Abstract
The Rivest–Shamir–Adleman (RSA) cryptosystem is currently the most influential and commonly used algorithm in public-key cryptography. Whether the security of RSA is equivalent to the intractability of the integer factorization problem is an interesting issue in mathematics and cryptography. Coron and May solved the above most fundamental problem and proved the polynomial-time equivalence of computing the RSA secret key and factoring. They demonstrated that the RSA modulus can be factored in polynomial time when given RSA key information . The CRT-RSA variant is a fast technical implementation of RSA using the Chinese Remainder Theorem (CRT), which aims to speed up the decryption process. We focus on the polynomial-time equivalence of computing the CRT-RSA secret key and factoring in this paper. With the help of the latest partial key exposure attack on CRT-RSA, we demonstrate that there exists a polynomial-time algorithm outputting the factorization of for when given the CRT-RSA key information . We apply Coppersmith’s lattice-based method as a basic mathematical tool for finding the small root solutions of modular polynomial equations. Furthermore, we provide validation experiments to illustrate the correctness of the CRT-RSA modulus factorization algorithm, and show that computing the CRT-RSA secret key and factoring its modulus is polynomial-time equivalent by using concrete numerical examples.
MSC:
94A60
1. Introduction
Rivest, Shamir, and Adleman proposed the first practical public-key cryptosystem named the RSA algorithm [1]. This algorithm just involves the elementary number-theoretic operations and is easy to compute and implement. Thus, RSA is widely studied in the field of information security and serves as an influential public-key cryptographic algorithm utilized by international standardization organizations. The RSA cryptosystem consists of a key generation algorithm, an encryption algorithm, and a decryption algorithm, which are described as follows.
- Key Generation.
- Randomly select two prime numbers of the same bit-size and compute the modulus along with its Euler’s totient function . Randomly select satisfying as the public key and compute as the private key.
- Encryption.
- Alice transforms a plaintext message into and computes as the corresponding ciphertext.
- Decryption.
- Bob receives a ciphertext c and calculates . Bob extracts the transformed m and recovers the original plaintext message.
The correctness of the encryption and decryption algorithms is ensured by Euler’s Totient Theorem. Since both the public key e and the private key d are calculated in the exponent position, they are mentioned as the public and private exponents, respectively.
The hardness assumption of the RSA algorithm is the intractability of the integer factorization problem [2]. There is still no known polynomial-time algorithm that can factor sufficiently large integers using current classical computers. So there is no known effective attack against the RSA algorithm. However, on the other hand, RSA with small private exponents have been proven to be insecure when using Wiener’s continued fraction-based attack [3] and Coppersmith’s lattice-based attack [4]. A series of cryptanalytic researches on RSA and its variants were subsequently developed based on the lattice-based method, see the literature [5,6,7,8,9,10,11,12]. One of these works related to the hardness assumption of RSA is the polynomial-time equivalence proof of computing the RSA secret key and factoring [8,13]. The main contribution is applying the lattice-based method to prove that there exists an algorithm that can output the factorization of the modulus in polynomial time when given .
In fact, in the public key cryptography standard PKCS #1 [14], the CRT-RSA algorithm is a fast technical implementation of RSA. Here CRT-RSA refers to the RSA variant using the Chinese Remainder Theorem, which was proposed in [15]. The Chinese Remainder Theorem formulates the solution to simultaneous linear congruences and is specified as follows.
Theorem 1.
Let be mutually coprime positive integers, and let be integers. Then the following system of linear congruences
has a unique solution in the sense of modulo . Let for , then the unique solution is
Since the RSA modulus is the product of two prime numbers, we consider the case of , i.e., the system of linear congruences is and . In this case, the solution expression is more concise.
For a ciphertext , the decryption algorithm works in the following strategy. One first does a partial decryption operation to recover , , and then use the Chinese Remainder Theorem to combine the above two parts to recover m. Since p and q are coprime, one applies the Formula (1) that yields
It can be further simplified as
Let and , by Fermat’s Little Theorem we have
Thus, are called CRT exponents and used as private exponents instead of d. The above Formula (2) is known as Garner’s algorithm [16]. Theoretically speaking, the decryption efficiency of the modular operations can be accelerated by a factor of four due to the reduction of the modulus from N to p or q. We summarize the CRT-RSA cryptosystem as follows.
- Key Generation.
- Randomly select two prime numbers of the same bit-size and compute the modulus and its Euler’s totient function . Randomly select satisfying as the public key and compute , as the private key.
- Encryption.
- Alice transforms a plaintext message into and computes as the corresponding ciphertext.
- Decryption.
- Bob receives a ciphertext c and calculates . Bob extracts and recovers the original plaintext message.
Cryptanalysis of the CRT-RSA algorithm also attracts many researchers. The small CRT-exponent attack was originally presented as an open problem in Wiener’s attack [3]. The first cryptanalytic result was given in [6], which was effective for unbalanced primes p and q. Subsequently, Jochemsz and May [17] proposed the small CRT-exponent attack for balanced primes when the attack range is . It was further improved to in [12] and shortly afterwards to [18]. In addition, the partial-key-exposure attacks such as [19,20,21,22,23] were studied due to the consideration of partial leakage of the CRT-RSA private key. From the implementation aspect, side-channel attacks such as [24,25,26,27,28] were proposed by exploiting the side-channel information leakage during the running process of the CRT-RSA algorithm.
Unlike the above attacks, we focus on the intrinsic security of CRT-RSA, i.e., its mathematical hardness assumption. From the theoretical research aspect, it is interesting to investigate the polynomial-time equivalence of computing the CRT-RSA secret key and factoring its modulus. Therefore, the research problem is stated as follows.
If the CRT-RSA key information is given as input, does there exist a polynomial-time algorithm that can output the factorization of N? Furthermore, is it possible that the CRT-exponents reach the natural constraint for ?
It is well known that and can be efficiently inferred from the factorization of and the public exponent e. Hence, it suffices to show that the above problem is solvable to conclude that computing the CRT-RSA secret key and factoring the modulus are polynomial-time equivalent. Our main goal is to demonstrate and design a polynomial-time algorithm outputting the factorization of N for given CRT-RSA key information . The specific goal is to further enlarge the attack range of CRT exponents . We study how to use improved analysis techniques to carry out attacks on CRT-RSA from the perspective of its intrinsic security, namely the polynomial-time equivalence of computing the CRT-RSA secret key and factoring its modulus.
Inspired by the latest partial key exposure attack on CRT-RSA [23], we show an optimized polynomial-time equivalence of computing the CRT-RSA secret key and factoring. To be specific, we give a positive answer to the above research problem based on the partial key exposure attack on CRT-RSA. A polynomial-time factoring algorithm is presented for the given CRT-RSA key information , which outputs the factorization result of . Technically speaking, the factoring algorithm involves an error term for . This term may equal to , which is negligible compared to in the most favorable case, and asymptotically leads to the natural constraint for . Moreover, we provide validation experiments in the form of numerical examples.
Our contribution mainly includes a new factoring algorithm and an improved attack result, which are summarized as follows.
- We study the security of CRT-RSA concerning its mathematical hardness assumption and propose an improved polynomial-time algorithm of factoring the CRT-RSA modulus.
- We verify the correctness and validity of the proposed CRT-RSA modulus factorization algorithm with numerical computer experiments and always successfully obtain the factorization results.
- We further discuss the advantages and disadvantages of our approach with several comparisons to properly assess the proposed factoring attack.
The rest of this paper is organized as follows. Section 2 introduces the lattice-based method, which is used as a basic mathematical tool to solve the research problem. Section 3 first reviews the latest partial key exposure attack on CRT-RSA and gives a refined theorem with more flexible parameters. Then we propose an improved polynomial-time equivalence of computing the CRT-RSA secret key and factoring. Both the CRT-RSA key computation algorithm and the CRT-RSA modulus factorization algorithm are presented. Finally, the validation experiments are provided in the form of numerical examples. We compare our results with previous studies and discuss the advantages and disadvantages of the proposed algorithms in Section 4. Section 5 concludes this paper.
2. Materials and Methods
We introduce the lattice-based method, which consists of the lattice reduction algorithm [29] and Coppersmith’s techniques [4]. Generally speaking, a lattice is a discrete additive subgroup in that is defined as follows.
Definition 1.
Let and be a set of linearly independent vectors. The lattice generated by is the set containing all linear combinations of the vectors with integer coefficients.
The vector set is called a basis of the lattice . Further, n is the lattice dimension, ω is the lattice rank, and is full-rank if . For , each basis vector can be written as in the form of row vectors, thus forming a basis matrix .
Definition 2.
The fundamental parallelepiped of is defined as , where is any basis matrix of the lattice . The lattice determinant is defined as the volume of the fundamental parallelepiped.
where is the transpose matrix of . Thus, it follows that the determinant of a full-rank lattice is
where is the determinant of the basis matrix .
The lattice determinant does not depend on a particular basis matrix since it is an invariant of the lattice itself. A lattice can usually be generated by many different basis matrices. More concretely, any two basis matrices of the same lattice can be converted to each other using a unimodular matrix. Unless otherwise specified, the lattices in this paper are full-rank.
The famous Lenstra–Lenstra–Lovász (LLL) lattice reduction algorithm was proposed in [29]. Though this algorithm cannot directly output the shortest lattice vector, it outputs the approximately shortest basis vectors in polynomial time. In other words, the length of the output vectors does not exceed a certain multiple of the shortest vector, and the LLL algorithm usually works better in practice. The works [29,30] show the following lemma for the upper bound estimation of the approximately shortest vectors output by the LLL algorithm.
Lemma 1
(LLL). Let be a set of basis vectors output by the LLL algorithm running on the lattice . We have
Its time complexity is that is polynomial in the lattice dimension ω and the length of the input vectors B.
Coppersmith presented how to solve modular or integer polynomial equations based on the LLL algorithm [31,32]. The core idea is to construct solvable equations over the integers, which are represented as short basis vectors in the lattice. Meanwhile, the short basis vectors can be efficiently found by the LLL algorithm.
We describe the specific problem of solving modular polynomial equations as follows. Let R be a known positive integer, and let be a multivariate polynomial. The goal is to find small root solutions of , i.e., to solve under , where is the upper bound on the absolute value of the variable related to the small root solution. It is required is to maximize the upper bound on the unknown variables, while keeping the time complexity polynomial in the input parameters.
Before describing the strategy of solving modular polynomial equations, we define the polynomial norm. For a certain k-variable polynomial , the non-zero coefficients are related to the corresponding monomials . The polynomial norm is defined as follows.
Definition 3.
Let with be a k-variable polynomial. Its norm is defined as
Howgrave-Graham [33] further improved on Coppersmith’s original techniques. The following lemma is used for determining whether the small root solution of a modular polynomial equation also holds on the integers, i.e., whether the modular condition can be eliminated.
Lemma 2
(Howgrave-Graham). Let be a k-variable integer polynomial containing ω monomials. When the following conditions are satisfied, also holds over the integers.
- 1.
- ,
- 2.
- .
The basic idea of solving k-variable polynomials is to construct algebraically with independent polynomials sharing the same small root over the integers. Hence, one can extract the final solution by the Gröbner basis computation [34]. By applying Lemma 2, the problem of solving modular polynomial equations can be turned to solving integer equations. Further, by combining Lemma 1, one can solve a given modular polynomial equation under certain conditions. The lattice-based method constructs a set of shift polynomials sharing the same root modulo R and then transforms the derived polynomials into integer equations in a specific way. Technically speaking, a lattice-basis matrix is generated from the coefficient vectors of the shift polynomials, which spans an -dimensional lattice. The LLL algorithm is applied to obtain the approximately shortest basis vectors, which are later transformed into polynomial equations. If the corresponding polynomial norm is small enough, then the derived equation also holds over the integers. We summarize the process of solving k-variable polynomial equations using the lattice-based method as follows.
- The first step is to construct the set of shift polynomials for given modular polynomials containing k unknown variables and a given modulus M. For and , the basic form of a shift polynomial is defined asThus, all polynomials in have the same root , where the modulus is .
- The second step is to use denoting the row vector transformed from the coefficient vectors of the shift polynomial when substituting for . The lattice is constructed by the lattice basis matrix . Then apply the LLL algorithm to the lattice and extract the first ℓ many approximately shortest vectors from the output. The output vectors are transformed into a system of integer equations , whose roots also hold over the integers.
- The third step is extract the desired small root solution. If the derived polynomials are mutually algebraically independent, the system of integer equations can be solved by applying the Gröbner basis computation. At this point, the small root solution of the original modular polynomials is obtained.
When obtaining the first ℓ number of basis vectors using the LLL algorithm, to ensure that the polynomial equations related to the basis vectors satisfy the solvable conditions, we have . Since we always have , the following simplified condition is obtained by omitting the lower error terms,
To make the lattice determinant easy to compute, it is generally required that the basis matrix is of lower or upper triangular form. Therefore, during the construction of shift polynomials, it is necessary to ensure that each new shift polynomial introduces exactly one new monomial . Hence, the lattice determinant is calculated by accumulating the monomials on the diagonal of the lattice basis matrix. We have .
The solution of multivariate polynomials using the lattice-based method is heuristic, so we note that its feasibility relies on the following heuristic assumption. Although the LLL algorithm guarantees that the reduced basis vectors are linearly independent, it cannot guarantee the algebraic independence of the transformed polynomials. On the other hand, similar to other cryptanalytic researches on RSA and its variants using the lattice-based method, the following assumption always holds in the validation experiments.
Assumption 1.
The system of integer equations related to the approximately shortest basis vectors output by the LLL algorithm can be efficiently solved. The small root solution can be extracted in polynomial time by the Gröbner basis computation.
3. Results
We aim to propose a polynomial-time algorithm outputting the factorization of N for given CRT-RSA key information by using the latest partial key exposure attack. To do so, we modify solving the factoring problem into conducting the partial key exposure attack. In other words, we extract two primes p and q for known LSB components of the CRT-exponents (i.e., the LSB components are exactly themselves if let the MSB components be 0). We follow the lattice-based method and briefly review the partial key exposure attack on CRT-RSA.
The partial key exposure attack on CRT-RSA [23] implicitly shows the existence of a factoring algorithm, which takes given CRT-RSA key information as input and outputs the factorization of for and . Therefore, we explicitly design a polynomial-time algorithm that outputs the factorization of N for and . From a mathematical standpoint, we simplify the complicated and redundant attack analysis in [23] and further present a refined theorem in order to fit the factoring problem on CRT-RSA. To be specific, we concentrate on the error term that appears in the mathematical derivation process. We carefully analyze and reduce the influence of this error term and hence obtain attack results that are better than previous studies [23,35].
3.1. Partial Key Exposure Attack on CRT-RSA
Recently, May, Nowakowski, and Sarkar [23] proposed an improved partial key exposure attack on CRT-RSA, which is based on the small CRT exponent attack working for of [18]. This attack applies to the range , which smoothly covers the full interval of the CRT exponents. Let be the CRT-RSA modulus, where p and q are prime numbers of the same bit-size. Assume that the public exponent is , the CRT-exponents are . The CRT-exponents can be written as , where and the LSB components are known, whereas the MSB components are unknown. Then, there exists a polynomial-time algorithm that outputs the secret information using the given partial key exposure.
According to and , we have
for two positive integers . Since the sizes of e, , , p, and q are known, the upper bounds on k and ℓ are estimated as
Applying the Formula (4), we have , whose root is . In addition, multiplying the Formula (5) by p and rearranging it gives
Similarly, we have , whose root is . Moreover, the Equations (4) and (5) can be rewritten as and . Multiplying them together gives , and we obtain
Therefore, we have , whose root is . Combining the above modular polynomials, we obtain the following system of polynomial equations,
Their common root is .
Considering the special algebraic relationship between the unknown variables, we use six variables, namely instead of three variables. In this case, the relevant elements in certain monomials of the original polynomials need to be converted algebraically as follows.
Thus, we obtain linear polynomials after the conversion,
Combining known values and , the polynomials involved in the partial key exposure attack are as follows.
The root is , and the corresponding upper bounds are and .
We apply the lattice-based method to extract . The first step is to construct the shift polynomials. Before that, we need to define the monomial set, whose elements are contained in the shift polynomials. The monomial set is closely related to the columns of the lattice basis matrix in the second step, and directly affects the alignment of the matrix rows.
Definition 4.
Let . The monomial set is defined as
To facilitate the exposition of the lattice construction, it is additional to define as
Furthermore, is partitioned using five disjoint subsets as follows.
The shift functions and the corresponding shift polynomials are defined based on the monomial sets and .
Definition 5.
The shift functions are defined as follows.
For a given monomial , the corresponding shift polynomial is determined as
It is known that all the shift polynomials have the common root . The shift polynomials are further adapted by using the algebraic relation Formula (7). We construct the updated shift polynomials under the following induced transformation rules.
Definition 6.
Let u be a polynomial defined over . is defined as the updated polynomial after the following transformation rules.
- 1.
- For all monomials, are converted to N,
- 2.
- For monomials without , are converted to and are converted to ,
- 3.
- For monomials with , are converted to and are converted to .
- Thus, contains only monomials of the form and , i.e., variables with subscripts p and q do not appear in a monomial at the same time.
The second step is to construct the lattice-basis matrix . To do this, we need to define the monomial order and the polynomial order, which are used to arrange the order of columns and rows in the lattice-basis matrix. When we generate the lattice-basis matrix, a polynomial is first multiplied by some extra variables and then transformed by Definition 6. Finally, the upper bounds on the unknown variables are substituted and the polynomials are arranged in a one-to-one correspondence with the monomial order.
Definition 7.
The monomial order is defined as follows.
The lattice basis matrix and the polynomial order (namely the matrix row) are defined in the following way. The i-th column is related to the monomial , which is for even b and for odd b. The parameters are taken from the i-th smallest monomial in . For , the i-th row is associated with the coefficient vector of polynomial . For with even b, the i-th row takes . For with odd b, it takes . Then the lattice basis matrix is lower triangular.
We then apply the lattice reduction algorithm to generated by the basis matrix . The first few approximately shortest basis vectors of the output are converted to polynomial form , which make up the system of integer equations . The third step is to solve the above system of integer equations. We apply the Gröbner basis computation to extract . At this point, we finally obtain the secret information p and q. Under the above lattice-based solution process, we present the following theorem.
Theorem 2.
Let be a sufficiently large CRT-RSA modulus, where p and q are prime numbers of the same bit-size. Assume that the public exponent is , the CRT exponents are . The CRT exponents are written as and , where and the LSB components are known, whereas the MSB components are unknown. Then given and ensuring , if the condition
holds then p and q can be computed in polynomial time in .
Proof.
We construct the lattice-basis matrix and generate the -dimensional full-rank lattice . Hence, each diagonal element of contains the powers of , X, Y, and N, , which are expressed as
To simplify the computation of the lattice determinant, we should multiply the polynomials of the rows by the following appropriate multiplicative inverse
to eliminate the effect of powers of N and . The updated diagonal elements are . Meanwhile, the root solution remains . Since it is assumed that in the most favorable case, its influence can be ignored. The lattice determinant is calculated asymptotically as , where the corresponding exponents are calculated as follows.
On the other hand, the dimension of the lattice is
We apply the condition (3), i.e., . By substituting , , and , we have
After simplification, we obtain . The running time mainly depends on the LLL algorithm, while the running time of the Gröbner basis computation is negligible in comparison. Thus, its time complexity is . Because m is a fixed number for generating the lattice, the time complexity is polynomial in . □
We elaborate on the details of the lattice-basis matrix in the partial key exposure attack on CRT-RSA and present the specific attack algorithm. Furthermore, to understand Theorem 2 and the order of columns and rows in the lattice construction more intuitively, we give a toy example of the lattice basis matrix for .
Example 1.

According to Definition 7, the lattice basis matrix for is shown in Table 1, where and are the derived polynomials to be solved.

Table 1.
A toy example of the lattice basis matrix for .
It is clear that the lattice basis matrix is indeed a lower triangular matrix, and that each new shift polynomial introduces only one new monomial .
We present the partial key exposure attack on CRT-RSA in Algorithm 1, which is denoted by .
| Algorithm 1 The partial key exposure attack algorithm . | |
| |
| {construct the monomial set} |
| {generate shift exponents} |
| |
| {generate the lattice basis matrix} |
| {compute reduced basis vectors} |
| {construct the equation system} |
| {extract the desired root} |
| |
3.2. Polynomial Time Equivalence of Computing the CRT-RSA Secret Key and Factoring
We show an explicit demonstration on the polynomial-time equivalence of computing the CRT-RSA secret key and factoring by invoking the partial key exposure attack algorithm . It is specified in the following theorem.
Theorem 3.
Let be a sufficiently large CRT-RSA modulus, where p and q are prime numbers of the same bit size. Let e be the public exponent and be the corresponding CRT-exponents. Then the following statements hold under the condition and ensuring .
- Given , and can be computed in polynomial time,
- Given , p and q can be computed in polynomial time.
When is close to the CRT-RSA modulus, the CRT-exponents satisfies the natural constraint (or ).
Note that the error term is derived from the proof of Theorem 2. To simplify the lattice determinant computation, we multiply each row polynomial by an appropriate multiplicative inverse, i.e., (11) to eliminate the effect of powers of N and . However, is at least equal to 2 and hence its influence cannot be completely eliminated. We further check whether the assumption holds in Section 4. From an algorithmic perspective, this error term affects the computation efficiency. To achieve the same attacking effect, a larger error term requires lattices with higher dimension and hence the corresponding factoring attack takes more time.
Proof.
We divide the proof into two parts. One part proves that knowing is sufficient to compute and in polynomial time. The other part proves that known is sufficient to compute p and q in polynomial time. According to the key generation algorithm, we have , . When is known, the values of and can be computed by applying the extended Euclidean algorithm. It is shown in Algorithm 2 and denoted by .
| Algorithm 2 The CRT-RSA key computation algorithm |
|
It is known that the time complexity of the modular inverse computation is , so the CRT-RSA secret key computation algorithm can be done in polynomial time. To prove that knowing is sufficient to compute p and q in polynomial time, we slightly modify the original problem into the form of the partial key exposure attack on CRT-RSA. Denoting and letting , we have leaked LSBs . By calling the partial key exposure attack algorithm , we can extract p and q in polynomial time. The specific algorithm is shown in Algorithm 3 and denoted by .
| Algorithm 3 The CRT-RSA modulus factorization algorithm | |
| |
| {construct the monomial set} |
| {generate shift exponents} |
| |
| {generate the lattice basis matrix} |
| {compute reduced basis vectors} |
| {construct the equation system} |
| {extract the desired root} |
| |
The time complexity of the CRT-RSA modulus factorization algorithm depends mainly on the partial key exposure attack, which can be done in according to Theorem 2. Thus, runs in polynomial time in . However, Algorithm 3 partially answers the research problem. It remains to show that the CRT exponents satisfy the natural constraint, i.e., for . For this purpose, we further apply the judgment condition (10) in Theorem 2. Assume that , , , the partial key exposure attack on CRT-RSA works if
In Algorithm 3, we have the implication , which shows that
Hence, it follows that , i.e., . The CRT-RSA modulus factorization algorithm is feasible for , and the CRT-exponents are in the range of . So far, our research goal is achieved. □
3.3. Validation Experiments
We implement the CRT-RSA key computation algorithm and the CRT-RSA modulus factorization algorithm based on SageMath [36]. The experimental platform is a personal computer running Windows 10 with Intel(R) Core(TM) i5-10500 CPU 3.10 GHz and 8 GB RAM. All numbers in the validation experiments are randomly selected. We summarize the experimental results as follows. The CRT-RSA key computation algorithm outputs the modular inverse values and quite efficiently. The CRT-RSA modulus factorization algorithm runs with enough integer equations for solving the unknown variables and finally factors the modulus N. To be specific, after running the LLL algorithm, we can obtain a sufficient number of approximately shortest basis vectors to meet the requirements in the lattice-based method. The desired root can be efficiently extracted by transforming the lattice vectors into a system of integer equations and then applying the Gröbner basis computation.
As the CRT-RSA key computation algorithm is a direct call to the extended Euclidean algorithm, we focus on the CRT-RSA modulus factorization algorithm. In the experiments, we first choose an appropriate m to control the construction of the shift polynomials. We then construct the lattice basis matrix and the -dimensional full-rank lattice . The LLL algorithm is applied to , and we transform the first few output vectors into a system of integer equations. We finally solve the system of integer equations using the Gröbner basis computation and extract the desired root.
The detailed experimental results are given in Table 2. The column provides the bit size of the CRT-RSA modulus of the generated instance. The column provides the bit size of the public exponent e. The column provides the bit size of the CRT exponents in our attacks. The lattice settings for conducting the factoring algorithms are indicated by the m and columns. The time consumption (recorded in seconds) of the LLL algorithm and the Gröbner basis computation are given in the Time-column. Two particular numerical CRT-RSA examples are given in Examples 2 and 3.

Table 2.
Experimental results of our proposed factoring attack on CRT-RSA.
Example 2.
In order to check the correctness and validity of the CRT-RSA modulus factorization algorithm, we choose the following specific parameters and generate the test example.
- 1.
- Randomly generate 512-bit prime numbers p, q and the modulus ,
- 2.
- Randomly generate 103-bit CRT exponents and ,
- 3.
- Generate the public exponent e based on above p, q and , ,
- 4.
- Denote the CRT-RSA key information as .
The values of the numerical CRT-RSA example are as follows.
In the CRT-RSA modulus factorization algorithm , we choose , which means that we need to apply the LLL algorithm to the lattice with . After running for almost 84221 s, the approximately shortest basis vectors that meet the solvable condition are obtained. The system of integer equations to be solved is then derived by transforming vectors into polynomials. We finally solve it by applying the Gröbner basis computation in less than one second and recover
One may check that does hold, so the CRT-RSA modulus factorization algorithm successfully outputs the factorization of .
To show that the CRT-RSA key computation algorithm also runs in polynomial time, we use the above CRT-RSA example and apply extended Euclidean algorithm. It runs in less than one second and outputs
Example 3.
In order to further check the correctness and validity of the CRT-RSA modulus factorization algorithm for smaller e and larger CRT exponents, we choose the following specific parameters and generate the test example.
- 1.
- Randomly generate 512-bit prime numbers p, q, and the modulus ,
- 2.
- Randomly generate 200-bit public exponent e,
- 3.
- Generate 768-bit CRT-exponents and based on above p, q, and e,
- 4.
- Denote the CRT-RSA key information as .
The values of the numerical CRT-RSA example are as follows.
In the CRT-RSA modulus factorization algorithm , we choose , which means that we need to apply the LLL algorithm to the lattice with . After running for almost 2482 s, the approximately shortest basis vectors that meet the solvable condition are obtained. The system of integer equations to be solved is then derived by transforming vectors into polynomials. We finally solve it by applying the Gröbner basis computation in less than one second and recover
One may check that does hold, so the CRT-RSA modulus factorization algorithm successfully outputs the factorization of .
To show that the CRT-RSA key computation algorithm also runs in polynomial time, we use the above CRT-RSA example and apply extended Euclidean algorithm. It runs in less than one second and outputs and .
4. Discussion
To solve the proposed research problem, we apply the lattice-based method and present an improved CRT-RSA modulus factorization algorithm in Section 3.2. The correctness and validity of our factoring algorithm have been verified in Section 3.3. Our validation experiments always output the desired modulus factorization for small CRT-exponents. The running time depends on the particular lattice dimension and is in the range of 1 s to s. Hence, the accuracy and speed of our factoring algorithm have been evaluated. Next, we discuss the difference between previous studies and ours and show the superiority of our approach.
Maitra and Sarkar [35] have proposed a factorization attack using lattice-based method when are known. Assume that one has , , and . They demonstrated that N can be factored in polynomial time in when . For , i.e., , we have . It implies that the above approach cannot reach the natural constraint since is not a negligible term.
Relatively speaking, our factoring algorithm involves an error term instead of and hence our result seems superior. To illustrate the superiority, we examine and compare in [35] and of ours. We choose 1024-bit CRT-RSA moduli and the corresponding CRT exponents of various bit sizes. The comparison results are given in Table 3. For the bit size of each CRT exponent, we randomly take 100 trials and calculate the average value.

Table 3.
The comparison of previous error term and ours.
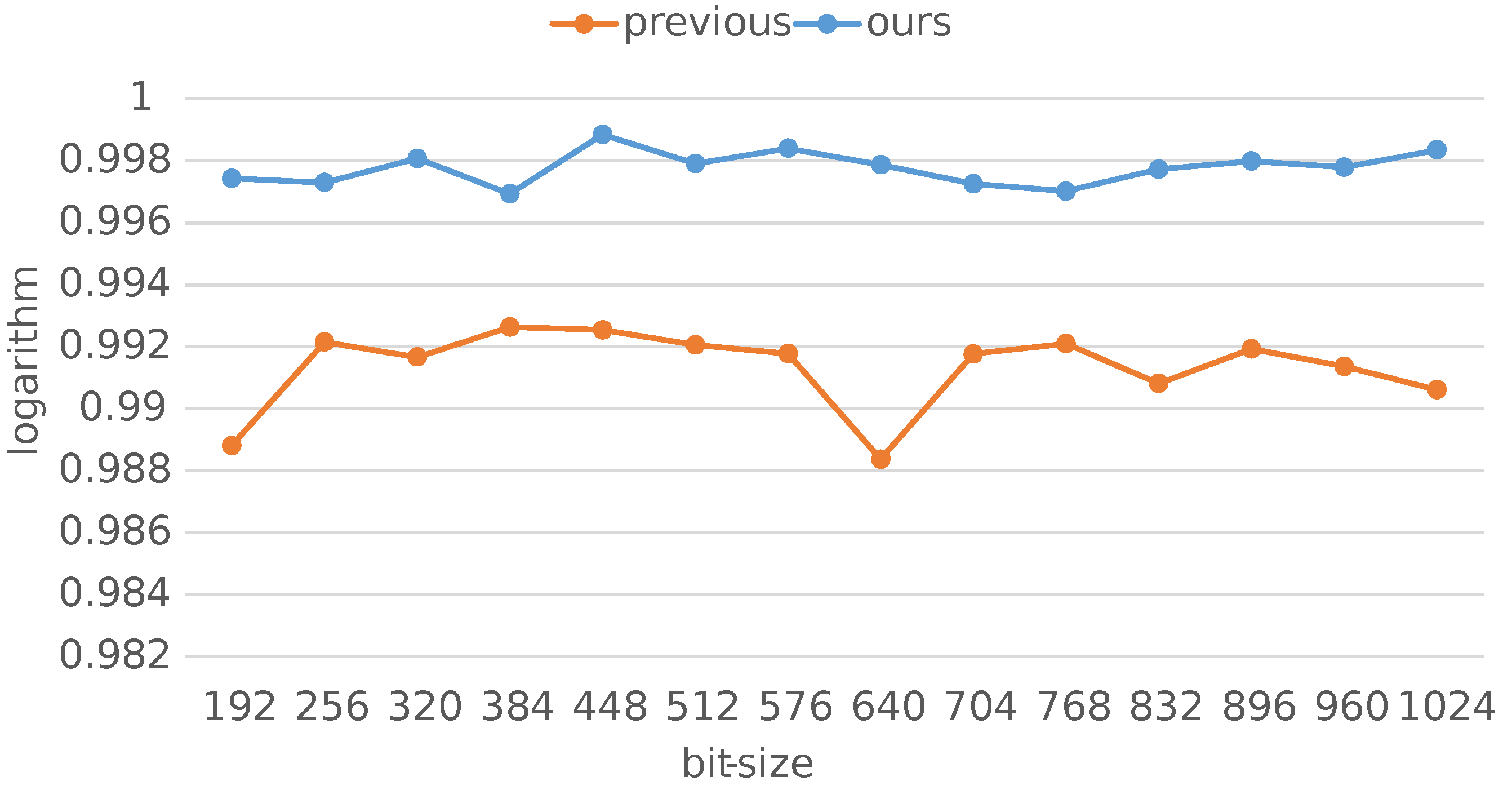
We observe that our error term equals to , i.e, negligible compared to in most cases. Further, our error term is always less than the previous one . Hence, our approach performs better than the previous work [35]. As shown in Figure 1, the attack upper bound of ours is closer to 1. Thus, our improvement further strengthens the modulus factoring attack on CRT-RSA when its key information is known.

Figure 1.
The comparison of previous work and ours with respect to the attack upper bound. The horizontal axis stands for the bit size of CRT exponents and the vertical one stands for the logarithm of the attack bound.
To illustrate the relation of our work to the field of attacking CRT-RSA, we compare and classify recent related works as shown in Table 4. Our work further enriches cryptanalyses of CRT-RSA. To be specific, the work not only makes further improvements on factoring attacks, but also reveals the importance and correctness of the polynomial-time equivalence of computing the CRT-RSA secret key and factoring. It can be seen that factoring attack is a more essential security threat.

Table 4.
The comparison and classification of related works and ours on cryptanalysis of CRT-RSA.
Notice that we experimentally verify our CRT-RSA modulus factorization algorithm for small CRT exponents. A limiting factor in achieving large CRT exponents is that we need to perform the lattice reduction algorithm with large lattice dimension in such cases. The running time increases rapidly, which leads to decreased attack efficiency, and is practically infeasible. This disadvantage can be eliminated with optimized lattice reduction algorithms and enhanced computing capability.
5. Conclusions
In this paper, we positively answer the research problem whether there exists a polynomial-time algorithm outputting the modulus factorization if given the CRT-RSA key information. Our work is summarized as follows.
- We study the security of CRT-RSA concerning its mathematical hardness assumption. We propose the improved polynomial-time algorithm of factoring the CRT-RSA modulus with the help of partial key exposure attack on CRT-RSA.
- Our asymptotic attack upper bound is superior to previous work [35]. Our factoring attack is a more essential security threat compared to others.
- We verify the correctness and validity of the proposed CRT-RSA modulus factorization algorithm with numerical experiments. Our validation experiments always successfully output the factorization results for small CRT-exponents.
- We discuss our results with several comparisons to properly assess the proposed factoring attack. Furthermore, we discuss the advantages and disadvantages of the proposed algorithm.
More concretely, under the condition that , the factoring algorithm takes the given CRT-RSA key information as input and outputs the factorization of modulus in polynomial time. We transform the original factorization problem into a modular polynomial solution problem. We apply Coppersmith’s lattice-based method to find the root solution, which contains the prime factors of the modulus. Notice that the polynomial-time equivalence of CRT-RSA key computation and factorization is still not completely solved. One open problem is whether there exists a polynomial-time algorithm for factoring the CRT-RSA modulus in the case of .
Future research should be devoted to the development of optimized lattice-reduction algorithm in order to enhance the efficiency of the proposed factoring attack. In addition, hybrid attacks based on the proposed CRT-RSA modulus factorization algorithm is an interesting topic for future work.
Funding
This work was supported by the National Natural Science Foundation of China, grant numbers 62002335 and Ningbo Natural Science Foundation, grant number 2021J174.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
The data presented in this study are available on request from the corresponding author.
Acknowledgments
We thank Julian Nowakowski for sharing the experimental code of the partial key exposure attack on CRT-RSA. We thank anonymous reviewers for their helpful and constructive comments that greatly improved this paper.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Rivest, R.L.; Shamir, A.; Adleman, L.M. A Method for Obtaining Digital Signatures and Public-Key Cryptosystems. Commun. ACM 1978, 21, 120–126. [Google Scholar] [CrossRef]
- Boudot, F.; Gaudry, P.; Guillevic, A.; Heninger, N.; Thomé, E.; Zimmermann, P. The State of the Art in Integer Factoring and Breaking Public-Key Cryptography. IEEE Secur. Priv. 2022, 20, 80–86. [Google Scholar] [CrossRef]
- Wiener, M.J. Cryptanalysis of short RSA secret exponents. IEEE Trans. Inf. Theory 1990, 36, 553–558. [Google Scholar] [CrossRef]
- Coppersmith, D. Small Solutions to Polynomial Equations, and Low Exponent RSA Vulnerabilities. J. Cryptol. 1997, 10, 233–260. [Google Scholar] [CrossRef]
- Boneh, D.; Durfee, G. Cryptanalysis of RSA with Private Key d Less than N0.292. In Advances in Cryptology—EUROCRYPT ’99, Proceedings of the International Conference on the Theory and Application of Cryptographic Techniques, Prague, Czech Republic, 2–6 May 1999; Stern, J., Ed.; Springer: Berlin/Heidelberg, Germany, 1999; Volume 1592, pp. 1–11. [Google Scholar] [CrossRef]
- May, A. Cryptanalysis of Unbalanced RSA with Small CRT-Exponent. In Advances in Cryptology—CRYPTO 2002, Proceedings of the 22nd Annual International Cryptology Conference, Santa Barbara, CA, USA, 18–22 August 2002; Yung, M., Ed.; Springer: Berlin/Heidelberg, Germany, 2002; Volume 2442, pp. 242–256. [Google Scholar] [CrossRef]
- Blömer, J.; May, A. New Partial Key Exposure Attacks on RSA. In Advances in Cryptology—CRYPTO 2003, Proceedings of the 23rd Annual International Cryptology Conference, Santa Barbara, CA, USA, 17–21 August 2003; Boneh, D., Ed.; Springer: Berlin/Heidelberg, Germany, 2003; Volume 2729, pp. 27–43. [Google Scholar] [CrossRef]
- May, A. Computing the RSA Secret Key is Deterministic Polynomial Time Equivalent to Factoring. In Advances in Cryptology—CRYPTO 2004, Proceedings of the 24th Annual International CryptologyConference, Santa Barbara, CA, USA, 15–19 August 2004; Franklin, M.K., Ed.; Springer: Berlin/Heidelberg, Germany, 2004; Volume 3152, pp. 213–219. [Google Scholar] [CrossRef]
- Ernst, M.; Jochemsz, E.; May, A.; de Weger, B. Partial Key Exposure Attacks on RSA up to Full Size Exponents. In Advances in Cryptology—EUROCRYPT 2005, Proceedings of the 24th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Aarhus, Denmark, 22–26 May 2005; Cramer, R., Ed.; Springer: Berlin/Heidelberg, Germany, 2005; Volume 3494, pp. 371–386. [Google Scholar] [CrossRef]
- Coron, J. Finding Small Roots of Bivariate Integer Polynomial Equations: A Direct Approach. In Advances in Cryptology—CRYPTO 2007, Proceedings of the 27th Annual International Cryptology Conference, Santa Barbara, CA, USA, 19–23 August 2007; Menezes, A., Ed.; Springer: Berlin/Heidelberg, Germany, 2007; Volume 4622, pp. 379–394. [Google Scholar] [CrossRef]
- Jochemsz, E.; May, A. A Polynomial Time Attack on RSA with Private CRT-Exponents Smaller Than N0.073. In Advances in Cryptology—CRYPTO 2007, Proceedings of the 27th Annual International Cryptology Conference, Santa Barbara, CA, USA, 19–23 August 2007; Menezes, A., Ed.; Springer: Berlin/Heidelberg, Germany, 2007; Volume 4622, pp. 395–411. [Google Scholar] [CrossRef]
- Takayasu, A.; Lu, Y.; Peng, L. Small CRT-Exponent RSA Revisited. In Part II, Advances in Cryptology—EUROCRYPT 2017—Proceedings of the 36th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Paris, France, 30 April 30–4 May 2017; Coron, J., Nielsen, J.B., Eds.; Springer International Publishing: Cham, Switzerland, 2017; Volume 10211, pp. 130–159. [Google Scholar] [CrossRef]
- Coron, J.; May, A. Deterministic Polynomial-Time Equivalence of Computing the RSA Secret Key and Factoring. J. Cryptol. 2007, 20, 39–50. [Google Scholar] [CrossRef][Green Version]
- Moriarty, K.; Kaliski, B.; Jonsson, J.; Rusch, A. PKCS #1: RSA Cryptography Specifications Version 2.2. 2016. Available online: https://rfc-editor.org/rfc/rfc8017.txt (accessed on 20 May 2022).
- Quisquater, J.J.; Couvreur, C. Fast Decipherment Algorithm for RSA Public-Key Cryptosystem. Electron. Lett. 1982, 18, 905–907. [Google Scholar] [CrossRef]
- Garner, H.L. The Residue Number System. IRE Trans. Electron. Comput. 1959, 8, 140–147. [Google Scholar] [CrossRef]
- Jochemsz, E.; May, A. A Strategy for Finding Roots of Multivariate Polynomials with New Applications in Attacking RSA Variants. In Advances in Cryptology—ASIACRYPT 2006, Proceedings of the 12th International Conference on the Theory and Application of Cryptology and Information Security, Shanghai, China, 3–7 December 2006; Lai, X., Chen, K., Eds.; Springer: Berlin/Heidelberg, Germany, 2006; Volume 4284, pp. 267–282. [Google Scholar] [CrossRef]
- Takayasu, A.; Lu, Y.; Peng, L. Small CRT-Exponent RSA Revisited. J. Cryptol. 2019, 32, 1337–1382. [Google Scholar] [CrossRef]
- Sarkar, S.; Maitra, S. Partial Key Exposure Attack on CRT-RSA. In Applied Cryptography and Network Security, Proceedings of the 7th International Conference, ACNS 2009, Paris-Rocquencourt, France, 2–5 June 2009; Abdalla, M., Pointcheval, D., Fouque, P., Vergnaud, D., Eds.; Springer: Berlin/Heidelberg, Germany, 2009; Volume 5536, pp. 473–484. [Google Scholar] [CrossRef]
- Lu, Y.; Zhang, R.; Lin, D. New Partial Key Exposure Attacks on CRT-RSA with Large Public Exponents. In Applied Cryptography and Network Security—Proceedings of the 12th International Conference, ACNS 2014, Lausanne, Switzerland, 10–13 June 2014; Boureanu, I., Owesarski, P., Vaudenay, S., Eds.; Springer International Publishing: Cham, Switzerland, 2014; Volume 8479, pp. 151–162. [Google Scholar] [CrossRef]
- Takayasu, A.; Kunihiro, N. Partial Key Exposure Attacks on CRT-RSA: Better Cryptanalysis to Full Size Encryption Exponents. In Applied Cryptography and Network Security—Proceedings of the 13th International Conference, ACNS 2015, New York, NY, USA, 2–5 June 2015; Revised Selected Papers; Malkin, T., Kolesnikov, V., Lewko, A.B., Polychronakis, M., Eds.; Springer International Publishing: Cham, Switzerland, 2015; Volume 9092, pp. 518–537. [Google Scholar] [CrossRef]
- Takayasu, A.; Kunihiro, N. Partial Key Exposure Attacks on CRT-RSA: General Improvement for the Exposed Least Significant Bits. In Information Security—Proceedings of the 19th International Conference, ISC 2016, Honolulu, HI, USA, 3–6 September 2016; Bishop, M., Nascimento, A.C.A., Eds.; Springer International Publishing: Cham, Switzerland, 2016; Volume 9866, pp. 35–47. [Google Scholar] [CrossRef]
- May, A.; Nowakowski, J.; Sarkar, S. Partial Key Exposure Attack on Short Secret Exponent CRT-RSA. In Advances in Cryptology—Proceedings of the ASIACRYPT 2021—27th International Conference on the Theory and Application of Cryptology and Information Security, Singapore, 6–10 December 2021; Part I; Tibouchi, M., Wang, H., Eds.; Springer International Publishing: Cham, Switzerland, 2021; Volume 13090, pp. 99–129. [Google Scholar] [CrossRef]
- Schindler, W.; Wiemers, A. Generic power attacks on RSA with CRT and exponent blinding: New results. J. Cryptogr. Eng. 2017, 7, 255–272. [Google Scholar] [CrossRef]
- Xu, S.; Lu, X.; Zhang, K.; Li, Y.; Wang, L.; Wang, W.; Gu, H.; Guo, Z.; Liu, J.; Gu, D. Similar operation template attack on RSA-CRT as a case study. Sci. China Inf. Sci. 2018, 61, 032111:1–032111:17. [Google Scholar] [CrossRef]
- Xu, S.; Wang, W.; Lu, X.; Guo, Z.; Liu, J.; Gu, D. Side channel attack of multiplication in GF(q)-application to secure RSA-CRT. Sci. China Inf. Sci. 2019, 62, 39105:1–39105:3. [Google Scholar] [CrossRef]
- Wan, W.; Chen, J.; Xia, J.; Zhang, J.; Zhang, S.; Chen, H. Clustering Collision Power Attack on RSA-CRT. Comput. Syst. Sci. Eng. 2021, 36, 417–434. [Google Scholar] [CrossRef]
- Kaedi, S.; Doostari, M.; Ghaznavi-Ghoushchi, M.B.; Yusefi, H. A New Side-Channel Attack on Reduction of RSA-CRT Montgomery Method Based. J. Circuits Syst. Comput. 2021, 30, 2150038:1–2150038:18. [Google Scholar] [CrossRef]
- Lenstra, A.K.; Lenstra, H.W.; Lovász, L. Factoring Polynomials with Rational Coefficients. Math. Ann. 1982, 261, 515–534. [Google Scholar] [CrossRef]
- May, A. New RSA Vulnerabilities Using Lattice Reduction Methods. Ph.D. Thesis, University of Paderborn, Paderborn, Germany, 2003. [Google Scholar]
- Coppersmith, D. Finding a Small Root of a Univariate Modular Equation. In Advances in Cryptology—EUROCRYPT ’96, Proceedings of the International Conference on the Theory and Application of Cryptographic Techniques, Saragossa, Spain, 12–16 May 1996; Maurer, U.M., Ed.; Springer: Berlin/Heidelberg, Germany, 1996; Volume 1070, pp. 155–165. [Google Scholar] [CrossRef]
- Coppersmith, D. Finding a Small Root of a Bivariate Integer Equation; Factoring with High Bits Known. In Advances in Cryptology—EUROCRYPT ’96, Proceedings of the International Conference on the Theory and Application of Cryptographic Techniques, Saragossa, Spain, 12–16 May 1996; Maurer, U.M., Ed.; Springer: Berlin/Heidelberg, Germany, 1996; Volume 1070, pp. 178–189. [Google Scholar] [CrossRef]
- Howgrave-Graham, N. Finding Small Roots of Univariate Modular Equations Revisited. In Cryptography and Coding, Proceedings of the 6th IMA International Conference, Cirencester, UK, 17–19 December 1997; Darnell, M., Ed.; Springer: Berlin/Heidelberg, Germany, 1997; Volume 1355, pp. 131–142. [Google Scholar] [CrossRef]
- Becker, T.; Weispfenning, V.; Kredel, H. Gröbner Bases—A Computational Approach to Commutative Algebra; Graduate Texts in Mathematics; Springer: Berlin/Heidelberg, Germany, 1993; Volume 141. [Google Scholar]
- Maitra, S.; Sarkar, S. On Deterministic Polynomial-Time Equivalence of Computing the CRT-RSA Secret Keys and Factoring. Def. Sci. J. 2012, 62, 122–126. [Google Scholar] [CrossRef][Green Version]
- The Sage Developers. SageMath, the Sage Mathematics Software System (Version 9.0). 2021. Available online: https://www.sagemath.org (accessed on 20 May 2022).
- Somsuk, K. The Improvement of Elliptic Curve Factorization Method to Recover RSA’s Prime Factors. Symmetry 2021, 13, 1314. [Google Scholar] [CrossRef]
- Peng, L.; Takayasu, A. Generalized cryptanalysis of small CRT-exponent RSA. Theor. Comput. Sci. 2019, 795, 432–458. [Google Scholar] [CrossRef]
- Oonishi, K.; Kunihiro, N. Attacking Noisy Secret CRT-RSA Exponents in Binary Method. In Information Security and Cryptology—Proceedings of the ICISC 2018—21st International Conference, Seoul, Korea, 28–30 November 2018; Revised Selected Papers; Lee, K., Ed.; Springer International Publishing: Cham, Switzerland, 2018; Volume 11396, pp. 37–54. [Google Scholar] [CrossRef]
- Oonishi, K.; Huang, X.; Kunihiro, N. Improved CRT-RSA Secret Key Recovery Method from Sliding Window Leakage. In Information Security and Cryptology—Proceedings of the ICISC 2019—22nd International Conference, Seoul, Korea, 4–6 December 2019; Revised Selected Papers; Seo, J.H., Ed.; Springer International Publishing: Cham, Switzerland, 2019; Volume 11975, pp. 278–296. [Google Scholar] [CrossRef]
- Oonishi, K.; Kunihiro, N. Recovering CRT-RSA Secret Keys from Noisy Square-and-Multiply Sequences in the Sliding Window Method. In Information Security and Privacy—Proceeding of the 25th Australasian Conference, ACISP 2020, Perth, WA, Australia, 30 November—2 December 2020; Liu, J.K., Cui, H., Eds.; Springer International Publishing: Cham, Switzerland, 2020; Volume 12248, pp. 642–652. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).