A Novel Chip-Level Blockchain Security Solution for the Internet of Things Networks
Abstract
:1. Introduction
2. Brief Review of Blockchain
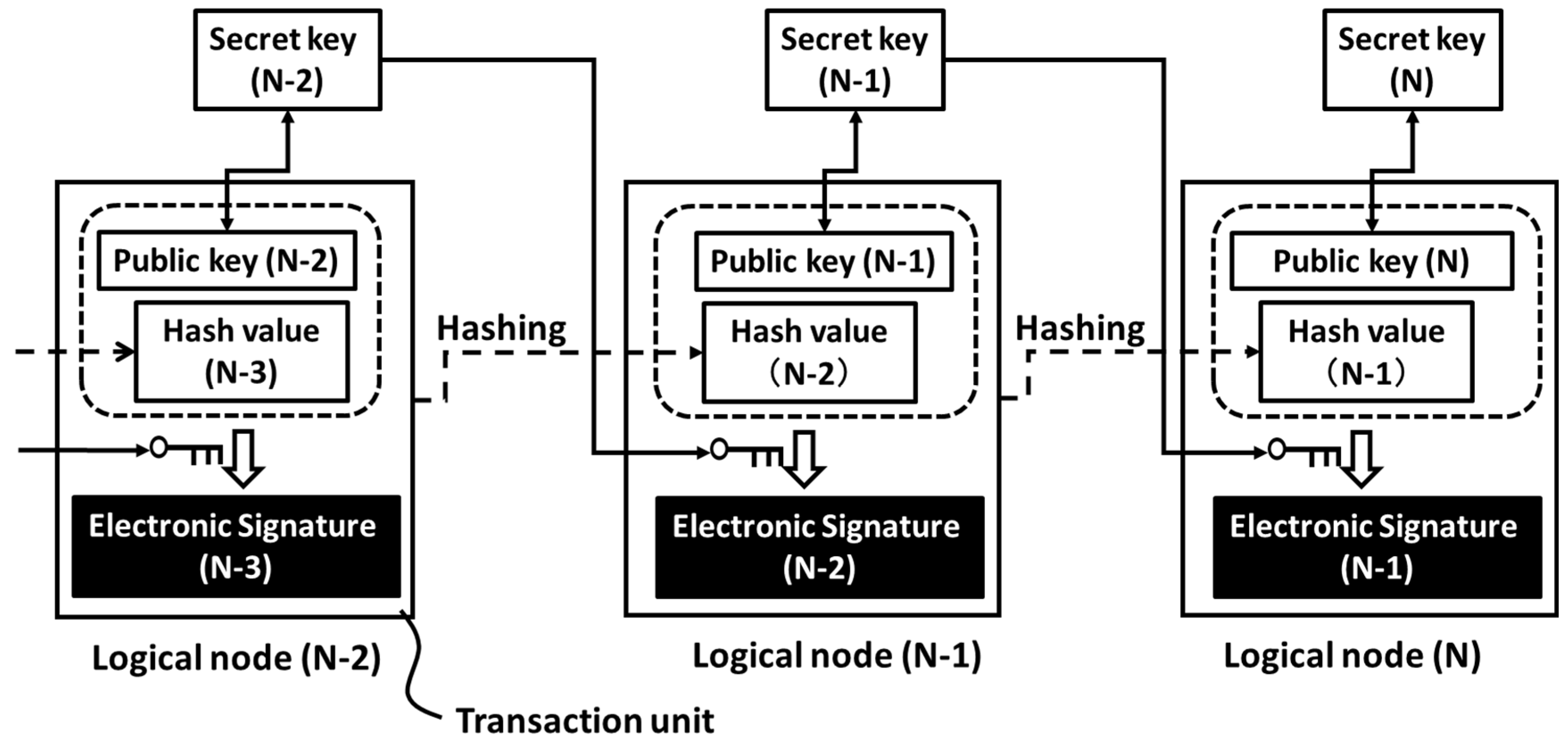
2.1. Transaction
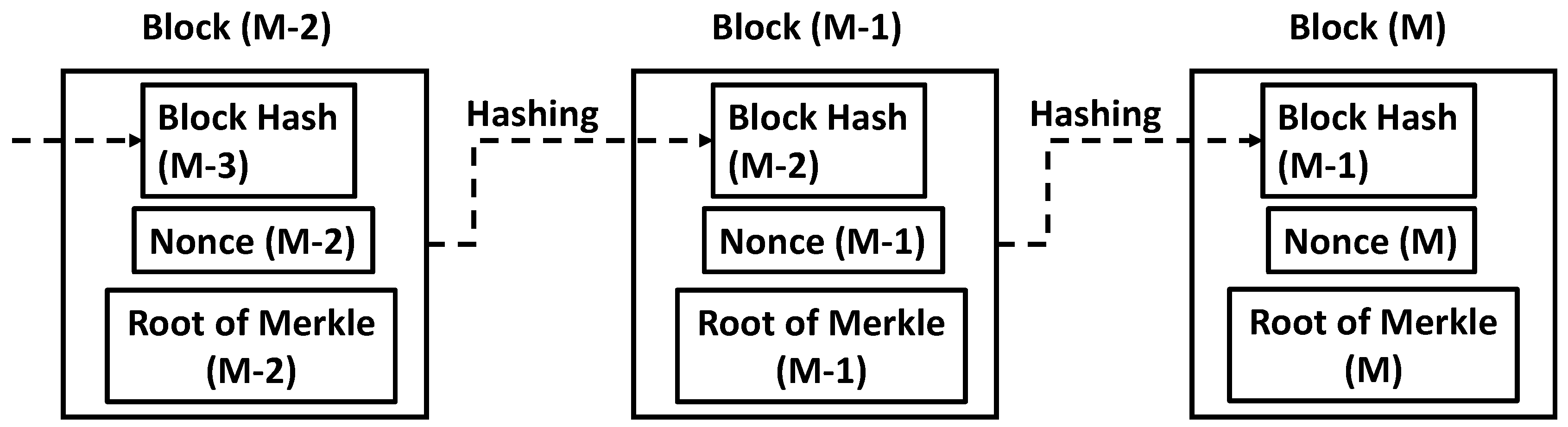
2.2. Generation of Blockchain
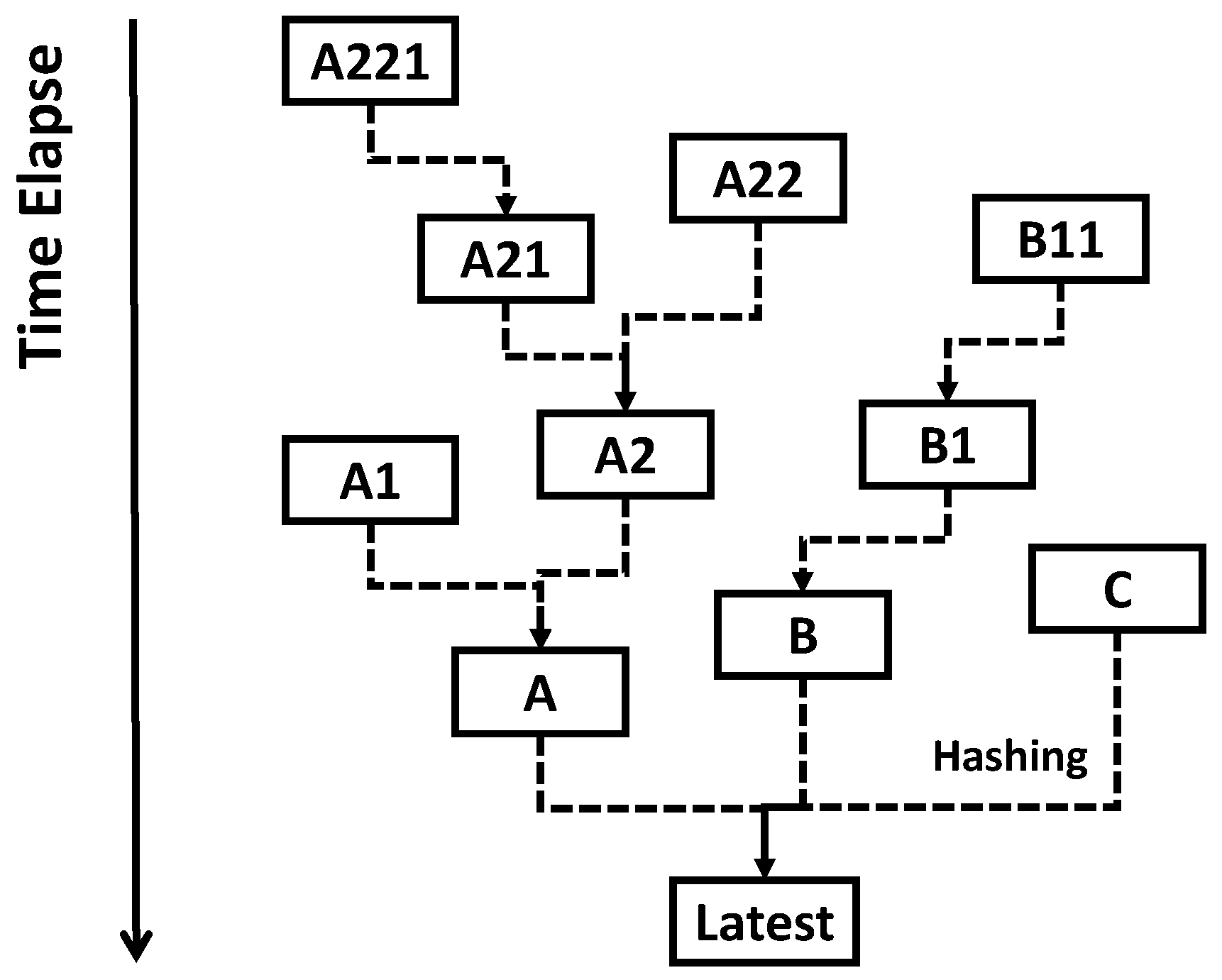
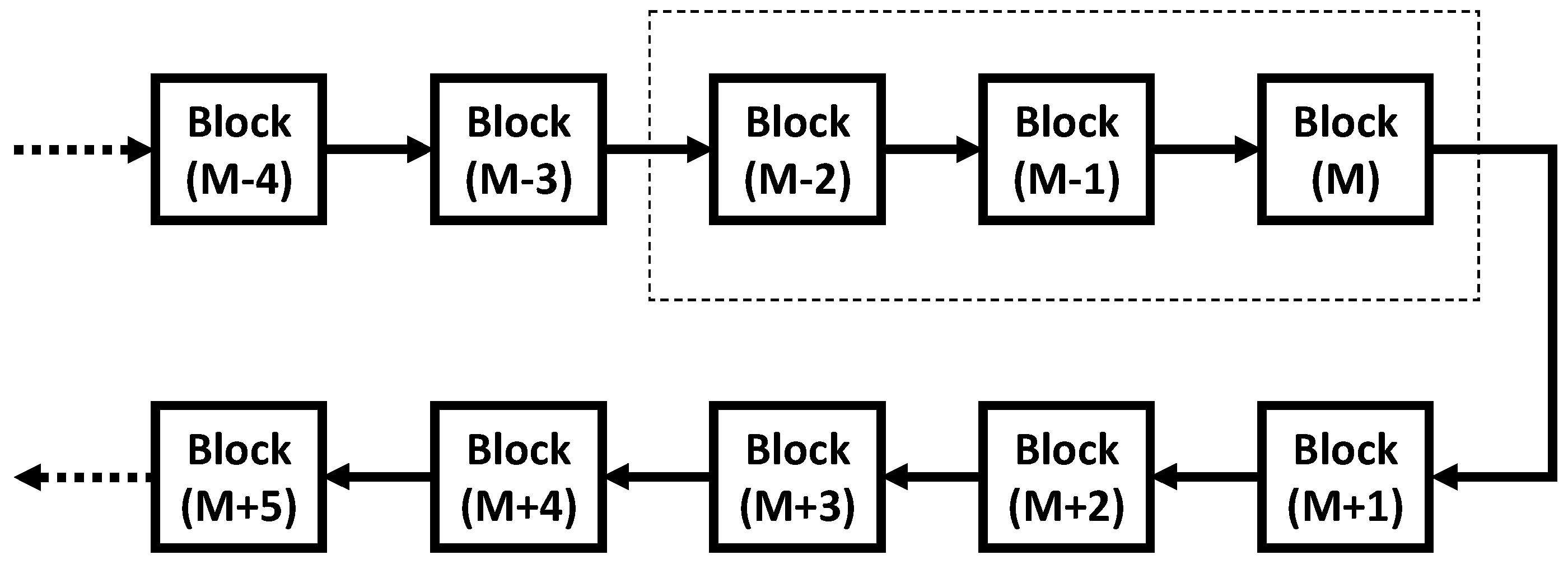
2.3. The Length of Blockchain and the Strrength of Anti-Tampering
2.4. Limitation of Blockchain Protection
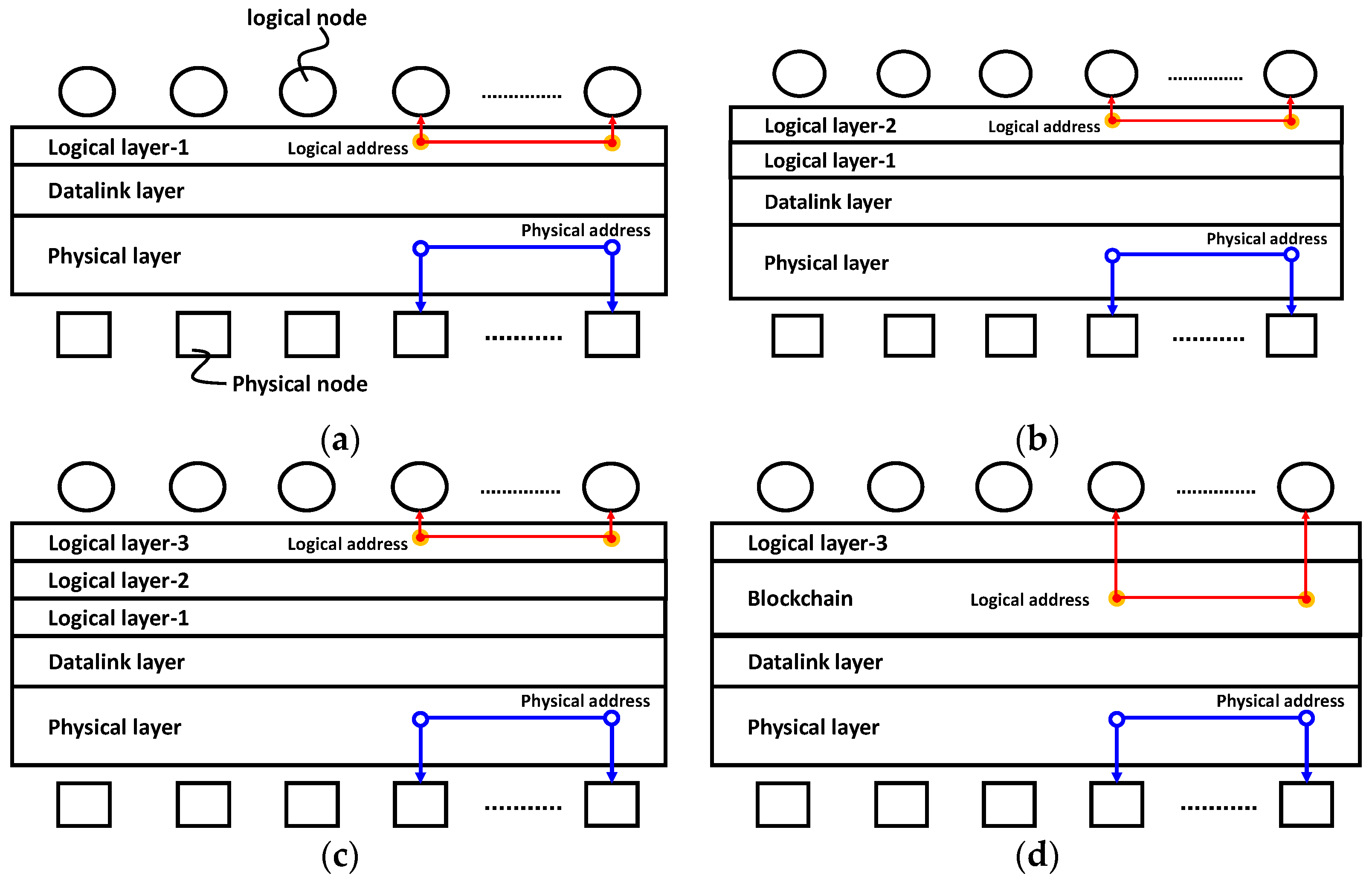
3. Blockchained IoT (BIoT)
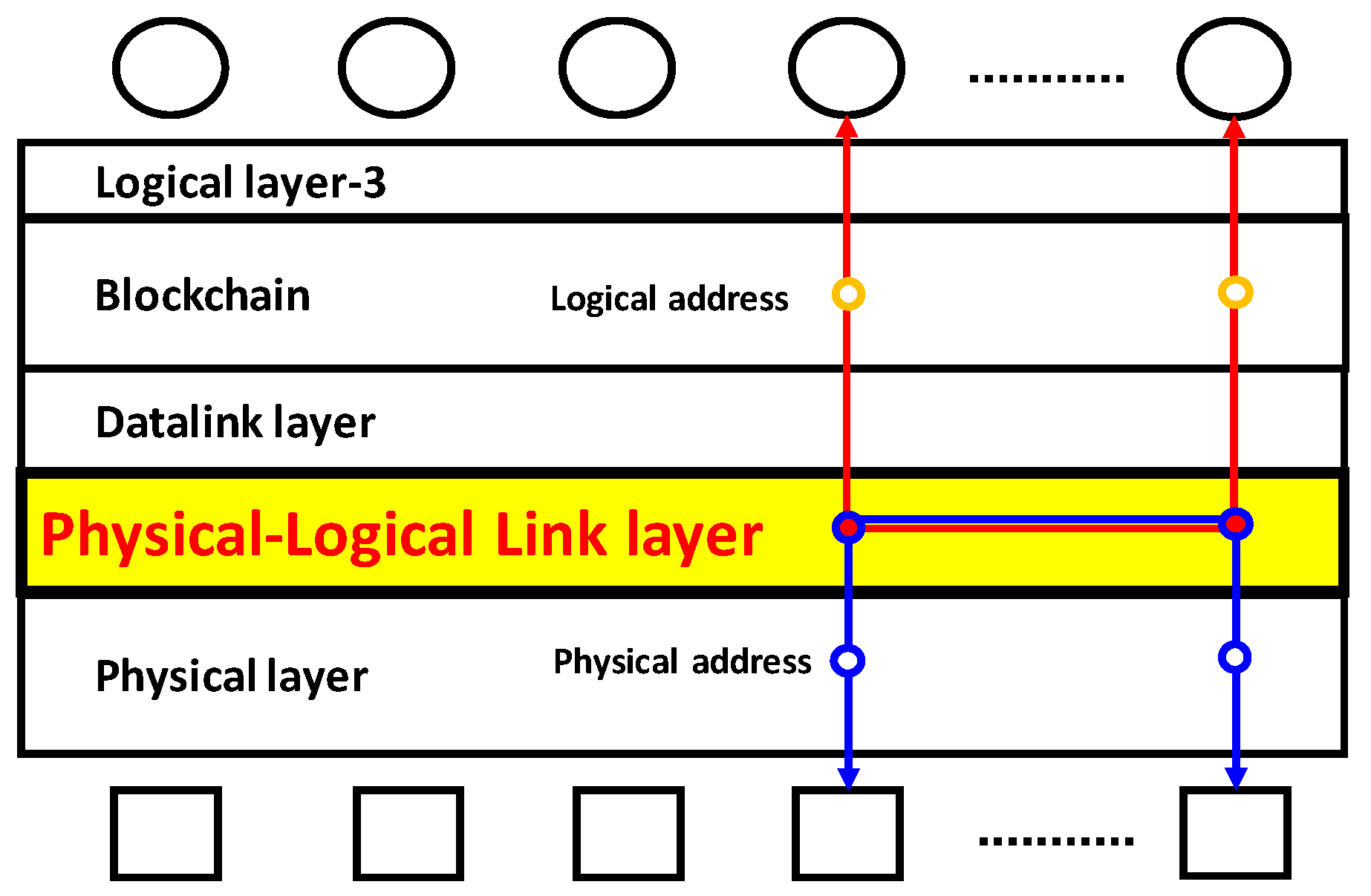
3.1. On a Chip-Level Countermeasure
3.1.1. Existing Solutions
RNG
PUF
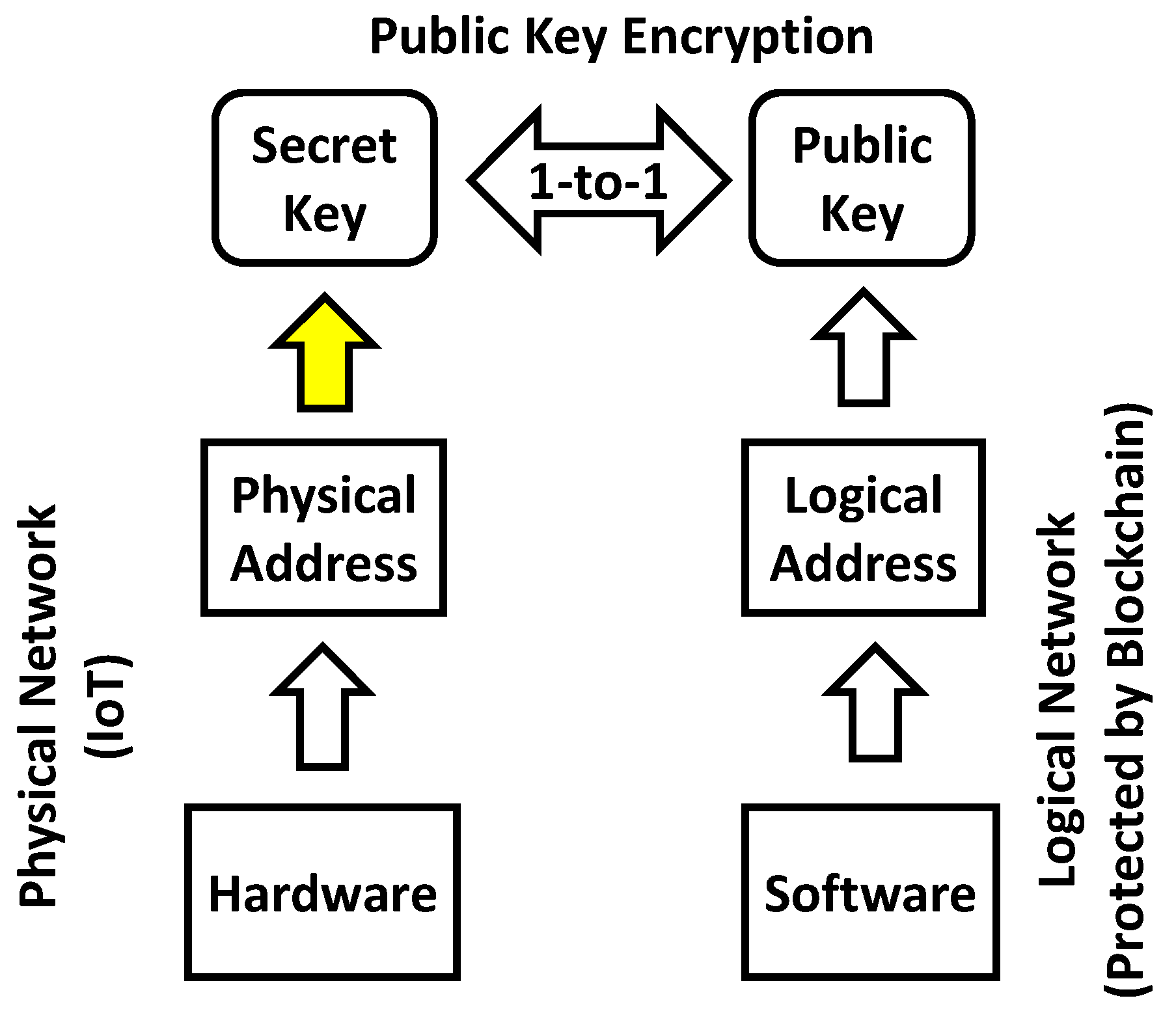
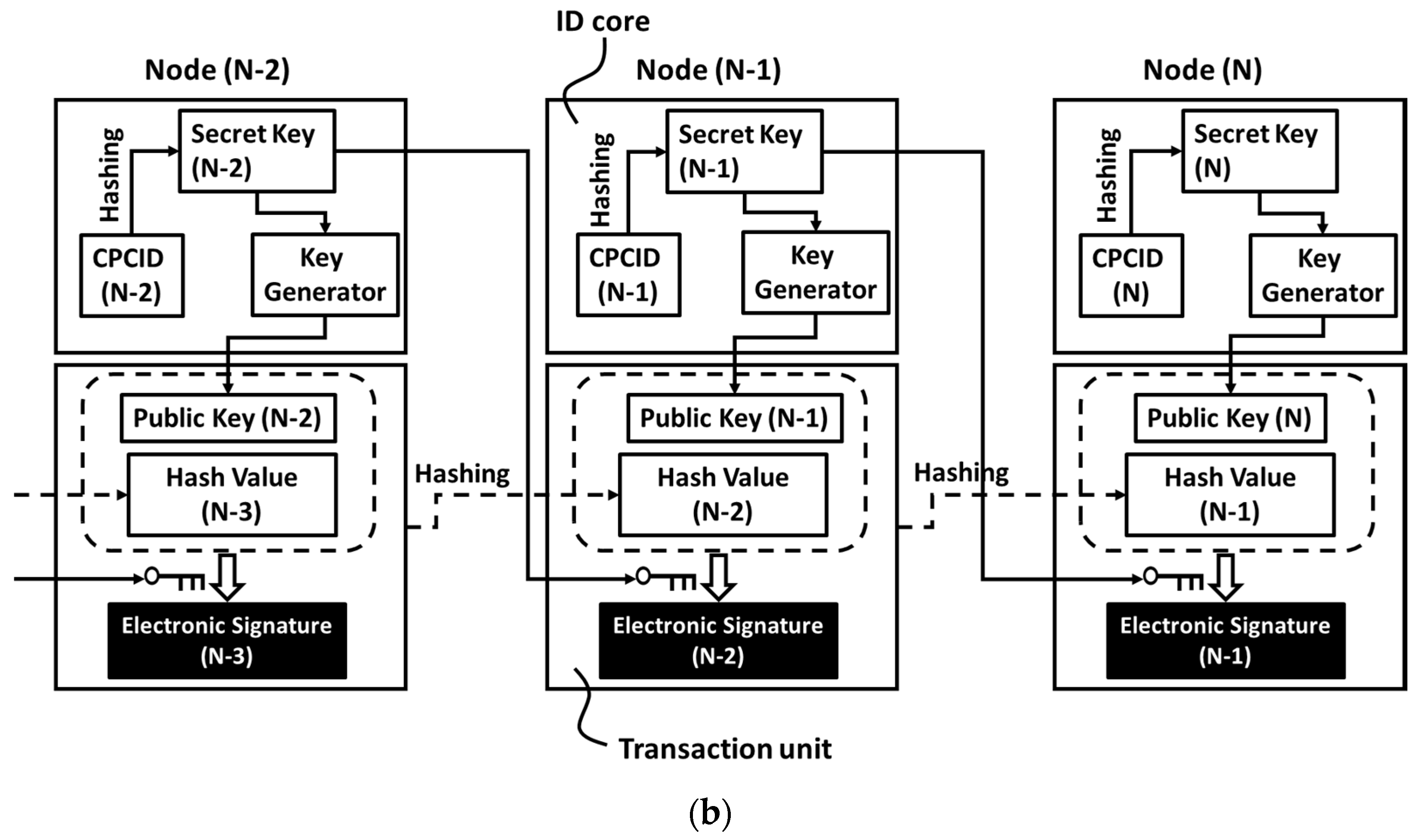
3.1.2. Cyber-physical Chip Identification
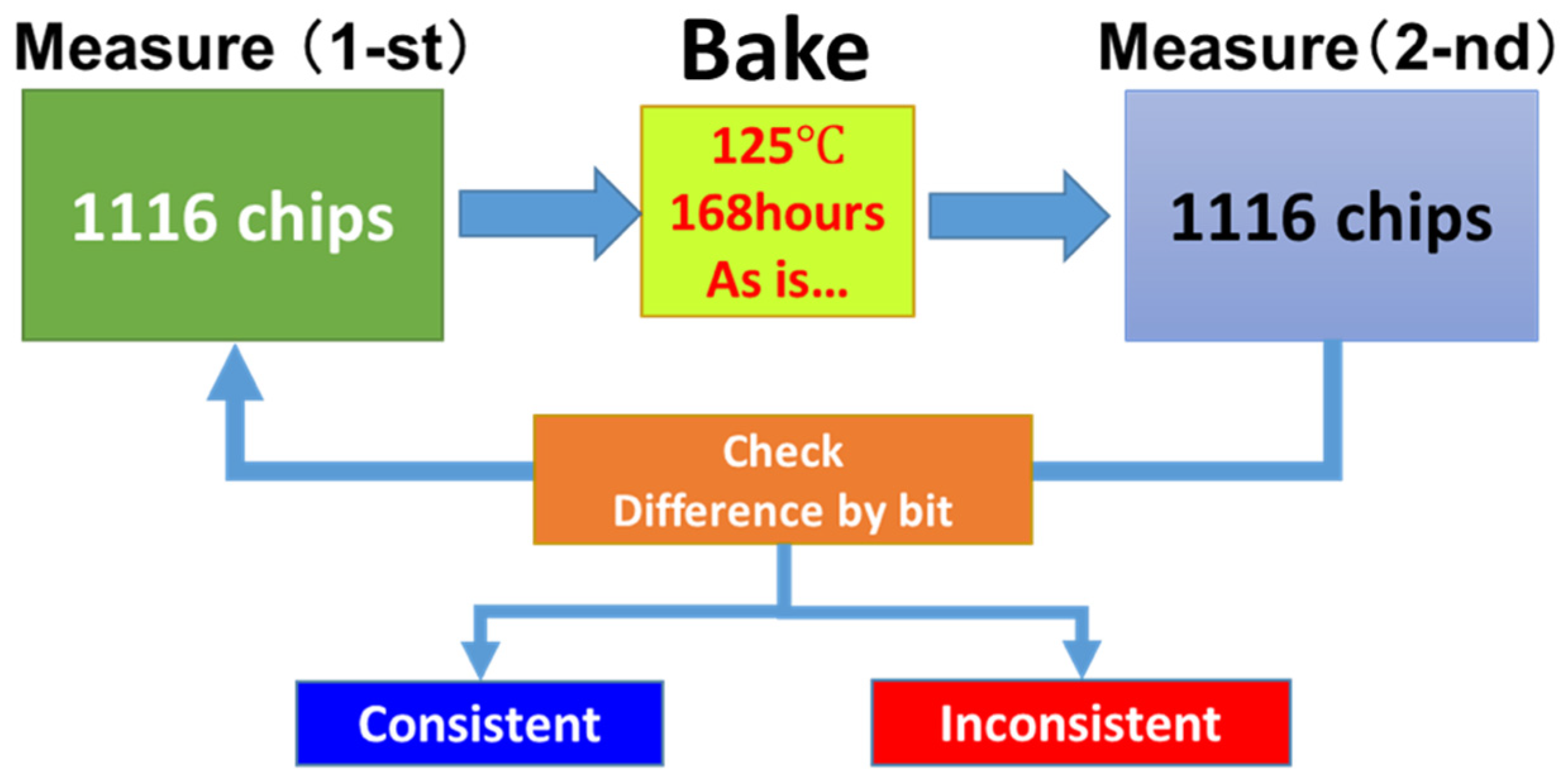
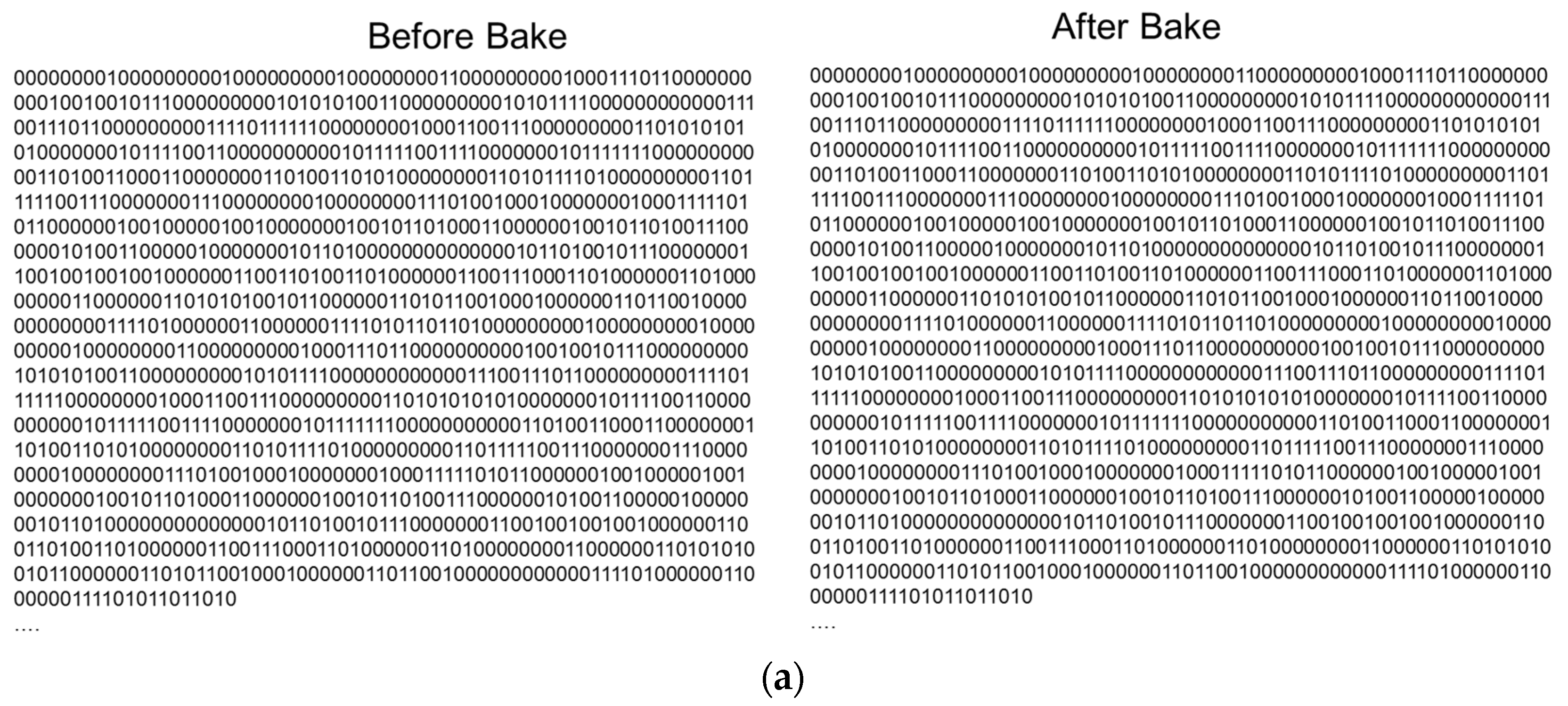
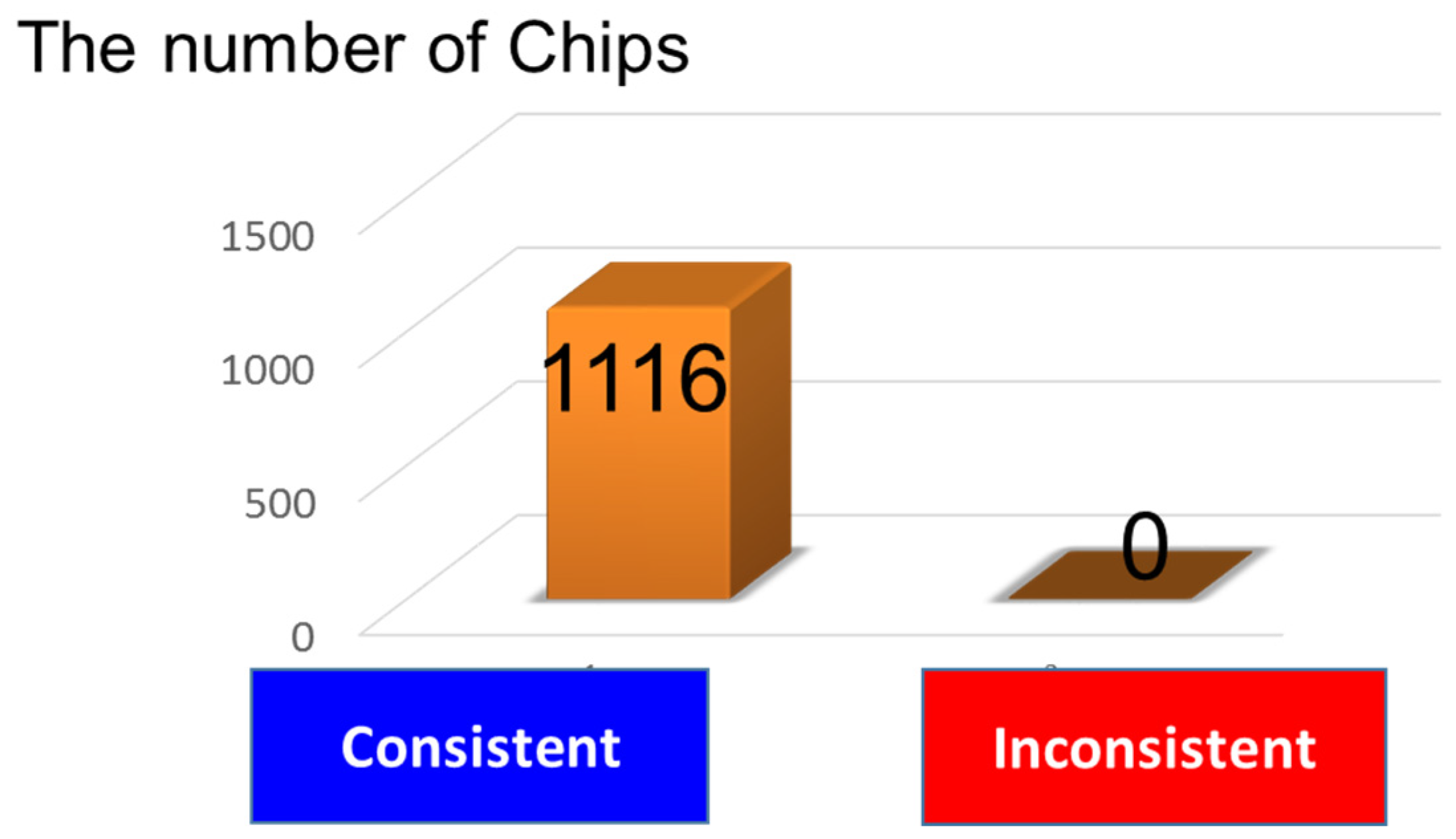
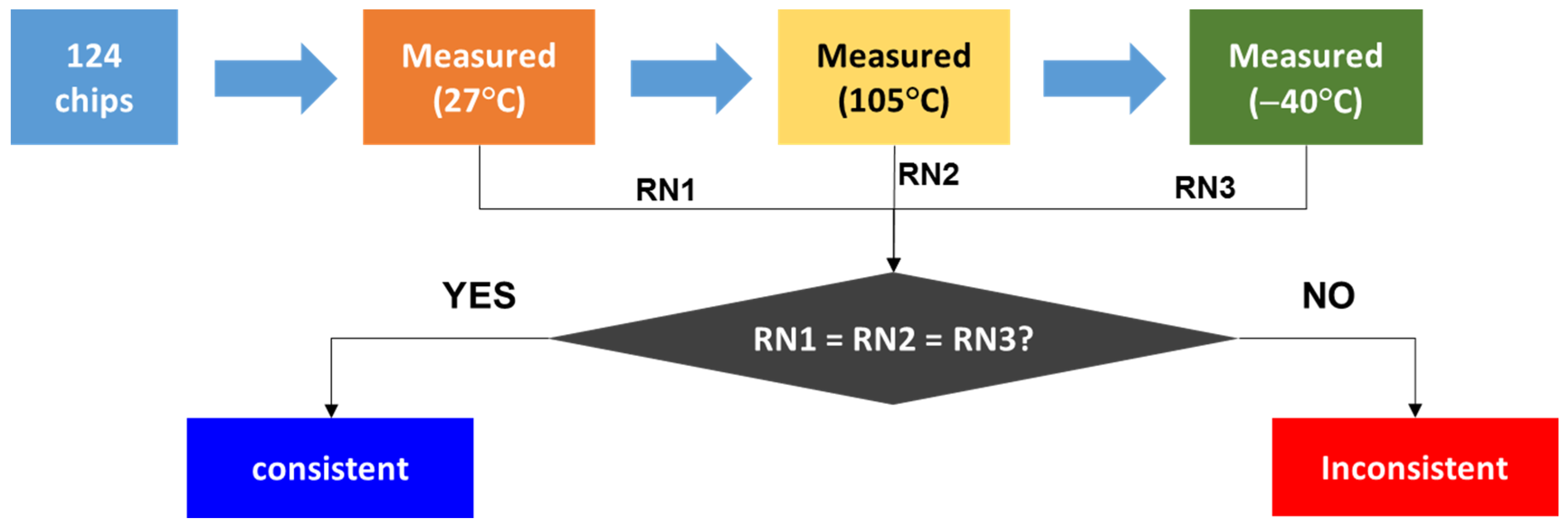
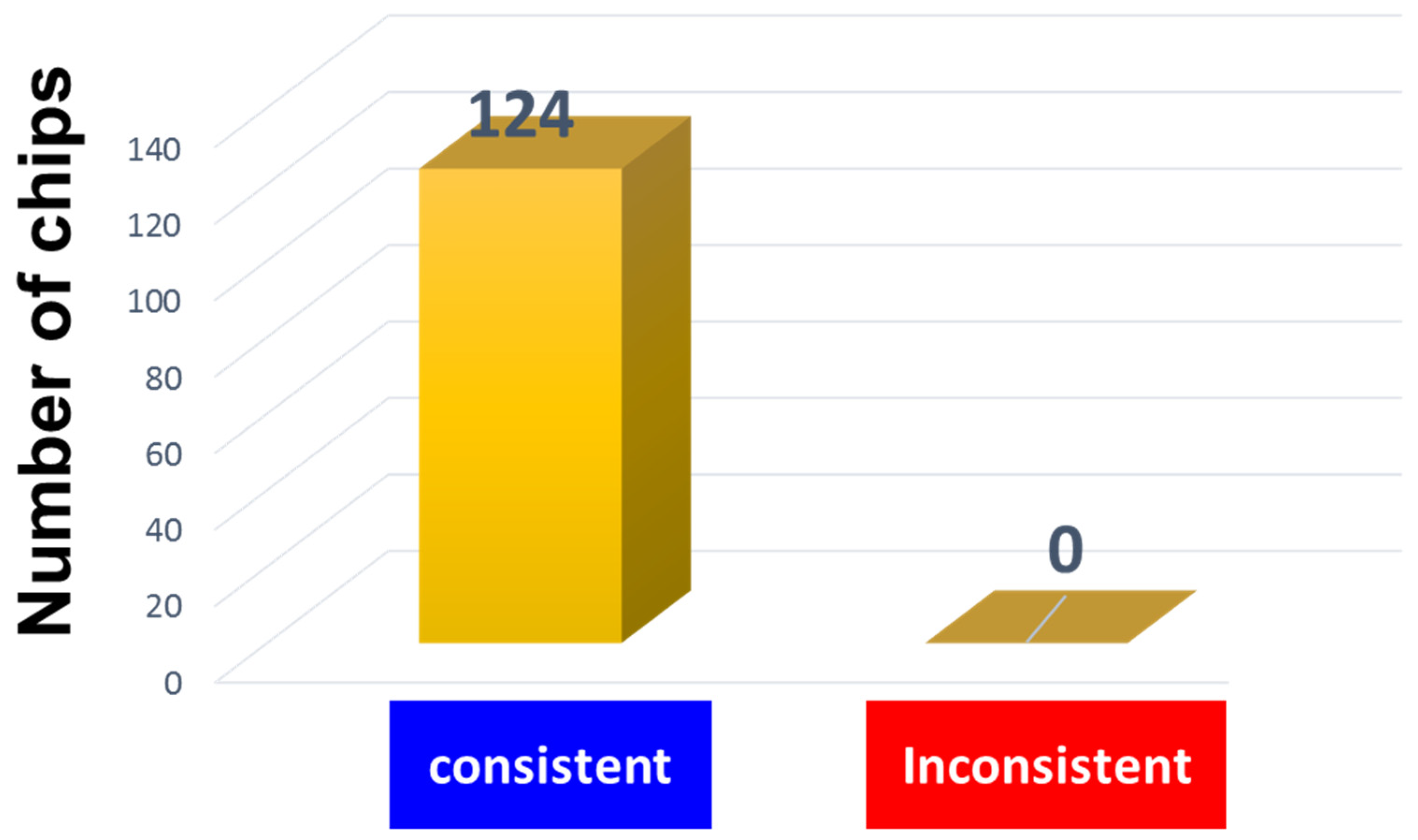
3.1.3. Experiment
3.2. Implementation of Cyber-Phsyical Chip Identification to Blockchain
4. Discussion
5. Conclusions
6. Patents
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Butt, V. How many risks are there in billions of connected devices, Zurich Insurance Group News. Available online: https://www.zurich.com/en/knowledge/articles/2015/04/how-many-risks-are-there-in-billions-of-connected-devices (accessed on 19 April 2015).
- Majithia, K. Ericsson appears to backtrack on 50B connected device vision, MOBILE WORLD LIVE. Available online: https://www.mobileworldlive.com/featured-content/top-three/ericsson-backtracks-2020-vision-connected-devices/ (accessed on 3 June 2015).
- Roman, R.; Najera, P.; Lopez, J. Securing the internet of things. IEEE Comput. 2011, 44, 51–58. [Google Scholar] [CrossRef]
- Ning, H.; Liu, H.; Yang, L.T. Cyberentity security in the internet of things. IEEE Comput. 2013, 46, 46–53. [Google Scholar] [CrossRef]
- Granjal, J.; Monterio, E.; Silva, J.S. Security for the internet of things: A survey of existing protocols and open research issues. IEEE Comm. Tutor. 2015, 17, 1294–1312. [Google Scholar] [CrossRef]
- Nurse, J.R.C.; Creese, S.; Roure, D.D. Security risk assessment in internet of things systems. IEEE IT Pro. 2017, 19, 20–26. [Google Scholar] [CrossRef]
- Lee, J.-H.; Kim, H. Security and privacy challenges in the internet of things. IEEE Consum. Electron. Mag. 2017, 6, 134–136. [Google Scholar] [CrossRef]
- Kim, H.; Lee, E.A. Authentication and authorization for the internet of things. IEEE IT Pro. 2017, 19, 27–33. [Google Scholar] [CrossRef]
- Yang, Y.; Wu, L.; Yin, G.; Li, L.; Zhao, H. A survey on security and privacy issues in internet-of-things. IEEE Internet Things J. 2017, 4, 1250–1258. [Google Scholar] [CrossRef]
- Lin, J.; Yu, W.; Zhang, N.; Yang, X.; Zhang, H.; Zhao, W. A survey on internet of things: Architecture, enabling technologies, security and privacy, and applications. IEEE Internet Things J. 2017, 4, 1125–1142. [Google Scholar] [CrossRef]
- Asano, T.; Maeda, Y.; Nakagawa, G.; Arima, Y. Physical random-number generator using Schottky MOSFET. Jpn. J. Appl. Phys. 2003, 52, 403–409. [Google Scholar]
- Zhou, S.-H.; Zhang, W.; Wu, N.-J. An ultra-low power CMOS random number generator. Solid State Electron. 2008, 52, 233–238. [Google Scholar] [CrossRef]
- Pareschi, F.; Setti, G.; Rovatti, R. Implementation and testing of high-speed CMOS true random number generators based on chaotic systems. IEEE Trans. Elec. Dev. 2010, 57, 3124–3137. [Google Scholar] [CrossRef]
- Kharraz, A.; Rbertson, W.; Kirda, E. Protecting against Ransomware. IEEE Secur. Priv. 2018, 16, 103–107. [Google Scholar] [CrossRef]
- The New York Times. Facebook Security Breach Exposes Accounts of 50 Million Users. Available online: https://www.nytimes.com/2018/09/28/technology/facebook-hack-data-breach.html (accessed on 28 September 2018).
- Padhy, R.P.; Patra, R.R.; Satapathy, S.C. Cloud computing security issues and research challenges. Int. J. Comput. Sci. Inf. Technol. Secur. 2011, 1, 136–146. [Google Scholar]
- Chistidis, K.; Devetsikiotis, M. Blockchains and smart contracts for the internet of things. IEEE Access 2016, 4, 2292–2303. [Google Scholar] [CrossRef]
- Sharma, P.K.; Singh, S.; Jeong, Y.-S.; Park, J.H. DistBlockNet: A distributed blockchains-based secure SDN architecture for IoT network. IEEE Commun. Mag. 2017, 55, 78–85. [Google Scholar] [CrossRef]
- Kshetri, N. Can blockchain strengthen the internet of things? IEEE IT Pro. 2017, 19, 68–72. [Google Scholar] [CrossRef]
- Miller, D. Blockchain and the internet of things in the industrial sector. IEEE Prof. 2018, 20, 15–18. [Google Scholar] [CrossRef]
- Novo, O. Blockchain meets IoT: An architecture for scalable access management in IoT. IEEE Internet Things J. 2018, 5, 1184–1195. [Google Scholar] [CrossRef]
- Dori, A.; Kanhere, S.S.; Jurdak, R. Towards an optimized blockchain for IoT. In Proceedings of the ACM 2017 IEEE/ACM Second International Conference on Internet-of-Things Design and Implementation (IoTDI), Pittsburgh, PA, USA, 18–21 April 2017. [Google Scholar] [CrossRef]
- Mandrita, B.; Lee, J.; Choo, K.-K.-R. A blockchain future for internet of things security: A position paper. Dig. Commun. Netw. 2018, 4, 149–160. [Google Scholar]
- Kouicem, D.E.; Bouabdallah, A.; Lakhlef, H. Internet of things security: A top-down survey. Comput. Netw. 2018, 141, 199–221. [Google Scholar] [CrossRef] [Green Version]
- Dorri, A.; Kanhere, S.; Jurdak, R.; Gauravaram, P. Blockchain for IoT Security and Privacy: The Case Study of a Smart Home. In Proceedings of the 2ND IEEE PERCOPM Workshop on Security Privacy and Trust in the Internet of Things 2017, Kona, HI, USA, 13–17 March 2017. [Google Scholar] [CrossRef]
- Petracek, N. Is Blockchain The Way to Save IoT? Forbes Community Voice, Forbes Technology Council, 18 July 2018. [Google Scholar]
- Bauer, H.; Burkacky, O.; Knochenhauer, C. Security in the Internet of Things; Semiconductor, McKinsey & Company: New York, NY, USA, 2017. [Google Scholar]
- Watanabe, H. Can Blockchain Protect Internet-of-Things? In Proceedings of the Future Technology Conference 2017 (FTC2017), Vancouver, Canada, 29–30 November 2017.
- Watanabe, H. Blockchain technology in SSD controller—Flash in IoT security. In Proceedings of the Flash Memory Summit 2017 (FMS2017), Santa Clara, CA, USA, 8–10 August 2017. [Google Scholar]
- Watanabe, H. Blockchain & IoT. In Proceedings of the Hack PWN, the China Internet Security Conference 2017 (ISC 2017), Beijing, China, 14 September 2017. [Google Scholar]
- Watanabe, H.; Hamamoto, T. The cheapest physical CPCID fully compatible to mass-product DRAM process. In Proceedings of the 2017 Asia-Pacific Workshop on fundamental and applications of advanced semiconductor devices (AWAD2017), Gyeongju, Korea, 3–5 July 2017. [Google Scholar]
- Nakamoto, S. Bitcoin: A Peer-To-Peer Electronic Cash System. Available online: https://bitcoin.org/bitcoin.pdf; https://nakamotoinstitute.org (accessed on 31 October 2008).
- Belinkyh, M.; Rennick, E.; Veitch, A. Santander. The Fintech 2.0 Paper: Rebooting financial services, InnoVentures. Available online: http://santanderinnoventures.com/fintech2/ (accessed on 6 March 2015).
- Merkle, R.C. A digital signature based on a conventional encryption function. In Proceedings of the Conference on the Theory and Applications of Cryptographic Techniques on Advances in Cryptology (CRYPTO ’87), Santa Barbara, CA, USA, 16–20 August 1987; pp. 369–378. [Google Scholar]
- Lee, J.W.; Lim, D.; Gassend, B.; Suh, G.E.; van Dijk, M.; Devadas, S. A technique to build a secret key in integrated circuits for identification and authentication applications. In Proceedings of the 2004 Symposium VLSI Circuits, Digest of Technical Papers, Honolulu, HI, USA, 15–19 June 2004; pp. 176–179. [Google Scholar]
- Suh, G.E.; Devadas, S. Physical unclonable functions for device authentication and secret key generation. In Proceedings of the Design Automation Conference (DAC 2007), San Diego, CA, USA, 4–8 June 2007. [Google Scholar]
- Yu, M.D.; Sowell, R.; Sing, A.; M’Raihi, D.; Devadas, S. Performance metrics and empirical results of a PUF cryptographic key generations ASIC. In Proceedings of the 2012 IEEE International Symposium on Hardware-Oriented Security and Trust, San Francisco, CA, USA, 3–4 June 2012. [Google Scholar]
- Tehranipoor, F.; Karimian, N.; Xiao, K.; Chandy, J. DRAM based intrinsic physical unclonable functions for system level security and authentication. IEEE T VLSI Syst. 2017, 25, 1085–1097. [Google Scholar] [CrossRef]
- Diffie, W.; Hellman, M.E. New directions in cryptography. IEEE Trans. Inf. Theory 1976, IT-22, 644654. [Google Scholar] [CrossRef]
- Accelerate towards autonomous driving. In Proceedings of the SK Hynix automotive symposium, Santa Clara, CA, USA, 7 August 2017.
- Yamamoto, M.; Ochiai, T.; Takenaka, M.; Sakiyama, K.; Ito, K.; Iwamoto, M.; Ota, K. Temperature Sensor, Encryptor, Encryption Method, and the Individual-Specific Information Generating Device. JP5857726B2, 20 December 2011. (In Japanese). [Google Scholar]
- Yamamoto, M.; Ochiai, T.; Takenaka, M.; Ito, K.; Sakiyama, K.; Iwamoto, M.; Ota, K. Temperature Sensor, Encryption Device, Encryption Method and Individual Information Generation Device. JP5870675B2, 20 December 2011. (In Japanese). [Google Scholar]
- Rivest, R.L.; Shamir, A.; Adelman, L.M. A Method for Obtaining Digital Signature and Public-Key Cryptsystems, MIT-LCS-TM-082; MIT Laboratory for Computer Science: Cambridge, MA, USA, 1977. [Google Scholar]
- Elgamal, T. A public-key cryptosystem and a signature scheme based on discrete logarithms. IEEE Trans. Inf. Theory 1985, IT-31, 469–472. [Google Scholar] [CrossRef]
- Kravitz, D.W.; Mills, O. Digital Signature Algorithm. U.S. Patent 5,231,668, 26 July 1991. [Google Scholar]
- Schnorr, C.P. Method for Identifying Subscribers and for Generating and Verifying Electronic Signatures in a Data Exchange System. U.S. Patent 4,995,082, 23 February 1990. [Google Scholar]
- Kleinjung, T.; Aoki, K.; Franke, J.; Lenstra1, A.K.; Thomé, E.; Bos, J.W.; Gaudry, P.; Kruppa, A.; Montgomery, P.L.; Osvik, D.A.; et al. Factrozation of a 768-bit RSA modulus version 1.3, 24 January 2010. In Proceedings of the Advances in cryptology—CRYPTO 2010, 30th Annual Cryptology Conference, Santa Barbara, CA, USA, 15–19 August 2010. [Google Scholar]
- Hayashi, T.; Shimoyama, T.; Shinohara, N.; Takagi, T. Breaking pairing-based cryptosystems using ηT pairing over GF (397). In Proceedings of the ASIACRYPT 2012, Beijing, China, 2–6 December 2012. [Google Scholar]



| Automotive | Industry | Consumer | |
|---|---|---|---|
| Longevity | >10 years | 5 to 10 years | 1 to 3 years |
| Temperature | −40 to 150 °C | −40 to 85 °C | 0 to 70 °C |
| Humidity | 0–100% | High | Low |
| Failure Rate (ppm) | As low as possible | <100 | <300 |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Watanabe, H.; Fan, H. A Novel Chip-Level Blockchain Security Solution for the Internet of Things Networks. Technologies 2019, 7, 28. https://doi.org/10.3390/technologies7010028
Watanabe H, Fan H. A Novel Chip-Level Blockchain Security Solution for the Internet of Things Networks. Technologies. 2019; 7(1):28. https://doi.org/10.3390/technologies7010028
Chicago/Turabian StyleWatanabe, Hiroshi, and Howie Fan. 2019. "A Novel Chip-Level Blockchain Security Solution for the Internet of Things Networks" Technologies 7, no. 1: 28. https://doi.org/10.3390/technologies7010028
APA StyleWatanabe, H., & Fan, H. (2019). A Novel Chip-Level Blockchain Security Solution for the Internet of Things Networks. Technologies, 7(1), 28. https://doi.org/10.3390/technologies7010028





