2. Cryptography and Congruences
The problem of encrypting a message so that the enemy does not understand it and the ally can decrypt it again has been important since ancient times. It is known that Gaius Julius Caesar already used a simple code in which each letter was replaced by a different one found in the Latin alphabet “three places further”, i.e.,
,
,
, etc. Important mathematicians took part in solving codes. For example, François Viète (1540–1603) deciphered the code used by Spanish troops in France. During World War II, the Germans used an encryption machine called ENIGMA. The breaking of this code by a group of British correspondents led by Alan Turing [
12] was essential for the Allied victory in the North Atlantic, where German submarines threatened the convoys of Allied ships. In the Pacific, the decipherment of the Japanese code before the Battle of Midway Roundtable brought the Americans a great advantage when they managed to sink four Japanese aircraft carriers and lost only one themselves.
It can be said that until the early 1970s, cryptography was more or less a military matter and not much was published about the theory of coding. However, the civilian, commercial and banking sphere began to make more and more use of wireless data transmission, which could also be “sensitive”. Therefore, there arose the need to find a simple cryptographic algorithm used for secure and fast data transmission. In November 1976, it was formally adopted in the USA as a federal standard called DES (Digital Encryption Standard) [
13]. It was a cryptographic system with a secret key, where any two users had to exchange this key before they could exchange encrypted messages. The encrypted message was very difficult to decipher for those who did not know the key.
In 1976, Diffie and Hellman proposed a fundamentally new method using the so-called public key for encryption systems. However, the system also has a secret key, and only those who know it are able to easily decrypt the text encrypted with the public key. The implementation of this system was proposed by Rivest, Shamir and Adleman (a so-called RSA system) [
14]. This method is related to the issue of electronic signatures or trading on the Internet. It is based on the mathematical apparatus (factorization) of natural numbers into powers of prime numbers. It is an encryption in which each of its principles is known and is public, but no one decrypts the encrypted information, because the public key only (i.e., knowledge of the encryption principle) is not enough. To decipher the cipher and read the message, it is necessary to obtain prime number elements of prime factorization that can only be obtained by the recipient of the message who also knows the private key (that is, some necessary information on how the product originated). One of the first standards was RSA-768 [
15], which represents a 232-digit number. The standard has been broken by scientists by bringing together hundreds of computers that have been working for a period representing 2000 years of one computers work. Later, the RSA-1024, RSA-2048 or RSA-4096 standards have been developed which are used today. The use of linear congruences for coding problems stems from knowledge from the 18th century, which has started to be used practically now in the 20th century.
Thus, we can easily algorithmically decompose only numbers of a certain “small” size into the product of prime numbers and this fact is the basis of virtual security. If we take two very large prime numbers, where both the first and the second represent some information, it is easy to multiply them with each other, giving a very large composite number practically decomposable (unless we know the so-called private key, i.e., some necessary information how the large number came up). Algorithms that would look for the factors of a product by “brute force”, i.e., by trying all possibilities, would have a tremendous time complexity [
16]. The principle of coding a given message
using the RSA method is that we take two large primes
and
, which mutually different such that
and
,
. We create their product
, which is publicly accessible. However, only one who knows both primes
and
can easily calculate the value of the Euler function
. For those who do not know from which primes the product originated, it is very difficult to calculate the value of
because the decomposition of the large number which originated as a product of prime numbers is demanding. Now we choose any number
, incommensurable with
, except
and
. This number, a so-called encryption exponent, shall also be disclosed. Anyone who knows the numbers
and
can encrypt their message by calculating the number
for which
holds true. The author of the message must calculate the so-called decoding exponent
, presented by a private key. It can be found as a solution of the congruence
. It holds true that
and the search for the number
is performed by Euclid’s algorithm [
17], so there exist integers
,
such that
. Then,
and thus
is divisible by
and
. The decryption of the encoded word
consists of the following steps. We know that
. Let
, then
. As
, then according to Euler’s theorem [
18],
and also
then
The last relation describes that in order to decrypt the encoded word
, it is sufficient to calculate the smallest non-negative remainder by dividing the power
by the number
, which is an easily solvable task. The RSA method is the simplest one and it shows how modular arithmetic has a practical application. The RSA method has become very widespread in e-banking, online shopping, electronic signatures, etc. [
19].
We will show the RSA encryption principle using the congruences on a specific example. We will encrypt (and decrypt) the name (message) “REX” by RSA method using prime numbers , . We will work with the letters of English alphabet, A, B, C, D, E, F, G, H, I, J, K, L, M, N, O, P, Q, R, S, T, U, V, W, X, Y, and Z, assigning each letter a numeric two-digit number, sequentially to letter A—01, to letter B—02 etc. to letter Z—26.
Then the word “REX” in numeric form will presented by number
. Now, we will encrypt letter by letter. The product
, hence
[
20]. Let us choose, e.g.,
as the encryption exponent so that
. Now we have to calculate the number
that
. Using the Euclidean algorithm, we get
,
,
a
. Next
. From that we see
, and therefore
. Then the decryption exponent is
.
As we encrypt letter by letter, we now have to calculate the numbers
such that
(resp. we solve the Diophantine equation
, because
) sequentially for
. Now we calculate
, so we’re searching such
that belong to the same residual class as the number
modulo
. It holds
Analogously from congruences
and
we get the remaining values 26 and 52 for
. To decrypt the message back with the private key
letter by letter, we first calculate the congruence
and we get
, which represents the letter R. The same way we calculate the remaining two congruences
and
. The results obtained are shown in
Table 1.
More information on RSA cryptosystems using congruences can be found, e.g., in [
21].
3. Results
Consider
, while
. Then we say that number
is congruent with number
by module
(or we call it modulo
), if
. Additionally, we note
The number
is called the left side, the number
the right side of congruence. The notation
means that the number
is not congruent with number
by module
., i.e.,
[
22].
The relation of congruence is:
Now we show that if and then . From it applies and from it applies. Then and , thus . Then , and therefore . Out of previous .
Furthermore, if
and
is any integer, then:
Because if , then . As , then , out of which .
Now consider the congruence system:
Then . The formula can be proved by mathematical induction. First let . Then we must show that . Let us denote . From the assumptions of the first and second congruence the following applies and , and thus . The second step is analogous.
From the last statement we can deduce the result that if
and
is any integer, then:
Next, let
. Let
be an integer with properties
,
,
. Then:
To prove the validity of this formula, let us denote , . Based on the assumption , it is valid that . As , it is valid that . Then , thus .
Again, let
and
be a common divisor of numbers
,
,
. Then:
If it is true that, then there is such an integer , that . After dividing by number we get , which means that , and thus .
Next consider any natural number
. According to the division with remainder theorem [
23], we can write every integer
in the form:
While the number is called the remainder of division of the number by number . Now let us decompose the set to subsets in such a way that is the set of all those integers whose remainder after dividing by a number is .
Then the sets are called the residual classes according to a module (or we talk about modulo) . The residual classes are disjoint by pairs and each integer belongs to one of them. At the same time the set is a set of all integers , to which it applies that . If modulo is known, we simply refer instead of .
Integers and belong to the same modulo class if and only if . We can prove the validity of the statement from both sides.
I. Let us express the numbers
in the form:
Then , i.e., , and then .
II. Now let and . Suppose for example that . As , then . However, then , out of which , but that is a contradiction because . Similarly, a contradiction arises from the assumption . It must therefore apply , and then numbers a belong to the same residual class.
The -tuple of numbers is called a complete residual modulo system , if for . We say that the residual class by module is reduced if . For example, the residual class is reduced modulo 7, because . The class it is not reduced by any module.
If is a reduced residual class modulo , then for any it applies . Because it is valid that , thus , and therefore there exists such an integer that , thus . Then every common divisor of numbers and would also be a divisor of number , and thus the common divisor of and . However, as , it is valid that .
There exist
reduced residual classes of modulo
[
23]. We say that
-tuple of numbers
forms a reduced residual modulo system
if numbers
are selected one by one from the reduced residual classes. The elements of the reduced system are coprime with
. The reduced residual system can be obtained by omitting numbers that are commensurable with the module, from the complete. E.g., if
. The complete residual system consists e.g., of numbers
. We will choose
6 from those because they are commensurable with
, so we get a reduced residual system of 1,3,5,7. It is valid that
.
Generally, all non-negative numbers less than coprime with form the smallest non-negative reduced residual system.
If
is a reduced residual system modulo
and
, then
is a reduced residual system too, by module
. Numbers
belong to different residual classes and the same can be said of numbers
because of congruence
under the condition
the following results:
The count of numbers is while . It means the numbers are selected one by one out of the reduced residual classes.
Let
and
are any reduced residual systems modulo
. Then
Each
is congruent with just one
because both groups are selected one by one from the reduced classes. Additionally, the evidence then results directly from the properties of the congruences, while if:
then
.
A linear congruence with one unknown is a congruence in the form:
The solution of linear congruence is such a residual class that applies. A congruence is called solvable if it has at least one solution.
Congruence
can also be written in the form:
which actually gives a linear Diophantine equation with two unknowns [
17].
A linear congruence is solvable if and only if If module and coefficient are coprime, then linear congruence is always solvable and the elements of one residual class are the solution.
Let is a solution to congruence and let . Then all the elements of the set are a solution to congruence . Thus, a solvable linear congruence has infinitely many solutions. This follows directly from the basic properties of congruences and residual classes. If , then and .
If
, then congruence
has just
mutually non-congruent (or we talk about incongruent) solutions. Let us denote
. Let
is such a congruence solution
to which it applies
. Additionally, let us examine numbers that are in the form:
These numbers are congruent
because it is true that
because
is an integer, and thus
is a multiple of the number
. Now we indirectly prove that the numbers
are non-congruent with each other according to modulo
. Suppose:
From this, based on common congruence simplifications, we get:
which is not possible, because
while
. Vice versa, if
and
are different solutions to congruence
, then the following applies:
As
, it is valid that:
So, all solutions of congruence that belong to the interval are congruent with by module and are in form of and all remaining solutions are congruent with some of the solutions.
A linear congruence can also be solved using Euler’s theorem [
18]. If we have a congruence
where
, then the number
is one of its solutions. Because it is true that
.
4. Research Methodology
The research was carried out at a selected university in the Slovak Republic with the knowledge and consent of the faculty management. Before the start of the research, all students of the 1st year of bachelor’s study in computer science study fields were addressed. A total of 38 students volunteered for the research. All participants in the research were informed about the anonymity of the obtained data. The methodological research is based on the claims of Dahlin and Watkins [
24], according to which the connecting point between memorization and comprehension is meaningful repetition. Meaningful repetition creates a deep impression, which leads to memorization and can also lead to the “discovery of a new meaning”, which leads to understanding [
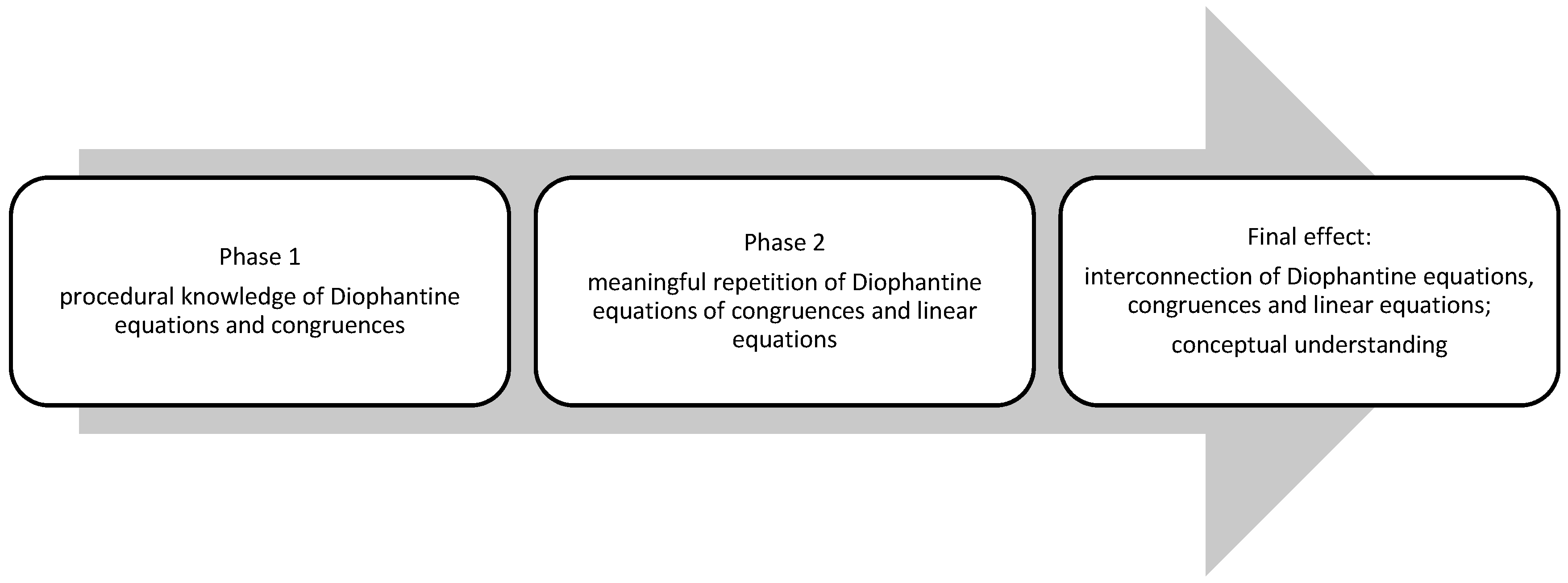
25]. Therefore, we divided the teaching of congruences into two phases (
Figure 1):
Phase 1—teaching congruences with a focus on the development of procedural knowledge about congruences, Phase 2—“meaningful repetition” of congruences in order to create a conceptual understanding of the concept of congruence in students. This division is theoretically based on the finding that improving procedural knowledge can support the improvement of conceptual knowledge. Evidence comes from studies of carefully constructed practical problems [
26,
27,
28,
29]. We used the solution of Diophantine equations in the second phase as a “tool” to connect between congruences and linear equations. According to [
30], this connection is very important for the successful solution of congruences.
In the first phase of the research, students completed a seminar on mathematics consisting of two parts: (a) solving Diophantine equations, and (b) congruences. The seminar was realized in the form of full-time teaching. In this phase, students became acquainted with the basic algorithm for solving Diophantine equations. We solved linear Diophantine equations with two unknowns in the form
,
, while explaining the algorithmic solution procedure. As the solution procedure required knowledge of the Euclidean algorithm, this was taken over separately [
31]. Subsequently, they adopted the concept of “congruence” and their basic properties. Then simple congruences (equations on the set
) were solved. Within the curriculum of congruences, we first took over the basic properties of congruences and the basic theorems for working with congruences. We have separately explained the residual classes and definitions as a complete or reduced residual system. We have defined a linear congruence with one unknown in the form
and showed an algorithm for its solution. We explained conditions for solvable congruence and what congruent and incongruent solutions mean (
Section 3, part Equations (15)–(22)). The same time was devoted to both parts of the seminar. After completing the seminar, a pre-test was carried out, in which tasks from both parts of the seminar were equally represented (two tasks from each thematic area). Students had 60 min to solve the four tasks. We asked students to measure the real time they needed to solve each task in addition to solving the given tasks. In the second phase of the research, after passing the pre-test, the same students completed another part of the mathematics seminar, where attention was paid to the connection between congruences and Diophantine equations. In this part of the seminar, students were introduced to the method of using congruences to solve Diophantine equations (
Section 3, Equation (16)). This can be considered a meaningful repetition in order to link the solution of congruences with the solution of equations. Thus, students can use already acquired algebraic knowledge and skills in solving congruences. After the second part of the mathematics seminar, students completed a post-test, which included two problems to be solved by Diophantine equations and two problems for congruences (as in the pre-test). In addition to solving the problems, they also recorded the time needed for solving.
We sought answers to the following research hypotheses by content analysis of respondents work and statistical analysis of respondents success in pre-test and post-test:
Hypothesis (H1): Linking congruences with the solution of Diophantine equations and linear equations will increase the success of students in solving congruences.
Hypothesis (H2): Conceptual understanding of congruences will reduce students’ time to solve congruent problems.
6. Discussion
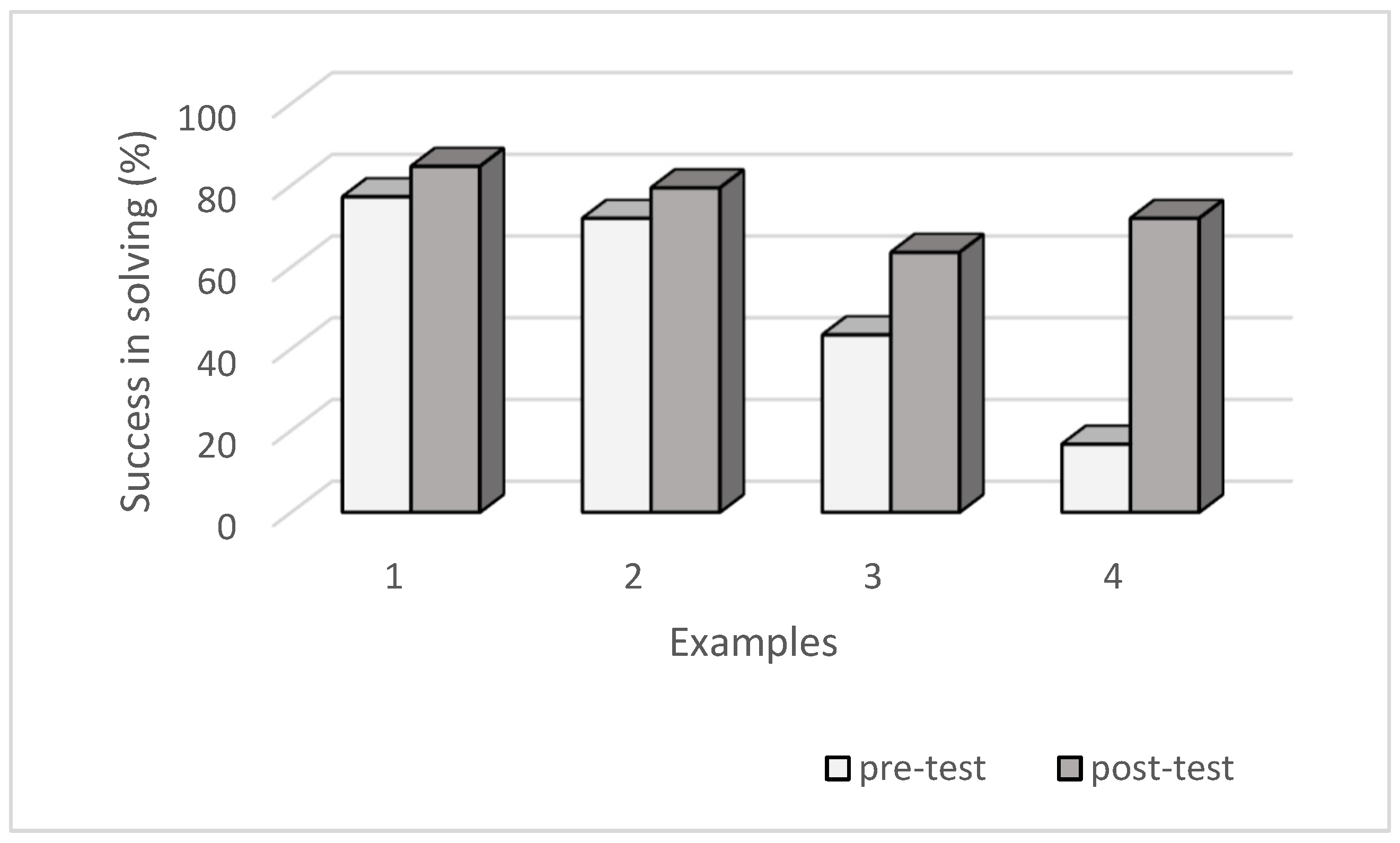
In the pre-test, which followed the first phase of teaching congruences, students recorded very low success in solving problems focused on congruences (success rate was 43% or 17%). Congruences were a new concept for them and, according to students, it was an isolated concept for them (72% of students). Isolated knowledge leads to the acquisition of skills without understanding [
32]. The solution of congruences was for them a “branched” algorithm, the memory of which caused them problems. This was evidenced by the large number of unresolved problems. Our findings confirmed the fact that learning new concepts is difficult for students if there is no network of previously learned concepts and skills with which to combine a new topic [
33]. Despite sufficient time to solve the pre-test, the students were unable to reconstruct the insufficiently memorized algorithm. This indicates their focus on acquiring procedural skills without understanding the individual steps of the algorithm [
34]. However, a conceptual understanding of a new concept is also necessary for the successful solution of problems, and this requires the connection of new knowledge with already acquired knowledge [
35]. In our case.
There is a need to link the concept of “congruence” with knowledge of equations and their solutions. Based on the results of the pre-test, students did not find this connection. The same conclusion was found out by [
36], according to who university students in the USA, future teachers of mathematics did not find linear congruences analogous to equations. The high success of students in the pre-test in solving Diophantine equations was probably conditioned by the existing connection with the term “equation” and students learned a new algorithm for solving another type of equation. It is also evidenced by the fact that some students solved Diophantine equations by choosing one unknown as a parameter and then expressing the other unknown depending on the value of the parameter. In rare cases, we also recorded a solution by trial and error. When solving Diophantine equations, students showed faith in their own ability to solve the equation, because they could use their already acquired knowledge and skills in solving equations. In solving the congruences, the students relied on the limited possibilities of the memorized “branched” algorithm. In the post-test, the students were divided into two groups for Diophantine equations. One group of students (mainly those students who successfully solved both problems on Diophantine equations in the pre-test) did not use congruence to solve a simpler problem. They preferred the already “proven” way of solving Diophantine equations. This approach of students corresponds to the knowledge that when students learn a new, more effective procedure, they do not always abandon the old procedure. Instead, they use either the old procedure or the new one, depending on the situation. Only with time and practice they stop using fewer effective methods [
37,
38]. In the second (more complex) problem, they considered a method of solution—to use or not to use congruences. According to their own statements, they considered which of the procedures would lead to the result in a shorter way. In determining how to use as few computational steps as possible, students analyzed the problem, demonstrating the ability to think of higher order [
39]. These students mastered the solution of congruences at a higher level of knowledge, such as understanding, because they were able to evaluate the suitability of using congruences to solve a given problem [
40]. The second group (most students) solved Diophantine equations using congruences, i.e., they evaluated the use of congruences as a more efficient way of solving Diophantine equations. Replacing learned practices with new more effective solutions are part of the development of strategic skills [
33]. This group of students was also more successful in solving congruences. Overall, in the post-test, the success of students in solving congruences increased significantly, mainly due to their connection with the solution of equations. The number of unresolved tasks decreased significantly.
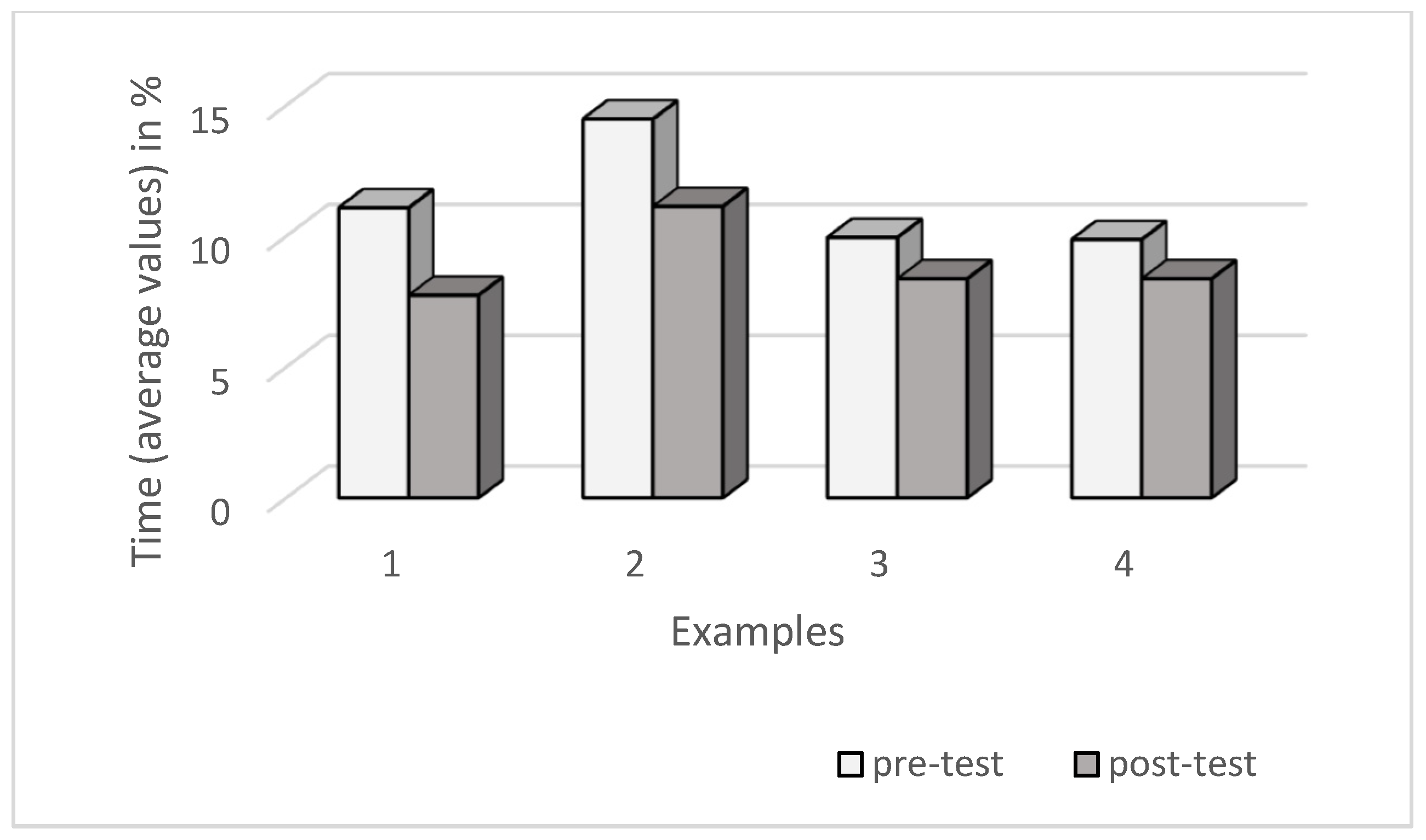
In the post-test, there was also a statistically significant decrease in the time that students needed to solve particular problems, which indicates an increase in the procedural fluency of the use of learned algorithms. Procedural fluency is the ability to flexibly, accurately, and efficiently perform learned problem-solving procedures (mostly algorithms) in conjunction with the ability to assess the appropriateness of using a given procedure [
33]. Students will acquire procedural fluency in the use of their strategic abilities to choose between effective procedures. This finding indicates an increase in the conceptual understanding of the concept of “congruence” and also an understanding of the algorithm for solving congruences. According to [
41], experience in solving diverse problems using developed procedural fluency in conjunction with experience in solving problems help students gain new conceptual knowledge. The flexibility of procedural knowledge is positively related to conceptual knowledge [
42].