Group Authentication Scheme for Neighbourhood Area Networks (NANs) in Smart Grids
Abstract
:1. Introduction
2. Group Authentication
2.1. The Need for Group Authentication
- Localise the topology: the SMs are distributed geographically based on the location of the consumers. It is essential that these devices are within the radio range of each other to be able to communicate with each other. Therefore, it is necessary to form groups of SMs. Groups are typically formed with some nodes in each group having overlapping radio range with other group/s. Such overlap provides potential redundant paths, when necessary.
- Balance workload of intermediate relay hosts: SMs communicate to an upstream data sink in the smart grid via an intermediate host, typically a SM performing the role of a group gateway. It is necessary to limit the processing and storage load on the intermediate host that does the forwarding of data to and from the SMs. Typically, the SMs are organised into groups and assigned gateways to communicate with.
- Distribute the SMs into functional groups: from an electricity provider’s perspective, it helps to organise different categories of users into different groups (domestic, commercial, industrial, essential service provider, etc.) for purposes of estimating demand, geographically, validating the usage, and controlling theft. Often, domestic and non-domestic users are located geographically close and the need for creating groups of SMs for operational semantics is necessary.
2.2. Related Work
2.3. Security Requirements
- All the devices being able to authenticate in one go (single message) rather than one-to-one with the authentication server and each device with a unique verified identity, (Centralised Authentication) and
- All devices being able to authenticate between themselves in the absence of an upstream authentication server (Distributed Autonomous Authentication)
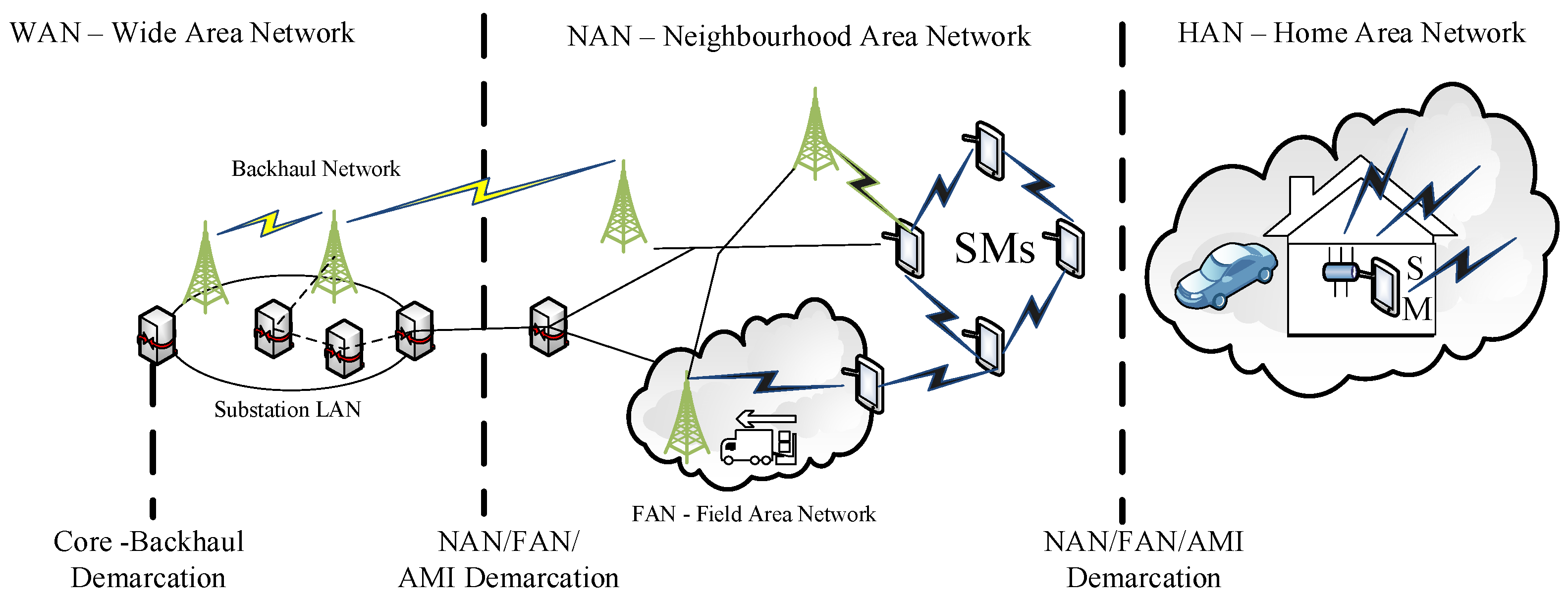
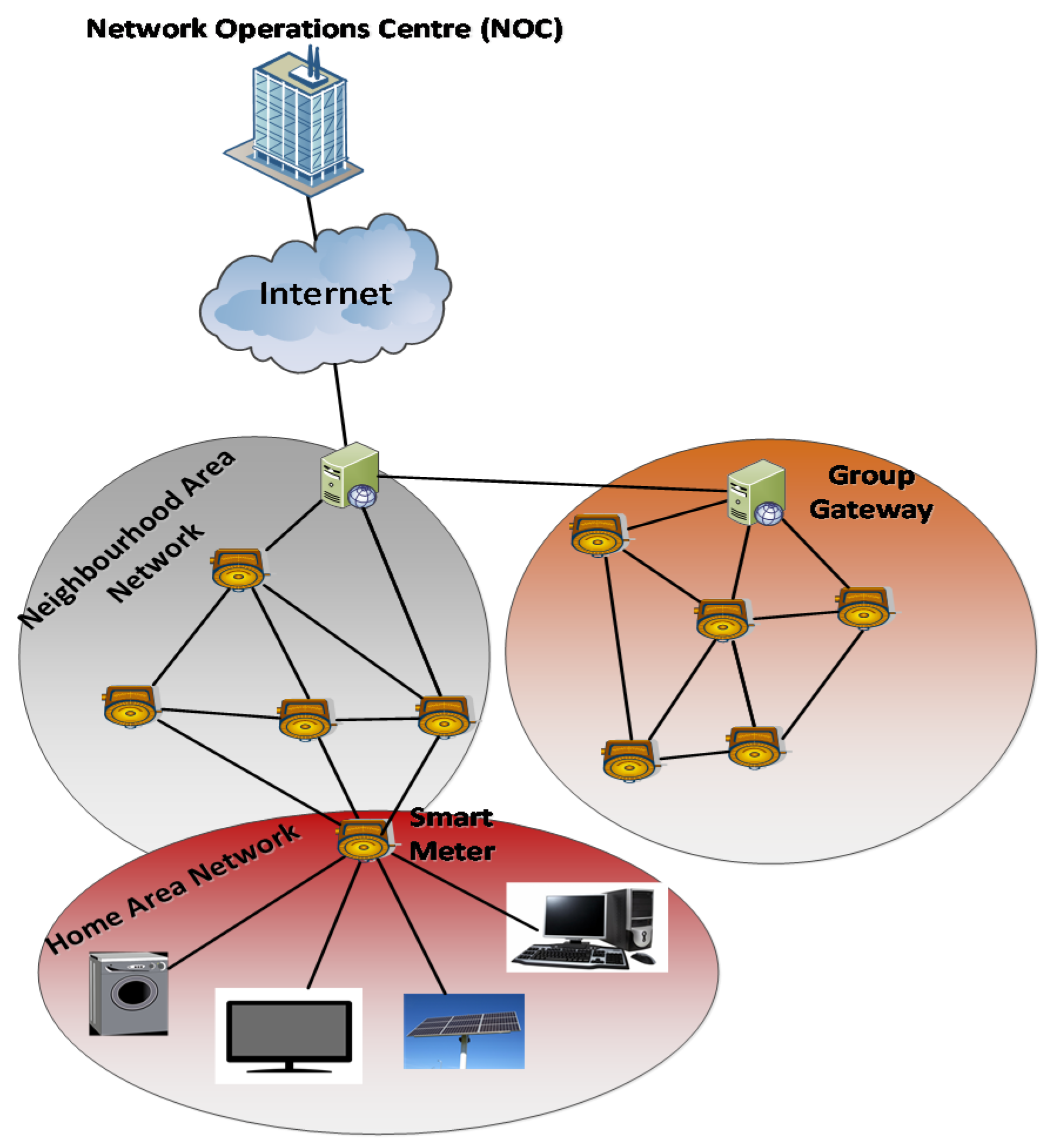
3. The Smart Grid Network Model
- Home Area Network (HAN): one smart meter (SM) and N smart devices (SDs). This group of devices is interconnected in a star topology with a SM as the star point.
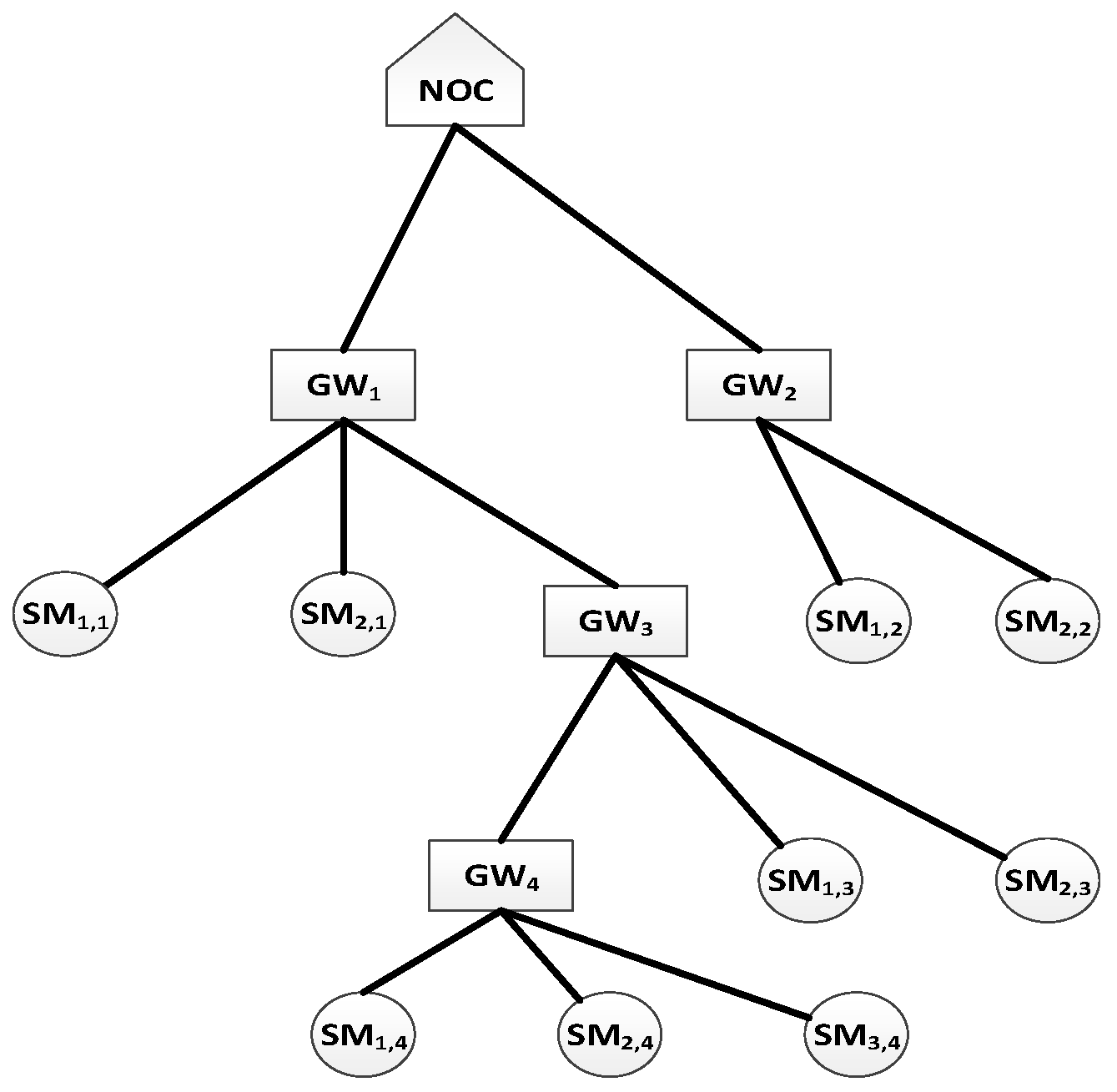
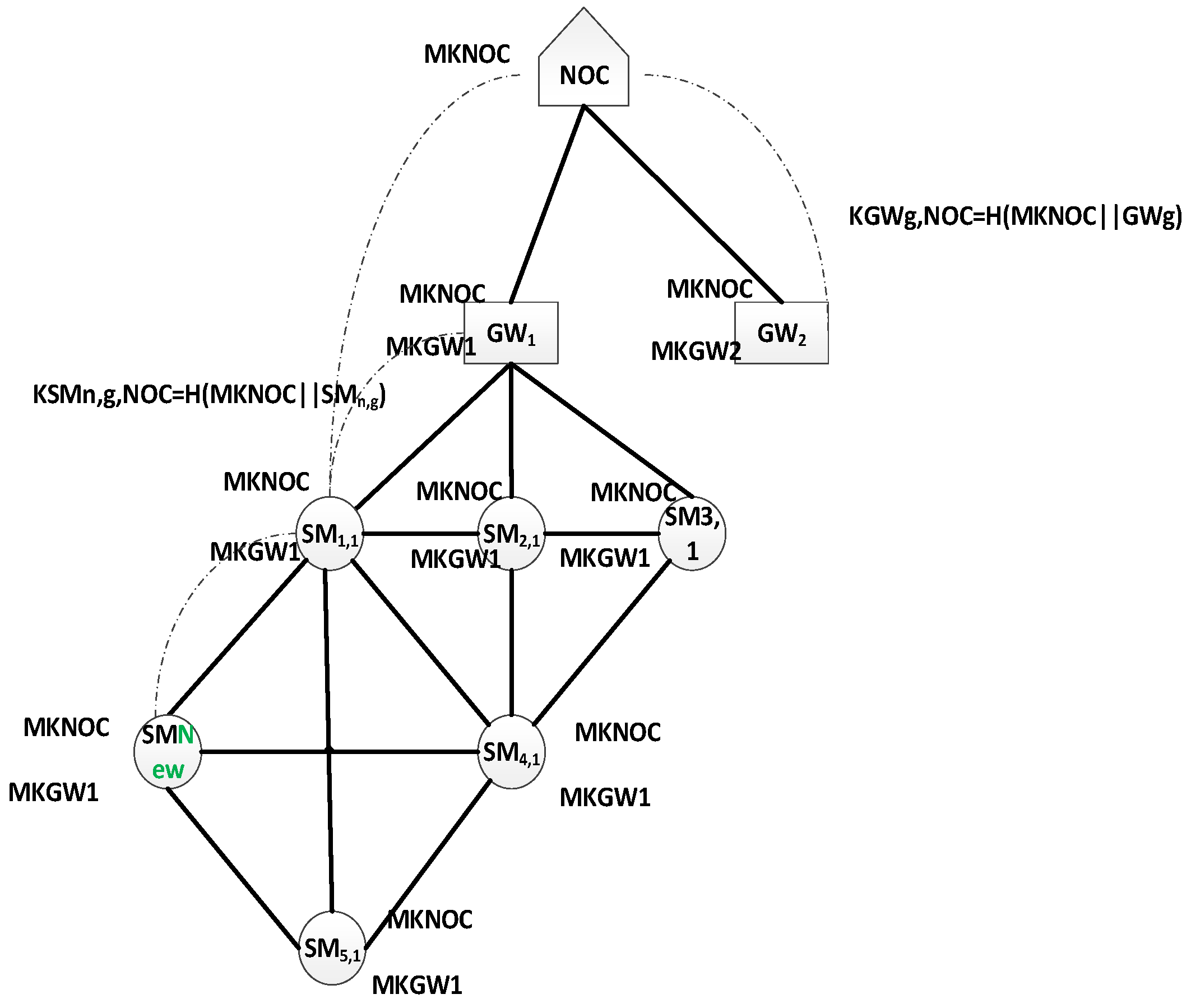
- Neighbourhood Area Network (NAN): mesh network (not necessary full mesh) of M SMs. SMs are divided into G groups. Group g (g = 1,..., G) has Mg SMs. Hence the following equation is considered:One SM of each group is selected as Group Controller (GC). The GC is hereafter termed as the gateway node, GW.
- Wide Area Network (WAN): Network (e.g., Internet) that connects GCs to the Network Operations Centre (NOC).
3.1. Threat Model and Assumptions
- Smart meters are grouped together based on a policy and are aware of the group members. The events and functionalities of the policy are not in the scope of this paper. This work does not address the policy on which smart meter groups are constituted.
- Every smart meter in a group has a unique identity, which is a serial number and each group has a unique group identity, which are used in the authentication process. All network devices involved in the group authentication process know these details.
- The link layer between the smart meters and gateway are protected at the link layer, which makes communication encrypted at the link layer.
- Every smart meter in a group maintains a wireless connection with its gateway and the network topology between the home smart meter and the gateway node is a tree. The topology between the gateway and the utility could be a mesh. They form a cluster-tree topology between the SM and the gateway.
- The smart meters have pre-distributed shared symmetric keys, which are used for initiating the authentication process and keys during authentication.
- Symmetric cryptography yields a better cryptographic strength for a given key length compared to asymmetric cryptography. The resulting data length is close to the size of the input.
- Smart meters cooperate with one another to forward packets on multi-hop paths to the NOC. A routing protocol to handle the mesh topology is active and provides the shortest route from a given end device to the GW, within the group.
- GW nodes have sufficient power (more than the end devices) to be able to perform the forwarding from the group to the NOC and vice versa.
- In the event of the failure of a gateway node, all nodes in the group will be unable to access the NOC, until the GW is reinstated/active. There is no fall-back node that will take on the role of a gateway. The failure rates of the GW are low.
- The groups and the group gateways are pre-identified and formed. These formations are not ad hoc and, therefore, there is no need for a node to play the role of a gateway.
- The nodes on the network are not time synchronized.
- The value of the clock ticks of a node cannot be retrieved to set the same clock value on another node. Such an operation is possible only with a reset of the node, which essentially implies that the clock tick value is lost since the clock is reset. It can be argued that such is the exact function of a time protocol such as Network Time Protocol (NTP), but sufficient care is taken to ensure that this value is not accessed by any network function.
- The NOC provides a central authentication service. It comprises a sufficiently large server with a fail-over configuration and able to maintain the state of all of the devices on the network. Given the nature of the service requirement of the smart meters in the smart grid, all authentication attempts, except the one at start-up upon installation, must be approved before the NOC sends an authentication response to the node requesting authentication.
- The NOC maintains a history of the metadata (originator-ID, timestamp, group-ID) over a sufficiently long period to derive statistics, such as message arrival epochs, message arrival times, inter-message times, message size, and activity profiles so that it knows when it can expect the next packet from a specific ID. Such a history is essential to detect malicious attack traffic since our scheme does not require the devices on the network to be time synchronized.
3.2. Notations
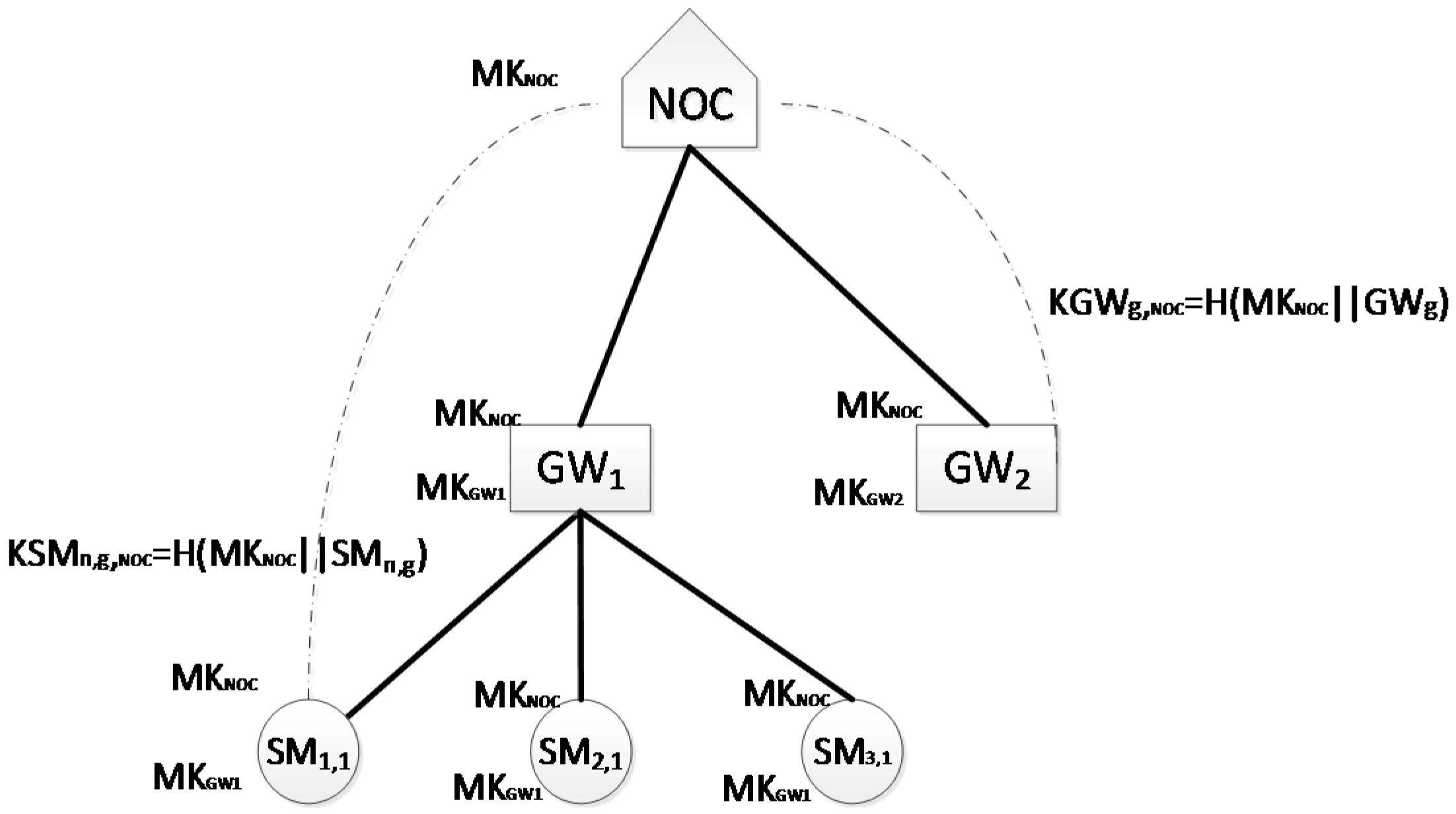
3.3. Authentication of Group Gateway
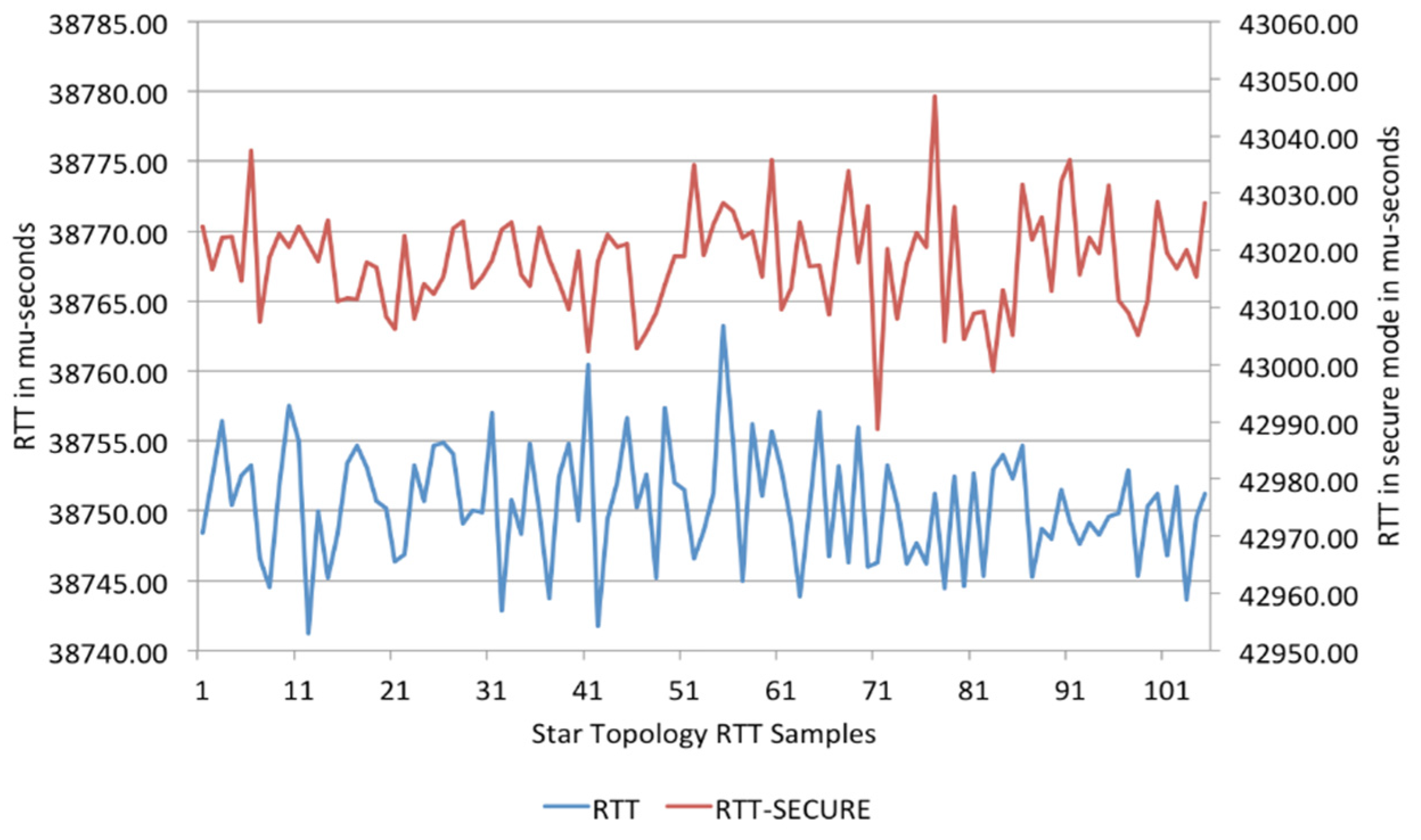
3.4. Case 1—Star-Star Topology
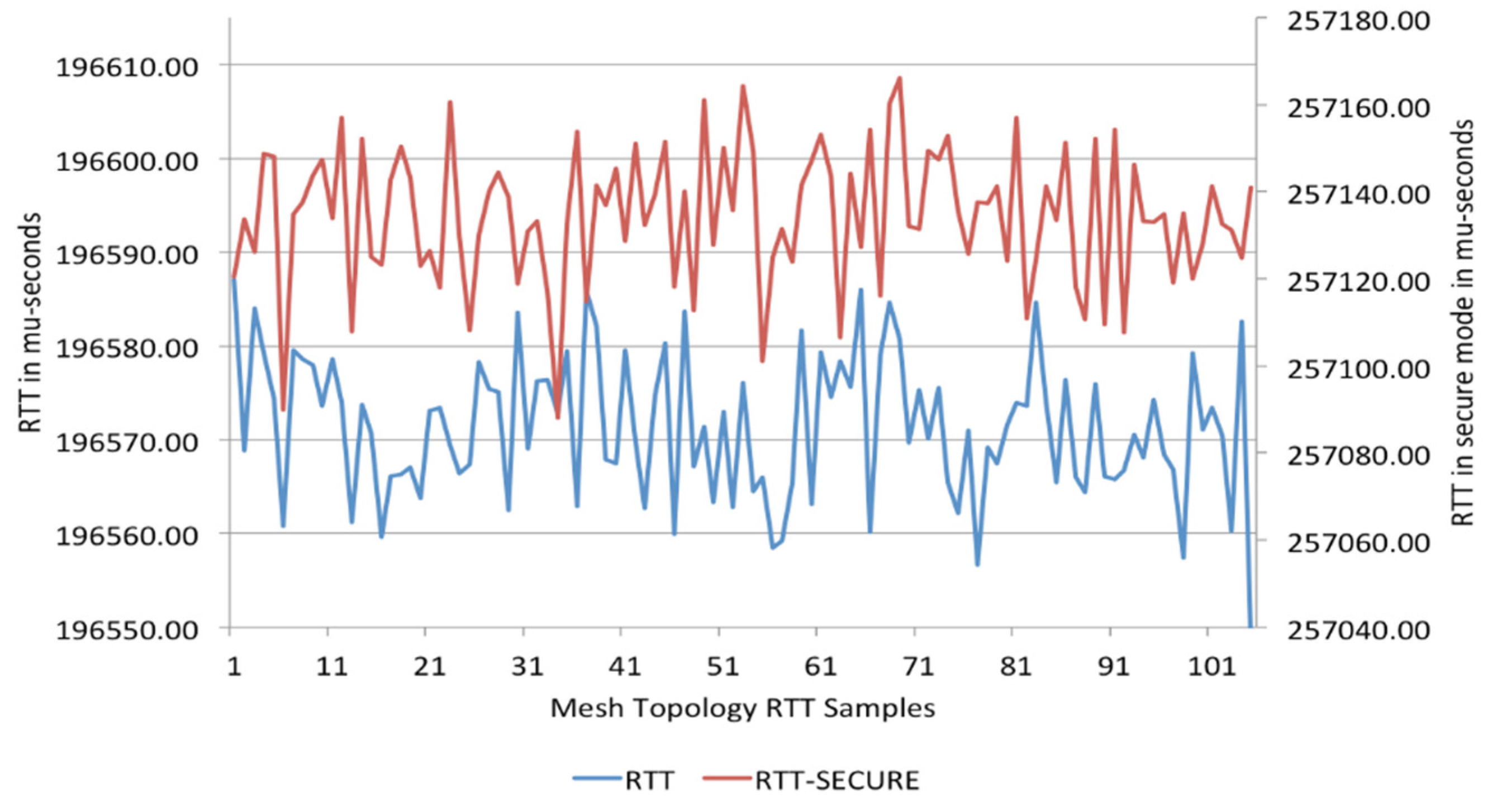
3.5. Case Two—Multi-Hop (Mesh)
3.5.1. Network Discovery and Registration
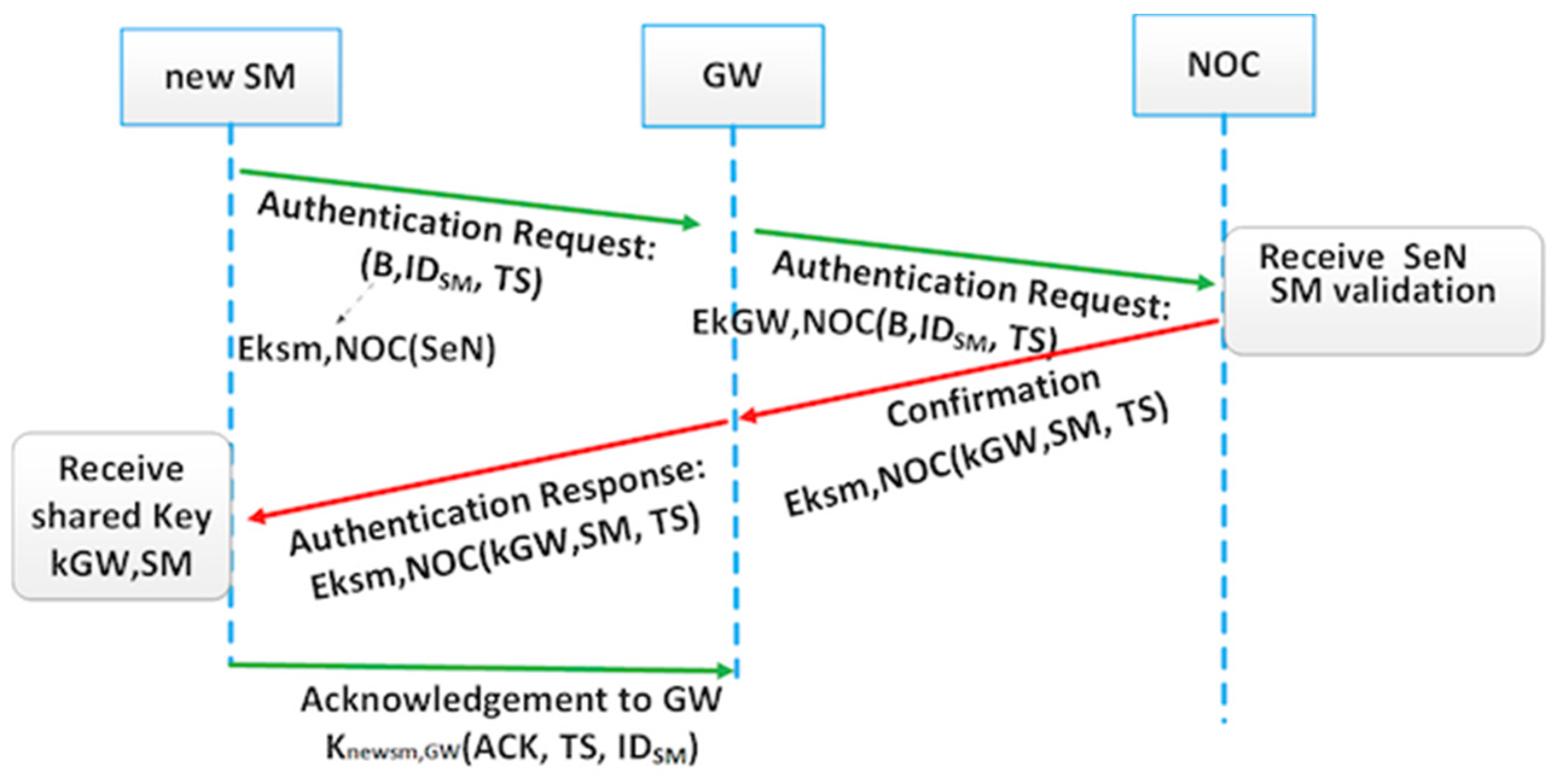
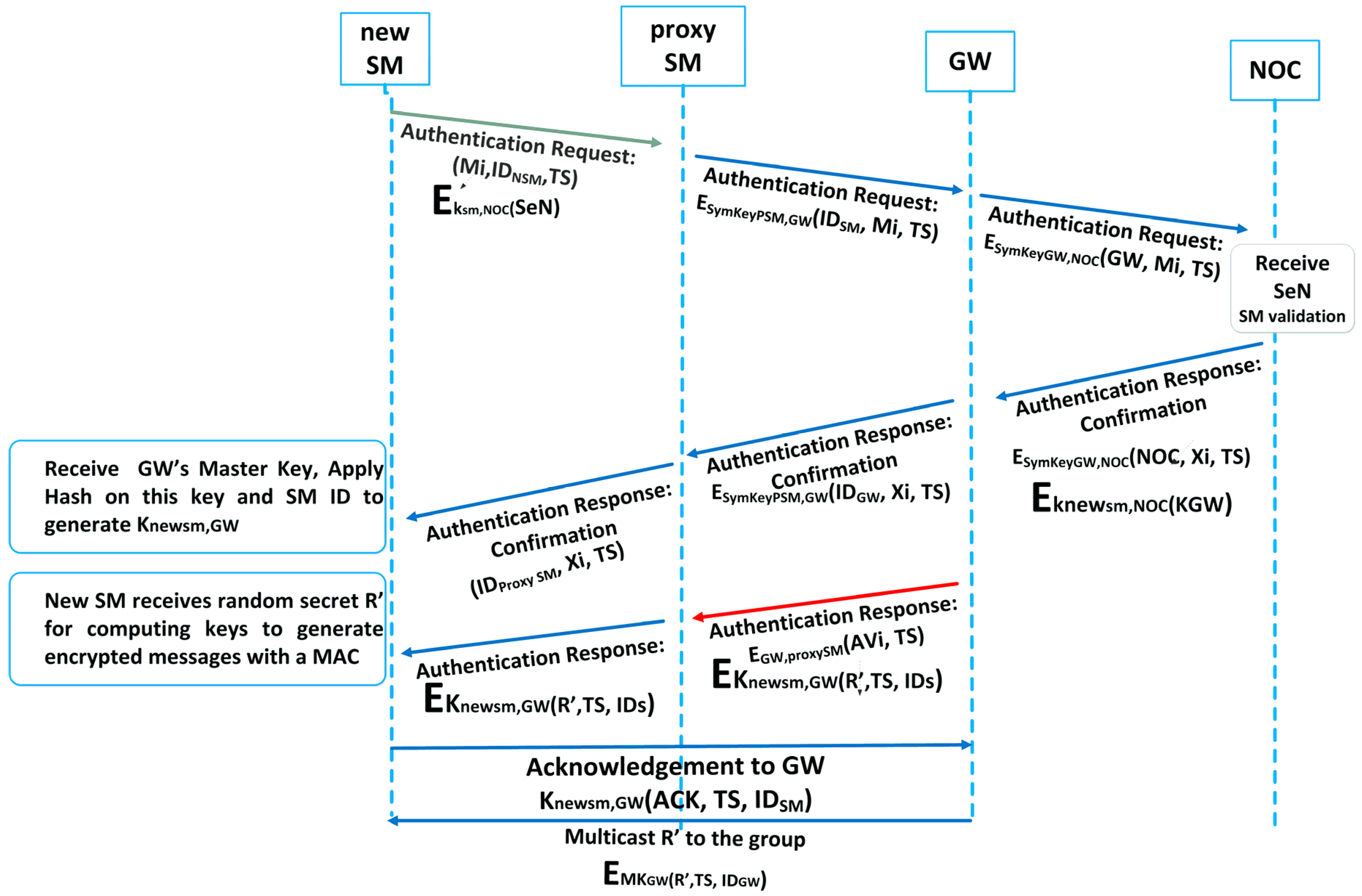
3.5.2. Authentication of the Smart Meters,
- Mi, the serial number of and SNNSM, encrypted using ,
- Identity number of new , ID,
- Timestamp TS.
- SM sends an authentication request.
- NOC validates data and sends an authentication response.
- Authentication response contains .
- GW sends R to the new SM.
- New SM sends an ACK to GW.
- GW multicasts R to the group.
- SM decides the neighbour to forward to, for a packet destined to the NOC.
- SM generates its encryption key , ’ (||) where ’ is the one-way-hash function.
- SM generates a MAC for the message using .
- The neighbour receives the message with MAC and validates it. Knowing what node id it came from, it generates the forwarding key of the source.
- If successful, it generates a MAC and forwards it to a neighbour (to the GW, if it is the neighbour). If the MAC fails, the packet is simply dropped.
3.5.3. Updating of
- A smart meter node must send a network leaving request to the assigned dedicated node of that group. (, TS, ID).
- The will inform the other nodes in its group (multicast) and (unicast) about the leave using the messages (, TS, ID GW) and (, TS, ID GW).
- Removing the node with
- regenerates a new master gateway key and sends it to the specific gateway.
- Additional processing overhead. Assume that the generation of a key requires × CPU cycles. The processing overhead, Oproc noc = 1 × (because NOC has to generate one key for .
- Communication overhead that includes two multicast and two unicast messages. The unicast messages are between the gateway and the NOC and the multicast messages are within the group.
4. Security Analysis
4.1. Node Capture Attack
4.2. Replay Attack
4.3. Sybil Attack
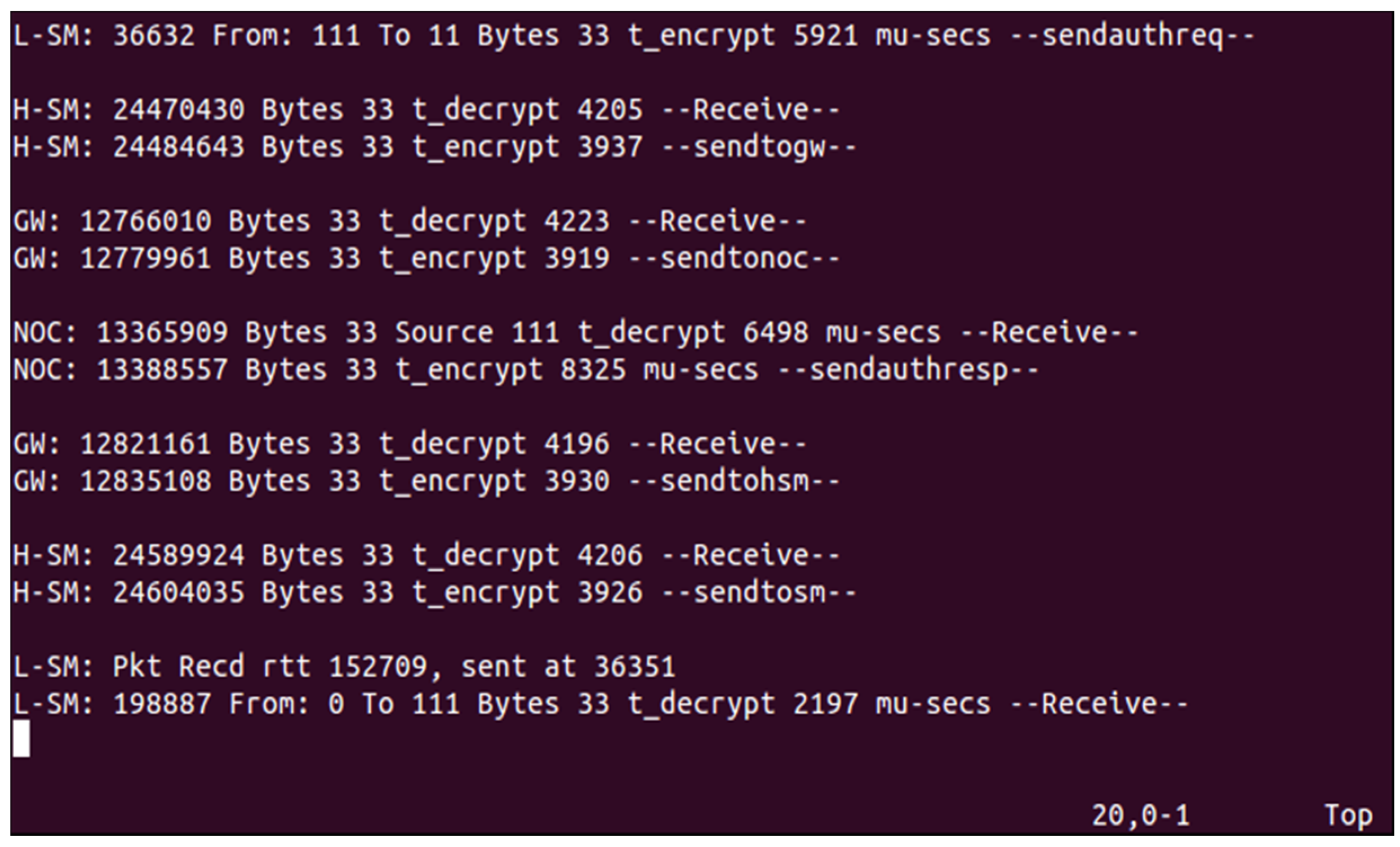
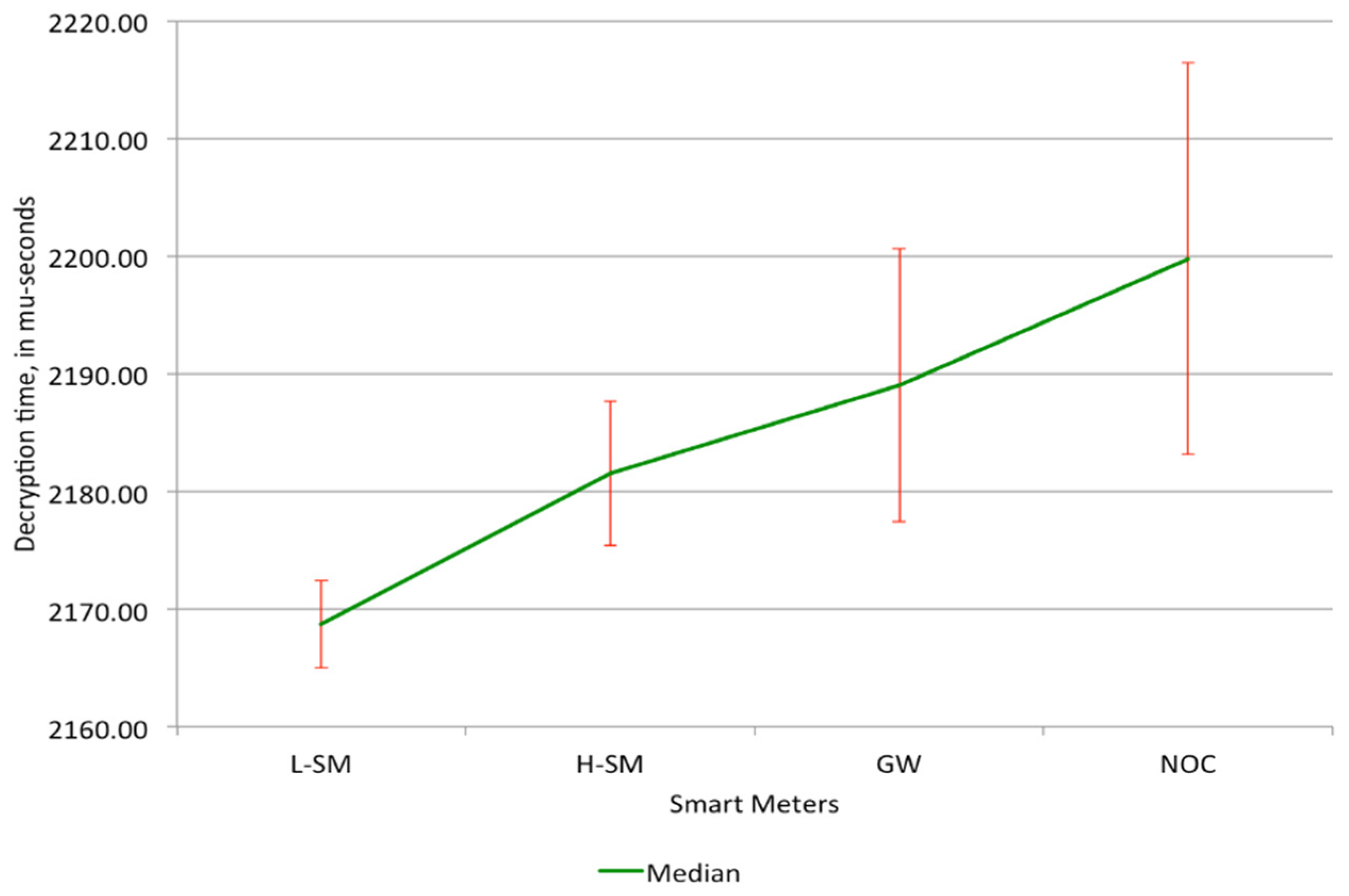
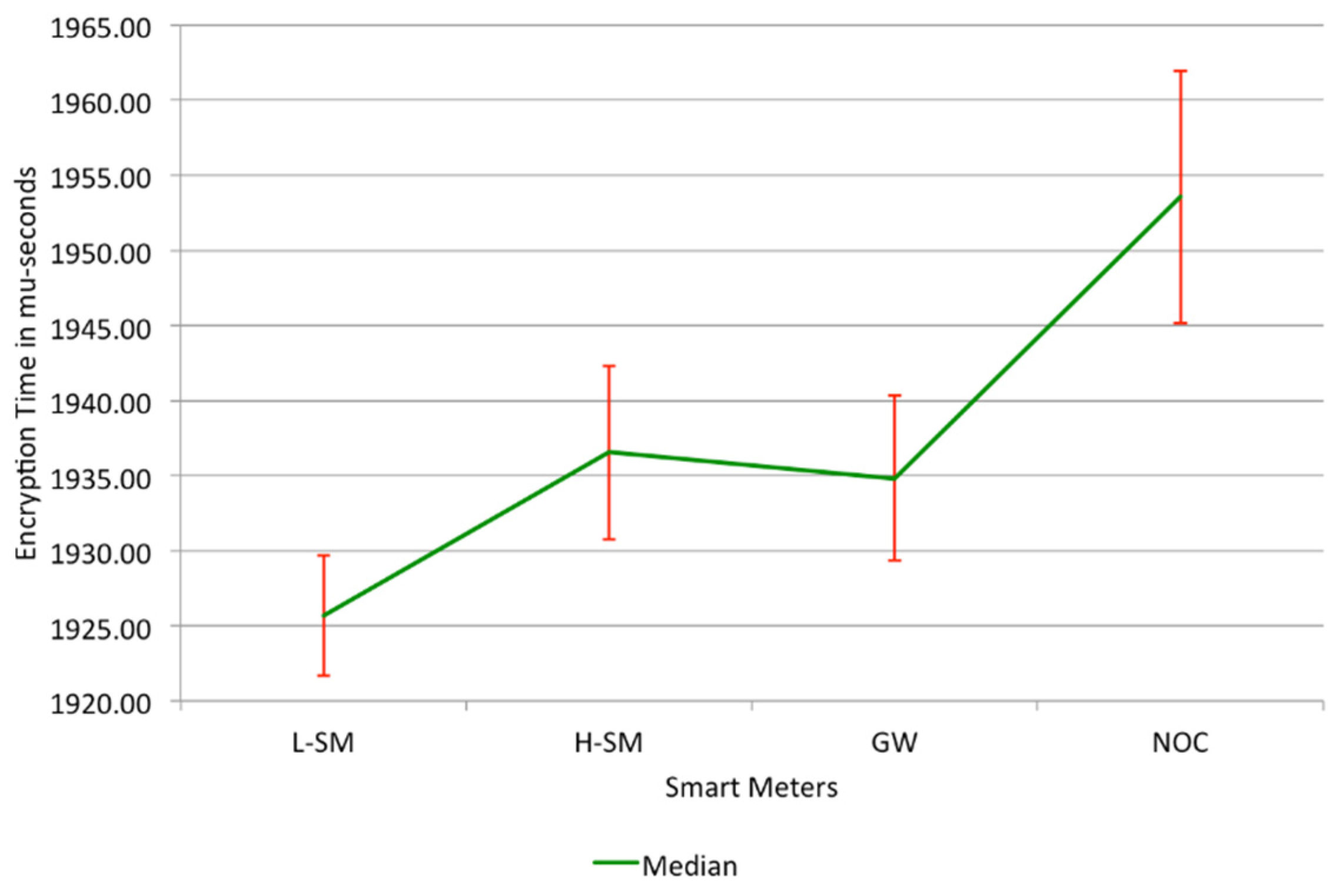
5. Implementation
6. Conclusions
Author Contributions
Conflicts of Interest
References
- Fang, X.; Misra, S.; Xue, G.; Yang, D. Smart grid; the new and improved power grid: A survey. IEEE Commun. Surv. Tutor. 2012, 14, 944–980. [Google Scholar] [CrossRef]
- Wang, W.; Lu, Z. Cyber security in the smart grid: Survey and challenges. Comput. Netw. 2013, 57, 1344–1371. [Google Scholar] [CrossRef]
- Dollen, D.V. Report to Nist on the Smart Grid Interoperability Standards Roadmap. Available online: http://www.nist.gov/smartgrid/upload/InterimSmartGridRoadmapNISTRestructure.pdf (accessed on 9 December 2015).
- Technology, N.I.O.S.A. Announcing the Advanced Encryption Standard (Aes); Federal Information Processing Standards Publications (FIPS PUBS), National Technical Information Service (NTIS): Springfield, VA, USA, 2001. [Google Scholar]
- Technology, N.I.O.S.A. Data Encryption Standard; Federal Information Processing Standards Publications (FIPS PUBS), National Institute of Standards and Technology: Gaithersburg, MD, USA, 1999. [Google Scholar]
- Yan, Y.; Qian, Y.; Sharif, H.; Tipper, D. A survey on cyber security for smart grid communications. IEEE Commun. Surv. Tutor. 2012, 14, 998–1010. [Google Scholar] [CrossRef]
- Meng, W.; Ma, R.; Chen, H.-H. Smart grid neighborhood area networks: A survey. IEEE Netw. 2014, 28, 24–32. [Google Scholar] [CrossRef]
- Zhong, F.; Kulkarni, P.; Gormus, S.; Efthymiou, C.; Kalogridis, G.; Sooriyabandara, M.; Ziming, Z.; Lambotharan, S.; Woon, C. Smart grid communications: Overview of research challenges, solutions, and standardization activities. IEEE Commun. Surv. Tutor. 2013, 15, 21–38. [Google Scholar]
- Broustis, I.; Sundaram, G.S.; Viswanathan, H. Group authentication: A new paradigm for emerging applications. Bell Labs Tech. J. 2012, 17, 157–173. [Google Scholar] [CrossRef]
- Harn, L. Group authentication. IEEE Trans. Comput. 2013, 62, 1893–1898. [Google Scholar] [CrossRef]
- Shamir, A. How to share a secret. Commun. ACM 1979, 22, 612–613. [Google Scholar] [CrossRef]
- Mahalle, P.N.; Prasad, N.R.; Prasad, R. Threshold cryptography-based group authentication (TCGA) scheme for the internet of things (IoT). In Proceedings of the 4th International Conference on Wireless Communications, Vehicular Technology, Information Theory and Aerospace & Electronic Systems (VITAE), Aalborg, Denmark, 11–14 May 2014; pp. 1–5.
- Ghanbarimaman, R.; Pour, A.N. A new definition of group authentication increasing performance of server calculation. In Proceedings of the 2012 International Conference on Information Science and Applications (ICISA), Suwon, Korea, 23–25 May 2012; pp. 1–6.
- Yang, H.; Jiao, L.; Oleshchuk, V.A. A general framework for group authentication and key exchange protocols. In Foundations and Practice of Security; Springer: Gewerbestrasse, Switzerland, 2014; pp. 31–45. [Google Scholar]
- Wang, F.; Chang, C.-C.; Chou, Y.-C. Group authentication and group key distribution for ad hoc networks. Int. J. Netw. Secur. 2015, 17, 199–207. [Google Scholar]
- Choi, D.; Jeong, H.; Won, D.; Kim, S. Hybrid Key Management Architecture for Robust SCADA Systems. J. Inf. Sci. Eng. 2011, 2011, 197–211. [Google Scholar]
- Nicanfar, H.; Jokar, P.; Leung, V.C.M. Smart grid authentication and key management for unicast and multicast communications. In Proceedings of the Innovative Smart Grid Technologies Asia (ISGT), Perth, Australia, 13–16 November 2011; pp. 1–8.
- Aboba, B.; Simon, D.; Eronen, P. Extensible authentication protocol (EAP) key management framework. Network Working Group, Request For Comments 5247, August 2008. Available online: https://tools.ietf.org/html/rfc5247 (accessed on 9 December 2015).
- Das, S.; Ohba, Y.; Kanda, M.; Famolari, D.; Das, S.K. A key management framework for ami networks in smart grid. IEEE Commun. Mag. 2012, 50, 30–37. [Google Scholar] [CrossRef]
- Alohali, B.; Merabti, M.; Kifayat, K. A cloud of things (COT) based security for home area network (HAN) in the smart grid. In Proceedings of the Eighth International Conference on Next Generation Mobile Apps, Services and Technologies (NGMAST), Oxford, UK, 10–12 September 2014; pp. 326–330.
- Abdullah, M.D.H.; Hanapi, Z.M.; Zukarnain, Z.A.; Mohamed, M.A. Attacks, vulnerabilities and security requirements in smart metering networks. TIIS 2015, 9, 1493–1515. [Google Scholar]
- Efthymiou, C.; Kalogridis, G. Smart grid privacy via anonymization of smart metering data. In Proceedings of the First IEEE International Conference on Smart Grid Communications (SmartGridComm), Gaithersburg, MD, USA, 13 August 2010; pp. 238–243.
- Lu, R.; Liang, X.; Li, X.; Lin, X.; Shen, X.S. Eppa: An efficient and privacy-preserving aggregation scheme for secure smart grid communications. IEEE Trans. Parall. Distrib. Syst. 2012, 23, 1621–1631. [Google Scholar]
- Li, F.; Luo, B.; Liu, P. Secure information aggregation for smart grids using homomorphic encryption. In Proceedings of the First IEEE International Conference on Smart Grid Communications (SmartGridComm), Gaithersburg, MD, USA, 13 August 2010; pp. 327–332.
- Kim, S.; Kwon, E.Y.; Kim, M.; Cheon, J.H.; Ju, S.-H.; Lim, Y.-H.; Choi, M.-S. A secure smart-metering protocol over power-line communication. IEEE Trans. Power Deliv. 2011, 26, 2370–2379. [Google Scholar] [CrossRef]
- Ayday, E.; Rajagopal, S. Secure, intuitive and low-cost device authentication for smart grid networks. In Proceedings of the Consumer Communications and Networking Conference (CCNC), Las Vegas, NV, USA, 9–12 January 2011; pp. 1161–1165.
- Choi, J.; Shin, I.; Seo, J.; Lee, C. An efficient message authentication for non-repudiation of the smart metering service. In Proceedings of the First ACIS/JNU International Conference on Computers, Networks, Systems and Industrial Engineering (CNSI), Jeju Island, Korea, 23–25 May 2011; pp. 331–333.
- Merabti, M.; Alohali, B.; Kifayat, K. A new key management scheme based on smart grid requirements. In Proceedings of the 9th International Conference on Computer Engineering and Applications (CEA’15), Dubai, UAE, 22–24 February 2015; pp. 436–443.
- Levis, P.; Madden, S.; Polastre, J.; Szewczyk, R.; Whitehouse, K.; Woo, A.; Gay, D.; Hill, J.; Welsh, M.; Brewer, E. Tinyos: An operating system for sensor networks. In Ambient Intelligence; Springer: Heidelberg, Germany, 2005; pp. 115–148. [Google Scholar]
- Riverbed. 2014. Riverbed Modeler Version 17.5, pl6, Riverbed Software. Available online: http://www.riverbed.com/ (accessed on 9 December 2015).
| Features | Security Schemes | ||||||
|---|---|---|---|---|---|---|---|
| Broustis et al. [9] | Harn [10] | Wang et al. [15] | Yang et al. [14] | Nicanfar et al. [17] | Subir et al. [19] | Our Goal | |
| Topology S/M/CT | M | N/A | N/A | S | M | N/A | S, M, CT |
| Multi-hop paths | Yes | Yes | Yes | No | Yes | N/A | Required |
| Validated Forwarding at intermediate nodes | Yes | Yes | Yes | No | Yes | No | Required |
| Symmetric Crypto | Yes | No | No | No | No | EAS | Required |
| Resilient to NC attack | No | No | No | Yes | No | Yes | Required |
| Resilient to replay attack | No | Yes | Yes | Yes | Yes | Yes | Required |
| Resilient to Sybil attack | Yes | Yes | Yes | Yes | Yes | Yes | Required |
| Centralized Authentication | No | No | No | No | Yes | Yes | Required |
| Specifically designed for NAN | No | No | No | No | Yes | Yes | Required |
| Nodes are not time synchronized | No | Yes | Yes | No | Yes | No | Required |
| Scalability | N/A | N/A | N/A | N/A | N/A | N/A | Required |
| Symbol | Description |
|---|---|
| Unique group number | |
| Smart meter ID | |
| A gateway for a group of smart meters to the NOC | |
| Master Key for NOC | |
| Master key for the group Gateway | |
| Symmetric key generated by = F(||), and shared with , and . | |
| Symmetric key generated by , and shared with , and . | |
| Existing smart meter for authenticating a new smart meter | |
| Symmetric key shared between , and | |
| Symmetric key shared with and | |
| Authentication value inside the group where | |
| R | Random number generated by to produce |
© 2016 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alohali, B.; Kifayat, K.; Shi, Q.; Hurst, W. Group Authentication Scheme for Neighbourhood Area Networks (NANs) in Smart Grids. J. Sens. Actuator Netw. 2016, 5, 9. https://doi.org/10.3390/jsan5020009
Alohali B, Kifayat K, Shi Q, Hurst W. Group Authentication Scheme for Neighbourhood Area Networks (NANs) in Smart Grids. Journal of Sensor and Actuator Networks. 2016; 5(2):9. https://doi.org/10.3390/jsan5020009
Chicago/Turabian StyleAlohali, Bashar, Kashif Kifayat, Qi Shi, and William Hurst. 2016. "Group Authentication Scheme for Neighbourhood Area Networks (NANs) in Smart Grids" Journal of Sensor and Actuator Networks 5, no. 2: 9. https://doi.org/10.3390/jsan5020009
APA StyleAlohali, B., Kifayat, K., Shi, Q., & Hurst, W. (2016). Group Authentication Scheme for Neighbourhood Area Networks (NANs) in Smart Grids. Journal of Sensor and Actuator Networks, 5(2), 9. https://doi.org/10.3390/jsan5020009






