1. Introduction
Cybersecurity is an important component of Industry 4.0, which has become an integral part of society. New requirements for IoT security encourage inclusion of components related to cybersecurity and safety of complex production and cybernetic systems in the educational profiles of university students. For significantly different training profiles, there should be different volumes and depths of information security knowledge, including cybersecurity as a component.
Student motivation and discovery are the main components of the professional training process. Additionally, teaching, engagement, achievements and satisfaction are important to training and workforce development. The literature shows that the classifications of methods for good student motivation in the educational process are:
Methods using words and communication;
using pictures, photos, schemes.
Methods of information analysis and of learning new material include listening to the new information and correspondingly working with it. That means students are using methods, schemes and algorithms, which they have learnt during lectures or practical hours. Using a creative way of studying new material is also important. For example, using interactive tools, video, games, research methods, working independently to acquire new knowledge and analyzing the new material. Additionally, special attention should be paid to students working in teams. When conducting scientific research and international projects, analytical and research skills are very important for the participants. Therefore, it is important to encourage young people to develop and improve their research skills as it will enhance job readiness. Nowadays, there are a lot of special international scientific–educational programs, which are engaging students to work on interesting tasks, using their hard and soft skills.
The Literature Review describes the results of modern research related to the learning cybersecurity discipline block for various specialties, the basics of the Scrum and eduScrum method and related issues. The Materials and Methods section describes the approach that was applied to the implementation of project tasks, primarily project management methods. The Results section contains the implementation of the used Scrum models for two types of projects and the visualization of statistical results as well as calculations for comparing the effectiveness of the Scrum method with the usual learning approach. In the Discussion section, features of the Scrum method for both an educational project and a research project have been described. The final Conclusions section sums up the successful application of the Scrum method.
Aim of the research: Application of the Scrum method to motivate students of various specializations while improving skills in both the basics of cybersecurity and its profound learning in the process of performing educational and research projects. Additionally, comparing the effectiveness of training using the Scrum method and without it based on the obtained statistical data on the learning results.
2. Literature Review
The evolution of changes in requirements for professional skills in information security is presented in [
1] (pp. 3–9). Modern specialties in relation to their content of information security knowledge could be divided into three large groups. The first group is purely cybersecurity specialists (for example, the security of computer systems and networks) and that part of information security that concerns technical information protection, information security management, etc. Such specialists are characterized by the deepest knowledge.
The next group is engineers developing and implementing various industrial projects. For them, information security knowledge should not be as deep as for the previous group, but when developing industrial systems, they should consider information security as a system characteristic [
2]. The third group is non-technical specialists. Their professional knowledge is not directly related to technical issues, but they use information technologies in their own activities. This group is the least aware of information security issues and is a target for hackers widely using social engineering methods. The approach to providing the necessary knowledge for this group of future specialists is just being developed and is one of the topics of the specialized international WISE conference [
3], with topics of Informing Citizens in Information Security and Programs to Raise Information Security Awareness, E-Learning for the Listed Areas of Security Education. Students of the third group should be well motivated to acquire information security knowledge. The authors will describe performing an educational project for this third group [
4] and a research project for the first group, taking into account the previous EU TEMPUS Project experience of developing “Educating the Next generation experts in Cyber Security: the new EU-recognized Master’s program” (ENGENSEC) [
5].
Using Sternberg’s Triarchic Model of Intelligence [
6] as well as Bloom’s Taxonomy [
7] is helpful for the educators and student mentors in the field of cybersecurity. Triarchic theory applied to cybersecurity allows the proposal of approaches for teamwork with students developing their analytical, practical and creative skills. Bloom’s Taxonomy helps to classify learning objectives into categories associated with lower or higher level thinking and also even with problem solving.
The abovementioned learning methods were successfully implemented for international projects for students that have technical or non-technical specializations. The research results presented in this article have been obtained while working on CRDF Global projects. CRDF Global [
8] is an independent non-profit organization, which is supporting international scientific-technical collaboration through grants, technical resources, education and services. Competitions of CRDF Global for research and innovations (RI) allow cross-border cooperation and the strengthening of international research through the implementation of peer-reviewed competitions for scientific grants. International research partnerships are opening the way for new research directions and creating new abilities for collaboration between scientists from different countries.
One such CRDF Global research project was connected with protection against cyberattacks on information processing devices such as computers, tablets, mobile phones or other gadgets, using authentication methods, based on small differences between devices at the physical level. Such differences are, in fact, individual and appear during the process of device production. This allows them to differentiate devices by the statistical characteristics of their internal electric noises. Such an approach ensures device mobility, does not require any additional external means and significantly increases correct authentication probability.
Our previous research engaged faculty staff together with master students [
9] and an authentication method for personal computers by their internal electrical noise was developed. Participation in this scientific project demonstrated the STEM approach for cybersecurity students: Students need to understand the physics of the formation of unique electrical signals inside a working electronic information processing device (science), the technology for recording electrical signals using an analog-to-digital converter (ADC) sound card (technology), develop software to transfer data from a client computer to a server (engineering) and mathematical processing of data records to extract stable authentication features and further comparison with a sample (mathematics). This scientific project made it possible to implement the principle of active learning of cybersecurity students.
Another project (educational), the results of which are presented in this article, was about training in the basics of cybersecurity. The project was attended by students whose future specialties are not related to cybersecurity, but for whom cyberhygiene skills are relevant and socially significant. The training was organized as a set of game situations where students learnt about the possible negative consequences of actions with their laptops, smartphones and computers. After each game situation, students had to take a test.
In this article, we describe the results of applying the Scrum method [
10] to enhance the cognitive activity of students, which we used for different projects.
The desire to transfer the Scrum project management method into the educational process led to the creation of the eduScrum guide. Since 2015, eduScrum has been used in schools and universities. Dutch educators from Alphen-aan-den-Rijn adapted the project management method to the school system [
11]. The use of eduScrum gives a positive result, and there is evidence that, on average, the result of training is 20% higher compared to the classical method [
12]. The main idea of eduScrum is to transfer part of the responsibility for the learning process from the teacher to the students. Since eduScrum is an agile methodology, it describes “what” and “why”, but does not describe “how” [
13,
14,
15]. The eduScrum allows creation of a structure of the learning process in which different techniques and processes can be used. It has mandatory structure elements, these are roles, events, elements and rules. The emphasis is on organizing and completing work in time. There are many applications of eduScrum in practice [
15,
16,
17,
18,
19]. To date, many lecturers have worked on the use of eduScrum in their educational activities. The articles present the results of applying the eduScrum methodology in engineering courses for postgraduate students in industrial engineering [
16], as the method for teaching programming of an Arduino microcontroller [
17], in a virtual programming lab [
18], an interactive course for JavaScript in LMS Moodle [
19] and in an engineering course [
20]. Education in the 21st century must change to meet the rapidly changing needs of manufacturing [
21]. Students become more independent and self-reliant in their learning, which allows them to use the acquired skills of learning and working on projects in real production [
22].
3. Materials and Methods
Taking into account that information technologies are used in various areas of day to day activity, it is absolutely impossible to ignore the impact of cybersecurity risks. Securing information from threats, vulnerabilities and attacks is important. As testing the educational course “Cyber Hygiene E-Learning” [
4,
23] was proposed to our university by CRDF Global, we were also provided with learning outcomes after its completion. Therefore, statistics were automatically collected on the website during student training. During registering on the website of the course, students had to indicate the name of the university, specialization and other information, so the authors had detailed statistics: Qualitative and point evaluations for the course for each student, time of course completion and other data. This allowed us to obtain a variety of distributions, which are demonstrated in the Results section. This research takes into account that cyberattacks are often based on bypassing passwords, which allows bad actors to obtain access to confidential or secret information as well as take control of our computers. The modern world is filled with cyber-physical systems which work without input from users. Not only do people have passwords, but information processing devices have passwords as well. Usually, the passwords for devices are appointed by their manufacturers. However, such passwords could be easily broken by a simple brute force attack.
Students’ participation in CRDF Global projects allowed them to study the cybersecurity problem more deeply. More complicated passwords are based on the “biometrics” of devices and, thus, a cyberattack is more difficult. Promising results in this direction allow us to select serial computers, which are absolutely identical from the first point of view. Small differences in computers are allowed at the component level, as manufacturing processes have deviations within tolerances. In our research, internal electric noises are used for computer identification, which are recorded by the sound card. The advantages of such an approach are the following: All factors needed for identification are already present in the computers themselves, therefore they remain mobile; the influence of the external electromagnetic environment on the measurement results can be neglected; malefactors do not have any possibility to create the same noise to start the attack.
We are expecting that the results of our research “Developing software and hardware complex for dynamical authentication of information processing devices in a corporate network for cybersecurity purposes” will provide a real opportunity to increase the protection against cyberattacks, in addition to teaching students about the modern approaches to increasing cybersecurity as well as to create a basis for further research in educational institutions.
For cybersecurity, master students performed teamwork estimating threat sources. Each three to four person team had its own object (organization) as a task for taxonomy of threat sources capable of initiating threat events [
10]. The teams analyzed the existing sources of threats and the object’s framework for improving critical infrastructure cybersecurity initially at the organizational level, then at the mission/business process level and finally at the information system level. For the master students, this was useful, especially to become acquainted with how to use the appropriate NIST documents [
24,
25,
26]. The team leaders presented reports describing the cybersecurity framework core including functions (identify, protect, detect, respond and recover), categories and subcategories. Categories are the subdivisions of a function, while the subcategories are the further divisions of the categories into the needed specific outcomes.
The functions identify, protect, detect, respond and recover are described in [
24]. The first one, the identify function, is connected with understanding of the organization staff’s cybersecurity risk management of systems, people, assets, data and capabilities. The protect function means safety for the systems and critical infrastructure. In that case, it was very helpful that almost all the students learnt the discipline “IT Audit Cybersecurity” during their bachelor studies. The detect function means identifying a cybersecurity incident, if it had happened, while the respond function describes which actions should be taken. The recover function is responsible for maintaining and fixing the situation after the cybersecurity incident. This maintenance ability in each organization was estimated by each student team using the framework implementation tiers.
There are four tiers characterizing current risk management practices: Partial (the lowest), risk informed, repeatable and adaptive (the most secure). In the case of the first one, risk management practices are not formalized in the organization and the awareness of cybersecurity risk is totally insufficient. For the risk informed tier, the situation is a little bit better than in the previous one, however, cybersecurity risk management has not been widely established in the company. The repeatable tier means that risk management practices exist as a policy, however, the organization usually acts formally upon the risks, further expanding to the adaptive tier.
Our team worked not only with the cybersecurity students, but also with computer science and economics students and, for them, teaching methods should be different. For effective work on the specified project, our team determined a list of effective methods and approaches to obtain effective final results. We used project management methods to organize teamwork [
27]. Project management involves planning, organizing, resource control, monitoring milestones and activities, reporting and project finalizing for achieving an aim satisfying the determined estimating success criteria.
During the work with the students, careful attention was paid to communications, competencies and feedback between the participants. Additionally, six phases (shown below) of the project life cycle were used:
Planning.
Writing a schedule of events.
Monitoring and control.
Determination of intermediate results.
Evaluating, making changes.
Obtaining final result.
Working on a project is an ongoing process and it does not have final deadlines. For example, it is necessary to perform X experiments during time Y in order to write Z scientific works. Article publication and processing results may take a long time, and while the materials are in the evaluation process, the team continues to perform the project. In fact, there are no terms from the beginning to the end for planning the project according to the traditional waterfall system. We have analyzed the most popular and effective methodologies of working in a team on a project (
Table 1).
The Scrum system was selected for teamwork. Scrum is an effective methodology, motivating for both students and teams.
Based on work experience, we will underline the advantages of Scrum for the implementation of a project while involving students:
The team has an open exchange of information, knowledge and problems. Everyone feels engaged in the process of realizing a common aim. It is possible to check the work at various stages, make corrections and receive actual information about the delivery dates of project stages.
Team members decide themselves how to work on the project, and freedom of action and responsibility are motivating.
The Scrum concept allows each member of the group to see his own and general achievements every day.
Determining the main stages of work on the project is an important stage of organizing work in a team and is determined by the following phases:
The planning phase is the most important and critical step in creating a successful system. At this stage, the decision should be made on what exactly needs to be carried out and developed and what problems should be solved; problems, objectives and resources are defined; possibilities of alternative solutions to problems are studied.
- 2.
System analysis.
It is necessary to define and document the requirements of the project. If needed, it is necessary to develop the input documentation and the technical task—what are its expectations and how to implement them. It is important to maintain a good level of communication in the team, to find answers to the participants’ questions.
- 3.
System design.
The design phase is the next after a good understanding has been achieved among the team members of the requirements for the project and the tools and programs for project implementation have been determined.
- 4.
Experimental operation and integration.
At this stage, various components and subsystems are united into a single integrated system. Input data are submitted to the system. The output signal, behavior and functioning are modeled and analyzed.
- 5.
Checking and result analysis.
4. Results
The educational course “Cyber Hygiene E-Learning” was performed with non-cybersecurity specialization students at the Lviv Polytechnic National University. We had a team of teacher consultants who were acquainted with the course in detail. They communicated with their students, who were not from a cybersecurity discipline. First of all, a series of meetings were organized with consulting teachers, and the scope was determined as well as terms for the course and groups of participating students. The education period from 28 September 2020 till 10 October 2020 was online due to quarantine restrictions. Teacher consultants had to provide information about the course using MS Teams and Zoom platforms. Then, consulting teachers informed students about the possibility of taking the course during their online lectures, as well as during group supervisors’ meetings with their groups. The following departments were involved:
Department of Computational Mathematics and Programming (when teaching informatics to students of humanitarian specializations—management, social work, social welfare),
Institute of Telecommunications, Radio Electronics and Electronic Engineering,
Applied Mathematics Department,
Department of Foreign Trade and Customs Affairs,
Department of Machine Design and Operation.
The results of the course are as follows:
Mainly the first/second-year students took the course. All finished the course with 210 students of 12 specializations passing the test. One third of them were studying the specialization of “management”.
Finally, during the implementation of the second project, the required number of 100 participants who passed the final test was surpassed more than two times: 210 students passed the test.
We have developed a model for working with each group, which consists of 100 participants. It is based on the Scrum method described above. A Scrum team consists of the following participants: Project manager, Scrum master, technical writer. Students are task performers. As a manager, we indicated a teacher for every 10 student performers. An active student with significant success in learning and good soft skills, i.e., good communication, optimism and organizational qualities, was elected as a Scrum-master. The technical writer was a student who possesses organizational qualities, with a good level in studying. The team leader was a leader among the students who reported about fulfilling the tasks. Performers were students who were included in the group and fulfilled the objective tasks. Note that Scrum-master and technical writer also belong to the group of student performers, and, thus, perform both roles in the project (general Scrum description for a group).
Scrum tasks:
Backlog is the place where all the modules that are needed to complete the project are loaded. The product backlog is an ordered list of everything that is known to be needed in a product based on the product goal. It is constantly evolving and is never complete.
Sprint backlog is a list of everything that the team commits to achieve in a given sprint. Once created, no one can add to the sprint backlog except the development team.
Sprint is a time segment, the duration of which was determined by the team at the very beginning. During the development of the entire project, the duration of the sprint usually does not change, in our project it lasted two weeks.
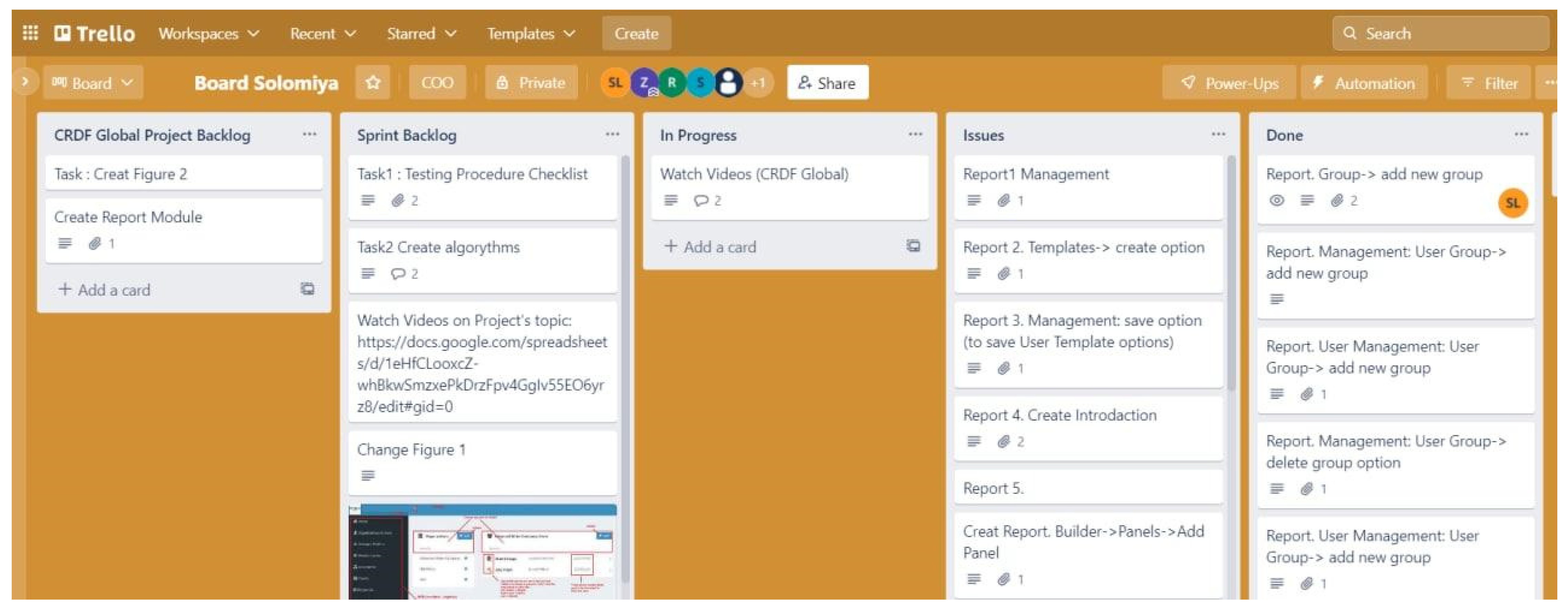
For working and assigning tasks, we created a Trello board for each participant, where we added cards with tasks (
Figure 1). In this way, it is convenient to use the dynamics of work on each card. For example:
For the Scrum tasks, the following were used:
This is a meeting where the team determines what will be developed in the next iteration.
- 2.
Scrum daily meeting, or standup meeting. It was this Scrum ritual that motivated students and allowed them to control their emotional state.
Based on the basic principles of working in a Scrum team, we have developed a model for a team:
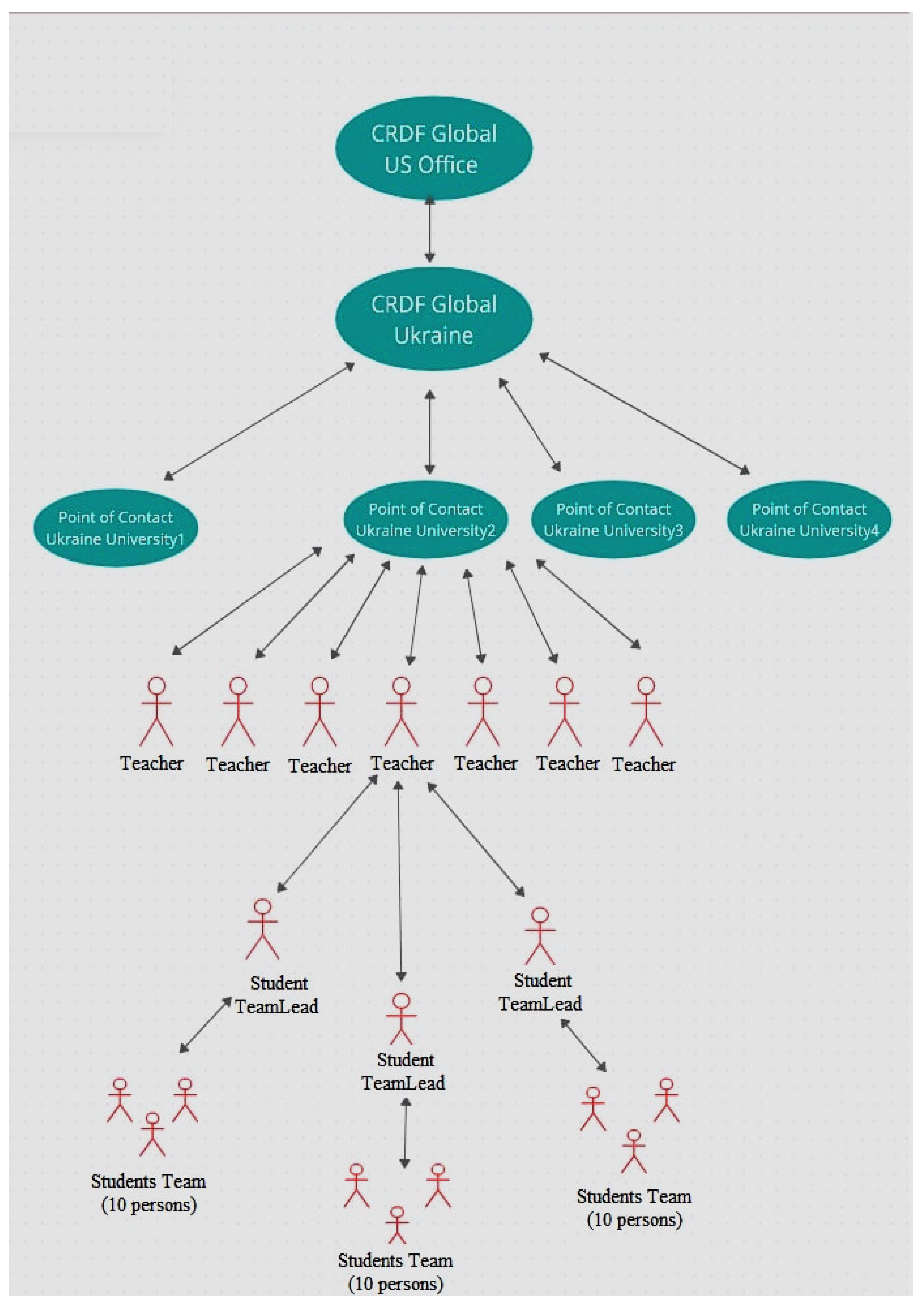
The first team example for an educational project is illustrated in
Figure 2. In fact, there are two teams, connected by the teachers. Primarily, the US CRDF Global Office in Arlington with the help of the Ukrainian CRDF Global Office in Kyiv organized testing of the online educational course “Cyber Hygiene E-Learning” in the four Ukrainian universities. Each university authorized a point of contact person responsible for communication with Kyiv’s office as well as organizing a number of teachers and explaining their role in the project of engaging students, organizing seminars and online meetings to “train the trainer”.
Then, the second team could be organized by each experienced teacher with about ten students (the lower part in
Figure 2). For better communication with the student team, they had a student team lead who always kept in touch with their teacher. The activity during the project has been illustrated by flowchart in
Figure 3.
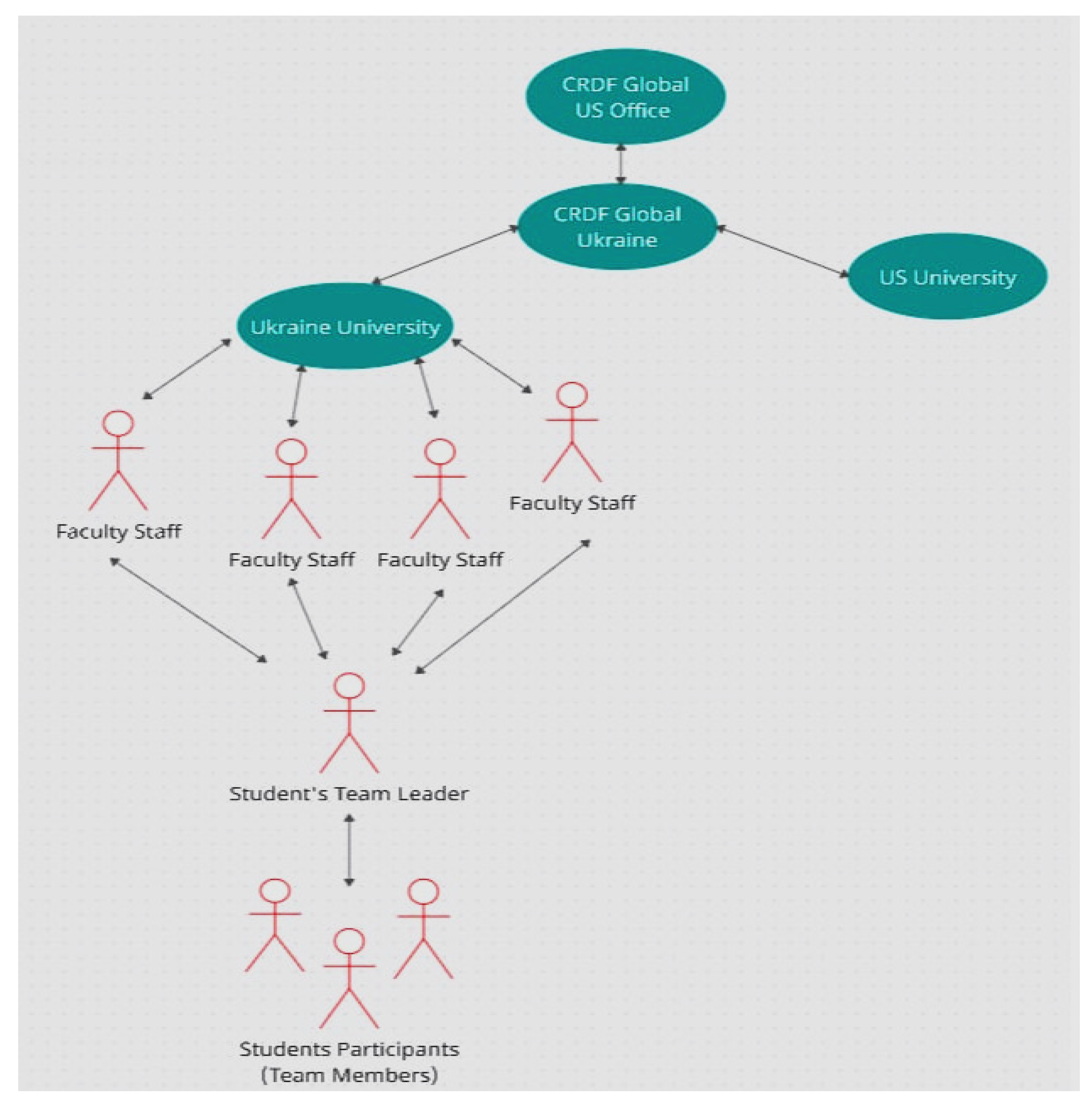
The second example of a research project is illustrated in
Figure 4. Instead of the four Ukrainian universities in the second row in
Figure 2, here are two participating universities: Our Ukrainian university and US university partner (Purdue University in Indiana). Each university has its own principal investigator, a person responsible for communication with the officers of the CRDF Global Ukrainian Office in Kyiv on the one hand, and with their university faculty staff participants on the other hand. Each faculty staff participant communicates with their own student team with the help of the student team leader of the student group.
For this project, we applied the same model to a group of participants consisting of 16 students. So, we had 4 such groups, and approximately 4 students were distributed in each group for comfortable communication. Teachers, who were recorded as Scrum managers, took part in all discussions. Faculty had a mentoring plan in which they worked with teams of students to achieve project aims:
Understanding the purpose and objectives of scientific research, the development of creative potential:
- −
Studying the other researchers’ work in various publication databases, for example, at
https://ieeexplore.ieee.org/ (accessed on 30 August 2022);
- −
development of the ability to formulate the aim, investigations, determining the research objects;
- −
developing scientific work planning skills.
Performing direct scientific experiments, development of professional competencies and skills:
- −
Understanding the needs to implement safety measures in the laboratory;
- −
obtaining experience in working with modern scientific equipment currently used for information protection;
- −
the need for short-term planning of a scientific experiment and how to keep a laboratory research journal.
Development of generalization skills of the obtained experimental results:
- −
Writing articles for publication;
- −
writing scientific reports.
Development of social and communication skills as well as personal potential:
- −
Effective presentation skills—participation in Zoom meetings and presenting results at conferences;
- −
visiting other laboratories;
- −
communication skills in English, writing an effective resume.
Development of knowledge and skills received during university studies, professional motivation development:
- −
Programming skills for specific tasks;
- −
skills in using software tools, cybersecurity platforms;
- −
skills of understanding the application of industry standards;
- −
preparing grant applications.
The next
Table 2 illustrates the roles of the team members in our projects.
We also organized an administrative team, responsible for directly processing and executing reports on work on the CRDF Global project. A mentor team was authorized according to the relevant criteria and whose duties included the development of issues related to planning, statements, conducting experiments on a software and hardware complex, taking into account the influence of external factors of a natural and technological nature, writing articles, reports, participating in conferences and in a mentoring program and necessary communications during the project. This administrative team included faculty staff with experience in working with financial documents and experience in: Conducting scientific research in the field of microelectronic devices and their manufacturing technology, measuring internal electrical noise, web security and prevention of cyberattacks, writing scientific articles, participating in international conferences, performing the duties of master and bachelor thesis supervisor.
The engaged students had experience of working as interns at international IT companies and IT security companies as well, where they had obtained the following skills: Bash script creation, Python scripting, Linux monitoring, log analysis and SIEM correlation, Penetration testing basics, incident and case management, automation and playbooks, regular expressions, operations work—events/tickets processing—reduction of false-positive events; GitHub, Docker, Python, PostgreSQL, networking, B2 English level. Such a joint team of professional mentors together with the experienced student interns allowed them to perform the research work on the project successfully for mutual benefit of both teachers and students [
28,
29].
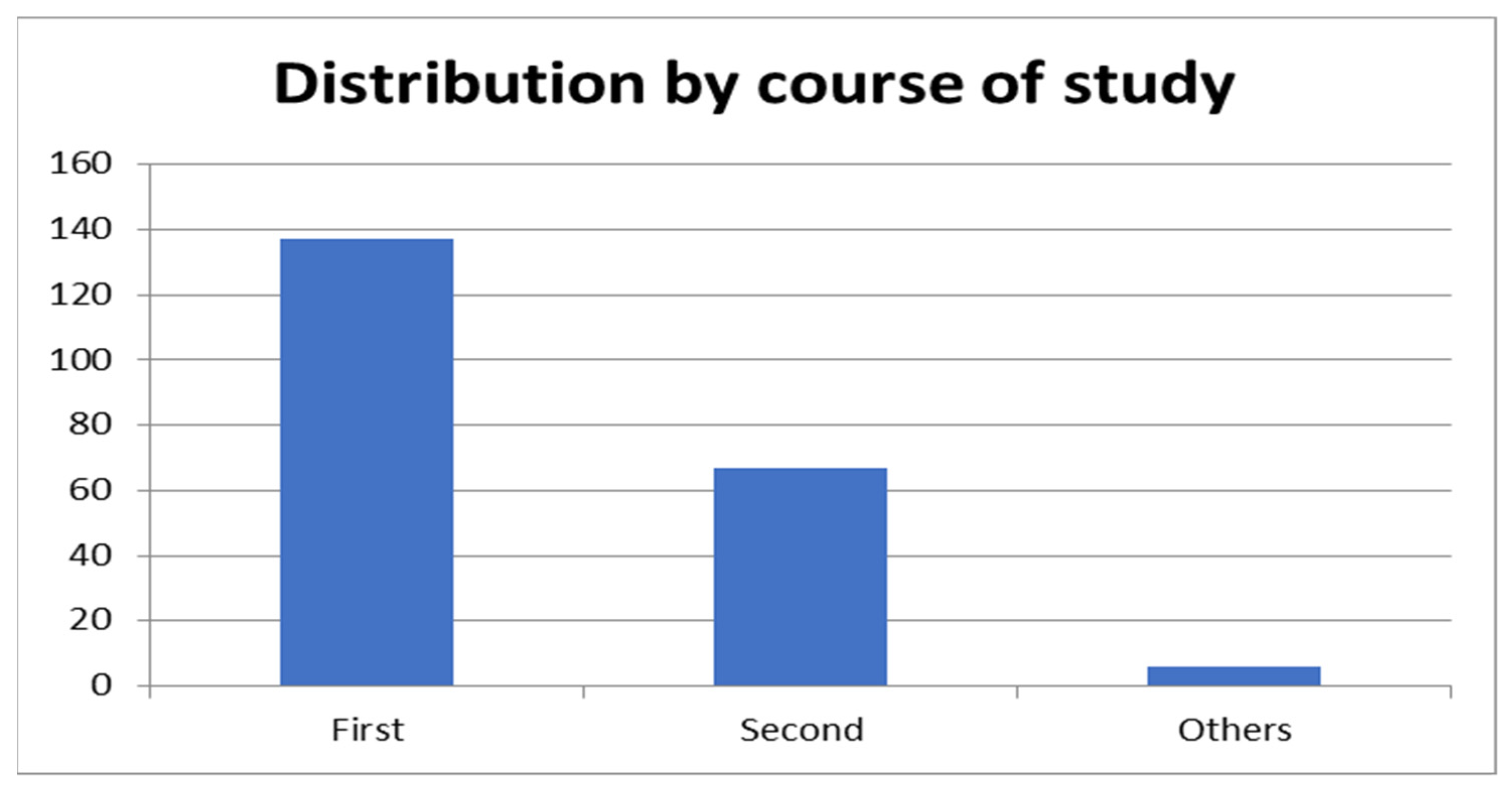
During the educational project, the first and the second-year students were the most active and demonstrated the best results in the Cyber Hygiene E-Learning course.
Figure 5 illustrates the distribution while
Table 3 shows gender composition of students.
Further visualization of statistical data of the educational project participants illustrates the distribution by specialties (
Table 4).
This course was helpful for the faculty staff because security skills for personal data and corporate information with limited access are necessary in almost every discipline. The staff actively supported the idea of using teamwork with students.
Students were asked to express their feedback about the course. For this purpose, a group was created in a Telegram channel. In the reviews, students characterized the course as accessible and clear, providing up-to-date information to protect personal data from Internet malefactors. For example: “…completed the Basics of Cyberhygiene course on the advice of the teacher, have never regretted the time spent. The course is designed for people with an initial level of knowledge in the field of cyber security, but who wants to improve…”, “…the information, presented in the form of audio and video material, helped to focus on the educational material, everything was presented in an accessible and clear way, and even what was already known was interesting to hear in this format…” or “…the information was presented easily, but in a quite interesting way, it is remembered from the first time. In general, the course itself is quite important and necessary for people, because in my opinion, everyone should know these rules…”
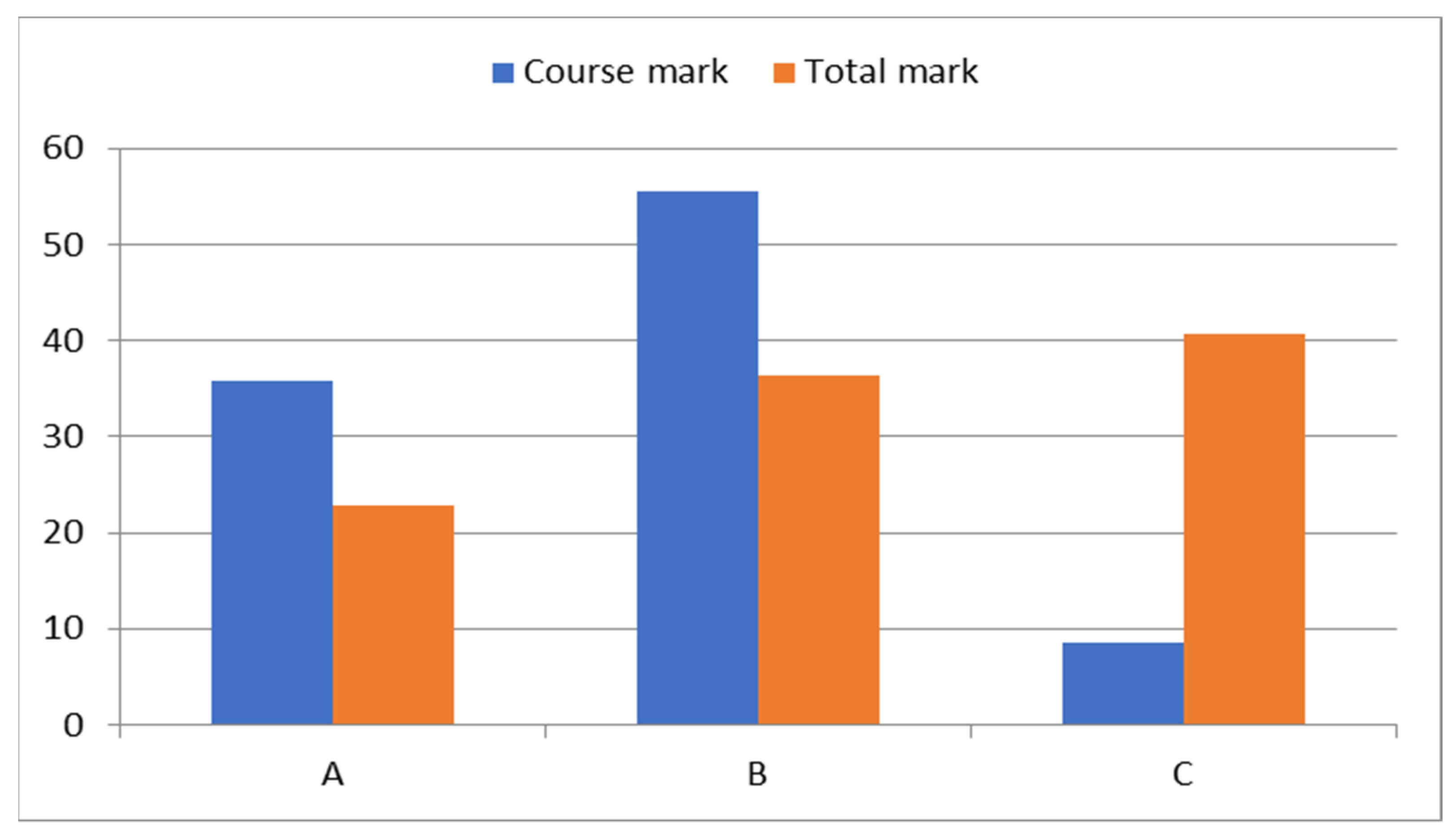
Finally, we compare the Cyber Hygiene E-Learning course marks (blue color) with the average level marks of the students in their faculties (dark orange color) in
Figure 6.
When studying the Cyber Hygiene E-Learning course, students had a diagnostic assessment at the very beginning and then, in each of the 11 modules [
11], they had a formative assessment. At the end of the course, they answered 41 test questions and that was a final assessment [
30]. The results of the final assessment are used in
Table 5 and
Figure 6. Semester rating grades were also included in the final assessment, but the exam had both written and practical components.
The diagram in
Figure 6 is in favor of the Scrum method; the average scores for the center of gravity method were calculated to assess its impact on the quality of knowledge. To calculate that, the average values of each range A, B and C were multiplied by the percentage of students whose knowledge was assessed within the boundaries of the corresponding range, with subsequent summation. The calculation results are presented in
Table 5.
Here, the authors consider that one of the important indicators of students’ training in the Cyber Hygiene E-Learning course is characterized by the qualitative grades, which were obtained from the database provided by the administrators of the course site. There were 490 students who started the course, however, only 210 successfully completed it. The condition for successful completion was obtaining a quality grade in the range from A to C, inclusively. For comparing the distribution of grades by course with the semester rating grades of students of the same specializations (for the range A–C), shown in
Figure 6, the authors compared their mathematical expectations, that is, the average grades of the range A–C. The midpoints of the intervals were determined for this purpose,
, where
, and average evaluations were calculated,
. Here,
is the percentage of students who received a grade and from the total number of students with grades from A to C.
The difference between the average marks was 3.7. An increase in the average mark by this value for the range A–C corresponds to its improvement by 14.2%. This testifies to the clear success of the Scrum method.
5. Discussion
In this section, the authors would like to consider several issues. The first one concerns the possibility of comparing the rating of semester grades of students of different specialties, i.e., different profiles and preferences in education. As already mentioned, most of the students who attended the Cyber Hygiene E-Learning course were students of the first and second year of study. First-year students have just started their studies at the university while second-year students have started their studies in the third semester. During the first year of study, students of all specialties study practically the same disciplines. The main educational disciplines of the participating students consist of mathematics and natural sciences, and foreign language, history and computer science are also common. Therefore, the study profiles are practically the same.
Two methods used in IT companies for teamwork were analyzed for modern knowledge of teaching cybersecurity students and the Scrum technology was selected as the best for the universities, taking into account experience of the wide-spread eduScrum. The Scrum implementation was successful in the case of the research project and educational project. In both cases, the student participants were very highly motivated and the teachers could easily find the team leaders among them. The educational project allowed hundreds of students to participate using Scrum methodology while the research project was provided for a smaller number of students and only for the cybersecurity specialization and the Scrum model should be changed.
The visualization of statistical data for the Cyber Hygiene E-Learning course during the educational project illustrated distributions of students by specialization, gender composition and by marks. Gender composition was almost equal. The course was the most popular among the management students.
However, the most interesting results were obtained while comparing the project course marks with the average ones in the students’ faculties, as the project course level marks were 14% greater according to
Figure 6.
The application of the Scrum method in education helps students to develop the important social skills of working with others in a team, developing tolerance for their views. These skills can be used later in the workplace. Additionally, wide testing of the same course in different countries, such as in the platform [
23] for more than 20,000 participants from Albania, Serbia, Romania, Bosnia and Herzegovina, Macedonia, Montenegro, etc., allows comparison of the state of cybersecurity learning in different European countries and even using the Big Data method.