Abstract
Recently, Internet of Drones (IoD) applications have grown in various fields, including the military, healthcare, smart agriculture, and traffic monitoring. Drones are equipped with computation resources, communication units, and embedded systems that allow them to sense, collect, and deliver data in real-time through public communication channels. However, this fact introduces the risk of attack on data transmitted over unsecured public channels. Addressing several security threats is crucial to ensuring the secure operation of IoD networks. Robust authentication protocols play a vital role in establishing secure processes in the IoD environment. However, designing efficient and lightweight authentication solutions is a complex task due to the unique characteristics of the IoD and the limitations of drones in terms of their communication and computational capabilities. There is a need to review the role of authentication processes in controlling security threats in the IoD due to the increasing complexity and frequency of security breaches. This review will present the primary issues and future path directions for authentication schemes in the IoD and provide a framework for relevant existing schemes to facilitate future research into the IoD. Consequently, in this paper, we review the literature to highlight the research conducted in this area of the IoD. This study reviews several existing methods for authenticating entities in the IoD environment. Moreover, this study discusses security requirements and highlights several challenges encountered with the authentication schemes used in the IoD. The findings of this paper suggest future directions for research to consider in order for this domain to continue to evolve.
1. Introduction
The concept of the Internet of Drones has attracted a great deal of interest in the connectivity of drones, which are often referred to as unmanned aerial vehicles. To enable its remote interaction and its ability to automate data collection, analysis, and transmission through the IoD, a drone consists of computing power, sensors, a communication module, actuators, and power supplies. Each drone has a specific flight area in which it flies and sends data [1]. In the forthcoming era of the Internet of Drones (IoD), drones will play a vital role as flying smart “things” and will work in conjunction with various enabling technologies. These technologies include the Internet of Things (IoT) [2], mobile edge computing (MEC) [3], machine learning (ML) [4], blockchain [5], and software-defined networking (SDN) [6]. The IoD has recently gained widespread attention due to the services it provides and its various applications, which greatly facilitate work and support a wide range of fields that enhance our way of life from health and military to commercial fields, such as the delivery of medical shipments, search and rescue, and smart agriculture [1,2]. However, numerous challenges must be addressed to establish and evolve the IoD. These challenges include the wide distribution of high mobility features and the presence of weak, unencrypted, and unsecured wireless communication channels. Additionally, drones are susceptible to a variety of attacks because to their limited energy, computation, and storage capabilities [7]. These attacks include eavesdropping, man-in-the-middle attacks, spoofing, tampering, denial-of-service (DoS) attacks, impersonation attacks, and replay attacks, with the aim of obtaining the sensitive data stored in drones or exploiting unauthorized connections. Given the potential economic, societal, and environmental consequences, it is crucial to mitigate privacy and security risks and protect the IoD against intruders. There is a conflict between security and efficiency when designing authentication methods for the Internet of Things. In light of these findings, the aim of this review paper is to provide insight into a variety of modern, cutting-edge authentication methods that maintain the trade-off between functionality and security for the IoD.
1.1. Related Previous Works
Several review articles have investigated the interact between entities in the IoD environment and its impact on security and performance. A survey was conducted that aimed at comparing various relevant reviews and surveys, highlighting the strengths, weaknesses, and focus of existing methods for authenticating entities within an IoD environment. By analyzing these research papers, the survey aimed to identify the limitations and advantages of different authentication techniques. The survey’s results help to enhance our understanding of the authentication landscape in IoD environments, supporting the development of more robust and effective authentication mechanisms. A classification of security challenges in 5G-enabled, UAV-aided networks was presented in [8]. The paper also proposed a blockchain-based security measure to address concerns related to privacy, security, and communication. However, it is important to note that this survey paper may be outdated, as it did not incorporate recent research.
Furthermore, the survey did not study hardware security techniques used specifically for the authentication of drones. A comprehensive review was conducted in [8]. to explore drone’s current security vulnerabilities and the security problems encountered in different sectors. The study provided a thorough examination of the potential risks and weaknesses that can compromise drone systems. Additionally, a realistic scenario depicting the life cycle of an attack was presented, highlighting the various stages and potential threats involved. To address these security concerns, the review also proposed countermeasures aimed at safeguarding drone systems and mitigating the identified risks. The results of that study led to valuable insights and recommendations for enhancing the security posture of drones in diverse sectors. Furthermore, Ref. [9] Examined the incorporation of UAVs into cellular networks and provided a thorough analysis of the core technologies and challenges involved. The study specifically focused on topics such as UAV kinds, the utilization of UAVs as flying relays, interference mitigation strategies, and activities related to standardization, regulation, and experimentation.
Furthermore, it included an overview of cybersecurity issues and highlighted potential use cases. Nevertheless, it is crucial to remember that the primary research objective of [9], did not center around the security of the IoD. As a result, its investigation of authentication techniques within the IoD context was incomplete and inadequate, and the review lacked up-to-date research findings. Another study [10] addressed the security challenges arising in higher communication layers within the context of UAV-based delivery systems and real-time multimedia streaming. The study highlighted the specific security concerns that emerge in these domains and provided insights into their implications. Furthermore, the paper introduced artificial neural network schemes as potential solutions to reduce the identified threats. These ANN-based approaches were proposed as mechanisms to enhance security measures and protect the communication systems involved in UAV-based delivery and real-time multimedia streaming.
Publication [11], highlighted the advantages and disadvantages of security remedies to protect critical UAV-based applications from potential threats and attacks, such as military and disaster scenarios. The role of blockchain, ML, and watermarking techniques was highlighted in addressing these security concerns. Additionally, A thorough literature review of the current UAV security protocols was conducted, and the potential vulnerabilities associated with these protocols that could be exploited by attackers were examined. The study aimed to comprehensively analyze the security measures and protocols that have been developed for UAVs. By reviewing the literature, the publication identified the strengths and weaknesses of these protocols, thereby shedding light on the potential vulnerabilities that attackers could exploit. This thorough examination of security protocols and their vulnerabilities contributes to a better understanding of the security landscape in UAV systems.
Furthermore, ref. [12] reviewed drone-based communications application scenarios in detail, noted security issues, and talked about cutting-edge security solutions including edge computing, blockchain, and machine learning. However, it’s crucial to remember that the hardware security issues concerning the Internet of Drones were not addressed in the studies [8,10,11,12]. The investigation of hardware security concerns within the IoD context was not a focal point of these papers. The IoD’s hardware security features require more investigation and analysis. Beyond the Internet of Drones, it is crucial to ensure the protection of the hardware components of IoT devices, alongside their software, against attacks based on hardware Trojans (HTs).
In [13], the necessity of safeguarding IoT device hardware from potential HT-based attacks was highlighted. Additionally, a taxonomy of HTs was provided, categorizing the different types of malicious hardware modifications, and indicative countermeasures were discussed. By addressing the importance of hardware security and providing countermeasures, the study aimed to enhance the resilience and security of IoT devices against HT-based attacks. Several security measures to prevent the threats and cyberattacks that arise in SDN-enabled UAV networks are presented in [14].
In [15], the state-of-the-art mechanisms for hardware security in the context of IoT devices were outlined and particular emphasis was placed on the employment of ML solutions. The study provided an overview of the latest advancements and techniques used to enhance the security of hardware components in IoT devices. It explored how ML solutions can be utilized to detect and mitigate potential threats and vulnerabilities. Another study highlighted the advantages and disadvantages of security measures used against potential attacks in UAV-based applications in different scenarios and, discussed the role of blockchain, ML, and watermarking [16]. In [17], a review of effective software-based and hardware-based authentication solutions for IoD network nodes was offered, and future directions for the IoD were discussed.
In [18], Security solutions for an IoT enabled by MEC with the help of UAVs were showcased. Subsequently, security strategies based on cutting-edge technology such as blockchain technology and machine learning for network node authentication were discussed. It is clear that a thorough comparison of the latest developments in hardware-based and software-based authentication methods and their use in the IoD is necessary, as well as a need for the development of previous surveys through comprehensive analysis to identify research gaps and open issues. Planning an authentication scheme for the IoD while considering the balance between security and performance is a complex task, as various authentication schemes can achieve a certain degree of scheme security, but performance is decreased.
Therefore, it is a necessary to thoroughly study and analyze modern authentication systems, their technologies, and their different types. Such an analysis will act as a bridge for scholars interested in this topic, helping them navigate its complexities and make informed decisions. While several survey papers have been published recently that explore software-based and hardware-based authentication techniques [10,19,20], there is still a need for further analysis to identify any security shortcomings and address them. These surveys have discussed authentication schemes and their associated techniques, but a more comprehensive examination is required to learn more about the field and uncover any potential vulnerabilities. The review papers on security issues in the IoD assessed in this review are displayed in Table 1.

Table 1.
Summary of review papers on security issues in the IoD.
1.2. Contribution
The following is a list of this paper’s main contributions:
- –
- We provided an overview of a wide range of relevant review papers on entity interaction in the Internet of Drone environment, focusing on their impact on security and performance (in Section 1.1). In this section, we conduct a survey aimed at comparing various relevant reviews and surveys, highlighting the strengths, weaknesses, and areas of focus of current approaches to entity authentication within this context. By examining authentication systems and their associated technologies, we aim to identify the best practices and gaps in the existing literature, developing a better comprehension of the potential and challenges associated with enhancing security in the Internet of Drones.
- –
- We present an overview of IoD communication links used to achieve secure drone operations (in Section 3). This section focuses on the requirements authentication schemes must meet in the IoD, covering essential security features including integrity, availability, authenticity, confidentiality, and privacy. Additionally, we discuss common attacks in the IoD and outline drone performance requirements that are related to computation, communication, storage costs, and power consumption. We aim to offer a thorough grasp of the security landscape by addressing these components and performance considerations necessary for effective drone operations within the IoD.
- –
- The IoD environment faces attacks due to a lack of security measures. To mitigate these adverse impacts, protection measures must be established to guarantee IoD security (in Section 4). We offer a comprehensive taxonomy of the latest authentication schemes used in the IoD and conduct comparative analyses of software-based, hardware-based, and hybrid-based techniques and their application in the IoD. Also, we examine the security and performance requirements of these techniques and discuss potential attacks on these IoD authentication schemes.
- –
- A discussion and comparison of the surveyed schemes is presented, (in Section 5) highlighting open issues in the IoD that require attention in future scheme designs.
- –
- We discuss the security landscape (In Section 6), including various scenarios in which attacks can cause a drone or ground station server to stop responding, along with mitigation strategies to ensure service continuity and system resilience. We also address the threat modeling of drone delivery systems in the cyber domain and explore mitigation methods. By examining these aspects, we aim to highlight the importance of proactive security measures in maintaining the operational integrity of drone services.
- –
- We cover open research topics (in Section 7) and, explore several such topics for the IoD that can significantly contribute to future IoD systems. We discuss promising directions for further study that have the potential to enhance the design of authentication schemes. By focusing on these areas, researchers can address current challenges and develop more robust and secure systems for drone operations, ultimately improving the overall effectiveness and reliability of the IoD environment.
2. Methodology
This paper seeks to summarize existing IoD authentication schemes. The PRISMA (Preferred Reporting Items for Systematic Reviews and Meta-Analyses) method was utilized for searching and selecting papers related to the scope of the study. The process followed in this paper is illustrated in Figure 1.
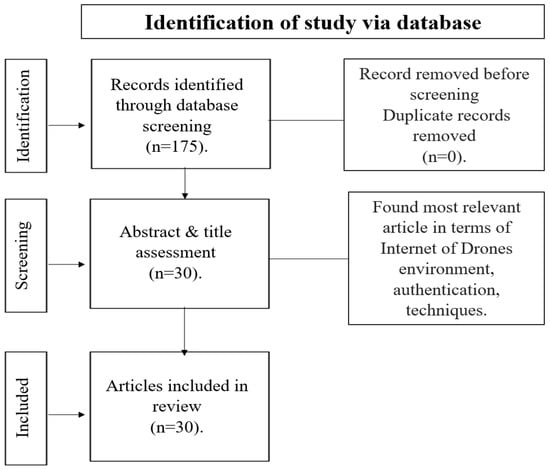
Figure 1.
Research methodology of the current review.
2.1. Identification
In the study identification phase, we selected databases considered to contain most known publications and journals, such as Springer, Elsevier (Computer Communications, Computer Networking), MDPI (Journal of Sensor and Actuator Networks, Drones), and IEEE (IEEE Access and IEEE Internet of Things Journal, IEEE Transactions on Information Theory, IEEE Communications Society). Then, several keywords were used to find relevant papers published between (2019 and 2023). These keywords include Internet of Drones, authentication, protocol, lightweight protocol, attack, security analysis, and performance analysis. Initially, 157 papers were found focused on covering the topic of various proposed authentication protocols in wireless network environments. There were no duplicate papers.
2.2. Screening and Eligibility
The titles and abstract sections of the retrieved publications were assessed to find papers related to proposed authentication protocols in the IoD. We selected the 30 most relevant papers, including those on IoD environment, security attacks on the IoD, and authentication techniques. This review includes all 30 papers, as shown in Figure 1.
3. An Overview of the IoD
The IoD refers to a network of networked drones that use the Internet to communicate with centralized systems and other devices. This interconnected network of drones enables various applications and services that leverage the capabilities of UAVs for a wide range of industries. As illustrated in Figure 2, the IoD environment comprises three elements:
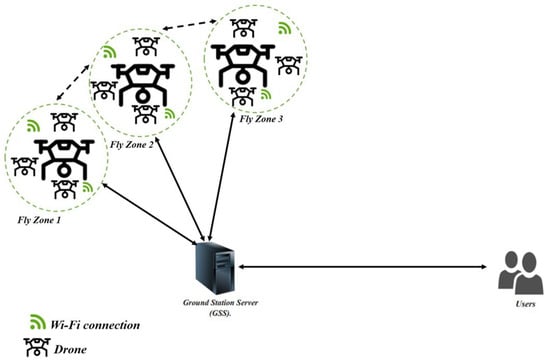
Figure 2.
IoD architecture [21].
- The ground station server registers the system’s components and initializes the system as a trusted authority.
- The user who has a smart device through which they can request access to the server’s stored data. The user interacts with the GSS to establish a secure connection and authenticate their identity.
- The drone, also referred to as an “unmanned aerial vehicle,” is an autonomous or distantly piloted flight system that performs various tasks within the IoD environment. The drone interacts with the GSS to establish a secure connection and authenticate its identity.
By connecting these objects and facilitating their interactions, an IoD authentication scheme enables secure access to drones within the IoD environment. An IoD authentication protocol aims to create a trusted, secure environment within the interconnected network of drones, guaranteeing that resources and drone communication are limited to authorized users and drones. By implementing a comprehensive and robust authentication scheme that includes user authentication, drone authentication, secure communication channels, and authorization controls for security protocols, the IoD environment can ensure a high standard of dependability and security in its operations.
3.1. Requirements of Authentication Scheme in the IoD
In the context of IoD communication links, ensuring information security is of paramount importance to achieving secure operations and safe drone traffic management. This section focuses on the authentication scheme requirements, which are essential for establishing a robust and protected communication infrastructure in the IoD.
3.1.1. Security Requirements
Security requirements are critical considerations when implementing any system, including an IoD system. These requirements outline the protect against data breaches, illegal access, and other security threats. Below, we have categorized the most common security features and attacks in the IoD [1,22].
- –
- Security Features
Security features are essential capabilities and functions implemented to mitigate threats and vulnerabilities within a system. In the context of the Internet of Drones, security features, such as integrity, availability, authenticity, confidentiality, and privacy, play a crucial role in mitigating threats and vulnerabilities [1,23]. In the table below we discuss each feature (Table 2).

Table 2.
Security features.
- –
- Security Attack
The IoD system is vulnerable to attacks that aim to compromise its security requirements. To mitigate these risks, several research papers have discussed the potential threats that the system may face during the authentication process. The insights derived from these studies serve to assist the designers of authentication schemes in identifying and addressing any potential faults that could lead to security breaches. Furthermore, the analysis and enhancement of authentication schemes are critical tasks in the security of the IoD system. By conducting thorough evaluations, researchers and system developers can identify and implement effective measures that strengthen authentication mechanisms, thereby enhancing the security and integrity of the IoD system against potential attacks [23,24]. In Table 3, we discuss some common attacks seen in the IoD.

Table 3.
Common attacks in IoD.
3.1.2. Performance Requirements
Performance requirements are critical considerations when evaluating authentication schemes in the IoD. Key performance metrics include communication overheads, computation overheads, storage overheads, and power consumption. These metrics directly impact the efficiency of authentication schemes in the IoD [9,24]. By addressing these performance requirements, we can design and optimize Internet of Drones systems to deliver high-performance, reliable, and efficient operations that meet the demands of drone communication, data processing, and control in various applications and scenarios.
- –
- Communication overheads:
The communication overhead encompasses supplementary data and, data processing, or time required to manage and support communication processes within a system. In the context of Internet of Drones communication, numerous factors contribute to communication overheads, including the volume of data transmitted during the authentication process, network bandwidth, and latency. Efficient authentication protocols aim to minimize communication overheads to mitigate network congestion and latency.
- –
- Computation overheads:
Computation overheads refer to the additional computational resources, processing time, and energy consumption required to execute tasks. On the Internet of Drones systems, computational overhead is essential to the effective function of drones and their associated components. Authentication protocols involve cryptographic processes such as encryption, decryption, hashing, and digital signatures, which require computational resources. The computation costs are the processing power and time needed for the execution of these cryptographic operations. Performance-efficient authentication protocols optimize computational complexity to ensure fast and efficient authentication without computational overhead.
- –
- Storage overheads:
Storage overheads for Internet of Drones systems refer to the additional storage space, management complexity, and associated costs incurred beyond the primary data requirements. Authentication protocols may require the storage of several kinds of data, such as user credentials and authentication tokens. Storage overheads refer to the storage space needed to keep these data secure. Efficient authentication protocols aim to minimize storage costs to optimize resource utilization.
- –
- Power consumption:
When designing and running Internet of Drones systems, power consumption is a crucial consideration. Drones typically rely on batteries for power and optimizing their power consumption is essential to extend flight times, improve operational efficiency, and reduce costs. Authentication protocols that consume excessive energy can significantly impact the operational lifespan of drones, by necessitating frequent battery replacements. Performance-efficient authentication protocols prioritize energy efficiency by reducing computational overhead and implementing power-saving techniques.
By considering these performance requirements, authentication protocols in the IoD can provide secure and efficient authentication while minimizing communication, computation, storage, and power overheads.
3.1.3. Summarization
We started this section by searching for and choosing relevant research articles published between 2019 and 2023. We then highlighted the security requirements of IoD authentication schemes, including security features, Integrity, availability, authenticity, secrecy, and privacy, as well as their defense against the following types of attacks: DoS, replay, spoofing, impersonation, eavesdropping, MITM, forgery, and known key attacks. Furthermore, we have outlined their performance requirements regarding computation, communication, storage costs, and power consumption. Figure 3 lists all the functional and security features of IoD systems, as well as their corresponding attacks. In the next chapter, we present a taxonomy and review of the latest authentication schemes in the IoD and conduct comparative analyses of the reviewed schemes based on these security attacks and features. We also present open issues with IoD authentication schemes.
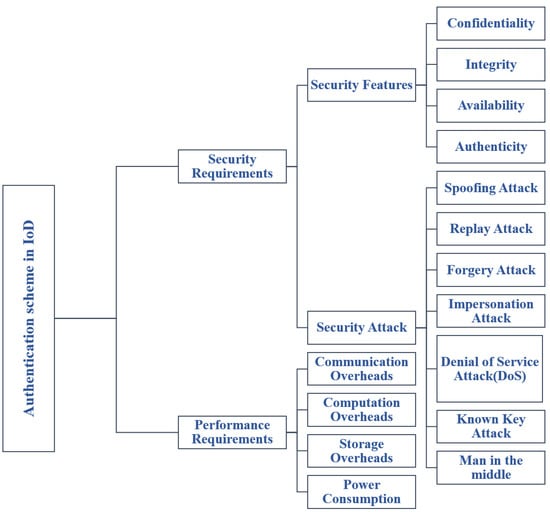
Figure 3.
Requirements of Authentication scheme in IoD.
4. Taxonomy of Existing IoD Authentication Techniques
The absence of security safeguards in its entities and communication routes exposes the IoD environment to possible hostile assaults. Establishing protection methods to assure IoD security, including authentication approaches, is required to lessen the negative effects of known and undiscovered security assaults [1,25]. In this section, we analyze existing authentication techniques. Figure 4 illustrates the classification of a current authentication scheme that can be established to ensure IoD security.
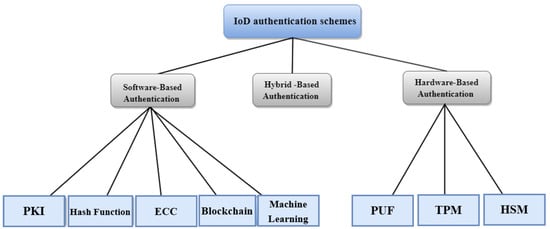
Figure 4.
Taxonomy of authentication schemes for the IoD.
4.1. Software-Based Authentication Techniques
To achieve lightweight and efficient authentication against malicious entities in the IoD environment, researchers of the architecture of the IoD seeks to explore emerging technologies and leverage advances in scientific research. Furthermore, they utilizes software-based techniques to address authentication challenges, software techniques refers to the use of authentication techniques that rely on software components and algorithms. These methods typically involve cryptographic techniques such as digital signatures, certificates, and public-key infrastructure (PKI) [1,17]. This section offered an overview of recent research efforts in this field, which are also shown in Table 4.
4.1.1. Public Key Infrastructure-Based Authentication
SENTINEL, proposed in [26], is a lightweight authentication scheme designed for the IoD environment. It utilizes PKI to authenticate drones and the GSS. The main objective of the scheme is to prevent unauthorized UAVs from accessing the IoD infrastructure. To accomplish this, the scheme relied on a secure protocol with a lightweight binary certificate format, and the SENTINEL prototype was implemented into this. Its security level was verified by ProVerif and compared to the traditional “TLS for IoT” protocol with client authentication. The experimental results show that the proposed scheme outperforms it and can perform authentication around 3.1 times faster than Transport Layer Security (TLS) for the IoT protocol.
In [27], a secure authentication protocol for the IoD was designed based on PKI. The protocol includes a key exchange during encryption and decryption, with the public and private keys, which dynamically change for each session generated at the GCS. The security of the authentication protocol was validated, and the performance results demonstrated that the proposed protocol is secure and efficient. The evaluation considered communication, computation, and storage costs using ProVerif and Real-Or-Random (ROR).
The scheme proposes in [28], is a secure identity and location validation scheme based on signature technology authentication with low computing requirements. The scheme enables the identification of drones before they enter a specific group. This method can handle the authentication of drones using PKI. The protocol improves the accuracy of detecting hostile drones by combining two approaches to identify intruders that depart from the planned trajectory. The proposed design was evaluated using a network simulator setup based on INET and OMNetCC. The results revealed a detection accuracy score over 85%.
4.1.2. Hash Function-Based Authentication
The proposed scheme in [29] used simple hash cryptographic functions to resist different types of attacks and reduce computation costs. An authentication protocol for the IoD environment based on hash-based authentication was presented to reduce computation cost and power consumption during the encryption and decryption process and resist possible attacks. The suggested protocol is safe and lightweight, according to the findings of a security study and performance assessment.
The protocol proposed in [30], was a lightweight, effective privacy-preserving protocol for the Internet of Devices. Cluster heads, server stations, and clustered drone nodes that collected sensory data made up the IoD network. The safe transmission of sensing data was made possible by the suggested scheme’s use of hash functions and XOR operations to create a secure channel and carry out mutual authentication between the nodes.
Subsequently, a formal verification was conducted using a verification tool and a random Oracle model. The results show that the proposed protocol is secure, exhibits low power consumption, and incurs low computation costs. In [31], a lightweight authenticated key exchange protocol for the Internet of Drone environment offered three-factor security protocols that employed the user’s password, mobile device, and biometrics. The proposed protocol utilized a hash function and exclusive-OR operation. The suggested protocol has superior security features and has minimal computational and communication costs, according to a formal security analysis done with BAN logic.
4.1.3. ECC-Based Authentication
The scheme proposed in [32] is an authentication scheme based on ECC and symmetric keys that ensure secure communication between users and drones. An informal analysis demonstrated the proposed scheme’s superior security and efficiency performance. Furthermore, the performance of this method during formal testing using the ROM in [32] shows that there is a balance between security and efficiency. In [33], an authentication scheme using elliptic curve cryptography was introduced for wireless sensor networks, where the UAVs collect data from sensors to against various types of security attacks. According to the performance review, this plan reduced the amount of time required to complete system operations.
In [34], the suggested model considered a polynomial adversary capable of significantly impacting the communication channels in the IoD network that, dynamically added drones. It consisted of a Trusted Authority Center responsible for key generation, mobile edge computing devices that aided drones in computation tasks, and the GCS. The security analysis used for both informal and formal evaluations, utilizing the ProVerif tool, showed that the suggested model is secured against attacks. A lightweight multi-factor authentication protocol for the IoD was Presented in [35]. The proposed protocol realizes multi-factor security using smart cards, passwords, and biometrics; It also accomplishes anonymity, untraceability, and complete forward secrecy. According to a security study, the suggested protocol can withstand assaults. A performance investigation revealed that the protocol had improved execution efficiency and decreased power consumption.
4.1.4. Blockchain-Based Authentication
In [36], addressing the simultaneous authentication of several entities in UAV-based networks was the main goal. An attribute-based voting system for a blockchain-enabled trustworthy UAV network (BT-UAVN) was introduced. Blockchain technology was used by the BT-UAVN to organize and record transactions for vulnerability assessments. The security evaluation of the BT-UAVN was conducted through hands-on experimentation and, considering two attack scenarios:one related to facilities and one associated with the communication channel. Additionally, in order to identify ineligible UAVs, a blockchain-based technique called ACSU-IoD (Access Control Scheme for Unauthorized UAV Detection and Mitigation in an IoD Environment) was developed in [37]. The study focused on an IoD system where AI analytics aided in decision-making and mutual authentication between the UAVs and the ground control station was required.
4.1.5. Machine Learning-Based Authentication
In the context of UAV-based IoT networks, the utilization of Federated Learning FL for UAV authentication has been a focus of contemporary research. In [38], a proposed drone authentication model based on RF features in the IoT network is presented. It utilizes the data generated by drones while providing privacy preservation advantages by employing FL to train the data. Its proposed Deep Neural Network architecture enhances the performance of drone authentication and, outperforms other machine learning models. In [39], a situational-aware authentication scheme for UAV deployments was suggested. The scheme addressed the secure selection of a legitimate cluster head from the UAVs within a cluster to ensure security during this selection process. The proposed scheme effectively prevented attacks by leveraging edge intelligence and applying a linear discriminant analysis.
In addition, the scheme underwent evaluation in various application scenarios, including environments with unreliable communication links and at varying flying altitudes. Moreover, the results included from the simulation of cross-layer data verify the authentication scheme’s low computational cost and accuracy. To improve the detection of intruder drones and optimize resource management, ref. [40] proposed a smart drone controller framework based on machine learning. The framework dynamically selects the appropriate ML algorithm based on the specific scenario, allowing many drones with Wi-Fi to operate independently and cooperatively without requiring visual line-of-sight connectivity. In general, it is crucial to emphasize that the system must have enough processing power and sensor data in order for ML solutions to be practically viable.

Table 4.
Recent research on software-based authentication techniques for the IoD.
Table 4.
Recent research on software-based authentication techniques for the IoD.
| Scheme | Environment | Techniques | Security Analysis and Simulation Tools | Advantages |
|---|---|---|---|---|
| [29] | Flying Ad Hoc Network (FANET) | Hash functions | Real-Or-Random (ROR), ProVerif. | Low computation and communication costs. |
| [26] | IoD | Public key infrastructure (PKI), Hash functions | ProVerif. | Execution efficiency, low computation costs. |
| [33] | Wireless sensor network (WSN) | Elliptic-Curve Cryptography (ECC) | Informal analysis. | Low computation cost. |
| [30] | UAV-based IoT | Hash functions | Random Oracle model (ROM). | Low power consumption, low computation cost. |
| [31] | IoD | Exclusive-OR (XOR) operations, hash functions | Burrows–Abadi–Needham (BAN) logic. | Low communication and computation costs, enhanced security features. |
| [27] | IoD | PKI, hash functions | ROR, ProVerif. | Robustness against various attacks and efficiency through communication and computation overhead. |
| [28] | FANET | PKI | Informal analysis. | Acceptable costs and high accuracy detection. |
| [32] | IoD | ECC | Informal analysis. | Trade-off between efficiency and security. |
| [34] | IoD | ECC | Informal analysis and ProVerif. | Low power consumption, computation, and communication costs |
| [38] | UAV-based IoT | Deep Neural Network (DNN) | Informal analysis. | High level of accuracy. |
| [39] | UAV | Linear discriminant Analysis (LDA) | Informal analysis. | Low computational overhead, and high accuracy. |
| [40] | UAV | Machine Learning | - | Mitigate security risk through intruder detection. |
| [36] | UAV | Blockchain | Informal analysis. | Efficiency and secure links. |
| [37] | IoD. | ECC, hash functions, blockchain | Informal analysis, ROR, AVISPA. | Low communication, low computation costs. |
4.2. Hardware-Based Authentication Techniques
Hardware-based authentication involves the use of specialized devices or hardware components for authentication purposes. These hardware components provide additional security measures due to secure elements such as USB tokens, smart cards, and hardware security modules (HSMs). Moreover, hardware-based authentication offers advantages such as tamper resistance, secure key storage, and protection against attacks [1,17]. This section provides an overview of recent research efforts in this field, which are also shown in Table 5.
4.2.1. PUF-Based Authentication
To optimize the utilization of UAV network resources and enhance service provision, hardware security modules (HSMs) can be used, as these are well-suited to managing and handling UAV communication networks. In [41], a two-stage, lightweight mutual authentication scheme was proposed for deployment in surveillance areas. The protocol leveraged physically unclonable function (PUF) chips, which were embedded in the drones to generate challenge-response pairs, eliminating the need to store secret keys in the UAV nodes’ physical memory. Specifically, the leader drone and the base station were involved in the first authentication step, while the powerful intermediate leader drones and resource-constrained micro drones were the focus of the second authentication phase. Two distinct session keys—one between the leader drone and the ground station and another between the small drone and the ground station—were created during each authentication procedure.
The PARTH protocol was evaluated in terms of its computing overheads, latency, and resilience against security attacks. A performance comparison demonstrated that the PARTH protocol employed simple computations, resulting in a lightweight and efficient solution. Furthermore, the protocol achieved mutual authentication and physical security. It also exhibited security and resilience against various security attacks. Recently, the integration of radio frequency identification (RFID) technology and physically unclonable functions (PUFs) has been proposed for the effective real-time recognition and tracking of UAVs. In [42], a privacy-preserving authentication protocol based on PUFs for an RFID-enabled UAV system was suggested. The protocol focused on a military scenario where UAV authentication was crucial for secure operations within a specific fly zone.
With in this protocol, a ground-based reader scanned the tags to verify the credentials of the UAVs. Through security and performance analyses, it was demonstrated that the proposed authentication protocol achieves both security and efficiency, ensuring the secure operation of UAVs. In [43], a lightweight identity security authentication protocol called the Optimized Identity Authentication Protocol (ODIAP) was proposed for the IoD to address security threats in a power-efficient manner.
The protocol utilized the Chinese Remainder Theorem to optimize computing resources at UAV nodes and facilitate the transmission of complex computation tasks to server nodes while maintaining security. The ODIAP verification used the widely adopted ProVerif-based automated analysis tools, which showed that the ODIAP has sufficient security. Moreover, the ODIAP significantly improved the utilization of computing resources. To sum up, the ODIAP can effectively optimize the authentication process of IOD networks. To enhance the mutual authentication process in UAV connections while minimizing communication, computation, and storage overheads, it employes physically unclonable functions (PUFs).
A lightweight mutual authentication protocol called SecAuthUAV was proposed in [44], for UAV-ground station authentication, eliminating the need for storing any data i the UAVs. This protocol was further extended to support UAV-UAV authentication. During the authentication process involving the ground station, SecAuthUAV establishes a secure session key utilizing secret information generated by PUFs. The protocol guarantees essential security features and can generate a unique session key for each session without storing secret keys.
Additionally, SecAuthUAV demonstrates competitive performance compared to other authentication schemes for UAVs when, considering computation, communication, and storage costs. Overall, SecAuthUAV is highly efficient and viable for UAV-ground station authentication, providing a secure and efficient solution. In this direction, ensuring hardware and software security in drones, a drone authentication protocol based on PUFs and the utilization of a Trusted Execution Environment (TEE) established through ARM’s TrustZone technology was proposed in [45]. Moreover, it included drones equipped with field-programmable gate array (FPGA)-based Ring Oscillator (RO) PUFs, which served as digital fingerprints for the onboard companion computer. The main objective of this protocol was to address various security challenges, including software and hardware breaches, drone identification, and the prevention of link hijacking. By leveraging the unique fingerprints generated by the PUFs, the protocol enabled authentication.
The combination of TEE and PUF-based authentication contributed to strengthening the security of the drones. This protocol also aimed to mitigate security risks and enhance the overall security posture of drones. A cost-effective hardware-based authentication mechanism for drones was proposed in [46], where PUF units based on a memristors deployment were placed on the UAV and the GS. One potential approach for UAV ID verification is the usage of memristors. It is challenging to identify a UAV because of the distinct features of memristors that their technology offers, which guarantee that these devices cannot be replicated. Such memristors are inexpensive to produce, and integrating them with current data transfer devices makes system deployment simple. Additionally, this kind of PUF is less vulnerable to a number of physical assaults.
4.2.2. TPM and HSM-Based Authentication
There are challenges that hinder the authentication process for UAVs, such as resource limitations, the joint utilization of cross-domain drones, and their operation in weakly connected task networks. Therefore, in [47], a secure and globally applicable cryptographic authentication system for UAVs was proposed, utilizing public key infrastructure (PKI), hardware security modules (HSMs), and the widely accepted Transport Layer Security (TLS) protocol. This system aims to provide mutual and robust cryptographic authentication. The TLS protocol was utilized for mutual authentication and communication protection. Specifically, a flight control server was securely notified via a secure communication channel of the UAV coordinates, which dictated the UAV’s position inside the airspace. The UAVs were given authorization to fly in the authorized flight zone after completing the certificate authentication process. An HSM was put in place to guarantee that the required keys and certificates were stored securely. According to an analysis, it can accomplish global connectivity while avoiding security threats.

Table 5.
Recent research on hardware-based authentication techniques for the IoD.
Table 5.
Recent research on hardware-based authentication techniques for the IoD.
| Scheme | Environment | Techniques | Security Analysis and Simulation Tools | Advantages |
|---|---|---|---|---|
| [41] | UAV | PUF | Informal analysis and Mao and Boyd logic | Low computational cost and resistance against attacks. |
| [42] | IoD | Trusted Platform Module (TPM). | Informal analysis | Low computation and communication costs, and high security. |
| [47] | UAV | PUF | Informal analysis | Low computation cost. |
| [43] | IoD | PUF | Informal analysis, and ProVerif | Sufficient security features and efficient use of computer resources. |
| [44] | UAV | PUF | Informal analysis and Mao and Boyd logic | Acceptable computation, and communication costs, and sufficient security. |
| [48] | UAV | PUF | Informal analysis | Low computation cost, and low power consumption |
| [46] | UAV | PUF | Informal analysis | Efficiency. |
4.3. Hybrid-Based Authentication Techniques
Hybrid-based authentication is a technique that combines software-based and hardware-based techniques to enhance the security of IoD environments. By integrating the strengths of both techniques, we can obtain a hybrid-based authentication technique that provides a robust and layered approach to authentication. Software-based authentication involves the use of protocols, cryptographic algorithms, and user credentials to verify the identity of the entity or user. However, it may be vulnerable to security attacks such as replay or impersonation attacks. On the other hand, hardware-based authentication relies on physical characteristics or unique user identifiers to establish trust, including biometrics, hardware tokens, or PUFs. Hardware-based authentication enhances security by adding an extra layer of protection that is difficult to clone. This section provides an overview of recent research efforts in this field, which are also shown in Table 6.
To sum up, the hybrid-bead authentication technique combines software-based and hardware-based techniques and offers several advantages. The most significant among them is its enhancing security through protection against various attacks and greater confidence in the authenticity of users or entities in the IoD environment. In the context of V2G systems, protocols must meet security requirements, be lightweight in their implementation, and protect against various attacks. To address these requirements, in [49] proposed a combination of authentication techniques, physical unclonable functions, and secure user key exchange authentication (SUKA) protocol. The SUKA protocol utilizes PUFs to establish two-step mutual authentication between electric vehicles and the grid server in V2G systems. The proposed protocol aims to protect against various attacks, such as MITM, replay, and impersonation attacks. The simulation results show the proposed protocol is lightweight in terms of its communication and computation overheads and secure against security attacks.
Additionally, the security challenges associated with physically protecting healthcare IoT devices against node tampering attacks have prompted the design of several authentication techniques. One such technique is a two-stage authentication protocol that utilizes PUF, message authentication code, and symmetric key, as presented in [50]. It creates distinct session keys for every authentication action and uses PUFs to dynamically produce the secret data needed for authentication, ensuring session key confidentiality and uniqueness. The suggested protocol has several security characteristics, including physical security, authentication, integrity, and untraceability, and is safe from a number of security threats, including replay attacks, node manipulation, and MITM. The suggested protocol outperforms similar authentication systems employing computing overheads, according to a simulation.
In [51], For safe communications between the UAV and its base station, PCAP—a lightweight mutual authentication protocol—is suggested. The challenge-response pair of the physical unclonable functions is utilized as the beginning condition of a chaotic system to randomly mix messages in order to produce a secret session key, using both a UAV and a ground station. To verify the efficacy of the PCAP, OMNeT++ simulations are performed per the suggested procedure. In terms of processing, communication overhead, power consumption, and secure communications against assaults, the simulation results show that the PCAP performs well.
A two-stage lightweight authentication and key agreement system was presented in [52]. The context of an emerging environment for UAVs, where they are susceptible to a variety of security risks, including physical capture assaults, given their low capability. The protocol aimed to address the limited power constraints of UAVs. In this protocol, two session keys were generated in a single session: one between the member drone and the head drone, and another between the head drone and the ground station server. The protocol achieved improved authentication efficiency by adopting the hash function and XOR operations. To protect privacy and enhance identity verification, PUF chips were embedded into the UAVs. The challenge and response pairs generated by the PUF served as an effective credential for identity verification. The proposed protocol’s security was demonstrated through security proofs using BAN logic, AVISPA simulation tools, and an informal security analysis. It exhibited communication security and resistance against several security attacks. A performance analysis, including of its computational overheads and communication overheads, further confirmed the protocol’s security and effectiveness for UAV networks.
As task-oriented authentication model (ToAM) for UAVs based on the blockchain was proposed in [53]. This model leverages the tamper-resistant properties of the blockchain and utilizes smart contracts to achieve decentralized identity authentication, reducing the computing cost for UAVs. In a ToAM, UAVs are prepared with TPM chips for secure data storage and proper network operation in weak connection scenarios. Analyzing the results demonstrated that the ToAM enables lightweight and secure authentication for UAVs with low computation and communication overheads.

Table 6.
Recent research works on hybrid-based authentication techniques for the IoD.
Table 6.
Recent research works on hybrid-based authentication techniques for the IoD.
| Scheme | Environment | Techniques | Security Analysis and Simulation Tools | Advantages |
|---|---|---|---|---|
| [52] | UAV | PUF Hash functions XOR | Informal analysis BAN logic AVISPA | Efficiency, and ability to, resist different types of security attacks. |
| [50] | IoT | PUF MAC Symmetric key | Informal analysis Mao and Boyd logic | Low computation and communication costs, and high security. |
| [53] | UAV | TPM Blockchain Hash functions PKI | Informal analysis | High security, and low computation and communication overheads. |
| [49] | IoT | PUF SUKA | Informal analysis Mao and Boyd logic | Low computationa cost and resistance against attacks. |
| [51] | UAV | PUF Chaotic system | Informal analysis OMNeT++ | High security. |
5. Open Issues in IoD Authentication Schemes
Even though the literature suggests that authentication schemes for the IoD have made significant progress in tackling many security threats and issues in the IoD environment, there are still open issues and significant challenges that researchers and industry professionals are addressing [54,55]. In this section, we will discuss the open issues in the IoD. These are listed in. Table 7 and Table 8 below. In Table 7, we have LISTED various security attacks that target the IoD environment. In Table 8, we have illustrated the security and functional features of authentication schemes. Consequently, through Table 7, we can see that IoD schemes are still vulnerable to DoS attacks and privileged insiders. Moreover, we have illustrated the most common attack that threatens most of the schemes discussed, which is DoS attacks. In addition, the scheme’s robustness against different security attacks was determined, and it was found that the most common attack that authentication schemes resist, is the replay attack. Furthermore, the approach proposed in [30,55] has achieved a higher level of security compared to alternative schemes in terms of its resistance against attacks. We noticed that most IoD authentication schemes in Table 8 have issues with anonymity, un-traceability, and forward secrecy. The key open issues in IoD authentication schemes can be summarized as follows:
- Scalability: As the number of drones in the airspace continues to increase, authentication schemes must be scalable in terms of the amount of information transferred, the number of nodes in their architecture, and their time slots, while also being able to handle many devices simultaneously. Thus, most systems are either overwhelmed with operations or cause operations to become delayed or stop functioning.
- Security and Robustness against attacks: It is important for IoD authentication schemes to be resilient against various types of attacks, including impersonation, replay attacks, tampering attacks, etc. Enhancing the security of authentication protocols in the IoD is important for scheme creators, especially considering the sensitivity of the data involved. Authentication protocols are designed to protect sensitive information and ensure that only authorized entities can access it. As a result of that, the scheme needs to provide authenticity, confidentiality, integrity, and privacy. All these security aspects must be guaranteed through simulation tools and mathematical proofs.
- Privacy: Protecting the privacy of drone operators and their sensitive information is paramount and essential. Authentication schemes should incorporate privacy-preserving techniques, such as anonymous authentication, to maintain the anonymity of operators and ensure un-linkability to prevent unauthorized tracking. These procedures ensure the confidentiality of operators activities and personal information, enhancing the privacy and security of authentication.
- Environments with limited resources: Many IoD entities, especially drones, operate with limited computational power, storage capacity, and power consumption. Designing a lightweight authentication protocol that minimizes communication, computation, and storage costs while maintaining sufficient security is vital.
- Trust: Establishing trust between network entities in an IoD environment, such as drones, ground stations, and other entities, is essential for secure communication. Designing techniques to verify the trustworthiness and integrity of participants in an environment is crucial. These techniques aim to ensure that the entities in the authentication phase are trusted and that their actions are conducted with integrity. By implementing these techniques, authentication schemes ensure their security and reliability.

Table 7.
Security attacks on authentication schemes discussed in the literature.
Table 7.
Security attacks on authentication schemes discussed in the literature.
| Scheme | Resist Impersonation Attack | Resist MITM | Resist Privileged Insider | Resist Replay Attack | Resist DoS Attack | Resistance to Drone-Capture Attack |
|---|---|---|---|---|---|---|
| [56] | × | ✓ | ✓ | ✓ | × | × |
| [57] | × | ✓ | × | ✓ | × | ✓ |
| [33] | × | × | ✓ | ✓ | ✓ | ✓ |
| [31] | ✓ | × | ✓ | × | × | ✓ |
| [26] | ✓ | × | ✓ | × | ✓ | × |
| [45] | × | × | × | ✓ | × | ✓ |
| [30] | × | ✓ | ✓ | ✓ | ✓ | ✓ |
| [53] | × | × | ✓ | ✓ | × | × |
| [41] | ✓ | ✓ | × | ✓ | × | ✓ |
| [44] | × | ✓ | × | ✓ | × | × |
| [58] | × | ✓ | × | ✓ | × | × |
| [59] | × | × | × | ✓ | × | ✓ |
| [29] | × | × | × | × | ✓ | × |
| [27] | ✓ | ✓ | ✓ | ✓ | × | ✓ |
| [28] | ✓ | × | ✓ | × | ✓ | × |
| [35] | ✓ | ✓ | ✓ | × | × | ✓ |
| [32] | ✓ | × | ✓ | ✓ | × | ✓ |
| [34] | ✓ | ✓ | ✓ | ✓ | ✓ | × |
| [36] | ✓ | × | × | × | ✓ | × |
| [37] | ✓ | ✓ | × | ✓ | ✓ | ✓ |
| [47] | × | × | × | ✓ | × | × |
| [42] | × | ✓ | × | ✓ | ✓ | ✓ |
| [43] | ✓ | ✓ | × | ✓ | ✓ | × |
| [60] | × | ✓ | ✓ | ✓ | × | |
| [52] | ✓ | × | × | ✓ | × | ✓ |
| [61] | ✓ | ✓ | × | ✓ | × | ✓ |
| [62] | ✓ | × | ✓ | ✓ | ✓ | ✓ |
| [63] | ✓ | ✓ | × | ✓ | ✓ | × |
| [64] | × | ✓ | × | ✓ | × | × |
| [65] | ✓ | ✓ | × | ✓ | × | × |

Table 8.
Functional security features of authentication schemes.
Table 8.
Functional security features of authentication schemes.
| Scheme | Mutual Authentication | Scalability | Anonymity | Un-Traceability | Perfect Forward Security |
|---|---|---|---|---|---|
| [56] | ✓ | × | × | × | ✓ |
| [57] | × | ✓ | ✓ | × | × |
| [33] | ✓ | ✓ | ✓ | ✓ | × |
| [31] | ✓ | × | ✓ | ✓ | × |
| [26] | × | ✓ | × | × | ✓ |
| [45] | ✓ | ✓ | × | × | × |
| [30] | ✓ | ✓ | × | × | ✓ |
| [53] | ✓ | ✓ | × | × | × |
| [41] | ✓ | ✓ | × | × | ✓ |
| [44] | ✓ | × | ✓ | × | - |
| [58] | ✓ | × | × | × | ✓ |
| [59] | ✓ | ✓ | × | ✓ | × |
| [29] | ✓ | ✓ | × | × | ✓ |
| [27] | ✓ | ✓ | × | × | × |
| [28] | ✓ | ✓ | × | × | ✓ |
| [35] | ✓ | × | ✓ | ✓ | ✓ |
| [32] | ✓ | ✓ | ✓ | ✓ | × |
| [34] | ✓ | × | × | × | ✓ |
| [36] | ✓ | × | × | ✓ | × |
| [37] | ✓ | ✓ | × | × | - |
| [47] | ✓ | × | × | × | × |
| [42] | ✓ | ✓ | × | × | ✓ |
| [43] | × | × | ✓ | ✓ | ✓ |
| [60] | × | ✓ | × | × | × |
| [52] | ✓ | × | ✓ | ✓ | ✓ |
| [61] | ✓ | × | ✓ | ✓ | × |
| [62] | ✓ | × | ✓ | × | ✓ |
| [63] | ✓ | ✓ | × | × | ✓ |
| [64] | ✓ | ✓ | × | × | ✓ |
| [65] | ✓ | × | ✓ | ✓ | × |
6. Use Case: Threat Modeling for Drone Delivery
Network entities usually communicate using a public communication channel. Due to the channel’s openness and lack of defenses, the exchanged information is exposed to various security threats. This creates an opportunity for an adversary to use the communication channel’s open nature to compromise the integrity, confidentiality, or availability of information shared between network entities. In this section, we discuss some scenarios where attacks can cause a drone or ground station server to stop responding, along with mitigation strategies to ensure service continuity and system resilience.
- Endpoint entities, whether a user or a drone, are reliable entities that can connect to the network via public channels. Consequently, an adversary can intercept or eavesdrop on conversations and then alter or forge the exchanged messages.
- –
- Mitigation: Implementing end-to-end encryption techniques can ensure that data are secured on the drone’s end and stay encrypted until they reach the intended receiver, who possesses the decryption key. This method secures the communication channel by making the data unreadable to any unauthorized party that might attempt to intercept them during transmission. End-to-end encryption protects the security and privacy of the data being transferred from malicious actors and possible eavesdroppers. Attempts to access sensitive information or alter the transmitted messages are thwarted because, even if the data are intercepted, they cannot be decrypted without the encryption key [62].
- An adversary can launch a hardware attack targeting a drone or ground station server’s components, leading to system unresponsiveness. As a result, there could be security breaches, communication problems, and a loss of control over the drone.
- –
- Mitigation: Set up failover protocols that automatically switch communication channels or systems in the event of the drone or ground station server becoming unresponsive, thereby, ensuring continuous communication and control over the drone by transitioning to backup systems or communication links. [63].
Furthermore, it is presumed that in an IoD environment, the GSS is a trusted network entity that cannot be penetrated by an attacker.
- –
- Threat Modeling for Amazon Drone Delivery
Through its drone delivery service, Amazon delivers packages that do not exceed five pounds in weight to customers within sixty minutes. Drone technology powers the service improving delivery efficiency and creating sustainable delivery solutions for packages. Drone delivery markets will achieve a global value of USD 29 billion by 2027 due to customer demand for rapid delivery as technology continues to advance in this sector [64]. The delivery procedure commences after Amazon customers select appropriate products through their website. Customers have the chance to select their delivery location at the checkout point. When customers choose to have products purchased through online orders delivered, the drone-based delivery system begins as the aircraft departs from a nearby distribution facility. The system has advanced sensors that can detect obstacles in its path to delivery locations as the system finishes its assigned routes. The drone takes a descending trajectory, after which it releases packages to the exact delivery location and proceeds back to its base [65]. However, these drones also face various security and operational challenges, particularly regarding authentication and location tracking.
- –
- Scenario of Unauthorized Access during Amazon Drone Delivery
Various severe security threats challenge Amazon’s drone delivery system. Attackers gain control of drones through compromised credentials which are a major unauthorized access threat. The interception of data presents a grave security threat to Amazon’s drone delivery system since cyber attackers can monitor transmissions to steal customer details along with their shipment information. When attackers hijack drones they can send them to unauthorized drop locations for package theft purposes. DoS attacks make system security more complex because they have the ability to flood the control platform with requests which results in operational disturbances and delivery delays. Physical strikes on drone delivery vehicles which involve sabotage or other methods could interrupt distribution operations while simultaneously reducing service dependability. The system requires strong protective measures because these security risks demonstrate its potential weaknesses.
- –
- Mitigation: It is crucial to concentrate on robust encryption and authentication. By asking users to confirm their identity using a secondary method—such as a number given to their mobile device—two-factor authentication will provide an additional degree of protection, as well as their password. Enforcing robust password policies is equally important, this includes requiring complicated passwords that contain a mix of capital and lowercase letters, digits, and special characters. It also entails enforcing frequent password changes to lessen the chance of unwanted access.
In conjunction with strong authentication, encryption strategies are vital for protecting sensitive data. Ensuring that all communication between drones and control systems is encrypted will safeguard against data interception and eavesdropping. Utilizing protocols such as TLS (Transport Layer Security) can help secure data in transit. At the same time, end-to-end encryption can protect information from the point of transmission to its destination. Additionally, encrypting data stored in control systems guarantees that, even in the event of unwanted access, the data cannot be decrypted without the right keys [62].
This scenario demonstrates the significant risks associated with unauthorized access to the drone delivery system. The potential for abuse and, fraud, and the resulting harm to finances and reputation underscores the importance of implementing strong security measures to guard against these threats. By prioritizing robust authentication and encryption strategies, Amazon can significantly reduce the likelihood of unauthorized access and enhance the overall security of its drone delivery operations.
7. Discussion of Future Research Directions
Drone operations in a variety of IoD applications can become safer and more dependable thanks to IoD authentication approaches that can improve security and efficiency [66]. Some future research directions for the IoD are as follows:
- –
- IoD authentication schemes based on emerging technologies such as blockchain, edge computing, and machine learning should be proposed in tandem with traditional cryptography schemes. This is a research topic in the IoD that needs critical attention. Emerging technologies have the potential to enhance security and privacy in the IoD environment.
- –
- Investigating methods to increase the efficiency of authentication protocols and enhance their scalability for large-scale deployments of drones. This might involve exploring lightweight cryptographic techniques, optimizing communication protocols, and designing efficient key management approaches.
- –
- Advancing privacy-preserving techniques for IoD authentication protocols should protect the privacy of drones and the sensitive data transmitted by drones. This may involve exploring different privacy techniques, anonymization approaches, and secure multi-party computation.
- –
- Developing IoD authentication protocols that are resilient against advanced attacks, including advanced malware, sophisticated attacks, and spoofing techniques, is vital. This may require behavior analyses, the incorporation of anomaly detection, and security measures.
- –
- Future work could be dedicated to real-world deployments and validations of IoD authentication schemes to evaluate their usability, effectiveness, and performance. This would involves assessing the robustness, practicality, and scalability of these schemes in various scenarios.
8. Conclusions
Because of their agility, adaptability, relative affordability, and simplicity of deployment, drones have found widespread usage in both defense and civilian applications. Drones have become more common in civilian uses including weather forecasting, search and rescue, agronomy, and healthcare in recent years. In the upcoming years, a number of innovative services and applications are anticipated. Drones have also become a crucial component of the communication channels connecting IoT facilities. as well as in the field of wireless communication networks. The performance and dependability of drone-assisted wireless networks are seriously threatened by a number of security issues and privacy and security hurdles, which might limit the Internet of Things’ potential to have the greatest possible influence on the community and industry. In scenarios where drones have limited resources, restricted batteries, or lack dedicated edge computing infrastructures, the utilization of complex cryptographic methods may face significant limitations. Therefore, there is a need to focus on developing lightweight authentication techniques that are either software-based or hardware-based.
These lightweight techniques are expected to play an essential role in helping to establish IoD systems, as they can operate efficiently within the resource constraints of drones while maintaining high security levels. This paper was designed with the aim of providing a convenient technique for the successful authentication of network entities in the IoD. In this regard, we initially presented the security requirements of these systems, including their requierd security features, and the most common security attacks on the IoD. Additionally, we found that the most frequent attacks in IoD schemes are DoS and privileged insider assaults, which must to be prevented in the design of any authentication system. Then, we discussed and compared related survey papers. Subsequently, this paper outlined current trends in IoD authentication. Furthermore, in this paper we also presented an overview and categorization of software-based authentication techniques and reviewed hardware-based authentication techniques.
In conclusion, our survey paper addressed future research directions in this field and highlighted the unresolved concerns that should be taken into account when proposing any IoD authentication technique. The following is a summary of the paper’s findings:
- –
- A trade-off between security and efficiency should be made during the practical implementation of the IoD. While robust security measures are essential to protect against various threats, they often introduce overhead that can adversely affect system performance. This is particularly important for drones, which rely on battery power. For instance, implementing strong encryption algorithms may enhance security but lead to increased latency, which is significant in real-time applications. Therefore, finding the right balance between security and efficiency is vital to ensure that the IoD is secure and operationally efficient.
- –
- Computation, communication, and power consumption are the primary performance metrics employed by various authentication schemes.
- –
- Conventional cryptographic techniques, such as hash functions, ECC, and PKI, can be used to reduce the security threats and risks posed by malicious attacks.
- –
- ML-based techniques have opened up new avenues for security protection and separating malevolent from benign entities. Running these algorithms on the cloud greatly improves an IoD system’s efficiency, despite the fact that they need a large amount of processing power.
- –
- The implementation of blockchain technology provide an extra degree of protection.
Author Contributions
Conceptualization, A.F.A. and A.M.A.; methodology, A.F.A. and A.M.A.; data curation, A.F.A.; writing—original draft preparation, A.F.A.; writing—review and editing, A.F.A. and A.M.A.; supervision, A.M.A.; funding acquisition, A.M.A. All authors have read and agreed to the published version of the manuscript.
Funding
The APC was funded by the National Cybersecurity Authority Grant Agreement No. CRPG-25-2056 and, SAUDI ARAMCO Cybersecurity Chair, Imam Abdulrahman Bin Faisal University.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Acknowledgments
The authors are grateful to the National Cybersecurity Authority for the Cybersecurity Pioneers Research and Innovation Grant they were awarded. They also thank the Saudi Aramco Cybersecurity Chair at Imam Abdulrahman bin Faisal University for their generous funding and valuable support. Their contributions have significantly advanced the progress of this research.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Abdelmaboud, A. The internet of drones: Requirements, taxonomy, recent advances, and challenges of research trends. Sensors 2021, 21, 5718. [Google Scholar] [CrossRef]
- Michailidis, E.T.; Potirakis, S.M.; Kanatas, A.G. AI-Inspired Non-Terrestrial Networks for IIoT: Review on Enabling Technologies and Applications. IoT 2020, 1, 21–48. [Google Scholar] [CrossRef]
- Michailidis, E.T.; Miridakis, N.I.; Michalas, A.; Skondras, E.; Vergados, D.J. Energy optimization in dual-ris uav-aided mec-enabled internet of vehicles. Sensors 2021, 21, 4392. [Google Scholar] [CrossRef] [PubMed]
- Bithas, P.S.; Michailidis, E.T.; Nomikos, N.; Vouyioukas, D.; Kanatas, A.G. A survey on machine-learning techniques for UAV-based communications. Sensors 2019, 19, 5170. [Google Scholar] [CrossRef] [PubMed]
- Mehta, P.; Gupta, R.; Tanwar, S. Blockchain envisioned UAV networks: Challenges, solutions, and comparisons. Comput. Commun. 2020, 151, 518–538. [Google Scholar] [CrossRef]
- McCoy, J.; Rawat, D.B. Software-defined networking for unmanned aerial vehicular networking and security: A survey. Electronics 2019, 8, 1468. [Google Scholar] [CrossRef]
- Yaacoub, J.P.; Noura, H.; Salman, O.; Chehab, A. Security analysis of drones systems: Attacks, limitations, and recommendations. Internet Things 2020, 11, 100218. [Google Scholar] [CrossRef]
- Fotouhi, A.; Qiang, H.; Ding, M.; Hassan, M.; Giordano, L.G.; Garcia-Rodriguez, A.; Yuan, J. Survey on UAV Cellular Communications: Practical Aspects, Standardization Advancements, Regulation, and Security Challenges. IEEE Commun. Surv. Tutor. 2019, 21, 3417–3442. [Google Scholar] [CrossRef]
- Challita, U.; Ferdowsi, A.; Chen, M.; Saad, W. Machine learning for wireless connectivity and security of cellular-connected uavs. IEEE Wirel. Commun. 2019, 26, 28–35. [Google Scholar] [CrossRef]
- Syed, F.; Gupta, S.K.; Alsamhi, S.H.; Rashid, M.; Liu, X. A survey on recent optimal techniques for securing unmanned aerial vehicles applications. Trans. Emerg. Telecommun. Technol. 2021, 32, e4133. [Google Scholar] [CrossRef]
- Hassija, V.; Chamola, V.; Agrawal, A.; Goyal, A.; Luong, N.C.; Niyato, D.; Yu, F.R.; Guizani, M. Fast, Reliable, and Secure Drone Communication: A Comprehensive Survey. IEEE Commun. Surv. Tutor. 2021, 23, 2802–2832. [Google Scholar] [CrossRef]
- Shafique, A.; Mehmood, A.; Elhadef, M. Survey of Security Protocols and Vulnerabilities in Unmanned Aerial Vehicles. IEEE Access 2021, 9, 46927–46948. [Google Scholar] [CrossRef]
- Sidhu, S.; Mohd, B.J.; Hayajneh, T. Hardware security in IoT devices with emphasis on hardware trojans. J. Sens. Actuator Netw. 2019, 8, 42. [Google Scholar] [CrossRef]
- Michailidis, E.T.; Kogias, D.G.; Voyiatzis, I. A Review on Hardware Security Countermeasures for IoT: Emerging Mechanisms and Machine Learning Solutions. In ACM International Conference Proceeding Series; Association for Computing Machinery: New York, NY, USA, 2020; pp. 268–271. [Google Scholar] [CrossRef]
- Alsharif, H.; Khan, M.A.; Michailidis, E.T.; Vouyioukas, D. A Review on Software-Based and Hardware-Based Authentication Mechanisms for the Internet of Drones. Drones 2022, 6, 41. [Google Scholar] [CrossRef]
- Michailidis, E.T.; Maliatsos, K.; Skoutas, D.N.; Vouyioukas, D.; Skianis, C. Secure UAV-Aided Mobile Edge Computing for IoT: A Review. IEEE Access 2022, 10, 86353. [Google Scholar] [CrossRef]
- Mekdad, Y.; Aris, A.; Babun, L.; El Fergougui, A.; Conti, M.; Lazzeretti, R.; Uluagac, S. A Survey on Security and Privacy Issues of UAVs. arXiv 2021, arXiv:2109.14442. [Google Scholar] [CrossRef]
- Yahuza, M.; Idris, M.Y.I.; Bin Ahmedy, I.; Wahab, A.W.A.; Nandy, T.; Noor, N.M.; Bala, A. Internet of Drones Security and Privacy Issues: Taxonomy and Open Challenges. IEEE Access 2021, 9, 57243–57270. [Google Scholar] [CrossRef]
- Yang, W.; Wang, S.; Yin, X.; Wang, X.; Hu, J. A Review on Security Issues and Solutions of the Internet of Drones. IEEE Open J. Comput. Soc. 2022, 3, 96–110. [Google Scholar] [CrossRef]
- Ko, Y.; Kim, J.; Duguma, D.G.; Astillo, P.V.; You, I.; Pau, G. Drone secure communication protocol for future sensitive applications in military zone. Sensors 2021, 21, 2057. [Google Scholar] [CrossRef] [PubMed]
- Choudhary, G.; Sharma, V.; Kim, J.; Gupta, T.; You, I. Internet of Drones (IoD): Threats, Vulnerability, and Security Perspectives. Res. Briefs Inf. Commun. Technol. Evol. 2019, 4, 64–77. [Google Scholar] [CrossRef]
- Khan, A.S.; Sattar, M.A.; Nisar, K.; Ibrahim, A.A.A.; Annuar, N.B.; bin Abdullah, J.; Memon, S.K. A Survey on 6G Enabled Light Weight Authentication Protocol for UAVs, Security, Open Research Issues and Future Directions. Appl. Sci. 2023, 13, 277. [Google Scholar] [CrossRef]
- Pandey, G.K.; Gurjar, D.S.; Nguyen, H.H.; Yadav, S. Security Threats and Mitigation Techniques in UAV Communications: A Comprehensive Survey. IEEE Access 2022, 10, 112858–112897. [Google Scholar] [CrossRef]
- Cho, G.; Cho, J.; Hyun, S.; Kim, H. SENTINEL: A secure and efficient authentication framework for unmanned aerial vehicles. Appl. Sci. 2020, 10, 3149. [Google Scholar] [CrossRef]
- Jan, S.U.; Abbasi, I.A.; Algarni, F. A key agreement scheme for IoD deployment civilian drone. IEEE Access 2021, 9, 149311–149321. [Google Scholar] [CrossRef]
- De Melo, C.F.E.; e Silva, T.D.; Boeira, F.; Stocchero, J.M.; Vinel, A.; Asplund, M.; de Freitas, E.P. UAVouch: A Secure Identity and Location Validation Scheme for UAV-Networks. IEEE Access 2021, 9, 82930–82946. [Google Scholar] [CrossRef]
- Jan, S.U.; Qayum, F.; Khan, H.U. Design and Analysis of Lightweight Authentication Protocol for Securing IoD. IEEE Access 2021, 9, 69287–69306. [Google Scholar] [CrossRef]
- Deebak, B.D.; Al-Turjman, F. A smart lightweight privacy preservation scheme for IoT-based UAV communication systems. Comput. Commun. 2020, 162, 102–117. [Google Scholar] [CrossRef]
- Tanveer, M.; Zahid, A.H.; Ahmad, M.; Baz, A.; Alhakami, H. LAKE-IoD: Lightweight Authenticated Key Exchange Protocol for the Internet of Drone Environment. IEEE Access 2020, 8, 155645–155659. [Google Scholar] [CrossRef]
- Hussain, S.; Chaudhry, S.A.; Alomari, O.A.; Alsharif, M.H.; Khan, M.K.; Kumar, N. Amassing the Security: An ECC-Based Authentication Scheme for Internet of Drones. IEEE Syst. J. 2021, 15, 4431–4438. [Google Scholar] [CrossRef]
- Ever, Y.K. A secure authentication scheme framework for mobile-sinks used in the Internet of Drones applications. Comput. Commun. 2020, 155, 143–149. [Google Scholar] [CrossRef]
- Yahuza, M.; Idris, M.Y.I.; Wahab, A.W.A.; Nandy, T.; Ahmedy, I.B.; Ramli, R. An edge assisted secure lightweight authentication technique for safe communication on the internet of drones network. IEEE Access 2021, 9, 31420–31440. [Google Scholar] [CrossRef]
- Zhang, N.; Jiang, Q.; Li, L.; Ma, X.; Ma, J. An efficient three-factor remote user authentication protocol based on BPV-FourQ for internet of drones. Peer-to-Peer Netw. Appl. 2021, 14, 3319–3332. [Google Scholar] [CrossRef]
- Gai, K.; Wu, Y.; Zhu, L.; Choo, K.K.R.; Xiao, B. Blockchain-Enabled Trustworthy Group Communications in UAV Networks. IEEE Trans. Intell. Transp. Syst. 2021, 22, 4118–4130. [Google Scholar] [CrossRef]
- Bera, B.; Das, A.K.; Sutrala, A.K. Private blockchain-based access control mechanism for unauthorized UAV detection and mitigation in Internet of Drones environment. Comput. Commun. 2021, 166, 91–109. [Google Scholar] [CrossRef]
- Yazdinejad, A.; Parizi, R.M.; Dehghantanha, A.; Karimipour, H. Federated learning for drone authentication. Ad Hoc Networks 2021, 120, 102574. [Google Scholar] [CrossRef]
- Wang, H.; Fang, H.; Wang, X. Safeguarding Cluster Heads in UAV Swarm Using Edge Intelligence: Linear Discriminant Analysis-Based Cross-Layer Authentication. IEEE Open J. Commun. Soc. 2021, 2, 1298–1309. [Google Scholar] [CrossRef]
- Veerappan, C.S.; Loh, P.K.K.; Chennattu, R.J. Smart Drone Controller Framework—Toward an Internet of Drones. In Studies in Computational Intelligence; Springer Science and Business Media Deutschland GmbH: Berlin/Heidelberg, Germany, 2022; Volume 1002, pp. 1–14. [Google Scholar] [CrossRef]
- Alladi, T.; Chamola, V.; Naren; Kumar, N. PARTH: A two-stage lightweight mutual authentication protocol for UAV surveillance networks. Comput. Commun. 2020, 160, 81–90. [Google Scholar] [CrossRef]
- Gope, P.; Millwood, O.; Saxena, N. A provably secure authentication scheme for RFID-enabled UAV applications. Comput. Commun. 2021, 166, 19–25. [Google Scholar] [CrossRef]
- Lei, Y.; Zeng, L.; Li, Y.X.; Wang, M.X.; Qin, H. A Lightweight Authentication Protocol for UAV Networks Based on Security and Computational Resource Optimization. IEEE Access 2021, 9, 53769–53785. [Google Scholar] [CrossRef]
- Alladi, T.; Naren; Bansal, G.; Chamola, V.; Guizani, M. SecAuthUAV: A Novel Authentication Scheme for UAV-Ground Station and UAV-UAV Communication. IEEE Trans. Veh. Technol. 2020, 69, 15068–15077. [Google Scholar] [CrossRef]
- Pal, V.; Acharya, B.S.; Shrivastav, S.; Saha, S.; Joglekar, A.; Amrutur, B. PUF Based Secure Framework for Hardware and Software Security of Drones. In Proceedings of the 2020 Asian Hardware Oriented Security and Trust Symposium, AsianHOST 2020, Kolkata, India, 15–17 December 2020; Institute of Electrical and Electronics Engineers Inc.: New York, NY, USA, 2020. [Google Scholar] [CrossRef]
- Ionescu, O.; Besleaga, C.; Dumitru, V.; Pricop, E. UAV identification system based on memristor physical unclonable functions. In Proceedings of the 12th International Conference on Electronics, Computers and Artificial Intelligence, ECAI 2020, Bucharest, Romania, 25–27 June 2020; Institute of Electrical and Electronics Engineers Inc.: New York, NY, USA, 2020. [Google Scholar] [CrossRef]
- Chen, A.; Peng, K.; Sha, Z.; Yang, Z.; Lu, G. ToAM: A Task-oriented Authentication Model for UAVs Based on Blockchain. EURASIP J. Wirel. Commun. Netw. 2021, 2021, 166. [Google Scholar] [CrossRef]
- Institute of Electrical and Electronics Engineers. Generating IoT traffic: A Case Study on Anomaly Detection. In Proceedings of the 26th IEEE International Symposium on Local and Metropolitan Area Networks, Virtual Conference, 13–15 July 2020. [Google Scholar]
- Bansal, G.; Naren, N.; Chamola, V.; Sikdar, B.; Kumar, N.; Guizani, M. Lightweight Mutual Authentication Protocol for V2G Using Physical Unclonable Function. IEEE Trans. Veh. Technol. 2020, 69, 7234–7246. [Google Scholar] [CrossRef]
- Alladi, T.; Chamola, V.; Naren. HARCI: A Two-Way Authentication Protocol for Three Entity Healthcare IoT Networks. IEEE J. Sel. Areas Commun. 2021, 39, 361–369. [Google Scholar] [CrossRef]
- Zhang, L.; Xu, J.; Obaidat, M.S.; Li, X.; Vijayakumar, P. A PUF-based lightweight authentication and key agreement protocol for smart UAV networks. IET Commun. 2022, 16, 1142–1159. [Google Scholar] [CrossRef]
- Pirker, D.; Fischer, T.; Lesjak, C.; Steger, C. Global and Secured UAV Authentication System based on Hardware-Security. In Proceedings of the 2020 8th IEEE International Conference on Mobile Cloud Computing, Services, and Engineering, MobileCloud 2020, Oxford, UK, 3–6 August 2020; Institute of Electrical and Electronics Engineers Inc.: New York, NY, USA, 2020; pp. 84–89. [Google Scholar] [CrossRef]
- Aissaoui, R.; Deneuville, J.-C.; Guerber, C.; Pirovano, A. UAV Traffic Management: A Survey On Communication Security. arXiv 2022, arXiv:2211.05640. [Google Scholar] [CrossRef]
- Srinivas, J.; Das, A.K.; Kumar, N.; Rodrigues, J.J.P.C. TCALAS: Temporal credential-based anonymous lightweight authentication scheme for internet of drones environment. IEEE Trans. Veh. Technol. 2019, 68, 6903–6916. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Kumar, N.; Vasilakos, A.V.; Rodrigues, J.J.P.C. Design and Analysis of Secure Lightweight Remote User Authentication and Key Agreement Scheme in Internet of Drones Deployment. IEEE Internet Things J. 2019, 6, 3572–3584. [Google Scholar] [CrossRef]
- Bera, B.; Chattaraj, D.; Das, A.K. Designing secure blockchain-based access control scheme in IoT-enabled Internet of Drones deployment. Comput. Commun. 2020, 153, 229–249. [Google Scholar] [CrossRef]
- Chaudhry, S.A.; Yahya, K.; Karuppiah, M.; Kharel, R.; Bashir, A.K.; Zikria, Y.B. GCACS-IoD: A certificate based generic access control scheme for Internet of drones. Comput. Networks 2021, 191, 107999. [Google Scholar] [CrossRef]
- Li, C.T.; Weng, C.Y.; Chen, C.L.; Lee, C.C.; Deng, Y.Y.; Imoize, A.L. An Efficient Authenticated Key Agreement Scheme Supporting Privacy-Preservation for Internet of Drones Communications. Sensors 2022, 22, 9534. [Google Scholar] [CrossRef] [PubMed]
- Park, Y.; Ryu, D.; Kwon, D.; Park, Y. Provably Secure Mutual Authentication and Key Agreement Scheme Using PUF in Internet of Drones Deployments. Sensors 2023, 23, 2034. [Google Scholar] [CrossRef]
- Javed, S.; Khan, M.A.; Abdullah, A.M.; Alsirhani, A.; Alomari, A.; Noor, F.; Ullah, I. An Efficient Authentication Scheme Using Blockchain as a Certificate Authority for the Internet of Drones. Drones 2022, 6, 264. [Google Scholar] [CrossRef]
- Zhang, S.; Liu, Y.; Han, Z.; Yang, Z. A Lightweight Authentication Protocol for UAVs Based on ECC Scheme. Drones 2023, 7, 315. [Google Scholar] [CrossRef]
- Qiao, G.; Zhuang, Y.; Ye, T.; Qiao, Y. BCDAIoD: An Efficient Blockchain-Based Cross-Domain Authentication Scheme for Internet of Drones. Drones 2023, 7, 302. [Google Scholar] [CrossRef]
- Jan, M.A.; Zhang, W.; Usman, M.; Tan, Z.; Khan, F.; Luo, E. SmartEdge: An end-to-end encryption framework for an edge-enabled smart city application. J. Netw. Comput. Appl. 2019, 137, 1–10. [Google Scholar] [CrossRef]
- Sharma, P.; Prasad, R. Techniques for Implementing Fault Tolerance in Modern Software Systems to Enhance Availability, Durability, and Reliability. Available online: https://studies.eigenpub.com/index.php/erstEigenpubReviewofScienceandTechnologyhttps://studies.eigenpub.com/index.php/erst (accessed on 20 December 2024).
- “Delivery Drone Market Analysis Opportunities 2023–2030”. Available online: https://bisresearch.com/industry-report/drone-delivery-market.html (accessed on 20 December 2024).
- Drone Delivery FAQs—Amazon Customer Service. Available online: https://www.amazon.com/gp/help/customer/display.html?nodeId=T3jxhuvPfQ629BOIL4 (accessed on 5 May 2025).
- Grassi, P.A.; Fenton, J.L.; Newton, E.M.; Perlner, R.A.; Regenscheid, A.R.; Burr, W.E.; Richer, J.P. Digital Identity Guidelines: Authentication and Lifecycle Management; National Institute of Standards and Technology U.S. Department of Commerce: Gaithersburg, MD, USA, 2017. [CrossRef]
- Abro, G.E.M.; Zulkifli, S.A.B.M.; Masood, R.J.; Asirvadam, V.S.; Laouti, A. Comprehensive Review of UAV Detection, Security, and Communication Advancements to Prevent Threats. Drones 2022, 6, 284. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).