abd-El-Atty, B. Multimedia Cryptosystem for IoT Applications Based on a Novel Chaotic System around a Predefined Manifold. Sensors 2022, 22, 334. [Google Scholar] [CrossRef]
- Alanezi, A.; Abd-El-Atty, B.; Kolivand, H.; El-Latif, A.A.A.; El-Rahiem, B.A.; Sankar, S.; Khalifa, H.S. Securing Digital Images through Simple Permutation-Substitution Mechanism in Cloud-Based Smart City Environment. Secur. Commun. Netw. 2021, 2021, 6615512. [Google Scholar] [CrossRef]
- Liu, L.; Jiang, D.; Wang, X.; Rong, X.; Zhang, R. 2D Logistic-Adjusted-Chebyshev map for visual color image encryption. J. Inf. Secur. Appl. 2021, 60, 102854. [Google Scholar] [CrossRef]
- Khan, J.S.; Kayhan, S.K. Chaos and compressive sensing based novel image encryption scheme. J. Inf. Secur. Appl. 2021, 58, 102711. [Google Scholar] [CrossRef]
- Kang, Y.; Huang, L.; He, Y.; Xiong, X.; Cai, S.; Zhang, H. On a symmetric image encryption algorithm based on the peculiarity of plaintext DNA coding. Symmetry 2020, 12, 1393. [Google Scholar] [CrossRef]
- Cai, S.; Huang, L.; Chen, X.; Xiong, X. A symmetric plaintext-related color image encryption system based on bit permutation. Entropy 2018, 20, 282. [Google Scholar] [CrossRef] [Green Version]
- Huang, L.; Li, W.; Xiong, X.; Yu, R.; Wang, Q.; Cai, S. Designing a double-way spread permutation framework utilizing chaos and S-box for symmetric image encryption. Opt. Commun. 2022, 517, 128365. [Google Scholar] [CrossRef]
- Ye, G.; Pan, C.; Huang, X.; Zhao, Z.; He, J. A chaotic image encryption algorithm based on information entropy. Int. J. Bifurc. Chaos 2018, 28, 1850010. [Google Scholar] [CrossRef]
- Wang, X.; Feng, L.; Zhao, H. Fast image encryption algorithm based on parallel computing system. Inf. Sci. 2019, 486, 340–358. [Google Scholar] [CrossRef]
- Gan, Z.H.; Chai, X.L.; Han, D.J.; Chen, Y.R. A chaotic image encryption algorithm based on 3D bit-plane permutation. Neural Comput. Appl. 2019, 31, 7111–7130. [Google Scholar] [CrossRef]
- Lawnik, M.; Berezowski, M. New Chaotic System: M-Map and Its Application in Chaos-Based Cryptography. Symmetry 2022, 14, 895. [Google Scholar] [CrossRef]
- Murillo-Escobar, M.A.; Cruz-Hernández, C.; Abundiz-Pérez, F.; López-Gutiérrez, R.M.; Del Campo, O.A. A RGB image encryption algorithm based on total plain image characteristics and chaos. Signal Process. 2015, 109, 119–131. [Google Scholar] [CrossRef]
- Bao, H.; Hua, Z.; Li, H.; Chen, M.; Bao, B.C. Memristor-based hyperchaotic maps and application in AC-GANs. IEEE Trans. Ind. Inf. 2021, 18, 5297–5306. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).