Abstract
The data transmission in wireless networks is usually analyzed under the assumption of non-stationary rates. Nevertheless, they strictly depend on the time of day, that is, the intensity of arrival and daily workload profiles confirm this fact. In this article, we consider the process of downloading a file within a single network segment and unsteady speeds—for arrivals, file sizes, and losses due to impatience. To simulate the scenario, a queuing system with elastic traffic with non-stationary intensity is used. Formulas are given for the main characteristics of the model: the probability of blocking a new user, the average number of users in service, and the queue. A method for calculating the boundaries of convergence of the model is proposed, which is based on the logarithmic norm of linear operators. The boundaries of the rate of convergence of the main limiting characteristics of the queue length process were also established. For clarity of the influence of the parameters, a numerical analysis was carried out and presented.
1. Introduction
The fifth generation (5G) networks will consist of different services with different specifications. Experts have identified network slicing as a key technology to enable 5G networks [1,2,3,4]. Within the framework of network slicing, many models are proposed with different principles for slicing radio resources [5]. In some cases, it is necessary to distribute slices between several users, and this distribution and the slices can be changed depending on time, for example, in [6,7,8], various options for re-slicing the network are shown. Earlier, we studied models for studying network slicing in the framework of papers [9,10], but we considered a model in the form of a queuing system with stationary intensities.
Given the need to re-slice the network and because all processes are non-stationary and depend on time. For example, a traffic profile—user activity is different depending on the time of day. Activity may also depend on the time of year; in the summer many users go on vacation and fly to other countries, and in winter most users are actively working and on weekends they sit at home watching movies, for example. Taking into account this dependence, it is necessary to consider models with non-stationary intensities. In our work, we consider an example of downloading user files depending on the time of day. For convenience, we consider one slice of the radio frequency channel taking into account the non-stationary nature, and look at the behavior of the characteristics. As a mathematical model, we take a queuing system with a non-stationary arrival intensity of user arrival in the system, as in [11,12], where such systems with non-stationary intensities are used for the joint service of radio frequencies.
This article discusses a special, but rather non-standard, heterogeneous birth and death process, for which, in principle, one can apply the methods described, for example, in articles [13,14], but due to the specifics of the model, in order to obtain acceptable estimates, the authors had to “trick”. In particular, the rate of convergence in the example under consideration actually turns out to be rather slow, so that the existing (and constructed) limiting regime begins to adequately show the situation at sufficiently large times Usually, uniformization is used as a method for calculating the transition probabilities for Markov chains, as in [15,16]. However, the methods based on it work very poorly in the case of slow convergence, which takes place for the considered models. In addition, without a prior understanding of when the limiting regime is reached, significant computational efforts are required in order to be at least to some extent confident that the obtained solution is the required one [17].
The goal of the paper is to explore the nonstationary queue-length process based on file transferring in the wireless network and analyze the performance measures of this system model. The remainder of the paper is organized as follows. In Section 2, the queueing system and its performance measures are presented. The convergence analysis for large service rates and arrival rates of the mentioned queueing system are described in Section 3. Application for file transfer in the wireless network and numerical analysis of the considered system model are discussed in Section 4, followed by the conclusions in Section 5.
2. Queuing System
2.1. Overview and Assumptions
In this paper, we will consider a queuing system with elastic traffic and inpatient claims. To describe the flow of requests with a variable number of users, a Poisson flow of the first kind with the following parameters is suitable: the arrival intensity , the minimum requirement for the resource b, and the length of the transmitted data block . Table 1 reflects the main parameters that describe the system model and the corresponding terms of the mathematical model. In the system under consideration, there is a resource of volume C, a storage device with a finite capacity r. Requests also have the property of impatience—they leave the queue with intensity . We will assume that the block length is equal to some value . The entire volume C is divided equally between the orders, that is, if the number of customers is 1, then the entire resource is consumed by this customer, and the service rate is ; if the number of customers is 2, then the service rate is —the resource volume is divided in half. In the case when C cannot be divided equally between the customers with the provision of the minimum guaranteed threshold b, a new customer enters the queue.

Table 1.
System model parameters.
Let be the number of processed orders at the moment . Hence, the number is the maximum number of requests that the device can process simultaneously. The state-space of the system looks like this:
2.2. Continuous-Time Markov Chain
It is easy to see that the given model can be described by Markov process where denotes the number of customers in the system at time t (queue-length process). Denote by ,
From the above assumptions, the resulting behavior of the state probabilities are described by a forward Kolmogorov system:
Now, we consider the corresponding nonstationary situation. Namely, we suppose that the queue-length process is an inhomogeneous continuous-time Markov chain. All possible transition intensities say , are supposed to be non-random functions of time. We suppose that all intensity functions are nonnegative and locally integrable on .
Denote by the vector of state probabilities at the moment t. Put for and
2.3. Performance Measures
For analysis of the system let us consider some characteristics of the devoted model. First, the probability of blocking an incoming application:
The average number of serviced applications:
The average number of applications in the queue:
3. Convergence Analysis
3.1. Definitions of Terms
We denote the mathematical expectation (the mean) of at the moment t if as .
The Markov chain is called weakly ergodic, if for any initial conditions For our situation any is considered as a quasi-stationary distribution of the chain .
The mentioned Markov chain also has the limiting mean , if as for any k.
We recall the logarithmic norm of operator function from to itself is calculated as (12):
and the bound
is valid for the Cauchy operator of the corresponding differential equation
3.2. Preliminary Considerations
Let us put that , and for . Then
As indicated above, the considered method is based on the concept of the logarithmic norm and the corresponding estimates for the Cauchy operator.
The solution to this equation can be represented in the following form:
where is the Cauchy operator of the corresponding homogeneous equation:
Next, we will consider estimates in "weighted" norms. Suppose are positive numbers. Then let
We will denote by . Note that is essentially non-negative, that is, all off-diagonal elements of are non-negative for any . Then we get:
Let us put the following:
Then we will get:
For some positive we put , , .
3.3. Bounds on the Rate of Convergence for Large Service Rates
First, we let . Then we will get the following:
Therefore,
Theorem 1.
Let there be a positive number such that,
Then the Markov chain is weakly ergodic and has the following convergence rate bounds:
for any initial conditions and any .
We let that . Then we will get .
Corollary 1.
From the conditions of Theorem 1, has a limit mean, then we say , and we obtain that the following estimate is true for any j and any :
3.4. Bounds on the Rate of Convergence for Large Arrival Rates
Now consider the case and assume that . In this case, we have:
Then it follows that we have the same:
Theorem 2.
Let
for some . Then, the Markov chain is weakly ergodic and has the following convergence rate bounds:
and
for any initial conditions and any . In addition, there is also a marginal mean and bound (29).
In addition, note the following: if the process is homogeneous (i.e., all intensities are constant), then the conditions of Theorems 1 and 2 are equivalent to the inequalities and , respectively.
And it is also worth noting that when all intensities of the process are 1-periodic, then there is a weak ergodicity and the estimates of Theorem 1 or Theorem 2 if:
3.5. Perturbed CTMC and Bounds
In this subsection, we will consider the application of the general perturbation bounding in the same way as in the work [13]) for the models under study. We will consider a “perturbed” queue-length process with the corresponding transposed intensity matrix , where the “perturbing” matrix is small. That is, we assume that the perturbed queue is of the same nature as the original one. Then the perturbed intensity matrix also has the same structure with the corresponding perturbed intensities , , . We assume that for .
We suppose that:
Hence, we will get the following:
Then, from (8) we obtain the following bound:
Now from Theorem 1 and Corollary 1 in the paper [13] the following bounds of the perturbation follow.
Theorem 3.
Suppose that under the conditions of Theorem 1 or Theorem 2 the Markov chain is exponentially ergodic, that is,
for some positive . Then the following bounds of the perturbation take place:
and
for any perturbed queue with the respectively closed intensities satisfying to (36).
4. File Transfer in Wireless Network
4.1. Multi-Service Network
The system model of this work has the form of a cell, in the coverage area of which mobile devices are located (Figure 1). Each of them has its MSISDN (Mobile Subscriber Integrated Services Digital Number)—the mobile subscriber number of digital network with the integration of services. Each user behaves as follows: he sends a request to download a file, then downloads it, and also the user can disappear from the system. Disappearance can be associated with leaving the coverage area of the cell, or with a change in the type of service, or with the end of the service. The conclusion follows from the description of the system model: if we sum up the flow from all users, then the duration of the intervals between requests will not depend on the number of users, which is described by the Poisson flow of the first kind.
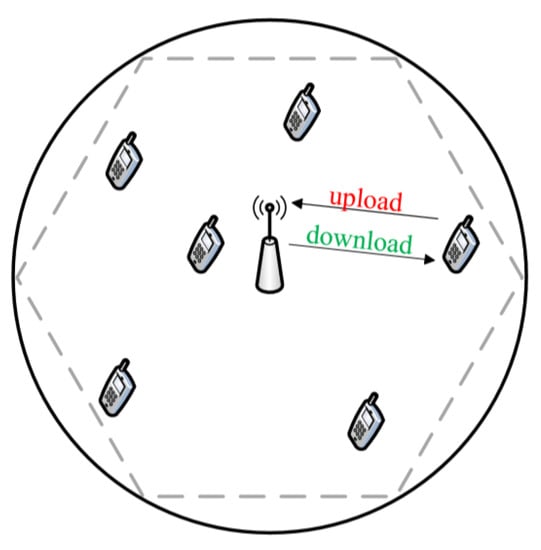
Figure 1.
Scheme of System Model.
The users are provided with various services that belong to different categories of data transmission. A more detailed overview of the categories is illustrated in the Table 2. However, of these, we consider only those that can be described by elastic traffic, such as email, file transfer, and others.

Table 2.
Description of service types.
4.2. Dataset Structure
The analysis of real traffic is of great importance, because the identification of the patterns of its arrival can make it possible to carry out studies of the system model described in the previous section in a non-stationary mode. Therefore, a task of this paper is formulated as follows: to analyze the traffic on one of the cell tower. There is a monitoring component to collect information about the system. Every hour, for each active device, the number of bits sent and received is added up. At the beginning of the next hour, the amount for the previous one hour is summed to the registration file. The principle of filling data during the monitoring is shown in Figure 2. There is a following designation —the sum of bits sent by the device per day d, at hour t. The part of the log file is shown in the Table 3. There are the column START_HOUR contains the full date and hour when the data was transferred; and the column MASKED_MSISDN—masked device identifier of the user; APP_CLASS—the class of the application that transfers data; UPLOAD—the number of bits, which were sent as we denoted ; and the last DOWNLOAD—the number of received bits as we denoted .
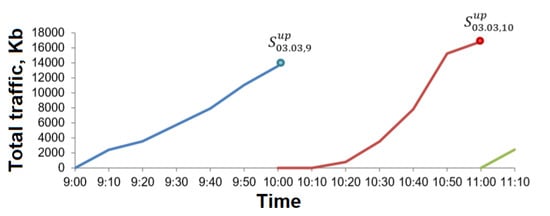
Figure 2.
The principle of data accumulation during monitoring.

Table 3.
Part of the log file.
4.3. Daily Traffic Profile
We consider elastic traffic, which is characterized by such a parameter as the length of the elastic data block. For the considered traffic model, monitoring data were taken with a class “File Transfer”, which corresponds to the transfer of data using the FTP protocol.
To get the number of requests per second at a particular hour of the day for the selected application class, we perform aggregation of the form:
where the received sum is determined in bits, d—date and l—average packet size, equal to 2 MB. Then, we perform the calculation on Formulas (42) and (43) and the results are shown in Table 4.

Table 4.
Dependence of the number of requests on the time of day.
4.4. Fourier Series Approximation
From the found values it is necessary to obtain some continuous function of the dependence of the fluctuation of the upward and downward traffic flows on the time of day. To do this, we perform approximation by the Fourier series. For clarity, we will gradually increase the number of conditions in a row, which is to choose the most optimal option.
Consider the dependence of the intensity of the upward data flow from time, and we will carry out the approximation by the Fourier series with one, two, and three conditions. As a result, we get a functions of the form (44)–(46) respectively and for our example the parameters will take values, which are shown in Table 5:

Table 5.
Parameters of Fourier Series Approximation for the upward data flow.
Using Matlab, we have built the plots of the considered approximation. It is easy to see that the plot of the obtained approximation for the one condition (Figure 3a) differs significantly from the initial data, therefore, so that is why we increased the number of conditions to two and the graph of the resulting function for two conditions (Figure 3b) significantly reflects more faithfully the relationship between real data. Then, according to the plot of the approximation for the three conditions (Figure 3c), it could be seen that, now, in the intervals with the highest network load, the function has become closer to the real data points. However, in general, the graph did not receive significant changes, and the variant of the approximation with two conditions can be considered the most optimal.
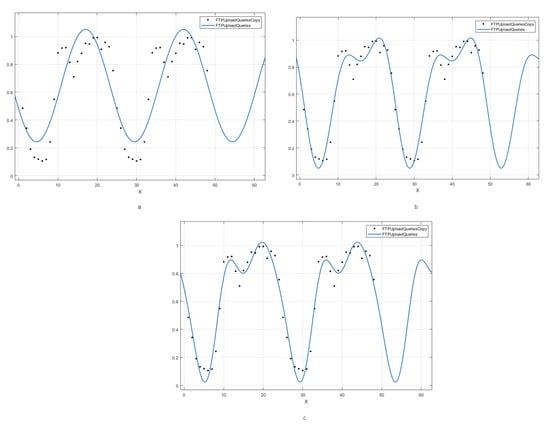
Figure 3.
(a) Graph of the approximation function for upward flow with one condition; (b) Graph of the approximation function for upward flow with two conditions; (c) Graph of the approximation function for upward flow with three conditions.
4.5. Numerical Analysis
For the numerical analysis, we will consider the following example: the volume of the resource block is Mbps, and the finite capacity drive is . The size of the transferred file equals to MB, that is 80 Mb, and the minimum transfer rate is Mbps. The arriving intensity of device equals to , where according to Section 4.4 equals to (46), where parameters are indicated in the Table 5 on the line for the third condition. The intensity of the flow of leaving requests for the transfer of a block of elastic data due to “impatience” is .
Apply all our bounds for this specific situation.
For applying of Theorems 2 and 3 we put , and for . Then, we will get:
therefore, one can get and in (39).
Now we obtain the following bounds on the rate of convergence:
from Theorem 2;
from Theorem 2 and Corollary 1.
The corresponding perturbation bounds are:
and
from Theorem 3.
To solve the Cauchy problem, the 4th order Adams–Multon method was used with the use of IntelliJ IDEA software, JDK and the JFreeChart library, the functionality of which is used for plotting. The convergence plots were built for the characteristics specified in Section 2.3, shown in Figure 4, Figure 5 and Figure 6. To analyze the characteristics, two scenarios were chosen: 1. At the initial moment of time, our system is empty: ; 2. At the initial moment, the system is completely occupied, that is, all devices are occupied and there are no free places in the queue . Figure 4 shows graphs for the blocking probability. Note that, since we are considering two scenarios, then according to Figure 4a. for the first scenario, the starting value of the probability is 0, since the system is empty and it is logical that there will be no locks, and for the second scenario, the starting value is 1 since the system is completely busy. We can notice that the blocking probability for the two scenarios converges at time and according to Figure 4b. We see that its values fluctuate within the range of –, and the period of fluctuation is 24. Further, in Figure 5, we see that the average number of service requests converges at 100; this may indicate a high load of devices in our system. However, the probability of blocking is small. Let us look at the average number of applications in the queue shown in Figure 6. As shown in Figure 6a. for the two scenarios, the graphs converge and the mean value is no less than 64 and no more than 75, as we can see in Figure 6b.
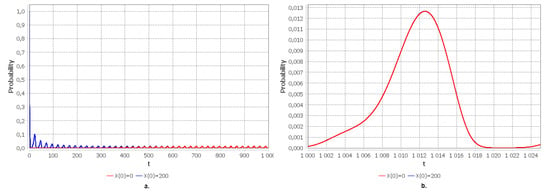
Figure 4.
(a) Probability of blocking for . (b) Approximation of the limiting probability of blocking for .
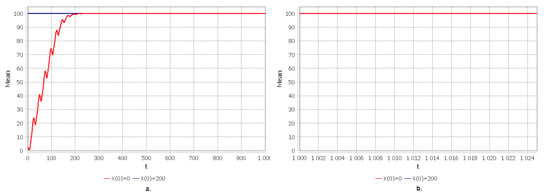
Figure 5.
(a) The mean of applications served for . (b) Approximation of the limiting mean of applications served for .
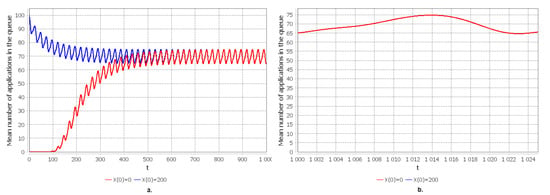
Figure 6.
(a) The mean of applications in the queue for . (b) Approximation of the limiting mean of applications in the queue for .
5. Conclusions
In this paper, we have investigated the process of downloading user files depending on the time in the form of a queuing system with elastic traffic and non-stationary intensities. We have developed a method for calculating the limits of convergence of such a model. Estimates of the rate of convergence are obtained based on the logarithmic norm of linear operators. As a result, it was found that the rate of convergence turned out to be low enough for an adequate representation of the situation in the limiting mode to begin at sufficiently long times. We evaluated the characteristics of such a model, namely, the probability of blocking new users, the average number of users downloading data, and the average number of users waiting for the download to start. We obtained the upper and lower bounds of their values.
We considered the model in the form of a single network slice and, in the framework of further tasks, we can consider the model in the form of several slices. If we want to scale our system, for example, to add another incoming stream, it will be necessary to solve the problem of redistribution; we will have to adapt our method for the new case. In addition, in our case, we have a one-dimensional random process, and for a new system where it will be multidimensional, we will first need to identify a function—a mapping, to go to the one-dimensional case to apply our method. This complexity can be viewed as a challenge for future research.
Author Contributions
Conceptualization, supervision, A.Z. and I.K. (Irina Kochetkova); methodology, Y.S. and I.K. (Irina Kochetkova); software, validation, visualization I.K. (Ivan Kovalev) and E.M.; investigation, writing, I.K. (Irina Kochetkova), Y.S., Ivan Kovalev, E.M., A.C., A.Z. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by Russian Science Foundation, grant number 19-11-00020 (recipients I.K. (Irina Kochetkova), Y.S., I.K. (Ivan Kovalev), A.Z., Section 3, Section 4 and Section 5). This paper has been supported by the RUDN University Strategic Academic Leadership Program (recipients A.C., E.M., Section 1 and Section 2).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Acknowledgments
The authors are sincerely grateful to Luis M. Correia (IST/INESC-ID, University of Lisbon) for providing the dataset for Section 4.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Kochetkov, D.; Almaganbetov, M. Using patent landscapes for technology benchmarking: A case of 5g networks. Adv. Syst. Sci. Appl. 2021, 21, 20–28. [Google Scholar] [CrossRef]
- Kochetkov, D.; Vuković, D.; Sadekov, N.; Levkiv, H. Smart cities and 5G networks: An emerging technological area? J. Geogr. Inst. Jovan Cvijic SASA 2019, 69, 289–295. [Google Scholar] [CrossRef] [Green Version]
- Barakabitze, A.A.; Ahmad, A.; Mijumbi, R.; Hines, A. 5G network slicing using SDN and NFV: A survey of taxonomy, architectures and future challenges. Comput. Netw. 2020, 167, 106984. [Google Scholar] [CrossRef]
- Khan, L.U.; Yaqoob, I.; Tran, N.H.; Han, Z.; Hong, C.S. Network Slicing: Recent Advances, Taxonomy, Requirements, and Open Research Challenges. IEEE Access 2020, 8, 36009–36028. [Google Scholar] [CrossRef]
- Muhizi, S.; Ateya, A.A.; Muthanna, A.; Kirichek, R.; Koucheryavy, A. A novel slice-oriented network model. Commun. Comput. Inf. Sci. 2018, 919, 421–431. [Google Scholar] [CrossRef]
- Ageev, K.A.; Sopin, E.S.; Yarkina, N.V.; Samouylov, K.E.; Shorgin, S.Y. Analysis of the network slicing mechanisms with guaranteed allocated resources for various traffic types. Inform. Primen. 2020, 14, 94–100. [Google Scholar] [CrossRef]
- Yarkina, N.; Gaidamaka, Y.; Correia, L.M.; Samouylov, K. An analytical model for 5G network resource sharing with flexible SLA-oriented slice isolation. Mathematics 2020, 8, 1177. [Google Scholar] [CrossRef]
- Kochetkova, I.; Vlaskina, A.; Burtseva, S.; Savich, V.; Hosek, J. Analyzing the effectiveness of dynamic network slicing procedure in 5g network by queuing and simulation models. Lect. Notes Comput. Sci. 2020, 12525, 71–85. [Google Scholar] [CrossRef]
- Vlaskina, A.; Polyakov, N.; Gudkova, I. Modeling and Performance Analysis of Elastic Traffic with Minimum Rate Guarantee Transmission under Network Slicing. Lect. Notes Comput. Sci. 2019, 11660, 621–634. [Google Scholar] [CrossRef]
- Vlaskina, A.S.; Polyakov, N.A.; Gudkova, I.A.; Gaidamaka, Y.V. Performance analysis of elastic traffic with minimum bit rate guarantee transmission in wireless network under network slicing, Izvestiya of Saratov University. Informatics 2020, 20, 378–387. [Google Scholar] [CrossRef]
- Gudkova, I.; Korotysheva, A.; Zeifman, A.; Shilova, G.; Korolev, V.; Shorgin, S.; Razumchik, R. Modeling and analyzing licensed shared access operation for 5G network as an inhomogeneous queue with catastrophes. In Proceedings of the International Congress on Ultra Modern Telecommunications and Control Systems and Workshops, Lisbon, Portugal, 18–20 October 2016; pp. 282–287. [Google Scholar] [CrossRef]
- Markova, E.; Satin, Y.; Kochetkova, I.; Zeifman, A.; Sinitcina, A. Queuing system with unreliable servers and inhomogeneous intensities for analyzing the impact of non-stationarity toperformance measures of wireless network under licensed shared access. Mathematics 2020, 8, 800. [Google Scholar] [CrossRef]
- Zeifman, A.; Korolev, V.; Satin, Y. Two approaches to the construction of perturbation bounds for continuous-time Markov chains. Mathematics 2020, 8, 253. [Google Scholar] [CrossRef] [Green Version]
- Zeifman, A.; Satin, Y.; Kryukova, A.; Razumchik, R.; Kiseleva, K.; Shilova, G. On the Three Methods for Bounding the Rate of Convergence for some Continuous-time Markov Chains. arXiv 2020, arXiv:1911.04086. [Google Scholar]
- Arns, M.; Buchholz, P.; Panchenko, A. On the numerical analysis of inhomogeneous continuous-time Markov chains. Informs J. Comput. 2010, 22, 416–432. [Google Scholar] [CrossRef]
- Andreychenko, A.; Sandmann, W.; Wolf, V. Approximate adaptive uniformization of continuous-time Markov chains. Appl. Math. Model. 2018, 61, 561–576. [Google Scholar] [CrossRef]
- Katoen, J.-P.; Zapreev, I.S. Safe on-the-fly steady-state detection for time-bounded reachability. In Proceedings of the 3rd International Conference on the Quantitative Evaluation of Systems, California, CA, USA, 11–14 September 2016. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).